b772b3b72e1e8f943d0b97a9af8b7cc0.ppt
- Количество слайдов: 28

Cyber Security Assessment & Management CSAM Highlight of Capabilities Comprehensive FISMA Compliance, Management & Reporting Five Services, One Complete FISMA Solution 1 Risk-Based Policy & Implementation Guidance 2 Program Management Plan 3 Subordinate System SSP 4 Management Reporting 5 Training & Quarterly Workshops n Demonstration Days n n Friday (3/16): 9 am - noon Monday (3/19): 9 am - noon

Cyber Security Assessment & Management CSAM 1 Risk-Based Policy & Implementation Guidance n Threats and Vulnerabilities n Roles – Responsibilities - Privileges n Standards 2 Program Management Plan 3 Subordinate System SSP 4 Management Reporting 5 Training & Quarterly Workshops
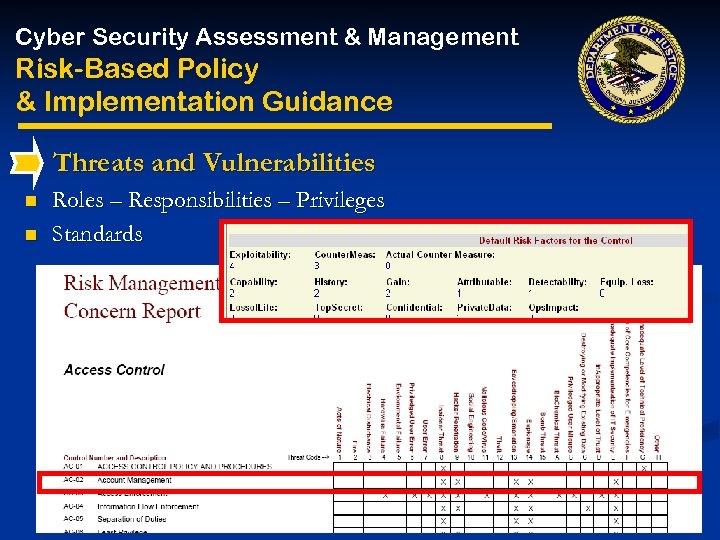
Cyber Security Assessment & Management Risk-Based Policy & Implementation Guidance Threats and Vulnerabilities n n Roles – Responsibilities – Privileges Standards

Cyber Security Assessment & Management Risk-Based Policy & Implementation Guidance n Threats and Vulnerabilities Roles – Responsibilities – Privileges n Standards

Cyber Security Assessment & Management Risk-Based Policy & Implementation Guidance n n Threats and Vulnerabilities Roles – Responsibilities – Privileges Standards Security Control Set Test Cases Expected Results Compliance Guidance &Descriptions Subject Matter Expertise
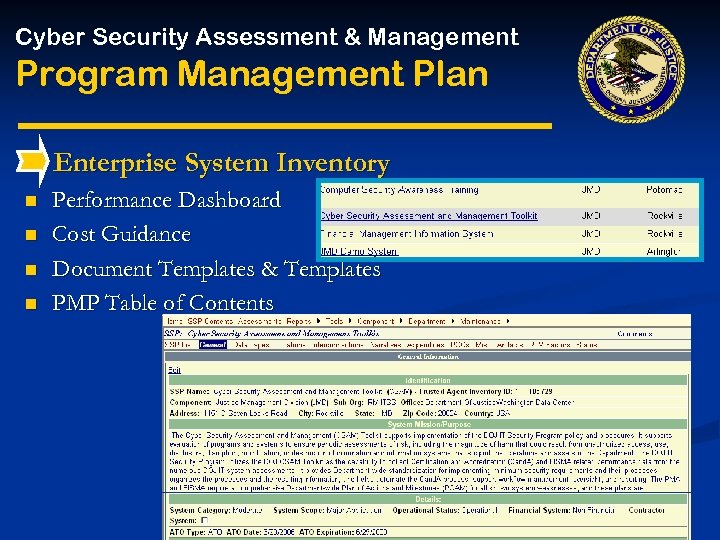
Cyber Security Assessment & Management Program Management Plan Enterprise System Inventory n n Performance Dashboard Cost Guidance Document Templates & Templates PMP Table of Contents
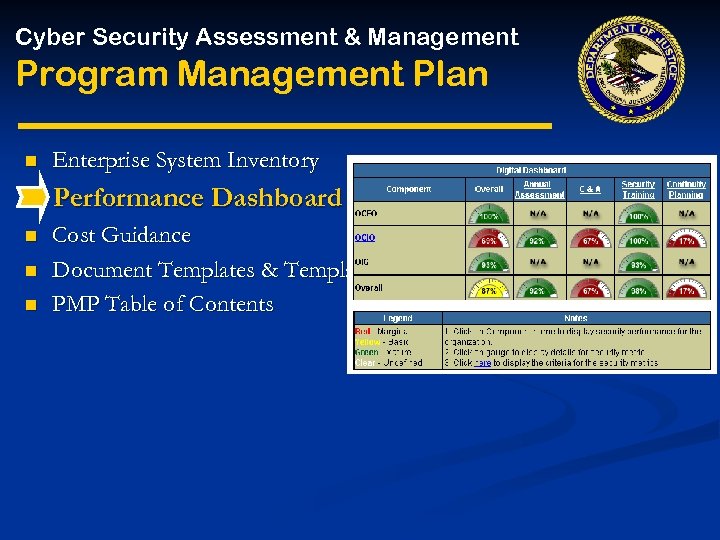
Cyber Security Assessment & Management Program Management Plan n Enterprise System Inventory Performance Dashboard n n n Cost Guidance Document Templates & Templates PMP Table of Contents
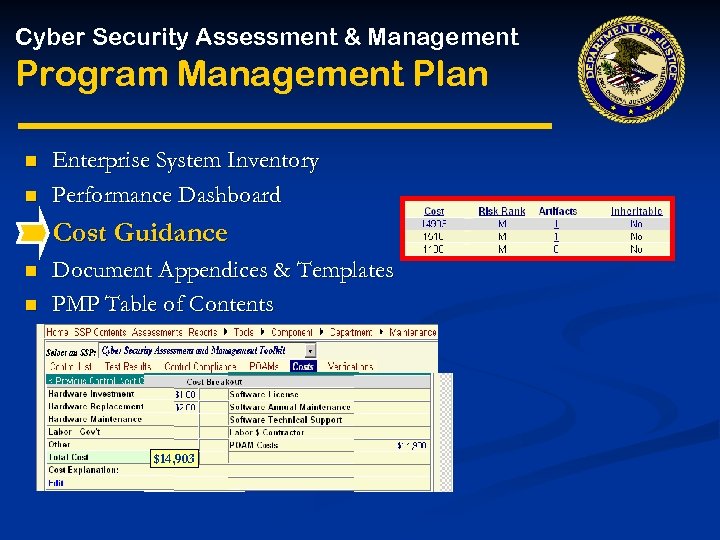
Cyber Security Assessment & Management Program Management Plan n n Enterprise System Inventory Performance Dashboard Cost Guidance n n Document Appendices & Templates PMP Table of Contents $14, 903
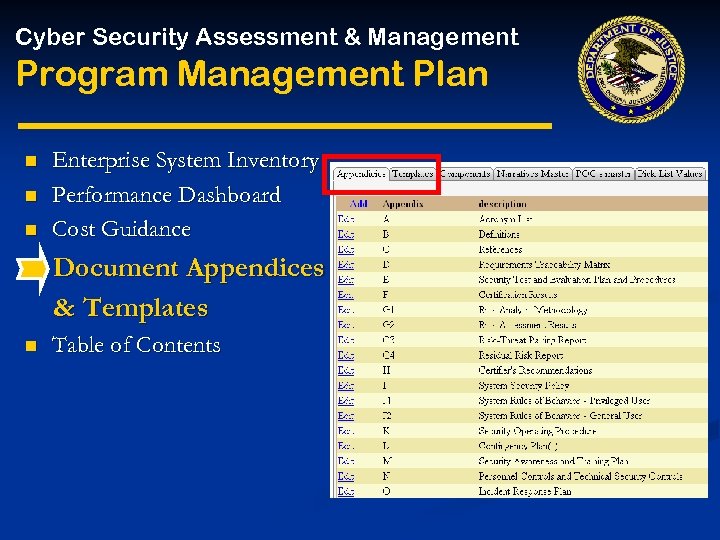
Cyber Security Assessment & Management Program Management Plan n Enterprise System Inventory Performance Dashboard Cost Guidance Document Appendices & Templates n Table of Contents

Cyber Security Assessment & Management Program Management Plan n n Enterprise System Inventory Enterprise Performance Dashboard Program Management Plan Cost Guidance Table of Contents Document Appendices • Missions, Strategic Goals, Objectives, Systems • IT Security Management Strategy & Templates Table of Contents • Core Program Management Approach • Organization of the IT Security Program • IT Security Program External Guidance • IT Security Program External Interfaces • Roles & Responsibilities • FISMA Reporting • Program Implementation • IT Security Goals and Action Plans

Cyber Security Assessment & Management Subordinate System SSP System Security Plan (SSP) n Scope n Category Inheritance (common controls) Artifacts POA&Ms n n n SSP • Risk Assessment • Threats-Impact 1. System Identification • Risk Control Requirements 2. System Operational Status • (Linked to policy (SRTM) 3. General Description/ Purpose 4. System Environment 5. System Interconnections/Information Sharing 6. Sensitivity of Information Handled 7. Planning for Security in the Life Cycle 8. Security Control Measures SSP Appendices Appendix D: Requirements (RTM) Appendix E: ST&E Plan And Procedures Appendix F: Certification Results Appendix G: Risk Assessment (RA) Results Appendix H: Certifier’s Recommendation Appendix I: System Security Policy Appendix J: System Rules of Behavior (ROB) Appendix K: Security Operating Procedures Appendix L: Contingency Plan(s) Appendix M: Security Awareness Training Plan Appendix O: Incident Response Plan Appendix P: MOA/Service Level Agreements (SLA) Appendix Q: Configuration Management Plan Appendix R: Accreditation Statement & Documentation Appendix S & T: Hardware & Software Listings Appendix U: C&A Schedule
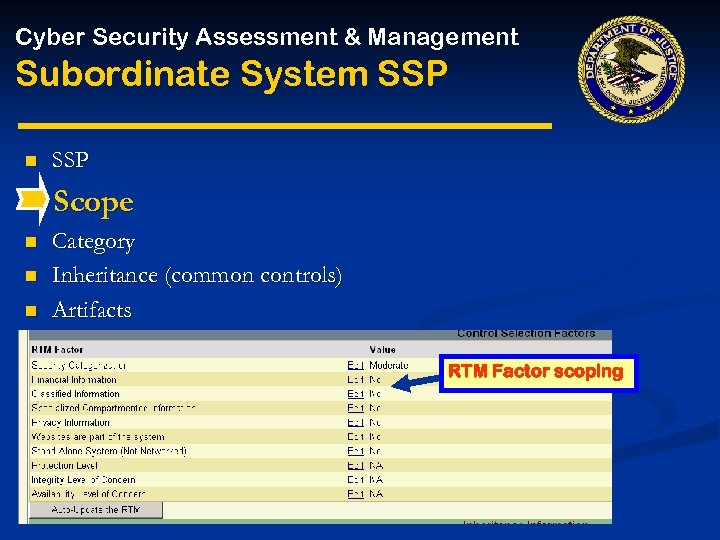
Cyber Security Assessment & Management Subordinate System SSP n SSP Scope n n Category Inheritance (common controls) Artifacts POA&Ms RTM Factor scoping
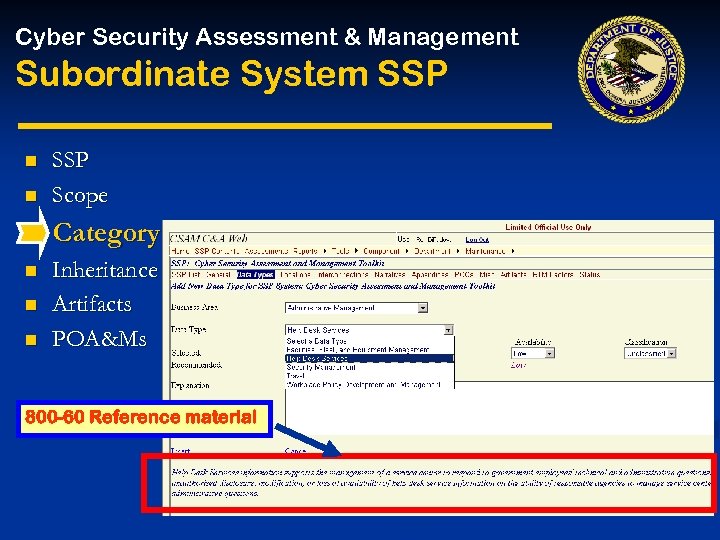
Cyber Security Assessment & Management Subordinate System SSP n n SSP Scope Category n n n Inheritance (common controls) Artifacts POA&Ms 800 -60 Reference material
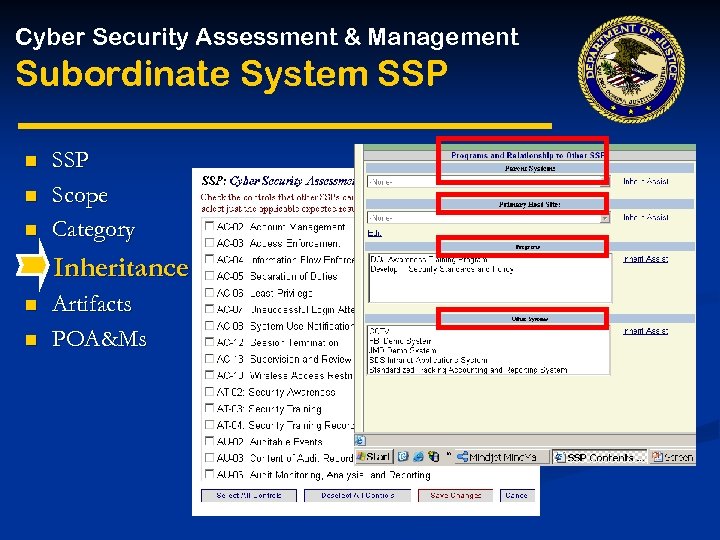
Cyber Security Assessment & Management Subordinate System SSP n n n SSP Scope Category Inheritance (common controls) n n Artifacts POA&Ms

Cyber Security Assessment & Management Subordinate System SSP n n SSP Scope Category Inheritance (common controls) Artifacts n POA&Ms
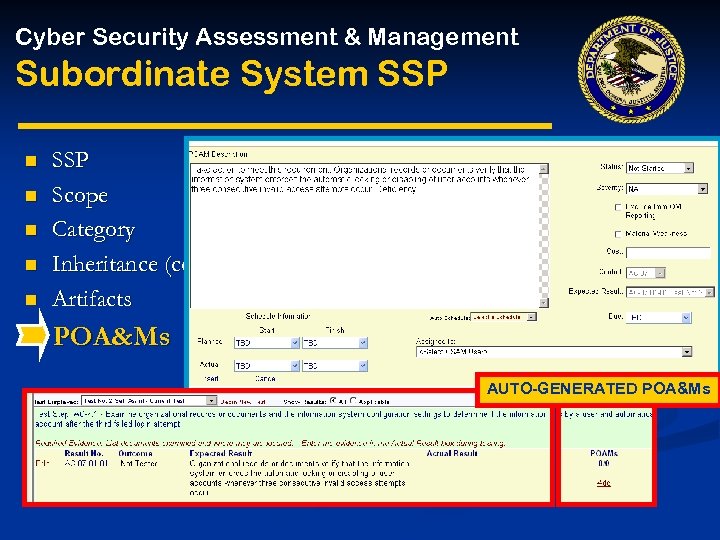
Cyber Security Assessment & Management Subordinate System SSP n n n SSP Scope Category Inheritance (common controls) Artifacts POA&Ms AUTO-GENERATED POA&Ms
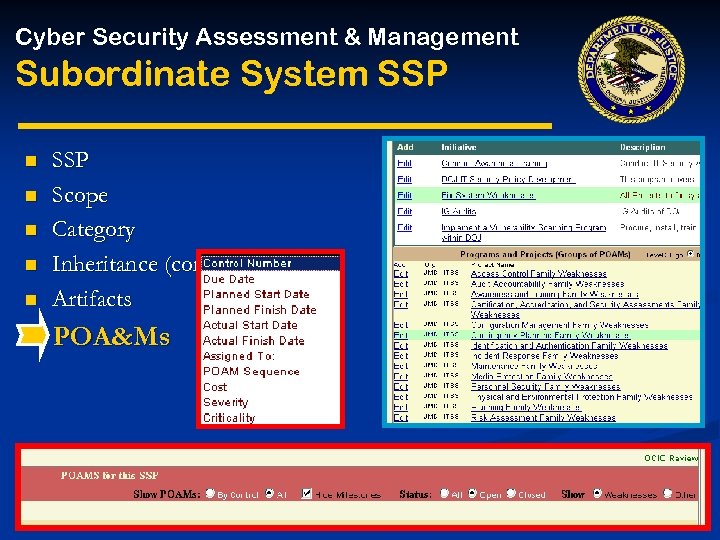
Cyber Security Assessment & Management Subordinate System SSP n n n SSP Scope Category Inheritance (common controls) Artifacts POA&Ms

Cyber Security Assessment & Management Subordinate System SSP n n n SSP Scope Category Inheritance (common controls) Artifacts POA&Ms

Cyber Security Assessment & Management Reporting Enterprise n n n System Regulatory Ad hoc O r O g A r O g B r O g C r O D g r O g r E O g F r O g G r O g H r AGENCY DASHBOARD g (PERFORMANCE METRIX & I J COMPLIANCE STATUS) FISMA REPORTS
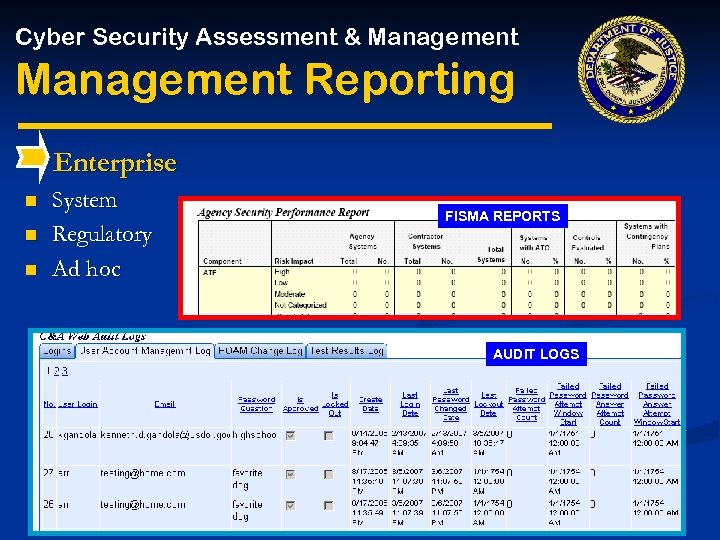
Cyber Security Assessment & Management Reporting Enterprise n n n System Regulatory Ad hoc FISMA REPORTS AUDIT LOGS
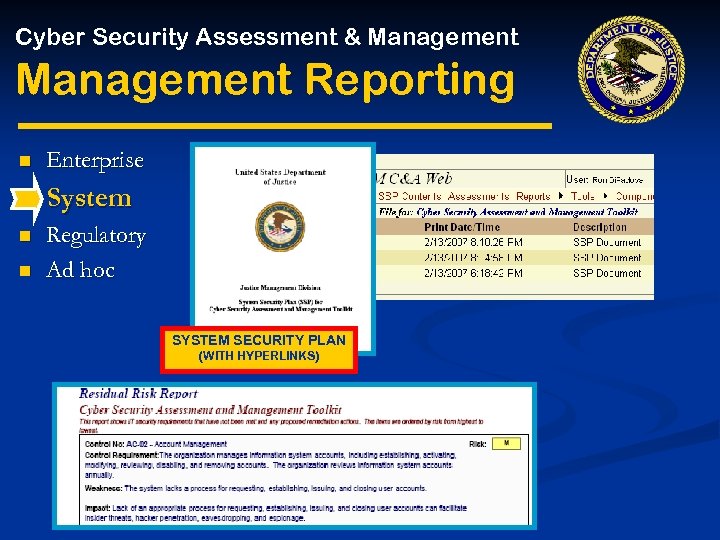
Cyber Security Assessment & Management Reporting n Enterprise System n n Regulatory Ad hoc SYSTEM SECURITY PLAN (WITH HYPERLINKS)
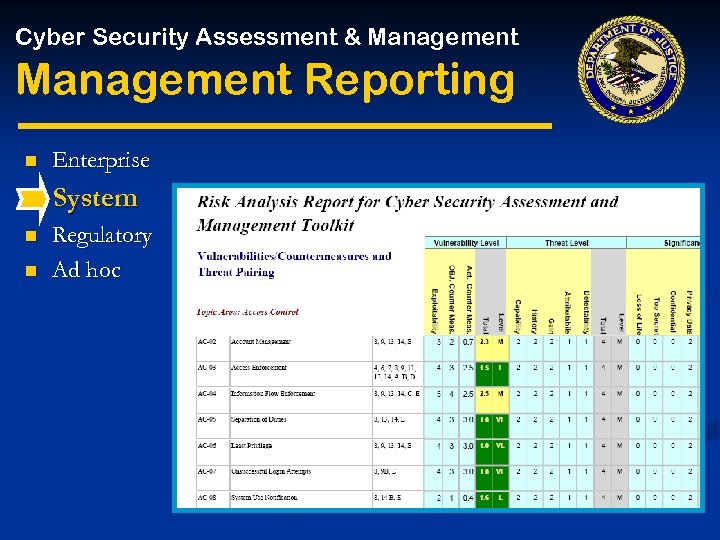
Cyber Security Assessment & Management Reporting n Enterprise System n n Regulatory Ad hoc

Cyber Security Assessment & Management Reporting n n n Enterprise System Regulatory Ad hoc PTA PIA
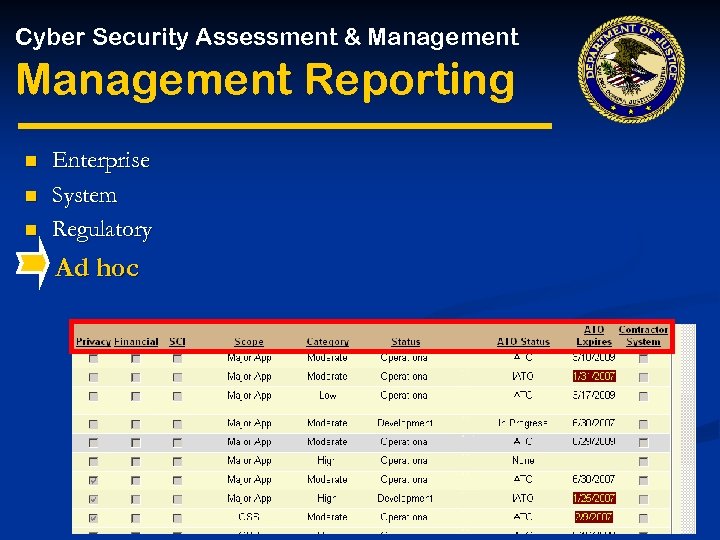
Cyber Security Assessment & Management Reporting n n n Enterprise System Regulatory Ad hoc
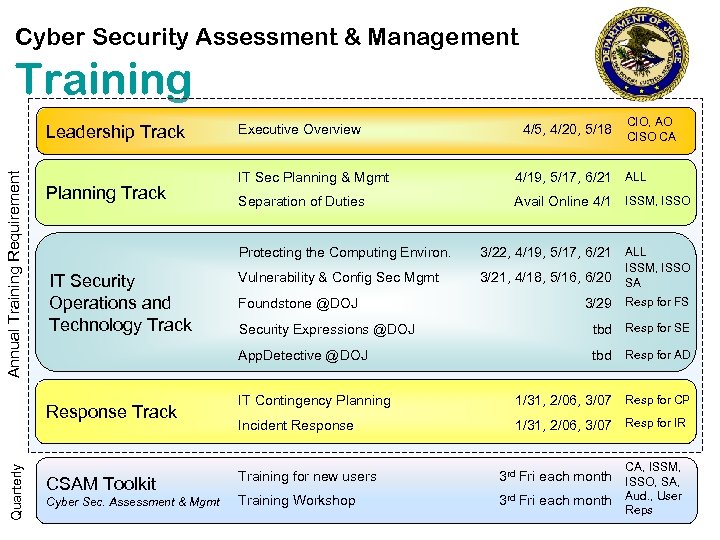
Cyber Security Assessment & Management Training Annual Training Requirement Leadership Track Planning Track 4/5, 4/20, 5/18 CIO, AO CISO CA IT Sec Planning & Mgmt 4/19, 5/17, 6/21 ALL Separation of Duties Avail Online 4/1 ISSM, ISSO Protecting the Computing Environ. IT Security Operations and Technology Track 3/22, 4/19, 5/17, 6/21 ALL Vulnerability & Config Sec Mgmt 3/21, 4/18, 5/16, 6/20 SA Foundstone @DOJ ISSM, ISSO 3/29 Resp for FS CSAM Toolkit Cyber Sec. Assessment & Mgmt Security Expressions @DOJ tbd Resp for SE App. Detective @DOJ Response Track Quarterly Executive Overview tbd Resp for AD IT Contingency Planning 1/31, 2/06, 3/07 Resp for CP Incident Response 1/31, 2/06, 3/07 Resp for IR Training for new users Training Workshop CA, ISSM, 3 rd Fri each month ISSO, SA, 3 rd Fri each month Aud. , User Reps
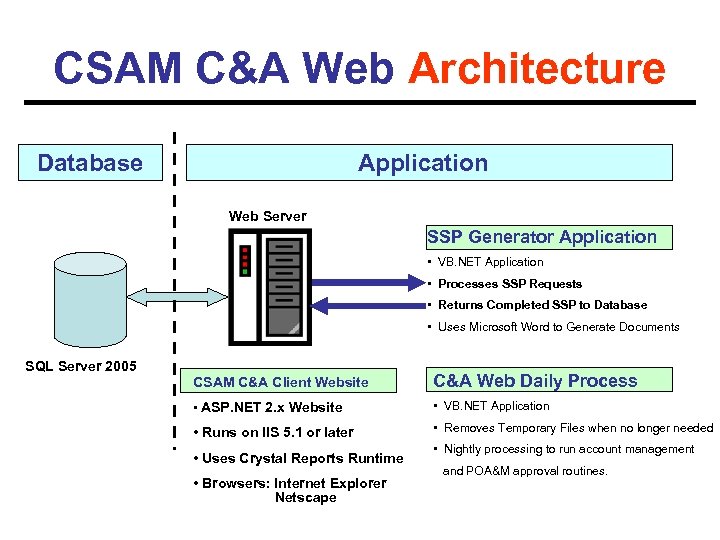
CSAM C&A Web Architecture Database Application Web Server SSP Generator Application • VB. NET Application • Processes SSP Requests • Returns Completed SSP to Database • Uses Microsoft Word to Generate Documents SQL Server 2005 CSAM C&A Client Website C&A Web Daily Process • ASP. NET 2. x Website • VB. NET Application • Runs on IIS 5. 1 or later • Removes Temporary Files when no longer needed • Uses Crystal Reports Runtime • Browsers: Internet Explorer Netscape • Nightly processing to run account management and POA&M approval routines.
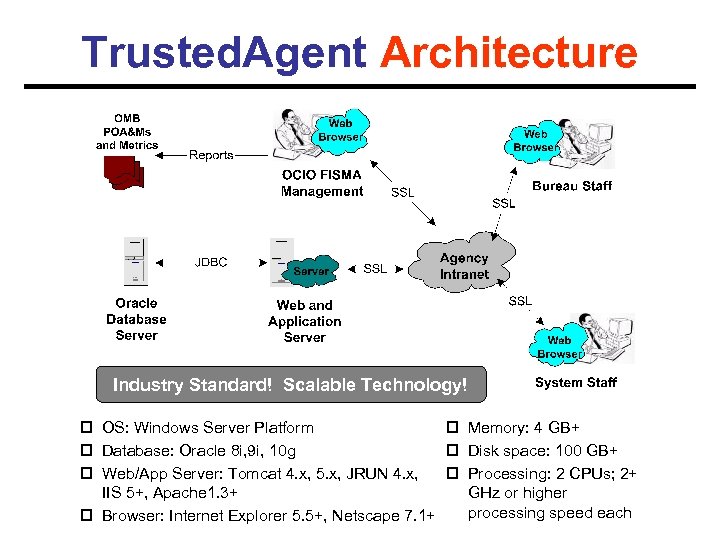
Trusted. Agent Architecture Industry Standard! Scalable Technology! p OS: Windows Server Platform p Memory: 4 GB+ p Database: Oracle 8 i, 9 i, 10 g p Disk space: 100 GB+ p Web/App Server: Tomcat 4. x, 5. x, JRUN 4. x, p Processing: 2 CPUs; 2+ IIS 5+, Apache 1. 3+ GHz or higher processing speed each p Browser: Internet Explorer 5. 5+, Netscape 7. 1+

Cyber Security Assessment & Management CSAM n Familiarization Demonstrations: n Friday, March 16 th: 9 am – noon n Monday, March 19 th: 9 am – noon n n Reservations Required Target audience: SSC Solutions Decision Makers C&A Functional Users IT Configuration Technicians For further information* : n n DOJLOBCSAM@usdoj. gov Ken Gandola 202 -353 -0081 Kenneth. d. gandola@usdog. gov Jim Leahy 202 -353 -8741 james. t. leahy@usdoj. gov * Please have agency project leads coordinate inputs for your agency or identify your position and project role with your inquiry.
b772b3b72e1e8f943d0b97a9af8b7cc0.ppt