f1d4715dd3db7bfca18f7f21109aa31c.ppt
- Количество слайдов: 71
![CSE 4482: Computer Security Management: Assessment and Forensics Instructor: Suprakash Datta (datta[at]cse. yorku. ca) CSE 4482: Computer Security Management: Assessment and Forensics Instructor: Suprakash Datta (datta[at]cse. yorku. ca)](https://present5.com/presentation/f1d4715dd3db7bfca18f7f21109aa31c/image-1.jpg) CSE 4482: Computer Security Management: Assessment and Forensics Instructor: Suprakash Datta (datta[at]cse. yorku. ca) ext 77875 Lectures: Tues (CB 122), 7– 10 PM Office hours: Wed 3 -5 pm (CSEB 3043), or by appointment. Textbooks: 1. "Management of Information Security", M. E. Whitman, H. J. Mattord, Nelson Education / CENGAGE Learning, 2011, 3 rd Edition 2. "Guide to Computer Forensics and Investigations", B. Nelson, A. Phillips, F. Enfinger, C. Steuart, Nelson Education / CENGAGE Learning, 2010, 4 th Edition. 3/15/2018 1
CSE 4482: Computer Security Management: Assessment and Forensics Instructor: Suprakash Datta (datta[at]cse. yorku. ca) ext 77875 Lectures: Tues (CB 122), 7– 10 PM Office hours: Wed 3 -5 pm (CSEB 3043), or by appointment. Textbooks: 1. "Management of Information Security", M. E. Whitman, H. J. Mattord, Nelson Education / CENGAGE Learning, 2011, 3 rd Edition 2. "Guide to Computer Forensics and Investigations", B. Nelson, A. Phillips, F. Enfinger, C. Steuart, Nelson Education / CENGAGE Learning, 2010, 4 th Edition. 3/15/2018 1
 Expected learning outcomes • Upon completion, you should be able to: – Identify the roles in organizations that are active in the planning process – Explain the principal components of information security system implementation planning in the organizational planning scheme – Differentiate between strategic organizational Info. Sec and specialized contingency planning – Describe the unique considerations and relationships between strategic and contingency plans Many of these slides are adapted from the authors 2 Management of Information Security, 3 rd Edition
Expected learning outcomes • Upon completion, you should be able to: – Identify the roles in organizations that are active in the planning process – Explain the principal components of information security system implementation planning in the organizational planning scheme – Differentiate between strategic organizational Info. Sec and specialized contingency planning – Describe the unique considerations and relationships between strategic and contingency plans Many of these slides are adapted from the authors 2 Management of Information Security, 3 rd Edition
 Planning • • Computing a path towards a goal Resemblance with game-playing Plan for expected and unlikely scenarios Risk assessment and management is a big part of security management planning (ch 8, 9, 10) 3
Planning • • Computing a path towards a goal Resemblance with game-playing Plan for expected and unlikely scenarios Risk assessment and management is a big part of security management planning (ch 8, 9, 10) 3
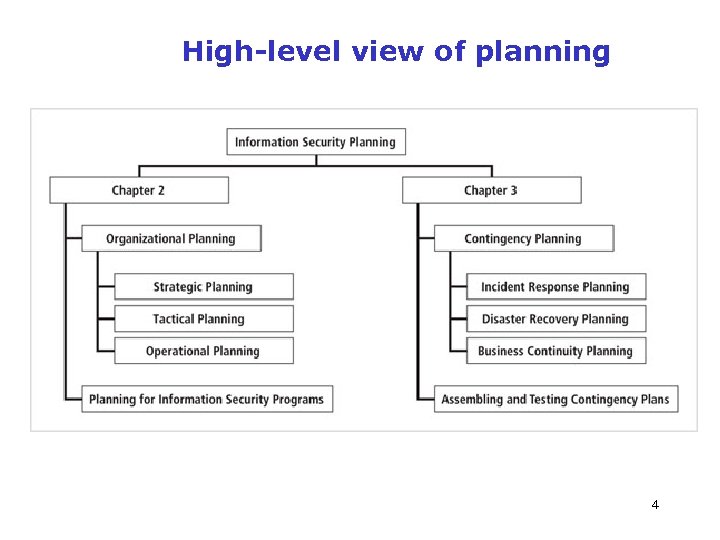 High-level view of planning Introduction Figure 2 -1 Information Security and Planning 4 Management of Information Security, 3 rd Edition Source: Course Technology/Cengage Learning
High-level view of planning Introduction Figure 2 -1 Information Security and Planning 4 Management of Information Security, 3 rd Edition Source: Course Technology/Cengage Learning
 The Role of Planning • Successful organizations utilize planning • Planning involves – Employees – Management – Stockholders – Other outside stakeholders – The physical and technological environment – The political and legal environment – The competitive environment 5 Management of Information Security, 3 rd Edition
The Role of Planning • Successful organizations utilize planning • Planning involves – Employees – Management – Stockholders – Other outside stakeholders – The physical and technological environment – The political and legal environment – The competitive environment 5 Management of Information Security, 3 rd Edition
 The Role of Planning (cont’d. ) • Strategic planning includes: – Vision statement Why are these needed? – Mission statement – Strategy – Coordinated plans for sub units • Knowing how the general organizational planning process works helps in the information security planning process 6 Management of Information Security, 3 rd Edition
The Role of Planning (cont’d. ) • Strategic planning includes: – Vision statement Why are these needed? – Mission statement – Strategy – Coordinated plans for sub units • Knowing how the general organizational planning process works helps in the information security planning process 6 Management of Information Security, 3 rd Edition
 Values Statement • Establishes organizational principles – Makes organization’s conduct standards clear • RWW values commitment, honesty, integrity and social responsibility among its employees, and is committed to providing its services in harmony with its corporate, social, legal and natural environments • The values, vision, and mission statements together provide the foundation for planning 7 Management of Information Security, 3 rd Edition
Values Statement • Establishes organizational principles – Makes organization’s conduct standards clear • RWW values commitment, honesty, integrity and social responsibility among its employees, and is committed to providing its services in harmony with its corporate, social, legal and natural environments • The values, vision, and mission statements together provide the foundation for planning 7 Management of Information Security, 3 rd Edition
 Vision Statement • The vision statement expresses what the organization wants to become • Vision statements should be ambitious(? ) – Random Widget Works will be the preferred manufacturer of choice for every business’s widget equipment needs, with an RWW widget in every machine they use 8 Management of Information Security, 3 rd Edition
Vision Statement • The vision statement expresses what the organization wants to become • Vision statements should be ambitious(? ) – Random Widget Works will be the preferred manufacturer of choice for every business’s widget equipment needs, with an RWW widget in every machine they use 8 Management of Information Security, 3 rd Edition
 Mission Statement • Mission statement – Declares the business of the organization and its intended areas of operations – Explains what the organization does and for whom – Random Widget Works, Inc. designs and manufactures quality widgets and associated equipment and supplies for use in modern business environments 9 Management of Information Security, 3 rd Edition
Mission Statement • Mission statement – Declares the business of the organization and its intended areas of operations – Explains what the organization does and for whom – Random Widget Works, Inc. designs and manufactures quality widgets and associated equipment and supplies for use in modern business environments 9 Management of Information Security, 3 rd Edition
 Figure 2 -2 Microsoft’s Mission and Values Statement 10 Management of Information Security, 3 rd Edition Source: Course Technology/Cengage Learning
Figure 2 -2 Microsoft’s Mission and Values Statement 10 Management of Information Security, 3 rd Edition Source: Course Technology/Cengage Learning
 Strategic Planning (Ch 2) • Strategy is the basis for long-term direction • Strategic planning guides organizational efforts – Focuses resources on clearly defined goals – “… strategic planning is a disciplined effort to produce fundamental decisions and actions that shape and guide what an organization is, what it does, and why it does it, with a focus on the future. ” 11 Management of Information Security, 3 rd Edition
Strategic Planning (Ch 2) • Strategy is the basis for long-term direction • Strategic planning guides organizational efforts – Focuses resources on clearly defined goals – “… strategic planning is a disciplined effort to produce fundamental decisions and actions that shape and guide what an organization is, what it does, and why it does it, with a focus on the future. ” 11 Management of Information Security, 3 rd Edition
 Creating a Strategic Plan • An organization develops a general strategy – Then creates specific strategic plans for major divisions – Each level or division translates those objectives into more specific objectives for the level below • In order to execute this broad strategy executives must define individual managerial responsibilities 12 Management of Information Security, 3 rd Edition
Creating a Strategic Plan • An organization develops a general strategy – Then creates specific strategic plans for major divisions – Each level or division translates those objectives into more specific objectives for the level below • In order to execute this broad strategy executives must define individual managerial responsibilities 12 Management of Information Security, 3 rd Edition
 Top-down vs bottom-up • Top down advantages – Management support, funding – Better coordination and cohesion – accountability • Bottom-up advantages – Comes from technical people 13
Top-down vs bottom-up • Top down advantages – Management support, funding – Better coordination and cohesion – accountability • Bottom-up advantages – Comes from technical people 13
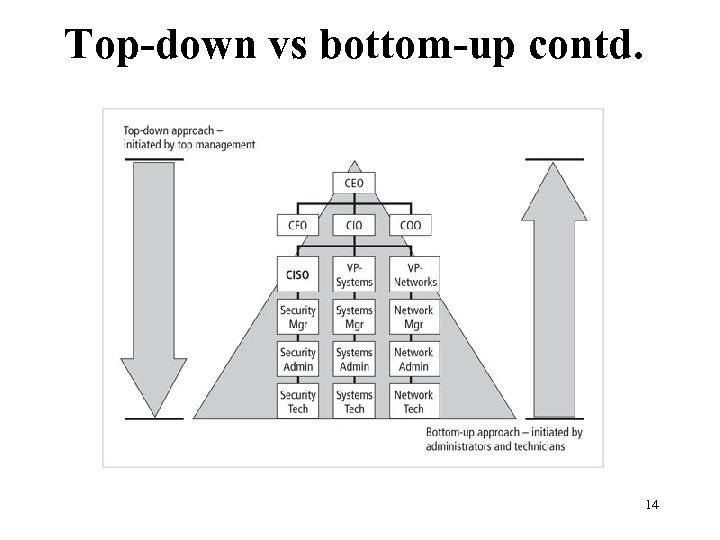 Top-down vs bottom-up contd. Figure 2 -9 Approaches to security implementation 14 Management of Information Security, 3 rd Edition Source: Course Technology/Cengage learning
Top-down vs bottom-up contd. Figure 2 -9 Approaches to security implementation 14 Management of Information Security, 3 rd Edition Source: Course Technology/Cengage learning
 Planning Levels • Strategic goals are translated into tasks • Objectives should be specific, measurable, achievable, reasonably high and time-bound (SMART) • Strategic planning then begins a transformation from general to specific objectives 15 Management of Information Security, 3 rd Edition
Planning Levels • Strategic goals are translated into tasks • Objectives should be specific, measurable, achievable, reasonably high and time-bound (SMART) • Strategic planning then begins a transformation from general to specific objectives 15 Management of Information Security, 3 rd Edition
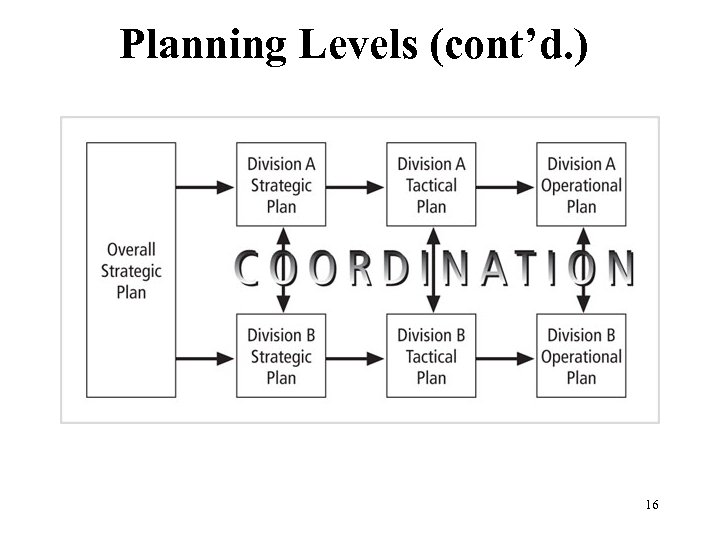 Planning Levels (cont’d. ) Figure 2 -4 Planning Levels 16 Management of Information Security, 3 rd Edition Source: Course Technology/Cengage Learning
Planning Levels (cont’d. ) Figure 2 -4 Planning Levels 16 Management of Information Security, 3 rd Edition Source: Course Technology/Cengage Learning
 Planning Levels (cont’d. ) • Tactical Planning – Has a shorter focus than strategic planning – Usually one to three years – Breaks applicable strategic goals into a series of incremental objectives 17 Management of Information Security, 3 rd Edition
Planning Levels (cont’d. ) • Tactical Planning – Has a shorter focus than strategic planning – Usually one to three years – Breaks applicable strategic goals into a series of incremental objectives 17 Management of Information Security, 3 rd Edition
 Planning Levels (cont’d. ) • Operational Planning – Used by managers and employees to organize the ongoing, day-to-day performance of tasks – Includes clearly identified coordination activities across department boundaries such as: • • Communications requirements Weekly meetings Summaries Progress reports 18 Management of Information Security, 3 rd Edition
Planning Levels (cont’d. ) • Operational Planning – Used by managers and employees to organize the ongoing, day-to-day performance of tasks – Includes clearly identified coordination activities across department boundaries such as: • • Communications requirements Weekly meetings Summaries Progress reports 18 Management of Information Security, 3 rd Edition
 Information Security Governance • Governance of information security is a strategic planning responsibility – Importance has grown in recent years • Information security objectives must be addressed at the highest levels of an organization's management team – To be effective and offer a sustainable approach 19 Management of Information Security, 3 rd Edition
Information Security Governance • Governance of information security is a strategic planning responsibility – Importance has grown in recent years • Information security objectives must be addressed at the highest levels of an organization's management team – To be effective and offer a sustainable approach 19 Management of Information Security, 3 rd Edition
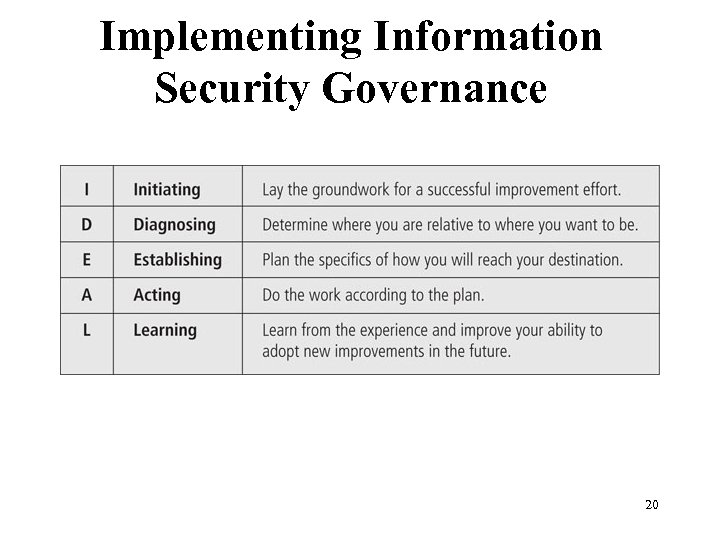 Implementing Information Security Governance Figure 2 -6 General Governance Framework 20 Management of Information Security, 3 rd Edition Source: IDEAL is a service mark of Carnegie Mellon University
Implementing Information Security Governance Figure 2 -6 General Governance Framework 20 Management of Information Security, 3 rd Edition Source: IDEAL is a service mark of Carnegie Mellon University
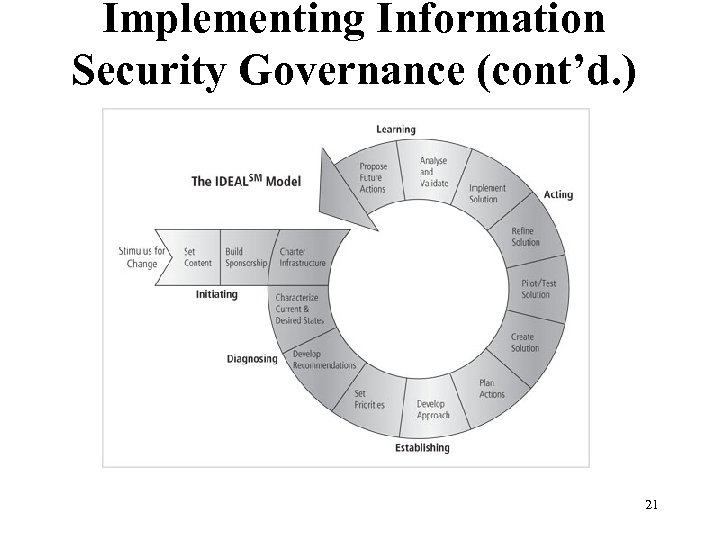 Implementing Information Security Governance (cont’d. ) Figure 2 -7 The IDEAL model governance framework 21 Management of Information Security, 3 rd Edition Source: IDEAL is a service mark of Carnegie Mellon University
Implementing Information Security Governance (cont’d. ) Figure 2 -7 The IDEAL model governance framework 21 Management of Information Security, 3 rd Edition Source: IDEAL is a service mark of Carnegie Mellon University
 Planning For Information Security Implementation • CISO Job Description – Creates a strategic information security plan with a vision for the future of information security – Understands the fundamental business activities and suggests appropriate information security solutions to protect these activities – Develops action plans, schedules, budgets, and status reports 22 Management of Information Security, 3 rd Edition
Planning For Information Security Implementation • CISO Job Description – Creates a strategic information security plan with a vision for the future of information security – Understands the fundamental business activities and suggests appropriate information security solutions to protect these activities – Develops action plans, schedules, budgets, and status reports 22 Management of Information Security, 3 rd Edition
 Security Systems Development Life Cycle • An SDLC is a methodology for the design and implementation of an information system • SDLC-based projects may be initiated by events or planned • At the end of each phase, a review occurs to determine if the project should be continued, discontinued, outsourced, or postponed 23 Management of Information Security, 3 rd Edition
Security Systems Development Life Cycle • An SDLC is a methodology for the design and implementation of an information system • SDLC-based projects may be initiated by events or planned • At the end of each phase, a review occurs to determine if the project should be continued, discontinued, outsourced, or postponed 23 Management of Information Security, 3 rd Edition
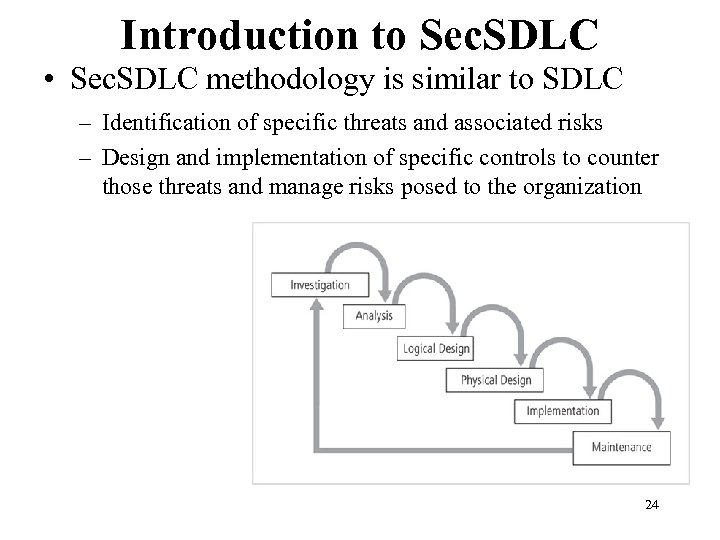 Introduction to Sec. SDLC • Sec. SDLC methodology is similar to SDLC – Identification of specific threats and associated risks – Design and implementation of specific controls to counter those threats and manage risks posed to the organization 24 Management of Information Security, 3 rd Edition
Introduction to Sec. SDLC • Sec. SDLC methodology is similar to SDLC – Identification of specific threats and associated risks – Design and implementation of specific controls to counter those threats and manage risks posed to the organization 24 Management of Information Security, 3 rd Edition
 Introduction to the Sec. SDLC contd. • Investigation – directive from management specifying the process, outcomes, and goals of the project and its budget – Teams assembled to analyze problems, define scope, specify goals and identify constraints – Feasibility analysis: resources, commitment • Analysis – existing security policies and programs, known threats and current controls – relevant legal issues that could affect the design of the security solution 25 Management of Information Security, 3 rd Edition
Introduction to the Sec. SDLC contd. • Investigation – directive from management specifying the process, outcomes, and goals of the project and its budget – Teams assembled to analyze problems, define scope, specify goals and identify constraints – Feasibility analysis: resources, commitment • Analysis – existing security policies and programs, known threats and current controls – relevant legal issues that could affect the design of the security solution 25 Management of Information Security, 3 rd Edition
 Introduction to the Sec. SDLC contd. • Analysis (cont’d. ) – Risk management • identifying, assessing, and evaluating the levels of risk facing the organization, specifically the threats to the information stored and processed by the organization • A threat is an object, person, or other entity that represents a constant danger to an asset 26 Management of Information Security, 3 rd Edition
Introduction to the Sec. SDLC contd. • Analysis (cont’d. ) – Risk management • identifying, assessing, and evaluating the levels of risk facing the organization, specifically the threats to the information stored and processed by the organization • A threat is an object, person, or other entity that represents a constant danger to an asset 26 Management of Information Security, 3 rd Edition
 Risks • An attack –A deliberate act that exploits a vulnerability to achieve the compromise of a controlled system –Accomplished by a threat agent that damages or steals an organization’s information or physical assets • An exploit –A technique or mechanism used to compromise a system • A vulnerability –An identified weakness of a controlled system in which necessary controls that are not present or are no longer effective 27 Management of Information Security, 3 rd Edition
Risks • An attack –A deliberate act that exploits a vulnerability to achieve the compromise of a controlled system –Accomplished by a threat agent that damages or steals an organization’s information or physical assets • An exploit –A technique or mechanism used to compromise a system • A vulnerability –An identified weakness of a controlled system in which necessary controls that are not present or are no longer effective 27 Management of Information Security, 3 rd Edition
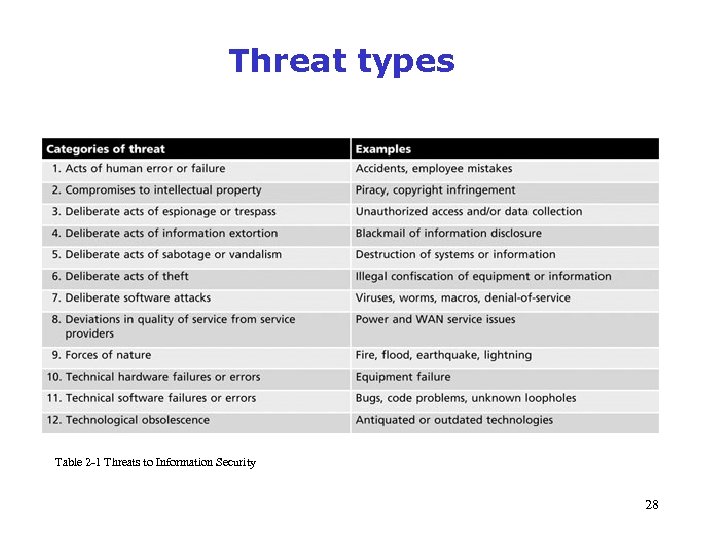 Threat types. ) Table 2 -1 Threats to Information Security 28 Management of Information Security, 3 rd Edition Source: Course Technology/Cengage Learning (adapted from Whitman, 2003)
Threat types. ) Table 2 -1 Threats to Information Security 28 Management of Information Security, 3 rd Edition Source: Course Technology/Cengage Learning (adapted from Whitman, 2003)
 Common Attacks • Malicious code (viruses, worms, Trojan horses, spyware, bots, adware) • Back doors • Password crack (Brute force, Dictionary) • Denial-of-service (Do. S) and distributed denial-of-service (DDo. S) (zombie) • Social engineering (phishing) • Buffer overflow • DNS cache poisoning (pharming) 29
Common Attacks • Malicious code (viruses, worms, Trojan horses, spyware, bots, adware) • Back doors • Password crack (Brute force, Dictionary) • Denial-of-service (Do. S) and distributed denial-of-service (DDo. S) (zombie) • Social engineering (phishing) • Buffer overflow • DNS cache poisoning (pharming) 29
 Common Attacks - contd • • Spoofing (ingress filtering, egress filtering) Man-in-the-middle (TCP hijacking) Spam Mail bombing Sniffer Timing Hoaxes 30
Common Attacks - contd • • Spoofing (ingress filtering, egress filtering) Man-in-the-middle (TCP hijacking) Spam Mail bombing Sniffer Timing Hoaxes 30
 Planning to protect against attacks • Prioritize the risk posed by each category of threat • Identify and assess the value of your information assets – Assign a comparative risk rating or score to each specific information asset • Design and implementation of Sec. SDLC : read on your own 31
Planning to protect against attacks • Prioritize the risk posed by each category of threat • Identify and assess the value of your information assets – Assign a comparative risk rating or score to each specific information asset • Design and implementation of Sec. SDLC : read on your own 31
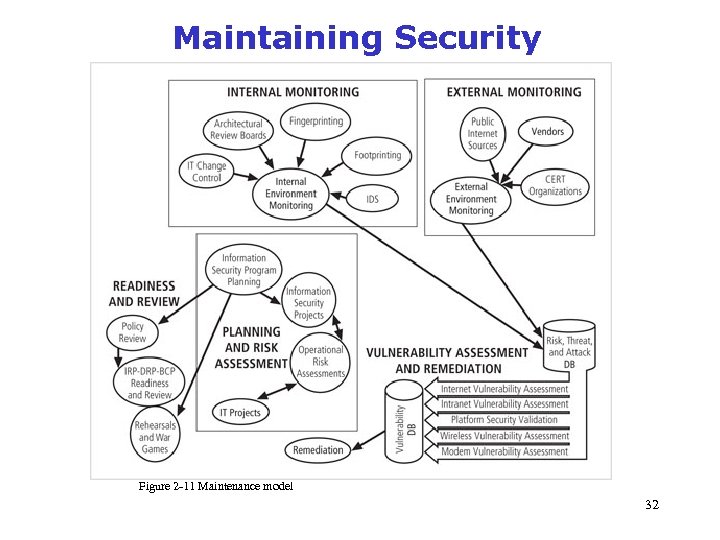 Maintaining Security Figure 2 -11 Maintenance model 32 Source: Course Technology/Cengage learning
Maintaining Security Figure 2 -11 Maintenance model 32 Source: Course Technology/Cengage learning
 Summary • • Introduction Components of organizational planning Information security governance Planning for information security implementation • Introduction to the security systems development life cycle 33 Management of Information Security, 3 rd Edition
Summary • • Introduction Components of organizational planning Information security governance Planning for information security implementation • Introduction to the security systems development life cycle 33 Management of Information Security, 3 rd Edition
 Ch 3: Contingency planning • Plan for unexpected scenarios – When the use of technology is disrupted and business operations come close to a standstill – Procedures are required to permit the organization to continue essential functions if information technology support is interrupted – Over 40% of businesses that don't have a disaster plan go out of business after a major loss • What scenarios should a company plan for? 34 Management of Information Security, 3 rd Edition
Ch 3: Contingency planning • Plan for unexpected scenarios – When the use of technology is disrupted and business operations come close to a standstill – Procedures are required to permit the organization to continue essential functions if information technology support is interrupted – Over 40% of businesses that don't have a disaster plan go out of business after a major loss • What scenarios should a company plan for? 34 Management of Information Security, 3 rd Edition
 Objectives • Upon completion of this material, you should be able to: – Recognize the need for contingency planning – Describe the major components of contingency planning – Create a simple set of contingency plans, using business impact analysis – Prepare and execute a test of contingency plans – Explain the combined contingency plan approach 35 Management of Information Security, 3 rd ed.
Objectives • Upon completion of this material, you should be able to: – Recognize the need for contingency planning – Describe the major components of contingency planning – Create a simple set of contingency plans, using business impact analysis – Prepare and execute a test of contingency plans – Explain the combined contingency plan approach 35 Management of Information Security, 3 rd ed.
 Contingency Planning fundamentals • Contingency planning (CP) – The overall planning for unexpected events – preparing for, detecting, reacting to, and recovering from events that threaten the security of information resources and assets • Main goal – The restoration to normal modes of operation with minimum cost and disruption to normal business activities after an unexpected event 36 Management of Information Security, 3 rd ed.
Contingency Planning fundamentals • Contingency planning (CP) – The overall planning for unexpected events – preparing for, detecting, reacting to, and recovering from events that threaten the security of information resources and assets • Main goal – The restoration to normal modes of operation with minimum cost and disruption to normal business activities after an unexpected event 36 Management of Information Security, 3 rd ed.
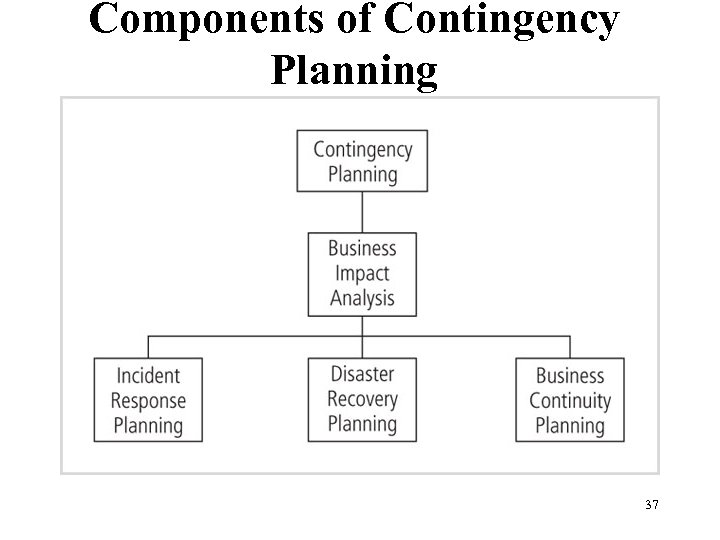 Components of Contingency Planning Figure 3 -1 Contingency planning hierarchies Management of Information Security, 3 rd ed. 37 Source: Course Technology/Cengage Learning
Components of Contingency Planning Figure 3 -1 Contingency planning hierarchies Management of Information Security, 3 rd ed. 37 Source: Course Technology/Cengage Learning
 Contingency Planning • Incident response planning (IRP) – immediate response • Disaster recovery planning (DRP) – restoring operations at the primary site after disasters • Business continuity planning (BCP) – establishment of operations at an alternate site • To ensure continuity planners should – Identify the mission- or business-critical functions and the resources that support them – Select contingency planning strategies – Implement the selected strategy – Test and revise contingency plans 38 Management of Information Security, 3 rd ed.
Contingency Planning • Incident response planning (IRP) – immediate response • Disaster recovery planning (DRP) – restoring operations at the primary site after disasters • Business continuity planning (BCP) – establishment of operations at an alternate site • To ensure continuity planners should – Identify the mission- or business-critical functions and the resources that support them – Select contingency planning strategies – Implement the selected strategy – Test and revise contingency plans 38 Management of Information Security, 3 rd ed.
 Contingency Planning - contd • the contingency planning policy statement Provides the authority and guidance necessary to develop an effective contingency plan • Conduct the BIA identify and prioritize critical IT systems and components • Identify preventive controls Measures taken to reduce the effects of system disruptions can increase system availability and reduce contingency life cycle costs • Develop recovery strategies – Ensure that the system may be recovered quickly and effectively following a disruption 39 Management of Information Security, 3 rd ed.
Contingency Planning - contd • the contingency planning policy statement Provides the authority and guidance necessary to develop an effective contingency plan • Conduct the BIA identify and prioritize critical IT systems and components • Identify preventive controls Measures taken to reduce the effects of system disruptions can increase system availability and reduce contingency life cycle costs • Develop recovery strategies – Ensure that the system may be recovered quickly and effectively following a disruption 39 Management of Information Security, 3 rd ed.
 Contingency Planning - contd • Develop an IT contingency plan – detailed guidance and procedures for restoring a damaged system • Plan testing, training, and exercises – Testing the plan identifies planning gaps – Training prepares recovery personnel for plan activation – Both activities improve plan effectiveness and overall agency preparedness • Plan maintenance – The plan should be updated regularly to remain current with system enhancements 40 Management of Information Security, 3 rd ed.
Contingency Planning - contd • Develop an IT contingency plan – detailed guidance and procedures for restoring a damaged system • Plan testing, training, and exercises – Testing the plan identifies planning gaps – Training prepares recovery personnel for plan activation – Both activities improve plan effectiveness and overall agency preparedness • Plan maintenance – The plan should be updated regularly to remain current with system enhancements 40 Management of Information Security, 3 rd ed.
 Business Impact Analysis (BIA) • Provides the CP team with information about systems and the threats they face – A crucial component of the initial planning stages – Provides detailed scenarios of each potential attack’s impact • BIA is not risk management (which focuses on identifying threats, vulnerabilities, and attacks to determine controls) • BIA assumes controls have been bypassed or are ineffective, and attack was successful 41 Management of Information Security, 3 rd ed.
Business Impact Analysis (BIA) • Provides the CP team with information about systems and the threats they face – A crucial component of the initial planning stages – Provides detailed scenarios of each potential attack’s impact • BIA is not risk management (which focuses on identifying threats, vulnerabilities, and attacks to determine controls) • BIA assumes controls have been bypassed or are ineffective, and attack was successful 41 Management of Information Security, 3 rd ed.
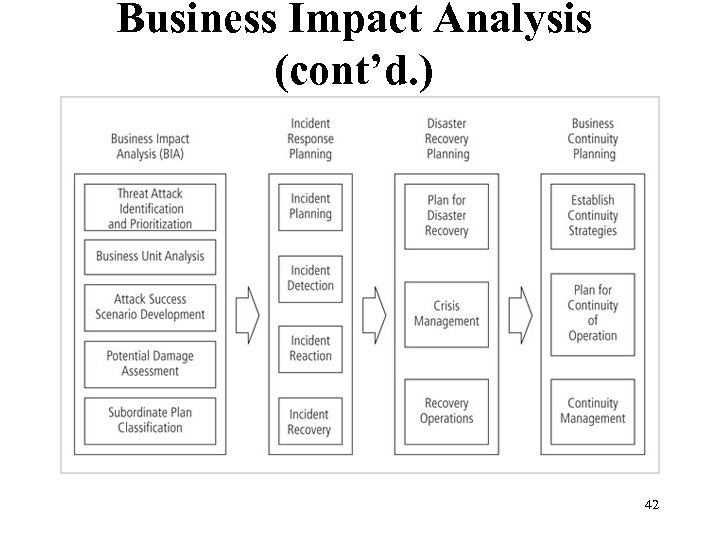 Business Impact Analysis (cont’d. ) Figure 3 -2 Major tasks in contingency planning 42 Management of Information Security, 3 rd ed. Source: Course Technology/Cengage Learning
Business Impact Analysis (cont’d. ) Figure 3 -2 Major tasks in contingency planning 42 Management of Information Security, 3 rd ed. Source: Course Technology/Cengage Learning
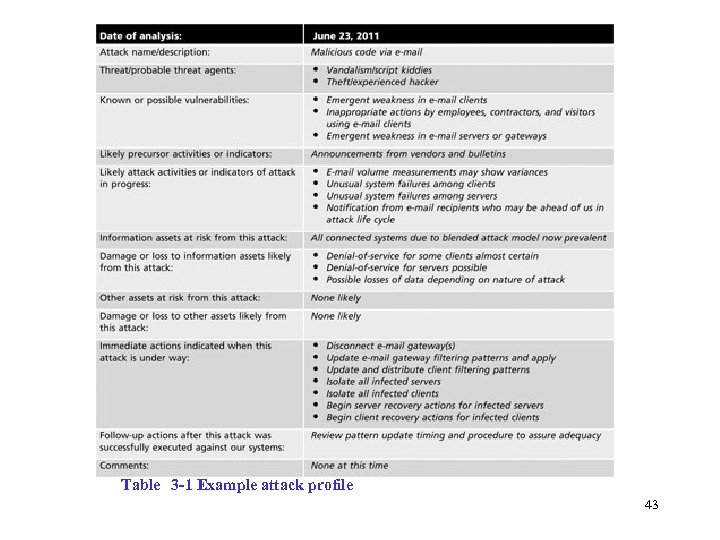 Table 3 -1 Example attack profile 43 Management of Information Security 3 rd ed. Source: Course Technology/Cengage Learning
Table 3 -1 Example attack profile 43 Management of Information Security 3 rd ed. Source: Course Technology/Cengage Learning
 Business Impact Analysis • Create a series of scenarios depicting impact of successful attack on each functional area • Attack profiles should include scenarios depicting typical attack including: – Methodology – Indicators – Broad consequences • List outcomes (Best case, worst case, and most likely) • Estimate the cost of each of these outcomes – By preparing an attack scenario end case – Allows identification of what must be done to recover from each possible case 44 Management of Information Security, 3 rd ed.
Business Impact Analysis • Create a series of scenarios depicting impact of successful attack on each functional area • Attack profiles should include scenarios depicting typical attack including: – Methodology – Indicators – Broad consequences • List outcomes (Best case, worst case, and most likely) • Estimate the cost of each of these outcomes – By preparing an attack scenario end case – Allows identification of what must be done to recover from each possible case 44 Management of Information Security, 3 rd ed.
 Incident Response Plan • A detailed set of processes and procedures that anticipate, detect, and mitigate the impact of an unexpected event that might compromise information resources and assets – Procedures commence when an incident is detected • When a threat becomes a valid attack, it is classified as an information security incident if: – It is directed against information assets – It has a realistic chance of success – It threatens the confidentiality, integrity, or availability of information assets • Incident response is a reactive measure, not a preventative one Management of Information Security, 3 rd ed. 45
Incident Response Plan • A detailed set of processes and procedures that anticipate, detect, and mitigate the impact of an unexpected event that might compromise information resources and assets – Procedures commence when an incident is detected • When a threat becomes a valid attack, it is classified as an information security incident if: – It is directed against information assets – It has a realistic chance of success – It threatens the confidentiality, integrity, or availability of information assets • Incident response is a reactive measure, not a preventative one Management of Information Security, 3 rd ed. 45
 Incident Response Plan details • Develop procedures for tasks that must be performed in advance of the incident – Details of data backup schedules – Disaster recovery preparation – Training schedules – Testing plans – Copies of service agreements – Business continuity plans 46 Management of Information Security, 3 rd ed.
Incident Response Plan details • Develop procedures for tasks that must be performed in advance of the incident – Details of data backup schedules – Disaster recovery preparation – Training schedules – Testing plans – Copies of service agreements – Business continuity plans 46 Management of Information Security, 3 rd ed.
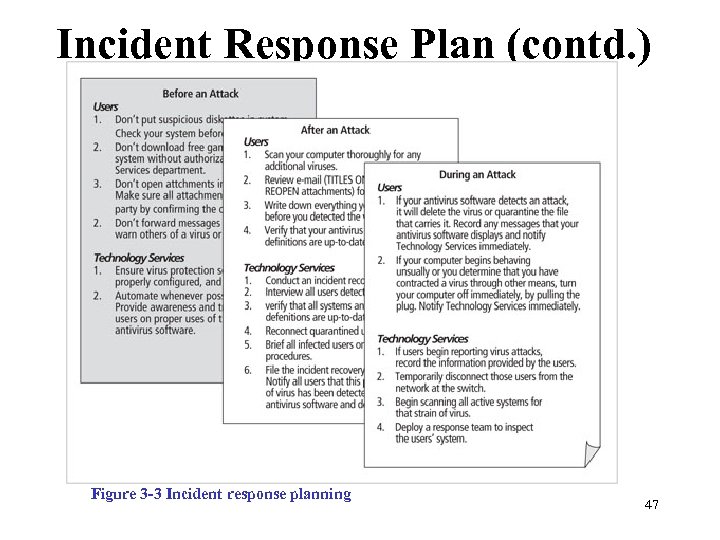 Incident Response Plan (contd. ) Figure 3 -3 Incident response planning Management of Information Security, 3 rd ed. 47 Source: Course Technology/Cengage Learning
Incident Response Plan (contd. ) Figure 3 -3 Incident response planning Management of Information Security, 3 rd ed. 47 Source: Course Technology/Cengage Learning
 Incident Response Plan (contd. ) • Incident classification – Determine whether an event is an actual incident – May be challenging – Uses initial reports from end users, intrusion detection systems, host- and network-based virus detection software, and systems administrators – Careful training allows everyone to relay vital information to the IR team 48 Management of Information Security, 3 rd ed.
Incident Response Plan (contd. ) • Incident classification – Determine whether an event is an actual incident – May be challenging – Uses initial reports from end users, intrusion detection systems, host- and network-based virus detection software, and systems administrators – Careful training allows everyone to relay vital information to the IR team 48 Management of Information Security, 3 rd ed.
 Incident Response Plan (contd. ) • Possible indicators – – Presence of unfamiliar files Presence or execution of unknown programs or processes Unusual consumption of computing resources Unusual system crashes • Probable indicators – – Activities at unexpected times Presence of new accounts Reported attacks Notification from IDS • Definite indicators – – – Use of dormant accounts Changes to logs Presence of hacker tools Notifications by partner or peer Notification by hacker Management of Information Security, 3 rd ed. 49
Incident Response Plan (contd. ) • Possible indicators – – Presence of unfamiliar files Presence or execution of unknown programs or processes Unusual consumption of computing resources Unusual system crashes • Probable indicators – – Activities at unexpected times Presence of new accounts Reported attacks Notification from IDS • Definite indicators – – – Use of dormant accounts Changes to logs Presence of hacker tools Notifications by partner or peer Notification by hacker Management of Information Security, 3 rd ed. 49
 Incident Response Plan (contd. ) • Occurrences of actual incidents – When these occur, the corresponding IR must be immediately activated • • • Loss of availability Loss of integrity Loss of confidentiality Violation of policy Violation of law • The essential task of IR is to stop the incident or contain its impact • Incident containment strategies focus – Stopping the incident – Recovering control of the systems 50 Management of Information Security, 3 rd ed.
Incident Response Plan (contd. ) • Occurrences of actual incidents – When these occur, the corresponding IR must be immediately activated • • • Loss of availability Loss of integrity Loss of confidentiality Violation of policy Violation of law • The essential task of IR is to stop the incident or contain its impact • Incident containment strategies focus – Stopping the incident – Recovering control of the systems 50 Management of Information Security, 3 rd ed.
 Containment strategies • Disconnect the affected communication circuits • Dynamically apply filtering rules to limit certain types of network access • Disabling compromised user accounts • Reconfiguring firewalls to block the problem traffic • Temporarily disabling the compromised process or service • Taking down the conduit application or server • Stopping all computers and network devices 51 Management of Information Security, 3 rd ed.
Containment strategies • Disconnect the affected communication circuits • Dynamically apply filtering rules to limit certain types of network access • Disabling compromised user accounts • Reconfiguring firewalls to block the problem traffic • Temporarily disabling the compromised process or service • Taking down the conduit application or server • Stopping all computers and network devices 51 Management of Information Security, 3 rd ed.
 Containment strategies (contd. ) • An incident may increase in scope or severity to the point that the IRP cannot adequately contain the incident – Each organization will have to determine, during the business impact analysis, the point at which the incident becomes a disaster • The organization must also document when to involve outside response 52 Management of Information Security, 3 rd ed.
Containment strategies (contd. ) • An incident may increase in scope or severity to the point that the IRP cannot adequately contain the incident – Each organization will have to determine, during the business impact analysis, the point at which the incident becomes a disaster • The organization must also document when to involve outside response 52 Management of Information Security, 3 rd ed.
 Containment strategies (contd. ) • Once contained and system control regained, incident recovery can begin – The IR team must assess the full extent of the damage in order to determine what must be done to restore the systems • Incident damage assessment – Determination of the scope of the breach of confidentiality, integrity, and availability of information and information assets • Those who document the damage must be trained to collect and preserve evidence, in case the incident is part of a crime or results in a civil action 53 Management of Information Security, 3 rd ed.
Containment strategies (contd. ) • Once contained and system control regained, incident recovery can begin – The IR team must assess the full extent of the damage in order to determine what must be done to restore the systems • Incident damage assessment – Determination of the scope of the breach of confidentiality, integrity, and availability of information and information assets • Those who document the damage must be trained to collect and preserve evidence, in case the incident is part of a crime or results in a civil action 53 Management of Information Security, 3 rd ed.
 Recovery process – Identify the vulnerabilities that allowed the incident to occur and spread and resolve them – Address the safeguards that failed to stop or limit the incident, or were missing from the system; install, replace or upgrade them – Evaluate existing monitoring capabilities, install new monitoring capabilities – Restore the data from backups as needed – Restore the services and processes in use where compromised (and interrupted) services and processes must be examined, cleaned, and then restored – Continuously monitor the system – Restore the confidence of the members of the organization’s communities of interest 54 Management of Information Security, 3 rd ed.
Recovery process – Identify the vulnerabilities that allowed the incident to occur and spread and resolve them – Address the safeguards that failed to stop or limit the incident, or were missing from the system; install, replace or upgrade them – Evaluate existing monitoring capabilities, install new monitoring capabilities – Restore the data from backups as needed – Restore the services and processes in use where compromised (and interrupted) services and processes must be examined, cleaned, and then restored – Continuously monitor the system – Restore the confidence of the members of the organization’s communities of interest 54 Management of Information Security, 3 rd ed.
 Recovery process (contd. ) • Before returning to routine duties, the IR team must conduct an after-action review (AAR) – A detailed examination of the events that occurred – All team members review their actions during the incident and identify areas where the IR plan worked, didn’t work, or should improve • When an incident violates civil or criminal law, it is the organization’s responsibility to notify the proper authorities – Selecting the appropriate law enforcement agency depends on the type of crime committed: Federal, State, or local 55 Management of Information Security, 3 rd ed.
Recovery process (contd. ) • Before returning to routine duties, the IR team must conduct an after-action review (AAR) – A detailed examination of the events that occurred – All team members review their actions during the incident and identify areas where the IR plan worked, didn’t work, or should improve • When an incident violates civil or criminal law, it is the organization’s responsibility to notify the proper authorities – Selecting the appropriate law enforcement agency depends on the type of crime committed: Federal, State, or local 55 Management of Information Security, 3 rd ed.
 Disaster Recovery Plan • The preparation for and recovery from a disaster, whether natural or man made • In general, an incident is a disaster when: – The organization is unable to contain or control the impact of an incident, or – The level of damage or destruction from an incident is so severe the organization is unable to quickly recover • The key role of a DRP is defining how to reestablish operations at the location where the organization is usually located 56 Management of Information Security, 3 rd ed.
Disaster Recovery Plan • The preparation for and recovery from a disaster, whether natural or man made • In general, an incident is a disaster when: – The organization is unable to contain or control the impact of an incident, or – The level of damage or destruction from an incident is so severe the organization is unable to quickly recover • The key role of a DRP is defining how to reestablish operations at the location where the organization is usually located 56 Management of Information Security, 3 rd ed.
 Disaster Recovery Plan (cont’d. ) • Key points in the DRP – Clear delegation of roles and responsibilities – Execution of the alert roster and notification of key personnel – Clear establishment of priorities – Documentation of the disaster – Action steps to mitigate the impact – Alternative implementations for the various systems components 57 Management of Information Security, 3 rd ed.
Disaster Recovery Plan (cont’d. ) • Key points in the DRP – Clear delegation of roles and responsibilities – Execution of the alert roster and notification of key personnel – Clear establishment of priorities – Documentation of the disaster – Action steps to mitigate the impact – Alternative implementations for the various systems components 57 Management of Information Security, 3 rd ed.
 Disaster Recovery Plan (cont’d. ) • classify disasters as – natural disasters vs man-made disasters – Rapid onset disasters vs slow onset disasters • Scenario development and impact analysis – Used to categorize the level of threat of each potential disaster • DRP must be tested regularly 58 Management of Information Security, 3 rd ed.
Disaster Recovery Plan (cont’d. ) • classify disasters as – natural disasters vs man-made disasters – Rapid onset disasters vs slow onset disasters • Scenario development and impact analysis – Used to categorize the level of threat of each potential disaster • DRP must be tested regularly 58 Management of Information Security, 3 rd ed.
 Business Continuity Plan • Ensures critical business functions can continue in a disaster • Managed by CEO of the organization • Activated and executed concurrently with the DRP when needed – While BCP reestablishes critical functions at alternate site, DRP focuses on reestablishment at the primary site • Relies on identification of critical business functions and the resources to support them 59 Management of Information Security, 3 rd ed.
Business Continuity Plan • Ensures critical business functions can continue in a disaster • Managed by CEO of the organization • Activated and executed concurrently with the DRP when needed – While BCP reestablishes critical functions at alternate site, DRP focuses on reestablishment at the primary site • Relies on identification of critical business functions and the resources to support them 59 Management of Information Security, 3 rd ed.
 Business Continuity Strategies • Exclusive-use options: hot, warm and cold sites • Hot Sites: Fully configured computer facility with all services • Warm Sites: Like hot site, but software applications not kept fully prepared • Cold Sites: Only rudimentary services and facilities kept ready • Shared-use options: timeshare, service bureaus, mutual agreements • Determining factor is usually cost 60 Management of Information Security, 3 rd ed.
Business Continuity Strategies • Exclusive-use options: hot, warm and cold sites • Hot Sites: Fully configured computer facility with all services • Warm Sites: Like hot site, but software applications not kept fully prepared • Cold Sites: Only rudimentary services and facilities kept ready • Shared-use options: timeshare, service bureaus, mutual agreements • Determining factor is usually cost 60 Management of Information Security, 3 rd ed.
 Business Continuity Strategies - 2 • Timeshares – Like an exclusive use site but leased • Service bureaus – Agency that provides physical facilities • Mutual agreements – Contract between two organizations to assist • Specialized alternatives – Rolling mobile site – Externally stored resources 61 Management of Information Security, 3 rd ed.
Business Continuity Strategies - 2 • Timeshares – Like an exclusive use site but leased • Service bureaus – Agency that provides physical facilities • Mutual agreements – Contract between two organizations to assist • Specialized alternatives – Rolling mobile site – Externally stored resources 61 Management of Information Security, 3 rd ed.
 Data recovery • To get any BCP site running quickly organization must be able to recover data • Options include: – Electronic vaulting • Bulk batch-transfer of data to an off-site facility – Remote journaling • Transfer of live transactions to an off-site facility – Database shadowing • Storage of duplicate online transaction data Each option adds different risks 62 Management of Information Security, 3 rd ed.
Data recovery • To get any BCP site running quickly organization must be able to recover data • Options include: – Electronic vaulting • Bulk batch-transfer of data to an off-site facility – Remote journaling • Transfer of live transactions to an off-site facility – Database shadowing • Storage of duplicate online transaction data Each option adds different risks 62 Management of Information Security, 3 rd ed.
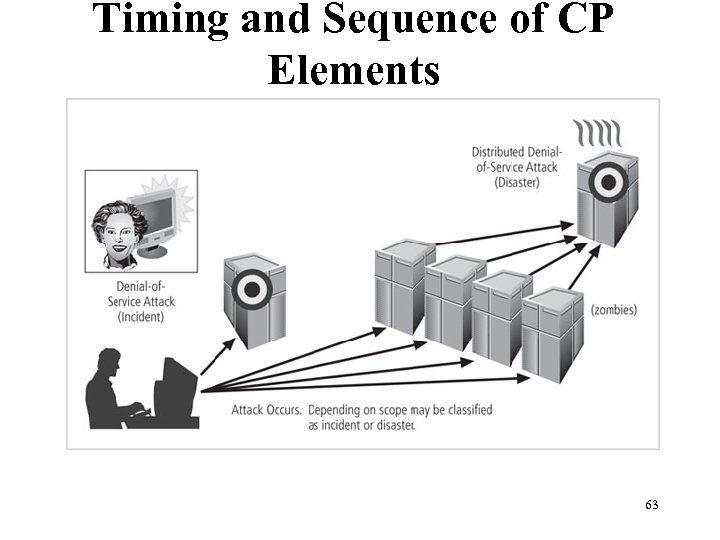 Timing and Sequence of CP Elements Figure 3 -4 Incident response and disaster recovery 63 Management of Information Security, 3 rd ed. Source: Course Technology/Cengage Learning
Timing and Sequence of CP Elements Figure 3 -4 Incident response and disaster recovery 63 Management of Information Security, 3 rd ed. Source: Course Technology/Cengage Learning
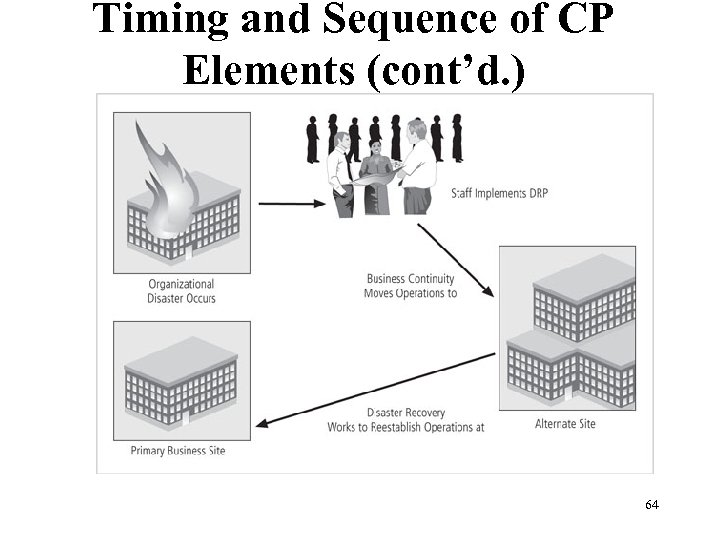 Timing and Sequence of CP Elements (cont’d. ) Figure 3 -5 Disaster recovery and business continuity planning Management of Information Security, 3 rd ed. 64 Source: Course Technology/Cengage Learning
Timing and Sequence of CP Elements (cont’d. ) Figure 3 -5 Disaster recovery and business continuity planning Management of Information Security, 3 rd ed. 64 Source: Course Technology/Cengage Learning
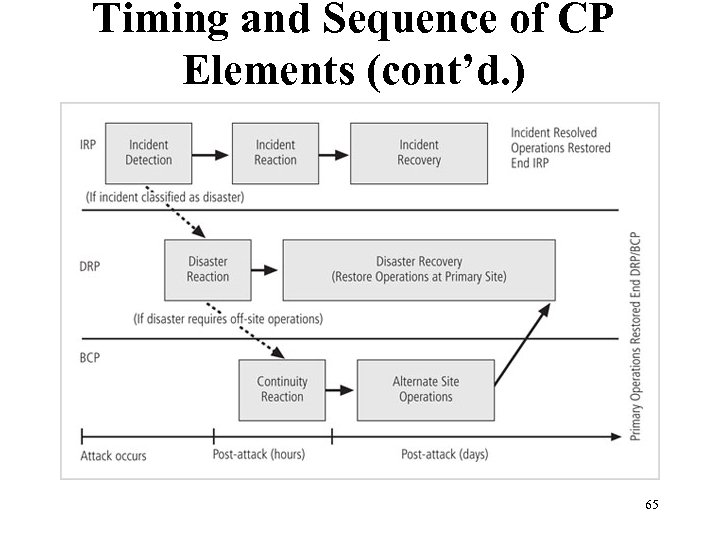 Timing and Sequence of CP Elements (cont’d. ) Figure 3 -6 Contingency planning implementation timeline Management of Information Security, 3 rd ed. 65 Source: Course Technology/Cengage Learning
Timing and Sequence of CP Elements (cont’d. ) Figure 3 -6 Contingency planning implementation timeline Management of Information Security, 3 rd ed. 65 Source: Course Technology/Cengage Learning
 Crisis Management • A set of focused steps that deal primarily with the people involved during and after a disaster • Crisis management team actions – Supporting personnel and their loved ones during the crisis – Determining the event's impact on normal business operations – Making a disaster declaration – Keeping the public informed about the event – Communicating with outside parties • Key tasks of the crisis management team – Verifying personnel status – Activating the alert roster 66 Management of Information Security, 3 rd ed.
Crisis Management • A set of focused steps that deal primarily with the people involved during and after a disaster • Crisis management team actions – Supporting personnel and their loved ones during the crisis – Determining the event's impact on normal business operations – Making a disaster declaration – Keeping the public informed about the event – Communicating with outside parties • Key tasks of the crisis management team – Verifying personnel status – Activating the alert roster 66 Management of Information Security, 3 rd ed.
 Business Resumption Planning • Because the DRP and BCP are closely related, most organizations prepare them concurrently • Components of a simple disaster recovery plan – – – – Name of agency, Date of completion Agency staff to be called in the event of a disaster Emergency services to be called (if needed) Locations of in-house emergency equipment, supplies Sources of off-site equipment and supplies Salvage priority list Agency disaster recovery procedures Follow-up assessment 67 Management of Information Security, 3 rd ed.
Business Resumption Planning • Because the DRP and BCP are closely related, most organizations prepare them concurrently • Components of a simple disaster recovery plan – – – – Name of agency, Date of completion Agency staff to be called in the event of a disaster Emergency services to be called (if needed) Locations of in-house emergency equipment, supplies Sources of off-site equipment and supplies Salvage priority list Agency disaster recovery procedures Follow-up assessment 67 Management of Information Security, 3 rd ed.
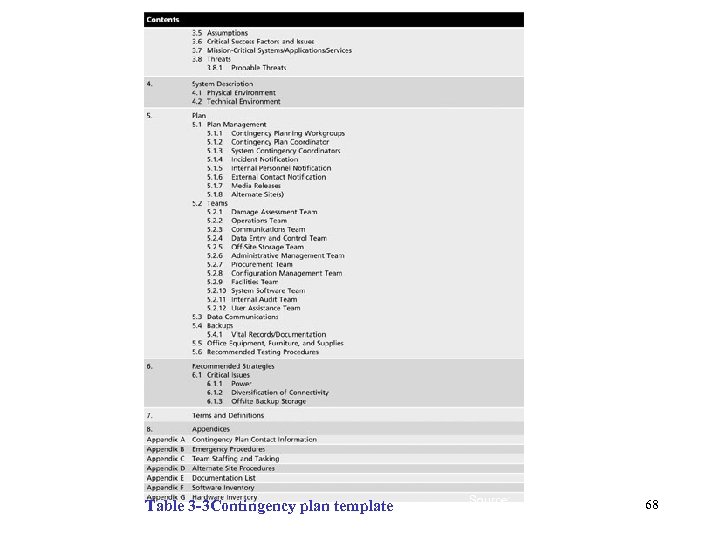 Table 3 -3 Contingency plan template Management of Information Security, 3 rd ed. Source: 68 (http: //csrc. nist. gov/fasp/FASPDocs/contingen cy-plan/contingencyplan-template. doc)
Table 3 -3 Contingency plan template Management of Information Security, 3 rd ed. Source: 68 (http: //csrc. nist. gov/fasp/FASPDocs/contingen cy-plan/contingencyplan-template. doc)
 Testing Contingency Plans • Problems are identified during testing – Improvements can be made, resulting in a reliable plan • Contingency plan testing strategies – Desk check – Structured walkthrough – Simulation – Parallel testing – Full interruption testing 69 Management of Information Security, 3 rd ed.
Testing Contingency Plans • Problems are identified during testing – Improvements can be made, resulting in a reliable plan • Contingency plan testing strategies – Desk check – Structured walkthrough – Simulation – Parallel testing – Full interruption testing 69 Management of Information Security, 3 rd ed.
 Contingency Planning: Final Thoughts • Iteration results in improvement • A formal implementation of this methodology is a process known as continuous process improvement (CPI) • Each time the plan is rehearsed it should be improved • Constant evaluation and improvement lead to an improved outcome 70 Management of Information Security, 3 rd ed.
Contingency Planning: Final Thoughts • Iteration results in improvement • A formal implementation of this methodology is a process known as continuous process improvement (CPI) • Each time the plan is rehearsed it should be improved • Constant evaluation and improvement lead to an improved outcome 70 Management of Information Security, 3 rd ed.
 Summary • • • Introduction What Is Contingency Planning? Components of Contingency Planning Putting a Contingency Plan Together Testing Contingency Plans A Single Continuity Plan 71 Management of Information Security, 3 rd ed.
Summary • • • Introduction What Is Contingency Planning? Components of Contingency Planning Putting a Contingency Plan Together Testing Contingency Plans A Single Continuity Plan 71 Management of Information Security, 3 rd ed.


