7577e5c156dc05a544cb852724e07c3b.ppt
- Количество слайдов: 23

CYBERCRIME Next Generation Cyber Threats: CHALLENGE A Glance. Investigating and Prosecuting Cybercrime Into the Future The Challenge of MSU Forum: April 12 -15, 2010 Marc Goodman, Chief Cyber Criminologist Dr. Marco Gercke Cybercrime Research Institute (c) 2010 Cybercrime Research Institute Page: 1

THE FUTURE IS ALREADY HERE – IT IS JUST UNEVENLY DISTRIBUTED. William Gibson, Neuromancer (c) 2010 Cybercrime Research Institute Seite: 2
LIFE MOVES ONLINE • Increasingly all aspects of human existence are moving into cyberspace, including • Work • Play • Education • Politics • Crime • Conflict (c) 2010 Cybercrime Research Institute Seite: 3

Technological Trends • • • Social Networking Virtual Worlds Cloud Computing Artificial Intelligence Biology/Genomics GPS/Location Awareness Mobile Computing Nanotechnology RFID Robotics Space/Satellite Web 3. 0/Semantic Web (c) 2010 Cybercrime Research Institute Picture removed in print version Bild zur Speicheroptimierung entfernt Seite: 4
Social Networking • • • Increasingly “life” is taking place online. If it happens there, it is real. If it doesn’t happy there, it never happened. 400 Million Facebook members… and counting Numerous crime possibilities, privacy concerns, pictures, network connections, etc (c) 2010 Cybercrime Research Institute Seite: 5

Virtual Worlds • • • They are real for those who use them 20% of MMORPG gamers say that the virtual world is their primary place of residence. The real world, a. k. a. meatspace, is just a place to get food and sleep. (c) 2010 Cybercrime Research Institute Seite: 6

Life in a Virtual World. The Good CYBERCRIME THANK YOU CHALLENGE The Challenge of Investigating and Prosecuting Cybercrime Buy a Coke Attend a U 2 Concert Dr. Marco Gercke Cybercrime Research Institute Test Drive a Toyota (c) 2010 Cybercrime Research Institute Visit Swedish Embassy Page: 7
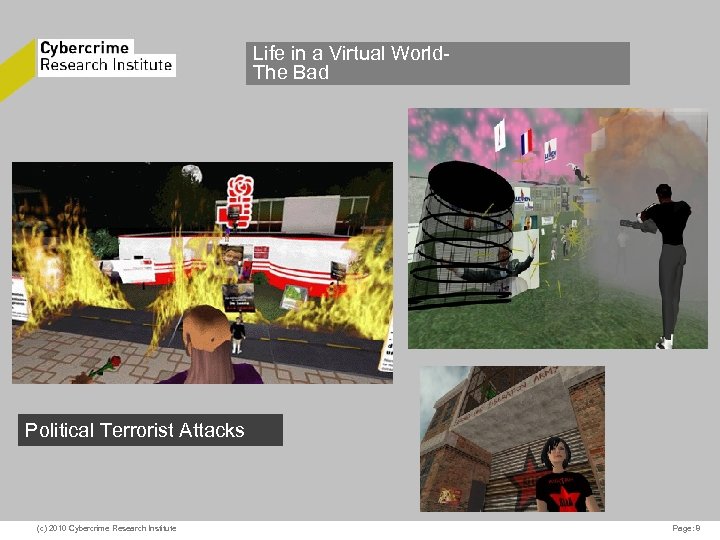
Life in a Virtual World. The Bad CYBERCRIME CHALLENGE The Challenge of Investigating and Prosecuting Cybercrime Political Terrorist Attacks Dr. Marco Gercke Cybercrime Research Institute (c) 2010 Cybercrime Research Institute Page: 8
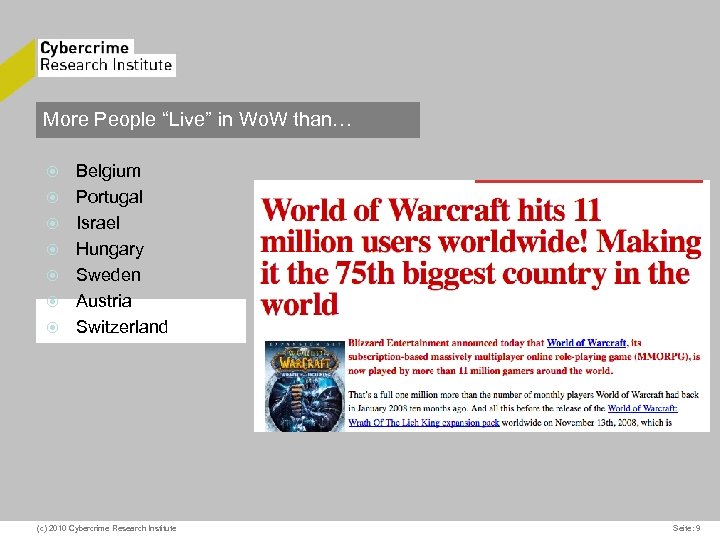
More People “Live” in Wo. W than… Belgium Portugal Israel Hungary Sweden Austria Switzerland (c) 2010 Cybercrime Research Institute Seite: 9
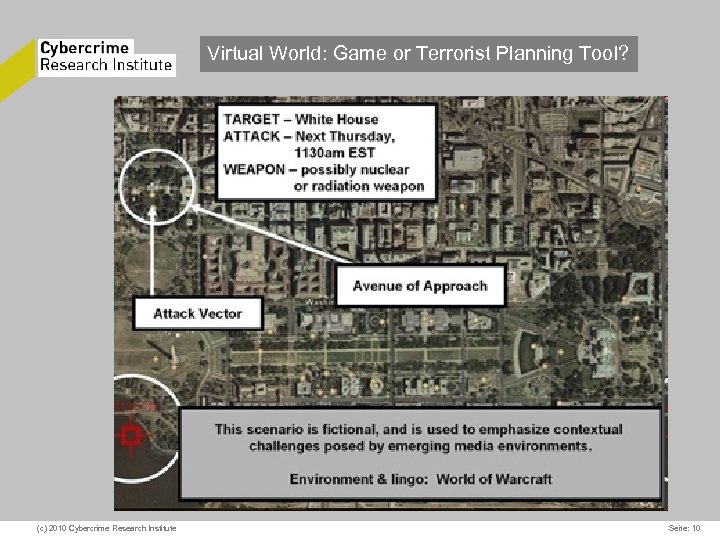
Virtual World: Game or Terrorist Planning Tool? (c) 2010 Cybercrime Research Institute Seite: 10

Virtual Worlds Have Virtual Economies • • People trade “real currencies” for virtual ones…some with ATM cards Estimated to be 12 -15 billion dollar (US) economy per year (8 B in China alone). Creates significant opportunities for money laundering and terrorist financing. Virtual currencies not regulated by international financial reporting standards, such as FATF. (c) 2010 Cybercrime Research Institute Seite: 11
Biology Meets Information Technology • • • Hacking the Human Heart Smaller technology being installed in the body—integration of IT and biology Cheaper monitoring from a distance, saves money for doctors. Pacemakers, diabetic pumps, cochlear implants/hearing aids are increasingly connected to the Internet. Coming days of Nanomedicine. University of Massachusetts study, March 2008 -Medtronic pacemaker attack technically possible. (c) 2010 Cybercrime Research Institute Seite: 12
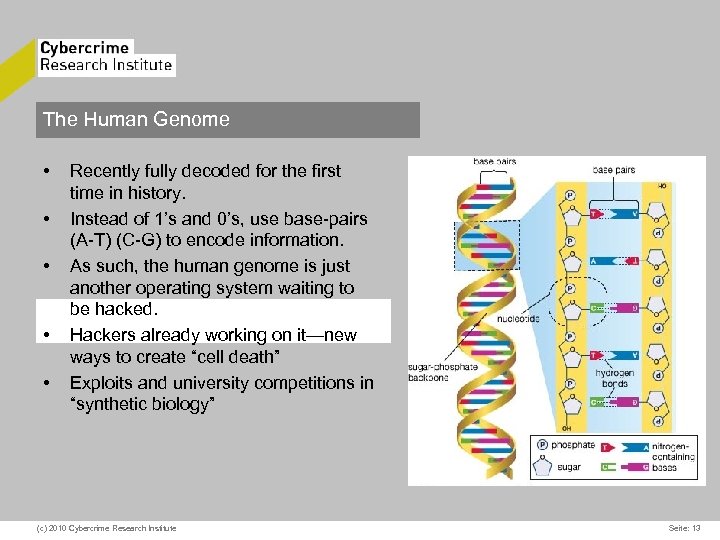
The Human Genome • • • Recently fully decoded for the first time in history. Instead of 1’s and 0’s, use base-pairs (A-T) (C-G) to encode information. As such, the human genome is just another operating system waiting to be hacked. Hackers already working on it—new ways to create “cell death” Exploits and university competitions in “synthetic biology” (c) 2010 Cybercrime Research Institute Seite: 13

Mobile Computing: • • • Growing power of mobile phones. It took approximately 35 years for to achieve the first one billion internet users. The second billion users will be added in the next three years, most of whom will access the Internet on mobile devices. (c) 2010 Cybercrime Research Institute Seite: 14
The Rise of Robotics: Connecting Robots to the Grid • • • Robotics is in its infancy Will grow very rapidly-the trend is clear, lower costs speed development Already have very basic robots (Roomba Vacuum) Home systems (heating, security, fire) connected to Net…why not robot? Robots poised to become as commonplace as computers They look cute…now. (c) 2010 Cybercrime Research Institute Seite: 15

Current Uses of Robots • • Factory automation (workers killed) Taking Care of the Elderly (Japan) Street Police Patrol (UK, Japan) Warfare (c) 2010 Cybercrime Research Institute Seite: 16

Subverting Robotic Systems • • Terrorists intercept and view predator drone feeds in Iraq (Dec. 2009) Armed Robots…Is this a good idea? Hackers obtain access to armed police robots, can be used against authorities. The case of South Africa (May 2009) (c) 2010 Cybercrime Research Institute Seite: 17

Passing the Turing Test: Full Automation of Crime and Cyber Attacks • • • In 1950, Alan Turing (father of modern AI) asked how we can tell if a machine is “intelligent” He concluded that if a neutral observer could not distinguish between a computer and a human being having a conversation, then computers would have achieved intelligence. When once cannot determine that he is talking to a machine, the computer is said to have passed the Turing Test. Already seeing applications of AI in organized crime botnets; humans not part of the game. Could be directed against state authorities. (c) 2010 Cybercrime Research Institute Seite: 18
Moore’s Law: In 1965, Gordon CYBERCRIME E. Moore, co-founder of Intel, accurately predicted that the capacity of computer chips would double every two years. CHALLENGE The Challenge of Investigating and Prosecuting Cybercrime People do not obey Moore's Law… Dr. Marco Gercke Cybercrime Research Institute (c) 2010 Cybercrime Research Institute Page: 19
Ray Kurzweil: The Singularity The technological singularity is a theoretical future point of CYBERCRIME unprecedented technological progress—typically associated with advancements in computer hardware or the ability of CHALLENGE The Challenge of machines. Investigating and Prosecuting Cybercrime using artificial intelligence to improve themselves Dr. Marco Gercke Cybercrime Research Institute (c) 2010 Cybercrime Research Institute What are the security implications of living with computers that are smarter than human beings? Page: 20

So what does this all mean? • • When we are speaking of “Partnership of State Authorities, Civil Society and the Business Community in Ensuring Information Security and Combating Terrorism… Technology is here to stay More and smarter devices connected than ever before. Soon desktop computer will exceed processing power of human brain— what will be security threats then? (c) 2010 Cybercrime Research Institute Seite: 21

Therefore: • • • We must build our frameworks to understand these problems now Sense of urgency regarding the threat Cooperative agreements must be secured now, before it is too late, or the problem is literally beyond our comprehension. Care and consideration must be applied before connecting new devices to the network. Security implications must be understood and considered. Forums such as these are an important step forward in international cooperation against transnational cyber threats (c) 2010 Cybercrime Research Institute Seite: 22
CYBERCRIME THANK YOU CHALLENGE FOR YOUR The Challenge of Investigating and Prosecuting Cybercrime ATTENTION Marc Goodman, Chief Cyber Criminologist Dr. Marco Gercke Cybercrime Research Institute (c) 2010 Cybercrime Research Institute Page: 23
7577e5c156dc05a544cb852724e07c3b.ppt