85135ccc5e01a255ec1e6f5945c6365c.ppt
- Количество слайдов: 25
 CS 5950/6030 Network Security Class 31 (F, 11/11/05) Leszek Lilien Department of Computer Science Western Michigan University Based on Security in Computing. Third Edition by Pfleeger and Pfleeger. Using some slides (as indicated) courtesy of: Prof. Aaron Striegel — at U. of Notre Dame Prof. Barbara Endicott-Popovsky and Prof. Deborah Frincke — at U. Washington Prof. Jussipekka Leiwo — at Vrije Universiteit (Free U. ), Amsterdam, The Netherlands Slides not created by the above authors are © by Leszek T. Lilien, 2005 Requests to use original slides for non-profit purposes will be gladly granted upon a written request.
CS 5950/6030 Network Security Class 31 (F, 11/11/05) Leszek Lilien Department of Computer Science Western Michigan University Based on Security in Computing. Third Edition by Pfleeger and Pfleeger. Using some slides (as indicated) courtesy of: Prof. Aaron Striegel — at U. of Notre Dame Prof. Barbara Endicott-Popovsky and Prof. Deborah Frincke — at U. Washington Prof. Jussipekka Leiwo — at Vrije Universiteit (Free U. ), Amsterdam, The Netherlands Slides not created by the above authors are © by Leszek T. Lilien, 2005 Requests to use original slides for non-profit purposes will be gladly granted upon a written request.
 7. Security in Networks. . . 7. 2. Threats in Networks. . . 7. 3. Networks Security Controls a) Introduction b) Security threat analysis c) Impact of network architecture/design and implementation on security—PART 1 Class 30 c) Impact of network architecture/design and implementation on security—PART 2 d) Encryption i. Link encryption vs. end-to-end (e 2 e) encryption ii. Virtual private network (VPN) iii. PKI and certificates—PART 1 2 © by Leszek T. Lilien, 2005
7. Security in Networks. . . 7. 2. Threats in Networks. . . 7. 3. Networks Security Controls a) Introduction b) Security threat analysis c) Impact of network architecture/design and implementation on security—PART 1 Class 30 c) Impact of network architecture/design and implementation on security—PART 2 d) Encryption i. Link encryption vs. end-to-end (e 2 e) encryption ii. Virtual private network (VPN) iii. PKI and certificates—PART 1 2 © by Leszek T. Lilien, 2005
 c. Impact of network architecture/ design & implement. on security (1) § Security principles for good analysis, design, implementation, and maintenance (as discussed in sections on Pgm Security and OS Security) apply to networks § Architecture can improve security by: 1) Segmentation 2) Redundancy 3) Single points of failure 4) Other means 3 © by Leszek T. Lilien, 2005
c. Impact of network architecture/ design & implement. on security (1) § Security principles for good analysis, design, implementation, and maintenance (as discussed in sections on Pgm Security and OS Security) apply to networks § Architecture can improve security by: 1) Segmentation 2) Redundancy 3) Single points of failure 4) Other means 3 © by Leszek T. Lilien, 2005
 d. Encryption Arguably most important/versatile tool for network security § § § We have seen that it can be used for: § Confidentiality/Privacy § Authentication § Integrity § Limiting data access i. ii. Kinds of encryption in networks: iii. iv. v. viii. 4 Link encryption vs. end-to-end (e 2 e) encryption Virtual private network (VPN) PKI and certificates SSH protocol SSL protocol (a. k. a. TLS protocol) IPsec protocol suite Signed code Encrypted e-mail © by Leszek T. Lilien, 2005
d. Encryption Arguably most important/versatile tool for network security § § § We have seen that it can be used for: § Confidentiality/Privacy § Authentication § Integrity § Limiting data access i. ii. Kinds of encryption in networks: iii. iv. v. viii. 4 Link encryption vs. end-to-end (e 2 e) encryption Virtual private network (VPN) PKI and certificates SSH protocol SSL protocol (a. k. a. TLS protocol) IPsec protocol suite Signed code Encrypted e-mail © by Leszek T. Lilien, 2005
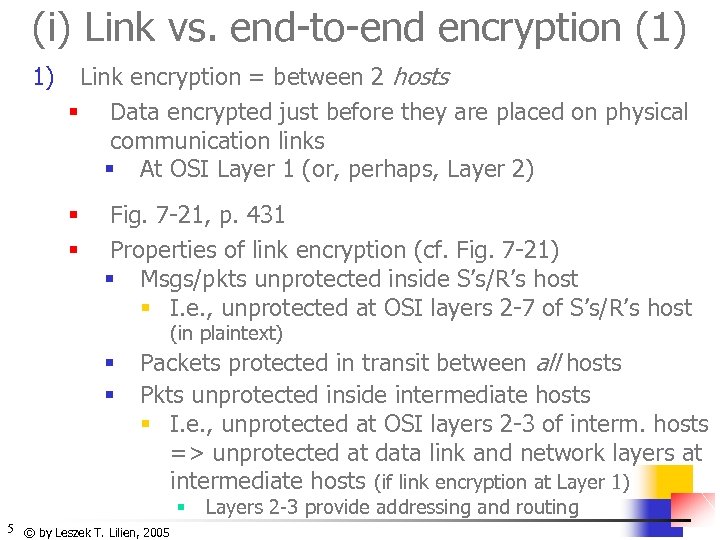 (i) Link vs. end-to-end encryption (1) 1) Link encryption = between 2 hosts § Data encrypted just before they are placed on physical communication links § At OSI Layer 1 (or, perhaps, Layer 2) § § Fig. 7 -21, p. 431 Properties of link encryption (cf. Fig. 7 -21) § Msgs/pkts unprotected inside S’s/R’s host § I. e. , unprotected at OSI layers 2 -7 of S’s/R’s host (in plaintext) § § Packets protected in transit between all hosts Pkts unprotected inside intermediate hosts § I. e. , unprotected at OSI layers 2 -3 of interm. hosts => unprotected at data link and network layers at intermediate hosts (if link encryption at Layer 1) § 5 © by Leszek T. Lilien, 2005 Layers 2 -3 provide addressing and routing
(i) Link vs. end-to-end encryption (1) 1) Link encryption = between 2 hosts § Data encrypted just before they are placed on physical communication links § At OSI Layer 1 (or, perhaps, Layer 2) § § Fig. 7 -21, p. 431 Properties of link encryption (cf. Fig. 7 -21) § Msgs/pkts unprotected inside S’s/R’s host § I. e. , unprotected at OSI layers 2 -7 of S’s/R’s host (in plaintext) § § Packets protected in transit between all hosts Pkts unprotected inside intermediate hosts § I. e. , unprotected at OSI layers 2 -3 of interm. hosts => unprotected at data link and network layers at intermediate hosts (if link encryption at Layer 1) § 5 © by Leszek T. Lilien, 2005 Layers 2 -3 provide addressing and routing
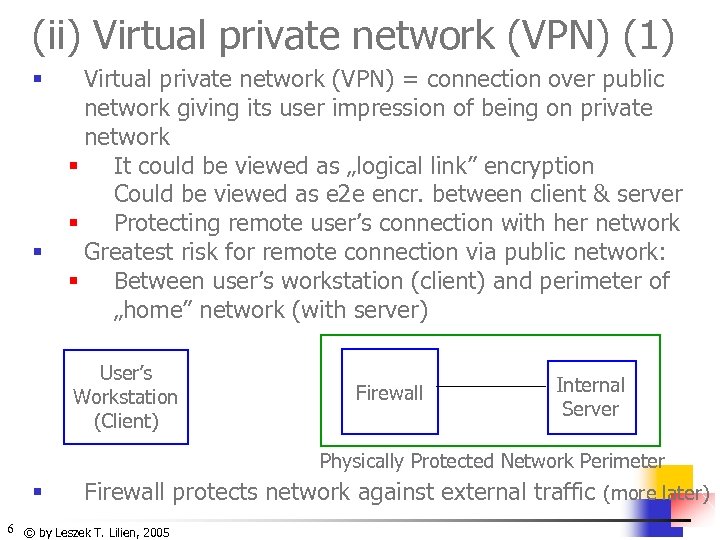 (ii) Virtual private network (VPN) (1) § § Virtual private network (VPN) = connection over public network giving its user impression of being on private network § It could be viewed as „logical link” encryption Could be viewed as e 2 e encr. between client & server § Protecting remote user’s connection with her network Greatest risk for remote connection via public network: § Between user’s workstation (client) and perimeter of „home” network (with server) User’s Workstation (Client) Firewall Internal Server Physically Protected Network Perimeter § Firewall protects network against external traffic (more later) 6 © by Leszek T. Lilien, 2005
(ii) Virtual private network (VPN) (1) § § Virtual private network (VPN) = connection over public network giving its user impression of being on private network § It could be viewed as „logical link” encryption Could be viewed as e 2 e encr. between client & server § Protecting remote user’s connection with her network Greatest risk for remote connection via public network: § Between user’s workstation (client) and perimeter of „home” network (with server) User’s Workstation (Client) Firewall Internal Server Physically Protected Network Perimeter § Firewall protects network against external traffic (more later) 6 © by Leszek T. Lilien, 2005
 (iii) PKI and certificates (1) § Public key infrastructure (PKI) = enables use of public key cryptography (asymmetric cryptography) § Usually in large & distributed environment § Elements of PKI: 1) Policies (higher level than procedures) § Define rules of operation § § E. g. , how to handle keys and sensitive info E. g. , how to match control level to risk level 2) Procedures (lower level than policies) § Dictate how keys should be generated, managed, used 3) Products § Implement policies and procedures § 7 © by Leszek T. Lilien, 2005 Generate, store, manage keys
(iii) PKI and certificates (1) § Public key infrastructure (PKI) = enables use of public key cryptography (asymmetric cryptography) § Usually in large & distributed environment § Elements of PKI: 1) Policies (higher level than procedures) § Define rules of operation § § E. g. , how to handle keys and sensitive info E. g. , how to match control level to risk level 2) Procedures (lower level than policies) § Dictate how keys should be generated, managed, used 3) Products § Implement policies and procedures § 7 © by Leszek T. Lilien, 2005 Generate, store, manage keys
 PKI and certificates (2) § PKI services: 1) PKI creates certificates § Certificate binds entity’s identity to entity’s public key § Entity = user or system or applicationor. . . 2) PKI gives out certificates from its database 3) PKI signs certificates § Adding its credibility to certificate’s authenticity § When queried about it 4) PKI confirms/denies validity of a certificate 5) PKI invalidates certificates § For entities that are no longer certified by PKI OR § For entities whose private key has been exposed 8 © by Leszek T. Lilien, 2005
PKI and certificates (2) § PKI services: 1) PKI creates certificates § Certificate binds entity’s identity to entity’s public key § Entity = user or system or applicationor. . . 2) PKI gives out certificates from its database 3) PKI signs certificates § Adding its credibility to certificate’s authenticity § When queried about it 4) PKI confirms/denies validity of a certificate 5) PKI invalidates certificates § For entities that are no longer certified by PKI OR § For entities whose private key has been exposed 8 © by Leszek T. Lilien, 2005
 Class 30 Ended Here 9 © by Leszek T. Lilien, 2005
Class 30 Ended Here 9 © by Leszek T. Lilien, 2005
 7. Security in Networks. . . 7. 2. Threats in Networks. . . 7. 3. Networks Security Controls. . . Class 30 Class 31 10 c) d) © by Leszek T. Lilien, 2005 Impact of network archit. /design and implem. on security—PART 2 Encryption i. Link encryption vs. end-to-end (e 2 e) encryption ii. Virtual private network (VPN) iii. PKI and certificates—PART 1 iii. iv. v. vi. PKI and certificates—PART 2 SSH protocol SSL protocol (a. k. a. TLS protocol) IPsec protocol suite—PART 1
7. Security in Networks. . . 7. 2. Threats in Networks. . . 7. 3. Networks Security Controls. . . Class 30 Class 31 10 c) d) © by Leszek T. Lilien, 2005 Impact of network archit. /design and implem. on security—PART 2 Encryption i. Link encryption vs. end-to-end (e 2 e) encryption ii. Virtual private network (VPN) iii. PKI and certificates—PART 1 iii. iv. v. vi. PKI and certificates—PART 2 SSH protocol SSL protocol (a. k. a. TLS protocol) IPsec protocol suite—PART 1
 PKI and certificates (3) § PKI sets up: 1) Certificate authorities (CAs) 2) Registration authority 1) Certificate authority (CA) § CA can be in-house or external (commercial TTP = trusted third party) § CA is trusted § § Entities delegate to CA creation, issuance, acceptance, and revocation of their certificates CA actions: § Managing public key certificates (whole life cycle) § Issuing certificates by binding entity’s identity to its public key § § § Binding is done via CA’s digital signature § By publishing revocation lists Determining expiration dates for certificates Revoking certificates when necessary 11 © by Leszek T. Lilien, 2005
PKI and certificates (3) § PKI sets up: 1) Certificate authorities (CAs) 2) Registration authority 1) Certificate authority (CA) § CA can be in-house or external (commercial TTP = trusted third party) § CA is trusted § § Entities delegate to CA creation, issuance, acceptance, and revocation of their certificates CA actions: § Managing public key certificates (whole life cycle) § Issuing certificates by binding entity’s identity to its public key § § § Binding is done via CA’s digital signature § By publishing revocation lists Determining expiration dates for certificates Revoking certificates when necessary 11 © by Leszek T. Lilien, 2005
 PKI and certificates (4) § Example of CA analog: credit card company (CCC) Certificate analog: credit card (binds identity to account) Revocation list analog: lists of invalid credit cards § CCC is trusted § § Customers delegate to CCC creation, issuance, acceptance, and revocation of their credit cards CCC actions: § Managing credit cards (whole life cycle) § Issuing credit cards by binding customer’s identity to customer’s account § Binding is done via CCC’s protected databases § By checking list of invalid credit cards (before computer-verification transaction era, CCC published booklets of invalidated credit cards) § Determining expiration dates for credit cards § Revoking credit cards when necessary 12 © by Leszek T. Lilien, 2005
PKI and certificates (4) § Example of CA analog: credit card company (CCC) Certificate analog: credit card (binds identity to account) Revocation list analog: lists of invalid credit cards § CCC is trusted § § Customers delegate to CCC creation, issuance, acceptance, and revocation of their credit cards CCC actions: § Managing credit cards (whole life cycle) § Issuing credit cards by binding customer’s identity to customer’s account § Binding is done via CCC’s protected databases § By checking list of invalid credit cards (before computer-verification transaction era, CCC published booklets of invalidated credit cards) § Determining expiration dates for credit cards § Revoking credit cards when necessary 12 © by Leszek T. Lilien, 2005
 PKI and certificates (5) 2) Registration authority (RA) = interface between user and CA § Duties: § Capture and authenticate user’s identity § Submit certificate requests to appropriate CA § Analog: U. S. Citizen applying for passport and U. S. Postal Service (USPS) Passport (official U. S. authentication) <-> certificate § USPS authenticates citizen § § § By verifies citizen’s driver license + other proofs of identity Passport office <-> CA USPS submits passport request forms to appropriate passport office of the U. S. Gov’t § USPS brings passport to customer’s home § Note: Trustworthiness of USPS authentication determines level of trust that can be placed in passports 13 © by Leszek T. Lilien, 2005
PKI and certificates (5) 2) Registration authority (RA) = interface between user and CA § Duties: § Capture and authenticate user’s identity § Submit certificate requests to appropriate CA § Analog: U. S. Citizen applying for passport and U. S. Postal Service (USPS) Passport (official U. S. authentication) <-> certificate § USPS authenticates citizen § § § By verifies citizen’s driver license + other proofs of identity Passport office <-> CA USPS submits passport request forms to appropriate passport office of the U. S. Gov’t § USPS brings passport to customer’s home § Note: Trustworthiness of USPS authentication determines level of trust that can be placed in passports 13 © by Leszek T. Lilien, 2005
 PKI and certificates (6) § PKI efforts stateside and overseas § Building PKI for various purposes § E. g. , Federal PKI Initiative – to provide secure communication to U. S. gov’t agencies § It also specifies how commercial s/w using PKI should operate (so gov’t can use off-the-shelf products) § Major PKI product vendors in the U. S. : § § Baltimore Technologies Northern Telecom/Entrust Identrus Certificates can bind: § Identity to public key – classic, most common § Other bindings under research § E. g. , binding financial status to key (credit card companies) § Draft standards: ANSI X 9. 45, Simple Public Key Infrastructure (SPKI) 14 © by Leszek T. Lilien, 2005
PKI and certificates (6) § PKI efforts stateside and overseas § Building PKI for various purposes § E. g. , Federal PKI Initiative – to provide secure communication to U. S. gov’t agencies § It also specifies how commercial s/w using PKI should operate (so gov’t can use off-the-shelf products) § Major PKI product vendors in the U. S. : § § Baltimore Technologies Northern Telecom/Entrust Identrus Certificates can bind: § Identity to public key – classic, most common § Other bindings under research § E. g. , binding financial status to key (credit card companies) § Draft standards: ANSI X 9. 45, Simple Public Key Infrastructure (SPKI) 14 © by Leszek T. Lilien, 2005
 PKI and certificates (7) § PKI is not yet mature § Many outstanding issues § Cf. Table 7 -6, p. 439 Still, many points are clear: § CA should be approved/verfied by independent body § CA’s private keys must be stored in tamper-resistant security module (maybe with h/w support) § Access to CAs and RAs should be tightly controlled § Using strong authentication (e. g. , 2 FA or 3 FA with smart cards) 15 © by Leszek T. Lilien, 2005
PKI and certificates (7) § PKI is not yet mature § Many outstanding issues § Cf. Table 7 -6, p. 439 Still, many points are clear: § CA should be approved/verfied by independent body § CA’s private keys must be stored in tamper-resistant security module (maybe with h/w support) § Access to CAs and RAs should be tightly controlled § Using strong authentication (e. g. , 2 FA or 3 FA with smart cards) 15 © by Leszek T. Lilien, 2005
 (iv) SSH protocol (SSH = Secure SHell) SSH protocol (newer: v. 2) – provides authenticated and encrypted communication with shell/OS command interpreter § § Originally defined for Unix Replaced insecure utilities for remote access § § Such as Telnet / rlogin / rsh Protects against spoofing attacks (falsifying one end of § communication, incl. masquerading, sesssion hijacking, MITM) message modification / falsification § Involves negotiation between local and remote sites § Negotiate which encryption algorithm to use § E. g. , DES? IDEA? AES? Negotiate which authentication technique to use § § E. g. , public key? Kerberos? 16 © by Leszek T. Lilien, 2005 &
(iv) SSH protocol (SSH = Secure SHell) SSH protocol (newer: v. 2) – provides authenticated and encrypted communication with shell/OS command interpreter § § Originally defined for Unix Replaced insecure utilities for remote access § § Such as Telnet / rlogin / rsh Protects against spoofing attacks (falsifying one end of § communication, incl. masquerading, sesssion hijacking, MITM) message modification / falsification § Involves negotiation between local and remote sites § Negotiate which encryption algorithm to use § E. g. , DES? IDEA? AES? Negotiate which authentication technique to use § § E. g. , public key? Kerberos? 16 © by Leszek T. Lilien, 2005 &
 (v) SSL protocol (a. k. a. TLS prot. ) (1) SSL protocol (v 3) = (approx. ) TLS protocol - interfaces betwen app (on client C) and TCP/IP protocols to provide server S authentication, optional C authentication, and encrypted communication channel between C and S for session between C and S § SSL = Secure Sockets Layer / TLS = Transport Layer Security § Simple but effective – most widely used secure communication protocol on Internet (incl. WWW browsers/servers) § § Originally defined by Netscape to protect browser-to-server communication Involves negotiation between C and S § Negotiate which encryption suite to use for session § § § E. g. , DES? RC 4 w/ 128 -bit/40 -bit key? RC 2? Fortezza? [Bishop] Negotiate which hashing technique to use for session E. g. , SHA 1 or MD 5? 17 © by Leszek T. Lilien, 2005
(v) SSL protocol (a. k. a. TLS prot. ) (1) SSL protocol (v 3) = (approx. ) TLS protocol - interfaces betwen app (on client C) and TCP/IP protocols to provide server S authentication, optional C authentication, and encrypted communication channel between C and S for session between C and S § SSL = Secure Sockets Layer / TLS = Transport Layer Security § Simple but effective – most widely used secure communication protocol on Internet (incl. WWW browsers/servers) § § Originally defined by Netscape to protect browser-to-server communication Involves negotiation between C and S § Negotiate which encryption suite to use for session § § § E. g. , DES? RC 4 w/ 128 -bit/40 -bit key? RC 2? Fortezza? [Bishop] Negotiate which hashing technique to use for session E. g. , SHA 1 or MD 5? 17 © by Leszek T. Lilien, 2005
 SSL protocol (a. k. a. TLS protocol) (2) § SSL use scenario (handshake protocol) § C requests an SSL session by sending: Hello-C, Rand-C (random nr), list of cipher (encryption) algorithms & hash algorithms known to C § Hash used to checksum messages S responds with msgs including: Hello-S, Rand-S, cipher & hash algorithm selected by S (from C’s list) , S’s certificate, KPUB-S, [OPTIONAL: request for cert. fr. C] § § C can use S’s certificate (X. 509 v 3 cert. ) to verify S’s authenticity [OPTIONAL: C replies with: C’s certificate] C returns „pre-master secret” encrypted under KPUB-S § § § Pre-master secret - e. g. , 48 random B if selected cipher is RSA [Bishop. Comp. Sec-A&S, p. 296] . . . continued. . . 18 © by Leszek T. Lilien, 2005
SSL protocol (a. k. a. TLS protocol) (2) § SSL use scenario (handshake protocol) § C requests an SSL session by sending: Hello-C, Rand-C (random nr), list of cipher (encryption) algorithms & hash algorithms known to C § Hash used to checksum messages S responds with msgs including: Hello-S, Rand-S, cipher & hash algorithm selected by S (from C’s list) , S’s certificate, KPUB-S, [OPTIONAL: request for cert. fr. C] § § C can use S’s certificate (X. 509 v 3 cert. ) to verify S’s authenticity [OPTIONAL: C replies with: C’s certificate] C returns „pre-master secret” encrypted under KPUB-S § § § Pre-master secret - e. g. , 48 random B if selected cipher is RSA [Bishop. Comp. Sec-A&S, p. 296] . . . continued. . . 18 © by Leszek T. Lilien, 2005
 SSL protocol (a. k. a. TLS protocol) (3) . . . continued. . . C and S calculate „master secret” using: § § § „Pre-master secret” Constant strings ‘A’, ‘BB’ and ‘CCC’ Rand-C and Rand-S, SHA hashing algorithm [ibid, p. 294] § C and S switch to encrypted communication using „master secret” as session key C and S exchange application data for session duration § TLS is potentially vulnerable to MITM attacks § (i. e. , for as long as they stay connected) [Conklin eta al. , p. 163] 19 © by Leszek T. Lilien, 2005
SSL protocol (a. k. a. TLS protocol) (3) . . . continued. . . C and S calculate „master secret” using: § § § „Pre-master secret” Constant strings ‘A’, ‘BB’ and ‘CCC’ Rand-C and Rand-S, SHA hashing algorithm [ibid, p. 294] § C and S switch to encrypted communication using „master secret” as session key C and S exchange application data for session duration § TLS is potentially vulnerable to MITM attacks § (i. e. , for as long as they stay connected) [Conklin eta al. , p. 163] 19 © by Leszek T. Lilien, 2005
 (vi) IPsec protocol suite (1) IPsec (IP Security Protocol Suite) = standard for securing § IP communications by encrypting and/or authenticating all IP packets § IPsec is public (published / scrutinized) § By design, protects against threats including: spoofing (incl. session hijacking) / eavesdropping § Choice of ciphers/hash protocols § Communicating parties negotiate which ones to use § IPsec defines some ciphers/hash as required in every IPsec implementaion 20 © by Leszek T. Lilien, 2005
(vi) IPsec protocol suite (1) IPsec (IP Security Protocol Suite) = standard for securing § IP communications by encrypting and/or authenticating all IP packets § IPsec is public (published / scrutinized) § By design, protects against threats including: spoofing (incl. session hijacking) / eavesdropping § Choice of ciphers/hash protocols § Communicating parties negotiate which ones to use § IPsec defines some ciphers/hash as required in every IPsec implementaion 20 © by Leszek T. Lilien, 2005
 IPsec protocol suite (2) § IPsec provides security at IP layer in IPv 6 or IPv 4[Stall. p. 499] § IP versions: § IPv 4 = v. 4 — older IP protocol version (still in use) § IPv 6 = v. 6 — newer IP protocol version § IPv 6 — larger address space § IPv 6 — also other functional enhancements § § Developed (1992 -1998) since IPv 4 runs out of address space — IPv 4 has 32 -bit source/destination addresses — IPv 6 has 128 -bit source/destination addresses To accommodate faster networks To accommodate mix of multimedia data streams IPsec protects all layers above IP layer (where it „resides”) § In particular, protects TCP or UDP protocols § Protects „automatically” § Protects transparently (no modifications to TCP, UDP needed) 21 © by Leszek T. Lilien, 2005
IPsec protocol suite (2) § IPsec provides security at IP layer in IPv 6 or IPv 4[Stall. p. 499] § IP versions: § IPv 4 = v. 4 — older IP protocol version (still in use) § IPv 6 = v. 6 — newer IP protocol version § IPv 6 — larger address space § IPv 6 — also other functional enhancements § § Developed (1992 -1998) since IPv 4 runs out of address space — IPv 4 has 32 -bit source/destination addresses — IPv 6 has 128 -bit source/destination addresses To accommodate faster networks To accommodate mix of multimedia data streams IPsec protects all layers above IP layer (where it „resides”) § In particular, protects TCP or UDP protocols § Protects „automatically” § Protects transparently (no modifications to TCP, UDP needed) 21 © by Leszek T. Lilien, 2005
 IPsec protocol suite (3) Basis of IPsec: security association (SA) = set of security parameters for a secured 1 -way communication channel § § § 2 SAs needed for 2 -way communication [St, 487] Components of SA: 1) Encryption algorithm and „mode” § 2) 3) 4) 5) E. g. , for DES, mode = CDC – cipher bloc chaining Encryption key Encryption params (e. g. , initialization vector for encryption) Authentication protocol and key SA lifespan § Allows long-running sessions to select new crypto key 6) Address of opposite end of SA (source <---> destination) 7) Sensitivity level of protected data § (e. g. , unclassified / restricted / confidential / secret / top secret) 22 © by Leszek T. Lilien, 2005
IPsec protocol suite (3) Basis of IPsec: security association (SA) = set of security parameters for a secured 1 -way communication channel § § § 2 SAs needed for 2 -way communication [St, 487] Components of SA: 1) Encryption algorithm and „mode” § 2) 3) 4) 5) E. g. , for DES, mode = CDC – cipher bloc chaining Encryption key Encryption params (e. g. , initialization vector for encryption) Authentication protocol and key SA lifespan § Allows long-running sessions to select new crypto key 6) Address of opposite end of SA (source <---> destination) 7) Sensitivity level of protected data § (e. g. , unclassified / restricted / confidential / secret / top secret) 22 © by Leszek T. Lilien, 2005
 IPsec protocol suite (4) Security parameter index (SPI) data structure § Resides on each host H running IPsec Used to select 1 of n SAs that exist on H § § Different SAs for concurrent communications with different remote Hs Fundamental IPsec data structures / protocols 1) AH = authentication header / AH protocol § For authentication-only IPsec service: § Authenticates S (sender ) 2) ESP = encapsulated security payload / ESP protocol § For encryption-only IPsec service OR § For combined encryption/authentication IPsec service 23 © by Leszek T. Lilien, 2005
IPsec protocol suite (4) Security parameter index (SPI) data structure § Resides on each host H running IPsec Used to select 1 of n SAs that exist on H § § Different SAs for concurrent communications with different remote Hs Fundamental IPsec data structures / protocols 1) AH = authentication header / AH protocol § For authentication-only IPsec service: § Authenticates S (sender ) 2) ESP = encapsulated security payload / ESP protocol § For encryption-only IPsec service OR § For combined encryption/authentication IPsec service 23 © by Leszek T. Lilien, 2005
 IPsec protocol suite (5) § IPsec can be used for various crypto sessions: § VPN § e 2 e (incl. app 2 app) § For network mgmt (e. g. , for routing) § IPsec scenario § TCP layer passes conventional TCP Header & Data down to IP layer § IP layer calls upon IPsec to encapsulate conventional TCP Header & Data into ESP (encapsulated security payload) § Fig. 7 -28, p. 441 § IP layer adds IP Header § IP layer passes packet down to physical layer § Physical layer adds Physical Header & Physical Trailer 24 © by Leszek T. Lilien, 2005
IPsec protocol suite (5) § IPsec can be used for various crypto sessions: § VPN § e 2 e (incl. app 2 app) § For network mgmt (e. g. , for routing) § IPsec scenario § TCP layer passes conventional TCP Header & Data down to IP layer § IP layer calls upon IPsec to encapsulate conventional TCP Header & Data into ESP (encapsulated security payload) § Fig. 7 -28, p. 441 § IP layer adds IP Header § IP layer passes packet down to physical layer § Physical layer adds Physical Header & Physical Trailer 24 © by Leszek T. Lilien, 2005
 End of Class 31 25 © by Leszek T. Lilien, 2005
End of Class 31 25 © by Leszek T. Lilien, 2005


