a2146505c1d89b59b23c2908936b9aa8.ppt
- Количество слайдов: 24

Cyber Threat Preparedness Amos Auringer Gartner Executive Programs Colorado Government IT Summit, November 2008, Denver, Colorado Government systems make attractive targets for many reasons, but chief among them is the vast amount of private and confidential information stored - all of which can potentially be misused for criminal profit or just plain mischief. The challenge of keeping systems and data secure is a perpetually moving target and it is vital to have the right set of tools and safeguards. This session looks at the latest strategies and solutions being used in the public sector. Notes accompany this presentation. Please select Notes Page view. These materials can be reproduced only with written approval from Gartner. Such approvals must be requested via e-mail: vendor. relations@gartner. com. Gartner is a registered trademark of Gartner, Inc. or its affiliates.

Life Is Dangerous, but Better Than the Alternatives • New threats appear continuously, but not completely unpredictably. • Most new threats will follow the introduction of new technologies, but the most-dangerous ones will come when the technology is mainstream. • Old threats never die — the trick is to reduce the cost of dealing with them. • Every threat can be mitigated or avoided — the question is always cost.
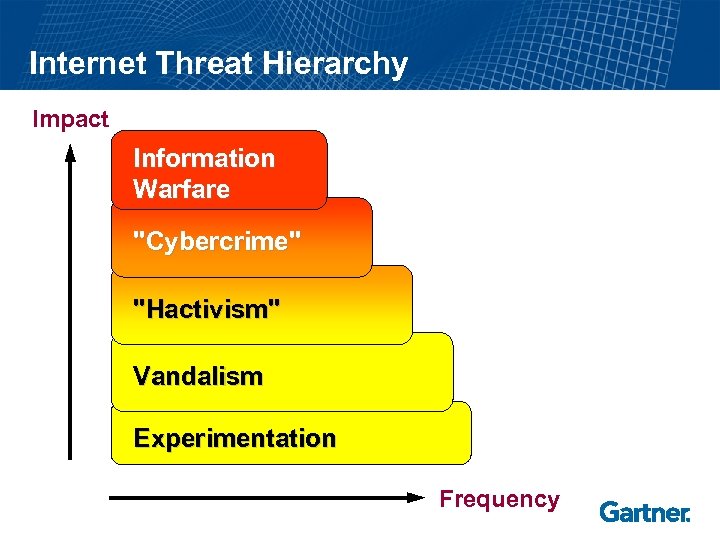
Internet Threat Hierarchy Impact Information Warfare "Cybercrime" "Hactivism" Vandalism Experimentation Frequency
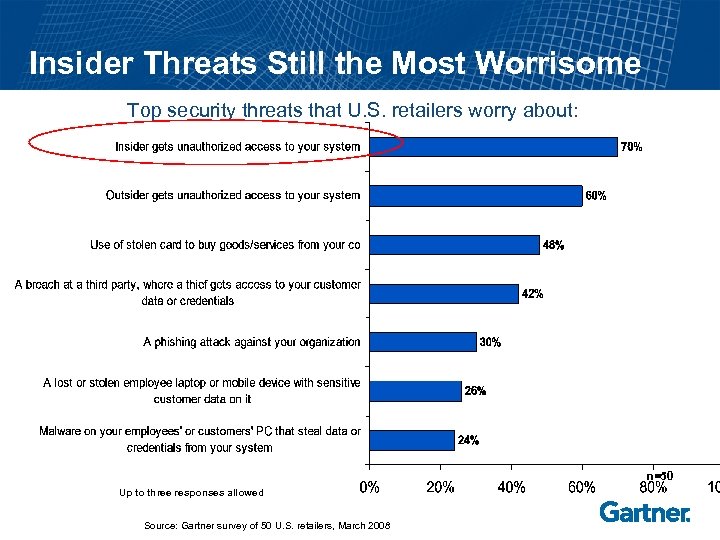
Insider Threats Still the Most Worrisome Top security threats that U. S. retailers worry about: n=50 Up to three responses allowed Source: Gartner survey of 50 U. S. retailers, March 2008
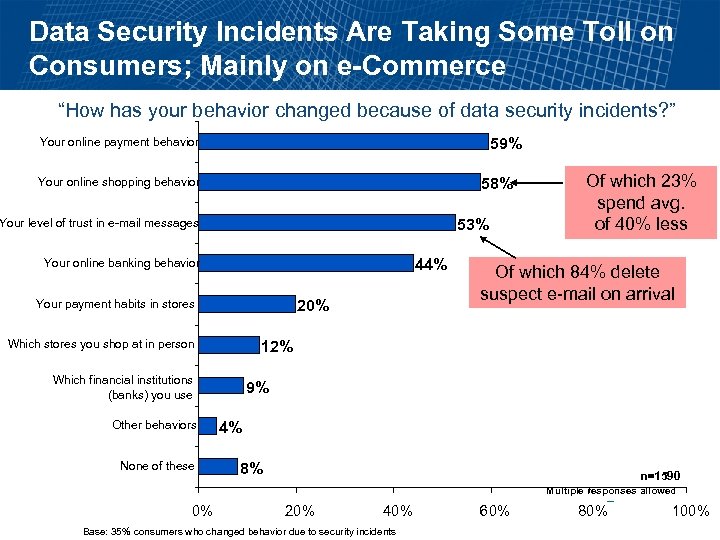
Data Security Incidents Are Taking Some Toll on Consumers; Mainly on e-Commerce “How has your behavior changed because of data security incidents? ” 59% Your online payment behavior 58% Your online shopping behavior 53% Your level of trust in e-mail messages 44% Your online banking behavior 20% Your payment habits in stores Which stores you shop at in person None of these Of which 84% delete suspect e-mail on arrival 12% Which financial institutions (banks) you use Other behaviors Of which 23% spend avg. of 40% less 9% 4% 8% n=1590 Multiple responses allowed 0% 20% 40% Base: 35% consumers who changed behavior due to security incidents 60% 80% 100%
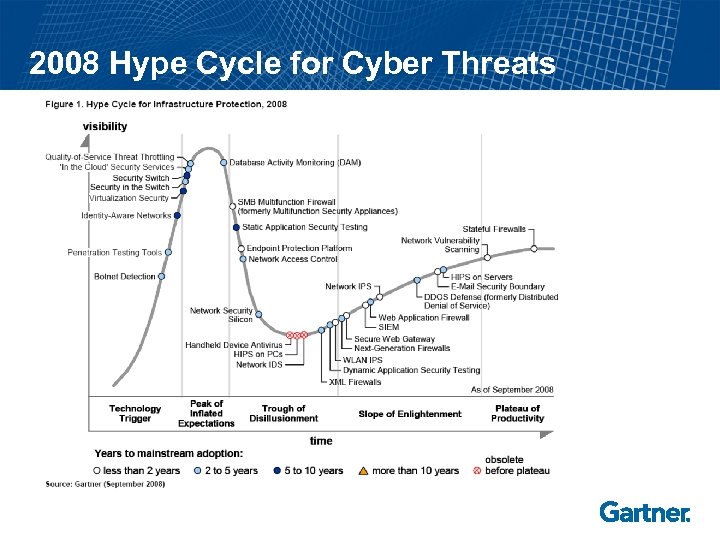
2008 Hype Cycle for Cyber Threats
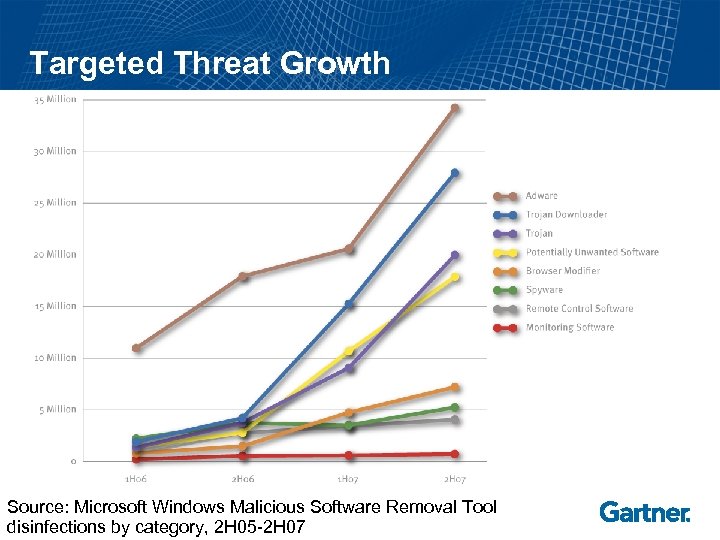
Targeted Threat Growth Source: Microsoft Windows Malicious Software Removal Tool disinfections by category, 2 H 05 -2 H 07
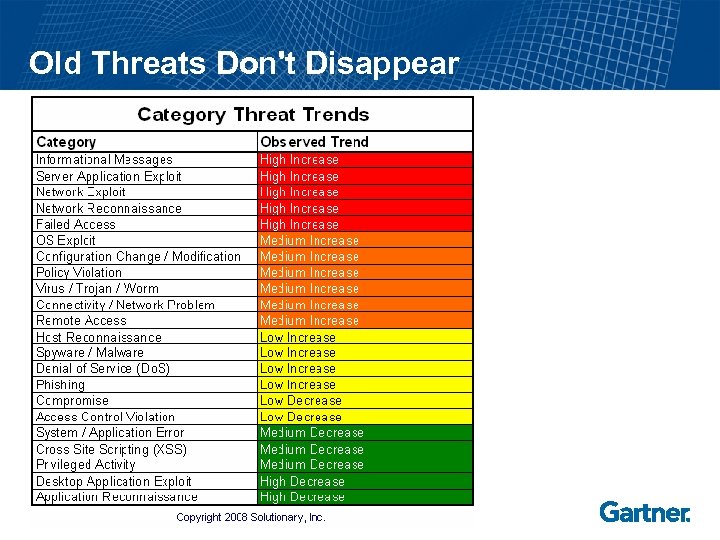
Old Threats Don't Disappear
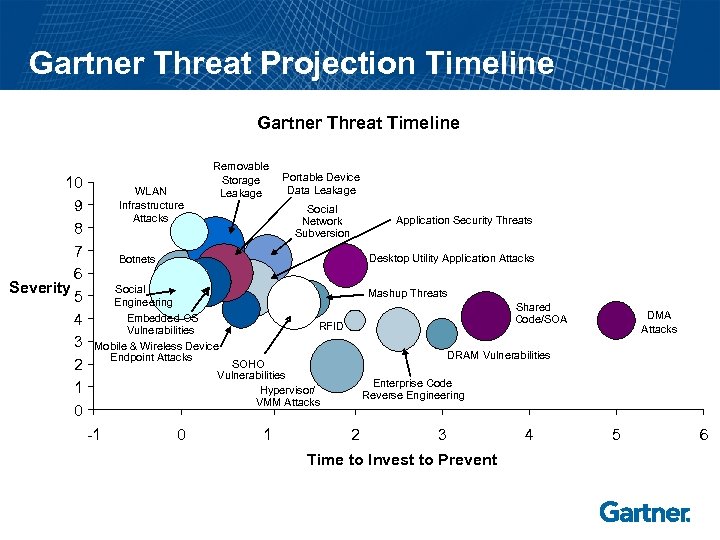
Gartner Threat Projection Timeline Gartner Threat Timeline 10 9 8 7 6 Severity 5 4 3 2 1 0 WLAN Infrastructure Attacks Removable Storage Leakage Portable Device Data Leakage Social Network Subversion Application Security Threats Desktop Utility Application Attacks Botnets Social Engineering Mashup Threats Embedded OS Vulnerabilities Mobile & Wireless Device Endpoint Attacks Shared Code/SOA RFID DRAM Vulnerabilities SOHO Vulnerabilities Hypervisor/ VMM Attacks -1 0 1 DMA Attacks Enterprise Code Reverse Engineering 2 3 Time to Invest to Prevent 4 5 6
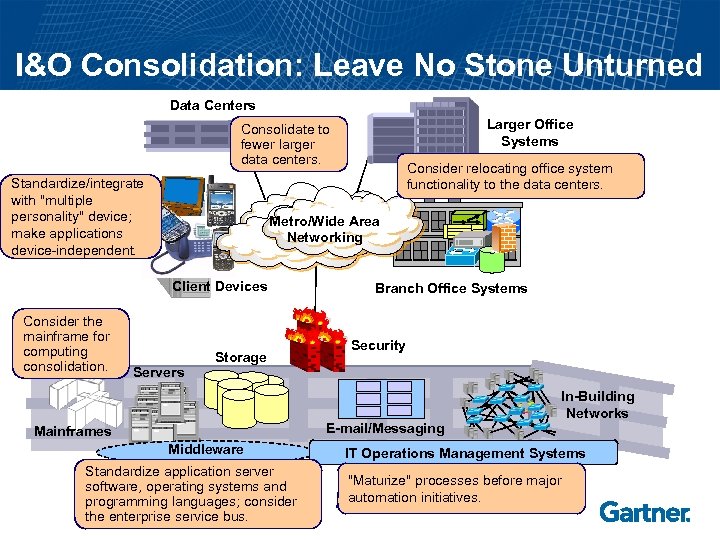
I&O Consolidation: Leave No Stone Unturned Data Centers Larger Office Systems Consolidate to fewer larger data centers. Standardize/integrate with "multiple personality" device; make applications device-independent. Metro/Wide Area Networking Client Devices Consider the mainframe for computing consolidation. Consider relocating office system functionality to the data centers. Servers Storage Branch Office Systems Security Storage E-mail/Messaging Mainframes Middleware Standardize application server software, operating systems and programming languages; consider the enterprise service bus. In-Building Networks IT Operations Management Systems "Maturize" processes before major automation initiatives.
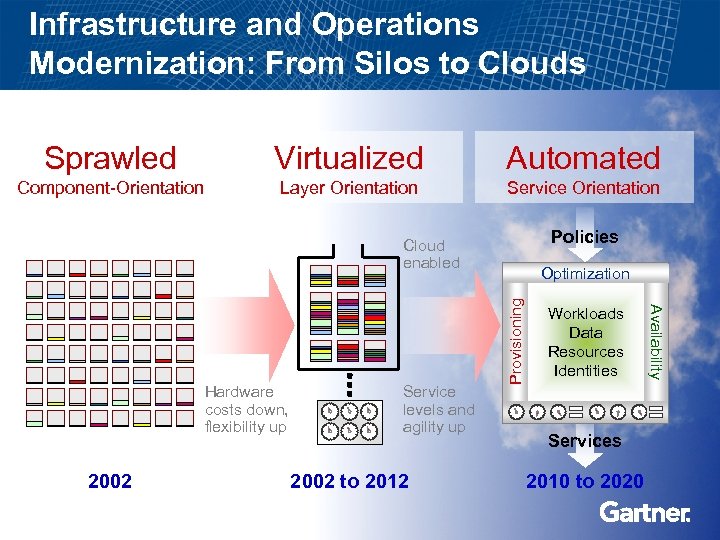
Infrastructure and Operations Modernization: From Silos to Clouds Sprawled Virtualized Automated Component-Orientation Layer Orientation Service Orientation Policies Cloud enabled 2002 to 2012 Provisioning Service levels and agility up Workloads Data Resources Identities Services 2010 to 2020 Availability Hardware costs down, flexibility up Optimization
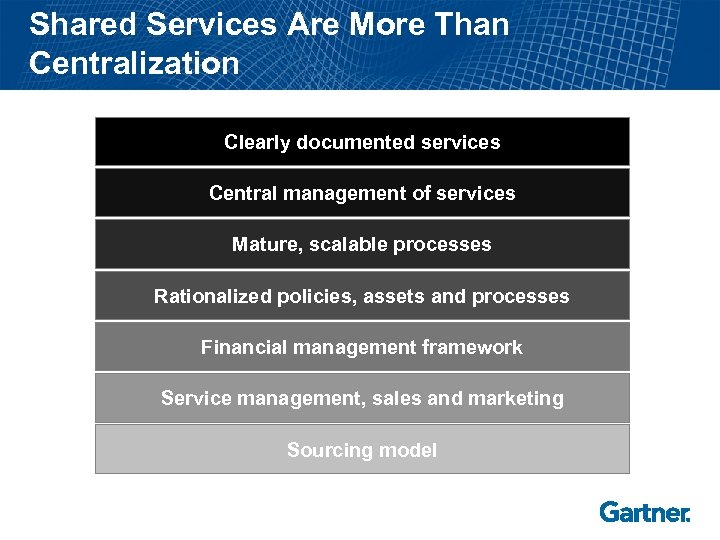
Shared Services Are More Than Centralization Clearly documented services Central management of services Mature, scalable processes Rationalized policies, assets and processes Financial management framework Service management, sales and marketing Sourcing model
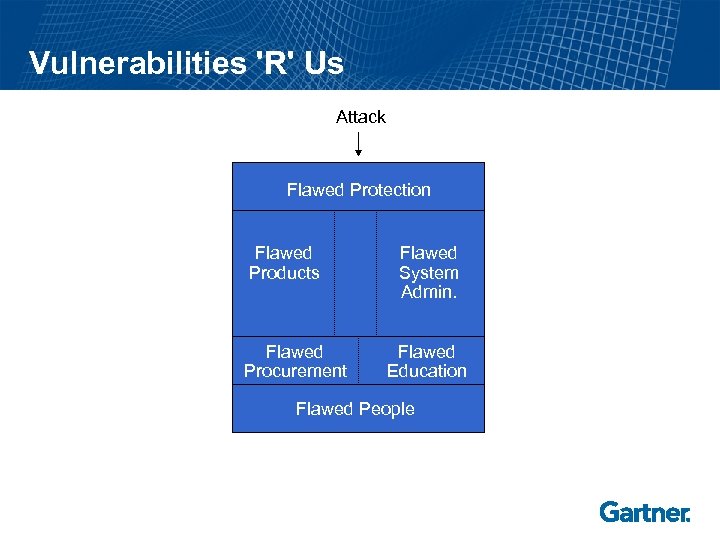
Vulnerabilities 'R' Us Attack Flawed Protection Flawed Products Flawed Procurement Flawed System Admin. Flawed Education Flawed People
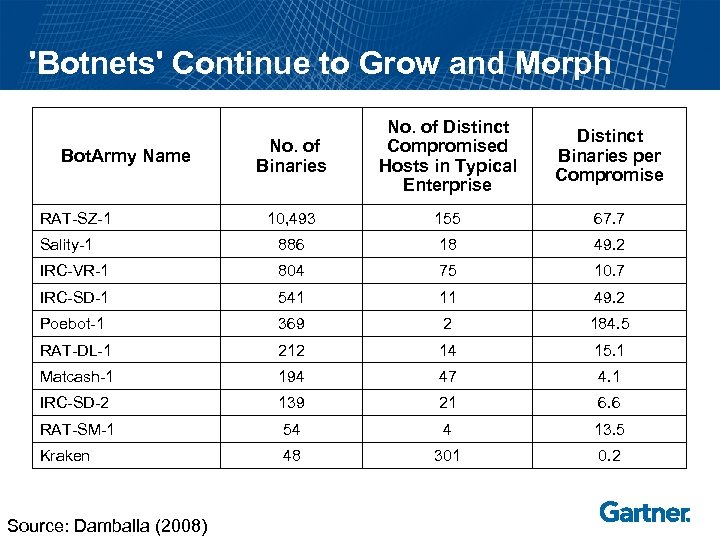
'Botnets' Continue to Grow and Morph No. of Binaries No. of Distinct Compromised Hosts in Typical Enterprise Distinct Binaries per Compromise 10, 493 155 67. 7 Sality-1 886 18 49. 2 IRC-VR-1 804 75 10. 7 IRC-SD-1 541 11 49. 2 Poebot-1 369 2 184. 5 RAT-DL-1 212 14 15. 1 Matcash-1 194 47 4. 1 IRC-SD-2 139 21 6. 6 RAT-SM-1 54 4 13. 5 Kraken 48 301 0. 2 Bot. Army Name RAT-SZ-1 Source: Damballa (2008)
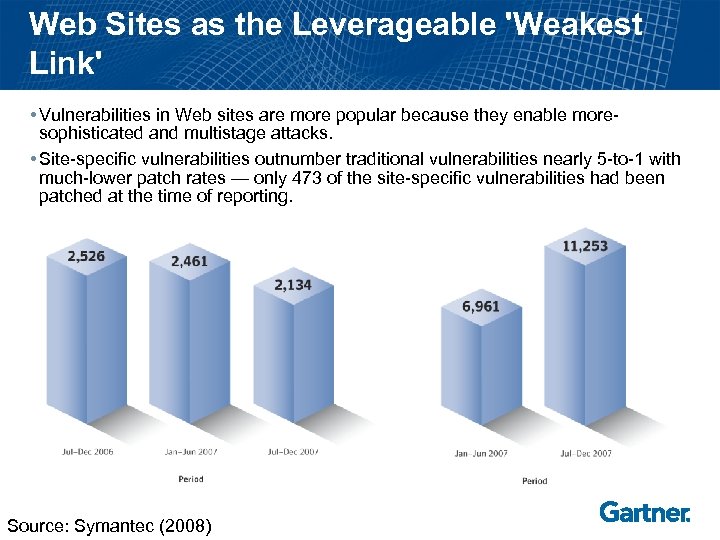
Web Sites as the Leverageable 'Weakest Link' • Vulnerabilities in Web sites are more popular because they enable moresophisticated and multistage attacks. • Site-specific vulnerabilities outnumber traditional vulnerabilities nearly 5 -to-1 with much-lower patch rates — only 473 of the site-specific vulnerabilities had been patched at the time of reporting. Source: Symantec (2008)
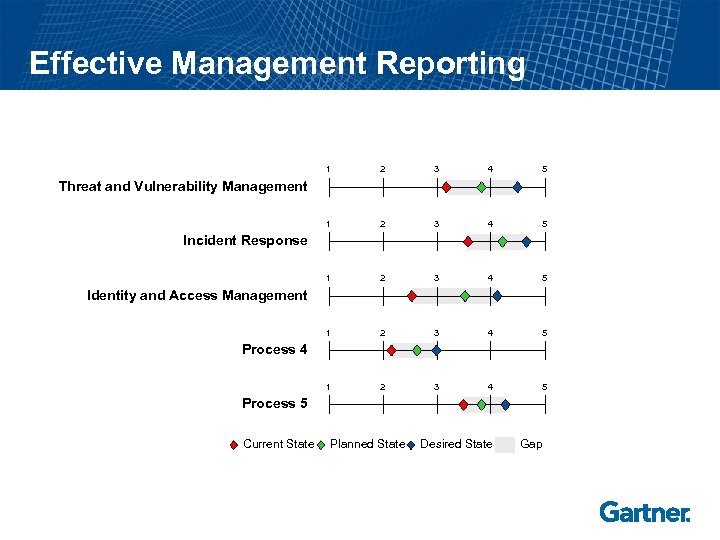
Effective Management Reporting 1 2 3 4 5 1 2 3 4 5 Threat and Vulnerability Management Incident Response Identity and Access Management Process 4 Process 5 Current State Planned State Desired State Gap
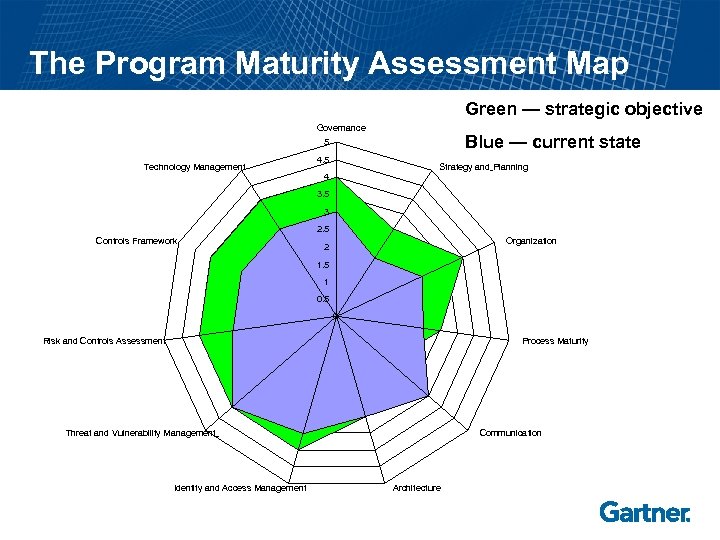
The Program Maturity Assessment Map Green — strategic objective Governance Blue — current state 5 Technology Management 4. 5 Strategy and Planning 4 3. 5 3 2. 5 Controls Framework Organization 2 1. 5 1 0. 5 0 Risk and Controls Assessment Process Maturity Threat and Vulnerability Management Identity and Access Management Communication Architecture
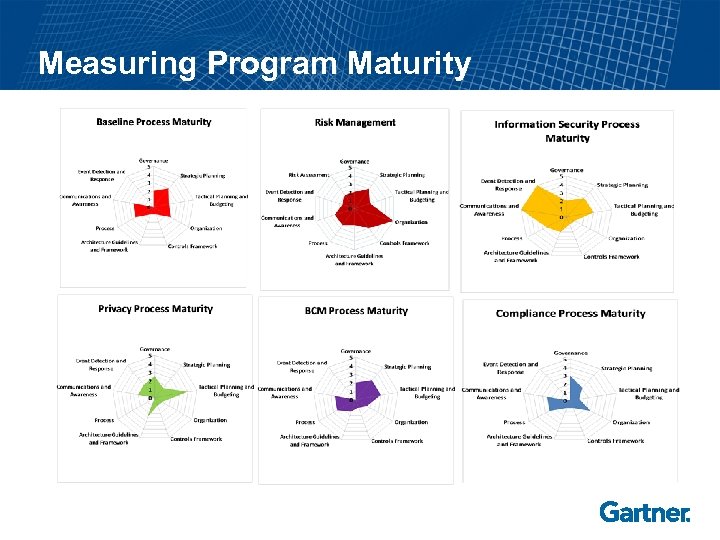
Measuring Program Maturity
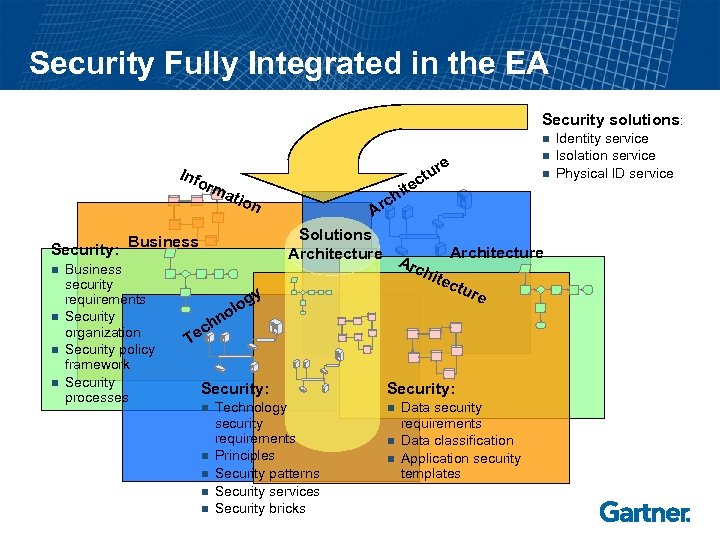
Security Fully Integrated in the EA Security solutions: n Info rm Security: n n atio Business security requirements Security organization Security policy framework Security processes c Te g olo y n n n Solutions Architecture A rch itec tur e hn Security: n ite h c Ar n re tu c Technology security requirements Principles Security patterns Security services Security bricks Security: n n n Data security requirements Data classification Application security templates Identity service Isolation service Physical ID service
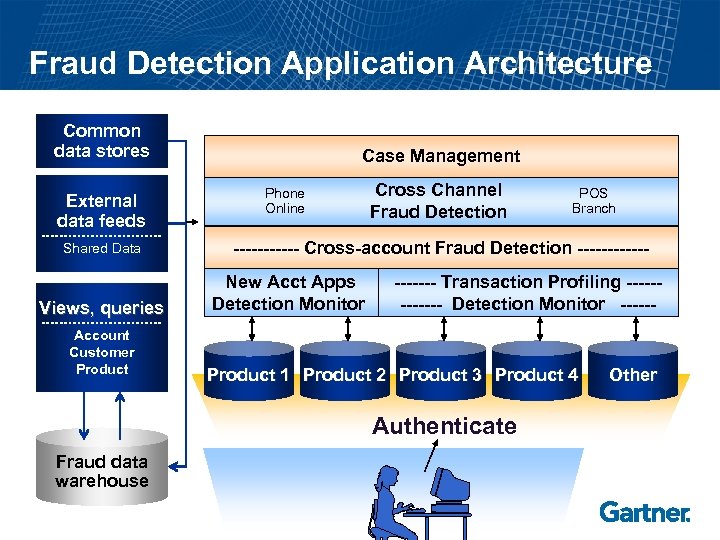
Fraud Detection Application Architecture Common data stores External data feeds Shared Data Views, queries Account Customer Product Case Management Phone Online Cross Channel Fraud Detection ------ Cross-account Fraud Detection ------New Acct Apps Detection Monitor ------- Transaction Profiling ------ Detection Monitor ------ Product 1 Product 2 Product 3 Product 4 Authenticate Fraud data warehouse POS Branch Other
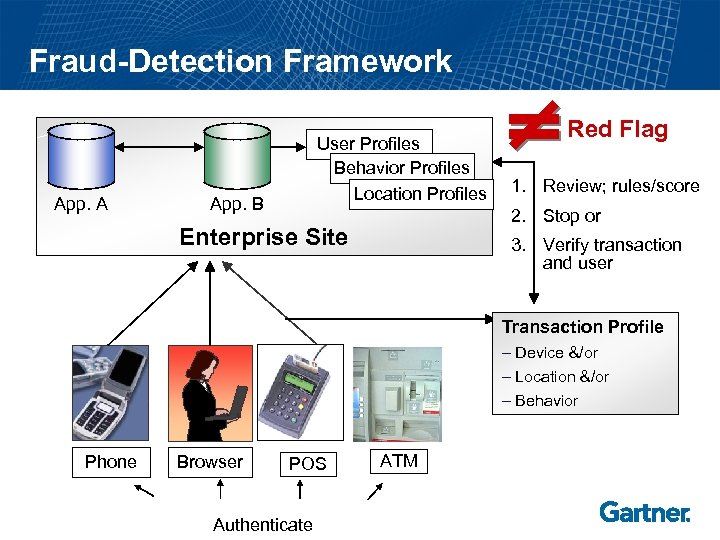
Fraud-Detection Framework App. A User Profiles Behavior Profiles Location Profiles App. B Red Flag 1. Review; rules/score 2. Stop or Enterprise Site 3. Verify transaction and user Transaction Profile – Device &/or – Location &/or – Behavior Phone Browser POS Authenticate ATM
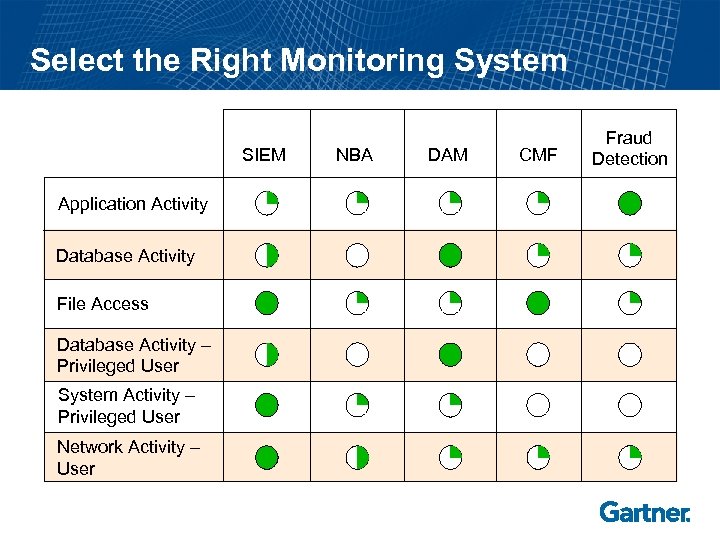
Select the Right Monitoring System SIEM Application Activity Database Activity File Access Database Activity – Privileged User System Activity – Privileged User Network Activity – User NBA DAM CMF Fraud Detection
Recommendation: Develop a Proactive and Layered Monitoring “System” • Use Database Activity Monitoring (DAM) to monitor database administration activity and database user access, especially when native database auditing is not enabled. • Use Content Monitoring and Filtering (CMF) to detect and prevent the inappropriate movement of sensitive data across the network — when well-defined data formats are present. • Use fraud detection to monitor or stop suspect user activity at the access or transaction layer, within supported applications. • Use Network Behavior Analysis (NBA) to monitor network traffic flows between applications and to discover anomalous traffic and associate it with a specific user. • Use Security Information and Event Monitoring (SIEM) to monitor, correlate and analyze user activity across a wide range of systems and applications.

Cyber Threat Preparedness Amos Auringer Gartner Executive Programs Notes accompany this presentation. Please select Notes Page view. These materials can be reproduced only with written approval from Gartner. Such approvals must be requested via e-mail: vendor. relations@gartner. com. Gartner is a registered trademark of Gartner, Inc. or its affiliates.
a2146505c1d89b59b23c2908936b9aa8.ppt