2f7d1b1395e96832c89f91c376539ff7.ppt
- Количество слайдов: 41
Cyber Security Concept, Cyber Wars and a New Milieu Kubilay Onur Güngör www. shibumidojo. org www. kirmizivesiyah. org OWASP ko. gungor@gmail. com Copyright 2007 © The OWASP Foundation Permission is granted to copy, distribute and/or modify this document under the terms of the OWASP License. The OWASP Foundation http: //www. owasp. org

About Member of Netsparker Project Multidisciplinary Cyber Security Engineer International Relations Analyst Penetration Tester, White. Hat, Security Tester, whatever you call it. Researcher at Cyber Security Project, Isik University IIBF Founder of Isik University Information Security and Research Group OWASP 2
Index OWASP ? Internet as a new social and cultural domain Cyber-World as a new milieu Why do we need a security perspective? First aggressions on Internet Hackers, Crackers White. Hats, Black. Hats, Grey. Hats Hacking, Phracking and Cracking Cases Organized Cyber-Crimes and Cyber-Wars!!! Size and Shape of the Threats Threat Hierarchy Timeline OWASP Cyber Wars, Cyber Terrorism 3

OWASP ? • • • Open Web Application Security Project All OWASP stuff, free and opensource Some extra numbers; – – – 120+ Chapters 30+ Sponsor 50+ Project 100+ mail lists Over 1. 000 visitor per month OWASP 4
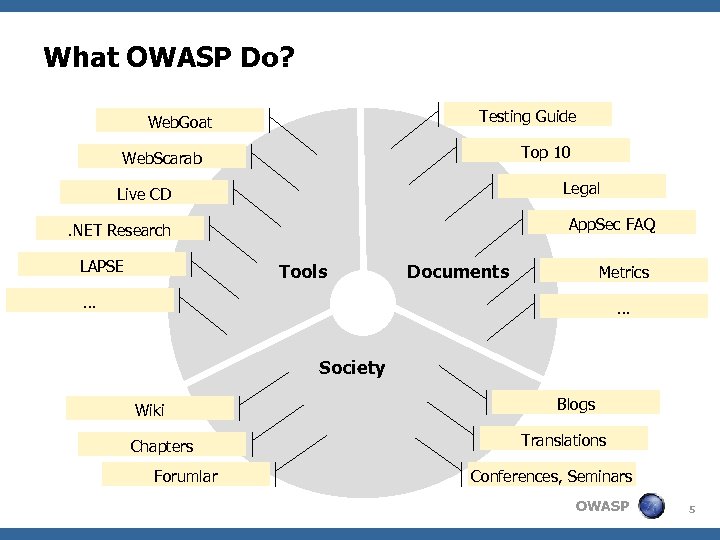
What OWASP Do? Testing Guide Web. Goat Top 10 Web. Scarab Legal Live CD App. Sec FAQ . NET Research LAPSE Tools Documents Metrics … … Society Wiki Chapters Forumlar Blogs Translations Conferences, Seminars OWASP 5

OWASP Corporate Members – Jul 2008 OWASP 6

OWASP TR- webguvenligi. org Projects • Owasp-We. Bekci (So. C 2008) ve MSALParser • CAMMP (Chroot Apache Mysql Mod. Security PHP) • Secure. Image (. NET, Java ve PHP API) • Secure. Tomcat (Tomcat J 2 EE sunucu güvenlik denetimi) • Çeviri Projesi (~400 sayfa doküman) • Otomatize Sql Enjektörleri Analizi (So. C 2008) • Jarvinen (Web tabanlı Mod. Security log analizi) • Web Güvenliği Terimler Sözlüğü • WIVET (Crawler Boy Ölçer) • E-Dergi - http: //dergi. webguvenligi. org OWASP 7

webguvenligi. org E-mail List owasp-turkey@lists. owasp. org bilgi@webguvenligi. org OWASP

Internet as a new social and cultural domain • • Where is Internet? Improvement of Internet and socializing of human-beings Social Groups on Internet Jargons, Languages, Reflexes, etc. OWASP 9
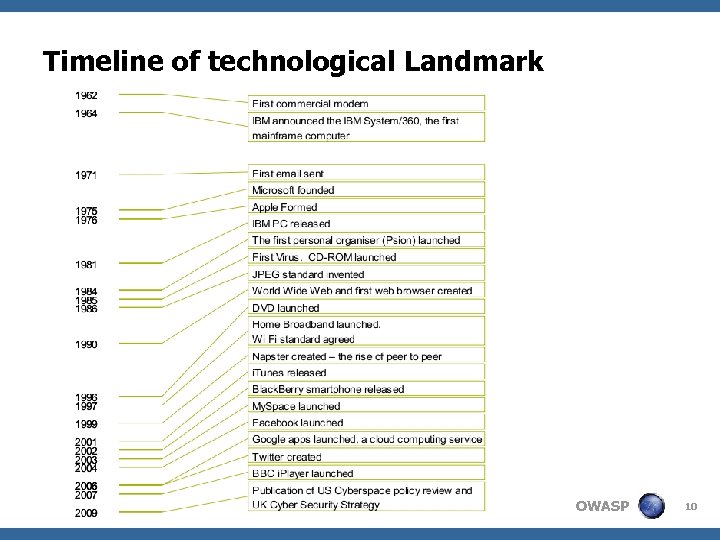
Timeline of technological Landmark OWASP 10
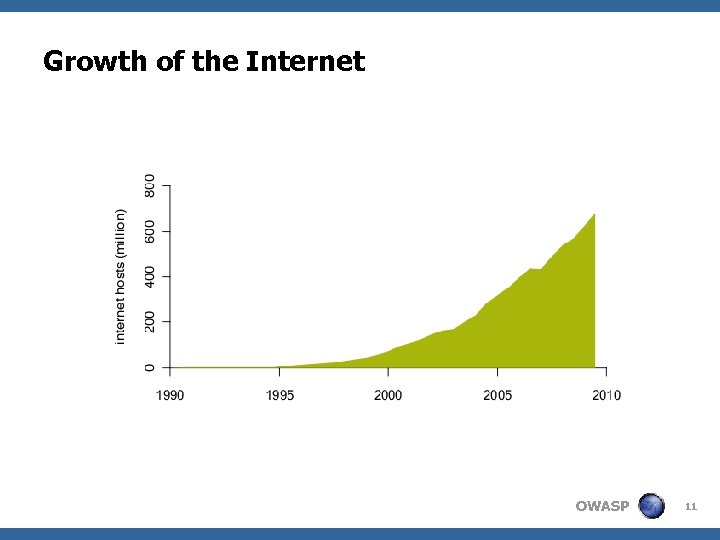
Growth of the Internet OWASP 11

Cyber-World as a new milieu • • Groups consist of many social groups : ) Audience Management Perception Management Rules Massif Aggressions Audience Behaviors Politics, Visions Differences, etc. OWASP 12

Why do we need a security perspective? • • • Security necessity in real world Cyber World ~ Real World The importance of Protection in Cyber World Personal Privacy Company Confidentiality Governmental Information Military Confidential Information International Conflicts Psychological Operations OWASP 13

First Aggressions on Internet • • • Nature of Human Beings Psychological aspects of crime and conflict First Aggressions : ) First Hacking with Fake Phone Signal by using fife. Nickname: Draper OWASP 14

Theories of Examining the Criminal Behaviors • • Every behavior against social life Individualist theories – – – • Classical Ecole Positivist Ecole Biological Ecole Psychological Ecole Geographical Ecole Sociological theories – – – Social structure theories (heterogeneous) Social process theories (social learning) Social conflict theories (construction of others) OWASP 15

First Aggressions on Internet Kevin Mitnick • • Fujitsu, Sun, Motorola Most Wanted Hacker Freedom Downtime Sentenced for 5 years OWASP 16

First Aggressions on Internet Viladimir Levin 10 Million $ from Citibank Robert Morris (RTM) One of the first Worm 1998 OWASP 17
First Aggressions on Internet • • • Different Relationships Different Perceptions Different Aims Different Hacker Groups Different Definitions OWASP 18

White Hat Hackers • • • Good Guys : ) Security Experts Refers Penetration Tester Ethical Hacker Specialized in Penetration Testing Report Security Vulnerabilities Risk Management Disaster Recovery Security Consultancy OWASP 19

Black Hat Hackers • • Bad Guys Specialized in Unauthorized Penetrations Attack to systems for fun, for profit, for political motivations or etc. They can damage the systems May also be called crackers Cracks serials, licenses, etc. What if there is a habitable system for everyone? Think OWASP 20

Grey Hat Hackers • • Hybrid between whitehat and blackhat hackers Usually do not hack for personal gains or malicious intentions a grey hat hacker may penetrate a computer system without authorization, an illegal act in most countries Grey hats may or may not release vulnerabilities to the vendor or the public. They OWASP 21

Hackers, Crackers, Phrakers, Hacktivists, Script Kiddies. . . • • • In common usage, a hacker is a person who breaks into computers, usually by gaining access to administrative controls A cracker who has malicious intentions, cracks software licenses, damages the systems, etc. Phreakers are phone fakers OWASP 22

Organized Cyber-Crimes and Cyber-Wars!!! OWASP 23

Organized Cyber-Crimes and Cyber-Wars!!! • • • More sophisticated attacks Attacks are getting more organized Conversion of reactions from attacks to sophisticate crimes in cyber world Organized Cyber Crimes Government supports for the Hacker Groups Finally Cyber Warfares and Cyber Operations OWASP 24

Overview of Attackers • • • Lone criminals, fraudsters Criminal Organizations State sponsored attackers Disgruntled Employees Industrials Spies Terrorists Hackers Hacktivists Cyber Vandals OWASP 25

Overview of Motivates and Methodes Motivates • Financial Gain • Revenge by a disgruntled employee • Industrial espionage • State sponsored espionage • Furthering religious or idealistic believes • Amusement or prestige • Political Reasons • National Security • Contra-Espionage Methods • Virus, Trojans, worms, spyware, etc • Internal Copying and destroying data • Manipulating or Blackmailing • Hacking • Key logging • Electromagnetic Interference • Denial of Service Attacks • Social Engineering • Abusing vulnerable codes • Design vulnerabilities • Etc. OWASP 26
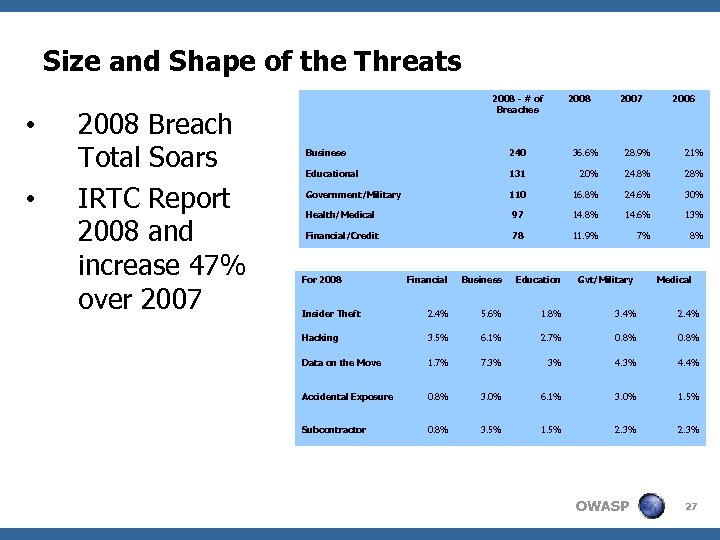
Size and Shape of the Threats • • 2008 Breach Total Soars IRTC Report 2008 and increase 47% over 2007 2008 - # of Breaches 2008 2007 2006 Business 240 36. 6% 28. 9% 21% Educational 131 20% 24. 8% 28% Government/Military 110 16. 8% 24. 6% 30% Health/Medical 97 14. 8% 14. 6% 13% Financial/Credit 78 11. 9% 7% 8% For 2008 Financial Business Education Gvt/Military Insider Theft 2. 4% 5. 6% 1. 8% 3. 4% 2. 4% Hacking 3. 5% 6. 1% 2. 7% 0. 8% Data on the Move 1. 7% 7. 3% 3% 4. 4% Accidental Exposure 0. 8% 3. 0% 6. 1% 3. 0% 1. 5% Subcontractor 0. 8% 3. 5% 1. 5% 2. 3% OWASP Medical 27
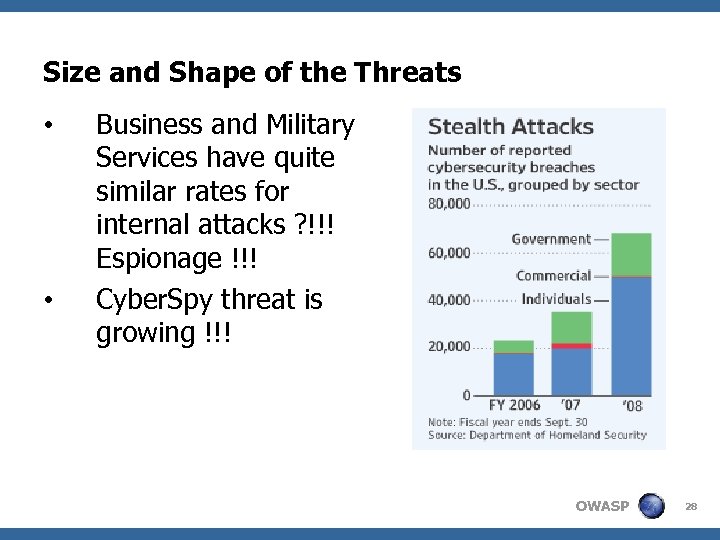
Size and Shape of the Threats • • Business and Military Services have quite similar rates for internal attacks ? !!! Espionage !!! Cyber. Spy threat is growing !!! OWASP 28
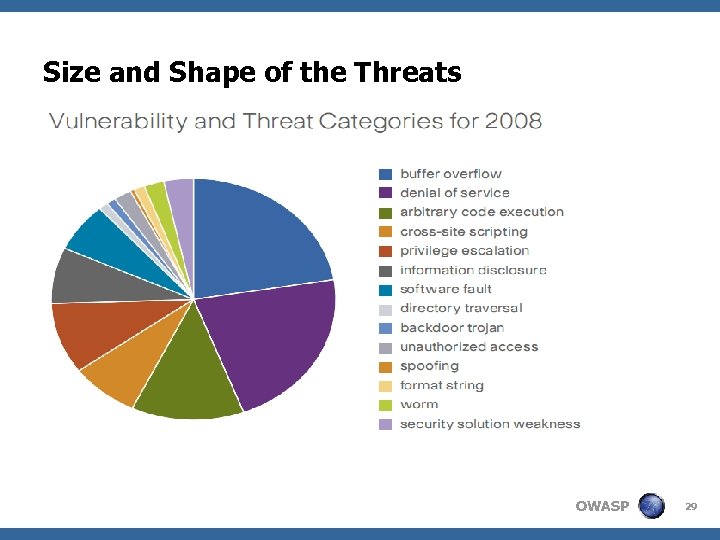
Size and Shape of the Threats OWASP 29
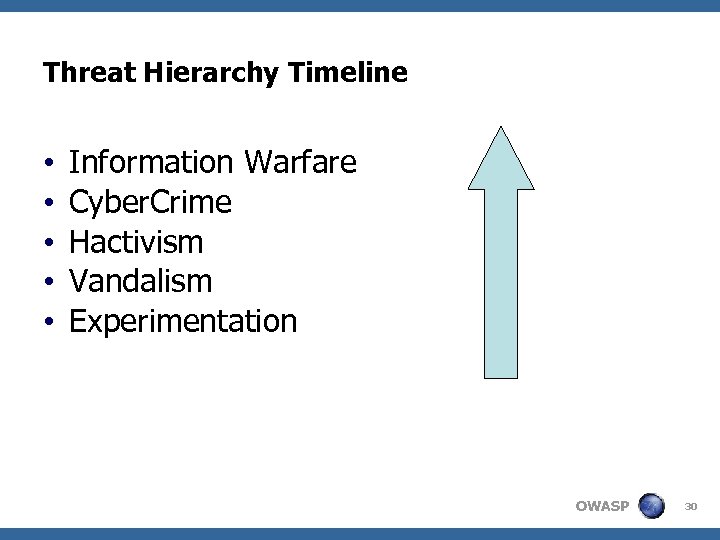
Threat Hierarchy Timeline • • • Information Warfare Cyber. Crime Hactivism Vandalism Experimentation OWASP 30
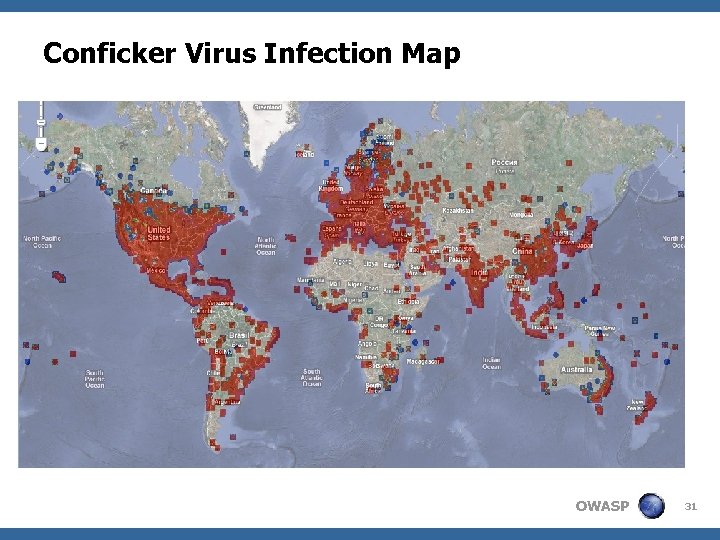
Conficker Virus Infection Map OWASP 31
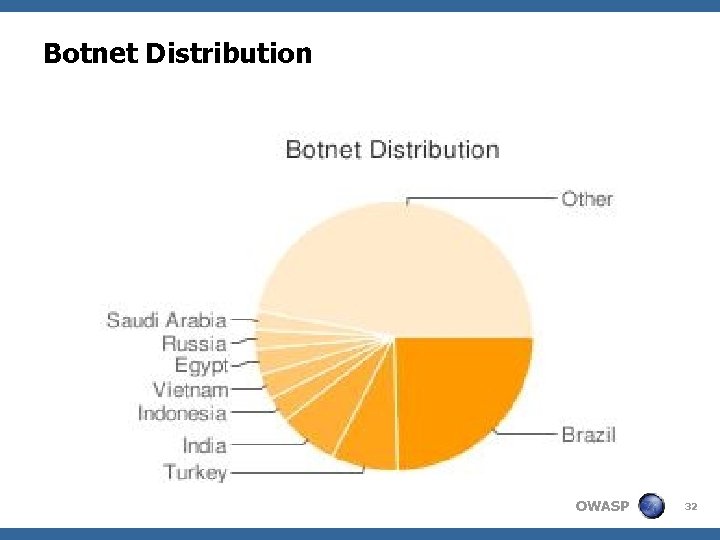
Botnet Distribution OWASP 32

Cyber Wars The Goal: Information Dominance The degree of information superiority that allows the possessor to use information systems and capabilities to achieve an operational advantage in a conflict or to control the situation in operations short of war, while denying those capabilities to the adversary. Field Manual 100 -6, Information Operations, August 1996 OWASP 33

Cyber Wars Break Out Examples Russian Suppress Estonia, March 2007 Ukrain November 2007 Lithuania, June 2008 Georgia, August 2008 OWASP 34

Cyber Wars and Cyber Terrorism • A new Era is arising and has been challenged with new tactics that have never been used or seen before. • terrorism can affect not only physically and mentally, but financially and emotionally as well. OWASP 35

Terrorism What, Why, Where and How ? • • There appears to be no one universally agreed upon definition of terrorism According to UN: any act intended to cause death or serious bodily injury to a civilian, or to any other person not taking an active paar in the hostilities in a situation of armed conflict Our Definition of terrorism will depend on how we construe the groups involved and what behaviors we consider to constitute a terrorist act. Thus, one's terrorist, fanatic or militant radical OWASP is another's martyr, revolutionary or freedom 36

Terrorism • • Frustration – Aggression Theory Relative Deprivation Theory Social Learning Theory etc. OWASP 37

Why Cyber Terrorism? • • Governments to E-Governments Water Systems Air Traffic Systems Infrastructures Medical, Health-care, pharmacy etc. National Security Cyber Space and Unconventional Tactics Die Hard 4 OWASP 38
Terrorist Units and Cells: A Functional Approach OWASP

How can we prepare ourselves to the future? • • • Analyzing the Cyber Protection Fundemantals Policy Development Mission Statement (visions, missions, goals, etc) Writing Standards and Procedures Information Classification Improving Security Awareness Well educated Security Professionals, Hackers Urgent Response Policy, Procedures and Professionals OWASP And of day, Cyber Force in a Military Concept 40
Thank you very much Further Question; ko. gungor@gmail. com Friend. Feed: Corpus. Callosum IRC: Freenode. com, chan: #archlinux. tr, #infosecrg, #crypto, #remote-exploit, #neuroscience Nick: Corpus. Callosum Please do not hesitate to share information and ask question. OWASP 41
2f7d1b1395e96832c89f91c376539ff7.ppt