c7cb5f720060fec3421678b40c51ba5f.ppt
- Количество слайдов: 51
 CSMA/CA Protocol: congestion control and fairness
CSMA/CA Protocol: congestion control and fairness
 Congestion Avoidance: IEEE 802. 1 DCF • If you heard something during a DIFS, wait until you hear a free DIFS • Then before transmitting a packet, randomly choose a backoff interval in the range [0, cw] – Even if medium isn’t busy – cw is the contention window • “Count down” the backoff interval once medium is idle – Count-down is suspended if medium becomes busy • When backoff interval reaches 0, transmit packet (or RTS)
Congestion Avoidance: IEEE 802. 1 DCF • If you heard something during a DIFS, wait until you hear a free DIFS • Then before transmitting a packet, randomly choose a backoff interval in the range [0, cw] – Even if medium isn’t busy – cw is the contention window • “Count down” the backoff interval once medium is idle – Count-down is suspended if medium becomes busy • When backoff interval reaches 0, transmit packet (or RTS)
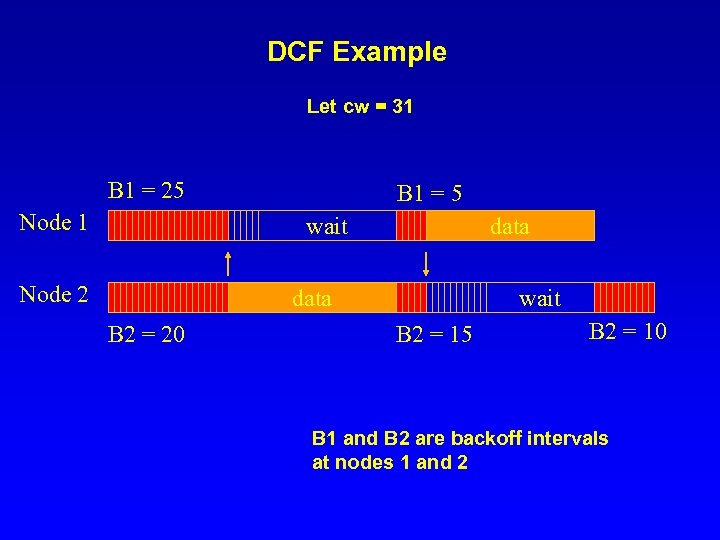 DCF Example Let cw = 31 B 1 = 25 Node 1 B 1 = 5 wait Node 2 data B 2 = 20 wait B 2 = 15 B 2 = 10 B 1 and B 2 are backoff intervals at nodes 1 and 2
DCF Example Let cw = 31 B 1 = 25 Node 1 B 1 = 5 wait Node 2 data B 2 = 20 wait B 2 = 15 B 2 = 10 B 1 and B 2 are backoff intervals at nodes 1 and 2
 Congestion Avoidance • The time spent counting down backoff intervals contributes to MAC overhead • Choosing a large cw leads to large backoff intervals and can result in larger overhead • Choosing a small cw leads to a larger number of collisions (more likely that two nodes count down to 0 simultaneously)
Congestion Avoidance • The time spent counting down backoff intervals contributes to MAC overhead • Choosing a large cw leads to large backoff intervals and can result in larger overhead • Choosing a small cw leads to a larger number of collisions (more likely that two nodes count down to 0 simultaneously)
 Congestion Control • Since the number of nodes attempting to transmit simultaneously may change with time, some mechanism to manage congestion is needed • IEEE 802. 11 DCF: Congestion control achieved by dynamically adjusting the contention window cw
Congestion Control • Since the number of nodes attempting to transmit simultaneously may change with time, some mechanism to manage congestion is needed • IEEE 802. 11 DCF: Congestion control achieved by dynamically adjusting the contention window cw
 Binary Exponential Backoff in DCF • When a node fails to receive CTS in response to its RTS, it increases the contention window – cw is doubled (up to an upper bound – typically 5 times) • When a node successfully completes a data transfer, it restores cw to CWmin
Binary Exponential Backoff in DCF • When a node fails to receive CTS in response to its RTS, it increases the contention window – cw is doubled (up to an upper bound – typically 5 times) • When a node successfully completes a data transfer, it restores cw to CWmin
![MILD Algorithm in MACAW [Bharghavan 94 Sigcomm] • When a node fails to receive MILD Algorithm in MACAW [Bharghavan 94 Sigcomm] • When a node fails to receive](https://present5.com/presentation/c7cb5f720060fec3421678b40c51ba5f/image-7.jpg) MILD Algorithm in MACAW [Bharghavan 94 Sigcomm] • When a node fails to receive CTS in response to its RTS, it multiplies cw by 1. 5 – Less aggressive than 802. 11, which multiplies by 2 • When a node successfully completes a transfer, it reduces cw by 1 – More conservative than 802. 11, where cw is restored to Cwmin – 802. 11 reduces cw much faster than it increases it – MACAW: cw reduction slower than the increase Exponential Increase Linear Decrease • MACAW can avoid wild oscillations of cw when congestion is high
MILD Algorithm in MACAW [Bharghavan 94 Sigcomm] • When a node fails to receive CTS in response to its RTS, it multiplies cw by 1. 5 – Less aggressive than 802. 11, which multiplies by 2 • When a node successfully completes a transfer, it reduces cw by 1 – More conservative than 802. 11, where cw is restored to Cwmin – 802. 11 reduces cw much faster than it increases it – MACAW: cw reduction slower than the increase Exponential Increase Linear Decrease • MACAW can avoid wild oscillations of cw when congestion is high
 Fairness Issue • Many definitions of fairness plausible • Simplest definition: All nodes should receive equal bandwidth A B Two flows C D
Fairness Issue • Many definitions of fairness plausible • Simplest definition: All nodes should receive equal bandwidth A B Two flows C D
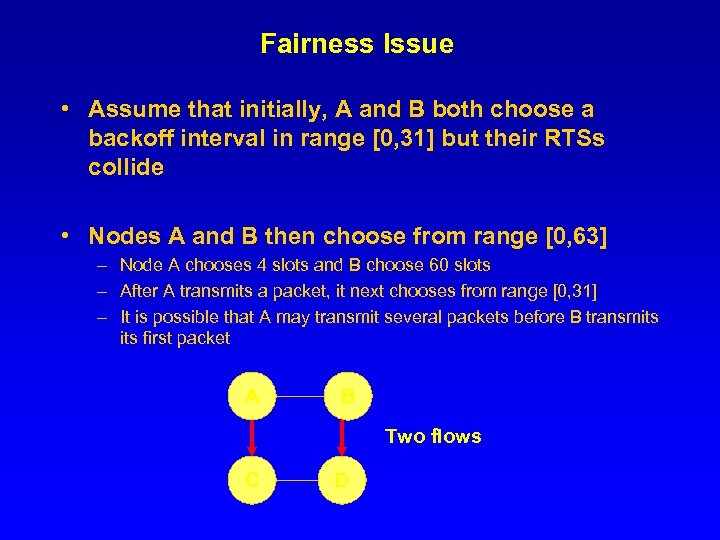 Fairness Issue • Assume that initially, A and B both choose a backoff interval in range [0, 31] but their RTSs collide • Nodes A and B then choose from range [0, 63] – Node A chooses 4 slots and B choose 60 slots – After A transmits a packet, it next chooses from range [0, 31] – It is possible that A may transmit several packets before B transmits first packet A B Two flows C D
Fairness Issue • Assume that initially, A and B both choose a backoff interval in range [0, 31] but their RTSs collide • Nodes A and B then choose from range [0, 63] – Node A chooses 4 slots and B choose 60 slots – After A transmits a packet, it next chooses from range [0, 31] – It is possible that A may transmit several packets before B transmits first packet A B Two flows C D
 Fairness Issue • Observation: unfairness occurs when one node has backed off much more than some other node A B Two flows C D
Fairness Issue • Observation: unfairness occurs when one node has backed off much more than some other node A B Two flows C D
 MACAW Solution for Fairness • When a node transmits a packet, it appends its current cw value to the packet • All nodes hearing that cw value use it for their future transmission attempts • The effect is to reset all competing nodes to the same ground rule
MACAW Solution for Fairness • When a node transmits a packet, it appends its current cw value to the packet • All nodes hearing that cw value use it for their future transmission attempts • The effect is to reset all competing nodes to the same ground rule
 Ad Hoc Nets - MAC layer CS 218 Fall 2015 Part II – Bluetooth
Ad Hoc Nets - MAC layer CS 218 Fall 2015 Part II – Bluetooth
 Bluetooth: Where does the name come from? A king of Denmark in the 10 th century
Bluetooth: Where does the name come from? A king of Denmark in the 10 th century
 What does Bluetooth do for you? Synchronization • Automatic synchronization of calendars, address books, business cards • Push button synchronization • Proximity operation
What does Bluetooth do for you? Synchronization • Automatic synchronization of calendars, address books, business cards • Push button synchronization • Proximity operation
 Cordless Headset Cordless headset User benefits • Multiple device access • Cordless phone benefits • Hands free operation
Cordless Headset Cordless headset User benefits • Multiple device access • Cordless phone benefits • Hands free operation
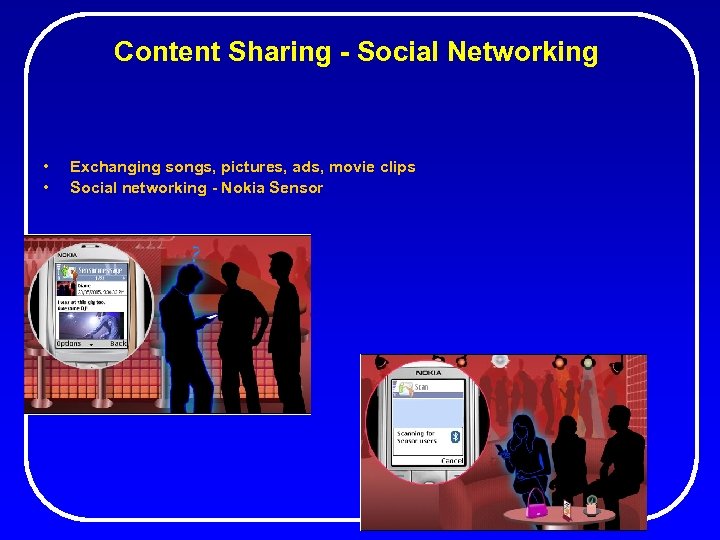 Content Sharing - Social Networking • • Exchanging songs, pictures, ads, movie clips Social networking - Nokia Sensor
Content Sharing - Social Networking • • Exchanging songs, pictures, ads, movie clips Social networking - Nokia Sensor
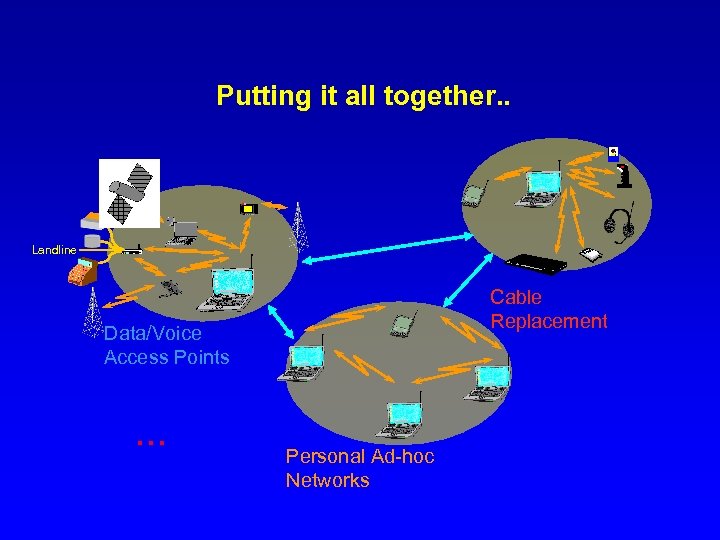 Putting it all together. . Landline Cable Replacement Data/Voice Access Points … Personal Ad-hoc Networks
Putting it all together. . Landline Cable Replacement Data/Voice Access Points … Personal Ad-hoc Networks
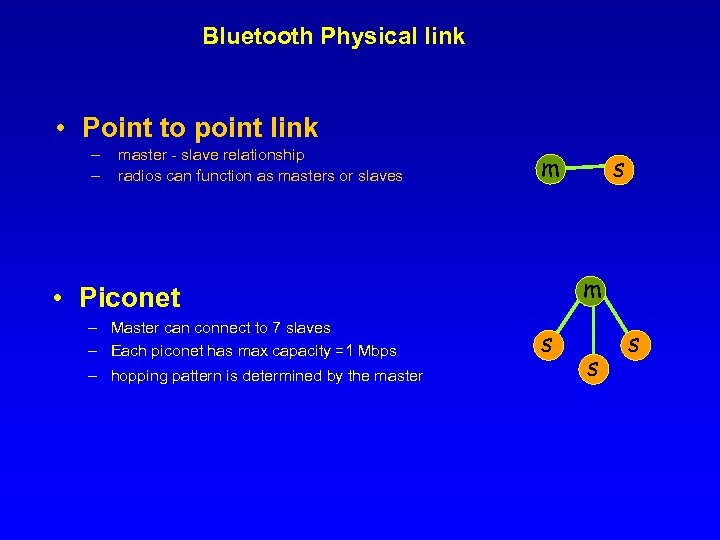 Bluetooth Physical link • Point to point link – – master - slave relationship radios can function as masters or slaves m m • Piconet – Master can connect to 7 slaves – Each piconet has max capacity =1 Mbps – hopping pattern is determined by the master s s
Bluetooth Physical link • Point to point link – – master - slave relationship radios can function as masters or slaves m m • Piconet – Master can connect to 7 slaves – Each piconet has max capacity =1 Mbps – hopping pattern is determined by the master s s
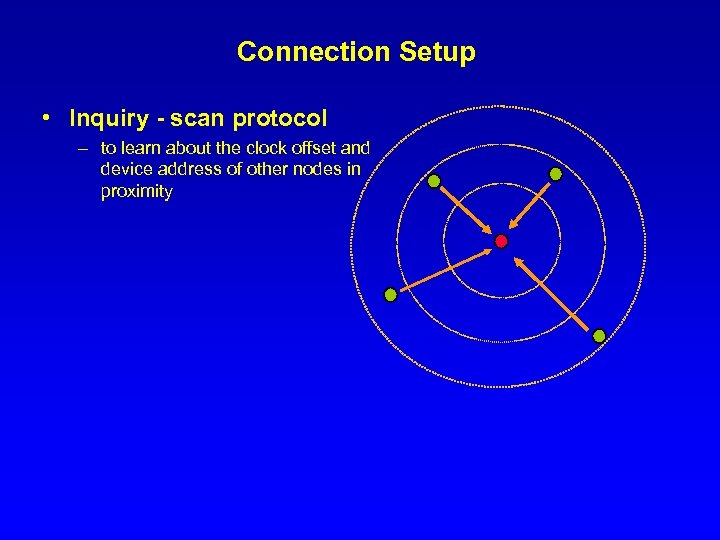 Connection Setup • Inquiry - scan protocol – to learn about the clock offset and device address of other nodes in proximity
Connection Setup • Inquiry - scan protocol – to learn about the clock offset and device address of other nodes in proximity
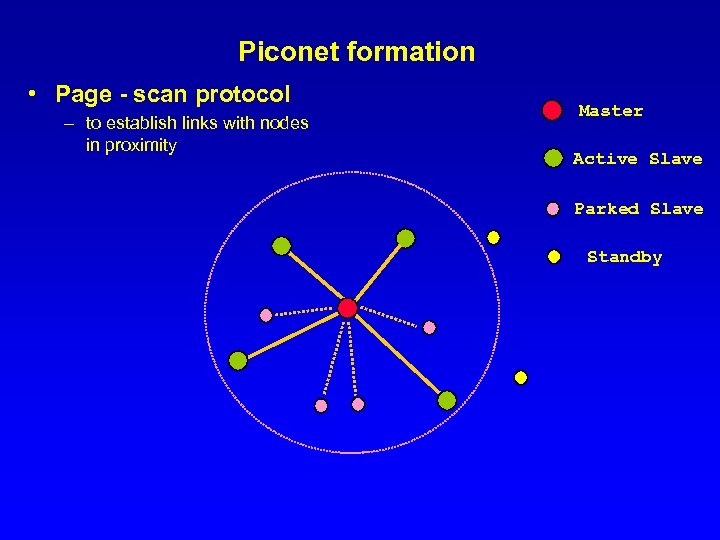 Piconet formation • Page - scan protocol – to establish links with nodes in proximity Master Active Slave Parked Slave Standby
Piconet formation • Page - scan protocol – to establish links with nodes in proximity Master Active Slave Parked Slave Standby
 Addressing • Bluetooth device address (BD_ADDR) – 48 bit IEEE MAC address • Active Member address (AM_ADDR) – 3 bits active slave address – all zero broadcast address • Parked Member address (PM_ADDR) – 8 bit parked slave address
Addressing • Bluetooth device address (BD_ADDR) – 48 bit IEEE MAC address • Active Member address (AM_ADDR) – 3 bits active slave address – all zero broadcast address • Parked Member address (PM_ADDR) – 8 bit parked slave address
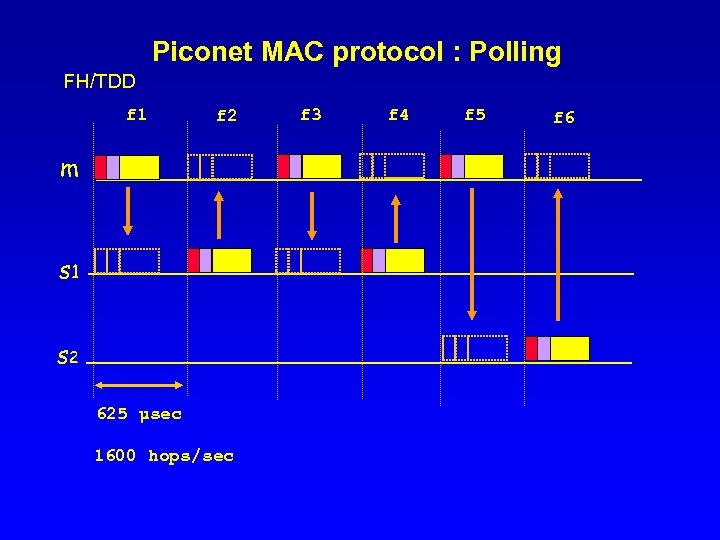 Piconet MAC protocol : Polling FH/TDD f 1 f 2 m s 1 s 2 625 µsec 1600 hops/sec f 3 f 4 f 5 f 6
Piconet MAC protocol : Polling FH/TDD f 1 f 2 m s 1 s 2 625 µsec 1600 hops/sec f 3 f 4 f 5 f 6
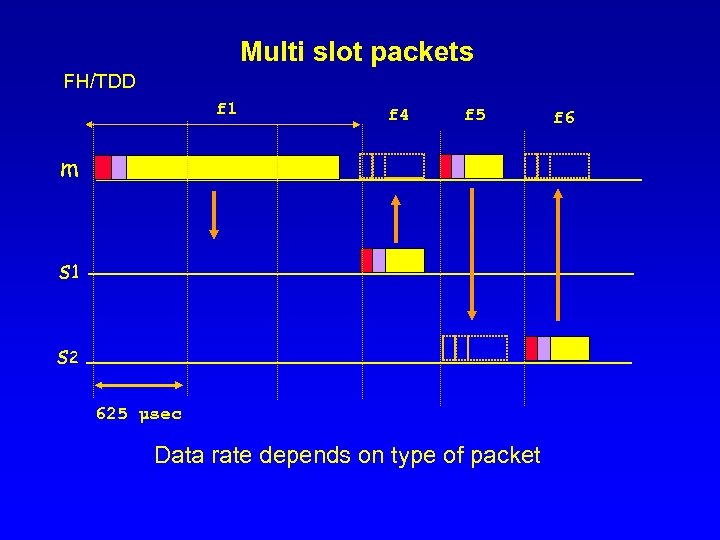 Multi slot packets FH/TDD f 1 f 4 f 5 m s 1 s 2 625 µsec Data rate depends on type of packet f 6
Multi slot packets FH/TDD f 1 f 4 f 5 m s 1 s 2 625 µsec Data rate depends on type of packet f 6
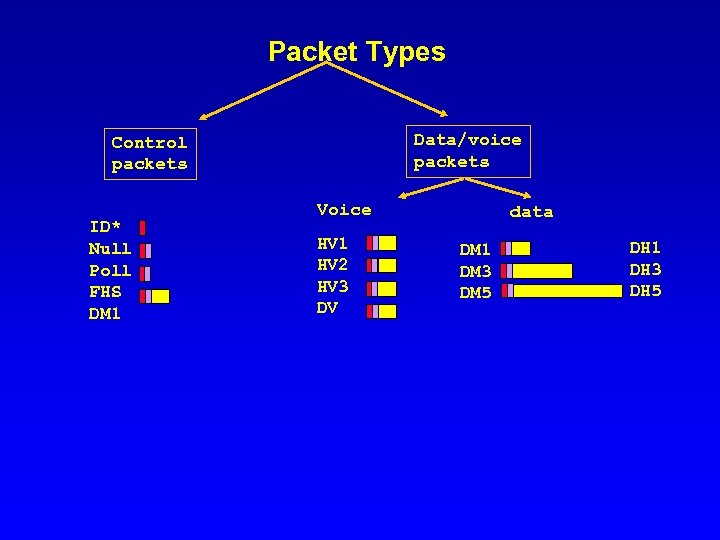 Packet Types Data/voice packets Control packets ID* Null Poll FHS DM 1 Voice HV 1 HV 2 HV 3 DV data DM 1 DM 3 DM 5 DH 1 DH 3 DH 5
Packet Types Data/voice packets Control packets ID* Null Poll FHS DM 1 Voice HV 1 HV 2 HV 3 DV data DM 1 DM 3 DM 5 DH 1 DH 3 DH 5
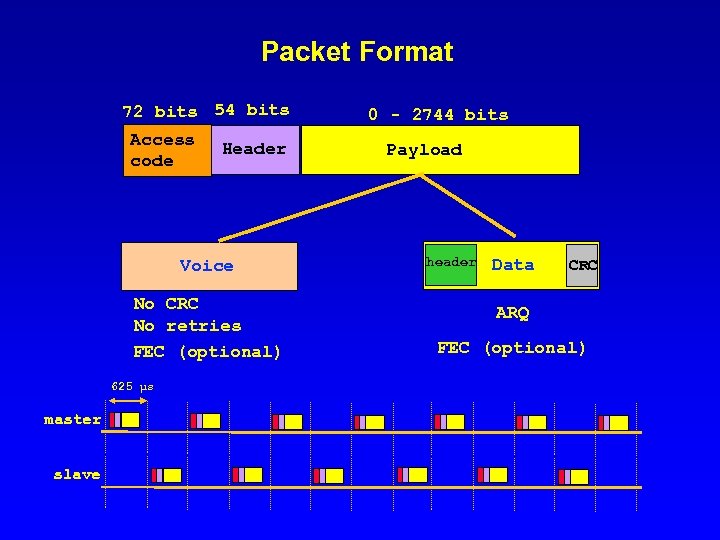 Packet Format 72 bits 54 bits Access code Header Voice No CRC No retries FEC (optional) 625 µs master slave 0 - 2744 bits Payload header Data CRC ARQ FEC (optional)
Packet Format 72 bits 54 bits Access code Header Voice No CRC No retries FEC (optional) 625 µs master slave 0 - 2744 bits Payload header Data CRC ARQ FEC (optional)
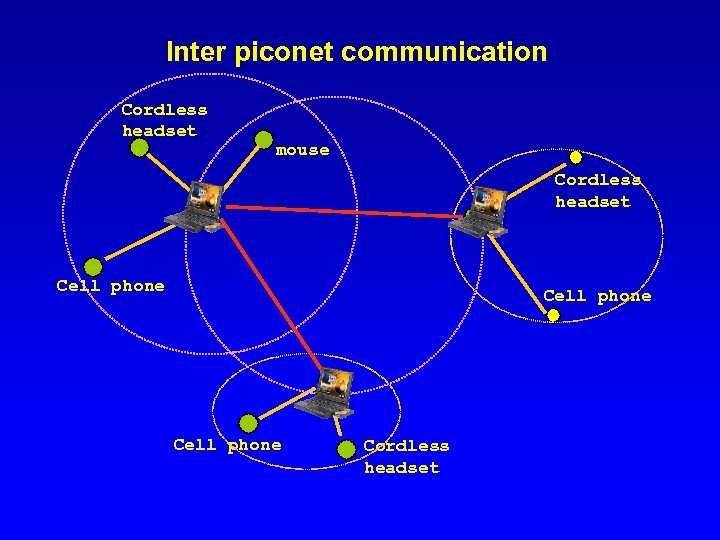 Inter piconet communication Cordless headset mouse Cordless headset Cell phone Cordless headset
Inter piconet communication Cordless headset mouse Cordless headset Cell phone Cordless headset
 Zig. Bee and IEEE 802. 15. 4 The MAC Layer CS 218 Fall 2014
Zig. Bee and IEEE 802. 15. 4 The MAC Layer CS 218 Fall 2014
 The Zig. Bee Alliance Solution • Targeted at home and building automation and controls, consumer electronics, toys etc. • Industry standard (IEEE 802. 15. 4 radios) • Primary drivers are simplicity, long battery life, networking capabilities, reliability, and cost Copyright 2002 The Zig. Bee Alliance, Inc.
The Zig. Bee Alliance Solution • Targeted at home and building automation and controls, consumer electronics, toys etc. • Industry standard (IEEE 802. 15. 4 radios) • Primary drivers are simplicity, long battery life, networking capabilities, reliability, and cost Copyright 2002 The Zig. Bee Alliance, Inc.
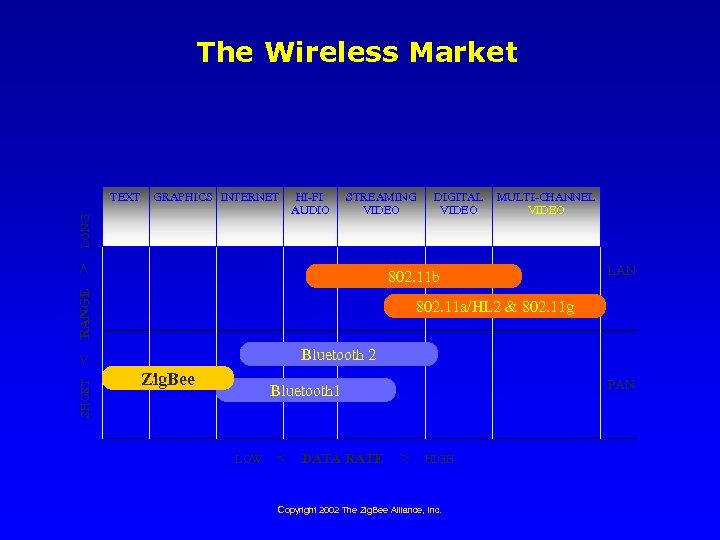 The Wireless Market GRAPHICS INTERNET HI-FI AUDIO STREAMING VIDEO > LONG TEXT MULTI-CHANNEL VIDEO RANGE 802. 11 b LAN 802. 11 a/HL 2 & 802. 11 g Bluetooth 2 < SHORT DIGITAL VIDEO Zig. Bee PAN Bluetooth 1 LOW < DATA RATE > HIGH Copyright 2002 The Zig. Bee Alliance, Inc.
The Wireless Market GRAPHICS INTERNET HI-FI AUDIO STREAMING VIDEO > LONG TEXT MULTI-CHANNEL VIDEO RANGE 802. 11 b LAN 802. 11 a/HL 2 & 802. 11 g Bluetooth 2 < SHORT DIGITAL VIDEO Zig. Bee PAN Bluetooth 1 LOW < DATA RATE > HIGH Copyright 2002 The Zig. Bee Alliance, Inc.
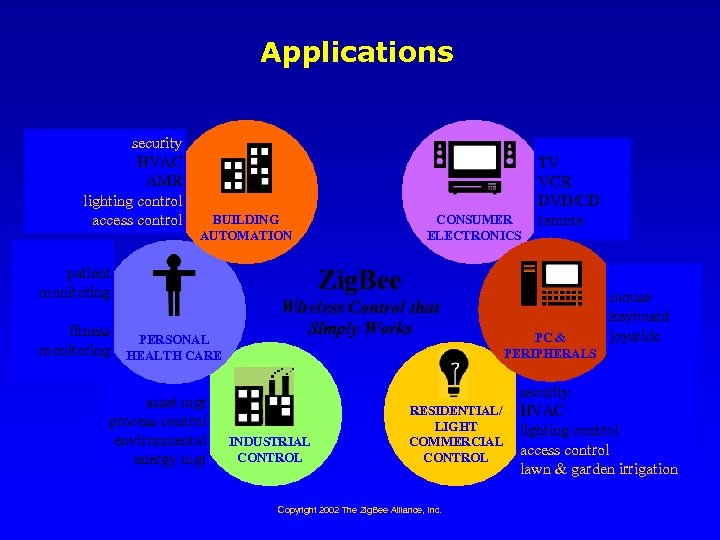 Applications security HVAC AMR lighting control access control BUILDING AUTOMATION patient monitoring fitness PERSONAL monitoring HEALTH CARE asset mgt process control environmental energy mgt CONSUMER ELECTRONICS TV VCR DVD/CD remote Zig. Bee Wireless Control that Simply Works INDUSTRIAL CONTROL RESIDENTIAL/ LIGHT COMMERCIAL CONTROL Copyright 2002 The Zig. Bee Alliance, Inc. PC & PERIPHERALS mouse keyboard joystick security HVAC lighting control access control lawn & garden irrigation
Applications security HVAC AMR lighting control access control BUILDING AUTOMATION patient monitoring fitness PERSONAL monitoring HEALTH CARE asset mgt process control environmental energy mgt CONSUMER ELECTRONICS TV VCR DVD/CD remote Zig. Bee Wireless Control that Simply Works INDUSTRIAL CONTROL RESIDENTIAL/ LIGHT COMMERCIAL CONTROL Copyright 2002 The Zig. Bee Alliance, Inc. PC & PERIPHERALS mouse keyboard joystick security HVAC lighting control access control lawn & garden irrigation
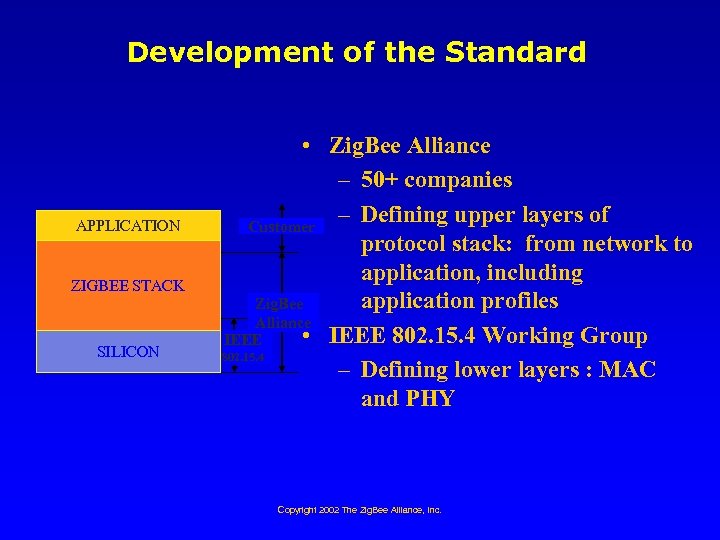 Development of the Standard APPLICATION ZIGBEE STACK SILICON • Zig. Bee Alliance – 50+ companies – Defining upper layers of Customer protocol stack: from network to application, including application profiles Zig. Bee Alliance • IEEE 802. 15. 4 Working Group IEEE 802. 15. 4 – Defining lower layers : MAC and PHY Copyright 2002 The Zig. Bee Alliance, Inc.
Development of the Standard APPLICATION ZIGBEE STACK SILICON • Zig. Bee Alliance – 50+ companies – Defining upper layers of Customer protocol stack: from network to application, including application profiles Zig. Bee Alliance • IEEE 802. 15. 4 Working Group IEEE 802. 15. 4 – Defining lower layers : MAC and PHY Copyright 2002 The Zig. Bee Alliance, Inc.
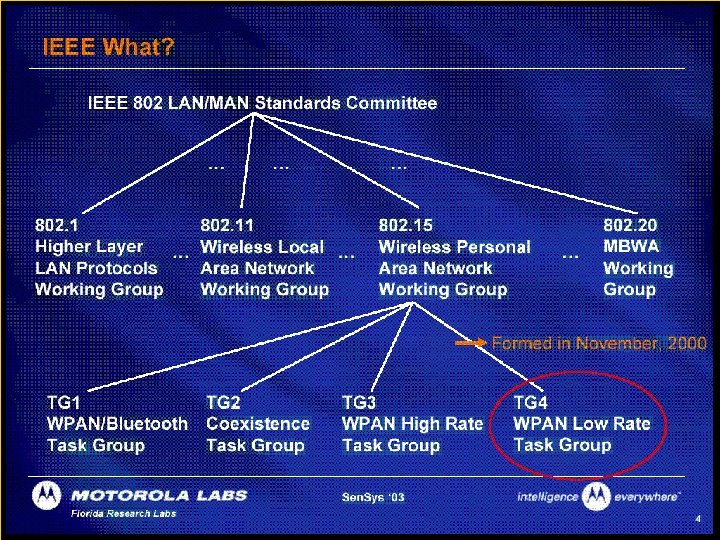 Copyright 2002 The Zig. Bee Alliance, Inc.
Copyright 2002 The Zig. Bee Alliance, Inc.
 IEEE 802. 15. 4 Basics • 802. 15. 4 is a simple packet data protocol: – Carrier Sense Multiple Access with collision avoidance – Optional time slotting and beacon structure – Three bands, 27 channels specified • 2. 4 GHz: 16 channels, 250 kbps • 868. 3 MHz : 1 channel, 20 kbps • 902 -928 MHz: 10 channels, 40 kbps • Works well for: – Long battery life, selectable latency for controllers, sensors, remote monitoring and portable electronics Copyright 2002 The Zig. Bee Alliance, Inc.
IEEE 802. 15. 4 Basics • 802. 15. 4 is a simple packet data protocol: – Carrier Sense Multiple Access with collision avoidance – Optional time slotting and beacon structure – Three bands, 27 channels specified • 2. 4 GHz: 16 channels, 250 kbps • 868. 3 MHz : 1 channel, 20 kbps • 902 -928 MHz: 10 channels, 40 kbps • Works well for: – Long battery life, selectable latency for controllers, sensors, remote monitoring and portable electronics Copyright 2002 The Zig. Bee Alliance, Inc.
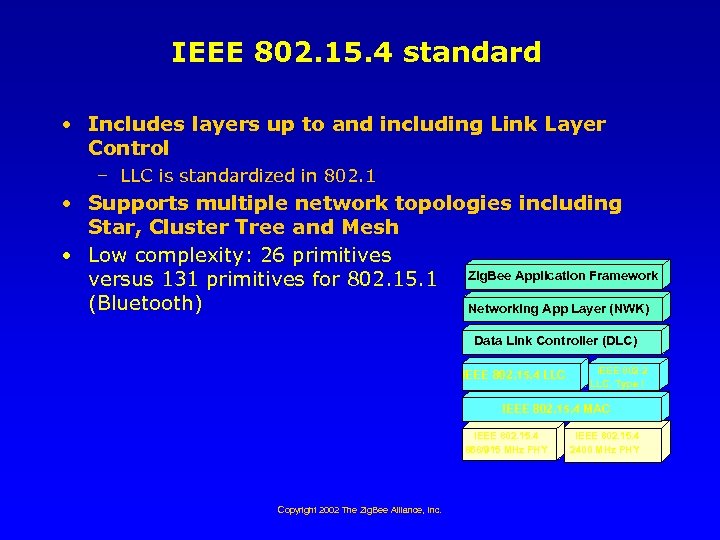 IEEE 802. 15. 4 standard • Includes layers up to and including Link Layer Control – LLC is standardized in 802. 1 • Supports multiple network topologies including Star, Cluster Tree and Mesh • Low complexity: 26 primitives Zig. Bee Application Framework versus 131 primitives for 802. 15. 1 (Bluetooth) Networking App Layer (NWK) Data Link Controller (DLC) IEEE 802. 15. 4 LLC IEEE 802. 2 LLC, Type I IEEE 802. 15. 4 MAC IEEE 802. 15. 4 868/915 MHz PHY Copyright 2002 The Zig. Bee Alliance, Inc. IEEE 802. 15. 4 2400 MHz PHY
IEEE 802. 15. 4 standard • Includes layers up to and including Link Layer Control – LLC is standardized in 802. 1 • Supports multiple network topologies including Star, Cluster Tree and Mesh • Low complexity: 26 primitives Zig. Bee Application Framework versus 131 primitives for 802. 15. 1 (Bluetooth) Networking App Layer (NWK) Data Link Controller (DLC) IEEE 802. 15. 4 LLC IEEE 802. 2 LLC, Type I IEEE 802. 15. 4 MAC IEEE 802. 15. 4 868/915 MHz PHY Copyright 2002 The Zig. Bee Alliance, Inc. IEEE 802. 15. 4 2400 MHz PHY
 IEEE 802. 15. 4 Device Types • Three device types – Network Coordinator • Maintains overall network knowledge; most memory and computing power – Full Function Device • Carries full 802. 15. 4 functionality and all features specified by the standard; ideal for a network router function – Reduced Function Device • Carriers limited functionality; used for network edge devices • All of these devices can be no more complicated than the transceiver, a simple 8 -bit MCU and a pair of AAA batteries! Copyright 2002 The Zig. Bee Alliance, Inc.
IEEE 802. 15. 4 Device Types • Three device types – Network Coordinator • Maintains overall network knowledge; most memory and computing power – Full Function Device • Carries full 802. 15. 4 functionality and all features specified by the standard; ideal for a network router function – Reduced Function Device • Carriers limited functionality; used for network edge devices • All of these devices can be no more complicated than the transceiver, a simple 8 -bit MCU and a pair of AAA batteries! Copyright 2002 The Zig. Bee Alliance, Inc.
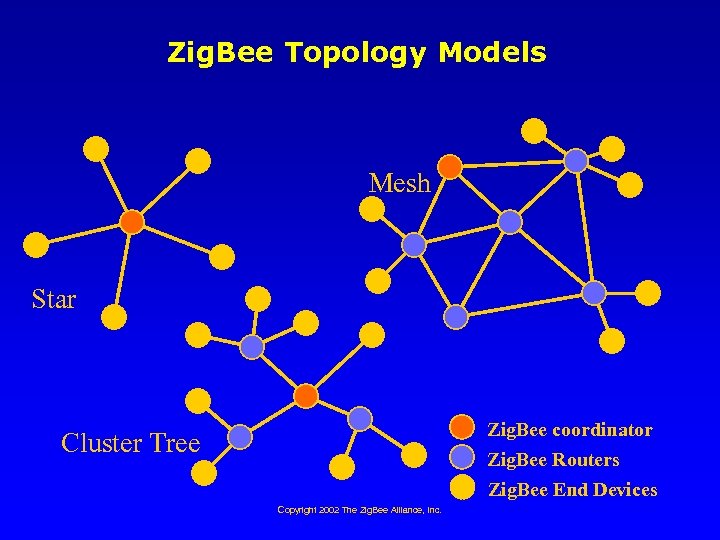 Zig. Bee Topology Models Mesh Star Zig. Bee coordinator Zig. Bee Routers Zig. Bee End Devices Cluster Tree Copyright 2002 The Zig. Bee Alliance, Inc.
Zig. Bee Topology Models Mesh Star Zig. Bee coordinator Zig. Bee Routers Zig. Bee End Devices Cluster Tree Copyright 2002 The Zig. Bee Alliance, Inc.
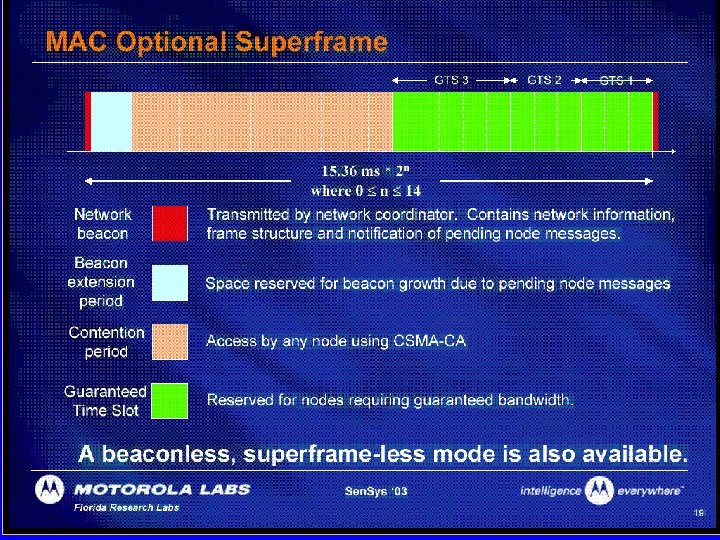
 MAC Options • Two channel access mechanisms – Non-beacon network • Standard CSMA-CA communications + ACK – Beacon-enabled network • Superframe structure – For dedicated bandwidth and low latency – Set up by network coordinator to transmit beacons at predetermined intervals • 15 ms to 252 sec • 16 equal-width time slots between beacons • Channel access in each time slot is contention free Copyright 2002 The Zig. Bee Alliance, Inc.
MAC Options • Two channel access mechanisms – Non-beacon network • Standard CSMA-CA communications + ACK – Beacon-enabled network • Superframe structure – For dedicated bandwidth and low latency – Set up by network coordinator to transmit beacons at predetermined intervals • 15 ms to 252 sec • 16 equal-width time slots between beacons • Channel access in each time slot is contention free Copyright 2002 The Zig. Bee Alliance, Inc.
 Copyright 2002 The Zig. Bee Alliance, Inc.
Copyright 2002 The Zig. Bee Alliance, Inc.
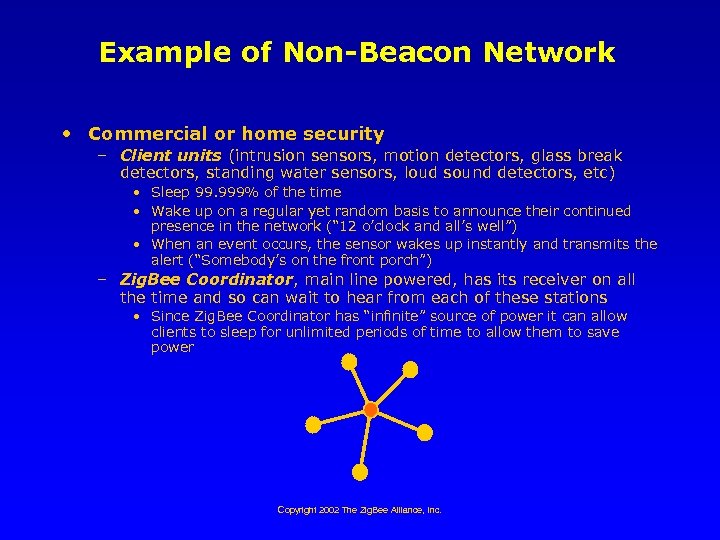 Example of Non-Beacon Network • Commercial or home security – Client units (intrusion sensors, motion detectors, glass break detectors, standing water sensors, loud sound detectors, etc) • Sleep 99. 999% of the time • Wake up on a regular yet random basis to announce their continued presence in the network (“ 12 o’clock and all’s well”) • When an event occurs, the sensor wakes up instantly and transmits the alert (“Somebody’s on the front porch”) – Zig. Bee Coordinator, main line powered, has its receiver on all the time and so can wait to hear from each of these stations • Since Zig. Bee Coordinator has “infinite” source of power it can allow clients to sleep for unlimited periods of time to allow them to save power Copyright 2002 The Zig. Bee Alliance, Inc.
Example of Non-Beacon Network • Commercial or home security – Client units (intrusion sensors, motion detectors, glass break detectors, standing water sensors, loud sound detectors, etc) • Sleep 99. 999% of the time • Wake up on a regular yet random basis to announce their continued presence in the network (“ 12 o’clock and all’s well”) • When an event occurs, the sensor wakes up instantly and transmits the alert (“Somebody’s on the front porch”) – Zig. Bee Coordinator, main line powered, has its receiver on all the time and so can wait to hear from each of these stations • Since Zig. Bee Coordinator has “infinite” source of power it can allow clients to sleep for unlimited periods of time to allow them to save power Copyright 2002 The Zig. Bee Alliance, Inc.
 Copyright 2002 The Zig. Bee Alliance, Inc.
Copyright 2002 The Zig. Bee Alliance, Inc.
 Example of Beacon Network • Now make the Zig. Bee Coordinator batteryoperated also – Client registration to the network • Client unit when first powered up listens for the Zig. Bee Coordinator’s network beacon (interval between 0. 015 and 252 seconds) • Register with the coordinator and look for any messages directed to it • Return to sleep, awaking on a schedule specified by the Zig. Bee Coordinator • Once client communications are completed, Zig. Bee coordinator also returns to sleep – Application examples: environmental sensors in the forest Copyright 2002 The Zig. Bee Alliance, Inc.
Example of Beacon Network • Now make the Zig. Bee Coordinator batteryoperated also – Client registration to the network • Client unit when first powered up listens for the Zig. Bee Coordinator’s network beacon (interval between 0. 015 and 252 seconds) • Register with the coordinator and look for any messages directed to it • Return to sleep, awaking on a schedule specified by the Zig. Bee Coordinator • Once client communications are completed, Zig. Bee coordinator also returns to sleep – Application examples: environmental sensors in the forest Copyright 2002 The Zig. Bee Alliance, Inc.
 Zig. Bee and Bluetooth Optimized for different applications • Bluetooth • Zig. Bee – Larger packets over small – Smaller packets over network large network – Ad-hoc networks – Mostly Static networks with many, – File transfer; streaming infrequently used – Screen graphics, pictures, devices hands-free audio, Mobile – Home automation, phones, headsets, PDAs, toys remote controls etc. – Energy saver!!! Copyright 2002 The Zig. Bee Alliance, Inc.
Zig. Bee and Bluetooth Optimized for different applications • Bluetooth • Zig. Bee – Larger packets over small – Smaller packets over network large network – Ad-hoc networks – Mostly Static networks with many, – File transfer; streaming infrequently used – Screen graphics, pictures, devices hands-free audio, Mobile – Home automation, phones, headsets, PDAs, toys remote controls etc. – Energy saver!!! Copyright 2002 The Zig. Bee Alliance, Inc.
 Zig. Bee and Bluetooth Address Different Needs • Bluetooth is a cable replacement for items like Phones, Laptop Computers, Headsets • Bluetooth expects regular charging – Target is to use <10% of host power Copyright 2002 The Zig. Bee Alliance, Inc.
Zig. Bee and Bluetooth Address Different Needs • Bluetooth is a cable replacement for items like Phones, Laptop Computers, Headsets • Bluetooth expects regular charging – Target is to use <10% of host power Copyright 2002 The Zig. Bee Alliance, Inc.
 Zig. Bee and Bluetooth Address Different Needs • Zig. Bee is better for devices where the battery is ‘rarely’ replaced – Targets are : • Tiny fraction of host power • New opportunities where wireless not yet used Copyright 2002 The Zig. Bee Alliance, Inc.
Zig. Bee and Bluetooth Address Different Needs • Zig. Bee is better for devices where the battery is ‘rarely’ replaced – Targets are : • Tiny fraction of host power • New opportunities where wireless not yet used Copyright 2002 The Zig. Bee Alliance, Inc.
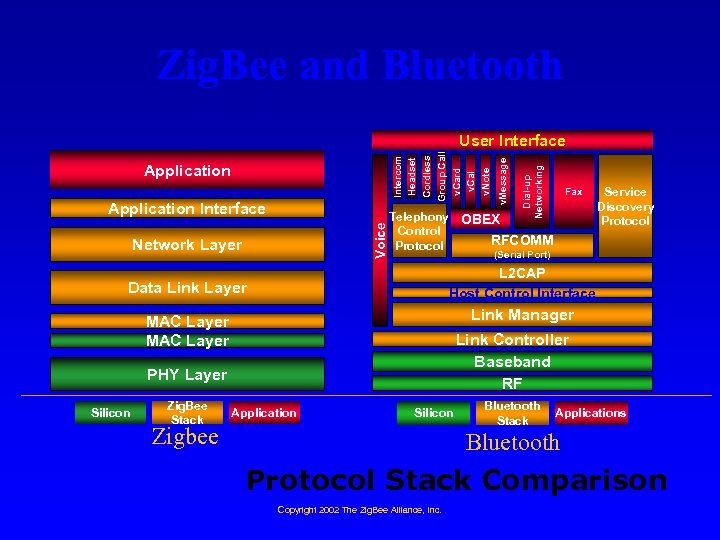 Zig. Bee and Bluetooth Voice Application Interface Network Layer Service Discovery Protocol (Serial Port) L 2 CAP Host Control Interface Link Manager MAC Layer Link Controller Baseband RF PHY Layer Zig. Bee Stack Fax Telephony OBEX Control RFCOMM Protocol Data Link Layer Silicon Dial-up Networking Application v. Message Intercom Headset Cordless Group Call v. Card v. Cal v. Note User Interface Application Silicon Zigbee Bluetooth Stack Applications Bluetooth Protocol Stack Comparison Copyright 2002 The Zig. Bee Alliance, Inc.
Zig. Bee and Bluetooth Voice Application Interface Network Layer Service Discovery Protocol (Serial Port) L 2 CAP Host Control Interface Link Manager MAC Layer Link Controller Baseband RF PHY Layer Zig. Bee Stack Fax Telephony OBEX Control RFCOMM Protocol Data Link Layer Silicon Dial-up Networking Application v. Message Intercom Headset Cordless Group Call v. Card v. Cal v. Note User Interface Application Silicon Zigbee Bluetooth Stack Applications Bluetooth Protocol Stack Comparison Copyright 2002 The Zig. Bee Alliance, Inc.
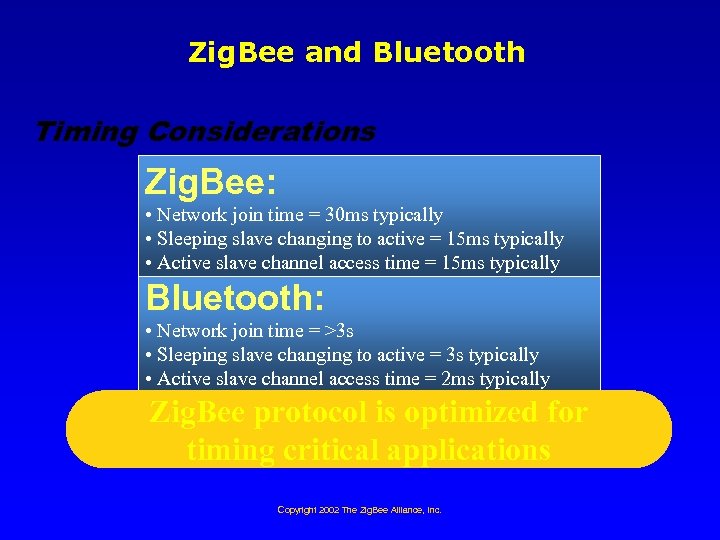 Zig. Bee and Bluetooth Timing Considerations Zig. Bee: • Network join time = 30 ms typically • Sleeping slave changing to active = 15 ms typically • Active slave channel access time = 15 ms typically Bluetooth: • Network join time = >3 s • Sleeping slave changing to active = 3 s typically • Active slave channel access time = 2 ms typically Zig. Bee protocol is optimized for timing critical applications Copyright 2002 The Zig. Bee Alliance, Inc.
Zig. Bee and Bluetooth Timing Considerations Zig. Bee: • Network join time = 30 ms typically • Sleeping slave changing to active = 15 ms typically • Active slave channel access time = 15 ms typically Bluetooth: • Network join time = >3 s • Sleeping slave changing to active = 3 s typically • Active slave channel access time = 2 ms typically Zig. Bee protocol is optimized for timing critical applications Copyright 2002 The Zig. Bee Alliance, Inc.
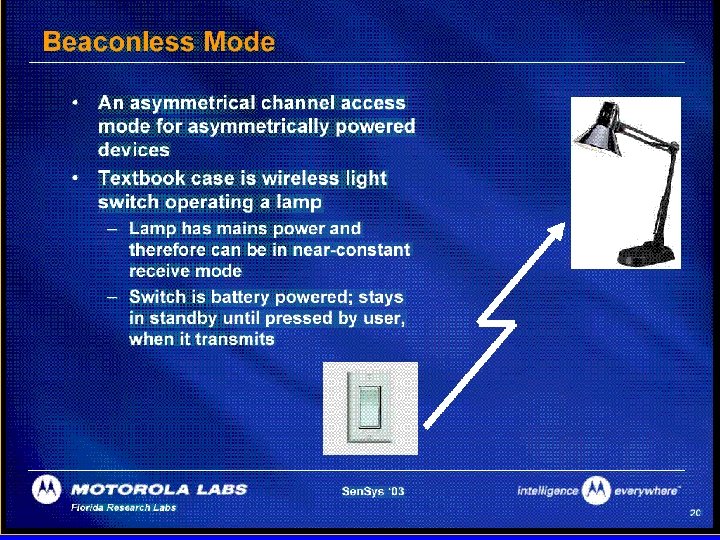
 An Application Example Battery Life & Latency in a Light Switch • Wireless Light switch – – Easy for Builders to Install • A Bluetooth Implementation would: – use the inquiry procedure to find the light each time the switch was operated. • Inquiry procedure – Bluetooth 1. 1 = up to 10 seconds typical – Bluetooth 1. 2 = several seconds even if optimized – Unacceptable latency Copyright 2002 The Zig. Bee Alliance, Inc.
An Application Example Battery Life & Latency in a Light Switch • Wireless Light switch – – Easy for Builders to Install • A Bluetooth Implementation would: – use the inquiry procedure to find the light each time the switch was operated. • Inquiry procedure – Bluetooth 1. 1 = up to 10 seconds typical – Bluetooth 1. 2 = several seconds even if optimized – Unacceptable latency Copyright 2002 The Zig. Bee Alliance, Inc.
 Light switch using Zig. Bee • With DSSS interface, only need to perform CSMA before transmitting – Only 200 µs of latency – Highly efficient use of battery power Zig. Bee offers longer battery life and lower latency than a Bluetooth equivalent. Copyright 2002 The Zig. Bee Alliance, Inc.
Light switch using Zig. Bee • With DSSS interface, only need to perform CSMA before transmitting – Only 200 µs of latency – Highly efficient use of battery power Zig. Bee offers longer battery life and lower latency than a Bluetooth equivalent. Copyright 2002 The Zig. Bee Alliance, Inc.
 Conclusion • Protocols are substantially different and designed for different purposes • 802. 15. 4 designed for low to very low duty cycle static and dynamic environments with many active nodes • Bluetooth designed for high Qo. S, variety of duty cycles, moderate data rates with limited # of active nodes • New entry (2006): Wi. Bree (Nokia), or BT Low Energy – extends the capabilities of the Bluetooth protocol to better enable low-power uses and to better process data intermittently, rather than continuously. • More recently: Near Field Comms – 13. 5 Mhz; for ecommerce (a few centrimeters) Copyright 2002 The Zig. Bee Alliance, Inc.
Conclusion • Protocols are substantially different and designed for different purposes • 802. 15. 4 designed for low to very low duty cycle static and dynamic environments with many active nodes • Bluetooth designed for high Qo. S, variety of duty cycles, moderate data rates with limited # of active nodes • New entry (2006): Wi. Bree (Nokia), or BT Low Energy – extends the capabilities of the Bluetooth protocol to better enable low-power uses and to better process data intermittently, rather than continuously. • More recently: Near Field Comms – 13. 5 Mhz; for ecommerce (a few centrimeters) Copyright 2002 The Zig. Bee Alliance, Inc.
 Zig. Bee and Bluetooth Conclusion • Zig. Bee targets applications not addressable by Bluetooth or any other wireless standard • Zig. Bee and Bluetooth complement for a broader solution Copyright 2002 The Zig. Bee Alliance, Inc.
Zig. Bee and Bluetooth Conclusion • Zig. Bee targets applications not addressable by Bluetooth or any other wireless standard • Zig. Bee and Bluetooth complement for a broader solution Copyright 2002 The Zig. Bee Alliance, Inc.
 Zig. Bee vs BT Low Energy Zig. Bee is LAN networking technology Coverage is a house Meshing capabilities to support essentially an unlimited number of nodes Applications are: sense and control networks Bluetooth Low Energy is a PAN Coverage is a few meters Star topology with limited number of nodes Applications are: body or peripheral networks Copyright 2002 The Zig. Bee Alliance, Inc.
Zig. Bee vs BT Low Energy Zig. Bee is LAN networking technology Coverage is a house Meshing capabilities to support essentially an unlimited number of nodes Applications are: sense and control networks Bluetooth Low Energy is a PAN Coverage is a few meters Star topology with limited number of nodes Applications are: body or peripheral networks Copyright 2002 The Zig. Bee Alliance, Inc.


