bee5061b6dd7a149521bd3563dceb2e2.ppt
- Количество слайдов: 33

CSCE 815 Network Security Lecture 16 Web Security Secure Sockets Layer (SSL) March 18, 2003

Overview PGP one more time 1. Note session key will be automatically generated 2. pgp –h pgp –k pgp –g 3. 4. // help on keys // help on groups Key distribution SSL SET – 2– CSCE 815 Sp 03

PGP Key distribution Generating key and getting it into a file n n pgp –kg pgp –kx matthews mykey. pgp Approaches Page 137 1. Physical – write to floppy, hand to friend 2. Verify key by telephone n n Read the key in radix 64 over the phone (not cell phone) Email key then verify by having PGP generate 160 bit SHA-1 digest of the key, read the hex digits (fingerprint) 3. Obtain key from a trusted mutual friend 4. Obtain key from a certifying authority – 3– CSCE 815 Sp 03
Web Security Outline Web Security Considerations Secure Socket Layer (SSL) and Transport Layer Security (TLS) Secure Electronic Transaction (SET) – 4– CSCE 815 Sp 03
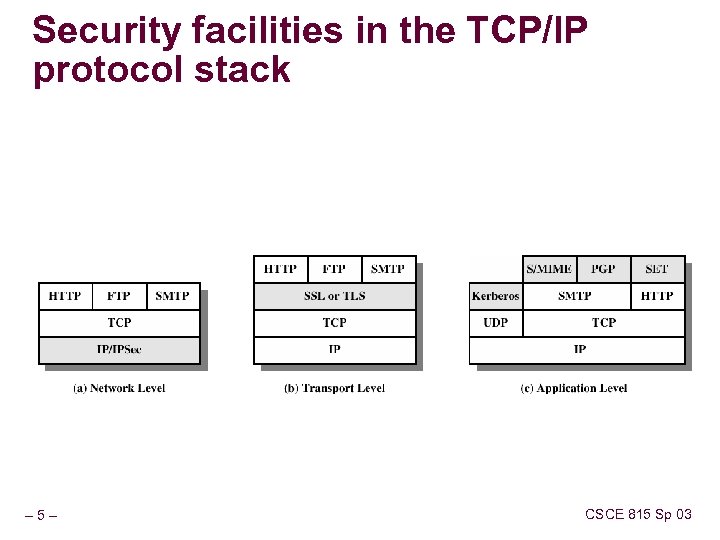
Security facilities in the TCP/IP protocol stack – 5– CSCE 815 Sp 03
SSL and TLS SSL was originated by Netscape TLS working group was formed within IETF First version of TLS can be viewed as an SSLv 3. 1 – 6– CSCE 815 Sp 03
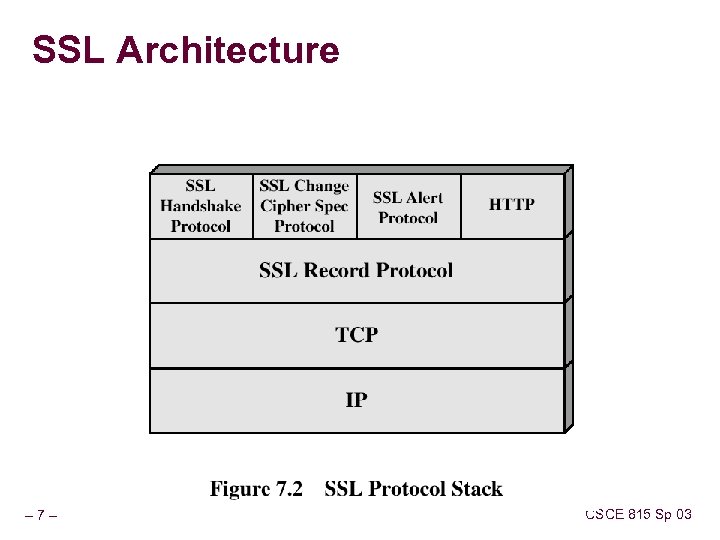
SSL Architecture – 7– CSCE 815 Sp 03

SSL Record Protocol Services Confidentiality – the handshake protocol defines a shared key for encryptions of SSL payloads Message Integrity – the handshake protocol defines a shared key used to form message authentication code (MAC) – 8– CSCE 815 Sp 03
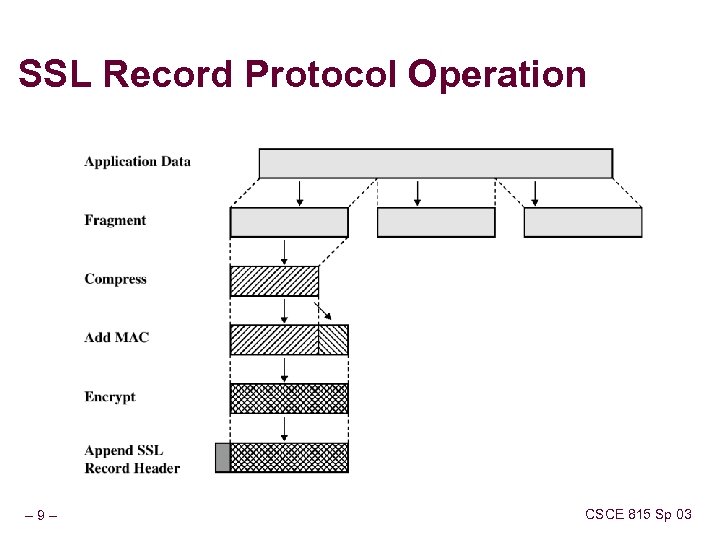
SSL Record Protocol Operation – 9– CSCE 815 Sp 03
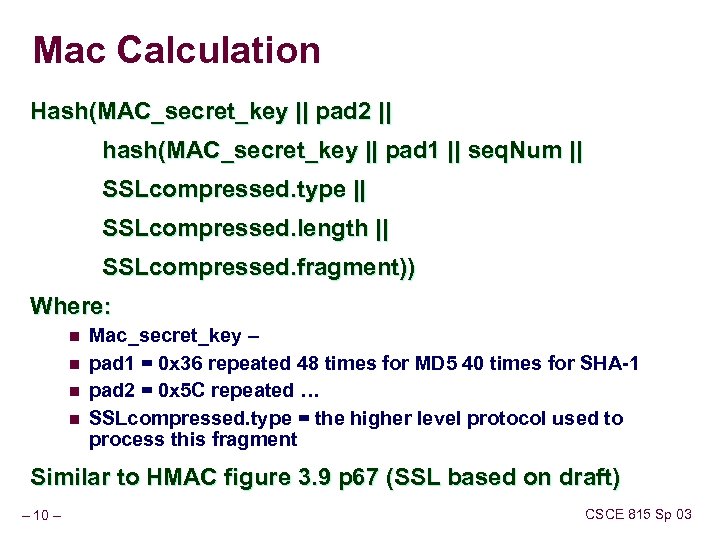
Mac Calculation Hash(MAC_secret_key || pad 2 || hash(MAC_secret_key || pad 1 || seq. Num || SSLcompressed. type || SSLcompressed. length || SSLcompressed. fragment)) Where: n n Mac_secret_key – pad 1 = 0 x 36 repeated 48 times for MD 5 40 times for SHA-1 pad 2 = 0 x 5 C repeated … SSLcompressed. type = the higher level protocol used to process this fragment Similar to HMAC figure 3. 9 p 67 (SSL based on draft) – 10 – CSCE 815 Sp 03

Encryption Methods for SSL Fragments 214 = 16384 bytes Compression must be lossless and must not increase length more than 1024 No compression algorithm specified in SSLv 3 – default no compression Block Cipher Encryption Methods n IDEA (128) RC 2 -40, DES (56), 3 DES (168), Fortezza(80) Stream Cipher Encryption choices n RC 4 -40, RC 4 -128 Fortezza used in smart cards – 11 – CSCE 815 Sp 03
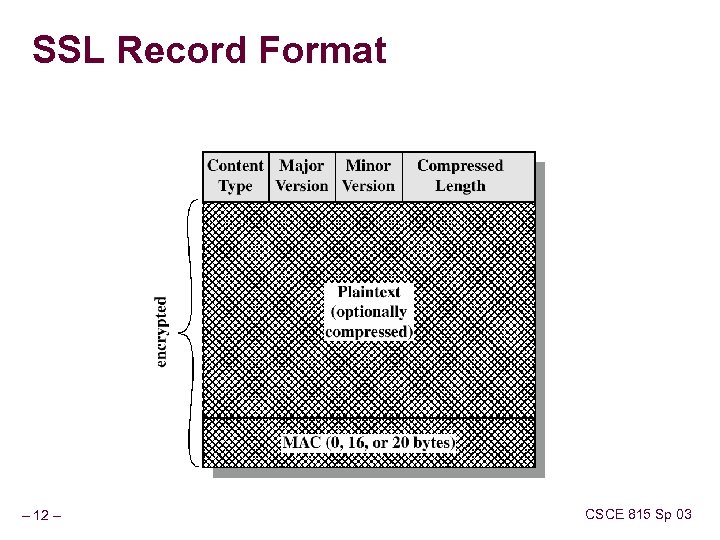
SSL Record Format – 12 – CSCE 815 Sp 03
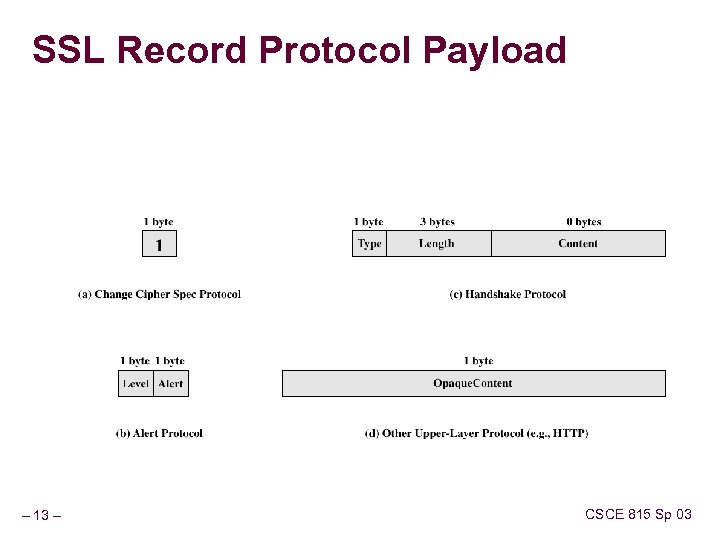
SSL Record Protocol Payload – 13 – CSCE 815 Sp 03
Change Cipher Spec and Alert Protocols Change Cipher Spec Protocol consists of a single message of a single byte with value 1 it means copy pending state to current state Alert Protocol – use to convey SSL-related alerts Two Bytes: 1. 2. Level – severity of alert 1=warning, 2=fatal Alert type: l l l – 14 – Unexpected message Bad-record_mac Decompression failure Handshake failure Illegal_parameter … CSCE 815 Sp 03
Handshake Protocol The most complex part of SSL. Allows the server and client to authenticate each other. Negotiate encryption, MAC algorithm and cryptographic keys. Used before any application data are transmitted. Message Fields n n n – 15 – Type (8) Length (24) Content (>= 1 byte) parameters CSCE 815 Sp 03

SSL Handshake Protocol Message Types Table 7. 2 Message type Parameters 1. Hello-request null 2. Client-hello session. ID, compression method version, random(32 B), cipher suite, 3. Server_hello ditto 4. Certificate chain of X. 509 v 3 certificates 5. Server_key_exchange parameters, signature 6. Certificate_request type, authorities 7. Server_done null 8. Certificate_verify signature 9. Client_key_exchange parameters, signature – 10. Finished 16 – hash value CSCE 815 Sp 03
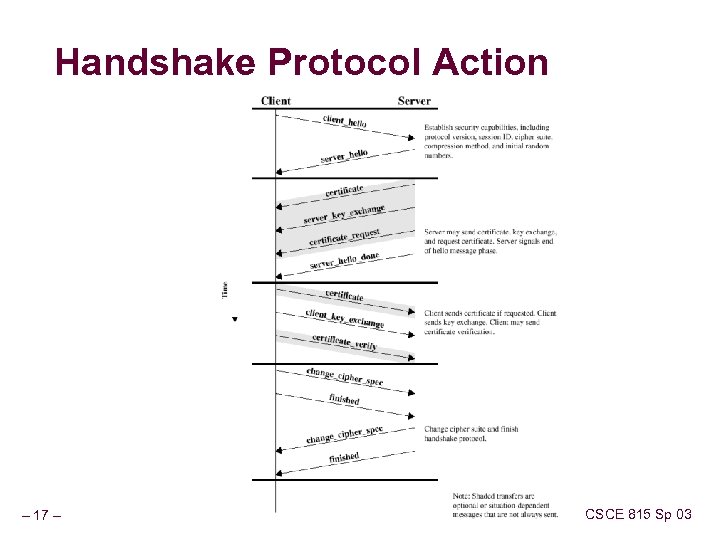
Handshake Protocol Action – 17 – CSCE 815 Sp 03

Handshake Protocol Phase 1 Establish security capabilities Client_hello n n n Version = highest SSL understood by client Random 32 bit time stamp + 28 random bytes (secure random number generator) session. ID: 0 establish new connection, non-zero means update parameters of an existing session Ciphersuite: sequence of cryptographic algorithms in decreasing order of preference (key exchange + Cipher. Spec) Compression methods: sequence of compression methods Server_hello is sent back n n – 18 – same as above but confirmation Highest common version, new random field, same session. ID if nonzero, new session. ID otherwise, the selected ciphersuite and the selected compression technique CSCE 815 Sp 03

Handshake Protocol Phase 1 Key Exchange methods 1. 2. 3. 4. 5. RSA – secrt key is encrypted with receiver’s RSA public key Fixed Diffie-Hellman Ephemeral Diffie Hellman Anonymous Diffie-Hellman Fortezza 1. Cipher. Spec follows containing the fields 1. 2. 3. 4. 5. – 19 – 6. Cipher algorithm MAC algorithm Cipher. Type: block or stream Hash size: 0, 16 for MD 5 or 20 for SHA-1 bytes Key material – sequence of bytes used to generate keys IV size of Initial Value for Cipher Block Chaining (CBC) 815 Sp 03 CSCE

Handshake Protocol Phase 2 Server Authentication and Key Exchange Server sends 1. 2. Certificate: X. 509 certificate chain (not required for anonymous Diffie-Hellman) Server_key_exchange (not always need e. g. fixed Diffie. Hellman) l Hash(Client_hello. random||Server. Hello. random||Server. Parms) 3. 4. – 20 – Certificate_request: certificate type and certificate authorities Server_hello_done: I’m done and I’ll wait on response CSCE 815 Sp 03

Handshake Protocol Phase 3 Client Authentication and Key Exchange Client verifies server certificate a checks the server hello paramters Client sends 1. 2. 3. – 21 – Certificate: if requested Client_key_exchange message must be sent Certificate_verify message to provide explicit verification of client certificate CSCE 815 Sp 03

Handshake Protocol Phase 4 Finish up: switch to next cipher_spec Client sends 1. 2. Change_cipher_spec message Finished message under new algorithms, keys (new cipher_spec) 1. Server sends back 1. 2. – 22 – Change_cipher_spec message Finished message under new algorithms, keys (new cipher_spec) CSCE 815 Sp 03

Transport Layer Security The same record format as the SSL record format. Defined in RFC 2246. Similar to SSLv 3. Differences in the: n n n n n – 23 – version number message authentication code pseudorandom function alert codes cipher suites client certificate types certificate_verify and finished message cryptographic computations padding CSCE 815 Sp 03

Secure Electronic Transactions An open encryption and security specification. Protect credit card transaction on the Internet. Companies involved: n Master. Card, Visa, IBM, Microsoft, Netscape, RSA, Terisa and Verisign Not a payment system. Set of security protocols and formats. – 24 – CSCE 815 Sp 03

SET Services Provides a secure communication channel in a transaction. Provides tust by the use of X. 509 v 3 digital certificates. Ensures privacy. – 25 – CSCE 815 Sp 03
SET Overview Key Features of SET: n Confidentiality of information n Integrity of data Cardholder account authentication Merchant authentication n n – 26 – CSCE 815 Sp 03

SET Participants – 27 – CSCE 815 Sp 03

Sequence of events for transactions The customer opens an account. The customer receives a certificate. Merchants have their own certificates. The customer places an order. The merchant is verified. The order and payment are sent. The merchant request payment authorization. The merchant confirm the order. The merchant provides the goods or service. The merchant requests payments. – 28 – CSCE 815 Sp 03
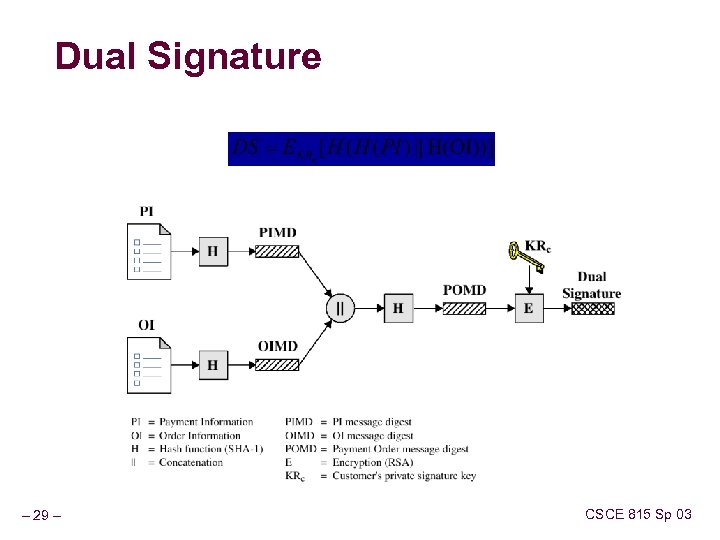
Dual Signature – 29 – CSCE 815 Sp 03

Payment processing Cardholder sends Purchase Request – 30 – CSCE 815 Sp 03

Payment processing Merchant Verifies Customer Purchase Request – 31 – CSCE 815 Sp 03
Payment processing Payment Authorization: n Authorization Request n Authorization Response Payment Capture: n n – 32 – Capture Request Capture Response CSCE 815 Sp 03

Recommended Reading and WEB sites http: //web. mit. edu/network/isakmp/ Drew, G. Using SET for Secure Electronic Commerce. Prentice Hall, 1999 Garfinkel, S. , and Spafford, G. Web Security & Commerce. O’Reilly and Associates, 1997 Master. Card SET site http: //www. mastercardintl. com/newtechnology/set/ Visa Electronic Commerce Site http: //usa. visa. com/personal/about_visa/newsroom/visa_security. html SETCo (documents and glossary of terms) http: //www. setco. org/set_specifications. html – 33 – CSCE 815 Sp 03
bee5061b6dd7a149521bd3563dceb2e2.ppt