1c56599071f2c1ce14839b4ba0659e93.ppt
- Количество слайдов: 32
 CS 854 – Hot Topics in Computer and Communications Security Fall 2006 Introduction to Cryptography and Security II 1
CS 854 – Hot Topics in Computer and Communications Security Fall 2006 Introduction to Cryptography and Security II 1
 Announcements r First paper review is due on Monday v Review one of the two mandatory papers v FYI, I am the co-author of one of them 2
Announcements r First paper review is due on Monday v Review one of the two mandatory papers v FYI, I am the co-author of one of them 2
 Digital Signatures Cryptographic technique analogous to handwritten signatures. r sender (Bob) digitally signs document, establishing he is document owner/creator. r verifiable, nonforgeable, nonrepudiable: recipient (Alice) can prove to third party that Bob, and no one else (including Alice), must have signed document r message integrity does not always require nonrepudiation v See later 3
Digital Signatures Cryptographic technique analogous to handwritten signatures. r sender (Bob) digitally signs document, establishing he is document owner/creator. r verifiable, nonforgeable, nonrepudiable: recipient (Alice) can prove to third party that Bob, and no one else (including Alice), must have signed document r message integrity does not always require nonrepudiation v See later 3
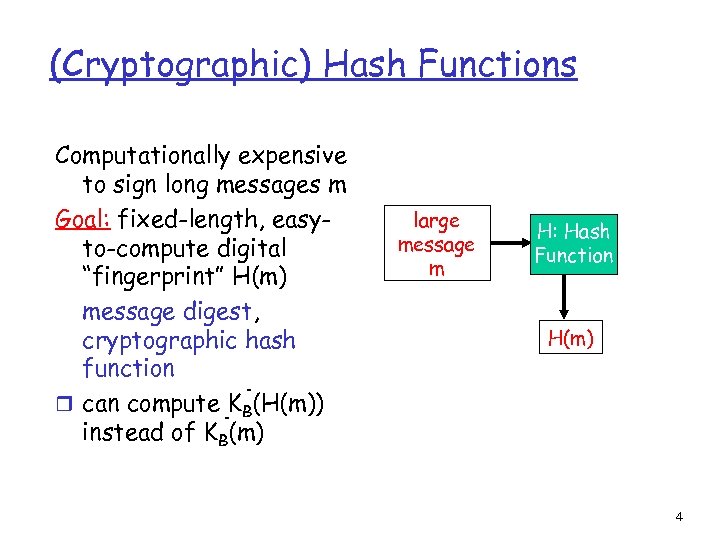 (Cryptographic) Hash Functions Computationally expensive to sign long messages m Goal: fixed-length, easyto-compute digital “fingerprint” H(m) message digest, cryptographic hash function r can compute KB(H(m)) instead of KB(m) large message m H: Hash Function H(m) 4
(Cryptographic) Hash Functions Computationally expensive to sign long messages m Goal: fixed-length, easyto-compute digital “fingerprint” H(m) message digest, cryptographic hash function r can compute KB(H(m)) instead of KB(m) large message m H: Hash Function H(m) 4
 Properties of H(m) r Input: arbitrarily long string of bits r Output: fixed-size (i. e. , H() is many to one) r Given m, easy to compute H(m) r One-way property/pre-image resistant v For any given value x, it is computationally infeasible to find m such that H(m) = x r Weak-collision resistance/2 nd pre-image resistant v For any given message m 1, it is computationally infeasible to find m 2 such that H(m 1) = H(m 2) r Strong-collision resistance/collision resistance v It is computationally infeasible to find a pair (m 1, m 2) such that H(m 1) = H(m 2) 5
Properties of H(m) r Input: arbitrarily long string of bits r Output: fixed-size (i. e. , H() is many to one) r Given m, easy to compute H(m) r One-way property/pre-image resistant v For any given value x, it is computationally infeasible to find m such that H(m) = x r Weak-collision resistance/2 nd pre-image resistant v For any given message m 1, it is computationally infeasible to find m 2 such that H(m 1) = H(m 2) r Strong-collision resistance/collision resistance v It is computationally infeasible to find a pair (m 1, m 2) such that H(m 1) = H(m 2) 5
 Does collision resistance imply preimage resistance? r Alfred Menezes: No 1 v G(x) is collision resistant hash function with nbit output v H(x) = 1 || x if x has bitlength n v 0 || G(x) otherwise v H(x) is collision resistant, but not preimage resistant r Doug Stinson: Yes 2 v In Random Oracle Model v Under certain circumstances (e. g. , uniform hash 1 Handbook of Applied Cryptography function) 2 Some observations on theory of cryptographic hash functions 6
Does collision resistance imply preimage resistance? r Alfred Menezes: No 1 v G(x) is collision resistant hash function with nbit output v H(x) = 1 || x if x has bitlength n v 0 || G(x) otherwise v H(x) is collision resistant, but not preimage resistant r Doug Stinson: Yes 2 v In Random Oracle Model v Under certain circumstances (e. g. , uniform hash 1 Handbook of Applied Cryptography function) 2 Some observations on theory of cryptographic hash functions 6
 Message Authentication Code (MAC) r MAC allows Alice and Bob to communicate such that each of them can be sure that received messages were not tampered with v no non-repudiation r Keyed hash function can be used for implementing MAC v v v e. g. , x = SHA-1(k||m), transmit m and x only Alice and Bob know k not secure against length-extension attack r HMAC = H(k XOR a || H(k XOR b || m)) a, b: specified constants H: preferably SHA-256 7
Message Authentication Code (MAC) r MAC allows Alice and Bob to communicate such that each of them can be sure that received messages were not tampered with v no non-repudiation r Keyed hash function can be used for implementing MAC v v v e. g. , x = SHA-1(k||m), transmit m and x only Alice and Bob know k not secure against length-extension attack r HMAC = H(k XOR a || H(k XOR b || m)) a, b: specified constants H: preferably SHA-256 7
 Entity Authentication r Prove that you are who you claim to be r Based on v what you know • password v what you own • badge v what you are • fingerprint 8
Entity Authentication r Prove that you are who you claim to be r Based on v what you know • password v what you own • badge v what you are • fingerprint 8
 Passwords r User enters password, computer compares it with password in file r Bad if file gets stolen r Store only password hashes in file v v Use salt to avoid dictionary attacks due to weak passwords E. g. , UNIX r Susceptible to replay attacks if attacker can sniff traffic exchanged between user and computer v v v Use secure channel (e. g. , SSL, see later) Challenge-response protocols Zero-knowledge protocols 9
Passwords r User enters password, computer compares it with password in file r Bad if file gets stolen r Store only password hashes in file v v Use salt to avoid dictionary attacks due to weak passwords E. g. , UNIX r Susceptible to replay attacks if attacker can sniff traffic exchanged between user and computer v v v Use secure channel (e. g. , SSL, see later) Challenge-response protocols Zero-knowledge protocols 9
 Overview r Network security r Symmetric-key encryption r Public-key encryption r Message integrity and authentication r Entity authentication r Key distribution r Computer security 10
Overview r Network security r Symmetric-key encryption r Public-key encryption r Message integrity and authentication r Entity authentication r Key distribution r Computer security 10
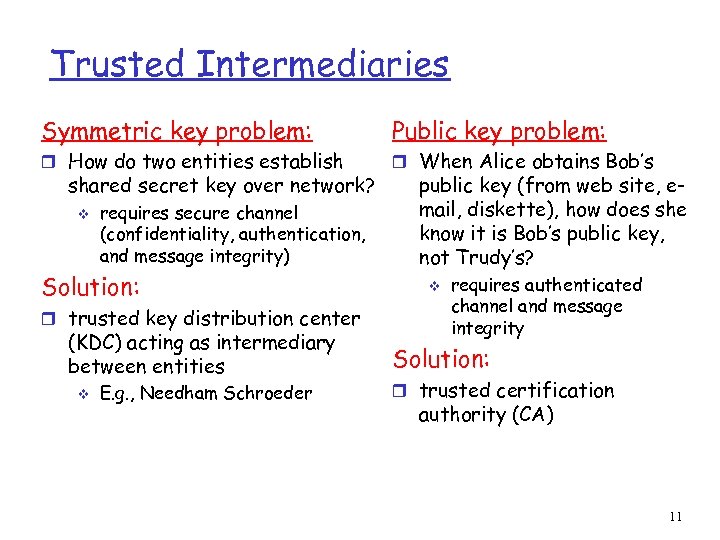 Trusted Intermediaries Symmetric key problem: Public key problem: r How do two entities establish r When Alice obtains Bob’s shared secret key over network? v requires secure channel (confidentiality, authentication, and message integrity) Solution: r trusted key distribution center (KDC) acting as intermediary between entities v E. g. , Needham Schroeder public key (from web site, email, diskette), how does she know it is Bob’s public key, not Trudy’s? v requires authenticated channel and message integrity Solution: r trusted certification authority (CA) 11
Trusted Intermediaries Symmetric key problem: Public key problem: r How do two entities establish r When Alice obtains Bob’s shared secret key over network? v requires secure channel (confidentiality, authentication, and message integrity) Solution: r trusted key distribution center (KDC) acting as intermediary between entities v E. g. , Needham Schroeder public key (from web site, email, diskette), how does she know it is Bob’s public key, not Trudy’s? v requires authenticated channel and message integrity Solution: r trusted certification authority (CA) 11
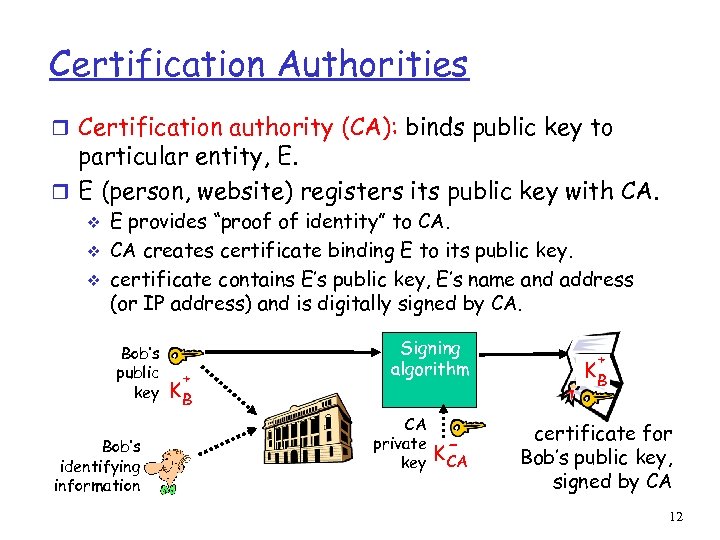 Certification Authorities r Certification authority (CA): binds public key to particular entity, E. r E (person, website) registers its public key with CA. v v v E provides “proof of identity” to CA. CA creates certificate binding E to its public key. certificate contains E’s public key, E’s name and address (or IP address) and is digitally signed by CA. Bob’s public key Bob’s identifying information + KB Signing algorithm CA private key K- CA + KB certificate for Bob’s public key, signed by CA 12
Certification Authorities r Certification authority (CA): binds public key to particular entity, E. r E (person, website) registers its public key with CA. v v v E provides “proof of identity” to CA. CA creates certificate binding E to its public key. certificate contains E’s public key, E’s name and address (or IP address) and is digitally signed by CA. Bob’s public key Bob’s identifying information + KB Signing algorithm CA private key K- CA + KB certificate for Bob’s public key, signed by CA 12
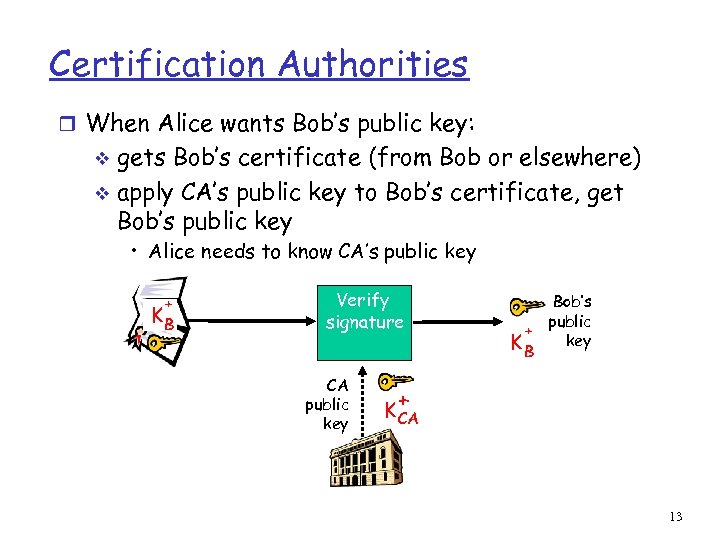 Certification Authorities r When Alice wants Bob’s public key: gets Bob’s certificate (from Bob or elsewhere) v apply CA’s public key to Bob’s certificate, get Bob’s public key v • Alice needs to know CA’s public key + KB Verify signature CA public key Bob’s public + key KB + K CA 13
Certification Authorities r When Alice wants Bob’s public key: gets Bob’s certificate (from Bob or elsewhere) v apply CA’s public key to Bob’s certificate, get Bob’s public key v • Alice needs to know CA’s public key + KB Verify signature CA public key Bob’s public + key KB + K CA 13
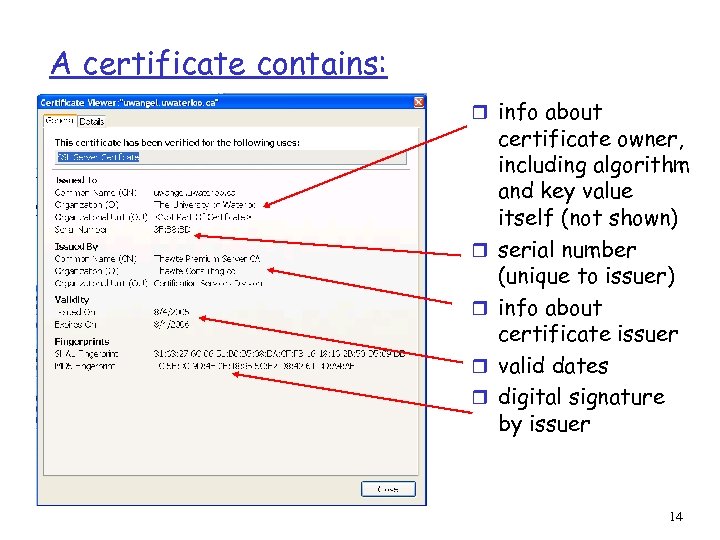 A certificate contains: r info about r r certificate owner, including algorithm and key value itself (not shown) serial number (unique to issuer) info about certificate issuer valid dates digital signature by issuer 14
A certificate contains: r info about r r certificate owner, including algorithm and key value itself (not shown) serial number (unique to issuer) info about certificate issuer valid dates digital signature by issuer 14
 SSL (Secure Socket Layer) r transport-layer security service r originally developed by Netscape r subsequently became Internet standard known as TLS (Transport Layer Security) r uses TCP to provide a reliable end-to-end service r server authentication v v v browser includes public keys for trusted CAs. • check your browser receives server certificate, issued by trusted CA, from server browser uses CA’s public key to validate certificate r client authentication v possible but typically applications use other means 15
SSL (Secure Socket Layer) r transport-layer security service r originally developed by Netscape r subsequently became Internet standard known as TLS (Transport Layer Security) r uses TCP to provide a reliable end-to-end service r server authentication v v v browser includes public keys for trusted CAs. • check your browser receives server certificate, issued by trusted CA, from server browser uses CA’s public key to validate certificate r client authentication v possible but typically applications use other means 15
 SSL Services r message integrity v using a MAC with shared secret key v similar to HMAC but with different padding r confidentiality v using symmetric encryption with a shared secret key defined by Handshake Protocol v AES, IDEA, RC 2 -40, DES, 3 DES, Fortezza, RC 4 -40, RC 4 -128 v message is compressed before encryption 16
SSL Services r message integrity v using a MAC with shared secret key v similar to HMAC but with different padding r confidentiality v using symmetric encryption with a shared secret key defined by Handshake Protocol v AES, IDEA, RC 2 -40, DES, 3 DES, Fortezza, RC 4 -40, RC 4 -128 v message is compressed before encryption 16
 SSL Handshake Protocol r allows server & client to: v v v r authenticate each other to negotiate encryption & MAC algorithms to negotiate cryptographic keys to be used comprises a series of messages in phases 1. 2. 3. 4. Establish Security Capabilities Server Authentication and Key Exchange Client Authentication and Key Exchange Finish 17
SSL Handshake Protocol r allows server & client to: v v v r authenticate each other to negotiate encryption & MAC algorithms to negotiate cryptographic keys to be used comprises a series of messages in phases 1. 2. 3. 4. Establish Security Capabilities Server Authentication and Key Exchange Client Authentication and Key Exchange Finish 17
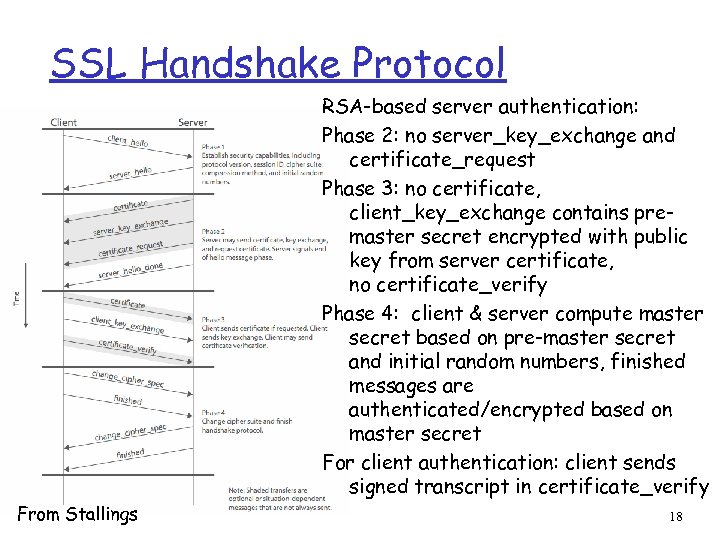 SSL Handshake Protocol RSA-based server authentication: Phase 2: no server_key_exchange and certificate_request Phase 3: no certificate, client_key_exchange contains premaster secret encrypted with public key from server certificate, no certificate_verify Phase 4: client & server compute master secret based on pre-master secret and initial random numbers, finished messages are authenticated/encrypted based on master secret For client authentication: client sends signed transcript in certificate_verify From Stallings 18
SSL Handshake Protocol RSA-based server authentication: Phase 2: no server_key_exchange and certificate_request Phase 3: no certificate, client_key_exchange contains premaster secret encrypted with public key from server certificate, no certificate_verify Phase 4: client & server compute master secret based on pre-master secret and initial random numbers, finished messages are authenticated/encrypted based on master secret For client authentication: client sends signed transcript in certificate_verify From Stallings 18
 SSL/TLS: Good Practices r never enter confidential information (e. g. , password) into a Web page that does not have URL starting with https: //. . . v even when the Web page says that it’s secure nonetheless… r pay attention to popup/warning messages related to SSL or certificates messages can be cryptic… v see usability section later in course v but now you can understand these messages v 19
SSL/TLS: Good Practices r never enter confidential information (e. g. , password) into a Web page that does not have URL starting with https: //. . . v even when the Web page says that it’s secure nonetheless… r pay attention to popup/warning messages related to SSL or certificates messages can be cryptic… v see usability section later in course v but now you can understand these messages v 19
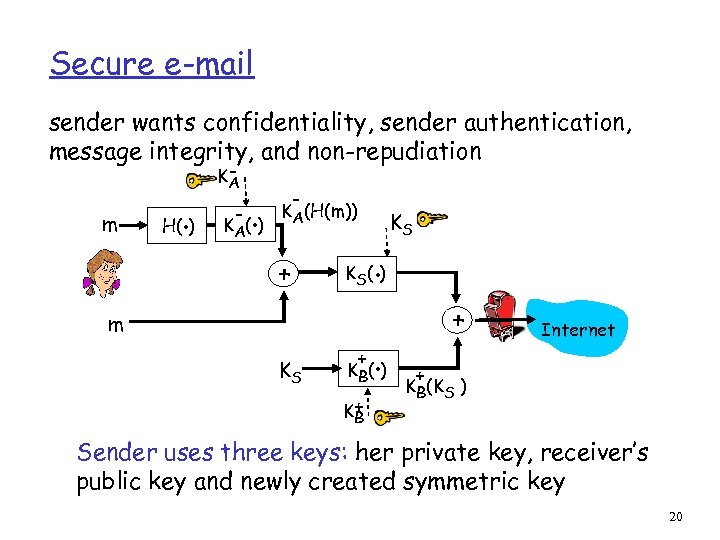 Secure e-mail sender wants confidentiality, sender authentication, message integrity, and non-repudiation m . H( ) KA - . K A( ) - KA(H(m)) + . K S( ) m KS KS + . K B( ) K+ B + Internet + KB(KS ) Sender uses three keys: her private key, receiver’s public key and newly created symmetric key 20
Secure e-mail sender wants confidentiality, sender authentication, message integrity, and non-repudiation m . H( ) KA - . K A( ) - KA(H(m)) + . K S( ) m KS KS + . K B( ) K+ B + Internet + KB(KS ) Sender uses three keys: her private key, receiver’s public key and newly created symmetric key 20
 Pretty Good Privacy (PGP) r widely used secure-email application r developed by Phil Zimmermann, was target of 3 - year federal investigation in USA r selected best available crypto algorithms to use r uses symmetric key cryptography, public key cryptography, hash function, and digital signature as described. r integrated into a single program, easy to use v not always, see usability section later in course r on Unix, PC, Macintosh and other systems r originally free, now also have commercial versions available 21
Pretty Good Privacy (PGP) r widely used secure-email application r developed by Phil Zimmermann, was target of 3 - year federal investigation in USA r selected best available crypto algorithms to use r uses symmetric key cryptography, public key cryptography, hash function, and digital signature as described. r integrated into a single program, easy to use v not always, see usability section later in course r on Unix, PC, Macintosh and other systems r originally free, now also have commercial versions available 21
 PGP Key Management r no centralized CA, every user is own CA v can sign keys for users they know directly r key servers collect/distribute (signed) public keys r forms a “web of trust” v fully trust keys that I have signed v (partially) trust keys others have signed if have a chain of signatures to them r locally stored public keys are associated with trust indicators v v I fully trust Bob (his public key) to sign keys I partially trust Alice (her public key) to sign keys r users can also revoke their keys 22
PGP Key Management r no centralized CA, every user is own CA v can sign keys for users they know directly r key servers collect/distribute (signed) public keys r forms a “web of trust” v fully trust keys that I have signed v (partially) trust keys others have signed if have a chain of signatures to them r locally stored public keys are associated with trust indicators v v I fully trust Bob (his public key) to sign keys I partially trust Alice (her public key) to sign keys r users can also revoke their keys 22
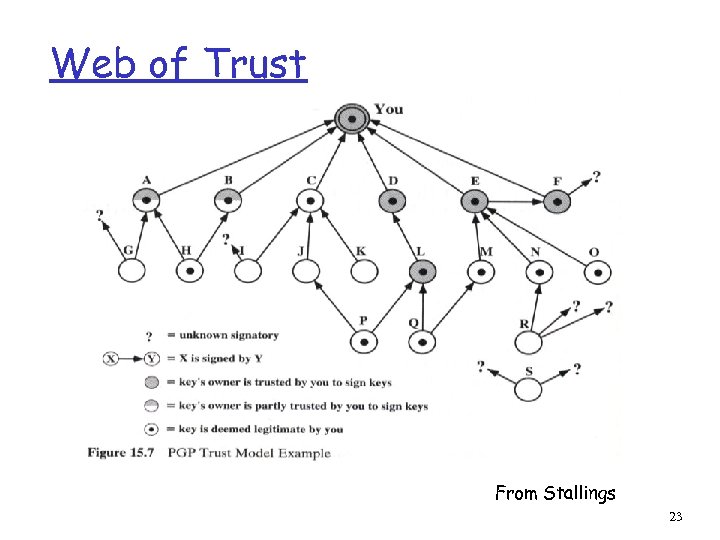 Web of Trust From Stallings 23
Web of Trust From Stallings 23
 Overview r Network security r Symmetric-key encryption r Public-key encryption r Message integrity and authentication r Entity authentication r Key distribution r Computer security 24
Overview r Network security r Symmetric-key encryption r Public-key encryption r Message integrity and authentication r Entity authentication r Key distribution r Computer security 24
 Access Control r Different levels v Applications (e. g. , database) v Operating system v Hardware r Access control matrix v Rows list resources, columns list people, entries list kind of access (read, write, execute, …) v Access control lists (ACLs): column-wise implementation • List of people that can access a resource v Capabilities: row-wise implementation • List of resources that a person can access v Hybrid • ACL upon first access, capability subsequently 25
Access Control r Different levels v Applications (e. g. , database) v Operating system v Hardware r Access control matrix v Rows list resources, columns list people, entries list kind of access (read, write, execute, …) v Access control lists (ACLs): column-wise implementation • List of people that can access a resource v Capabilities: row-wise implementation • List of resources that a person can access v Hybrid • ACL upon first access, capability subsequently 25
 Multilevel Security r Information has different levels of classification v Confidential, secret, top secret, … r Very well researched due to military funding r Security policy: Clearly and concisely expresses goals of protection mechanism v Confidentiality • To whom can what information be disclosed v Integrity • Who is allowed to modify what information 26
Multilevel Security r Information has different levels of classification v Confidential, secret, top secret, … r Very well researched due to military funding r Security policy: Clearly and concisely expresses goals of protection mechanism v Confidentiality • To whom can what information be disclosed v Integrity • Who is allowed to modify what information 26
 Bell-La. Padula Security Policy Model r Proposed in 1973 r Simple security property v No process may read data at a higher level v No read up (NRU) v People cleared to ‘confidential’ cannot access top secret data r *-property v No process may write to a lower level v No write down (NRW) v Process running as ‘top secret’ cannot write files at ‘confidential’ level (maybe inadvertently) r Mandatory access control v As opposed to discretionary access control 27
Bell-La. Padula Security Policy Model r Proposed in 1973 r Simple security property v No process may read data at a higher level v No read up (NRU) v People cleared to ‘confidential’ cannot access top secret data r *-property v No process may write to a lower level v No write down (NRW) v Process running as ‘top secret’ cannot write files at ‘confidential’ level (maybe inadvertently) r Mandatory access control v As opposed to discretionary access control 27
 Biba Integrity Model r Proposed in 1977 r Ignores confidentiality r Low water mark principle: integrity of an object is the lowest level of all objects that contributed to its creation r Later in course: (Remotely) proving integrity of a computer (e. g. , no virus) 28
Biba Integrity Model r Proposed in 1977 r Ignores confidentiality r Low water mark principle: integrity of an object is the lowest level of all objects that contributed to its creation r Later in course: (Remotely) proving integrity of a computer (e. g. , no virus) 28
 Other Aspects of Computer Security r Covert channels v Later in course r Software security v Buffer overflows v Cross-site scripting vulnerabilities v Later in course r Auditing r Intrusion detection and recovery r Computer forensics 29
Other Aspects of Computer Security r Covert channels v Later in course r Software security v Buffer overflows v Cross-site scripting vulnerabilities v Later in course r Auditing r Intrusion detection and recovery r Computer forensics 29
 Cryptography/Security Books r Mark Stamp, Information Security r Doug Stinson, Cryptography r Bruce Schneier, Applied Cryptography r Ross Anderson, Security Engineering http: //www. cl. cam. ac. uk/~rja 14/book. html r Viega & Mc. Graw, Building Secure Software r Cranor & Garfinkel, Security and Usability 30
Cryptography/Security Books r Mark Stamp, Information Security r Doug Stinson, Cryptography r Bruce Schneier, Applied Cryptography r Ross Anderson, Security Engineering http: //www. cl. cam. ac. uk/~rja 14/book. html r Viega & Mc. Graw, Building Secure Software r Cranor & Garfinkel, Security and Usability 30
 Current/Upcoming Cryptography/Security Courses r Fall 2006: v C&O 685: The Mathematics of Public-Key Cryptography r Winter 2007: v CS 758: Cryptography/Network Security r Fall 2007 (planned): v CS 698 – Computer/Networks Security 31
Current/Upcoming Cryptography/Security Courses r Fall 2006: v C&O 685: The Mathematics of Public-Key Cryptography r Winter 2007: v CS 758: Cryptography/Network Security r Fall 2007 (planned): v CS 698 – Computer/Networks Security 31
 Conferences of Interest r Security: USENIX Security, ACM CCS, IEEE Security & Privacy, NDSS, Secure. Comm r Privacy: PET, WPES, SOUPS r Economics: WEIS r Usability: SOUPS, CHI r Pervasive computing: Ubi. Comp, Per. Com, Pervasive, Per. Sec 32
Conferences of Interest r Security: USENIX Security, ACM CCS, IEEE Security & Privacy, NDSS, Secure. Comm r Privacy: PET, WPES, SOUPS r Economics: WEIS r Usability: SOUPS, CHI r Pervasive computing: Ubi. Comp, Per. Com, Pervasive, Per. Sec 32


