40e746d252678498f16d14a768579f91.ppt
- Количество слайдов: 44

CSCI E-170 L 06: Crypto 1 October 25, 2004 MD 5 SHA-1 HMAC

Administrivia • HW 3 returned. • AOL Survey

Message Digests • Message Digests make a “fingerprint” of a file. • Input: 1 -264 bytes • Output: 128, 160, 256 or more bits

Message Digests Constitution of the United States of America (In Convention, September 17, 1787) Preamble We the people of the United States, in order to form a more perfect union, establish justice, insure domestic tranquility, provide for the common defense, promote the general welfare, and secure the blessing of liberty to ourselves and our posterity, do ordain and establish the Constitution of the United States of America. Article I. Section 1. All legislative powers herein granted shall be vested in a Congress of the United States, which shall consist of a Senate and a House of Representatives. . bab 1 c 005 bad 1 ac 7 d 58 d 54 d 0 e 5 f 3 f ff 3881 c 932 e 7591 e 674 e 2 d 9 d 772817746 e 8 d 983 f

Computing Hash Functions % ls -l total 58 -rw-r--r-- 1 simsong wheel 47990 Jul 13 1990 Constitution -rw-r--r-- 1 simsong wheel 9949 Jul 13 1990 Declaration % md 5 Constitution MD 5 (Constitution) = bab 1 c 005 bad 1 ac 7 d 58 d 54 d 0 e 5 f 3 f % sha 1 Constitution SHA 1 (Constitution) = ff 3881 c 932 e 7591 e 674 e 2 d 9 d 772817746 e 8 d 983 f % openssl sha 1 < Constitution ff 3881 c 932 e 7591 e 674 e 2 d 9 d 772817746 e 8 d 983 f % openssl sha 1 Constitution SHA 1(Constitution) =ff 3881 c 932 e 7591 e 674 e 2 d 9 d 772817746 e 8 d 983 f %

Properties of a good Message Digest = f (Input) • Digest cannot be predicted from the input • Hard or impossible to find two inputs with the same digest. • Changing one bit of input changes ~50% of the output bits.

Message Digest Example message MD 5(message) “this is a test” ff 22941336956098 ae 9 a 564289 d 1 bf 1 b “this is c test” c 5 e 530 b 91 f 5 f 324 b 1 e 64 d 3 ee 7 a 21 d 573 “this is a test ” 6 df 4 c 47 dba 4 b 01 cc f 4 b 5 e 0 d 9 a 7 b 8 d 925

Key Points • Any change in the input changes the digest: • Adding a space • Changing a line break • Capitalizing a word

Message Digest Algorithms • Rivest Functions: • MD 2 (RFC 1319), MD 4 (RFC 1320), MD 5 (RFC 1321) • NIST Functions: • SHA, SHA-1, SHA-512, SHA-1024 • Other Functions: • Snerfu, N-Hash, RIPE-MD, HAVAL
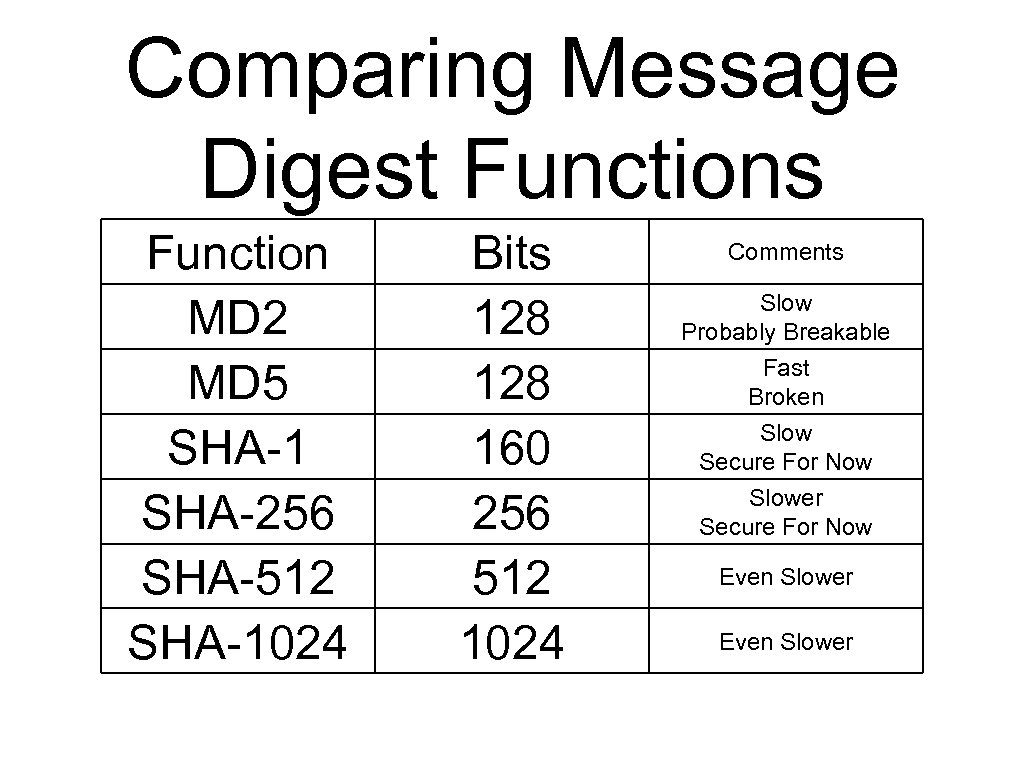
Comparing Message Digest Functions Function MD 2 MD 5 SHA-1 SHA-256 SHA-512 SHA-1024 Bits 128 160 256 512 1024 Comments Slow Probably Breakable Fast Broken Slow Secure For Now Slower Secure For Now Even Slower

“Breaking” a message digest Brute-force attack: Search for two messages that have the same digest (they should be many of them) Create a message with a desired message digest • •

“Breaking” a message digest Algorithm attack • Create two documents with the same digest. • Create one document with the same digest as another document.

MD 5 “Broken” • Collisions for Hash Functions MD 4, MD 5, HAVAL-128 and RIPEMD, Xiaoyun Wang and Dengguo Feng and Xuejia Lai and Hongbo Yu, August 16, 2004 • http: //eprint. iacr. org/2004/199/

file 1. dat: 00000010 00000020 00000030 00000040 00000050 00000060 00000070 d 1 31 dd 02 c 5 e 6 ee c 4 69 3 d 9 a 06 98 af f 9 5 c 2 f ca b 5 87 12 46 7 e ab 40 04 58 3 e b 8 fb 7 f 89 55 ad 34 06 09 f 4 b 3 02 83 e 4 88 83 25 71 41 5 a 08 51 25 e 8 f 7 cd c 9 9 f d 9 1 d bd f 2 80 37 3 c 5 b 96 0 b 1 d d 1 dc 41 7 b 9 c e 4 d 8 97 f 4 5 a 65 55 d 5 35 73 9 a c 7 f 0 eb fd 0 c 30 29 f 1 66 d 1 09 b 1 8 f 75 27 7 f 79 30 d 5 5 c eb 22 e 8 ad ba 79 cc 15 5 c ed 74 cb dd 5 f c 5 d 3 6 d b 1 9 b 0 a d 8 35 cc a 7 e 3 MD 5(file 1. dat) = a 4 c 0 d 35 c 95 a 63 a 805915367 dcfe 6 b 751 file 2. dat: 00000010 00000020 00000030 00000040 00000050 00000060 00000070 d 1 31 dd 02 c 5 e 6 ee c 4 69 3 d 9 a 06 98 af f 9 5 c 2 f ca b 5 07 12 46 7 e ab 40 04 58 3 e b 8 fb 7 f 89 55 ad 34 06 09 f 4 b 3 02 83 e 4 88 83 25 f 1 41 5 a 08 51 25 e 8 f 7 cd c 9 9 f d 9 1 d bd 72 80 37 3 c 5 b 96 0 b 1 d d 1 dc 41 7 b 9 c e 4 d 8 97 f 4 5 a 65 55 d 5 35 73 9 a 47 f 0 eb fd 0 c 30 29 f 1 66 d 1 09 b 1 8 f 75 27 7 f 79 30 d 5 5 c eb 22 e 8 ad ba 79 4 c 15 5 c ed 74 cb dd 5 f c 5 d 3 6 d b 1 9 b 0 a 58 35 cc a 7 e 3 MD 5(file 2. dat) = a 4 c 0 d 35 c 95 a 63 a 805915367 dcfe 6 b 751

Documents with Tunable Digests We the people citizens of the US United States, in order to form make a more perfect union, establish justice, insure domestic tranquility, provide for the common defense, promote the general welfare, and secure the blessing of liberty to ourselves and our posterity children, do ordain and establish the Constitution of the United States of America. 4 4 choices = 2 different SHA-1 codes. • Still a long way from 2 128 2 160 --- or even from

Just how big is 2 ? 128 2128 = 340, 282, 366, 920, 938, 463, 374, 607, 431, 768, 211, 456 2 If you could try a billion combinations a second, it would take 10, 790 billion years (2128 / 109 / (60*60*24*365) / 109)
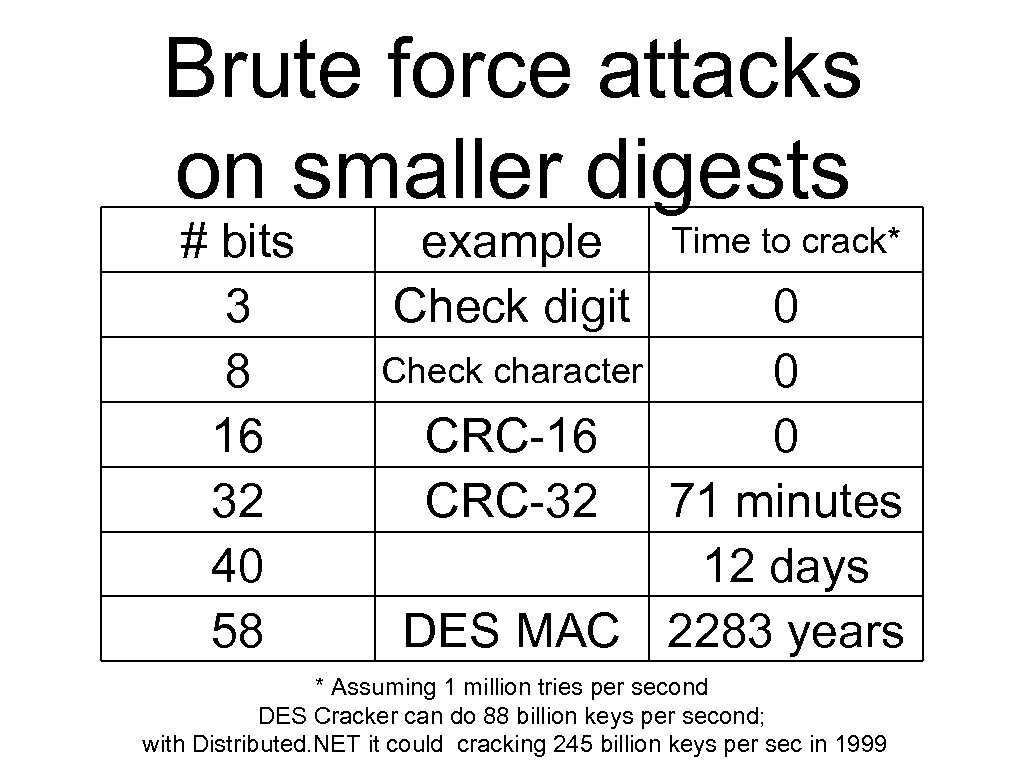
Brute force attacks on smaller digests # bits 3 8 16 32 40 58 example Check digit Time to crack* 0 Check character 0 CRC-16 0 CRC-32 71 minutes 12 days DES MAC 2283 years * Assuming 1 million tries per second DES Cracker can do 88 billion keys per second; with Distributed. NET it could cracking 245 billion keys per sec in 1999
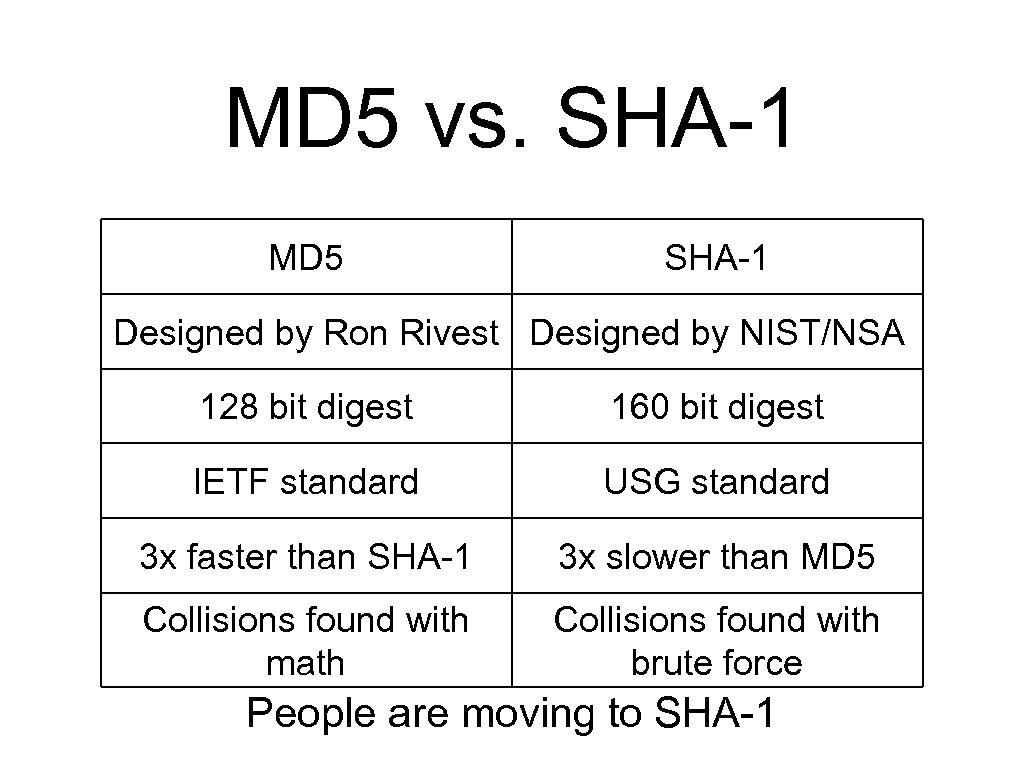
MD 5 vs. SHA-1 MD 5 SHA-1 Designed by Ron Rivest Designed by NIST/NSA 128 bit digest 160 bit digest IETF standard USG standard 3 x faster than SHA-1 3 x slower than MD 5 Collisions found with math Collisions found with brute force People are moving to SHA-1

Uses of Digest Functions • Integrity • Verifying downloaded code • Use Digest to determine if two files are • identical Verifying SSL streams Authentication verifying a shared secret w/o encryption • •

Class Discussion • What are the practical implications of it being broken? • Is it really “broken? ”
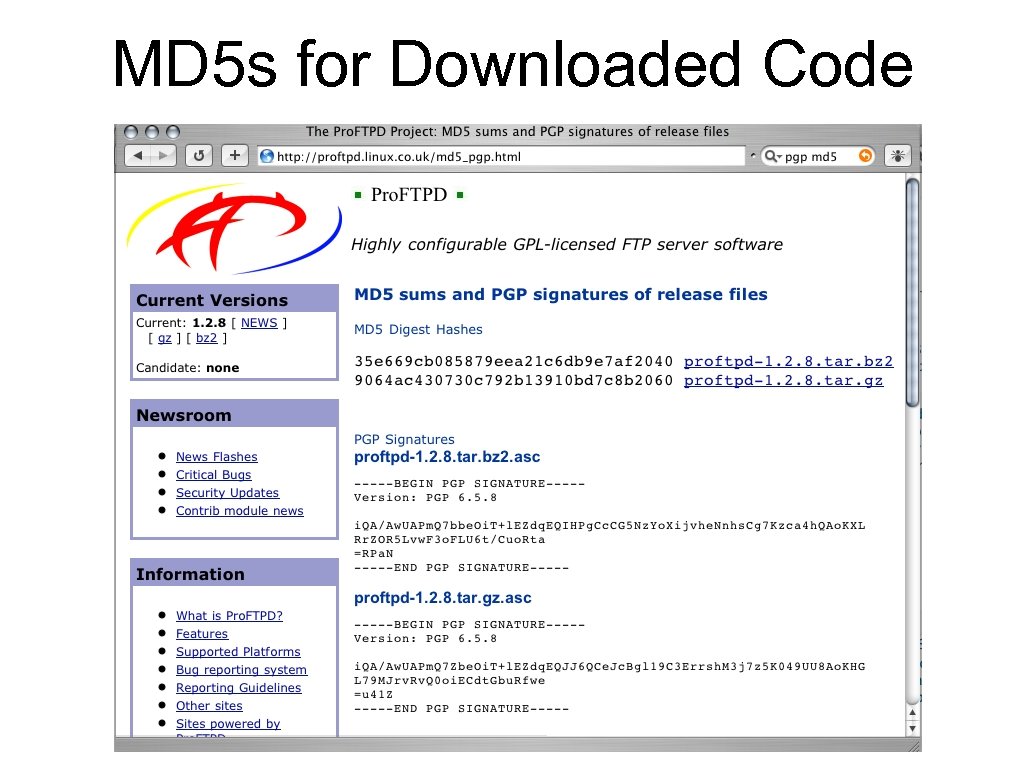
MD 5 s for Downloaded Code
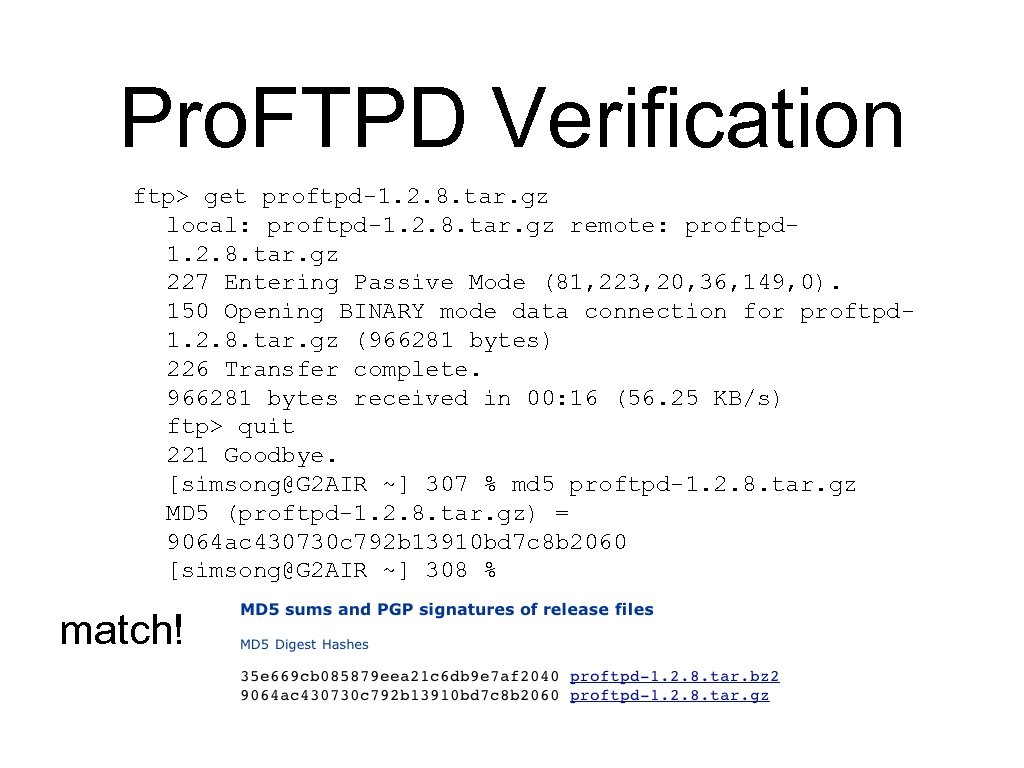
Pro. FTPD Verification ftp> get proftpd-1. 2. 8. tar. gz local: proftpd-1. 2. 8. tar. gz remote: proftpd 1. 2. 8. tar. gz 227 Entering Passive Mode (81, 223, 20, 36, 149, 0). 150 Opening BINARY mode data connection for proftpd 1. 2. 8. tar. gz (966281 bytes) 226 Transfer complete. 966281 bytes received in 00: 16 (56. 25 KB/s) ftp> quit 221 Goodbye. [simsong@G 2 AIR ~] 307 % md 5 proftpd-1. 2. 8. tar. gz MD 5 (proftpd-1. 2. 8. tar. gz) = 9064 ac 430730 c 792 b 13910 bd 7 c 8 b 2060 [simsong@G 2 AIR ~] 308 % match!

Question • Does MD 5 being “broken” matter for this application?

Storing Passwords • Instead of storing the password, store the hash of the password. • “Cracking” the password requires hashing every password entry to see if it matches the hash. • Unix originally used a DES-based hash, now it uses an MD 5 hash gigawalt: f. URfuu 4. 4 h. Y 0 U: 129: Walter Belgers: /home/gigawalt: /bin/csh root: $1$zl. C 9. Vfl$9 r. XSa. Qqe 1 HWDa. NNOSTJzh. : 0: 0: Nitroba &: /root: /bin/tcsh
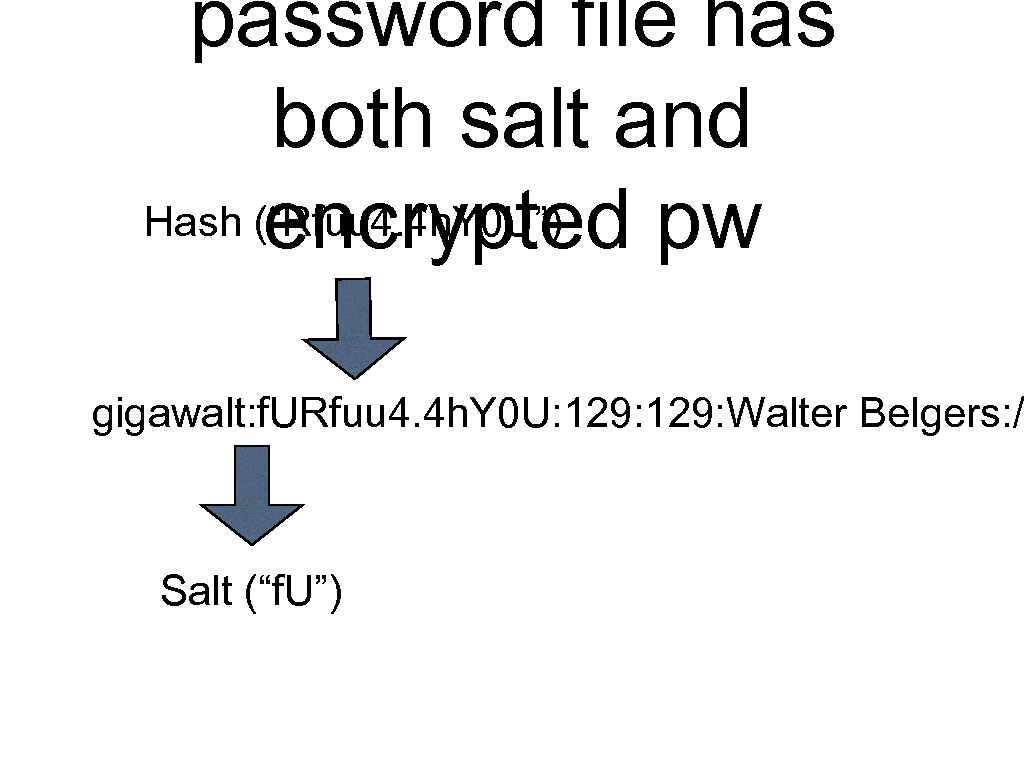
password file has both salt and Hash (“Rfuu 4. 4 h. Y 0 U”) encrypted pw gigawalt: f. URfuu 4. 4 h. Y 0 U: 129: Walter Belgers: / Salt (“f. U”)
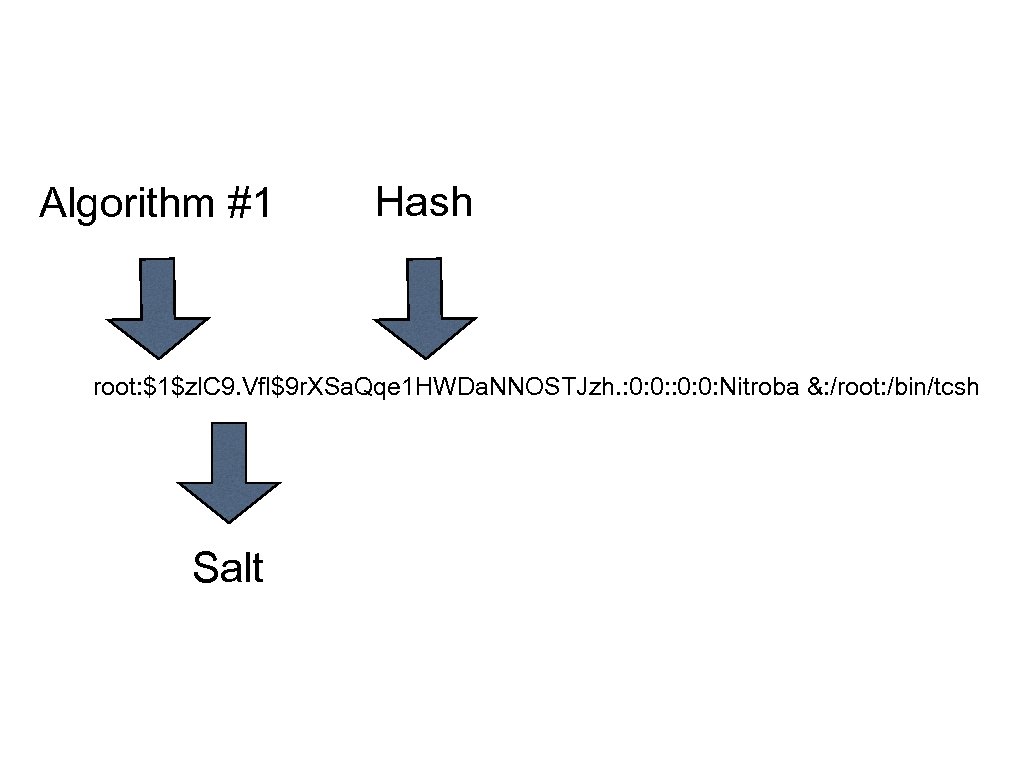
Algorithm #1 Hash root: $1$zl. C 9. Vfl$9 r. XSa. Qqe 1 HWDa. NNOSTJzh. : 0: 0: Nitroba &: /root: /bin/tcsh Salt

What’s the point of the salt?

MACs and HMACs • MAC = “Message Authentication Code” • HMAC = “Keyed Hashing for Message Authentication” (RFC 2104) • http: //www. ietf. org/rfc 2404. txt • http: //www. cs. ucsd. edu/users/mihir/pa pers/hmac. html
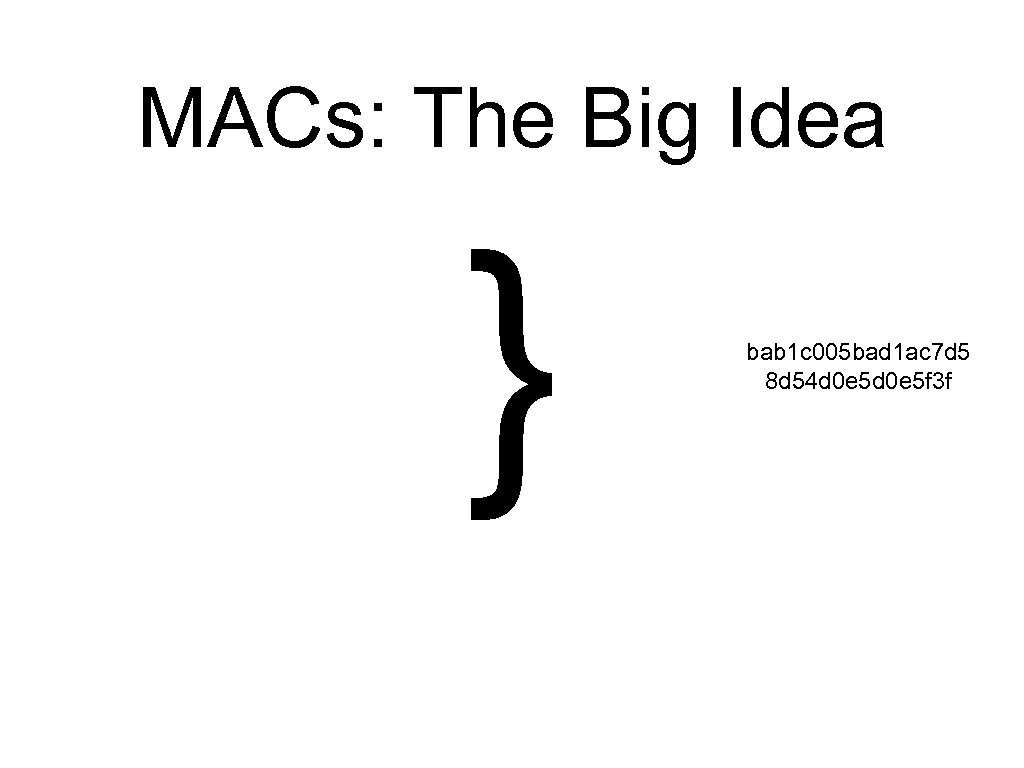
MACs: The Big Idea } bab 1 c 005 bad 1 ac 7 d 5 8 d 54 d 0 e 5 f 3 f

RFC 2104: HMAC 64 64 HMAC(f, K, M) = f(K⊕ 0 x 5 c · f(K⊕ 0 x 36 · M)) More complicated than concatenating the key and taking the hash, but more secure!
Uses of HMACs • Data integrity and authentication • BGP uses HMAC • IPsec Authentication Header and Encapsulating Security Payload use HMAC as a digital “signature. ” • Password protocols


MD 5 API: Perl % man Digest: : MD 5. . . # Functional style use Digest: : MD 5 qw(md 5_hex md 5_base 64); $digest = md 5($data); $digest = md 5_hex($data); $digest = md 5_base 64($data); # OO style use Digest: : MD 5; $ctx = Digest: : MD 5 ->new; $ctx->add($data); $ctx->addfile(*FILE); $digest = $ctx->digest; $digest = $ctx->hexdigest; $digest = $ctx->b 64 digest;

md 5. pl #!/usr/bin/perl use Digest: : MD 5 qw(md 5); use strict; open J, $ARGV[0] || die "Cannot open $ARGV[0], "; my $ctx = Digest: : MD 5 ->new; $ctx->addfile(*J); print "md 5($ARGV[0]) = ", $ctx->hexdigest, "n";

calc_md 5. py #!/usr/bin/python import md 5 import sys m = md 5. new() m. update(open(sys. argv[1], "r"). read()) print "md 5(%s) = %s" % (sys. argv[1], m. hexdigest()) Note: be careful not to call this file md 5. py!
![calc_md 5. py #!/usr/bin/python import md 5 import sys f = open(sys. argv[1], ”r”) calc_md 5. py #!/usr/bin/python import md 5 import sys f = open(sys. argv[1], ”r”)](https://present5.com/presentation/40e746d252678498f16d14a768579f91/image-36.jpg)
calc_md 5. py #!/usr/bin/python import md 5 import sys f = open(sys. argv[1], ”r”) data = f. read() m = md 5. new() m. update(data) print "md 5(%s) = %s" % (sys. argv[1], m. hexdigest())

MD 5 HMAC API NAME Digest: : HMAC_MD 5 - Keyed-Hashing for Message Authentication SYNOPSIS # Functional style use Digest: : HMAC_MD 5 qw(hmac_md 5_hex); $digest = hmac_md 5($data, $key); print hmac_md 5_hex($data, $key); # OO style use Digest: : HMAC_MD 5; $hmac = Digest: : HMAC_MD 5 ->new($key); $hmac->add($data); $hmac->addfile(*FILE); $digest = $hmac->digest; $digest = $hmac->hexdigest; $digest = $hmac->b 64 digest;

hash representations $digest = $ctx->digest; $digest = $ctx->b 64 digest; $digest = $ctx->hexdigest;
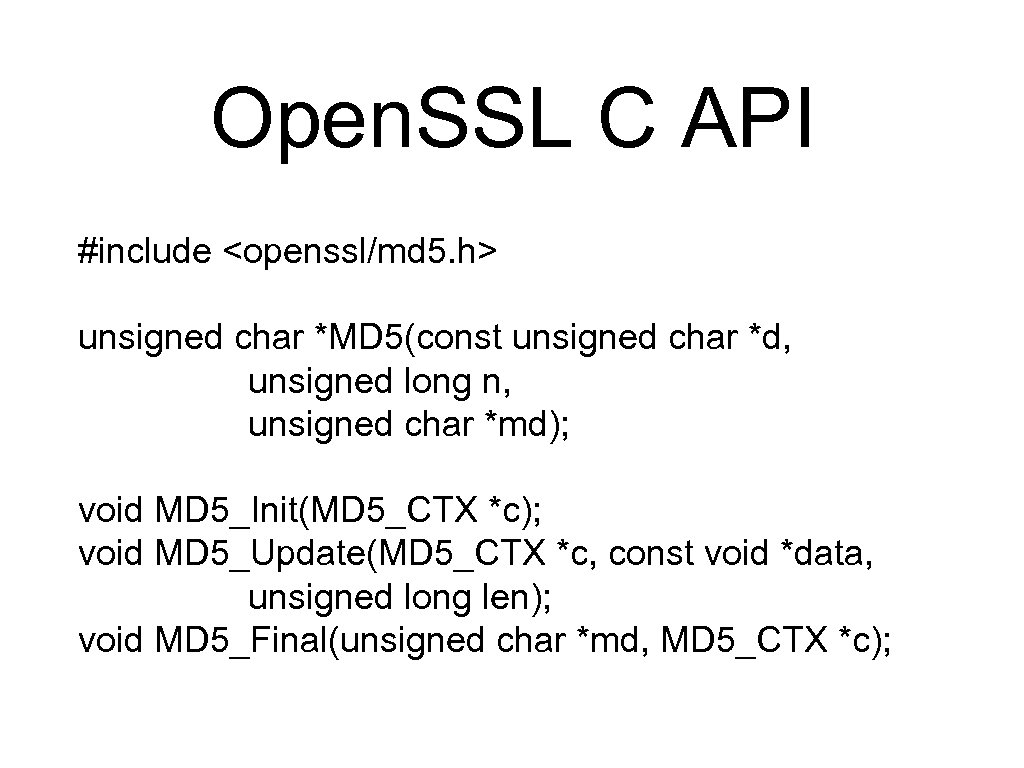
Open. SSL C API #include <openssl/md 5. h> unsigned char *MD 5(const unsigned char *d, unsigned long n, unsigned char *md); void MD 5_Init(MD 5_CTX *c); void MD 5_Update(MD 5_CTX *c, const void *data, unsigned long len); void MD 5_Final(unsigned char *md, MD 5_CTX *c);
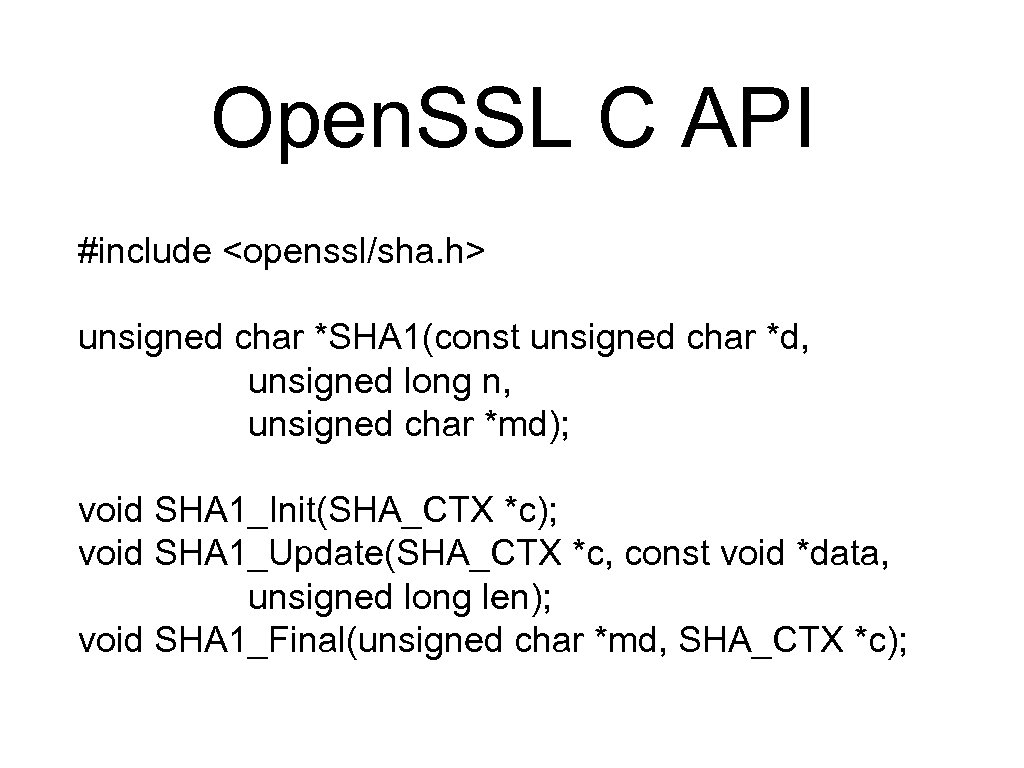
Open. SSL C API #include <openssl/sha. h> unsigned char *SHA 1(const unsigned char *d, unsigned long n, unsigned char *md); void SHA 1_Init(SHA_CTX *c); void SHA 1_Update(SHA_CTX *c, const void *data, unsigned long len); void SHA 1_Final(unsigned char *md, SHA_CTX *c);

void MD 5_Init(MD 5_CTX *c); void SHA 1_Init(SHA_CTX *c); • A context is used for a process that • needs to be repeated over many blocks of data Stream cipher Encryption of many blocks Calculation of a message digest Similar to instance variables in object oriented programming. • • •
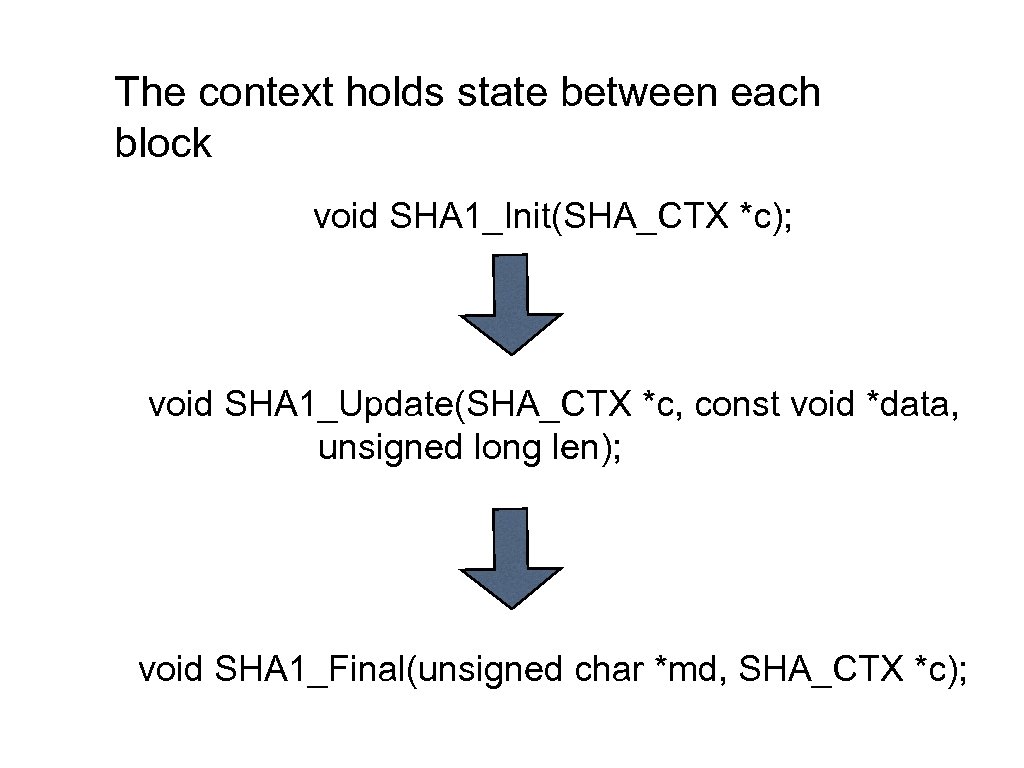
The context holds state between each block void SHA 1_Init(SHA_CTX *c); void SHA 1_Update(SHA_CTX *c, const void *data, unsigned long len); void SHA 1_Final(unsigned char *md, SHA_CTX *c);
![char buf[] vs. unsigned char buf[] • Technically, binary data should be unsigned char char buf[] vs. unsigned char buf[] • Technically, binary data should be unsigned char](https://present5.com/presentation/40e746d252678498f16d14a768579f91/image-43.jpg)
char buf[] vs. unsigned char buf[] • Technically, binary data should be unsigned char • Many C routines take char • (e. g. read(), write(), etc. ) • Expect frequent casts or compiler warnings

Other uses of MACs • Hash Trees - Shurety digital notary • S/KEY • Secure. ID • Password Challenge-Response
40e746d252678498f16d14a768579f91.ppt