bf6e5d8a4083948372e342e9b206389e.ppt
- Количество слайдов: 17
 Csilla Farkas Associate Professor Center for Information Assurance Engineering Dept. of Computer Science and Engineering University of South Carolina farkas@cse. sc. edu http: //www. cse. sc. edu/~farkas Computer Science and Engineering 1
Csilla Farkas Associate Professor Center for Information Assurance Engineering Dept. of Computer Science and Engineering University of South Carolina farkas@cse. sc. edu http: //www. cse. sc. edu/~farkas Computer Science and Engineering 1
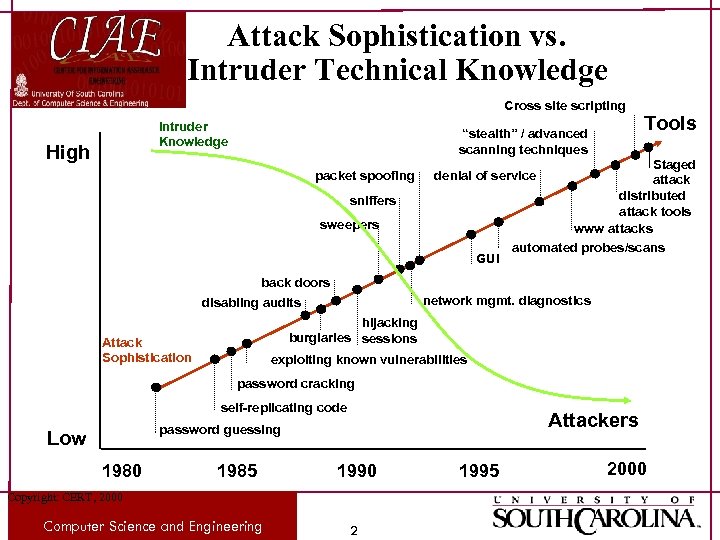 Attack Sophistication vs. Intruder Technical Knowledge Cross site scripting Intruder Knowledge High “stealth” / advanced scanning techniques packet spoofing Tools Staged attack distributed attack tools www attacks automated probes/scans denial of service sniffers sweepers GUI back doors network mgmt. diagnostics disabling audits hijacking burglaries sessions Attack Sophistication exploiting known vulnerabilities password cracking self-replicating code Attackers password guessing Low 1980 1985 1990 Copyright: CERT, 2000 Computer Science and Engineering 2 1995 2000
Attack Sophistication vs. Intruder Technical Knowledge Cross site scripting Intruder Knowledge High “stealth” / advanced scanning techniques packet spoofing Tools Staged attack distributed attack tools www attacks automated probes/scans denial of service sniffers sweepers GUI back doors network mgmt. diagnostics disabling audits hijacking burglaries sessions Attack Sophistication exploiting known vulnerabilities password cracking self-replicating code Attackers password guessing Low 1980 1985 1990 Copyright: CERT, 2000 Computer Science and Engineering 2 1995 2000
 Are we safe? Computer security: – Antivirus, antispyware tools – Automatic updates – Firewall, Intrusion Detection – Phishing, identity theft – Denial of Service attacks –… Computer Science and Engineering 3
Are we safe? Computer security: – Antivirus, antispyware tools – Automatic updates – Firewall, Intrusion Detection – Phishing, identity theft – Denial of Service attacks –… Computer Science and Engineering 3
 What is Droid. Dream? Malware – steals personal info from Android OS Google: March 6, 2011: started to erase Droid. Dream from smart phones Criminals: March 10, 2011: retooled Google’s security update by modifying the Android Market Security Tool to include a Trojan Horse M. Liebowitz, “Hackers hijack Android security update, ” MSN, http: //www. msnbc. msn. com/id/42010396/ns/ technology_and_science-security/ Computer Science and Engineering 4
What is Droid. Dream? Malware – steals personal info from Android OS Google: March 6, 2011: started to erase Droid. Dream from smart phones Criminals: March 10, 2011: retooled Google’s security update by modifying the Android Market Security Tool to include a Trojan Horse M. Liebowitz, “Hackers hijack Android security update, ” MSN, http: //www. msnbc. msn. com/id/42010396/ns/ technology_and_science-security/ Computer Science and Engineering 4
 How about Stuxnet? • Computer worm • Target: Iran's Bushehr nuclear reactor • Built by a very sophisticated and capable attacker R. Mc. Millan, Was Stuxnet Built to Attack Iran's Nuclear Program? , Cnet, http: //www. pcworld. com/businesscenter/article/205827/was_stuxnet_built_ to_attack_irans_nuclear_program. html Computer Science and Engineering 5
How about Stuxnet? • Computer worm • Target: Iran's Bushehr nuclear reactor • Built by a very sophisticated and capable attacker R. Mc. Millan, Was Stuxnet Built to Attack Iran's Nuclear Program? , Cnet, http: //www. pcworld. com/businesscenter/article/205827/was_stuxnet_built_ to_attack_irans_nuclear_program. html Computer Science and Engineering 5
 Top 5 Security Threats for 2011 • • • Threat 1: Mobile Apps Threat 2: Social Network-Based Scams Threat 3: Fake Antivirus Threat 4: PDFs Threat 5: War Games I. Paul, Five Big Security Threats for 2011, PCWorld, http: //www. pcworld. com/article/221780/five_big_security_threat s_for_2011. html Computer Science and Engineering 6
Top 5 Security Threats for 2011 • • • Threat 1: Mobile Apps Threat 2: Social Network-Based Scams Threat 3: Fake Antivirus Threat 4: PDFs Threat 5: War Games I. Paul, Five Big Security Threats for 2011, PCWorld, http: //www. pcworld. com/article/221780/five_big_security_threat s_for_2011. html Computer Science and Engineering 6
 What can we do? Computer Science and Engineering 7
What can we do? Computer Science and Engineering 7
 Information Assurance Courses At USC Computer Science and Engineering 8
Information Assurance Courses At USC Computer Science and Engineering 8
 Courses and Faculty Courses • CSCE 201 – Introduction to Security • CSCE 517 – Computer Crime and Forensics • CSCE 522 – Information Security Principles • CSCE 557 – Introduction to Cryptography • CSCE 548 – Secure Software Construction Faculty • Csilla Farkas • Chin-Tser Huang • Wenyuan Xu Computer Science and Engineering 9
Courses and Faculty Courses • CSCE 201 – Introduction to Security • CSCE 517 – Computer Crime and Forensics • CSCE 522 – Information Security Principles • CSCE 557 – Introduction to Cryptography • CSCE 548 – Secure Software Construction Faculty • Csilla Farkas • Chin-Tser Huang • Wenyuan Xu Computer Science and Engineering 9
 The Information Assurance Scholarship Program (IASP) USC is accredited by NSA as a Center of Academic Excellence in Information Assurance Engineering • US citizen students enrolled full-time at USC are eligible for IA Scholarship offered by the Department of Defense • 2011 Information and Application Materials are available at http: //www. cse. sc. edu/~farkas/iasp 2011/solicitation. htm • 2012 will be poster in Fall 2011 10 Computer Science and Engineering 10
The Information Assurance Scholarship Program (IASP) USC is accredited by NSA as a Center of Academic Excellence in Information Assurance Engineering • US citizen students enrolled full-time at USC are eligible for IA Scholarship offered by the Department of Defense • 2011 Information and Application Materials are available at http: //www. cse. sc. edu/~farkas/iasp 2011/solicitation. htm • 2012 will be poster in Fall 2011 10 Computer Science and Engineering 10
 Important Information • Students selected for the program will receive full scholarships. – $19, 000 + tuition per year for graduate students (GPA > 3. 5) – $14, 000 + tuition per year for undergraduate students (GPA > 3. 2) • Requires the student to agree to – serve one year of service to the Do. D, upon graduation, for each year of scholarship received – in addition to internship during studies • Check the solicitation for eligibility 11 Computer Science and Engineering 11
Important Information • Students selected for the program will receive full scholarships. – $19, 000 + tuition per year for graduate students (GPA > 3. 5) – $14, 000 + tuition per year for undergraduate students (GPA > 3. 2) • Requires the student to agree to – serve one year of service to the Do. D, upon graduation, for each year of scholarship received – in addition to internship during studies • Check the solicitation for eligibility 11 Computer Science and Engineering 11
 IA&S Certificate Graduate Program Admission Requirements • Baccalaureate degree in computer science, computer engineering, or a related field • Work experience as information security professional • Admission requirements for graduate study at the Department of Computer Science and Engineering http: //www. cse. sc. edu/GRADUATE/Admissions. Page. html Industry Certification • Security + • CISSP Computer Science and Engineering 12
IA&S Certificate Graduate Program Admission Requirements • Baccalaureate degree in computer science, computer engineering, or a related field • Work experience as information security professional • Admission requirements for graduate study at the Department of Computer Science and Engineering http: //www. cse. sc. edu/GRADUATE/Admissions. Page. html Industry Certification • Security + • CISSP Computer Science and Engineering 12
 Global IA Workforce Trends • A Frost & Sullivan Market Survey Sponsored by International Information Systems Security Certification Consortium (ISC)2® • Prepared by Robert Ayoub, CISSP, Global Program Director, Information Security • Electronic survey, conducted through a Web-based portal 13 Computer Science and Engineering 13
Global IA Workforce Trends • A Frost & Sullivan Market Survey Sponsored by International Information Systems Security Certification Consortium (ISC)2® • Prepared by Robert Ayoub, CISSP, Global Program Director, Information Security • Electronic survey, conducted through a Web-based portal 13 Computer Science and Engineering 13
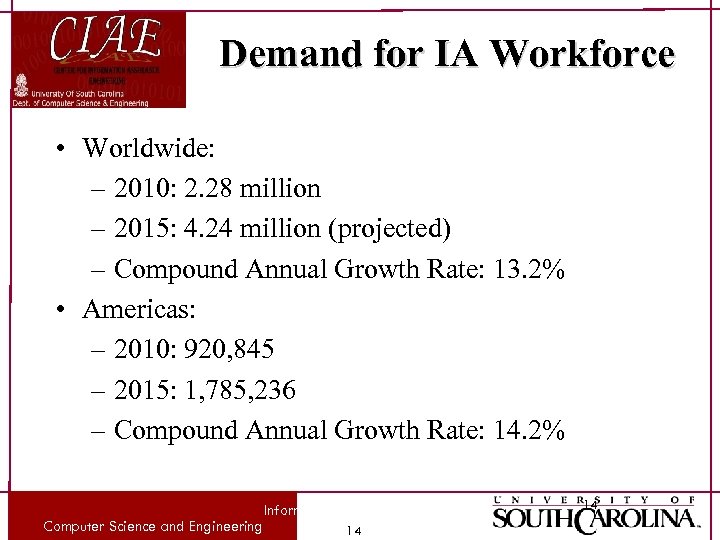 Demand for IA Workforce • Worldwide: – 2010: 2. 28 million – 2015: 4. 24 million (projected) – Compound Annual Growth Rate: 13. 2% • Americas: – 2010: 920, 845 – 2015: 1, 785, 236 – Compound Annual Growth Rate: 14. 2% Computer Science and Engineering Information Warfare - Farkas 14 14
Demand for IA Workforce • Worldwide: – 2010: 2. 28 million – 2015: 4. 24 million (projected) – Compound Annual Growth Rate: 13. 2% • Americas: – 2010: 920, 845 – 2015: 1, 785, 236 – Compound Annual Growth Rate: 14. 2% Computer Science and Engineering Information Warfare - Farkas 14 14
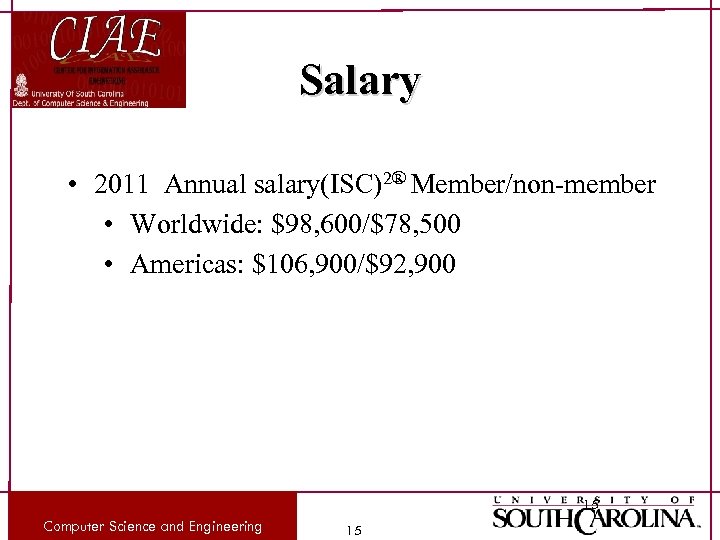 Salary • 2011 Annual salary(ISC)2® Member/non-member • Worldwide: $98, 600/$78, 500 • Americas: $106, 900/$92, 900 15 Computer Science and Engineering 15
Salary • 2011 Annual salary(ISC)2® Member/non-member • Worldwide: $98, 600/$78, 500 • Americas: $106, 900/$92, 900 15 Computer Science and Engineering 15
 IA Jobs • Job market – Civil (Join Information Systems Security Association, ISSA, https: //www. issa. org/ ) – Government (Internship available at USC-UTS, and SC Dept. of Probation, Parole, and Pardon Services) – Military (Internship available at SPAWAR, Charleston) • Education and training requirements (B. S. degree, certification, hands-on experiments) • Salary • FUN Computer Science and Engineering 16
IA Jobs • Job market – Civil (Join Information Systems Security Association, ISSA, https: //www. issa. org/ ) – Government (Internship available at USC-UTS, and SC Dept. of Probation, Parole, and Pardon Services) – Military (Internship available at SPAWAR, Charleston) • Education and training requirements (B. S. degree, certification, hands-on experiments) • Salary • FUN Computer Science and Engineering 16
 Thank you! Computer Science and Engineering 17
Thank you! Computer Science and Engineering 17


