65100e8aae4285aa2172926baee9d242.ppt
- Количество слайдов: 43

CS 6431 Security Issues in Web Applications Vitaly Shmatikov
User Input Validation [Bisht et al. “No. Tamper: Automatic Blackbox Detection of Parameter Tampering Opportunities in Web Applications”. CCS 2010] u. Web applications need to reject invalid inputs • “Credit card number should be 15 or 16 digits” • “Expiration date in the past is not valid” u. Traditionally done at the server • Round-trip communication, increased load u. Better idea (? ): do it in the browser using client-side Java. Script code slide 2
![Client-Side Validation [Bisht et al. ] on. Submit= validate. Card(); validate. Quantities(); Validation Ok? Client-Side Validation [Bisht et al. ] on. Submit= validate. Card(); validate. Quantities(); Validation Ok?](https://present5.com/presentation/65100e8aae4285aa2172926baee9d242/image-3.jpg)
Client-Side Validation [Bisht et al. ] on. Submit= validate. Card(); validate. Quantities(); Validation Ok? Yes No send inputs to server reject inputs slide 3
![Problem: Client Is Untrusted [Bisht et al. ] Previously rejected values sent to server Problem: Client Is Untrusted [Bisht et al. ] Previously rejected values sent to server](https://present5.com/presentation/65100e8aae4285aa2172926baee9d242/image-4.jpg)
Problem: Client Is Untrusted [Bisht et al. ] Previously rejected values sent to server Inputs must be re-validated at server! slide 4
![Online Shopping [Bisht et al. ] Code. Micro. com Client-side constraints: quantity 1 ≥ Online Shopping [Bisht et al. ] Code. Micro. com Client-side constraints: quantity 1 ≥](https://present5.com/presentation/65100e8aae4285aa2172926baee9d242/image-5.jpg)
Online Shopping [Bisht et al. ] Code. Micro. com Client-side constraints: quantity 1 ≥ 0 quantity 2 ≥ 0 Server-side code: total = quantity 1 * price 1 + quantity 2 * price 2 Vulnerability: malicious client submits negative quantities for unlimited shopping rebates Two items in cart: price 1 = $100, price 2 = $500 quantity 1 = -4, quantity 2 = 1, total = $100 (rebate of $400 on price 2) slide 5
![Online Banking [Bisht et al. ] Self. Reliance. com Client-side constraints: from IN (Accnt Online Banking [Bisht et al. ] Self. Reliance. com Client-side constraints: from IN (Accnt](https://present5.com/presentation/65100e8aae4285aa2172926baee9d242/image-6.jpg)
Online Banking [Bisht et al. ] Self. Reliance. com Client-side constraints: from IN (Accnt 1, Accnt 2) to IN (Accnt 1, Accnt 2) Server-side code: transfer money from to Vulnerability: malicious client submits arbitrary account numbers for unauthorized money transfers slide 6
![IT Support [Bisht et al. ] Client-side constraints: user. Id == 96 (hidden field) IT Support [Bisht et al. ] Client-side constraints: user. Id == 96 (hidden field)](https://present5.com/presentation/65100e8aae4285aa2172926baee9d242/image-7.jpg)
IT Support [Bisht et al. ] Client-side constraints: user. Id == 96 (hidden field) Hidden Field Server-side code: Update profile with id 96 with new details Vulnerability: update arbitrary account Inject a cross-site scripting (XSS) payload in admin account, cookies stolen every time admin logged in slide 7
![Content Management [Bisht et al. ] Server-side code: privilege = non-admin; if ( _COOKIE[‘make_install_prn’] Content Management [Bisht et al. ] Server-side code: privilege = non-admin; if ( _COOKIE[‘make_install_prn’]](https://present5.com/presentation/65100e8aae4285aa2172926baee9d242/image-8.jpg)
Content Management [Bisht et al. ] Server-side code: privilege = non-admin; if ( _COOKIE[‘make_install_prn’] == 1 ) privilege = admin; Vulnerability: malicious client sets make_install_prn cookie, creates fake admin account slide 8
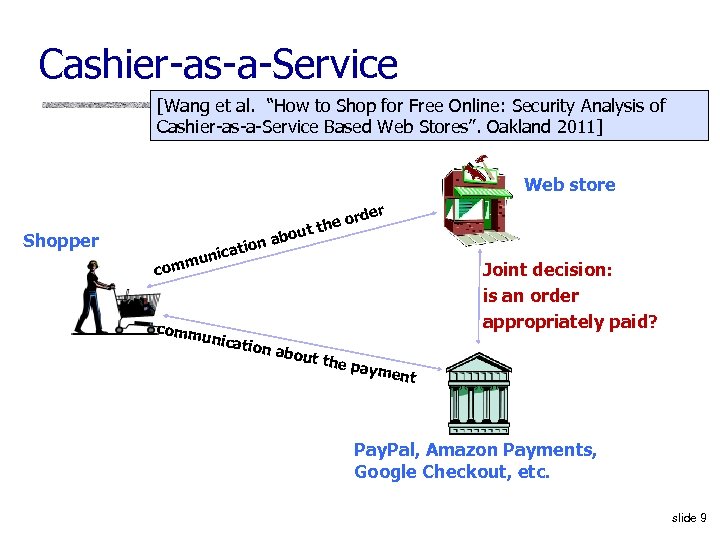
Cashier-as-a-Service [Wang et al. “How to Shop for Free Online: Security Analysis of Cashier-as-a-Service Based Web Stores”. Oakland 2011] Web store rder eo ut th bo Shopper on a icati un m com Joint decision: is an order appropriately paid? comm unica tion a bout t h e pay ment Pay. Pal, Amazon Payments, Google Checkout, etc. slide 9
![nop. Commerce + Amazon Simple Pay [Wang et al. ] u Anyone can register nop. Commerce + Amazon Simple Pay [Wang et al. ] u Anyone can register](https://present5.com/presentation/65100e8aae4285aa2172926baee9d242/image-10.jpg)
nop. Commerce + Amazon Simple Pay [Wang et al. ] u Anyone can register an Amazon seller account, so can Chuck • Purchase a $25 Master. Card gift card by cash, register under a fake address and phone number • Create seller accounts in Pay. Pal, Amazon and Google using the card u Chuck’s trick • Check out from Jeff, but pay to “Mark” (Chuck himself) • Amazon tells Jeff that payment has been successful • Jeff is confused, ships product Chuck, pay in Amazon with this signed letter: Amazon, I want to pay Dear Amazon, with this letter Great, I will ship order#123 is $10, when it is Dear Amazon, order#123! Jeff, paid, text me at 425 -111 -2222. order#123 is $10, when it is I want to buy this [Jeff’s signature] paid, text me at 425 -111 DVD. 2222. [Jeff’s signature] [Mark’s signature] Jeff Hi, $10 has been paid for order#123. [Amazon’s signature] Shopper Chuck (and seller Mark) Amazon (Caa. S) slide 10
![Interspire + Pay. Pal Express [Wang et al. ] Session 1: pay for a Interspire + Pay. Pal Express [Wang et al. ] Session 1: pay for a](https://present5.com/presentation/65100e8aae4285aa2172926baee9d242/image-11.jpg)
Interspire + Pay. Pal Express [Wang et al. ] Session 1: pay for a cheap order (order. ID 1), Session 2: place an expensive order but prevent the merchant from finalizing it (order. ID 2) , but skip the payment step by holding Message B store Message A Message B Message A redirects to store. com/finalize. Order? [order. ID 1]store Message A redirects to store. com/finalize. Order? [order. ID 2]store Message B calls store. com/finalize. Order? [order. ID 1]store [order. ID 2]store Expensive order is checked out but the cheap one is paid! slide 11
Side-Channel Leaks [Chen et al. “Side-Channel Leaks in Web Applications: a Reality Today, a Challenge Tomorrow”. Oakland 2010] encrypted! privacy problems solved? Attacker can still see the number of packets, size of each packet, time between packets… slide 12
![[Chen et al. ] u. Search using encrypted Wi-Fi (WPA / WPA 2) u. [Chen et al. ] u. Search using encrypted Wi-Fi (WPA / WPA 2) u.](https://present5.com/presentation/65100e8aae4285aa2172926baee9d242/image-13.jpg)
[Chen et al. ] u. Search using encrypted Wi-Fi (WPA / WPA 2) u. Example: user types “l-i-s-t” on his laptop… …different size of suggestion list 821 910 Each additional letter of query… 822 ery stio Qu gge su n 931 823 824 995 1007 Attacker’s effort linear in the size of query Consequence: any eavesdropper knows our search queries slide 13
![Online Medical Application [Chen et al. ] u. Entering health records • By typing Online Medical Application [Chen et al. ] u. Entering health records • By typing](https://present5.com/presentation/65100e8aae4285aa2172926baee9d242/image-14.jpg)
Online Medical Application [Chen et al. ] u. Entering health records • By typing – auto-suggestion • By mouse – a tree structure of elements u. Finding a doctor • Dropdown list 2000 x reduction in ambiguity Uniquely identify the specialty slide 14
![Tax Preparation Application [Chen et al. ] u. Wizard-style questionnaire • Tailor the questions Tax Preparation Application [Chen et al. ] u. Wizard-style questionnaire • Tailor the questions](https://present5.com/presentation/65100e8aae4285aa2172926baee9d242/image-15.jpg)
Tax Preparation Application [Chen et al. ] u. Wizard-style questionnaire • Tailor the questions based on previous inputs u. Which forms you work on reveal filing status, big medical bills, adjusted gross income… u. Knowing the state machine of the application the eavesdropper can infer sensitive information • Especially by combining information learned from multiple state machines slide 15
![Child Credit State Machine [Chen et al. ] Entry page of deductions & credits Child Credit State Machine [Chen et al. ] Entry page of deductions & credits](https://present5.com/presentation/65100e8aae4285aa2172926baee9d242/image-16.jpg)
Child Credit State Machine [Chen et al. ] Entry page of deductions & credits All transitions have unique traffic patterns Summary of deductions & credits Partial credit Not eligible Full credit Consult the IRS instruction: $1000 for each child Phase-out starting from $110, 000. For every $1000 income, lose $50 credit. slide 16
![Student Loan Interest State Machine [Chen et al. ] Even worse, most decision procedures Student Loan Interest State Machine [Chen et al. ] Even worse, most decision procedures](https://present5.com/presentation/65100e8aae4285aa2172926baee9d242/image-17.jpg)
Student Loan Interest State Machine [Chen et al. ] Even worse, most decision procedures for credits/deductions have asymmetric paths: eligible – more questions, not eligible – no more questions Entry page of deductions & credits Summary of deductions & credits Not eligible Enter your paid interest Partial credit Full credit slide 17
![Some Identifiable AGI Thresholds [Chen et al. ] Disabled Credit $0 Earned Income Credit Some Identifiable AGI Thresholds [Chen et al. ] Disabled Credit $0 Earned Income Credit](https://present5.com/presentation/65100e8aae4285aa2172926baee9d242/image-18.jpg)
Some Identifiable AGI Thresholds [Chen et al. ] Disabled Credit $0 Earned Income Credit $24999 Retirement Savings College Expense $41646 $53000 $116000 IRA Contribution Student Loan Interest Child Credit First-time Homebuyer Credit Adoption Expense $85000 $105000 $110000 $145000 $130000 or $150000 or $170000 … $150000 $174730 $214780 slide 18
![Online Investments [Chen et al. ] Which funds you invest in? u Each price Online Investments [Chen et al. ] Which funds you invest in? u Each price](https://present5.com/presentation/65100e8aae4285aa2172926baee9d242/image-19.jpg)
Online Investments [Chen et al. ] Which funds you invest in? u Each price history curve is a GIF image from Market. Watch • Anyone in the world can get them from this website u Just compare the image sizes! Your investment allocation? u Can see the size of the pie chart, but hundreds of pie charts have the same image… slide 19
![Change Over Time Is Revealing! [Chen et al. ] 800 charts 8 charts Size Change Over Time Is Revealing! [Chen et al. ] 800 charts 8 charts Size](https://present5.com/presentation/65100e8aae4285aa2172926baee9d242/image-20.jpg)
Change Over Time Is Revealing! [Chen et al. ] 800 charts 8 charts Size of day 4; Prices of the day Size of day 3; Prices of the day Size of day 2; Prices of the day Size of day 1 80000 charts Financial institution updates your pie chart every day after market close. Mutual fund prices are public knowledge. 1 chart slide 20
![Rounding? Padding? [Chen et al. ] u. Still have the asymmetric path problem u. Rounding? Padding? [Chen et al. ] u. Still have the asymmetric path problem u.](https://present5.com/presentation/65100e8aae4285aa2172926baee9d242/image-21.jpg)
Rounding? Padding? [Chen et al. ] u. Still have the asymmetric path problem u. Google’s responses are compressed, destination networks may or may not uncompress responses • For example, Microsoft gateways uncompress and inspect Web traffic, but university does not • Round before compression – university still sees distinguishable sizes; after compression – Microsoft does u. Random padding is not appropriate • If user checks several times, repeated random padding of the same responses quickly degrades effectiveness • Images come from Market. Watch, not site itself slide 21
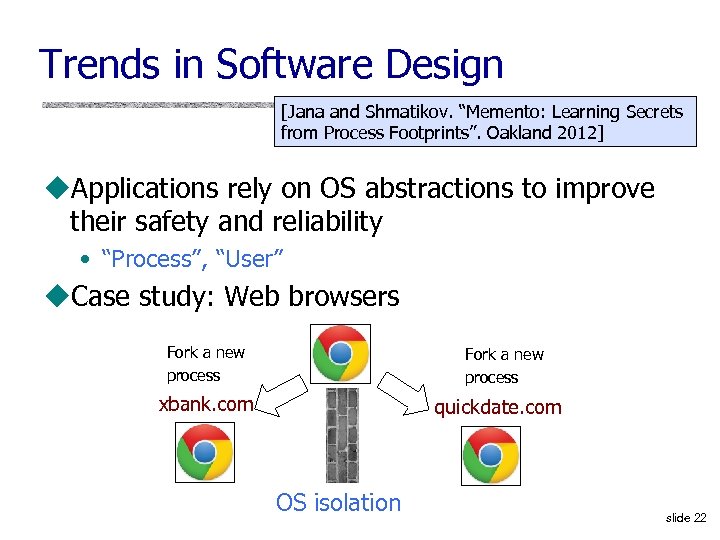
Trends in Software Design [Jana and Shmatikov. “Memento: Learning Secrets from Process Footprints”. Oakland 2012] u. Applications rely on OS abstractions to improve their safety and reliability • “Process”, “User” u. Case study: Web browsers Fork a new process xbank. com quickdate. com OS isolation slide 22
Unintended Consequences Good Bad • Better isolation Leaks more info to concurrent processes • Better reliability – Others not affected if one process crashes • Better safety slide 23
Proc. FS in Multi-User OS cat /proc/1/ status ps top –p 1 Introduced in the 1980 s Tom Killian "Processes as Files” (1984) slide 24

“Noone Uses Multi-User OS Anymore” slide 25
Multi-User Isolation ps top –p 1 cat /proc/1/ status UNIX multi-users in the 1980 s slide 26
Android Sandboxing ps top –p 1 cat /proc/1/ status Android “multi-users” today slide 27
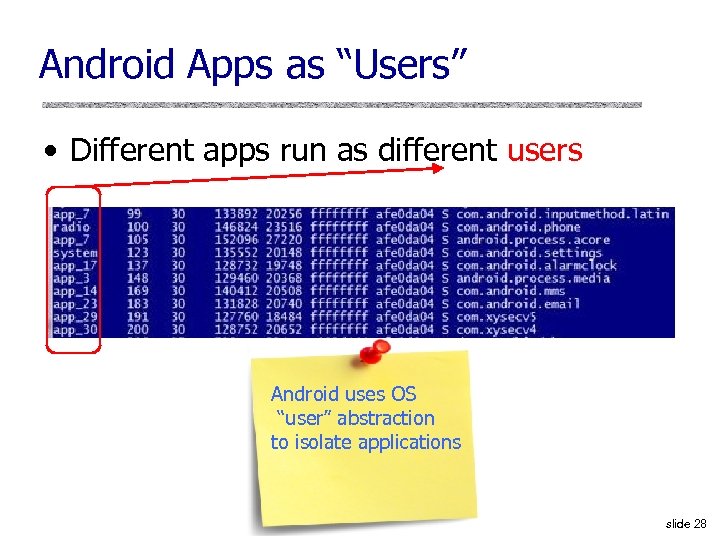
Android Apps as “Users” • Different apps run as different users Android uses OS “user” abstraction to isolate applications slide 28
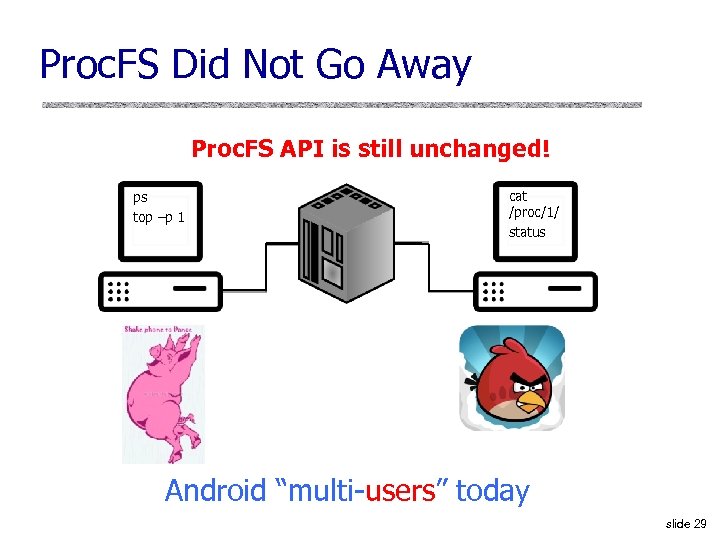
Proc. FS Did Not Go Away Proc. FS API is still unchanged! ps top –p 1 cat /proc/1/ status Android “multi-users” today slide 29
This Is Not Just About Android slide 30
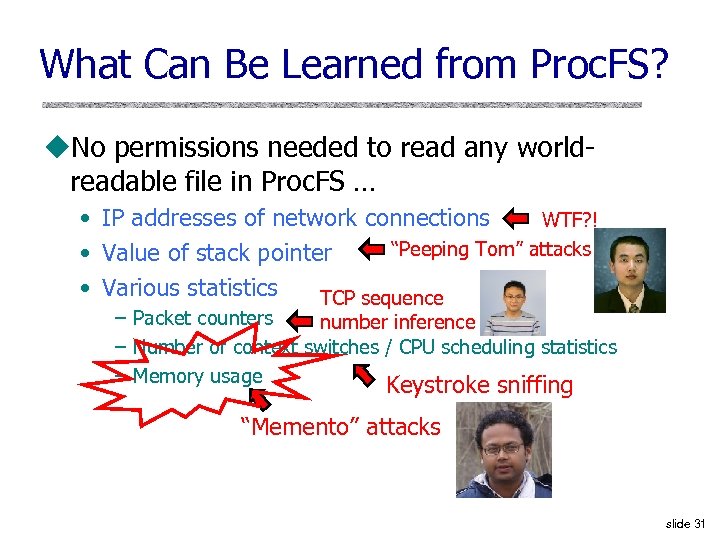
What Can Be Learned from Proc. FS? u. No permissions needed to read any worldreadable file in Proc. FS … • IP addresses of network connections WTF? ! “Peeping Tom” attacks • Value of stack pointer • Various statistics TCP sequence – Packet counters number inference – Number of context switches / CPU scheduling statistics – Memory usage Keystroke sniffing “Memento” attacks slide 31

Putting Memory Streams Together slide 32
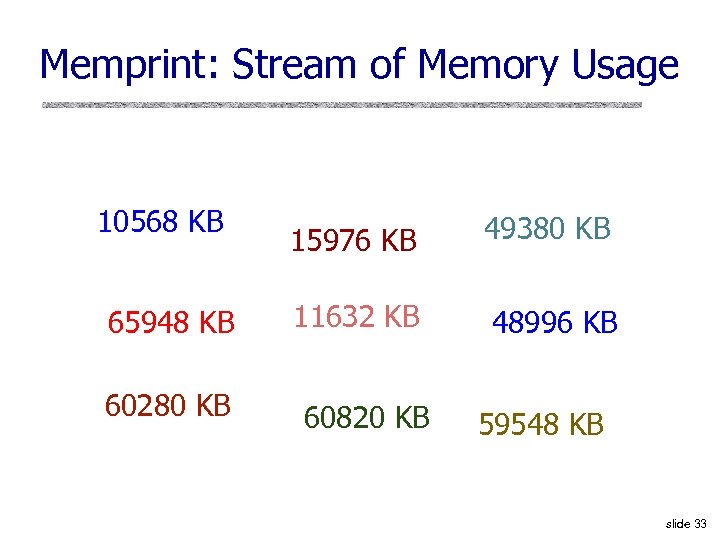
Memprint: Stream of Memory Usage 10568 KB 65948 KB 60280 KB 15976 KB 49380 KB 11632 KB 48996 KB 60820 KB 59548 KB slide 33
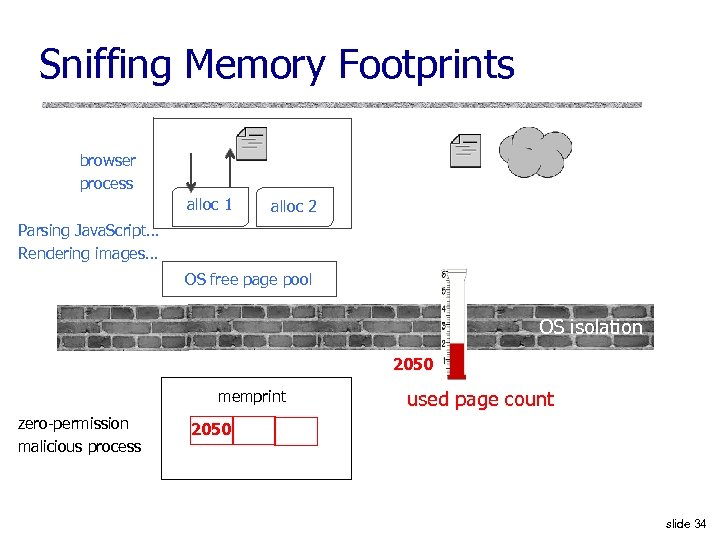
Sniffing Memory Footprints browser process alloc 1 alloc 2 Parsing Java. Script… Rendering images… OS free page pool OS isolation 2050 memprint zero-permission malicious process used page count 2050 slide 34
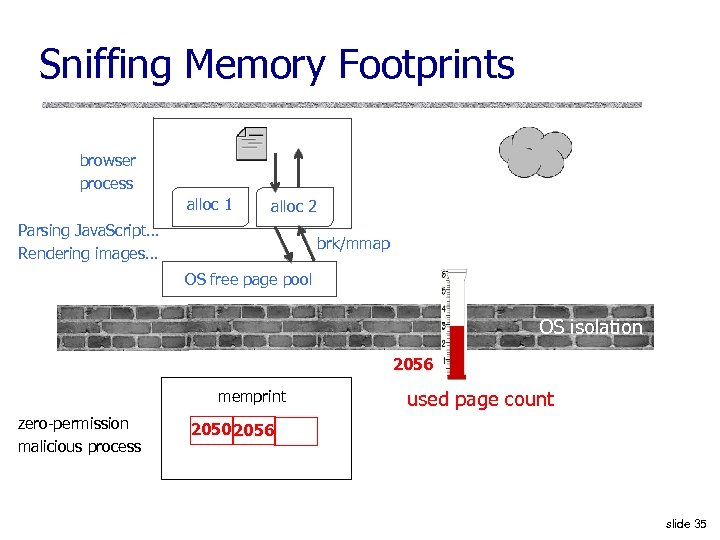
Sniffing Memory Footprints browser process alloc 1 alloc 2 Parsing Java. Script… Rendering images… brk/mmap OS free page pool OS isolation 2056 memprint zero-permission malicious process used page count 2050 2056 slide 35
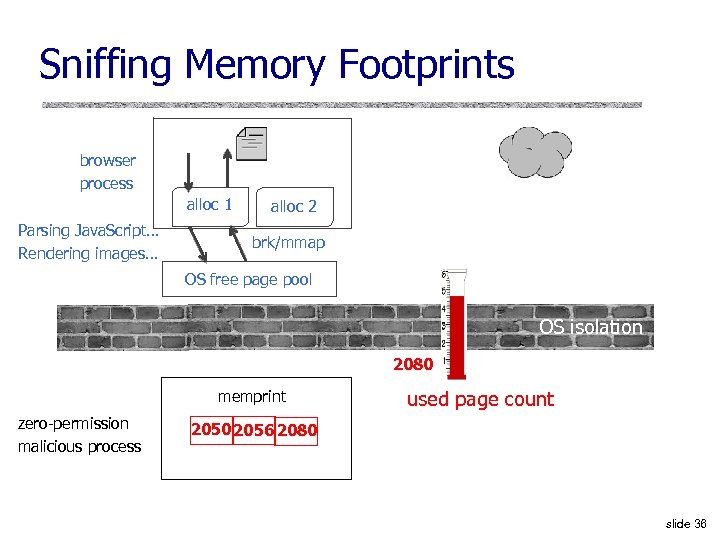
Sniffing Memory Footprints browser process alloc 1 Parsing Java. Script… Rendering images… alloc 2 brk/mmap OS free page pool OS isolation 2080 memprint zero-permission malicious process used page count 2050 2056 2080 slide 36
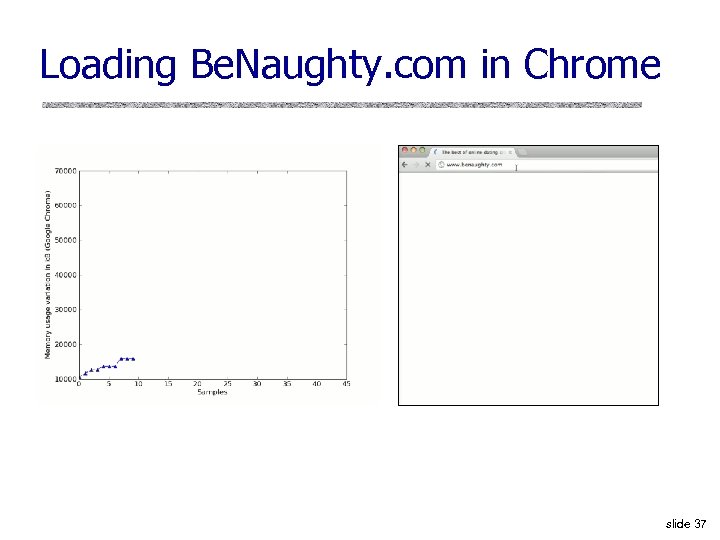
Loading Be. Naughty. com in Chrome slide 37
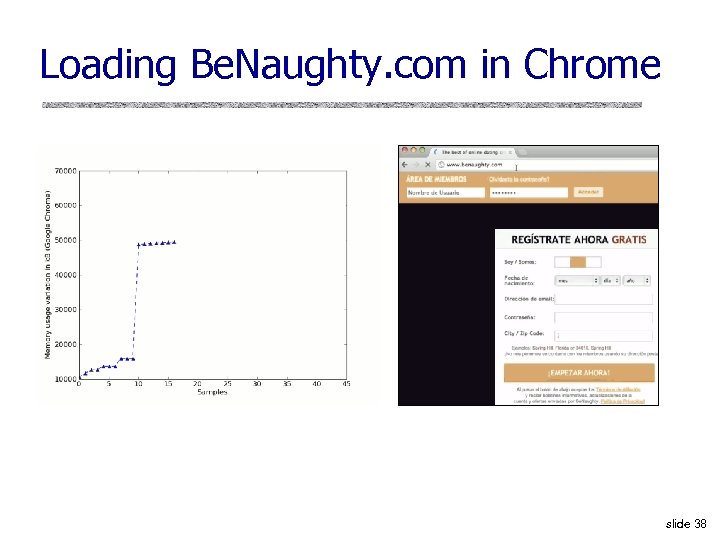
Loading Be. Naughty. com in Chrome slide 38
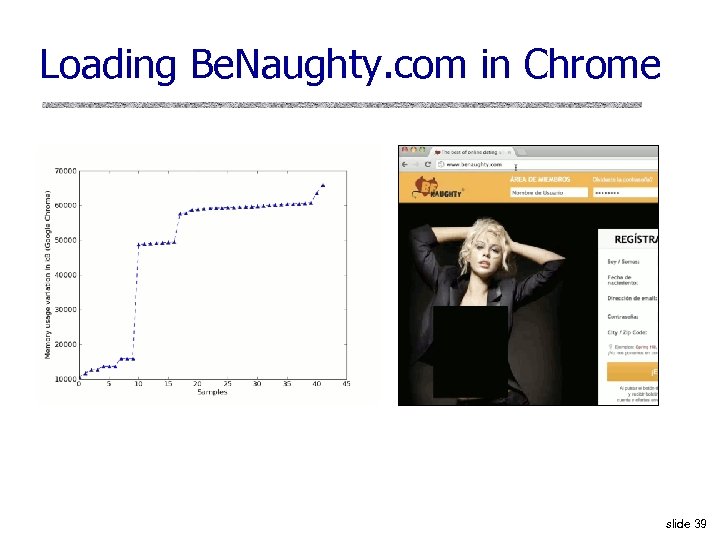
Loading Be. Naughty. com in Chrome slide 39
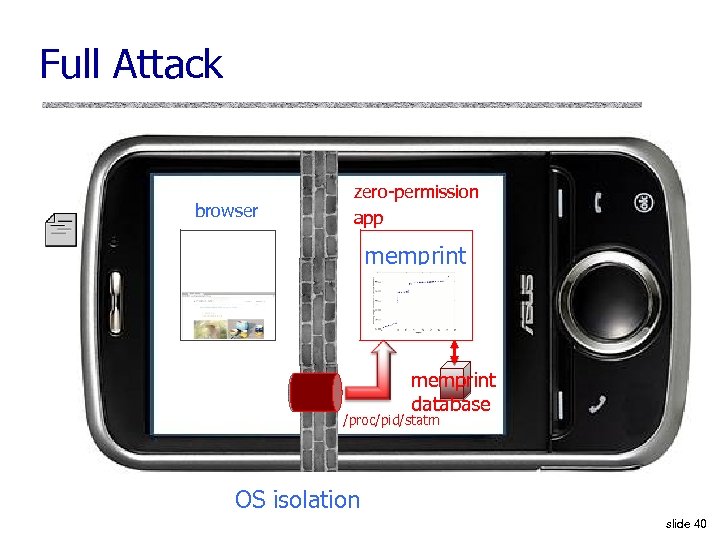
Full Attack browser zero-permission app memprint database /proc/pid/statm OS isolation slide 40
Why the Attack Works u Memprints are unique - for up to 43% of Alexa top 100, 000 pages • Can tune recognition to achieve zero false positives u Memprints are stable across repeated visits to the same page memprints are OS/browserdependent but machineindependent slide 41
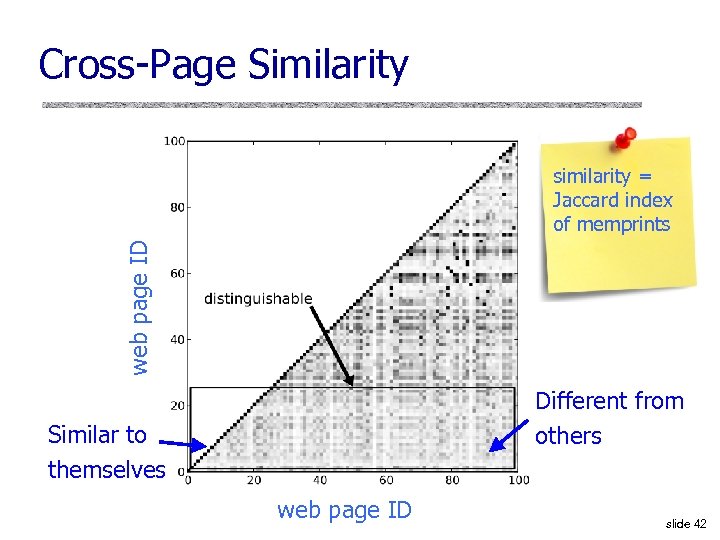
Cross-Page Similarity web page ID similarity = Jaccard index of memprints Different from others Similar to themselves web page ID slide 42

Other Privacy Leaks u. Fine-grained memory dynamics reveal membership in dating sites, interest in medical conditions, etc. u. Dynamics of CPU scheduling reveal individual keystrokes u. General problem: fine-grained resource usage statistics are correlated with secrets • These statistics are visible across isolation boundary • Their dynamics are a high-bandwidth side channel slide 43
65100e8aae4285aa2172926baee9d242.ppt