7cbdd00689ba6a717686e41fdd4decac.ppt
- Количество слайдов: 21
 CSCE 715: Network Systems Security Chin-Tser Huang huangct@cse. sc. edu University of South Carolina 02/18/2009
CSCE 715: Network Systems Security Chin-Tser Huang huangct@cse. sc. edu University of South Carolina 02/18/2009
 Network Security Designs n n n After discussion of cryptographic tools, we turn to look at various network security designs at different layers in protocol stack Link layer – secure address resolution Network layer – IPsec, hop integrity Transport layer – SSL/TLS Application layer – Kerberos, X. 509 certificate, firewall design 02/18/2009 2
Network Security Designs n n n After discussion of cryptographic tools, we turn to look at various network security designs at different layers in protocol stack Link layer – secure address resolution Network layer – IPsec, hop integrity Transport layer – SSL/TLS Application layer – Kerberos, X. 509 certificate, firewall design 02/18/2009 2
 Ethernet n n Most widely used LAN technology Low cost and high flexibility Versions of different speed: 10 Mbps, 100 Mbps, Gigabit Use globally unique media access control (MAC) address (hardware address) for every interface card 02/18/2009 3
Ethernet n n Most widely used LAN technology Low cost and high flexibility Versions of different speed: 10 Mbps, 100 Mbps, Gigabit Use globally unique media access control (MAC) address (hardware address) for every interface card 02/18/2009 3
 Use of Hardware Address n n Need an address to send a message to receiver on same Ethernet IP address is not usable because the data link does not recognize IP address Use hardware address to identify receiver’s interface Need to resolve receiver’s hardware address from receiver’s IP address 02/18/2009 4
Use of Hardware Address n n Need an address to send a message to receiver on same Ethernet IP address is not usable because the data link does not recognize IP address Use hardware address to identify receiver’s interface Need to resolve receiver’s hardware address from receiver’s IP address 02/18/2009 4
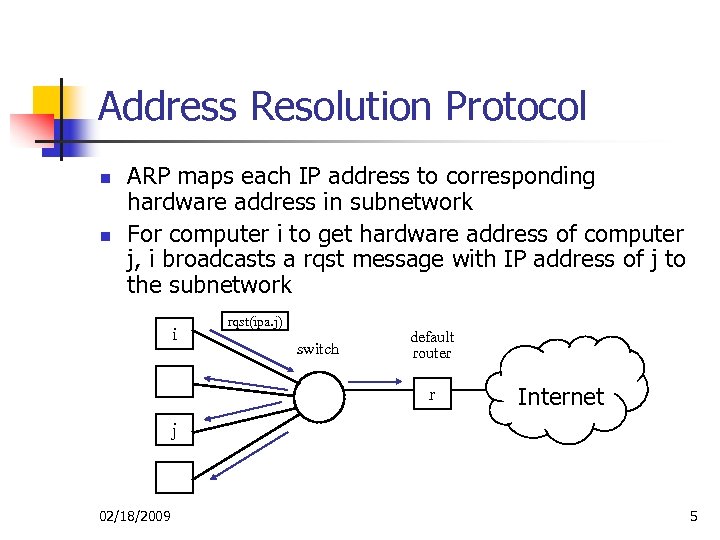 Address Resolution Protocol n n ARP maps each IP address to corresponding hardware address in subnetwork For computer i to get hardware address of computer j, i broadcasts a rqst message with IP address of j to the subnetwork i rqst(ipa. j) switch default router r Internet j 02/18/2009 5
Address Resolution Protocol n n ARP maps each IP address to corresponding hardware address in subnetwork For computer i to get hardware address of computer j, i broadcasts a rqst message with IP address of j to the subnetwork i rqst(ipa. j) switch default router r Internet j 02/18/2009 5
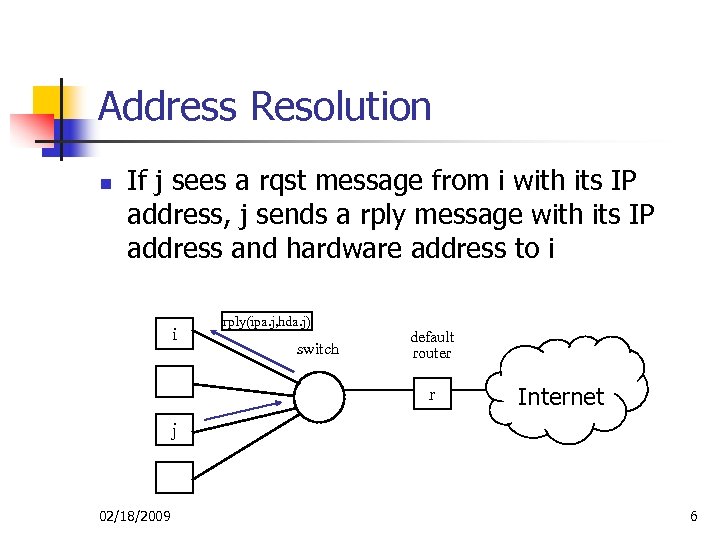 Address Resolution n If j sees a rqst message from i with its IP address, j sends a rply message with its IP address and hardware address to i i rply(ipa. j, hda. j) switch default router r Internet j 02/18/2009 6
Address Resolution n If j sees a rqst message from i with its IP address, j sends a rply message with its IP address and hardware address to i i rply(ipa. j, hda. j) switch default router r Internet j 02/18/2009 6
 Functions of ARP n Three functions of ARP n n n Resolving IP addresses Supporting dynamic assignment of addresses Detecting destination failures 02/18/2009 7
Functions of ARP n Three functions of ARP n n n Resolving IP addresses Supporting dynamic assignment of addresses Detecting destination failures 02/18/2009 7
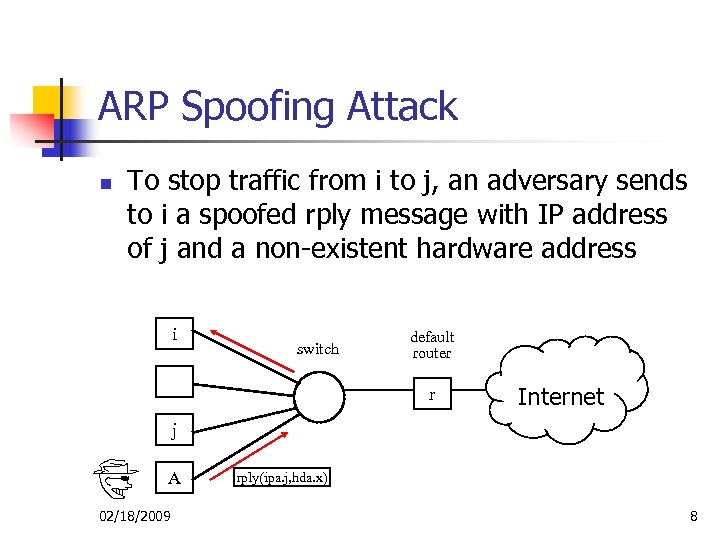 ARP Spoofing Attack n To stop traffic from i to j, an adversary sends to i a spoofed rply message with IP address of j and a non-existent hardware address i switch default router r Internet j A 02/18/2009 rply(ipa. j, hda. x) 8
ARP Spoofing Attack n To stop traffic from i to j, an adversary sends to i a spoofed rply message with IP address of j and a non-existent hardware address i switch default router r Internet j A 02/18/2009 rply(ipa. j, hda. x) 8
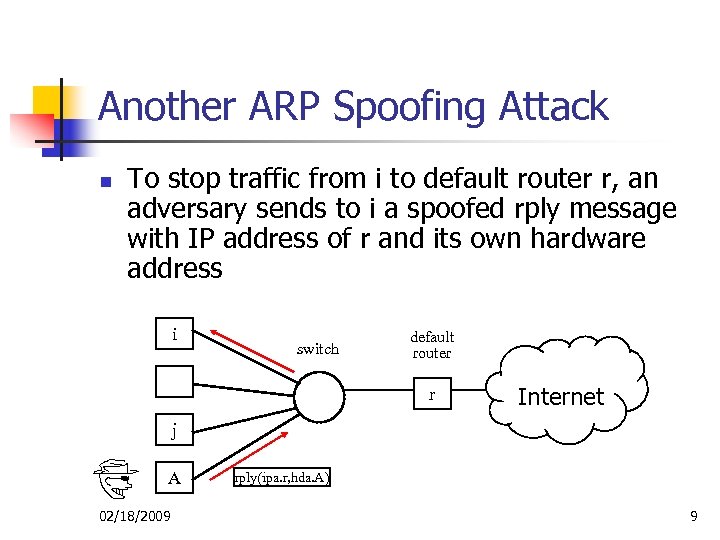 Another ARP Spoofing Attack n To stop traffic from i to default router r, an adversary sends to i a spoofed rply message with IP address of r and its own hardware address i switch default router r Internet j A 02/18/2009 rply(ipa. r, hda. A) 9
Another ARP Spoofing Attack n To stop traffic from i to default router r, an adversary sends to i a spoofed rply message with IP address of r and its own hardware address i switch default router r Internet j A 02/18/2009 rply(ipa. r, hda. A) 9
 Countering ARP Spoofing Attacks n Proposed solutions include ARPWATCH and static ARP caches n n ARPWATCH monitors transmission of rqst and rply messages over Ethernet and check them against a database of (IP addr, hardware addr) pairings Static ARP cache stores permanent (IP addr, hardware addr) pairings of trusted hosts to avoid sending rqst and rply messages over Ethernet 02/18/2009 10
Countering ARP Spoofing Attacks n Proposed solutions include ARPWATCH and static ARP caches n n ARPWATCH monitors transmission of rqst and rply messages over Ethernet and check them against a database of (IP addr, hardware addr) pairings Static ARP cache stores permanent (IP addr, hardware addr) pairings of trusted hosts to avoid sending rqst and rply messages over Ethernet 02/18/2009 10
 Insufficiencies of Proposed Solutions n n ARPWATCH does not support dynamic assignment of IP addresses Static ARP caches does not support dynamic assignment of IP addresses and detection of destination failures 02/18/2009 11
Insufficiencies of Proposed Solutions n n ARPWATCH does not support dynamic assignment of IP addresses Static ARP caches does not support dynamic assignment of IP addresses and detection of destination failures 02/18/2009 11
 Need for Secure Address Resolution n n When a computer receives a message m, it needs to determine whether m was indeed sent by claimed source, or was inserted, modified, or replayed by an adversary Use secure address resolution protocol between each computer and a secure address resolution server 02/18/2009 12
Need for Secure Address Resolution n n When a computer receives a message m, it needs to determine whether m was indeed sent by claimed source, or was inserted, modified, or replayed by an adversary Use secure address resolution protocol between each computer and a secure address resolution server 02/18/2009 12
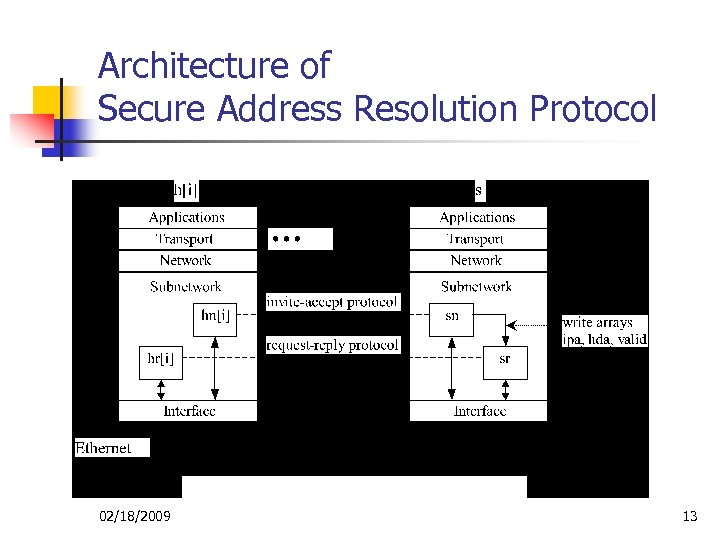 Architecture of Secure Address Resolution Protocol 02/18/2009 13
Architecture of Secure Address Resolution Protocol 02/18/2009 13
 Adversary n Adversary can perform three types of actions to disrupt communication between server s and any computer h[i] on the Ethernet n n n Message loss Message modification Message replay 02/18/2009 14
Adversary n Adversary can perform three types of actions to disrupt communication between server s and any computer h[i] on the Ethernet n n n Message loss Message modification Message replay 02/18/2009 14
 Secure Address Resolution Protocol n Use three mechanisms to counter adversarial actions n n n timeouts to counter message loss shared secrets to counter message modification nonces to counter message replay 02/18/2009 15
Secure Address Resolution Protocol n Use three mechanisms to counter adversarial actions n n n timeouts to counter message loss shared secrets to counter message modification nonces to counter message replay 02/18/2009 15
 Invite-Accept Protocol n n n Periodically, server s sends out an invt message to every computer on Ethernet Every up computer is required to send back an acpt message including its IP address and hardware address s updates its address database according to received acpt messages 02/18/2009 16
Invite-Accept Protocol n n n Periodically, server s sends out an invt message to every computer on Ethernet Every up computer is required to send back an acpt message including its IP address and hardware address s updates its address database according to received acpt messages 02/18/2009 16
![Invite-Accept Protocol s h[0. . n-1]: invt(nc, md) where md=MD(nc; scr[0])||MD(nc; scr[1])||…||MD(nc; scr[n-1]) h[i] Invite-Accept Protocol s h[0. . n-1]: invt(nc, md) where md=MD(nc; scr[0])||MD(nc; scr[1])||…||MD(nc; scr[n-1]) h[i]](https://present5.com/presentation/7cbdd00689ba6a717686e41fdd4decac/image-17.jpg) Invite-Accept Protocol s h[0. . n-1]: invt(nc, md) where md=MD(nc; scr[0])||MD(nc; scr[1])||…||MD(nc; scr[n-1]) h[i] s: acpt(nc, ipa[i], hda[i], d) where d=MD(nc; ipa[i]; hda[i]; scr[i]) 02/18/2009 17
Invite-Accept Protocol s h[0. . n-1]: invt(nc, md) where md=MD(nc; scr[0])||MD(nc; scr[1])||…||MD(nc; scr[n-1]) h[i] s: acpt(nc, ipa[i], hda[i], d) where d=MD(nc; ipa[i]; hda[i]; scr[i]) 02/18/2009 17
 Request-Reply Protocol n n n When a computer needs to resolve a destination’s hardware address, it sends a rqst message to server s If destination’s hardware address is still valid, s sends back a rply message with address information If destination’s hardware address is not valid anymore, s sends back a rply message with no address information 02/18/2009 18
Request-Reply Protocol n n n When a computer needs to resolve a destination’s hardware address, it sends a rqst message to server s If destination’s hardware address is still valid, s sends back a rply message with address information If destination’s hardware address is not valid anymore, s sends back a rply message with no address information 02/18/2009 18
![Request-Reply Protocol h[i] s: rqst(nc, ipa[j], d) where d=MD(nc; ipa[j]; scr[i]) If found, s Request-Reply Protocol h[i] s: rqst(nc, ipa[j], d) where d=MD(nc; ipa[j]; scr[i]) If found, s](https://present5.com/presentation/7cbdd00689ba6a717686e41fdd4decac/image-19.jpg) Request-Reply Protocol h[i] s: rqst(nc, ipa[j], d) where d=MD(nc; ipa[j]; scr[i]) If found, s h[i]: rply(nc, ipa[j], hda[j], d) where d=MD(nc; ipa[j]; hda[j]; scr[i]) If not found, s h[i]: rply(nc, ipa[j], 0, d) where d=MD(nc; ipa[j]; 0; scr[i]) 02/18/2009 19
Request-Reply Protocol h[i] s: rqst(nc, ipa[j], d) where d=MD(nc; ipa[j]; scr[i]) If found, s h[i]: rply(nc, ipa[j], hda[j], d) where d=MD(nc; ipa[j]; hda[j]; scr[i]) If not found, s h[i]: rply(nc, ipa[j], 0, d) where d=MD(nc; ipa[j]; 0; scr[i]) 02/18/2009 19
 Extensions n Four extensions of secure address resolution protocol n n Insecure address resolution Backup server System diagnosis Address resolution across multiple Ethernets 02/18/2009 20
Extensions n Four extensions of secure address resolution protocol n n Insecure address resolution Backup server System diagnosis Address resolution across multiple Ethernets 02/18/2009 20
 Next Class n IPsec n n Authentication Header (AH) Encapsulation Security Payload (ESP) key management Read Chapter 16 02/18/2009 21
Next Class n IPsec n n Authentication Header (AH) Encapsulation Security Payload (ESP) key management Read Chapter 16 02/18/2009 21


