06bf33e4f99fdc321eef7ace8da80421.ppt
- Количество слайдов: 42

Cyber-Identity, Authority and Trust in an Uncertain World Prof. Ravi Sandhu Laboratory for Information Security Technology George Mason University www. list. gmu. edu sandhu@gmu. edu

Outline n n n Perspective on security Role Based Access Control (RBAC) Objective Model-Architecture Mechanism (OM-AM) Framework Usage Control (UCON) Discussion 2

PERSPECTIVE

Security Conundrum n n Nobody knows WHAT security is Some of us do know HOW to implement pieces of it Result: hammers in search of nails 4
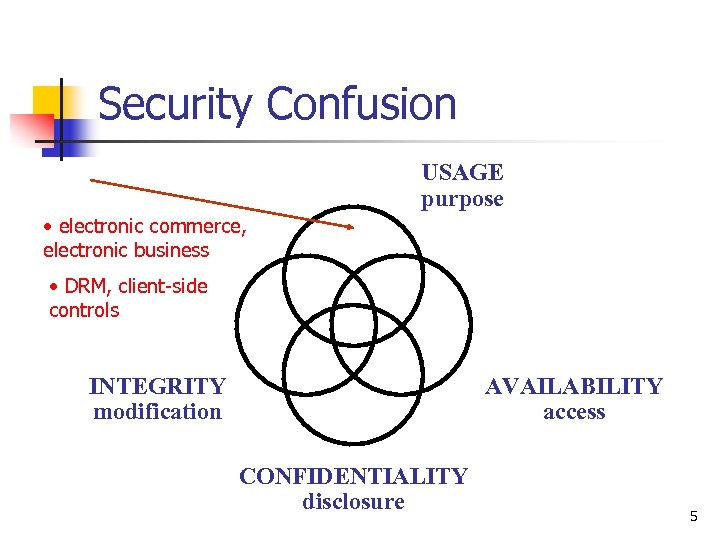
Security Confusion USAGE purpose • electronic commerce, electronic business • DRM, client-side controls INTEGRITY modification AVAILABILITY access CONFIDENTIALITY disclosure 5

Security Successes n n n On-line banking On-line trading Automatic teller machines (ATMs) GSM phones Set-top boxes Success is largely unrecognized by the security community 6

Good enough security n Exceeding good enough is not good n n n You will pay a price in user convenience, ease of operation, cost, performance, availability, … There is no such thing as free security Determining good enough is hard n Necessarily a moving target 7
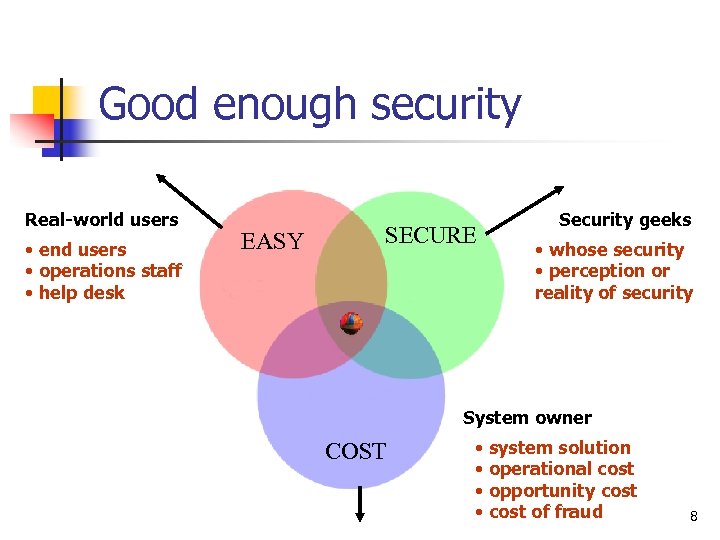
Good enough security Real-world users • end users • operations staff • help desk EASY SECURE Security geeks • whose security • perception or reality of security System owner COST • system solution • operational cost • opportunity cost • cost of fraud 8

Good enough security n In many cases good enough is achievable at a pretty low threshold n n The “entrepreneurial” mindset In extreme cases good enough will require a painfully high threshold n The “academic” mindset 9

ROLE-BASED ACCESS CONTROL (RBAC)
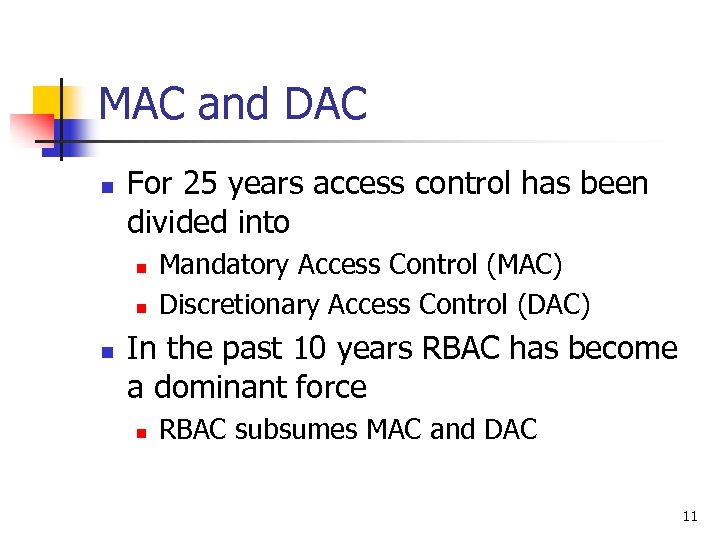
MAC and DAC n For 25 years access control has been divided into n n n Mandatory Access Control (MAC) Discretionary Access Control (DAC) In the past 10 years RBAC has become a dominant force n RBAC subsumes MAC and DAC 11
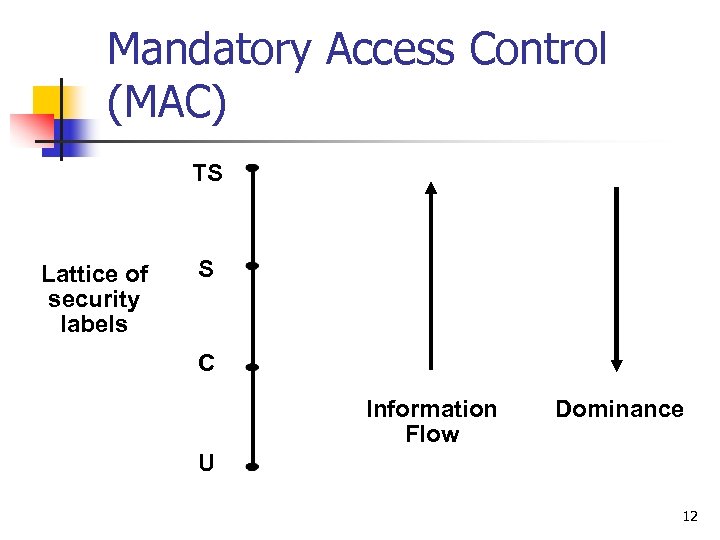
Mandatory Access Control (MAC) TS Lattice of security labels S C Information Flow Dominance U 12
![Mandatory Access Control (MAC) S, {A, B} S, {A] Lattice of security labels S, Mandatory Access Control (MAC) S, {A, B} S, {A] Lattice of security labels S,](https://present5.com/presentation/06bf33e4f99fdc321eef7ace8da80421/image-13.jpg)
Mandatory Access Control (MAC) S, {A, B} S, {A] Lattice of security labels S, {} Information Flow Dominance 13

Discretionary Access Control (DAC) n The owner of a resource determines access to that resource n n The owner is often the creator of the resource Fails to distinguish read from copy 14
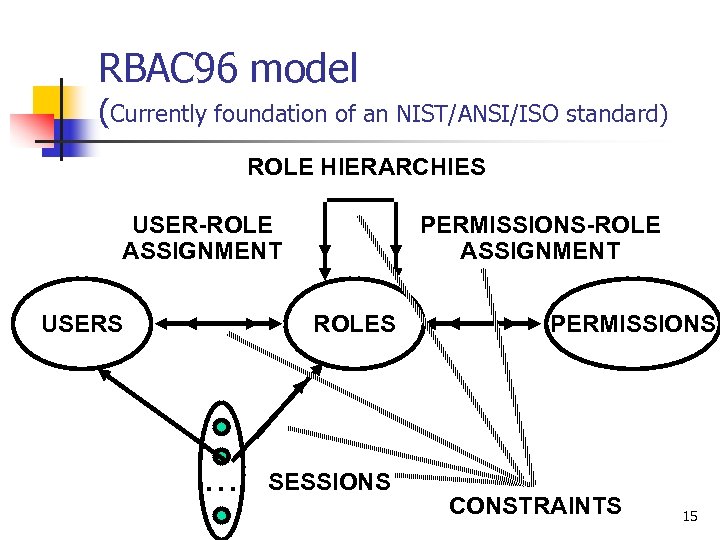
RBAC 96 model (Currently foundation of an NIST/ANSI/ISO standard) ROLE HIERARCHIES USER-ROLE ASSIGNMENT USERS PERMISSIONS-ROLE ASSIGNMENT ROLES . . . SESSIONS PERMISSIONS CONSTRAINTS 15

RBAC SECURITY PRINCIPLES n n least privilege separation of duties separation of administration and access abstract operations 16
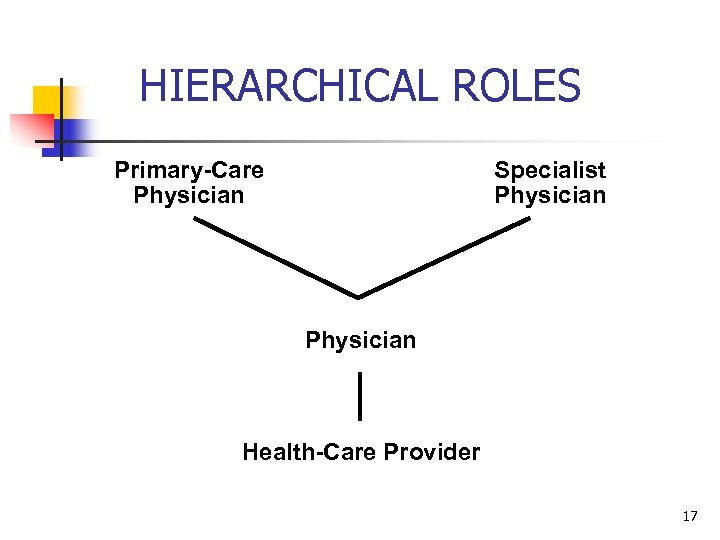
HIERARCHICAL ROLES Primary-Care Physician Specialist Physician Health-Care Provider 17

Fundamental Theorem of RBAC n n RBAC can be configured to do MAC RBAC can be configured to do DAC RBAC is policy neutral 18

OM-AM (Objective/Model. Architecture/Mechanism) Framework
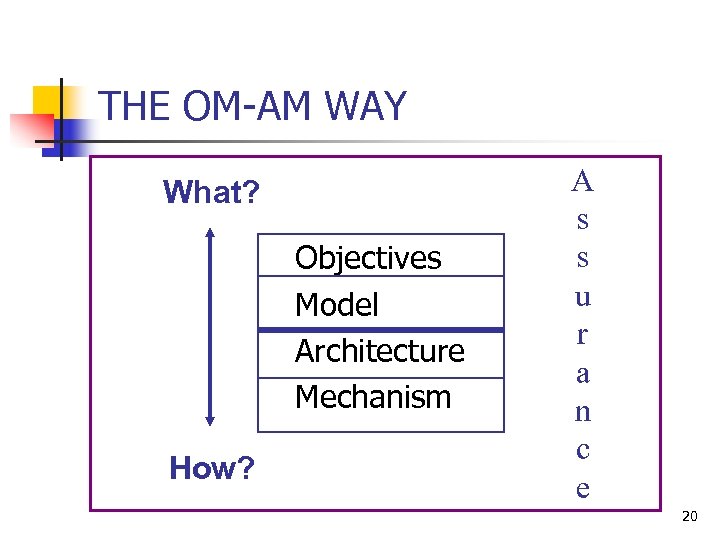
THE OM-AM WAY What? Objectives Model Architecture Mechanism How? A s s u r a n c e 20
LAYERS AND LAYERS n n n n Multics rings Layered abstractions Waterfall model Network protocol stacks Napolean layers Ro. Fi layers OM-AM etcetera 21
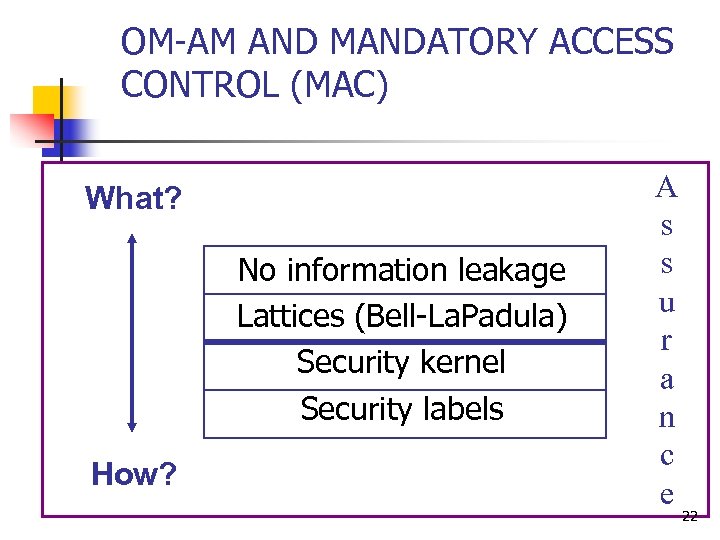
OM-AM AND MANDATORY ACCESS CONTROL (MAC) What? No information leakage Lattices (Bell-La. Padula) Security kernel Security labels How? A s s u r a n c e 22
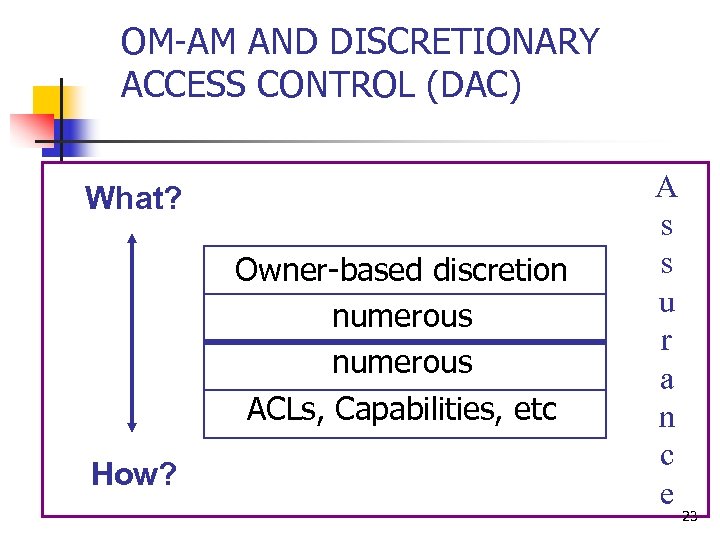
OM-AM AND DISCRETIONARY ACCESS CONTROL (DAC) What? Owner-based discretion numerous ACLs, Capabilities, etc How? A s s u r a n c e 23
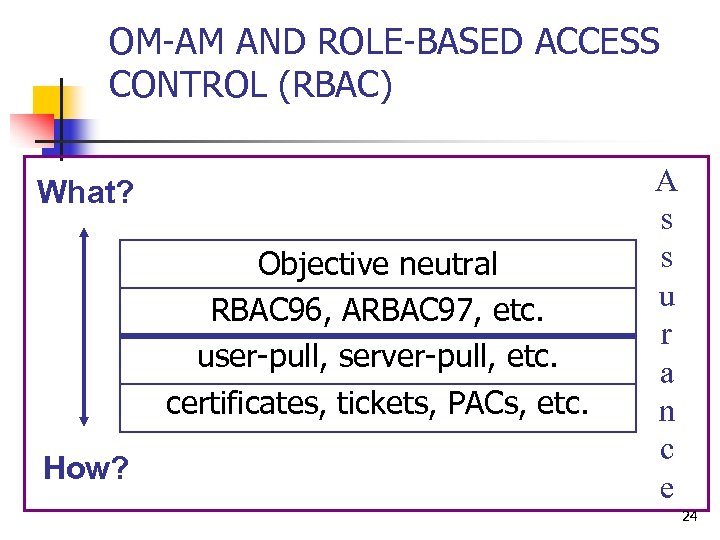
OM-AM AND ROLE-BASED ACCESS CONTROL (RBAC) What? Objective neutral RBAC 96, ARBAC 97, etc. user-pull, server-pull, etc. certificates, tickets, PACs, etc. How? A s s u r a n c e 24
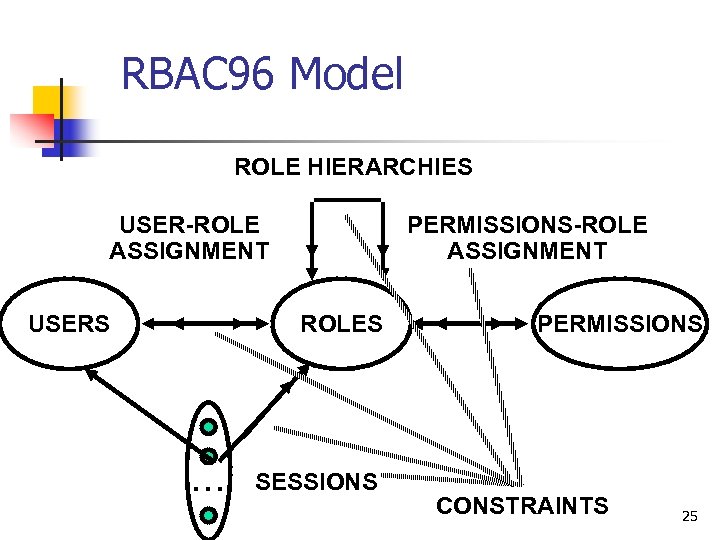
RBAC 96 Model ROLE HIERARCHIES USER-ROLE ASSIGNMENT USERS PERMISSIONS-ROLE ASSIGNMENT ROLES . . . SESSIONS PERMISSIONS CONSTRAINTS 25
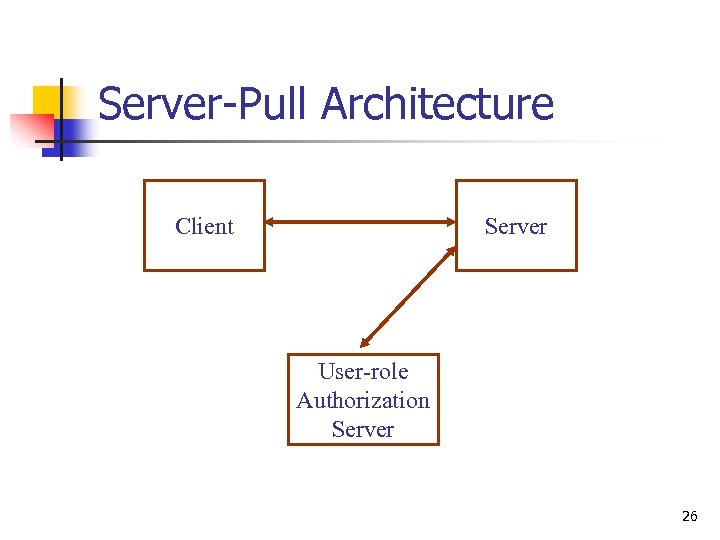
Server-Pull Architecture Client Server User-role Authorization Server 26
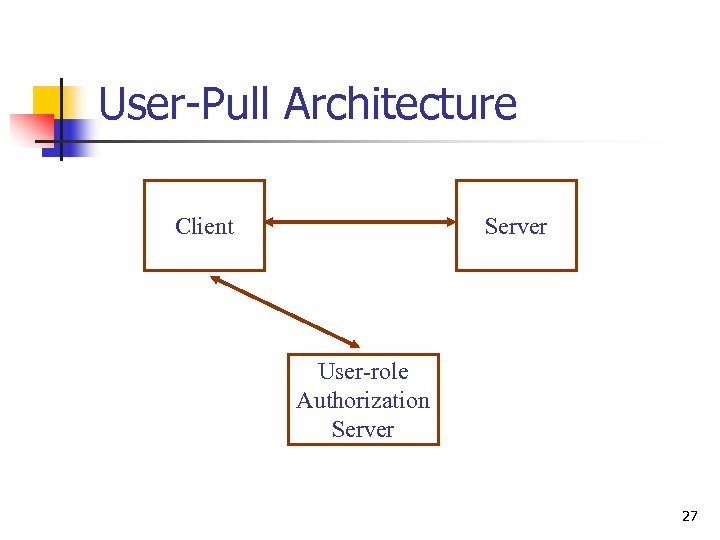
User-Pull Architecture Client Server User-role Authorization Server 27

Proxy-Based Architecture Client Proxy Server User-role Authorization Server 28

USAGE CONTROL (UCON)

The UCON Vision: A unified model n Traditional access control models are not adequate for today’s distributed, networkconnected digital environment. n n Authorization only – No obligation or condition based control Decision is made before access – No ongoing control No consumable rights - No mutable attributes Rights are pre-defined and granted to subjects 30
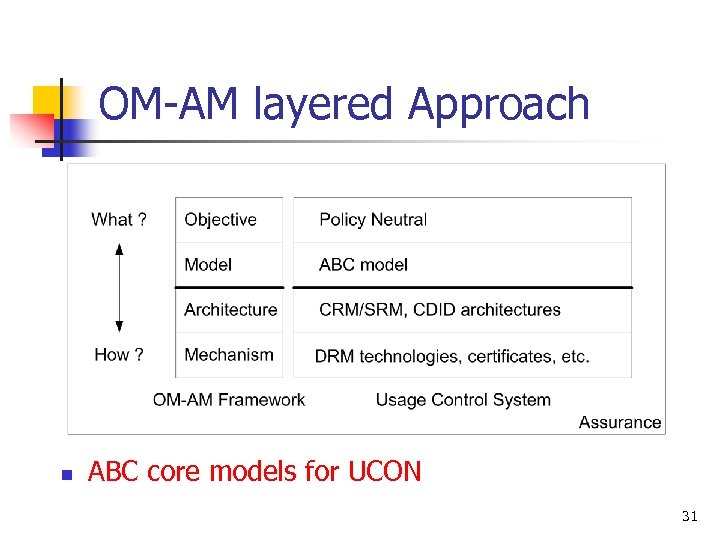
OM-AM layered Approach n ABC core models for UCON 31
Prior Work n Problem-specific enhancement to traditional access control n Digital Rights Management (DRM) n n n mainly focus on intellectual property rights protection. Architecture and Mechanism level studies, Functional specification languages – Lack of access control model Trust Management n Authorization for strangers’ access based on credentials 32
![Prior Work n Incrementally enhanced models n n Provisional authorization [Kudo & Hada, 2000] Prior Work n Incrementally enhanced models n n Provisional authorization [Kudo & Hada, 2000]](https://present5.com/presentation/06bf33e4f99fdc321eef7ace8da80421/image-33.jpg)
Prior Work n Incrementally enhanced models n n Provisional authorization [Kudo & Hada, 2000] EACL [Ryutov & Neuman, 2001] Task-based Access Control [Thomas & Sandhu, 1997] Ponder [Damianou et al. , 2001] 33
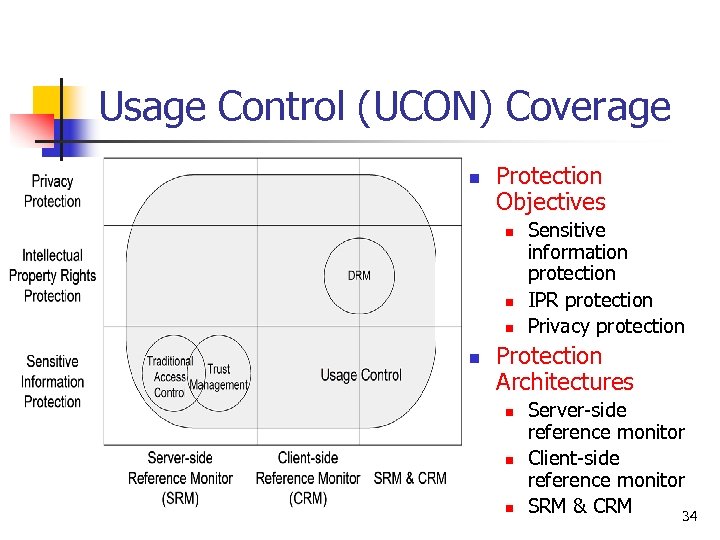
Usage Control (UCON) Coverage n Protection Objectives n n Sensitive information protection IPR protection Privacy protection Protection Architectures n n n Server-side reference monitor Client-side reference monitor SRM & CRM 34
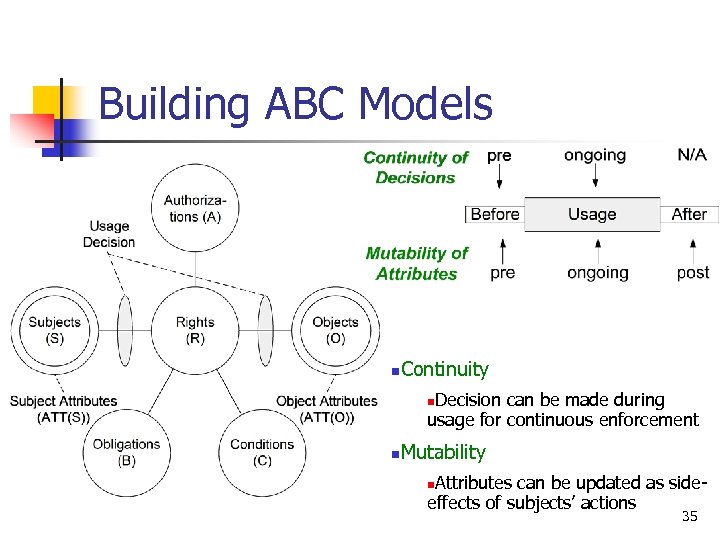
Building ABC Models n Continuity Decision can be made during usage for continuous enforcement n n Mutability Attributes can be updated as sideeffects of subjects’ actions n 35

Examples n n n Long-distance phone (pre-authorization with post-update) Pre-paid phone card (ongoing-authorization with ongoing-update) Pay-per-view (pre-authorization with preupdates) Click Ad within every 30 minutes (ongoingobligation with ongoing-updates) Business Hour (pre-/ongoing-condition) 36
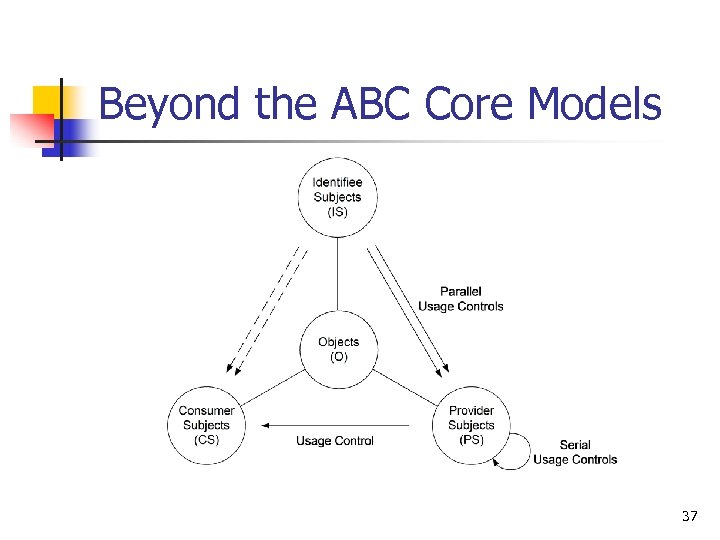
Beyond the ABC Core Models 37
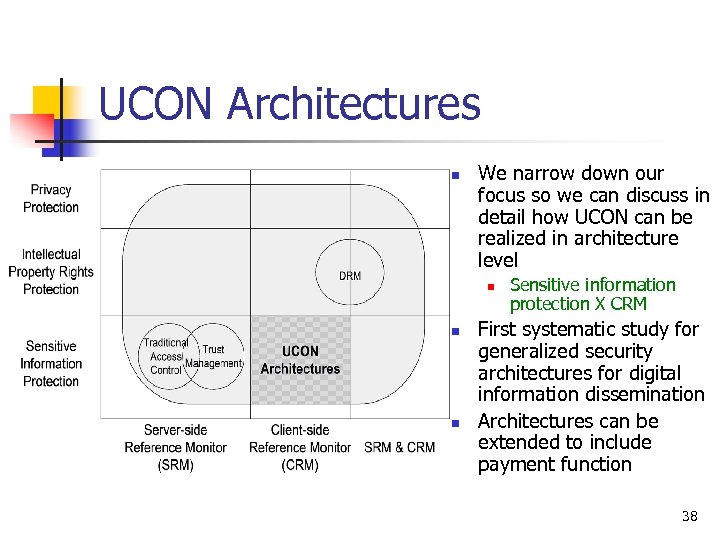
UCON Architectures n We narrow down our focus so we can discuss in detail how UCON can be realized in architecture level n n n Sensitive information protection X CRM First systematic study for generalized security architectures for digital information dissemination Architectures can be extended to include payment function 38
Three Factors of Security Architectures n Virtual Machine (VM) n n Control Set (CS) n n n runs on top of vulnerable computing environment and has control functions A list of access rights and usage rules Fixed, embedded, and external control set Distribution Style n Message Push (MP), External Repository (ER) style 39
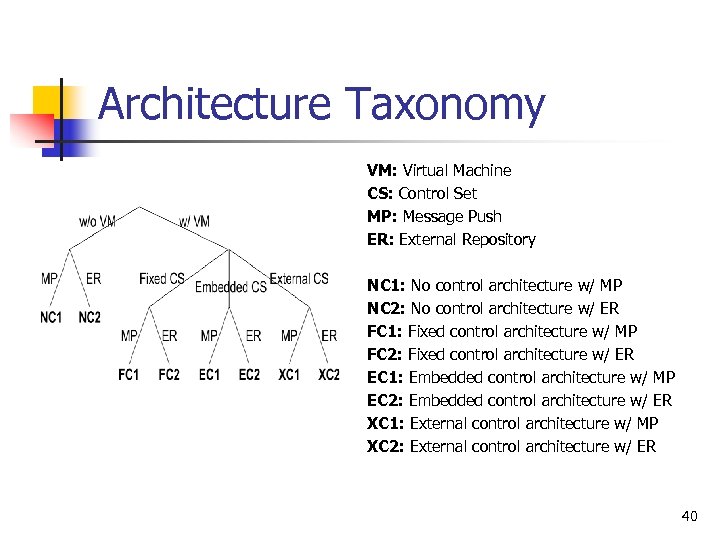
Architecture Taxonomy VM: Virtual Machine CS: Control Set MP: Message Push ER: External Repository NC 1: No control architecture w/ MP NC 2: No control architecture w/ ER FC 1: Fixed control architecture w/ MP FC 2: Fixed control architecture w/ ER EC 1: Embedded control architecture w/ MP EC 2: Embedded control architecture w/ ER XC 1: External control architecture w/ MP XC 2: External control architecture w/ ER 40

Conclusion n n Perspective on security Role Based Access Control (RBAC) Objective Model-Architecture Mechanism (OM-AM) Framework Usage Control (UCON) Discussion 41

Radical Shifts: get real Focus on n what needs to be done rather than how it is to be done n n n soft and informal rather than hard and formal n n n real-word business requirements rather than hypothetical academic scenarios the 80% problem rather than the 120% problem constructing the policy rather than auditing the policy constructive safety via policy articulation and evolution rather than post-facto algorithmic safety ordinary consumers as end-users and administrators rather than techno-geeks or math-geeks 42
06bf33e4f99fdc321eef7ace8da80421.ppt