 CSCE 715: Network Systems Security Chin-Tser Huang huangct@cse. sc. edu University of South Carolina 10/21/2004
CSCE 715: Network Systems Security Chin-Tser Huang huangct@cse. sc. edu University of South Carolina 10/21/2004
 Authentication Applications n n Developed to support application-level authentication and digital signatures A famous example is Kerberos – a password authentication service 10/21/2004 2
Authentication Applications n n Developed to support application-level authentication and digital signatures A famous example is Kerberos – a password authentication service 10/21/2004 2
 Kerberos n n Trusted key server system from MIT Provide centralized password third-party authentication in a distributed network n n allow users access to services distributed through network without needing to trust all workstations instead all trust a central authentication server Two versions in use: 4 & 5 10/21/2004 3
Kerberos n n Trusted key server system from MIT Provide centralized password third-party authentication in a distributed network n n allow users access to services distributed through network without needing to trust all workstations instead all trust a central authentication server Two versions in use: 4 & 5 10/21/2004 3
 Kerberos Requirements n First published report identified its requirements as n n n security reliability transparency scalability Implemented using an authentication protocol based on Needham-Schroeder 10/21/2004 4
Kerberos Requirements n First published report identified its requirements as n n n security reliability transparency scalability Implemented using an authentication protocol based on Needham-Schroeder 10/21/2004 4
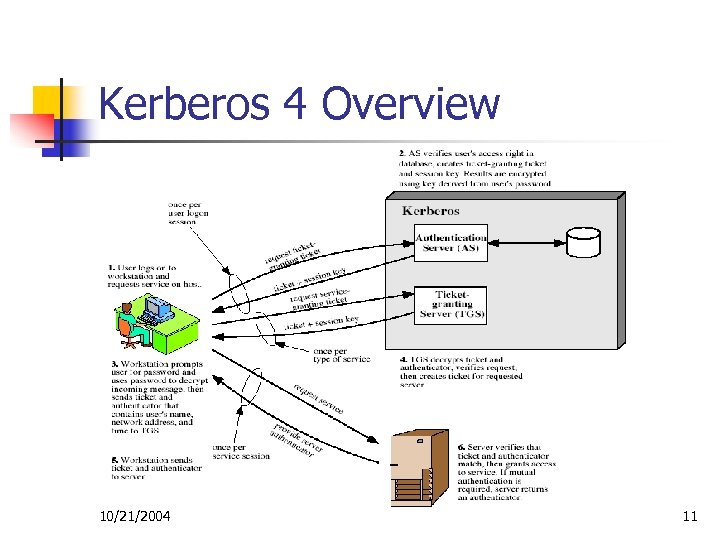
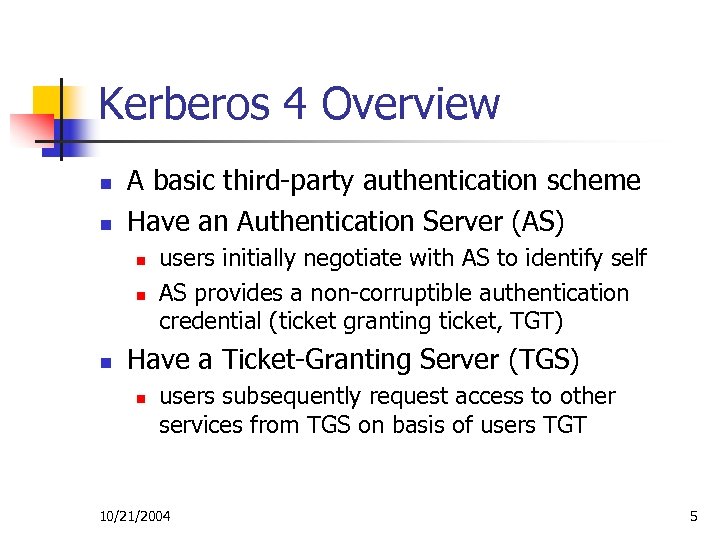 Kerberos 4 Overview n n A basic third-party authentication scheme Have an Authentication Server (AS) n n n users initially negotiate with AS to identify self AS provides a non-corruptible authentication credential (ticket granting ticket, TGT) Have a Ticket-Granting Server (TGS) n users subsequently request access to other services from TGS on basis of users TGT 10/21/2004 5
Kerberos 4 Overview n n A basic third-party authentication scheme Have an Authentication Server (AS) n n n users initially negotiate with AS to identify self AS provides a non-corruptible authentication credential (ticket granting ticket, TGT) Have a Ticket-Granting Server (TGS) n users subsequently request access to other services from TGS on basis of users TGT 10/21/2004 5
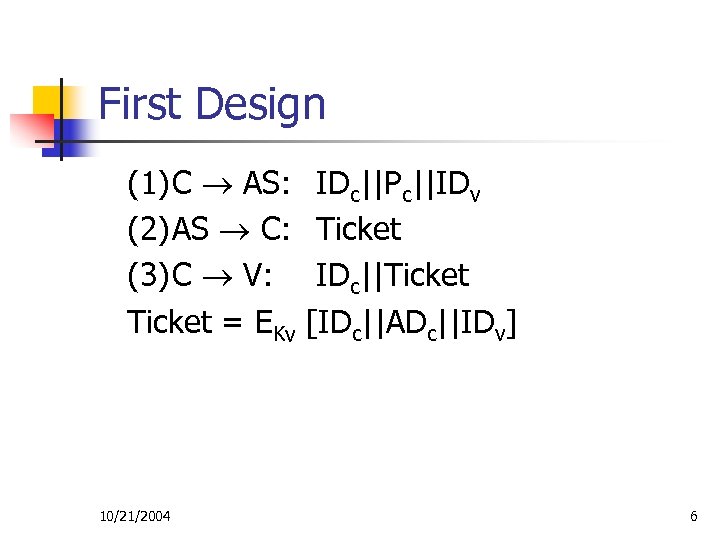 First Design (1)C AS: (2)AS C: (3)C V: Ticket = EKv 10/21/2004 IDc||Pc||IDv Ticket IDc||Ticket [IDc||ADc||IDv] 6
First Design (1)C AS: (2)AS C: (3)C V: Ticket = EKv 10/21/2004 IDc||Pc||IDv Ticket IDc||Ticket [IDc||ADc||IDv] 6
 Problems with First Design n n User may have to submit password many times in the same logon session Password is transmitted in clear 10/21/2004 7
Problems with First Design n n User may have to submit password many times in the same logon session Password is transmitted in clear 10/21/2004 7
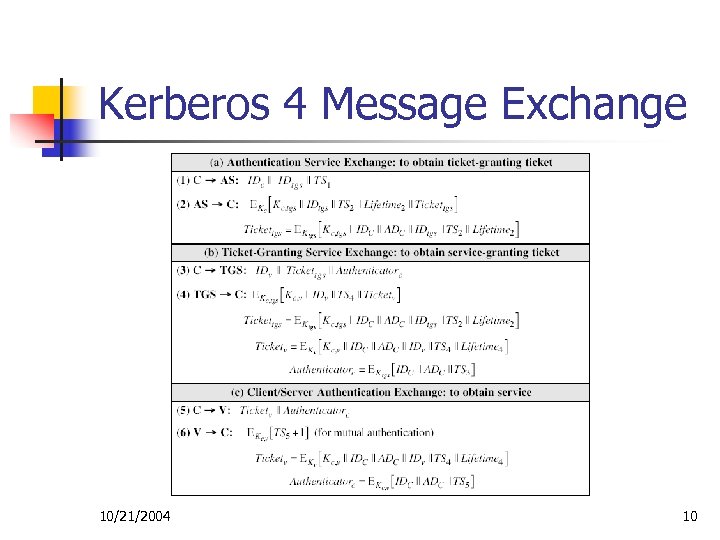
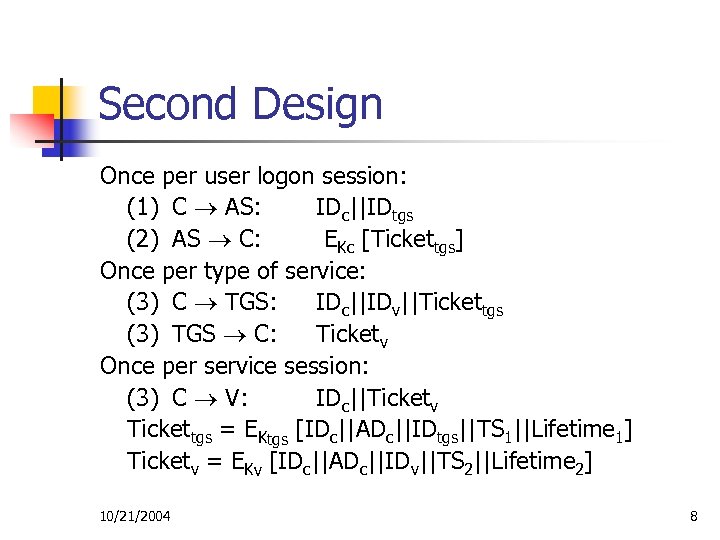 Second Design Once per user logon session: (1) C AS: IDc||IDtgs (2) AS C: EKc [Tickettgs] Once per type of service: (3) C TGS: IDc||IDv||Tickettgs (3) TGS C: Ticketv Once per service session: (3) C V: IDc||Ticketv Tickettgs = EKtgs [IDc||ADc||IDtgs||TS 1||Lifetime 1] Ticketv = EKv [IDc||ADc||IDv||TS 2||Lifetime 2] 10/21/2004 8
Second Design Once per user logon session: (1) C AS: IDc||IDtgs (2) AS C: EKc [Tickettgs] Once per type of service: (3) C TGS: IDc||IDv||Tickettgs (3) TGS C: Ticketv Once per service session: (3) C V: IDc||Ticketv Tickettgs = EKtgs [IDc||ADc||IDtgs||TS 1||Lifetime 1] Ticketv = EKv [IDc||ADc||IDv||TS 2||Lifetime 2] 10/21/2004 8
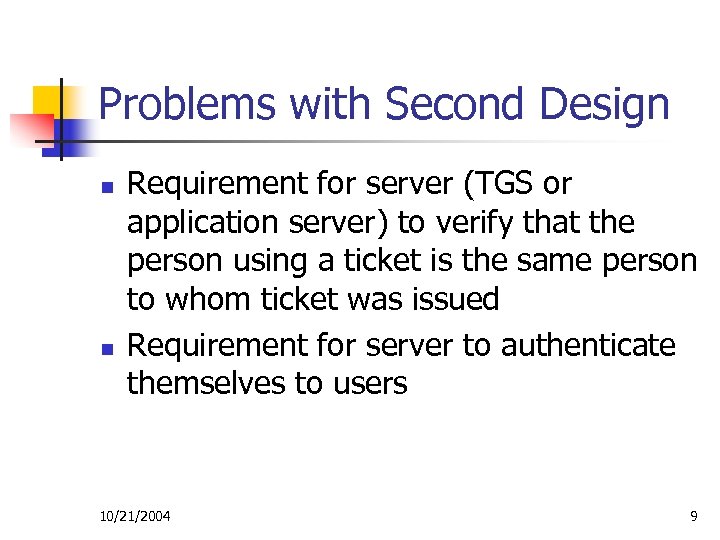 Problems with Second Design n n Requirement for server (TGS or application server) to verify that the person using a ticket is the same person to whom ticket was issued Requirement for server to authenticate themselves to users 10/21/2004 9
Problems with Second Design n n Requirement for server (TGS or application server) to verify that the person using a ticket is the same person to whom ticket was issued Requirement for server to authenticate themselves to users 10/21/2004 9
 Kerberos 4 Message Exchange 10/21/2004 10
Kerberos 4 Message Exchange 10/21/2004 10
 Kerberos 4 Overview 10/21/2004 11
Kerberos 4 Overview 10/21/2004 11
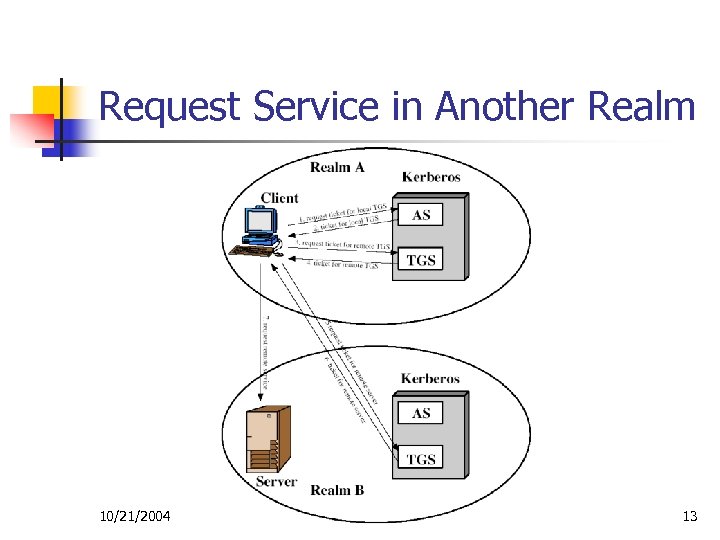
 Kerberos Realms n Kerberos environment consists of n n This is termed a “realm” n n a Kerberos server a number of clients, all registered with server application servers, sharing keys with server typically within a single administrative domain If have multiple realms, their Kerberos servers must share keys and trust each other 10/21/2004 12
Kerberos Realms n Kerberos environment consists of n n This is termed a “realm” n n a Kerberos server a number of clients, all registered with server application servers, sharing keys with server typically within a single administrative domain If have multiple realms, their Kerberos servers must share keys and trust each other 10/21/2004 12
 Request Service in Another Realm 10/21/2004 13
Request Service in Another Realm 10/21/2004 13
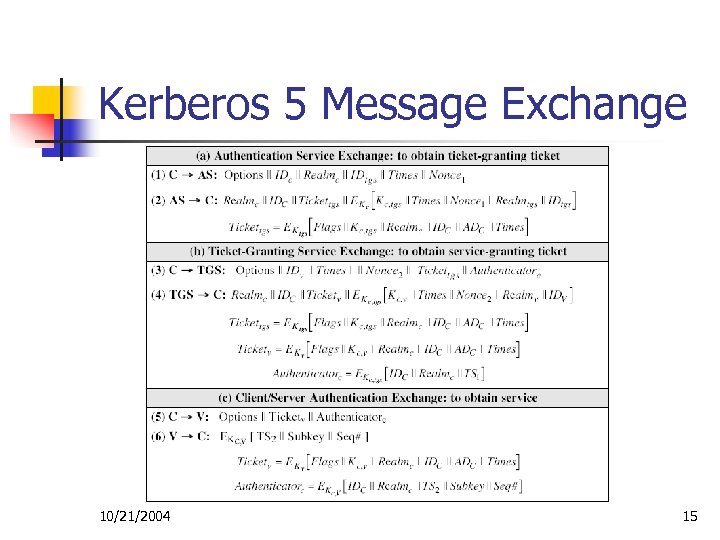
 Kerberos Version 5 n n Developed in mid 1990’s Provide improvements over Version 4 n addresses environmental shortcomings n n and technical deficiencies n n encryption alg, network protocol, byte order, ticket lifetime, authentication forwarding, interrealm auth double encryption, non-std mode of use, session keys, password attacks Specified as Internet standard RFC 1510 10/21/2004 14
Kerberos Version 5 n n Developed in mid 1990’s Provide improvements over Version 4 n addresses environmental shortcomings n n and technical deficiencies n n encryption alg, network protocol, byte order, ticket lifetime, authentication forwarding, interrealm auth double encryption, non-std mode of use, session keys, password attacks Specified as Internet standard RFC 1510 10/21/2004 14
 Kerberos 5 Message Exchange 10/21/2004 15
Kerberos 5 Message Exchange 10/21/2004 15
 Next Class n n n Certificate and authorization Firewall and access control Read Chapters 14, 20 10/21/2004 16
Next Class n n n Certificate and authorization Firewall and access control Read Chapters 14, 20 10/21/2004 16