3fa79c3ff1376562608a2bb4889e5ad2.ppt
- Количество слайдов: 46

Cybercrime workshop DPS Noida 20 th. May 2010 Introduction to cyberspace laws Karnika Seth Cyberlaw & IP expert Managing Partner, Seth Associates Chairperson, Cyberlaws Consulting Centre

Introduction p p p Seth Associates is a leading full service Indian law firm that is internationally networked to provide spectrum of legal services to its domestic and international clients Network of 2000 associate offices of Association of European lawyers (AEA alliance) as foreign associates We maintain one of the strongest Cyberlaws practice in India today. With more than a decade's experience in Cyberlaws Practice, Seth Associates recently established the World's first integrated 'Cyberlaws Consulting Centre' at Seth Associates

CCC- Cyberlaws Consulting Centre p p CCC renders cyber legal consultancy, cyber law analytics and forensic services to its clients world wide. Work experience of handling cybercrime matters with Delhi Police Delivered training workshops to Delhi police on dealing with cybercrime investigation cases Recently authored a book titled ‘Cyberlaws in the Information Technology age’ published by Lexis Nexis Butterworths that elucidates the key developments in the field of Cyberlaws across many important jurisdictions—India, United States and European nations

‘Cyberlaws in the Information Technology Age’ by Karnika Seth

Presentation plan p p p What is cyberspace? Regulating the internet The Internet usage categories of cybercrimes Child exploitation on internet Analysis of the cybercrime & Indian legal position case studies offences & penalties in IT Act, 2000 possible reliefs to a cybercrime victim and strategy adoption Incident response Legal recourse safety tips & best practices
What is the Cyberspace? p p p William Gibson in 1980 s wrote a science fiction named Neuromancer wherein computer hackers waged war against secure data. The setting had no physical existence and was named ‘Cyberspace’ by Gibson. Unique features - dynamic, borderless space, anonymity, speed, cost effective, marked with rapid technological advances
Regulating the Internet. . p p p Proponents of Cyberlaws believe that one’s activities on the Internet need regulation by framing laws and rules that govern our activities in the cyberspace. This branch of law is termed as “Cyberlaws” European Union, USA, UNCITAL framed important laws to govern cyberspace UNCITRAL Model law of ecommerce 1996 EU data protection Directive DMCA Act 1998 in USA WIPO domain name dispute Resolution policy p p Critics who advocate ‘no regulation’ or ‘self regulation’ in the Virtual space believe that government should have minimum interference in regulating the cyberspace and its use of surveillance or censorship measures. John Perry Barlow’s “Declaration of the Independence of the cyberspace” and David G. Post, The “Unsettled Paradox”: The Internet, the State, and the Consent of the Governed, 5 IND. J. GLOBAL LEGAL STUD. 521, 539 (1998)
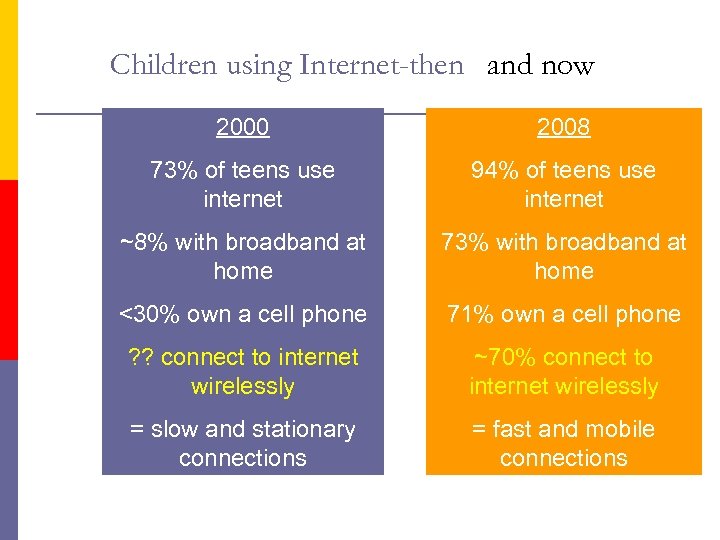
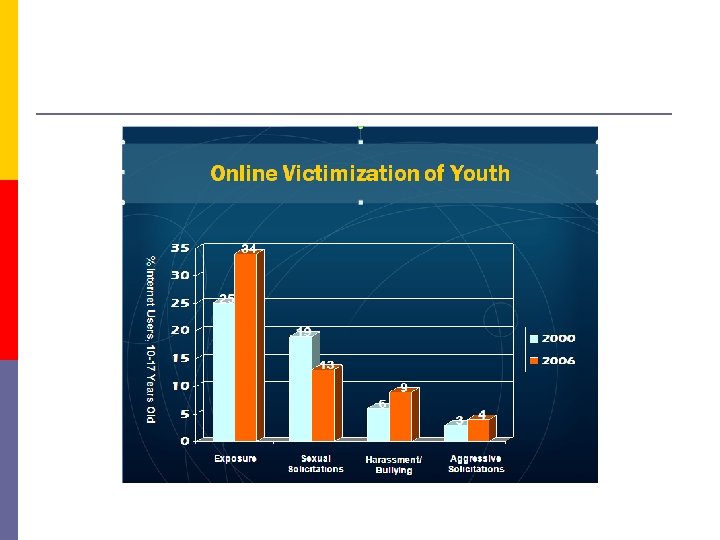
Children using Internet-then and now 2000 2008 73% of teens use internet 94% of teens use internet ~8% with broadband at home 73% with broadband at home <30% own a cell phone 71% own a cell phone ? ? connect to internet wirelessly ~70% connect to internet wirelessly = slow and stationary connections = fast and mobile connections
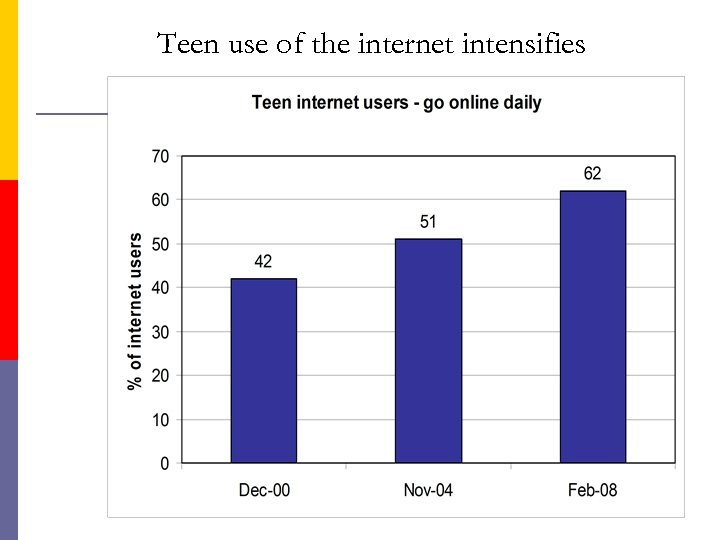
Teen use of the internet intensifies
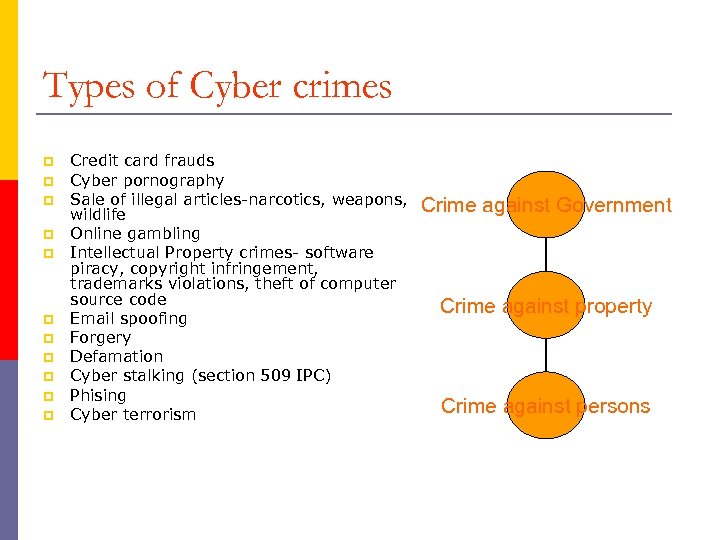
Types of Cyber crimes p p p Credit card frauds Cyber pornography Sale of illegal articles-narcotics, weapons, wildlife Online gambling Intellectual Property crimes- software piracy, copyright infringement, trademarks violations, theft of computer source code Email spoofing Forgery Defamation Cyber stalking (section 509 IPC) Phising Cyber terrorism Crime against Government Crime against property Crime against persons
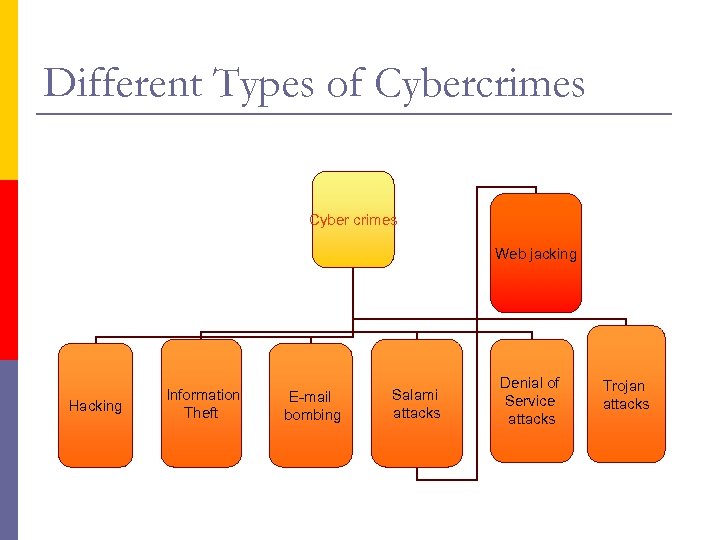
Different Types of Cybercrimes Cyber crimes Web jacking Hacking Information Theft E-mail bombing Salami attacks Denial of Service attacks Trojan attacks
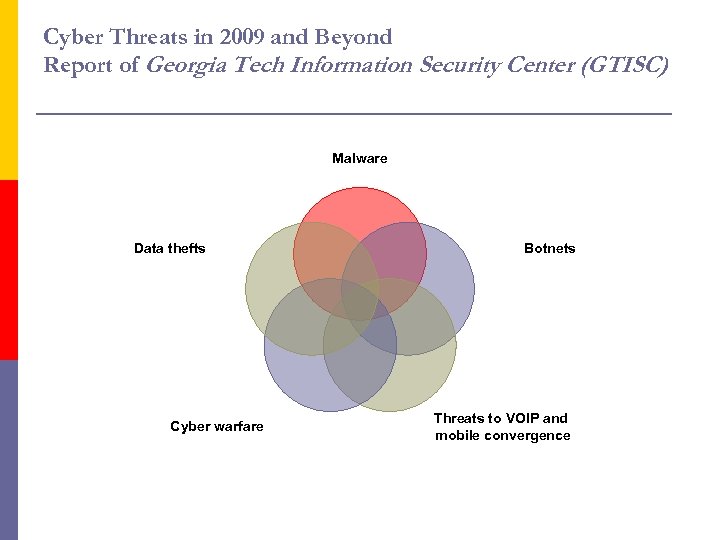
Cyber Threats in 2009 and Beyond Report of Georgia Tech Information Security Center (GTISC) Malware Data thefts Cyber warfare Botnets Threats to VOIP and mobile convergence
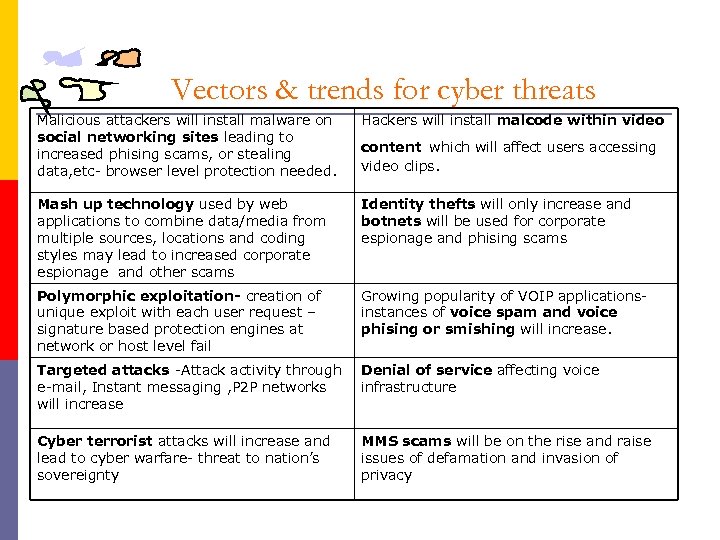
Vectors & trends for cyber threats Malicious attackers will install malware on social networking sites leading to increased phising scams, or stealing data, etc- browser level protection needed. Hackers will install malcode within video Mash up technology used by web applications to combine data/media from multiple sources, locations and coding styles may lead to increased corporate espionage and other scams Identity thefts will only increase and botnets will be used for corporate espionage and phising scams Polymorphic exploitation- creation of unique exploit with each user request – signature based protection engines at network or host level fail Growing popularity of VOIP applicationsinstances of voice spam and voice phising or smishing will increase. Targeted attacks -Attack activity through e-mail, Instant messaging , P 2 P networks will increase Denial of service affecting voice infrastructure Cyber terrorist attacks will increase and lead to cyber warfare- threat to nation’s sovereignty MMS scams will be on the rise and raise issues of defamation and invasion of privacy content which will affect users accessing video clips.
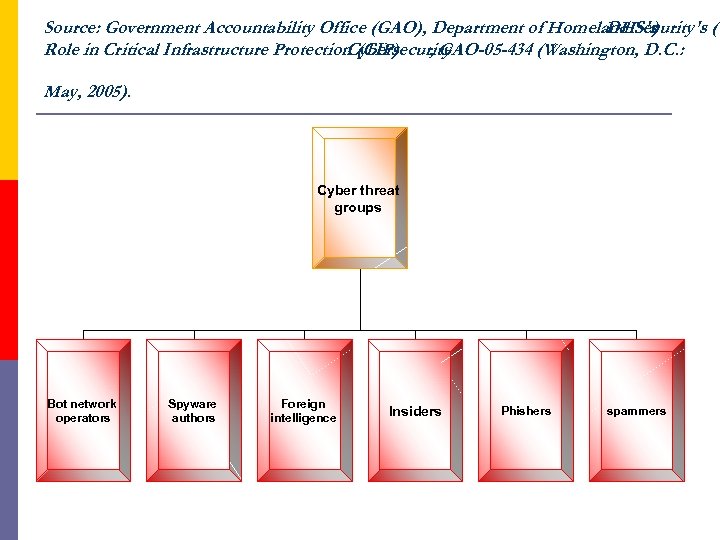
Source: Government Accountability Office (GAO), Department of Homeland Security's ( DHS's ) Role in Critical Infrastructure Protection (CIP) Cybersecurity , GAO-05 -434 (Washington, D. C. : May, 2005). Cyber threat groups Bot network operators Spyware authors Foreign intelligence Insiders Phishers spammers

Striking facts! p According to a report compiled by Panda Labs, in 2008, 10 million bot computers were used to distribute spam and malware across the Internet each day. p Annual take by theft-oriented cyber criminals is estimated to be as high as 100 billion dollars and 97 per cent of these offences go undetected, -CBI's Conference on International Police Cooperation against Cyber Crime, March 2009 .

Internet & Child Exploitation p Cultural & historical differences in definition of childhood and attitudes towards children p Work, slavery, marriage, prostitution p Sexual contact with children defined as pedophilia p Viewing children in sexual poses or sexual contact is child pornography p Internet has facilitated distribution p Digital techniques of photographic modification and image creation playing increasing role in generating child porn

Children on Internet could be victimized p p p p Cyber bullying Child pornography Child abuse Cognitive distortions Identity theft cases Cheating & fraud Lured into criminal activities Theft of personal information

General concerns for children online p p p May inadvertently or intentionally access adult pornographic or violent material Links or emails with innocent subjects that actually contain pornography Children being approached or observed in chat rooms Children’s identities, location or vulnerability being sourced from material available online Social networking sites may introduce child pornography

Unique problems arising from child pornography on the internet p p p p p Lack of borders/mobility Differences in international law Anonymity Accessibility Quantity Satiation and subsequent increasing thresholds for content Normalise deviant sexual interest Desire to replicate scenarios viewed on the internet Commercial trading Peer-to-peer networks n n Huge digital collections Encrypted files

Cyber Predators Statistics p p p “…A child goes missing every 40 seconds in the U. S, over 2, 100 per day” (OJJDP) In 2005, 662, 196 children were reported lost, runaway, or kidnapped (ncmec) 2/3 of all missing children reports were for youths aged 1517 (ncmec) 2/5 missing children ages 15 -17 are abducted due to Internet activity (ICAC) Air force Bal Bharati School case , Delhi; class(XII) student created pornographic site as revenge against his classmates (girls) and posted pornographic images of his classmates and lady teachers in internet. He was then suspended by school and arrested by Police under IPC and IT Act; though Juvenile Court allowed his bail thereafter.

Glaring Examples – Data thefts p p p The incidents in the recent past involving Cyber Space have highlighted the issues of privacy and data protection in India The Pune scam was the first among the many BPO frauds that made international headlines. In April 2005, five employees of Msourc. E in Pune were arrested for allegedly pulling off a fraud worth nearly 2. 5 crore rupees from the Citibank accounts of four New York-based account holders. In June 2005, the British tabloid Sun, in a sting operation, purchased the bank account details of 1, 000 Britons from Karan Bahree, an employee of Gurgaon-based BPO company Infinity E-Search.

The Noida MMS Scandal p p p In February 2009, an MBA student in Noida a boy circulated video clip of his 23 -year-old-girlfriend doing striptease for him to his classmates using the girl's email id. After the girl refused to marry him, the boy who had access to the girl's mail id and circulated that MMS clip to fellow students. Police registered a case of criminal intimidation following a complaint filed by the girl's family

Email spoofing: p Pranab Mitra , former executive of Gujarat Ambuja Cement posed as a woman, Rita Basu, and created a fake e-mail ID through which he contacted one V. R. Ninawe an Abu Dhabi businessmen. After long cyber relationship and emotional massages Mitra sent an e-mail that ‘‘she would commit suicide’’ if Ninawe ended the relationship. He also gave him ‘‘another friend Ruchira Sengupta’s’’ e-mail ID which was in fact his second bogus address. When Ninawe mailed at the other ID he was shocked to learn that Mitra had died and police is searching Ninawe. Mitra extorted few lacs Rupees as advocate fees etc. Mitra even sent e-mails as high court and police officials to extort more money. Ninawe finally came down to Mumbai to lodge a police case.

The Information Technology Act, 2000 and cybercrimes p p The Information Technology Act 2000 came into force in India on 17 October 2000. It extends to whole of India and also applies to any offence or contraventions committed outside India by any person (s 1(2), IT Act 2000). According to s 75 of the Act, the Act applies to any offence or contravention committed outside India by any person irrespective of his nationality, if such act involves a computer, computer system or network located in India.

Main Features of IT Act, 2000 Applicable to communications made through cell phones , PDAs p Conferred legal validity and recognition to electronic documents & digital signatures p Legal recognition to e-contracts p Set up Regulatory regime to supervise Certifying Authorities p Laid down civil and criminal liabilities for contravention of provisions of IT Act, 2000 p Created the office of Adjudicating Authority to adjudge contraventions p
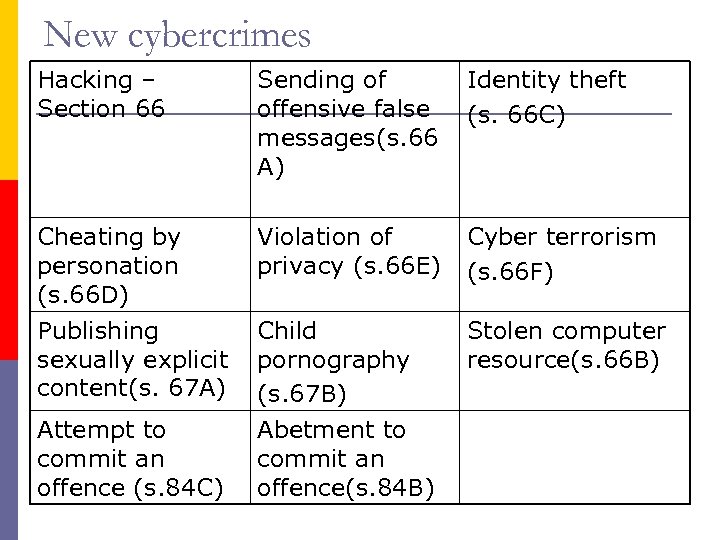
New cybercrimes Hacking – Section 66 Sending of offensive false messages(s. 66 A) Identity theft (s. 66 C) Cheating by personation (s. 66 D) Publishing sexually explicit content(s. 67 A) Violation of privacy (s. 66 E) Cyber terrorism (s. 66 F) Child pornography (s. 67 B) Stolen computer resource(s. 66 B) Attempt to commit an offence (s. 84 C) Abetment to commit an offence(s. 84 B)

Cognisability & bailability p p p Most offences introduced by the 2008 amendments prescribe punishment of upto 3 yrs , fine of one lac/2 lac For hacking term of imprisonment remains upto 3 yrs but fine increased from 2 lakhs to 5 lacs In S. 67 imprisonment term reduced from 5 yrs to three yrs. Fine increased from one lac to 5 lacs. Most Offences are cognisable but bailable This is a new challenge for cyberlaw enforcement authorities- need quick action by trained investigators to collect and preserve evidence as probability of tampering increases.
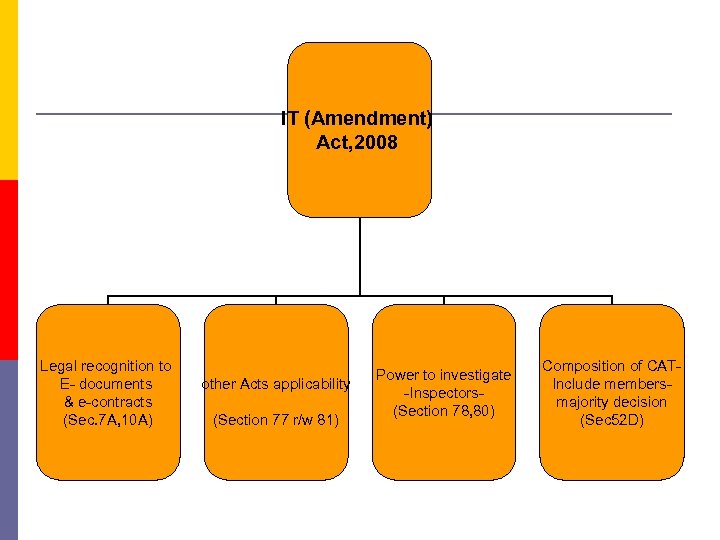
IT (Amendment) Act, 2008 Legal recognition to E- documents & e-contracts (Sec. 7 A, 10 A) other Acts applicability (Section 77 r/w 81) Power to investigate -Inspectors(Section 78, 80) Composition of CATInclude membersmajority decision (Sec 52 D)

Special and General statutes applicable to cybercrimes p p While the IT Act 2000, provides for the specific offences it has to be read with the Indian Penal Code 1860 (IPC) and the Code of Criminal Procedure 1973 (Cr PC) IT Act is a special law, most IT experts are of common consensus that it does not cover or deal specifically with every kind of cyber crime for instance, for defamatory emails reliance is placed on s 500 of IPC, for threatening e-mails, provisions of IPC applicable thereto are criminal intimidation (ch XXII), extortion (ch XVII), for e-mail spoofing, provisions of IPC relating to frauds, cheating by personation (ch XVII) and forgery (ch XVIII) are attracted. Likewise, criminal breach of trust and fraud (ss 405, 406, 408, 409) of the IPC are applicable and for false electronic evidence, s 193 of IPC applies. For cognisability and bailability, reliance is placed on Code of Criminal Procedure which also lays down the specific provisions relating to powers of police to investigate.

Incident Response – a precursor to Techniques of Cyber investigation & forensic tools p ‘Incident response’ could be defined as a precise set of actions to handle any security incident in a responsible , meaningful and timely manner. p Goals of incident response. To confirm whether an incident has occurred To promote accumulation of accurate information Educate senior management Help in detection/prevention of such incidents in the future, To provide rapid detection and containment Minimize disruption to business and network operations To facilitate for criminal action against perpetrators p p p p

Possible reliefs to a cybercrime victimstrategy adoption p p p A victim of cybercrime needs to immediately report the matter to his local police station and to the nearest cybercrime cell Depending on the nature of crime there may be civil and criminal remedies. In civil remedies , injunction and restraint orders , blocking of websites, may be sought, together with damages, delivery up of infringing matter and/or account for profits. In criminal remedies, a cybercrime case will be registered by police if the offence is cognisable and if the same is non cognisable, a complaint should be filed with metropolitan magistrate For certain offences, both civil and criminal remedies may be available to the victim

Before lodging a cybercrime case p p Important parameters. Gather ample evidence admissible in a court of law Fulfill the criteria of the pecuniary , territorial and subject matter jurisdiction of a court. Determine jurisdiction – case may be filed where the offence is committed or where effect of the offence is felt ( S. 177 to 179, Crpc)
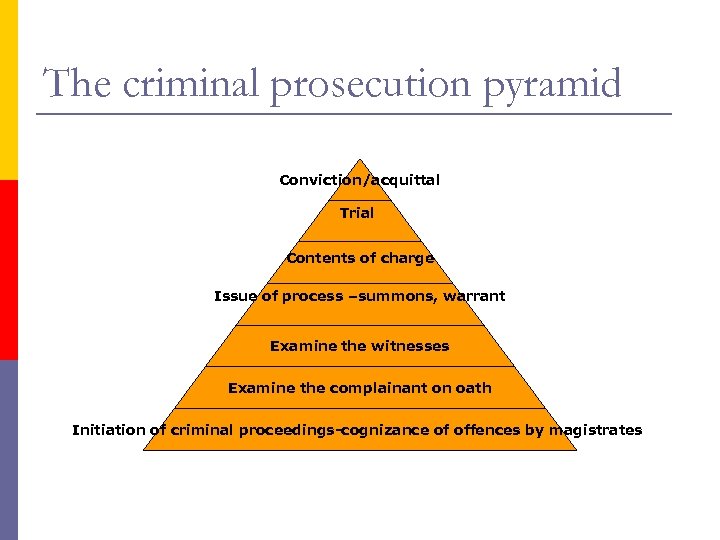
The criminal prosecution pyramid Conviction/acquittal Trial Contents of charge Issue of process –summons, warrant Examine the witnesses Examine the complainant on oath Initiation of criminal proceedings-cognizance of offences by magistrates

Preparation for prosecution p p p p Collect all evidence available & saving snapshots of evidence Seek a cyberlaw expert’s immediate assistance for advice on preparing for prosecution Prepare a background history of facts chronologically as per facts Pen down names and addresses of suspected accused. Form a draft of complaint and remedies a victim seeks Cyberlaw expert & police could assist in gathering further evidence e. g tracing the IP in case of e-mails, search & seizure or arrest as appropriate to the situation A cyber forensic study of the hardware/equipment/ network server related to the cybercrime is generally essential

Defending an accused in a cybercrime p p p p Preparation of chain of events table Probing where evidence could be traced? E-mail inbox/files/folders/ web history Has the accused any erase evidence software/tools Forensically screening the hardware/data/files /print outs / camera/mobile/pendrives of evidentiary value Formatting may not be a solution Apply for anticipatory bail Challenge evidence produced by opposite party and look for loopholes Filing of a cross complaint if appropriate

Amendments- Indian Evidence Act 1872 p p Section 3 of the Evidence Act amended to take care of admissibility of ER as evidence along with the paper based records as part of the documents which can be produced before the court for inspection. Section 4 of IT Act confers legal recognition to electronic records

Societe products Nestle SA case Des 2006 (33 ) PTC 469 p By virtue of provision of Section 65 A, the contents of electronic records may be proved in evidence by parties in accordance with provision of 65 B. p Held- Sub section (1) of section 65 B makes admissible as a document, paper print out of electronic records stored in optical or magnetic media produced by a computer subject to fulfillment of conditions specified in subsection 2 of Section 65 B. The computer from which the record is generated was regularly used to store or process information in respect of activity regularly carried on by person having lawful control over the period, and relates to the period over which the computer was regularly used. Information was fed in the computer in the ordinary course of the activities of the person having lawful control over the computer. The computer was operating properly, and if not, was not such as to affect the electronic record or its accuracy. Information reproduced is such as is fed into computer in the ordinary course of activity. a) b) c) d) p State v Mohd Afzal, 2003 (7) AD (Delhi)1

State v Navjot Sandhu (2005)11 SCC 600 p Held, while examining Section 65 B Evidence Act, it may be that certificate containing details of subsection 4 of Section 65 is not filed, but that does not mean that secondary evidence cannot be given. p Section 63 & 65 of the Indian Evidence Act enables secondary evidence of contents of a document to be adduced if original is of such a nature as not to be easily movable.

Presumptions in law- Section 85 B Indian Evidence Act p The law also presumes that in any proceedings, involving secure digital signature, the court shall presume, unless the contrary is proved, that the secure digital signature is affixed by the subscriber with the intention of signing or approving the electronic record p In any proceedings involving a secure electronic record, the court shall presume, unless contrary is proved, that the secure electronic record has not been altered since the specific point of time, to which the secure status relates
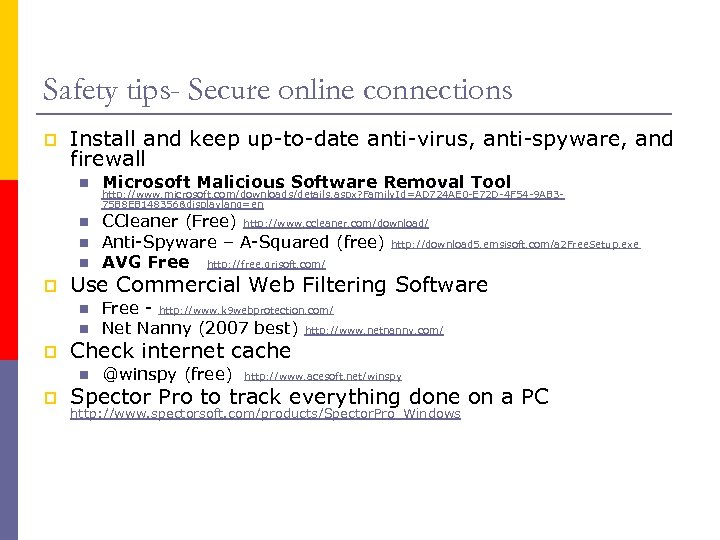
Safety tips- Secure online connections p Install and keep up-to-date anti-virus, anti-spyware, and firewall n Microsoft Malicious Software Removal Tool n CCleaner (Free) http: //www. ccleaner. com/download/ Anti-Spyware – A-Squared (free) http: //download 5. emsisoft. com/a 2 Free. Setup. exe AVG Free http: //free. grisoft. com/ n n p Use Commercial Web Filtering Software n n p Free - http: //www. k 9 webprotection. com/ Net Nanny (2007 best) http: //www. netnanny. com/ Check internet cache n p http: //www. microsoft. com/downloads/details. aspx? Family. Id=AD 724 AE 0 -E 72 D-4 F 54 -9 AB 375 B 8 EB 148356&displaylang=en @winspy (free) http: //www. acesoft. net/winspy Spector Pro to track everything done on a PC http: //www. spectorsoft. com/products/Spector. Pro_Windows

Live demo- sending fake e-mails and reading headers , phising attacks p p p p p Use of www. fakemailer. net Use of Who is Dissecting header and body of an e-mail message digest, IP address Return path Sender’s address Live demo phising- www. noodlebank. com, www. nood 1 ebank. com www. whois. sc www. readnotify. com
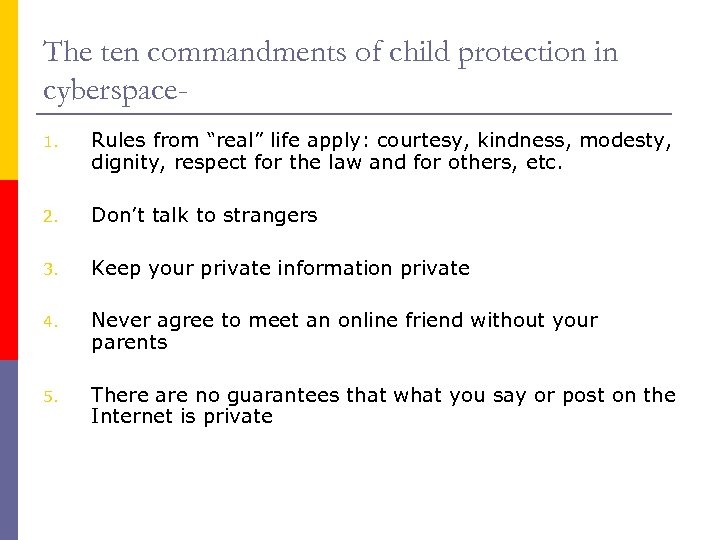
The ten commandments of child protection in cyberspace 1. Rules from “real” life apply: courtesy, kindness, modesty, dignity, respect for the law and for others, etc. 2. Don’t talk to strangers 3. Keep your private information private 4. Never agree to meet an online friend without your parents 5. There are no guarantees that what you say or post on the Internet is private
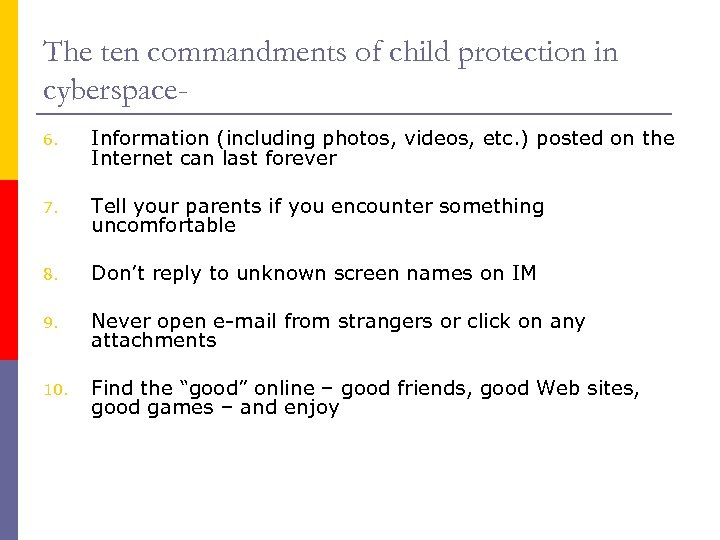
The ten commandments of child protection in cyberspace 6. Information (including photos, videos, etc. ) posted on the Internet can last forever 7. Tell your parents if you encounter something uncomfortable 8. Don’t reply to unknown screen names on IM 9. Never open e-mail from strangers or click on any attachments 10. Find the “good” online – good friends, good Web sites, good games – and enjoy
Precautions are better than cure. . p Discuss and agree upon precautions n n n People may not be who they say they are online Encourage the use of pen names Remove address and contact details from emails Never respond to obscene or suggestive messages Don’t send personal photos over the internet

Thank you! SETH ASSOCIATES ADVOCATES AND LEGAL CONSULTANTS New Delhi Law Office: C-1/16, Daryaganj, New Delhi-110002, India Tel: +91 (11) 65352272, +91 9868119137 Corporate Law Office: B-10, Sector 40, NOIDA-201301, N. C. R , India Tel: +91 (120) 4352846, +91 9810155766 Fax: +91 (120) 4331304 E-mail: mail@sethassociates. com
3fa79c3ff1376562608a2bb4889e5ad2.ppt