ea7af36b0716715caf1fc15fd15c856a.ppt
- Количество слайдов: 149
 CS 2302 - COMPUTER NETWORKS RAJALAKSHMI ENGINEERING COLLEGE DEPARTMENT OF INFORMATION TECHNOLOGY
CS 2302 - COMPUTER NETWORKS RAJALAKSHMI ENGINEERING COLLEGE DEPARTMENT OF INFORMATION TECHNOLOGY
 UNIT I INTRODUCTION: p p p A computer network is a group of interconnected computers A collection of computers and devices connected to each other. Allows computers to communicate with each other and share resources and information.
UNIT I INTRODUCTION: p p p A computer network is a group of interconnected computers A collection of computers and devices connected to each other. Allows computers to communicate with each other and share resources and information.
 Building a Network p To build a network Identify the set of constraints and requirements based on Application programmer Network designer Network provider
Building a Network p To build a network Identify the set of constraints and requirements based on Application programmer Network designer Network provider
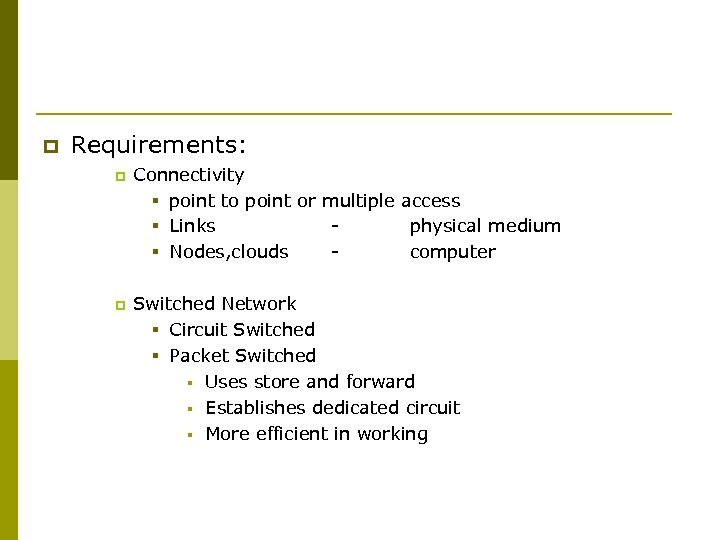 p Requirements: p p Connectivity § point to point or multiple access § Links physical medium § Nodes, clouds computer Switched Network § Circuit Switched § Packet Switched § Uses store and forward § Establishes dedicated circuit § More efficient in working
p Requirements: p p Connectivity § point to point or multiple access § Links physical medium § Nodes, clouds computer Switched Network § Circuit Switched § Packet Switched § Uses store and forward § Establishes dedicated circuit § More efficient in working
 p Routing § Provides Systematic procedure forwarding messages § Unicasting § Multicasting p Cost effective Resources sharing How system resource is shared effectively by multiple users multiplexing
p Routing § Provides Systematic procedure forwarding messages § Unicasting § Multicasting p Cost effective Resources sharing How system resource is shared effectively by multiple users multiplexing
 p Multiplexing methods n n STDM - Synchronous time division multiplexing FDM - Frequency division multiplexing
p Multiplexing methods n n STDM - Synchronous time division multiplexing FDM - Frequency division multiplexing
 Network Architecture p p Provides a general, effective, fair, and robust connectivity of computers Provides a blueprint n Types OSI Architecture p Internet Architecture p
Network Architecture p p Provides a general, effective, fair, and robust connectivity of computers Provides a blueprint n Types OSI Architecture p Internet Architecture p
 OSI ARCHITECTURE p Open Systems Interconnection (OSI) model is a reference model developed by ISO (International Organization for Standardization) in 1984 OSI model defines the communications process into Layers Provides a standards for communication in the network Primary architectural model for inter-computing and Inter networking communications. network communication protocols have a structure based on OSI Model
OSI ARCHITECTURE p Open Systems Interconnection (OSI) model is a reference model developed by ISO (International Organization for Standardization) in 1984 OSI model defines the communications process into Layers Provides a standards for communication in the network Primary architectural model for inter-computing and Inter networking communications. network communication protocols have a structure based on OSI Model
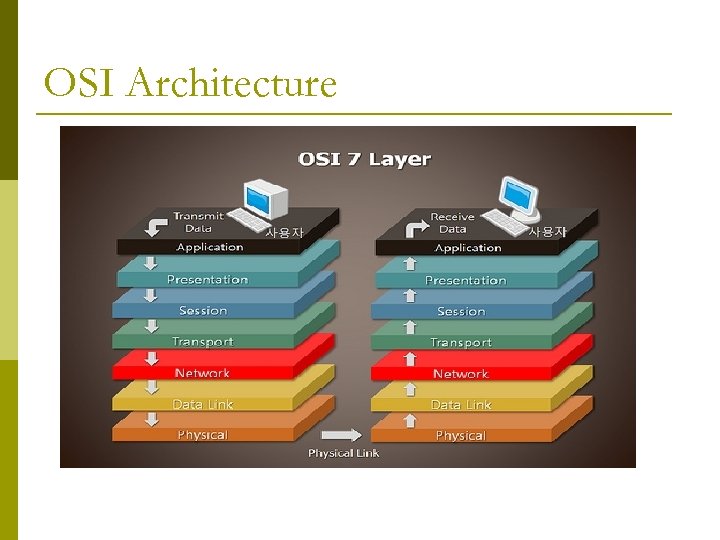 OSI Architecture
OSI Architecture
 Internet Architecture p p TCP/IP Architecture Four Layer model TCP, UDP, FTP, HTTP, SMTP Protocols used Internet Protocol Graph
Internet Architecture p p TCP/IP Architecture Four Layer model TCP, UDP, FTP, HTTP, SMTP Protocols used Internet Protocol Graph
 Direct Links: Outline p Physical Layer n n p Link technologies Encoding Framing Error Detection Reliable Transmission (ARQ protocols) Medium Access Control: Existing protocols: Ethernet, Token Rings, Wireless
Direct Links: Outline p Physical Layer n n p Link technologies Encoding Framing Error Detection Reliable Transmission (ARQ protocols) Medium Access Control: Existing protocols: Ethernet, Token Rings, Wireless
 Link Technologies p Cables: n n p Cat 5 twisted pair, 10 -100 Mbps, 100 m Thin-net coax, 10 -100 Mbps, 200 m Thick-net coax, 10 -100 Mbps, 500 m Fiber, 100 Mbps-2. 4 Gbps, 2 -40 km Leased Lines: n n Copper based: T 1 (1. 544 Mbps), T 3 (44. 736 Mbps) Optical fiber: STS-1 (51. 84 Mbps), STS-N (N*51. 84 Mbps)
Link Technologies p Cables: n n p Cat 5 twisted pair, 10 -100 Mbps, 100 m Thin-net coax, 10 -100 Mbps, 200 m Thick-net coax, 10 -100 Mbps, 500 m Fiber, 100 Mbps-2. 4 Gbps, 2 -40 km Leased Lines: n n Copper based: T 1 (1. 544 Mbps), T 3 (44. 736 Mbps) Optical fiber: STS-1 (51. 84 Mbps), STS-N (N*51. 84 Mbps)
 Link Technologies p p Last-Mile Links: n POTS (56 Kbps), ISDN (2*64 Kbps) n x. DSL: ADSL (16 -640 Kbps, 1. 554 -8. 448 Mbps), VDSL (12. 96 Mbps-55. 2 Mbps) n CATV: 40 Mbps downstream, 20 Mbps upstream Wireless Links: Cellular, Satellite, Wireless Local Loop
Link Technologies p p Last-Mile Links: n POTS (56 Kbps), ISDN (2*64 Kbps) n x. DSL: ADSL (16 -640 Kbps, 1. 554 -8. 448 Mbps), VDSL (12. 96 Mbps-55. 2 Mbps) n CATV: 40 Mbps downstream, 20 Mbps upstream Wireless Links: Cellular, Satellite, Wireless Local Loop
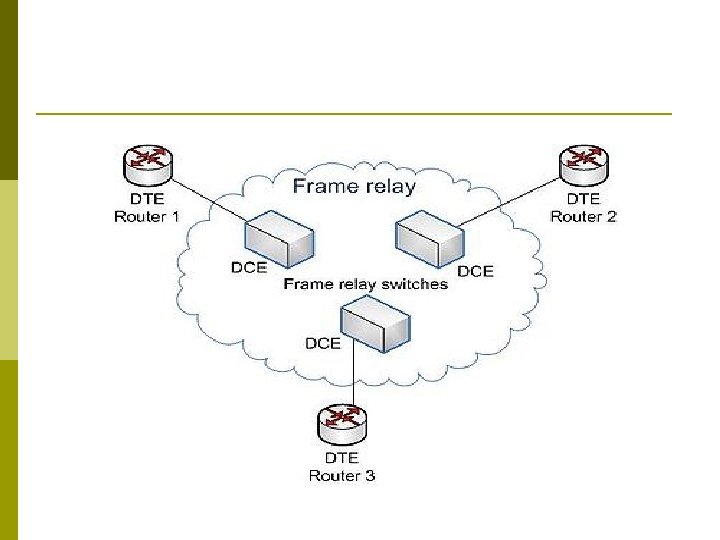
 FRAMING p An efficient data transmission technique p It is a message forwarding system in which data packets, called frames, are passed from one or many start-points to one
FRAMING p An efficient data transmission technique p It is a message forwarding system in which data packets, called frames, are passed from one or many start-points to one
 Approaches p Byte oriented Protocol(PPP) BISYNC Binary Synchronous Communication DDCMP Digital Data Communication Message Protocol Bit oriented Protocol(HDLC) p Clock based Framing(SONET) p
Approaches p Byte oriented Protocol(PPP) BISYNC Binary Synchronous Communication DDCMP Digital Data Communication Message Protocol Bit oriented Protocol(HDLC) p Clock based Framing(SONET) p
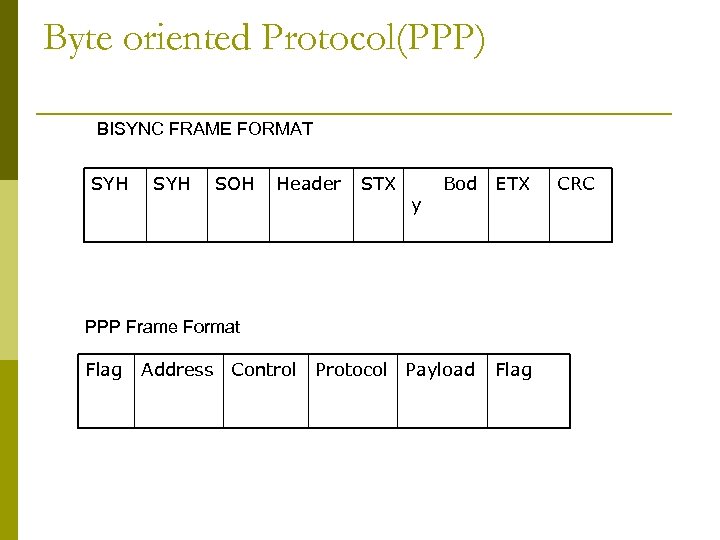 Byte oriented Protocol(PPP) BISYNC FRAME FORMAT SYH SOH Header STX Bod y ETX Protocol Payload Flag PPP Frame Format Flag Address Control CRC
Byte oriented Protocol(PPP) BISYNC FRAME FORMAT SYH SOH Header STX Bod y ETX Protocol Payload Flag PPP Frame Format Flag Address Control CRC
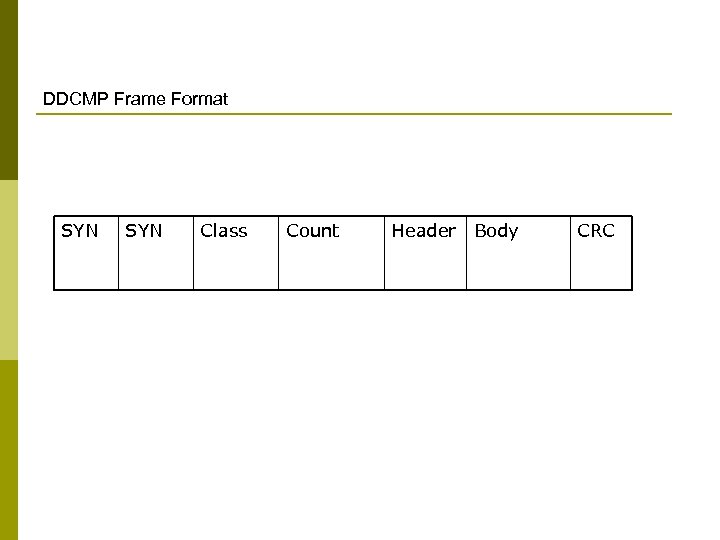 DDCMP Frame Format SYN Class Count Header Body CRC
DDCMP Frame Format SYN Class Count Header Body CRC
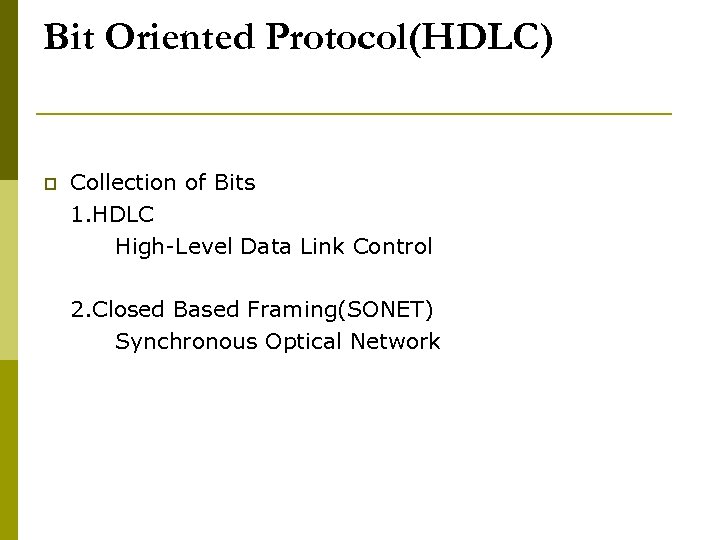 Bit Oriented Protocol(HDLC) p Collection of Bits 1. HDLC High-Level Data Link Control 2. Closed Based Framing(SONET) Synchronous Optical Network
Bit Oriented Protocol(HDLC) p Collection of Bits 1. HDLC High-Level Data Link Control 2. Closed Based Framing(SONET) Synchronous Optical Network
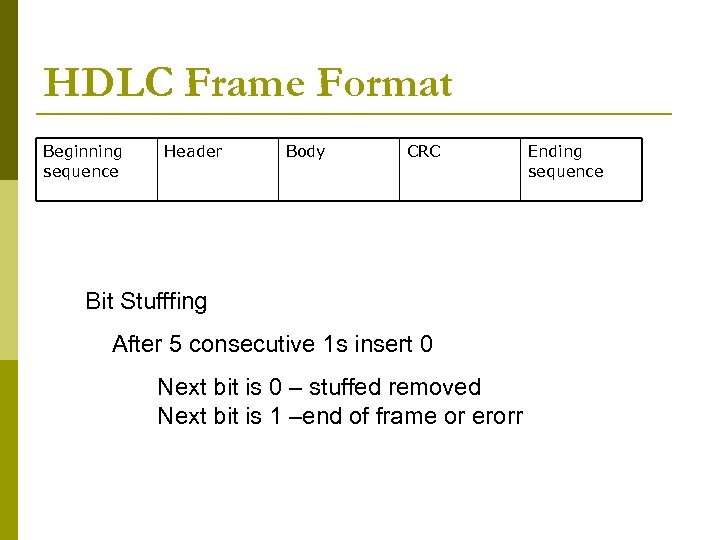 HDLC Frame Format Beginning sequence Header Body CRC Bit Stufffing After 5 consecutive 1 s insert 0 Next bit is 0 – stuffed removed Next bit is 1 –end of frame or erorr Ending sequence
HDLC Frame Format Beginning sequence Header Body CRC Bit Stufffing After 5 consecutive 1 s insert 0 Next bit is 0 – stuffed removed Next bit is 1 –end of frame or erorr Ending sequence
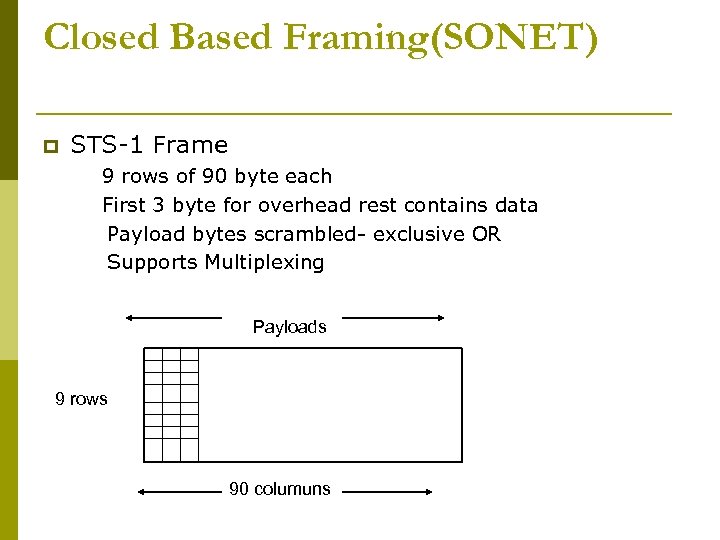 Closed Based Framing(SONET) p STS-1 Frame 9 rows of 90 byte each First 3 byte for overhead rest contains data Payload bytes scrambled- exclusive OR Supports Multiplexing Payloads 9 rows 90 columuns
Closed Based Framing(SONET) p STS-1 Frame 9 rows of 90 byte each First 3 byte for overhead rest contains data Payload bytes scrambled- exclusive OR Supports Multiplexing Payloads 9 rows 90 columuns
 ERROR DETECTION p Detecting Errors In Transmission Electrical Interference, thermal noise Approaches Two Dimensional Parity Internet Checksum Algorithm Cyclic Redundancy Check
ERROR DETECTION p Detecting Errors In Transmission Electrical Interference, thermal noise Approaches Two Dimensional Parity Internet Checksum Algorithm Cyclic Redundancy Check
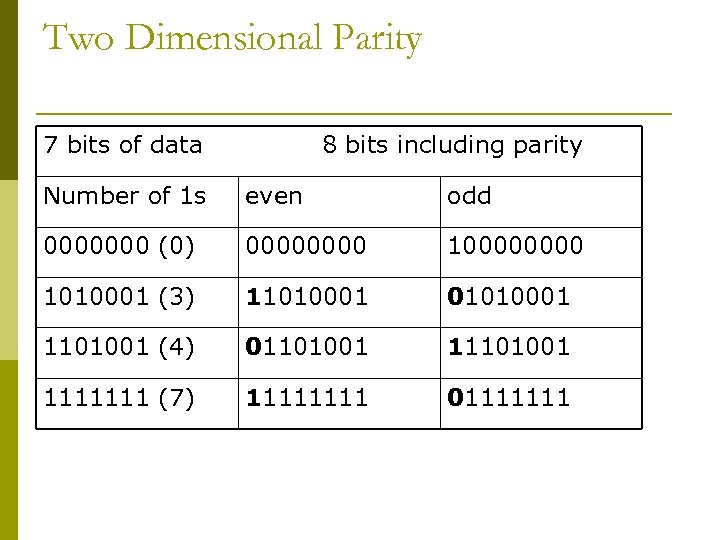 Two Dimensional Parity 7 bits of data 8 bits including parity Number of 1 s even odd 0000000 (0) 00000000 1010001 (3) 11010001 01010001 1101001 (4) 01101001 1111111 (7) 1111 01111111
Two Dimensional Parity 7 bits of data 8 bits including parity Number of 1 s even odd 0000000 (0) 00000000 1010001 (3) 11010001 01010001 1101001 (4) 01101001 1111111 (7) 1111 01111111
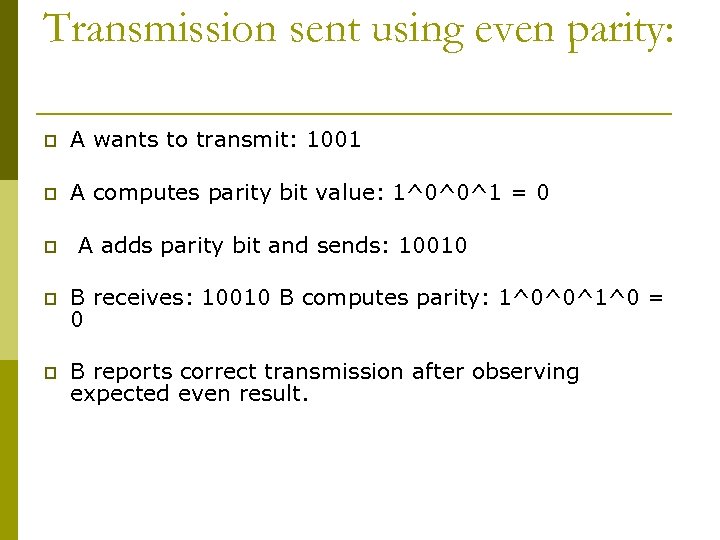 Transmission sent using even parity: p A wants to transmit: 1001 p A computes parity bit value: 1^0^0^1 = 0 p A adds parity bit and sends: 10010 p B receives: 10010 B computes parity: 1^0^0^1^0 = 0 p B reports correct transmission after observing expected even result.
Transmission sent using even parity: p A wants to transmit: 1001 p A computes parity bit value: 1^0^0^1 = 0 p A adds parity bit and sends: 10010 p B receives: 10010 B computes parity: 1^0^0^1^0 = 0 p B reports correct transmission after observing expected even result.
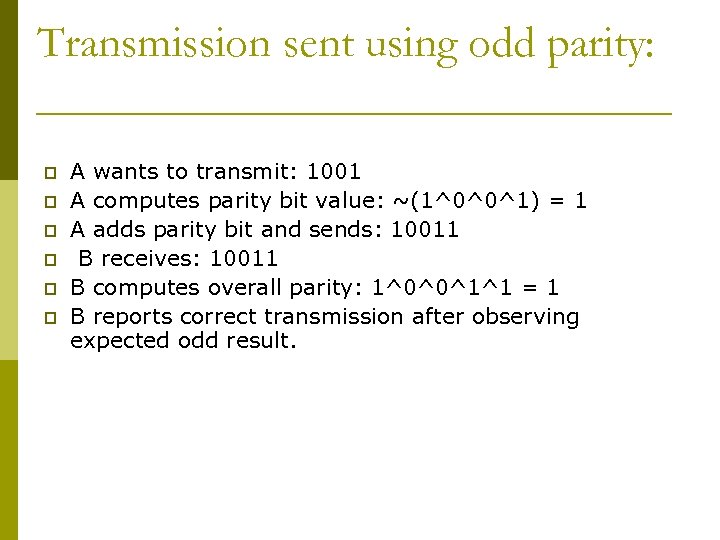 Transmission sent using odd parity: p p p A wants to transmit: 1001 A computes parity bit value: ~(1^0^0^1) = 1 A adds parity bit and sends: 10011 B receives: 10011 B computes overall parity: 1^0^0^1^1 = 1 B reports correct transmission after observing expected odd result.
Transmission sent using odd parity: p p p A wants to transmit: 1001 A computes parity bit value: ~(1^0^0^1) = 1 A adds parity bit and sends: 10011 B receives: 10011 B computes overall parity: 1^0^0^1^1 = 1 B reports correct transmission after observing expected odd result.
 Reliable Transmission Deliver Frames Reliably Accomplished by Acknowledgements and Timeouts ARQ-Automatic Repeat Request Mechanism: Stop and Wait Sliding Window Concurrent Logical Channels
Reliable Transmission Deliver Frames Reliably Accomplished by Acknowledgements and Timeouts ARQ-Automatic Repeat Request Mechanism: Stop and Wait Sliding Window Concurrent Logical Channels
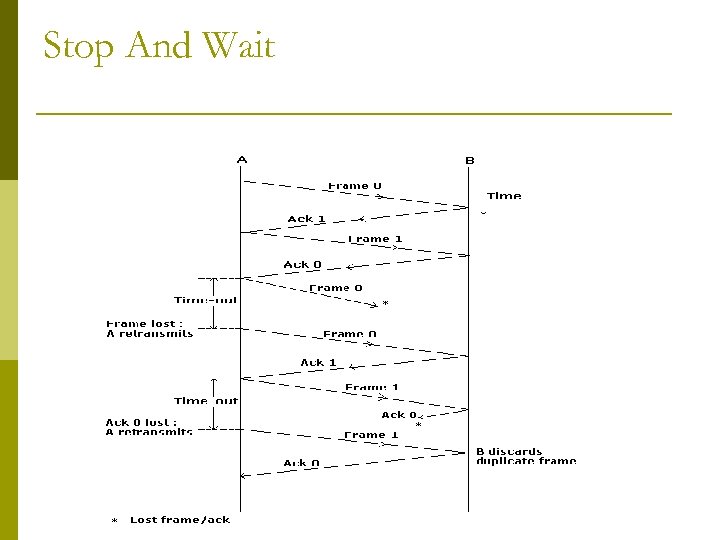
 Stop And Wait ARQ p The source station transmits a single frame and then waits for an acknowledgement (ACK). p Data frames cannot be sent until the destination station’s reply arrives at the source station. p It discards the frame and sends a negative acknowledgement (NAK) back to the sender causes the source to retransmit the damaged frame in case of error p
Stop And Wait ARQ p The source station transmits a single frame and then waits for an acknowledgement (ACK). p Data frames cannot be sent until the destination station’s reply arrives at the source station. p It discards the frame and sends a negative acknowledgement (NAK) back to the sender causes the source to retransmit the damaged frame in case of error p
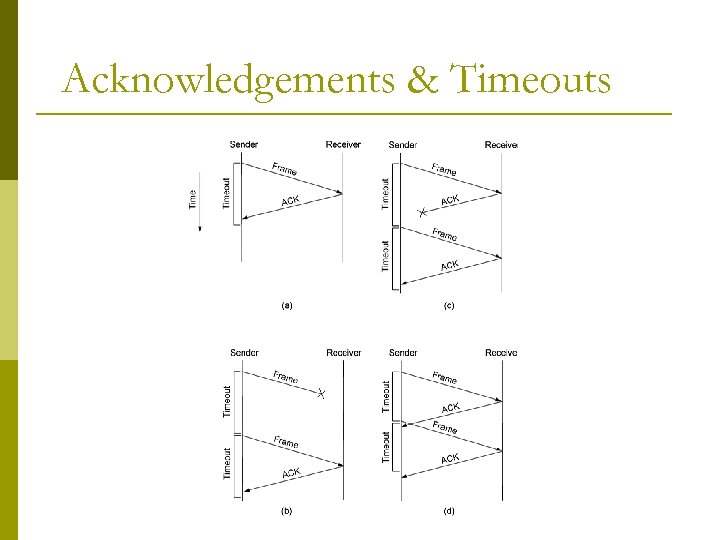 Acknowledgements & Timeouts
Acknowledgements & Timeouts
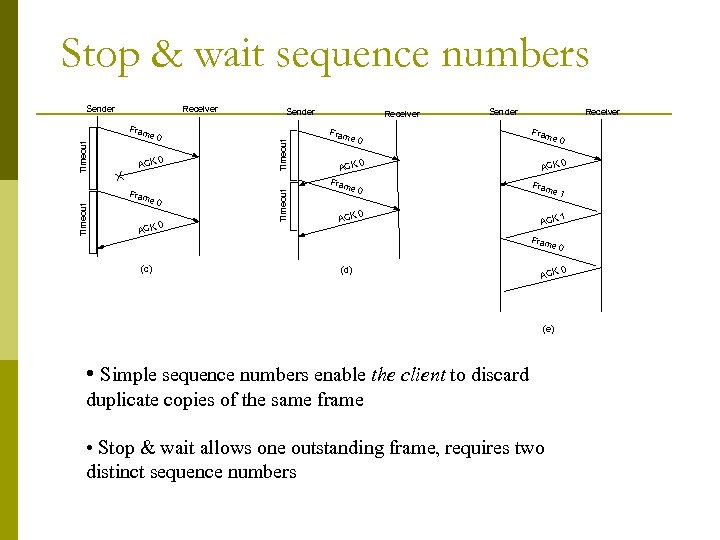 Stop & wait sequence numbers Sender Receiver Sender ACK 0 Timeout Fram e 0 0 ACK Timeout e 0 Timeout Fram Receiver Sender Fram e 0 ACK 0 Fram e 0 0 ACK Receiver Fram e 0 ACK 0 Fram e 1 ACK 1 Fram e 0 (c) (d) ACK (e) • Simple sequence numbers enable the client to discard duplicate copies of the same frame • Stop & wait allows one outstanding frame, requires two distinct sequence numbers 0
Stop & wait sequence numbers Sender Receiver Sender ACK 0 Timeout Fram e 0 0 ACK Timeout e 0 Timeout Fram Receiver Sender Fram e 0 ACK 0 Fram e 0 0 ACK Receiver Fram e 0 ACK 0 Fram e 1 ACK 1 Fram e 0 (c) (d) ACK (e) • Simple sequence numbers enable the client to discard duplicate copies of the same frame • Stop & wait allows one outstanding frame, requires two distinct sequence numbers 0
 Stop And Wait
Stop And Wait
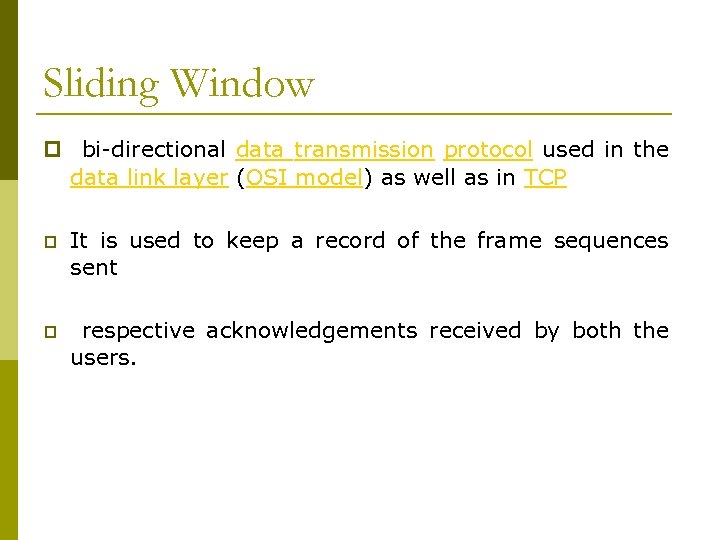 Sliding Window p bi-directional data transmission protocol used in the data link layer (OSI model) as well as in TCP p It is used to keep a record of the frame sequences sent p respective acknowledgements received by both the users.
Sliding Window p bi-directional data transmission protocol used in the data link layer (OSI model) as well as in TCP p It is used to keep a record of the frame sequences sent p respective acknowledgements received by both the users.
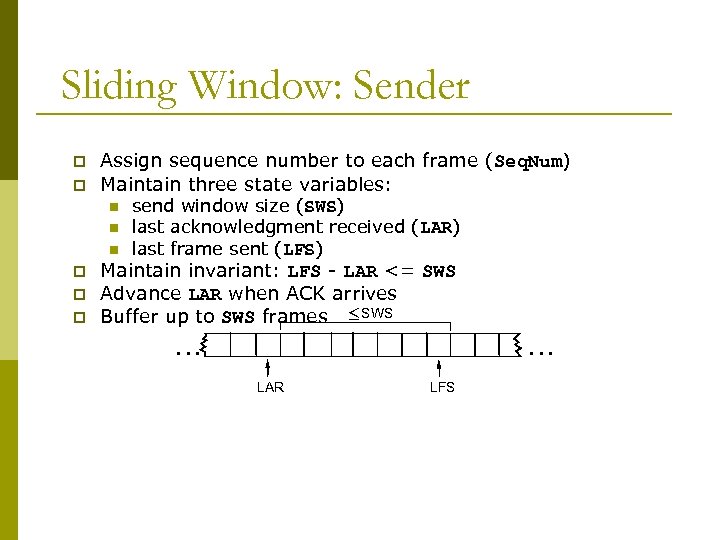 Sliding Window: Sender p p Assign sequence number to each frame (Seq. Num) Maintain three state variables: n n n p p p send window size (SWS) last acknowledgment received (LAR) last frame sent (LFS) Maintain invariant: LFS - LAR <= SWS Advance LAR when ACK arrives Buffer up to SWS frames £ SWS … … LAR LFS
Sliding Window: Sender p p Assign sequence number to each frame (Seq. Num) Maintain three state variables: n n n p p p send window size (SWS) last acknowledgment received (LAR) last frame sent (LFS) Maintain invariant: LFS - LAR <= SWS Advance LAR when ACK arrives Buffer up to SWS frames £ SWS … … LAR LFS
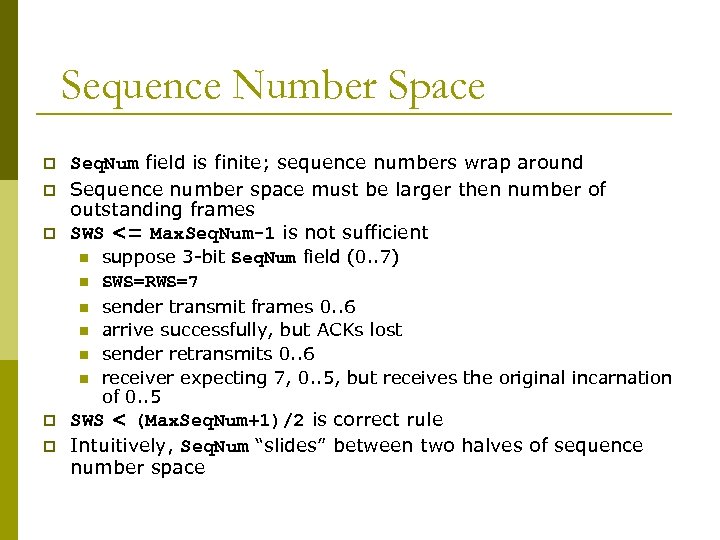 Sequence Number Space p p p Seq. Num field is finite; sequence numbers wrap around Sequence number space must be larger then number of outstanding frames SWS <= Max. Seq. Num-1 is not sufficient n n n p p suppose 3 -bit Seq. Num field (0. . 7) SWS=RWS=7 sender transmit frames 0. . 6 arrive successfully, but ACKs lost sender retransmits 0. . 6 receiver expecting 7, 0. . 5, but receives the original incarnation of 0. . 5 SWS < (Max. Seq. Num+1)/2 is correct rule Intuitively, Seq. Num “slides” between two halves of sequence number space
Sequence Number Space p p p Seq. Num field is finite; sequence numbers wrap around Sequence number space must be larger then number of outstanding frames SWS <= Max. Seq. Num-1 is not sufficient n n n p p suppose 3 -bit Seq. Num field (0. . 7) SWS=RWS=7 sender transmit frames 0. . 6 arrive successfully, but ACKs lost sender retransmits 0. . 6 receiver expecting 7, 0. . 5, but receives the original incarnation of 0. . 5 SWS < (Max. Seq. Num+1)/2 is correct rule Intuitively, Seq. Num “slides” between two halves of sequence number space
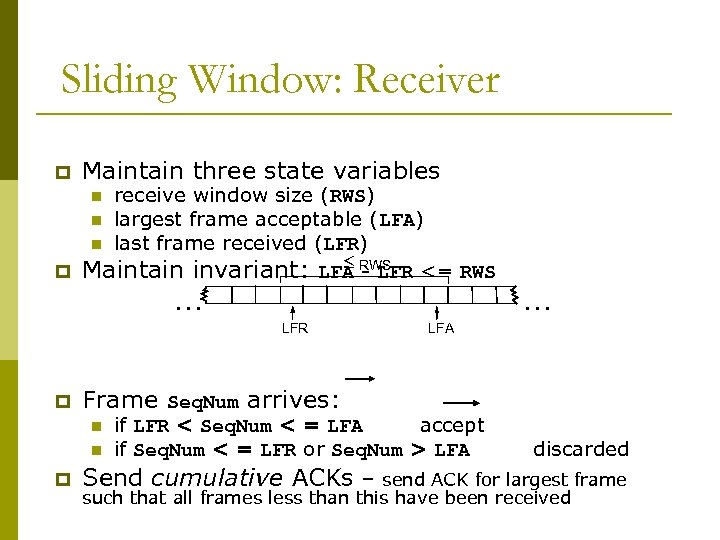 Sliding Window: Receiver p Maintain three state variables receive window size (RWS) n largest frame acceptable (LFA) n last frame received (LFR) £ RWS p Maintain invariant: LFA - LFR <= RWS n … LFR p … LFA Frame Seq. Num arrives: if LFR < Seq. Num < = LFA accept n if Seq. Num < = LFR or Seq. Num > LFA discarded p Send cumulative ACKs – send ACK for largest frame n such that all frames less than this have been received
Sliding Window: Receiver p Maintain three state variables receive window size (RWS) n largest frame acceptable (LFA) n last frame received (LFR) £ RWS p Maintain invariant: LFA - LFR <= RWS n … LFR p … LFA Frame Seq. Num arrives: if LFR < Seq. Num < = LFA accept n if Seq. Num < = LFR or Seq. Num > LFA discarded p Send cumulative ACKs – send ACK for largest frame n such that all frames less than this have been received
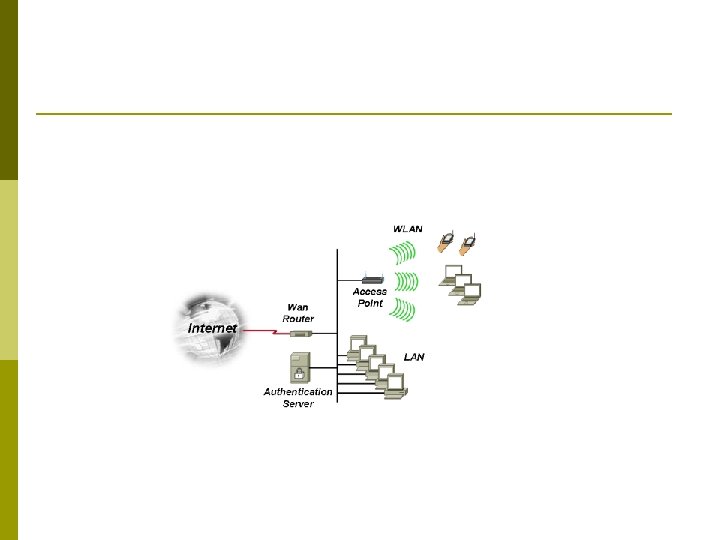
 UNIT II LAN Technology p p LAN (Local Area Network) refers to a group of computers interconnected into a network Objective: they are able to communicate, exchange information and share resources (e. g. printers, application programs, database etc). the same computer resources can be used by multiple users in the network, regardless of the physical location of the resources.
UNIT II LAN Technology p p LAN (Local Area Network) refers to a group of computers interconnected into a network Objective: they are able to communicate, exchange information and share resources (e. g. printers, application programs, database etc). the same computer resources can be used by multiple users in the network, regardless of the physical location of the resources.
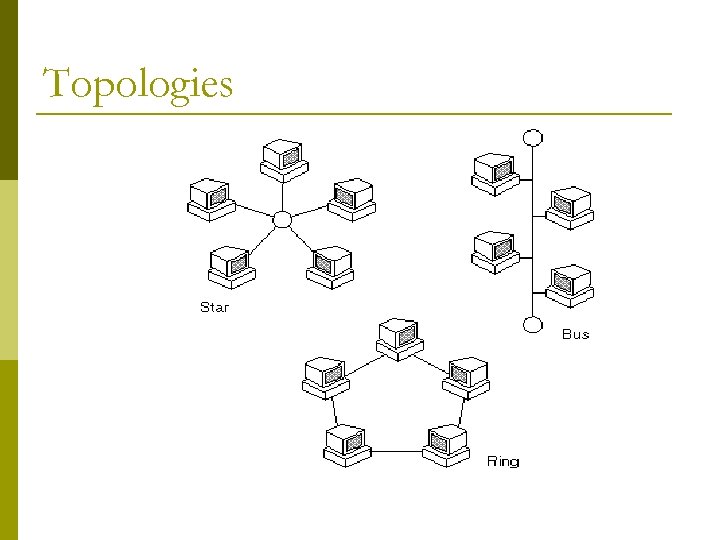
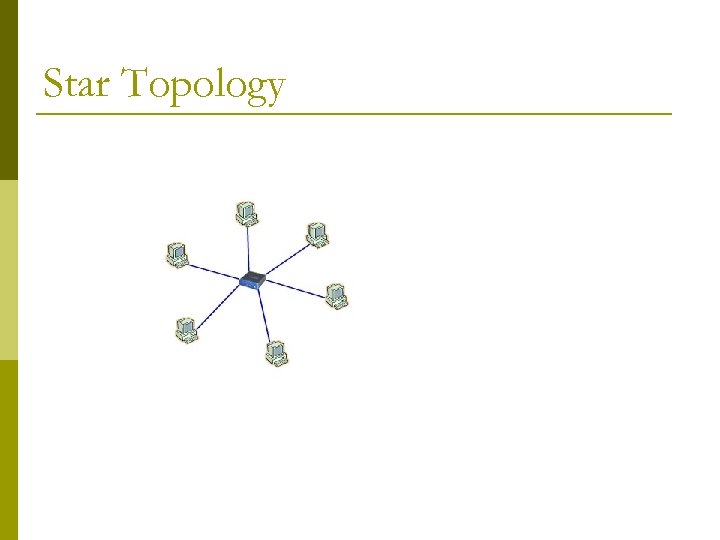
 LAN Architecture Describes the way in which the components in a Local Area Network are connected LAN Topologies: Star Ring Bus Tree
LAN Architecture Describes the way in which the components in a Local Area Network are connected LAN Topologies: Star Ring Bus Tree
 Star p All stations are connected by cable (or wireless) to a central point, such as hub or a switch. p central node is operating in a broadcast fashion such as a Hub transmission of a frame from one station to the node is retransmitted on all of the outgoing links. p
Star p All stations are connected by cable (or wireless) to a central point, such as hub or a switch. p central node is operating in a broadcast fashion such as a Hub transmission of a frame from one station to the node is retransmitted on all of the outgoing links. p
 Ring All nodes on the LAN are connected in a loop and their Network Interface Cards (NIC) are working as repeaters. No starting or ending point. Each node will repeat any signal that is on the network regardless its destination. The destination station recognizes its address and copies the frame into a local buffer. The frame continues to circulate until it returns to the source station, where it is removed. Example: Token Ring (IEEE 802. 5) FDDI (IEEE 802. 6) another protocol used in the
Ring All nodes on the LAN are connected in a loop and their Network Interface Cards (NIC) are working as repeaters. No starting or ending point. Each node will repeat any signal that is on the network regardless its destination. The destination station recognizes its address and copies the frame into a local buffer. The frame continues to circulate until it returns to the source station, where it is removed. Example: Token Ring (IEEE 802. 5) FDDI (IEEE 802. 6) another protocol used in the
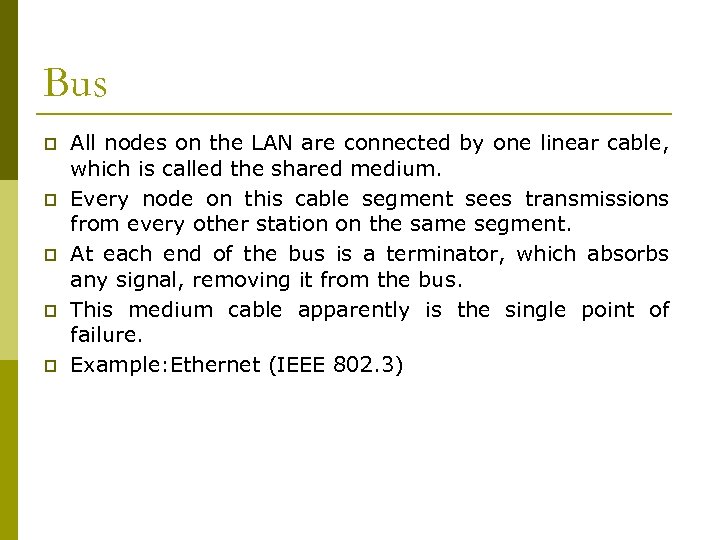 Bus p p p All nodes on the LAN are connected by one linear cable, which is called the shared medium. Every node on this cable segment sees transmissions from every other station on the same segment. At each end of the bus is a terminator, which absorbs any signal, removing it from the bus. This medium cable apparently is the single point of failure. Example: Ethernet (IEEE 802. 3)
Bus p p p All nodes on the LAN are connected by one linear cable, which is called the shared medium. Every node on this cable segment sees transmissions from every other station on the same segment. At each end of the bus is a terminator, which absorbs any signal, removing it from the bus. This medium cable apparently is the single point of failure. Example: Ethernet (IEEE 802. 3)
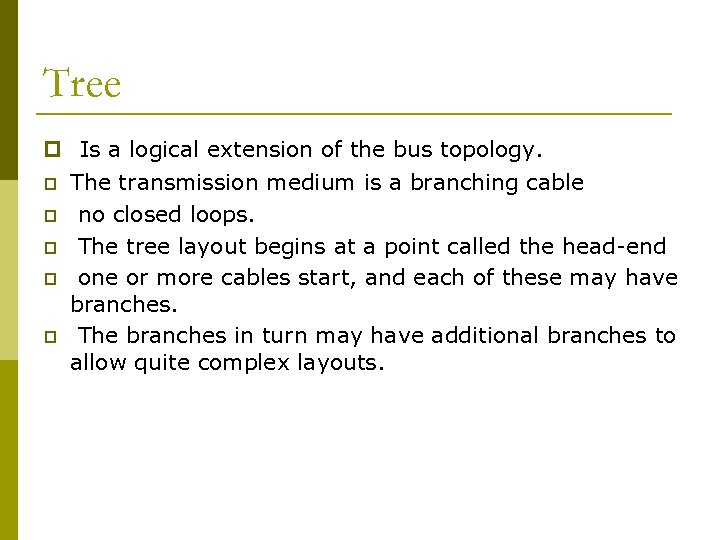 Tree p Is a logical extension of the bus topology. p p p The transmission medium is a branching cable no closed loops. The tree layout begins at a point called the head-end one or more cables start, and each of these may have branches. The branches in turn may have additional branches to allow quite complex layouts.
Tree p Is a logical extension of the bus topology. p p p The transmission medium is a branching cable no closed loops. The tree layout begins at a point called the head-end one or more cables start, and each of these may have branches. The branches in turn may have additional branches to allow quite complex layouts.
 Topologies
Topologies
 Token Ring p p p p All stations are connected in a ring and each station can directly hear transmissions only from its immediate neighbor. Permission to transmit is granted by a message (token) that circulates around the ring. Token Ring as defined in IEEE 802. 5 is originated from the IBM Token Ring LAN technologies. Token-passing networks move a small frame, called a token Possession of the token grants the right to transmit. The information frame circulates the ring until it reaches the intended destination station, which copies the information for further processing. The information frame continues to circle the ring and is finally removed when it reaches the sending station. The sending station can check the returning frame to see whether the frame was seen and subsequently copied by the destination.
Token Ring p p p p All stations are connected in a ring and each station can directly hear transmissions only from its immediate neighbor. Permission to transmit is granted by a message (token) that circulates around the ring. Token Ring as defined in IEEE 802. 5 is originated from the IBM Token Ring LAN technologies. Token-passing networks move a small frame, called a token Possession of the token grants the right to transmit. The information frame circulates the ring until it reaches the intended destination station, which copies the information for further processing. The information frame continues to circle the ring and is finally removed when it reaches the sending station. The sending station can check the returning frame to see whether the frame was seen and subsequently copied by the destination.
 Ehernet local-area network (LAN) covered by the IEEE 802. 3. p two modes of operation: p n n half-duplex full-duplex modes. .
Ehernet local-area network (LAN) covered by the IEEE 802. 3. p two modes of operation: p n n half-duplex full-duplex modes. .
 Three basic elements : 1. the physical medium used to carry Ethernet signals between computers, 2. a set of medium access control rules embedded in each Ethernet interface that allow multiple computers to fairly arbitrate access to the shared Ethernet channel, 3. an Ethernet frame that consists of a standardized set of bits used to carry data over the system
Three basic elements : 1. the physical medium used to carry Ethernet signals between computers, 2. a set of medium access control rules embedded in each Ethernet interface that allow multiple computers to fairly arbitrate access to the shared Ethernet channel, 3. an Ethernet frame that consists of a standardized set of bits used to carry data over the system
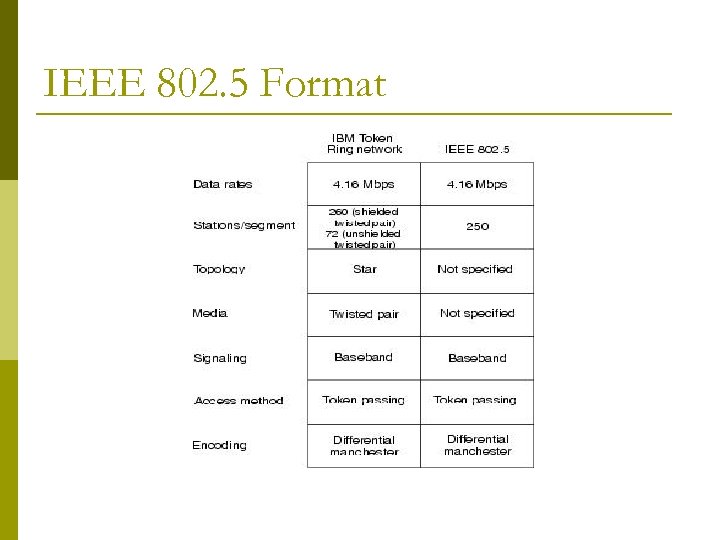 IEEE 802. 5 Format
IEEE 802. 5 Format
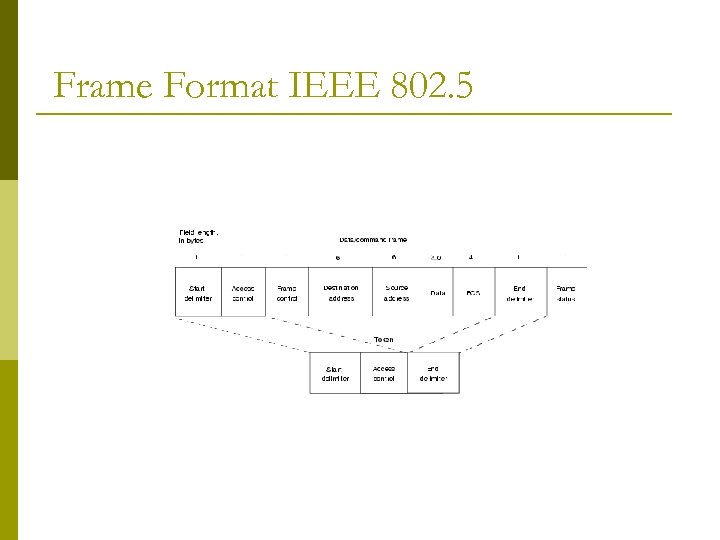 Frame Format IEEE 802. 5
Frame Format IEEE 802. 5
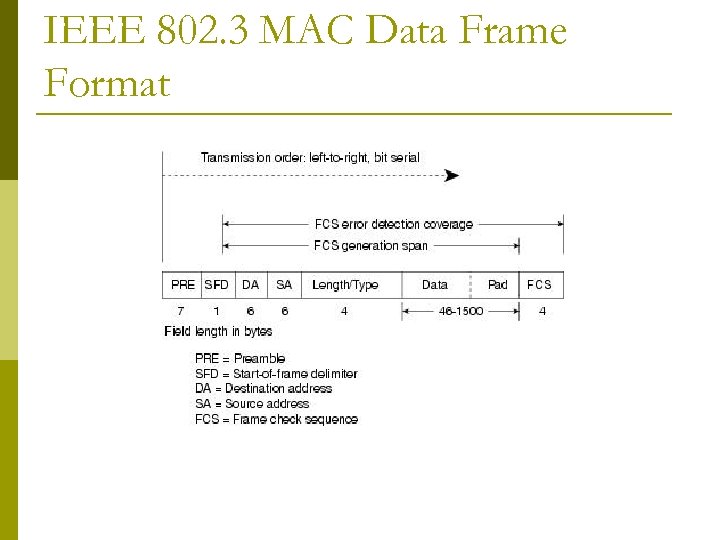 IEEE 802. 3 MAC Data Frame Format
IEEE 802. 3 MAC Data Frame Format
 Wireless p The process by which the radio waves are propagated through air and transmits data p Wireless technologies are differentiated by : p p p Protocol Connection type—Point-to-Point (P 2 P) Spectrum—Licensed or unlicensed
Wireless p The process by which the radio waves are propagated through air and transmits data p Wireless technologies are differentiated by : p p p Protocol Connection type—Point-to-Point (P 2 P) Spectrum—Licensed or unlicensed
 Types p Infrared Wireless Transmission n p Microwave Radio n p Tranmission of data signals using infrared-light waves sends data over long distances (regions, states, countries) at up to 2 megabits per second (AM/FM Radio) Communications Satellites n microwave relay stations in orbit around the earth.
Types p Infrared Wireless Transmission n p Microwave Radio n p Tranmission of data signals using infrared-light waves sends data over long distances (regions, states, countries) at up to 2 megabits per second (AM/FM Radio) Communications Satellites n microwave relay stations in orbit around the earth.
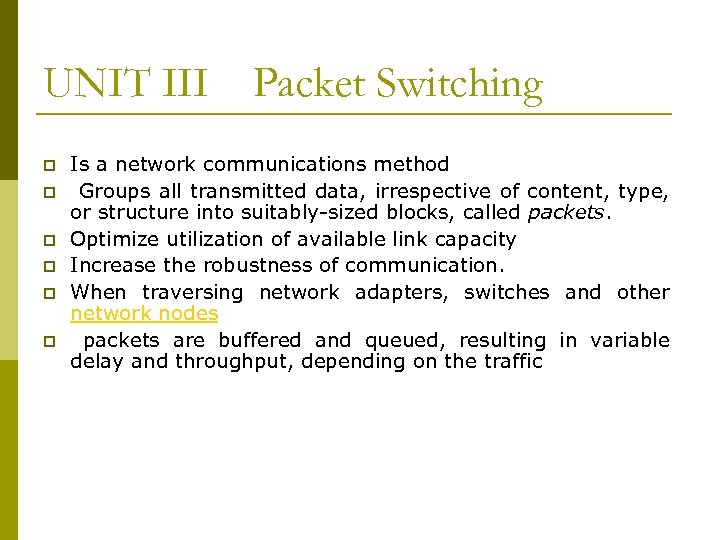 UNIT III p p p Packet Switching Is a network communications method Groups all transmitted data, irrespective of content, type, or structure into suitably-sized blocks, called packets. Optimize utilization of available link capacity Increase the robustness of communication. When traversing network adapters, switches and other network nodes packets are buffered and queued, resulting in variable delay and throughput, depending on the traffic
UNIT III p p p Packet Switching Is a network communications method Groups all transmitted data, irrespective of content, type, or structure into suitably-sized blocks, called packets. Optimize utilization of available link capacity Increase the robustness of communication. When traversing network adapters, switches and other network nodes packets are buffered and queued, resulting in variable delay and throughput, depending on the traffic
 Types p Connectionless each packet is labeled with a connection ID rather than an address. p Example: Datagram packet switching p p connection-oriented n n each packet is labeled with a destination address Example: X. 25 vs. Frame Relay
Types p Connectionless each packet is labeled with a connection ID rather than an address. p Example: Datagram packet switching p p connection-oriented n n each packet is labeled with a destination address Example: X. 25 vs. Frame Relay
 Star Topology
Star Topology
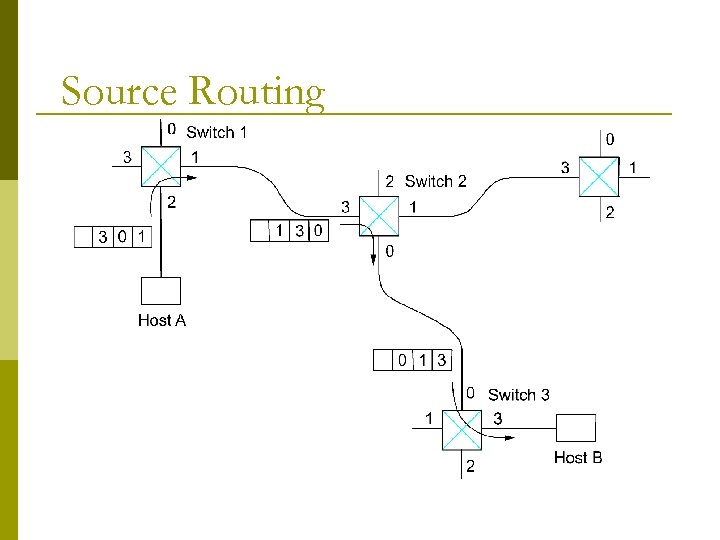 Source Routing
Source Routing
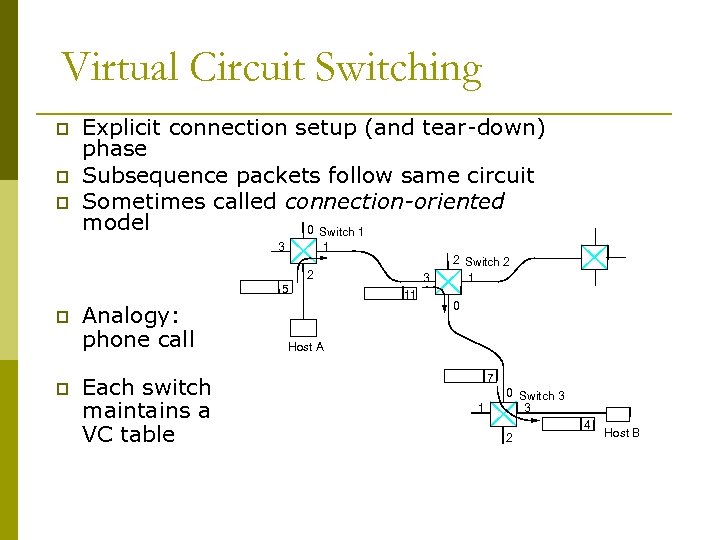 Virtual Circuit Switching p p p Explicit connection setup (and tear-down) phase Subsequence packets follow same circuit Sometimes called connection-oriented model 0 Switch 1 3 1 2 5 p p Analogy: phone call Each switch maintains a VC table 3 11 2 Switch 2 1 0 Host A 7 1 0 Switch 3 3 2 4 Host B
Virtual Circuit Switching p p p Explicit connection setup (and tear-down) phase Subsequence packets follow same circuit Sometimes called connection-oriented model 0 Switch 1 3 1 2 5 p p Analogy: phone call Each switch maintains a VC table 3 11 2 Switch 2 1 0 Host A 7 1 0 Switch 3 3 2 4 Host B
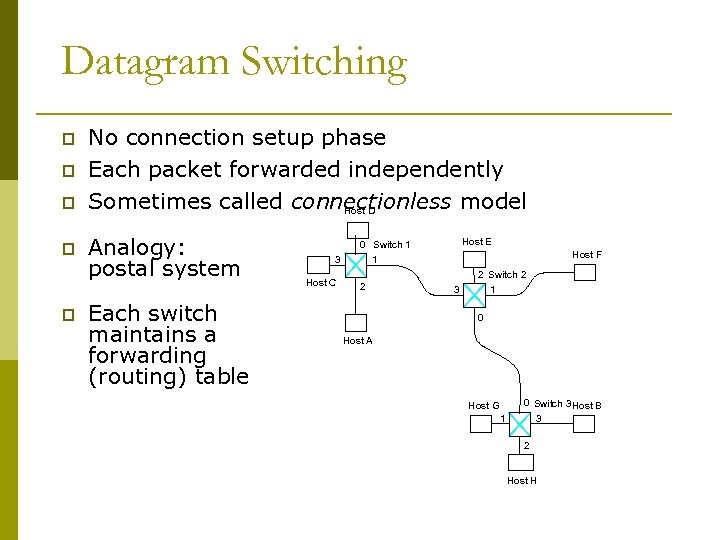 Datagram Switching p p p No connection setup phase Each packet forwarded independently Sometimes called connectionless model Host D Analogy: postal system Each switch maintains a forwarding (routing) table 3 Host C Host E 0 Switch 1 1 2 Host F 3 2 Switch 2 1 0 Host A Host G 1 0 Switch 3 Host B 3 2 Host H
Datagram Switching p p p No connection setup phase Each packet forwarded independently Sometimes called connectionless model Host D Analogy: postal system Each switch maintains a forwarding (routing) table 3 Host C Host E 0 Switch 1 1 2 Host F 3 2 Switch 2 1 0 Host A Host G 1 0 Switch 3 Host B 3 2 Host H
 Virtual Circuit Model p Typically wait full RTT for connection setup before sending first data packet. p While the connection request contains the full address for destination each data packet contains only a small identifier, making the per-packet header overhead small. p p If a switch or a link in a connection fails, the connection is broken and a new one needs to be established. p Connection setup provides an opportunity to reserve resources.
Virtual Circuit Model p Typically wait full RTT for connection setup before sending first data packet. p While the connection request contains the full address for destination each data packet contains only a small identifier, making the per-packet header overhead small. p p If a switch or a link in a connection fails, the connection is broken and a new one needs to be established. p Connection setup provides an opportunity to reserve resources.
 Datagram Model p There is no round trip delay waiting for connection setup; a host can send data as soon as it is ready. p Source host has no way of knowing if the network is capable of delivering a packet or if the destination host is even up. p Since packets are treated independently, it is possible to route around link and node failures. p Since every packet must carry the full address of the destination, the overhead per packet is higher than for the connection-oriented model.
Datagram Model p There is no round trip delay waiting for connection setup; a host can send data as soon as it is ready. p Source host has no way of knowing if the network is capable of delivering a packet or if the destination host is even up. p Since packets are treated independently, it is possible to route around link and node failures. p Since every packet must carry the full address of the destination, the overhead per packet is higher than for the connection-oriented model.
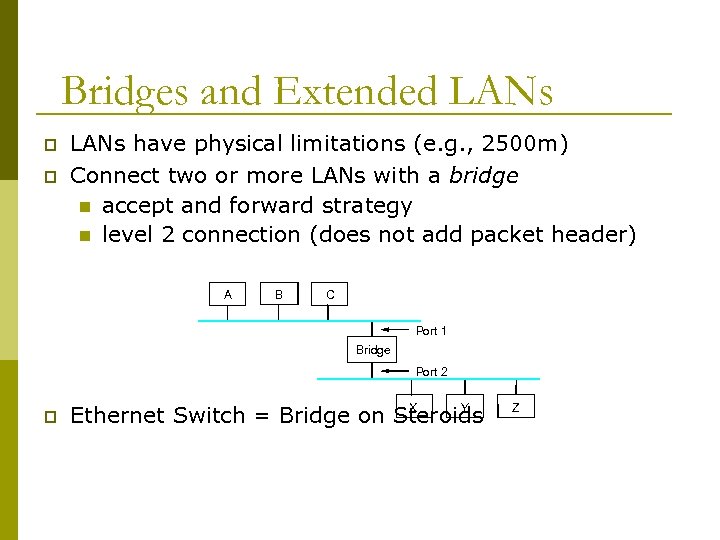 Bridges and Extended LANs p p LANs have physical limitations (e. g. , 2500 m) Connect two or more LANs with a bridge n accept and forward strategy n level 2 connection (does not add packet header) A B C Port 1 Bridge Port 2 p X Y Ethernet Switch = Bridge on Steroids Z
Bridges and Extended LANs p p LANs have physical limitations (e. g. , 2500 m) Connect two or more LANs with a bridge n accept and forward strategy n level 2 connection (does not add packet header) A B C Port 1 Bridge Port 2 p X Y Ethernet Switch = Bridge on Steroids Z
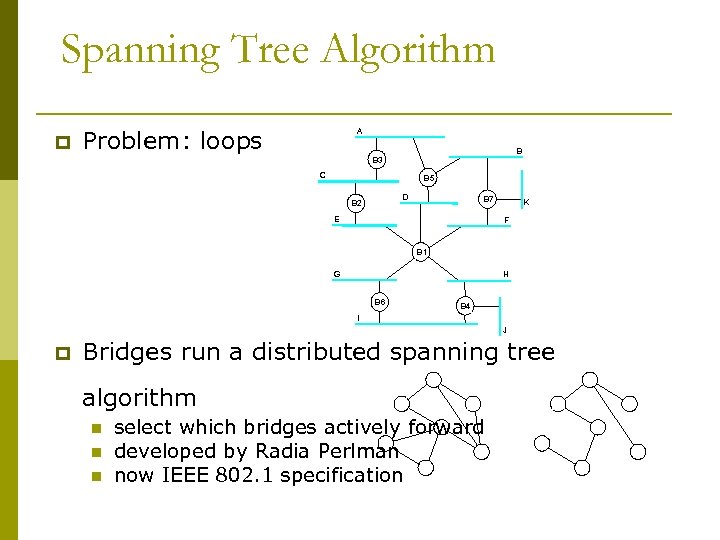 Spanning Tree Algorithm p Problem: loops A B B 3 C B 5 D B 2 B 7 E K F B 1 G H B 6 B 4 I J p Bridges run a distributed spanning tree algorithm n n n select which bridges actively forward developed by Radia Perlman now IEEE 802. 1 specification
Spanning Tree Algorithm p Problem: loops A B B 3 C B 5 D B 2 B 7 E K F B 1 G H B 6 B 4 I J p Bridges run a distributed spanning tree algorithm n n n select which bridges actively forward developed by Radia Perlman now IEEE 802. 1 specification
 Algorithm Details p p p Bridges exchange configuration messages n id for bridge sending the message n id for what the sending bridge believes to be root bridge n distance (hops) from sending bridge to root bridge Each bridge records current best configuration message for each port Initially, each bridge believes it is the root
Algorithm Details p p p Bridges exchange configuration messages n id for bridge sending the message n id for what the sending bridge believes to be root bridge n distance (hops) from sending bridge to root bridge Each bridge records current best configuration message for each port Initially, each bridge believes it is the root
 Algorithm Details p p p Bridges exchange configuration messages n id for bridge sending the message n id for what the sending bridge believes to be root bridge n distance (hops) from sending bridge to root bridge Each bridge records current best configuration message for each port Initially, each bridge believes it is the root
Algorithm Details p p p Bridges exchange configuration messages n id for bridge sending the message n id for what the sending bridge believes to be root bridge n distance (hops) from sending bridge to root bridge Each bridge records current best configuration message for each port Initially, each bridge believes it is the root
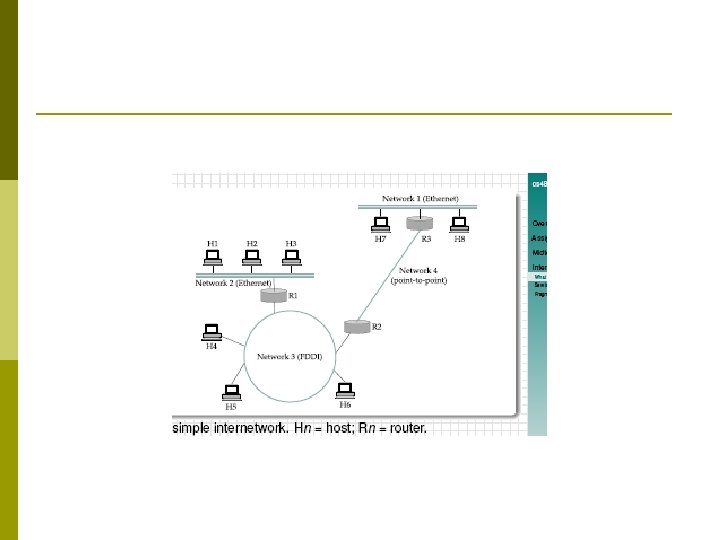
 Internetworking p An internetwork is a collection of individual networks, connected by intermediate networking devices, that functions as a single large network. p different kinds of network technologies that can be interconnected by routers and other networking devices to create an internetwork
Internetworking p An internetwork is a collection of individual networks, connected by intermediate networking devices, that functions as a single large network. p different kinds of network technologies that can be interconnected by routers and other networking devices to create an internetwork
 Types p Local-area networks (LANs)enabled multiple users in a relatively small geographical area to exchange files and messages, as well as access shared resources such as file servers and printers. p Wide-area networks (WANs) interconnect LANs with geographically dispersed users to create connectivity. p technologies used for connecting LANs include T 1, T 3, ATM, ISDN, ADSL, Frame Relay, radio links, and others.
Types p Local-area networks (LANs)enabled multiple users in a relatively small geographical area to exchange files and messages, as well as access shared resources such as file servers and printers. p Wide-area networks (WANs) interconnect LANs with geographically dispersed users to create connectivity. p technologies used for connecting LANs include T 1, T 3, ATM, ISDN, ADSL, Frame Relay, radio links, and others.
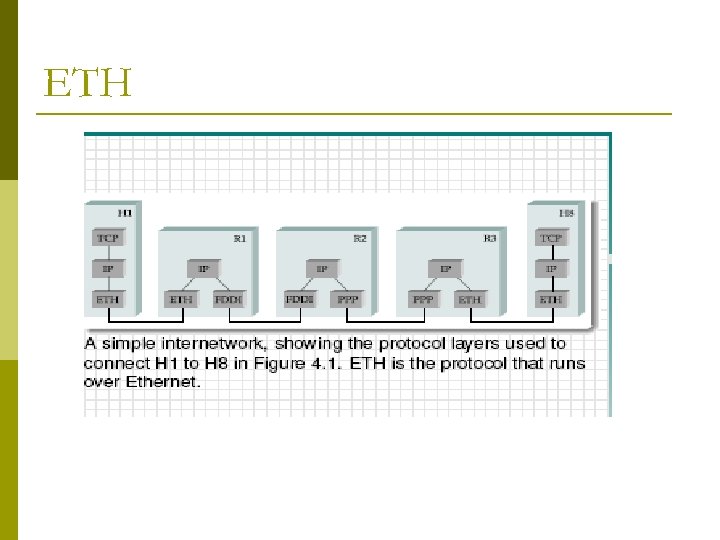 ETH
ETH
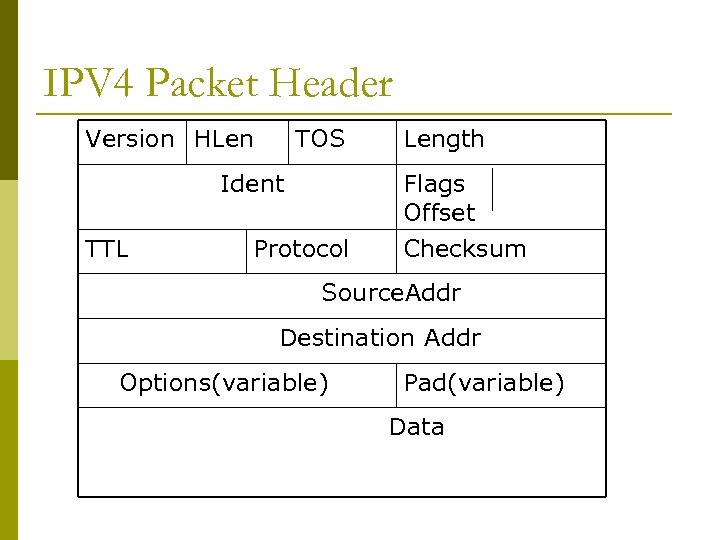 IPV 4 Packet Header Version HLen TOS Length Ident Flags Offset TTL Checksum Protocol Source. Addr Destination Addr Options(variable) Pad(variable) Data
IPV 4 Packet Header Version HLen TOS Length Ident Flags Offset TTL Checksum Protocol Source. Addr Destination Addr Options(variable) Pad(variable) Data
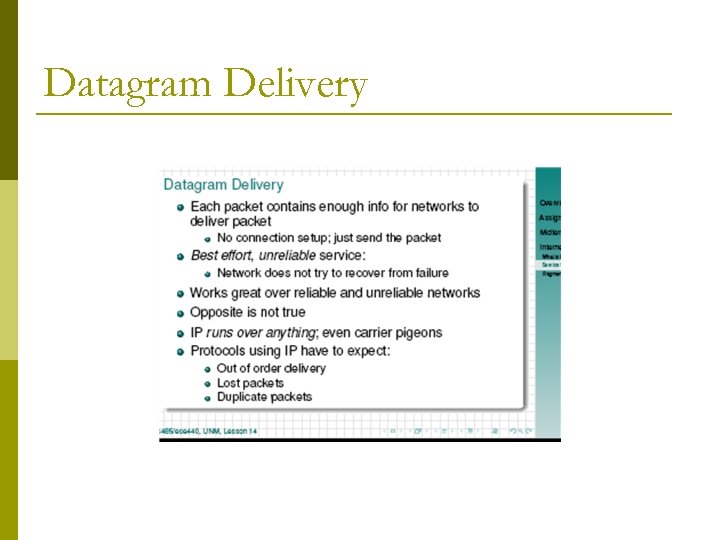 Datagram Delivery
Datagram Delivery
 Packet Format
Packet Format
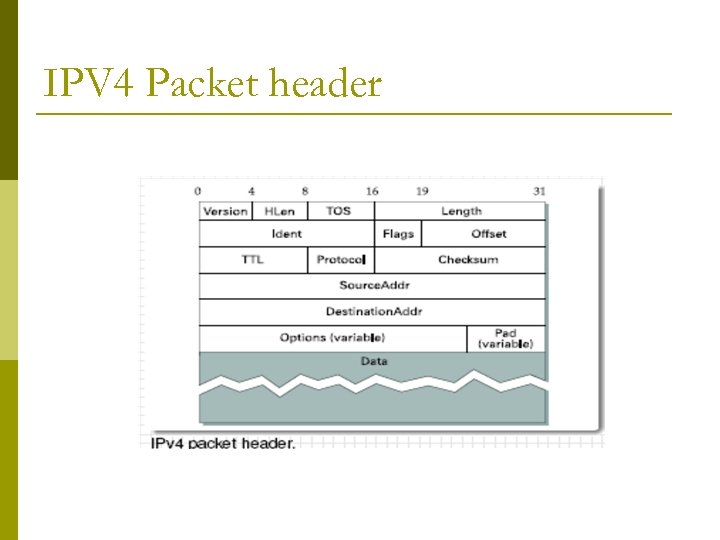 IPV 4 Packet header
IPV 4 Packet header
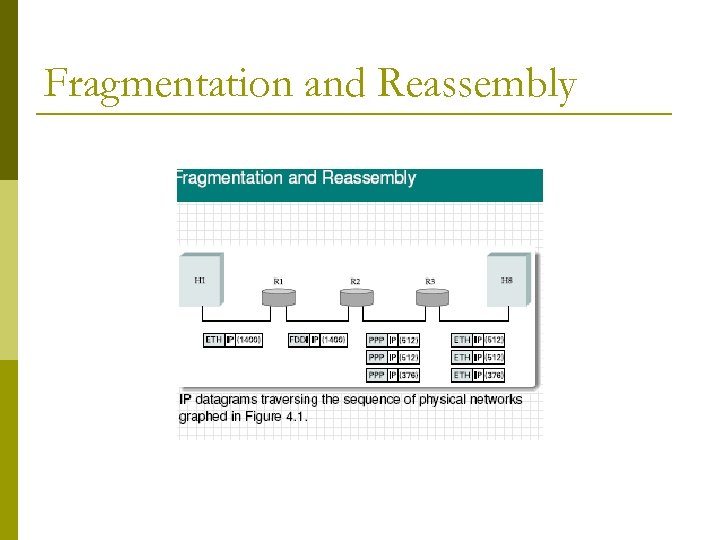
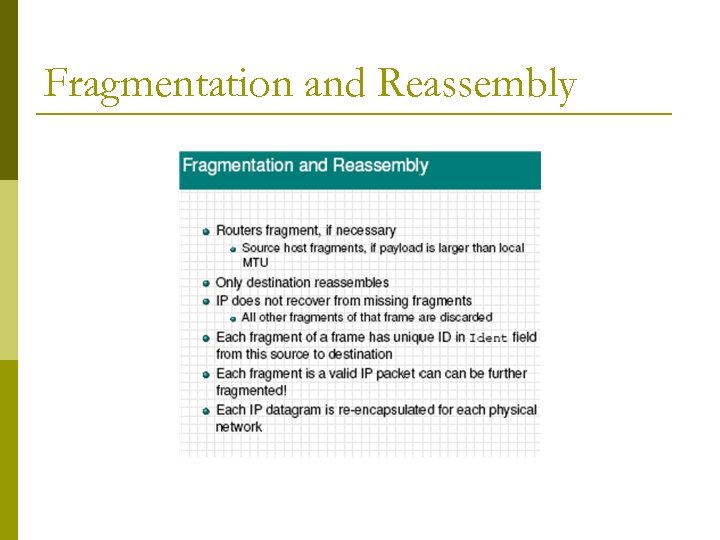 Fragmentation and Reassembly
Fragmentation and Reassembly
 Fragmentation and Reassembly
Fragmentation and Reassembly
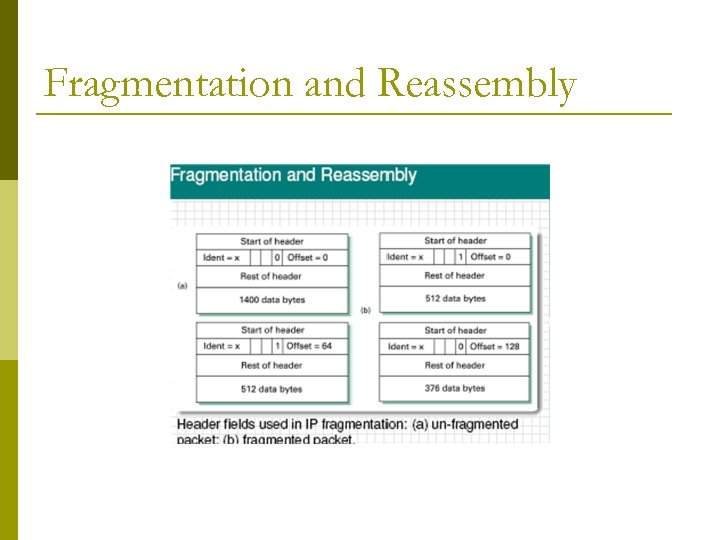 Fragmentation and Reassembly
Fragmentation and Reassembly
 (RARP)Reverse Address Resolution Protocol p p p (RARP) is a Link layer networking protocol RARP is described in internet Engineering. Task Force. ETF) publication RFC 903 It has been rendered obsolete by the Bootstrap Protocol (BOOTP) and the modern Dynamic Host Configuration Protocol(DHCP) BOOTP configuration server assigns an IP address to each client from a pool of addresses. BOOTP uses the User Datagram Protocol (UDP)
(RARP)Reverse Address Resolution Protocol p p p (RARP) is a Link layer networking protocol RARP is described in internet Engineering. Task Force. ETF) publication RFC 903 It has been rendered obsolete by the Bootstrap Protocol (BOOTP) and the modern Dynamic Host Configuration Protocol(DHCP) BOOTP configuration server assigns an IP address to each client from a pool of addresses. BOOTP uses the User Datagram Protocol (UDP)
 Routing p is the process of selecting paths in a network along which to send network traffic. p Routing is performed for many kinds of networks, including the telephone network electronic data networks (such as the Internet), and transportation networks.
Routing p is the process of selecting paths in a network along which to send network traffic. p Routing is performed for many kinds of networks, including the telephone network electronic data networks (such as the Internet), and transportation networks.
 Components p p p determining optimal routing paths and transporting information groups (typically called packets) through an internetwork. In the context of the routing process, the latter of these is referred to as packet switching. Although packet switching is relatively straightforward, path determination can be very complex.
Components p p p determining optimal routing paths and transporting information groups (typically called packets) through an internetwork. In the context of the routing process, the latter of these is referred to as packet switching. Although packet switching is relatively straightforward, path determination can be very complex.
 Distance Vector: p p p Distance Vector routing protocols are based on Bellman and Ford algorithms. Distance Vector routing protocols are less scalable such as RIP supports 16 hops and IGRP has a maximum of 100 hops. Distance Vector are classful routing protocols which means that there is no support of Variable Length Subnet Mask (VLSM) and Classless Inter Domain Routing (CIDR). Distance Vector routing protocols uses hop count and composite metric. Distance Vector routing protocols support discontiguous subnets.
Distance Vector: p p p Distance Vector routing protocols are based on Bellman and Ford algorithms. Distance Vector routing protocols are less scalable such as RIP supports 16 hops and IGRP has a maximum of 100 hops. Distance Vector are classful routing protocols which means that there is no support of Variable Length Subnet Mask (VLSM) and Classless Inter Domain Routing (CIDR). Distance Vector routing protocols uses hop count and composite metric. Distance Vector routing protocols support discontiguous subnets.
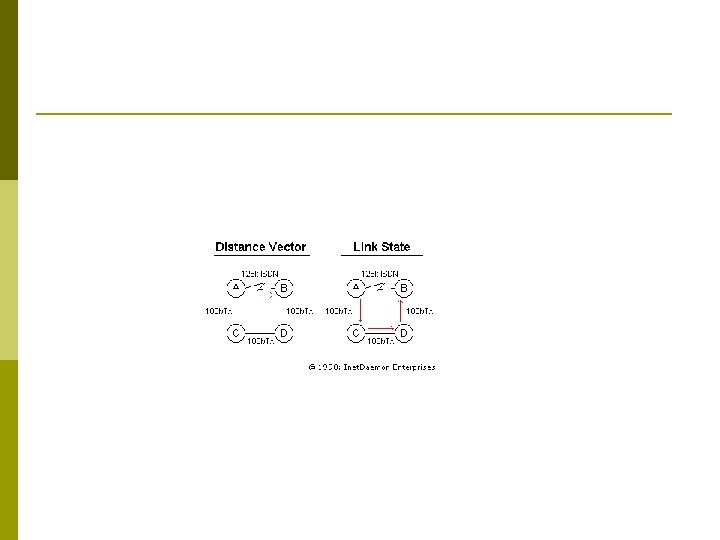
 Link State: p p p Link State routing protocols are based on Dijkstra algorithms. Link State routing protocols are very much scalable supports infinite hops. Link State routing protocols are classless which means that they support VLSM and CIDR. Cost is the metric of the Link State routing protocols support contiguous subnets.
Link State: p p p Link State routing protocols are based on Dijkstra algorithms. Link State routing protocols are very much scalable supports infinite hops. Link State routing protocols are classless which means that they support VLSM and CIDR. Cost is the metric of the Link State routing protocols support contiguous subnets.
 UNIT IV Reliable Byte Stream
UNIT IV Reliable Byte Stream
 TCP Overview
TCP Overview
 End to end issues
End to end issues
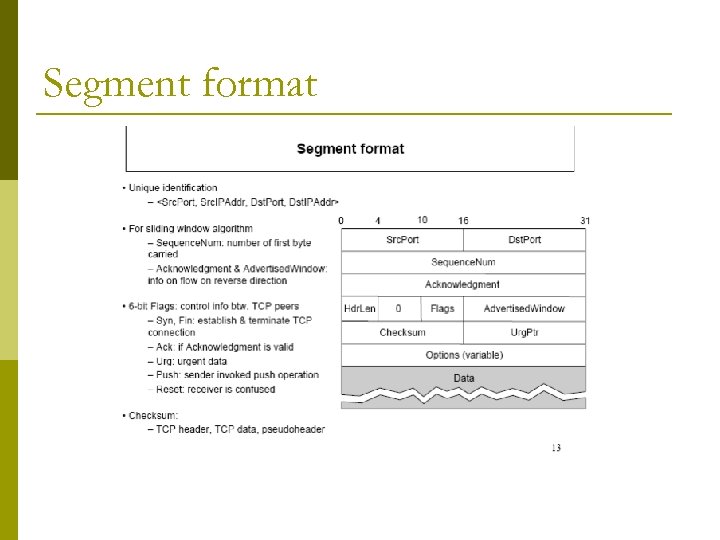 Segment format
Segment format
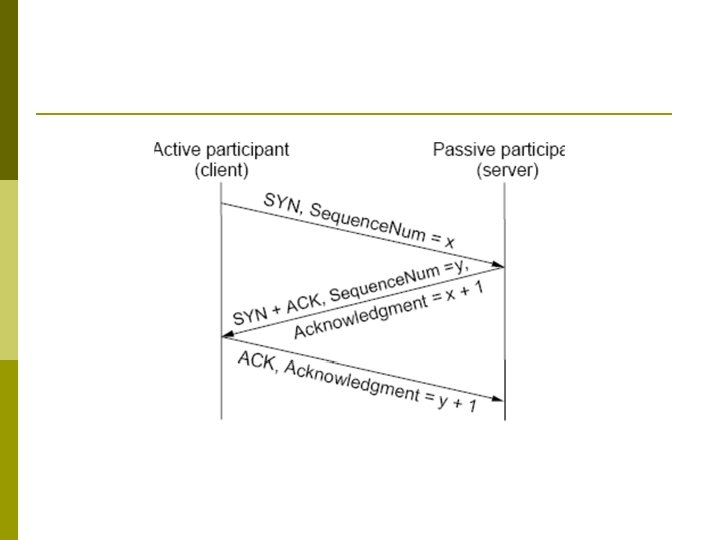
 Connection establishment
Connection establishment
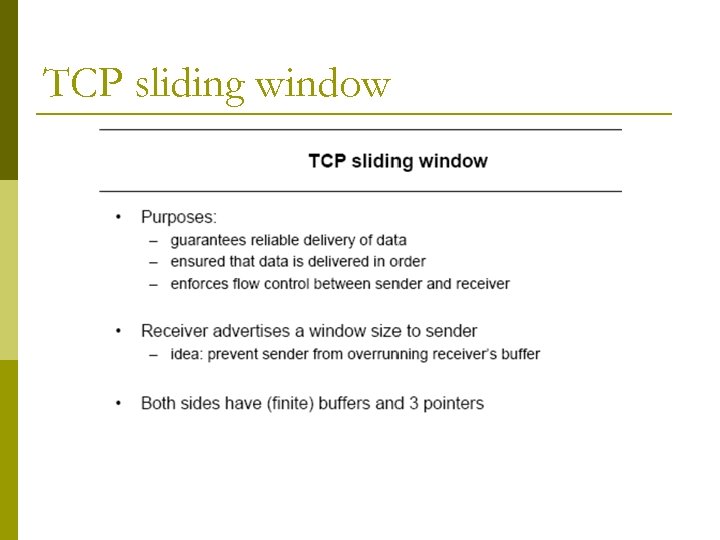 TCP sliding window
TCP sliding window

 Stream control Transmission Protocol
Stream control Transmission Protocol
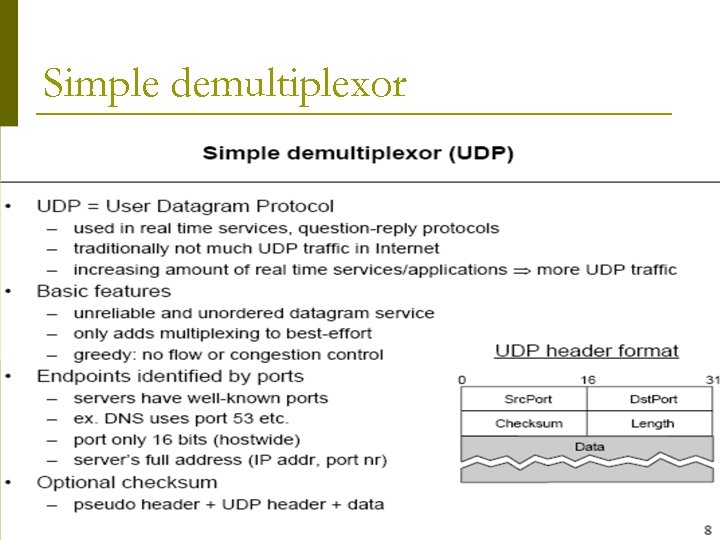 Simple demultiplexor
Simple demultiplexor
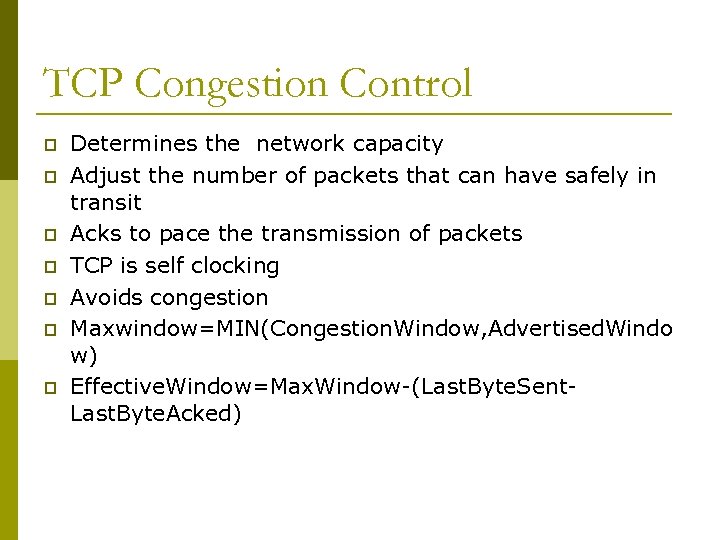 TCP Congestion Control p p p p Determines the network capacity Adjust the number of packets that can have safely in transit Acks to pace the transmission of packets TCP is self clocking Avoids congestion Maxwindow=MIN(Congestion. Window, Advertised. Windo w) Effective. Window=Max. Window-(Last. Byte. Sent. Last. Byte. Acked)
TCP Congestion Control p p p p Determines the network capacity Adjust the number of packets that can have safely in transit Acks to pace the transmission of packets TCP is self clocking Avoids congestion Maxwindow=MIN(Congestion. Window, Advertised. Windo w) Effective. Window=Max. Window-(Last. Byte. Sent. Last. Byte. Acked)
 Caused By p the shortage of buffer space. slow links. slow processors p Possible solutions p p n n p End-to-end versus link-by-link control Rate-Based versus Credit-Based control The rate-based traffic-flow technique constantly Integrated congestion control
Caused By p the shortage of buffer space. slow links. slow processors p Possible solutions p p n n p End-to-end versus link-by-link control Rate-Based versus Credit-Based control The rate-based traffic-flow technique constantly Integrated congestion control
 Principles of Congestion Control Congestion: p p informally: “too many sources sending too much data too fast for network to handle” different from flow control! manifestations: n lost packets (buffer overflow at routers) n long delays (queueing in router buffers) a top-10 problem!
Principles of Congestion Control Congestion: p p informally: “too many sources sending too much data too fast for network to handle” different from flow control! manifestations: n lost packets (buffer overflow at routers) n long delays (queueing in router buffers) a top-10 problem!
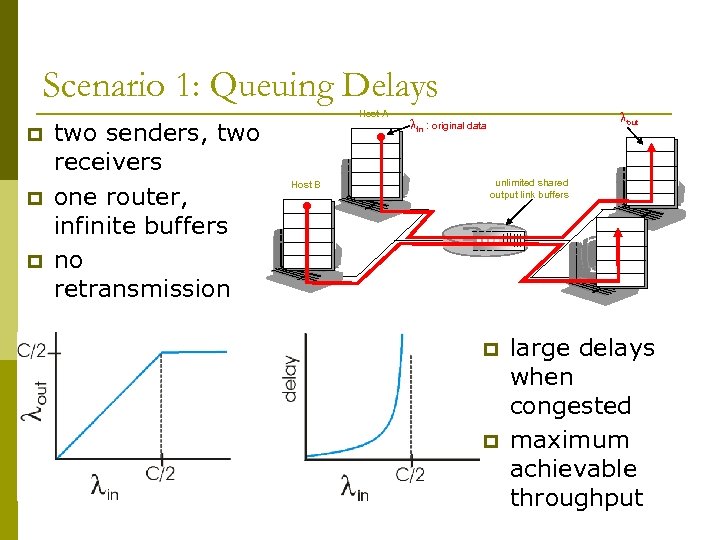 Scenario 1: Queuing Delays p p p two senders, two receivers one router, infinite buffers no retransmission Host A Host B lout lin : original data unlimited shared output link buffers p p large delays when congested maximum achievable throughput
Scenario 1: Queuing Delays p p p two senders, two receivers one router, infinite buffers no retransmission Host A Host B lout lin : original data unlimited shared output link buffers p p large delays when congested maximum achievable throughput
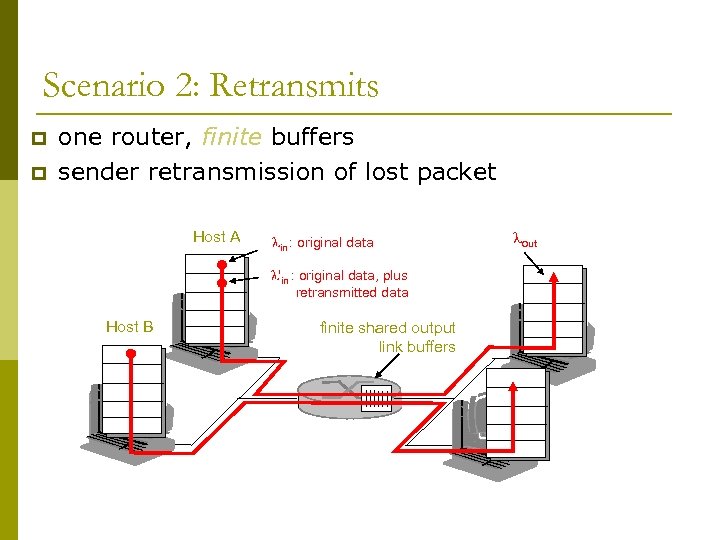 Scenario 2: Retransmits p p one router, finite buffers sender retransmission of lost packet Host A lin : original data l'in : original data, plus retransmitted data Host B finite shared output link buffers lout
Scenario 2: Retransmits p p one router, finite buffers sender retransmission of lost packet Host A lin : original data l'in : original data, plus retransmitted data Host B finite shared output link buffers lout
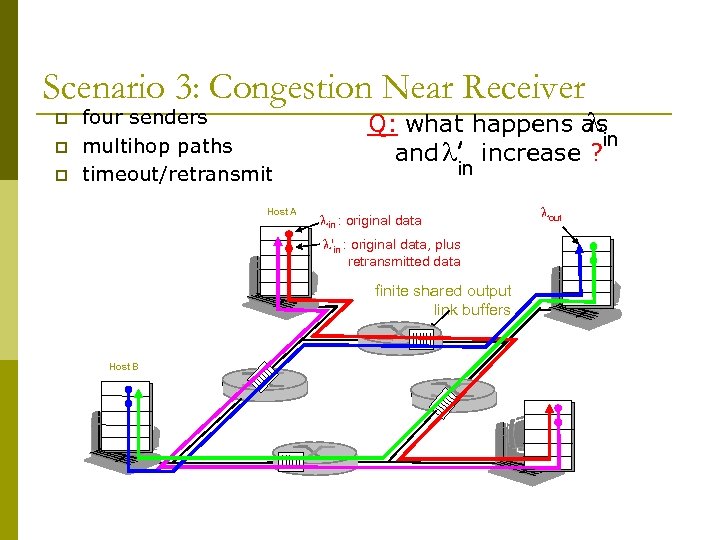 Scenario 3: Congestion Near Receiver p p p four senders multihop paths timeout/retransmit Host A l Q: what happens as in l and increase ? in lin : original data l'in : original data, plus retransmitted data finite shared output link buffers Host B lout
Scenario 3: Congestion Near Receiver p p p four senders multihop paths timeout/retransmit Host A l Q: what happens as in l and increase ? in lin : original data l'in : original data, plus retransmitted data finite shared output link buffers Host B lout
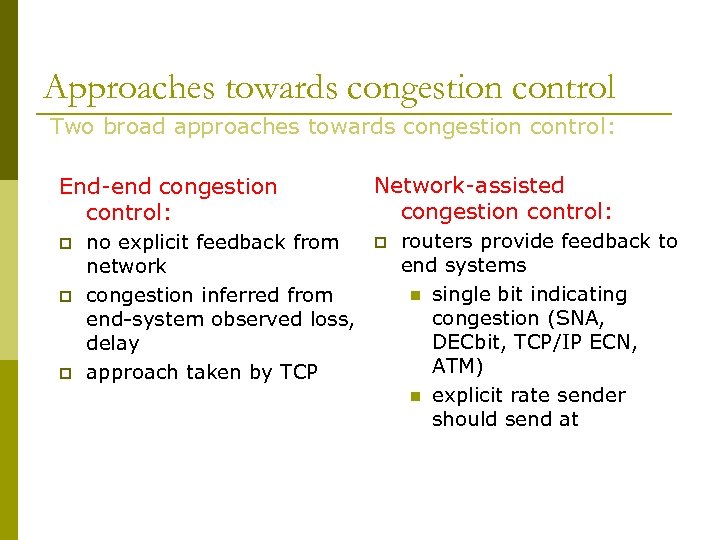 Approaches towards congestion control Two broad approaches towards congestion control: End-end congestion control: p p p no explicit feedback from network congestion inferred from end-system observed loss, delay approach taken by TCP Network-assisted congestion control: p routers provide feedback to end systems n single bit indicating congestion (SNA, DECbit, TCP/IP ECN, ATM) n explicit rate sender should send at
Approaches towards congestion control Two broad approaches towards congestion control: End-end congestion control: p p p no explicit feedback from network congestion inferred from end-system observed loss, delay approach taken by TCP Network-assisted congestion control: p routers provide feedback to end systems n single bit indicating congestion (SNA, DECbit, TCP/IP ECN, ATM) n explicit rate sender should send at
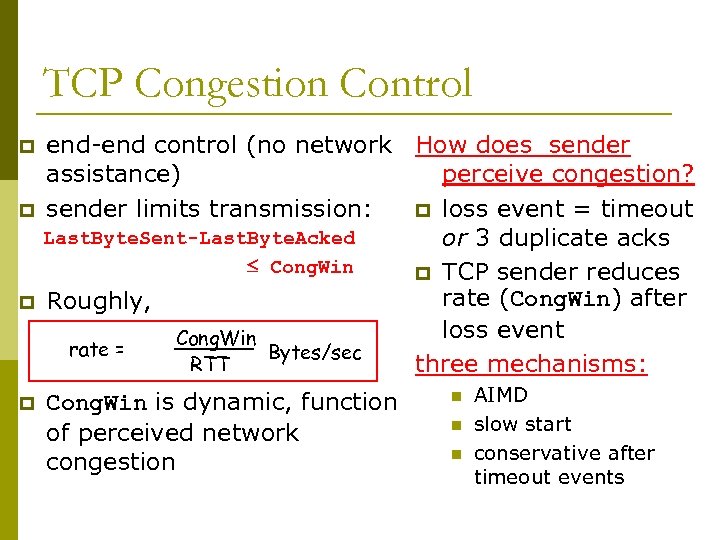 TCP Congestion Control p p end-end control (no network How does sender assistance) perceive congestion? sender limits transmission: p loss event = timeout Last. Byte. Sent-Last. Byte. Acked or 3 duplicate acks Cong. Win p TCP sender reduces rate (Cong. Win) after Roughly, loss event Cong. Win rate = Bytes/sec RTT three mechanisms: Cong. Win is dynamic, function of perceived network congestion n AIMD slow start conservative after timeout events
TCP Congestion Control p p end-end control (no network How does sender assistance) perceive congestion? sender limits transmission: p loss event = timeout Last. Byte. Sent-Last. Byte. Acked or 3 duplicate acks Cong. Win p TCP sender reduces rate (Cong. Win) after Roughly, loss event Cong. Win rate = Bytes/sec RTT three mechanisms: Cong. Win is dynamic, function of perceived network congestion n AIMD slow start conservative after timeout events
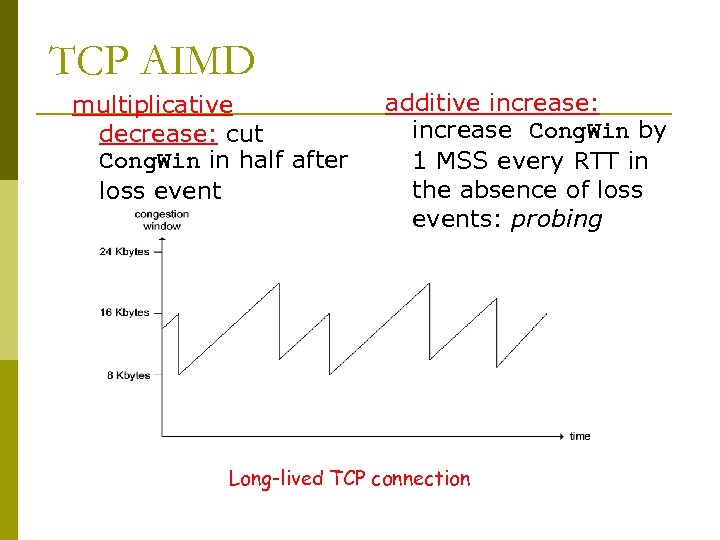 TCP AIMD multiplicative decrease: cut Cong. Win in half after loss event additive increase: increase Cong. Win by 1 MSS every RTT in the absence of loss events: probing Long-lived TCP connection
TCP AIMD multiplicative decrease: cut Cong. Win in half after loss event additive increase: increase Cong. Win by 1 MSS every RTT in the absence of loss events: probing Long-lived TCP connection
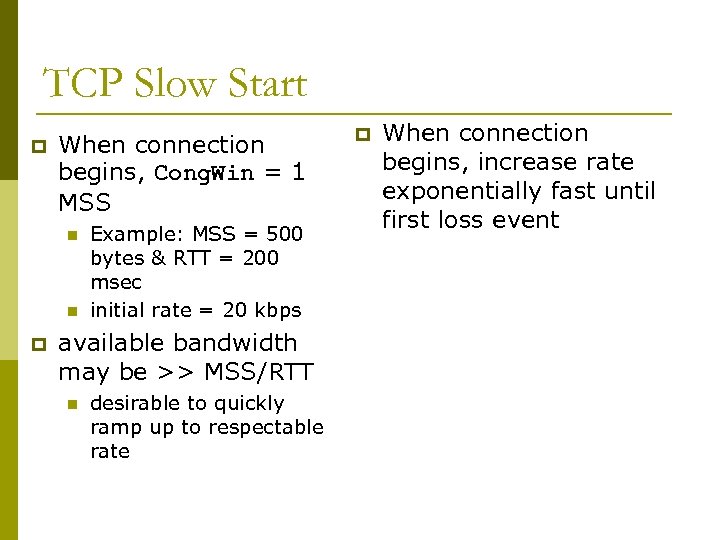 TCP Slow Start p When connection begins, Cong. Win = 1 MSS n n p Example: MSS = 500 bytes & RTT = 200 msec initial rate = 20 kbps available bandwidth may be >> MSS/RTT n desirable to quickly ramp up to respectable rate p When connection begins, increase rate exponentially fast until first loss event
TCP Slow Start p When connection begins, Cong. Win = 1 MSS n n p Example: MSS = 500 bytes & RTT = 200 msec initial rate = 20 kbps available bandwidth may be >> MSS/RTT n desirable to quickly ramp up to respectable rate p When connection begins, increase rate exponentially fast until first loss event
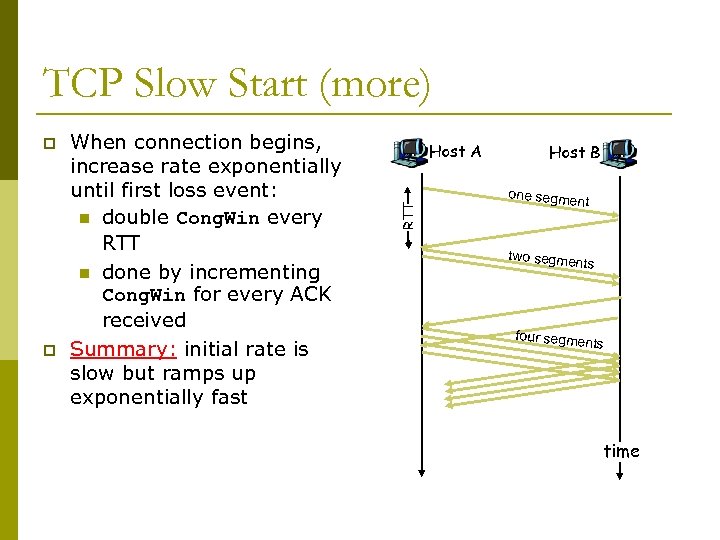 TCP Slow Start (more) p When connection begins, increase rate exponentially until first loss event: n double Cong. Win every RTT n done by incrementing Cong. Win for every ACK received Summary: initial rate is slow but ramps up exponentially fast Host A RTT p Host B one segme nt two segme nts four segme nts time
TCP Slow Start (more) p When connection begins, increase rate exponentially until first loss event: n double Cong. Win every RTT n done by incrementing Cong. Win for every ACK received Summary: initial rate is slow but ramps up exponentially fast Host A RTT p Host B one segme nt two segme nts four segme nts time
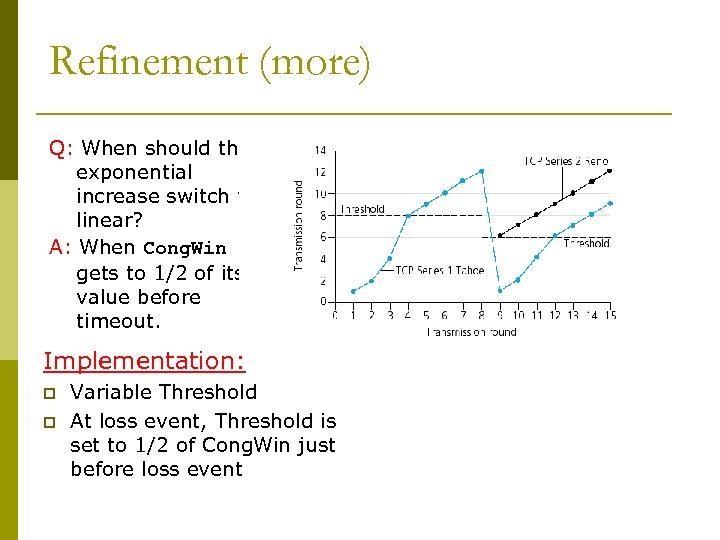 Refinement (more) Q: When should the exponential increase switch to linear? A: When Cong. Win gets to 1/2 of its value before timeout. Implementation: p Variable Threshold p At loss event, Threshold is set to 1/2 of Cong. Win just before loss event
Refinement (more) Q: When should the exponential increase switch to linear? A: When Cong. Win gets to 1/2 of its value before timeout. Implementation: p Variable Threshold p At loss event, Threshold is set to 1/2 of Cong. Win just before loss event
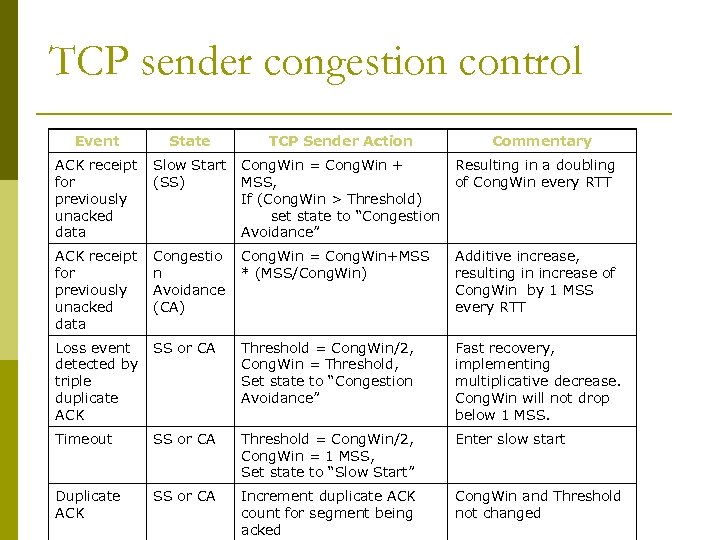 TCP sender congestion control Event State TCP Sender Action Commentary ACK receipt Slow Start Cong. Win = Cong. Win + Resulting in a doubling for (SS) MSS, of Cong. Win every RTT previously If (Cong. Win > Threshold) unacked set state to “Congestion data Avoidance” ACK receipt for previously unacked data Congestio Cong. Win = Cong. Win+MSS n * (MSS/Cong. Win) Avoidance (CA) Additive increase, resulting in increase of Cong. Win by 1 MSS every RTT Loss event SS or CA detected by triple duplicate ACK Threshold = Cong. Win/2, Cong. Win = Threshold, Set state to “Congestion Avoidance” Fast recovery, implementing multiplicative decrease. Cong. Win will not drop below 1 MSS. Timeout SS or CA Threshold = Cong. Win/2, Enter slow start Cong. Win = 1 MSS, Set state to “Slow Start” Duplicate ACK SS or CA Increment duplicate ACK count for segment being acked Cong. Win and Threshold not changed
TCP sender congestion control Event State TCP Sender Action Commentary ACK receipt Slow Start Cong. Win = Cong. Win + Resulting in a doubling for (SS) MSS, of Cong. Win every RTT previously If (Cong. Win > Threshold) unacked set state to “Congestion data Avoidance” ACK receipt for previously unacked data Congestio Cong. Win = Cong. Win+MSS n * (MSS/Cong. Win) Avoidance (CA) Additive increase, resulting in increase of Cong. Win by 1 MSS every RTT Loss event SS or CA detected by triple duplicate ACK Threshold = Cong. Win/2, Cong. Win = Threshold, Set state to “Congestion Avoidance” Fast recovery, implementing multiplicative decrease. Cong. Win will not drop below 1 MSS. Timeout SS or CA Threshold = Cong. Win/2, Enter slow start Cong. Win = 1 MSS, Set state to “Slow Start” Duplicate ACK SS or CA Increment duplicate ACK count for segment being acked Cong. Win and Threshold not changed
 Congestion Avoidance Mechanisms p p Helps to avoid congestion Additional functionality into the router to assist in anticipation of congestion to control congestion once it happens to repeatedly increase load in an effort to find the point at which congestion occurs, and then back off
Congestion Avoidance Mechanisms p p Helps to avoid congestion Additional functionality into the router to assist in anticipation of congestion to control congestion once it happens to repeatedly increase load in an effort to find the point at which congestion occurs, and then back off
 Mechanisms p router-centric: DECbit and RED Gateways p host-centric: TCP Vegas
Mechanisms p router-centric: DECbit and RED Gateways p host-centric: TCP Vegas
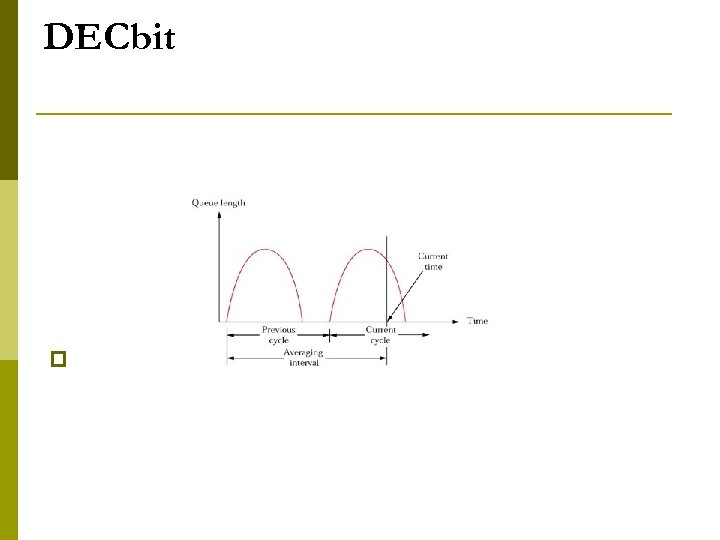 DECbit p
DECbit p
 DECbit p p Add binary congestion bit to each packet header Router n monitors average queue length over last busy+idle cycle n n p set congestion bit if average queue length greater than 1 when packet arrives attempts to balance throughput against delay
DECbit p p Add binary congestion bit to each packet header Router n monitors average queue length over last busy+idle cycle n n p set congestion bit if average queue length greater than 1 when packet arrives attempts to balance throughput against delay
 DECbit p End Hosts destination echos bit back to source p source records how many packets resulted in set bit p if less than 50% of last window's worth had bit set, then increase Congestion. Window by 1 packet p if 50% or more of last window's worth had bit set, then decrease Congestion. Window by 0. 875 times p
DECbit p End Hosts destination echos bit back to source p source records how many packets resulted in set bit p if less than 50% of last window's worth had bit set, then increase Congestion. Window by 1 packet p if 50% or more of last window's worth had bit set, then decrease Congestion. Window by 0. 875 times p
 Random Early Detection (RED) p Notification is implicit n just drop the packet (TCP will timeout) n p could make explicit by marking the packet Early random drop n rather than wait for queue to become full, drop each arriving packet with some drop probability whenever the queue length exceeds some drop level
Random Early Detection (RED) p Notification is implicit n just drop the packet (TCP will timeout) n p could make explicit by marking the packet Early random drop n rather than wait for queue to become full, drop each arriving packet with some drop probability whenever the queue length exceeds some drop level
 Random Early Detection (RED) p RED: fills in the details n compute average queue length n Avg. Len=(1 - Weight)*Avg. Len+Weight*Sample. Len p 0 < Weight < 1 (usually 0. 002) p Sample. Len is queue length each time a packet arrives
Random Early Detection (RED) p RED: fills in the details n compute average queue length n Avg. Len=(1 - Weight)*Avg. Len+Weight*Sample. Len p 0 < Weight < 1 (usually 0. 002) p Sample. Len is queue length each time a packet arrives
 Random Early Detection (RED
Random Early Detection (RED
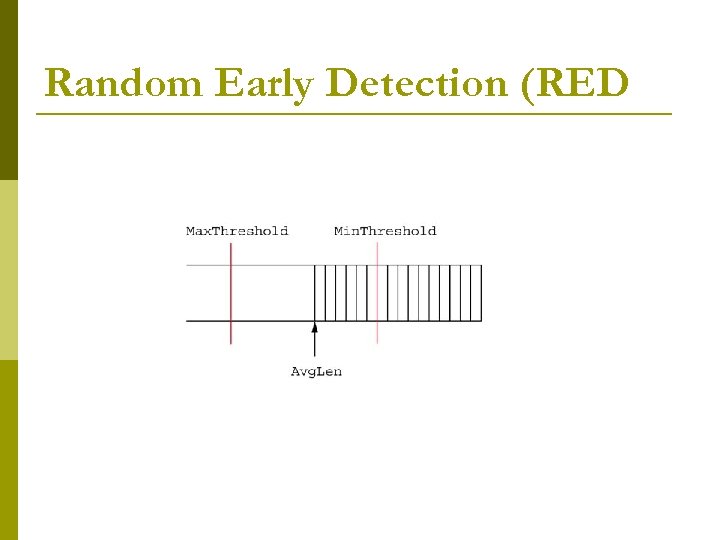
 Random Early Detection (RED) p two queue length thresholds if Avg. Len ? Min. Threshold then p enqueue the packet p if Min. Threshold < Avg. Len < Max. Threshold p calculate probability P p if Max. Threshold ? Avg. Len p drop arriving packet p
Random Early Detection (RED) p two queue length thresholds if Avg. Len ? Min. Threshold then p enqueue the packet p if Min. Threshold < Avg. Len < Max. Threshold p calculate probability P p if Max. Threshold ? Avg. Len p drop arriving packet p
 UNIT V Domain Name Service p is a hierarchical naming system for computers, services in the Internet p is an IETF-standard name service. p enables client computers on your network to register and resolve DNS domain names. p names are used to find access resources offered by other computers on your network or other networks, such as the Internet.
UNIT V Domain Name Service p is a hierarchical naming system for computers, services in the Internet p is an IETF-standard name service. p enables client computers on your network to register and resolve DNS domain names. p names are used to find access resources offered by other computers on your network or other networks, such as the Internet.
 three main components of DNS: p Domain name space and associated resource records (RRs) p DNS Name Servers p DNS Resolvers
three main components of DNS: p Domain name space and associated resource records (RRs) p DNS Name Servers p DNS Resolvers
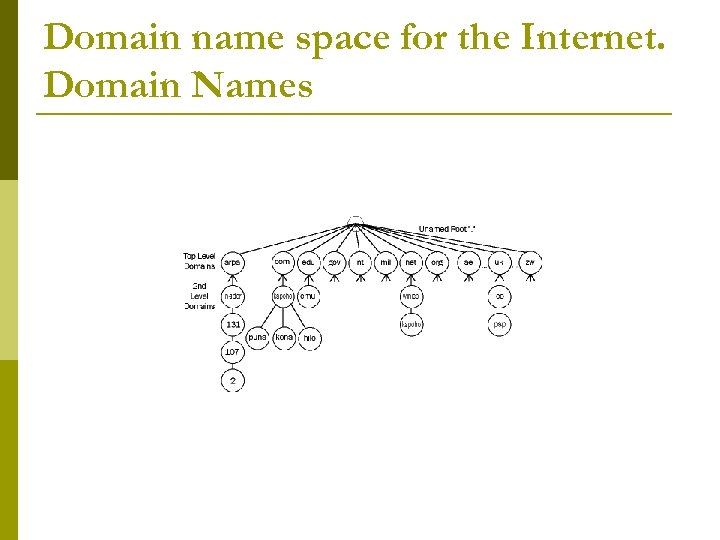 Domain name space for the Internet. Domain Names
Domain name space for the Internet. Domain Names
 Email p Electronic mail abbreviated as e-mail or email p is method of creating, transmitting, or storing primarily text-based human communications with digital communications systems p based on a store-and-forward model in which e-mail computer server systems, accept, forward, or store messages on behalf of users
Email p Electronic mail abbreviated as e-mail or email p is method of creating, transmitting, or storing primarily text-based human communications with digital communications systems p based on a store-and-forward model in which e-mail computer server systems, accept, forward, or store messages on behalf of users
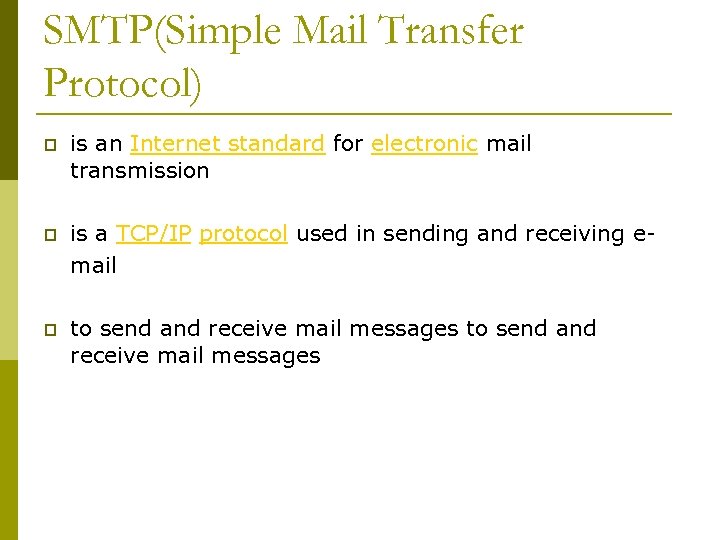 SMTP(Simple Mail Transfer Protocol) p is an Internet standard for electronic mail transmission p is a TCP/IP protocol used in sending and receiving email p to send and receive mail messages
SMTP(Simple Mail Transfer Protocol) p is an Internet standard for electronic mail transmission p is a TCP/IP protocol used in sending and receiving email p to send and receive mail messages
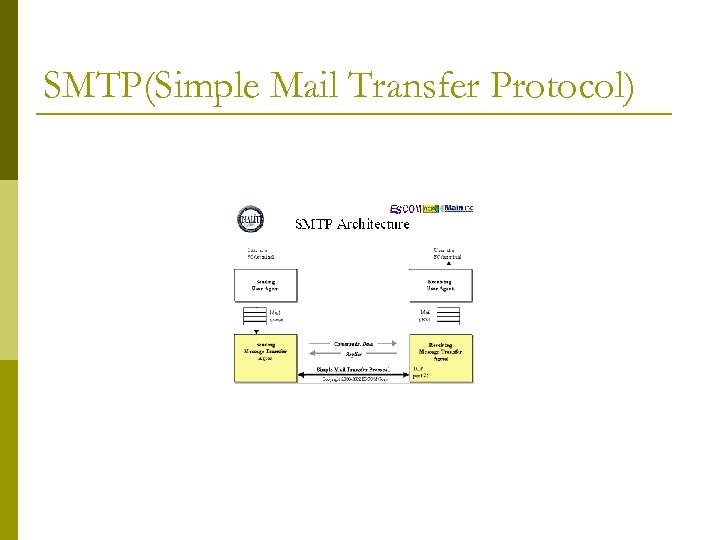 SMTP(Simple Mail Transfer Protocol)
SMTP(Simple Mail Transfer Protocol)
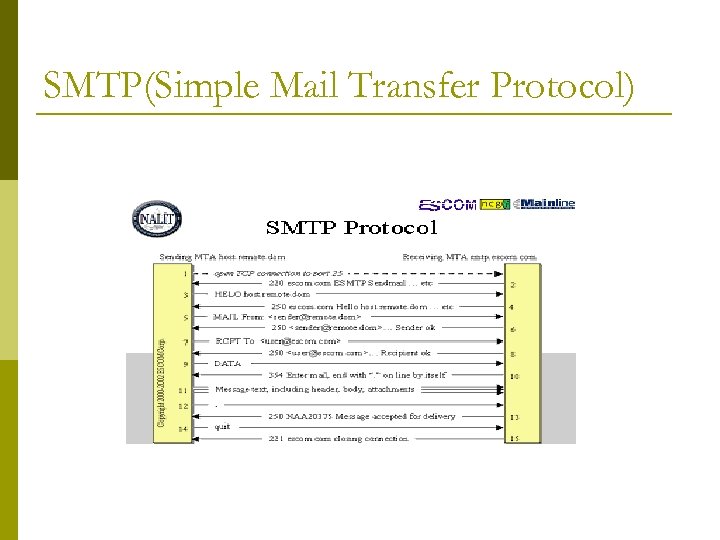 SMTP(Simple Mail Transfer Protocol)
SMTP(Simple Mail Transfer Protocol)
 MIME p p Multipurpose Internet Mail Extensions SMTP is ASCII based allows multi part messages containing content of various types combined into one message Types n n n GIF graphics files Post. Script files MIME messages can contain p text, images, audio, video, and other applicationspecific data.
MIME p p Multipurpose Internet Mail Extensions SMTP is ASCII based allows multi part messages containing content of various types combined into one message Types n n n GIF graphics files Post. Script files MIME messages can contain p text, images, audio, video, and other applicationspecific data.
 format of messages p p textual message bodies in character sets other than USASCII, an extensible set of different formats for non-textual message bodies, multi-part message bodies, and textual header information in character sets other than USASCII.
format of messages p p textual message bodies in character sets other than USASCII, an extensible set of different formats for non-textual message bodies, multi-part message bodies, and textual header information in character sets other than USASCII.
 HTTP p p is an application-level protocol for distributed, collaborative, hypermedia information systems. It is a generic, stateless, protocol which can be used for many tasks such as name servers and distributed object management systems, through extension of its request methods, error codes and headers [47]. typing and negotiation of data representation allows systems to be built independently of the data being transferred.
HTTP p p is an application-level protocol for distributed, collaborative, hypermedia information systems. It is a generic, stateless, protocol which can be used for many tasks such as name servers and distributed object management systems, through extension of its request methods, error codes and headers [47]. typing and negotiation of data representation allows systems to be built independently of the data being transferred.
 SNMP p p to monitor network-attached devices for conditions that warrant administrative attention SNMP basic components n n n Managed devices Agents Network-management stations (NMSs)
SNMP p p to monitor network-attached devices for conditions that warrant administrative attention SNMP basic components n n n Managed devices Agents Network-management stations (NMSs)
 Email Features p p Email is Fast Email is Inexpensive Email is Easy to Filter Transmission is Secure and Reliable n 1. Fast - Messages can be sent anywhere around the world in an instant 2. cheap - Transmission usually costs nothing, or at the most, very little 3. simple - Easy to use, after initial set-up 4. efficient - Sending to a group can be done in one step 5. versatile - Pictures, powerpoints or other files can be sent too
Email Features p p Email is Fast Email is Inexpensive Email is Easy to Filter Transmission is Secure and Reliable n 1. Fast - Messages can be sent anywhere around the world in an instant 2. cheap - Transmission usually costs nothing, or at the most, very little 3. simple - Easy to use, after initial set-up 4. efficient - Sending to a group can be done in one step 5. versatile - Pictures, powerpoints or other files can be sent too
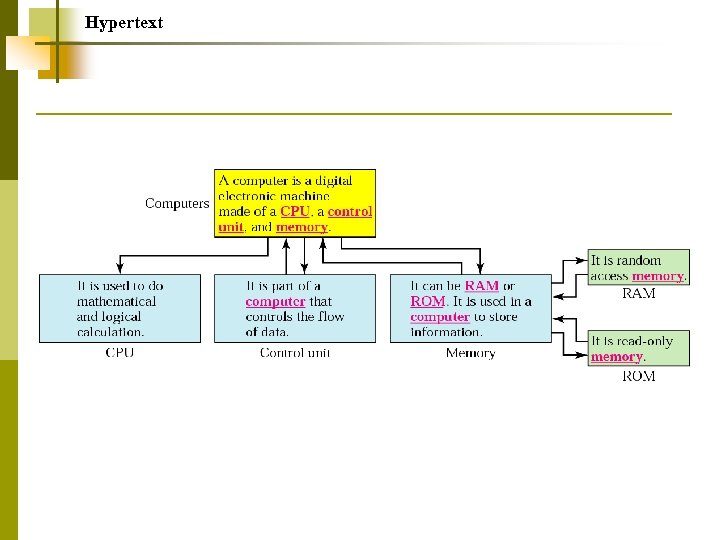
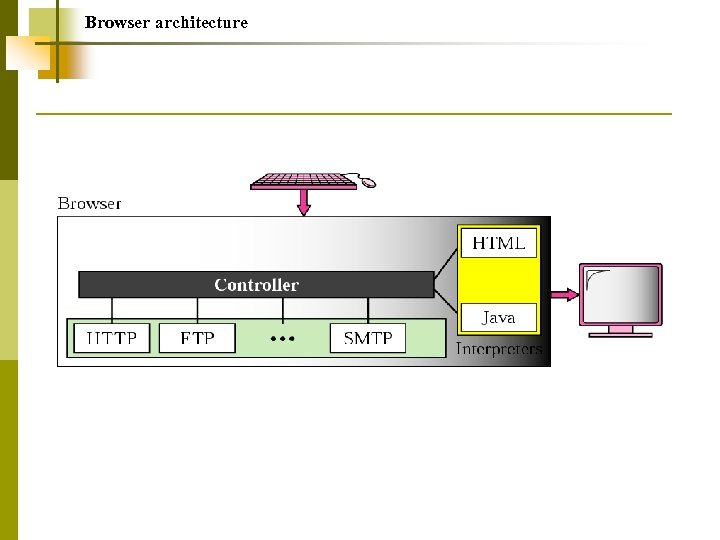
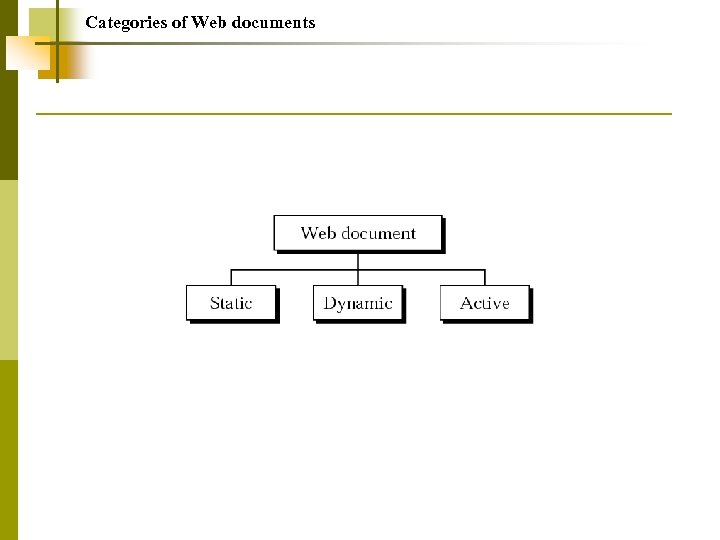
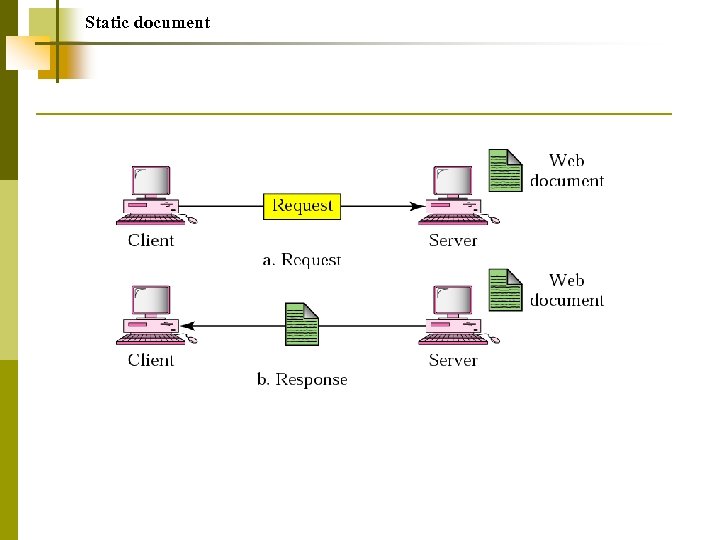
 World Wide Web Hypertext and Hypermedia Browser Architecture Static Document/HTML Dynamic Document/CGI Active Document/Java
World Wide Web Hypertext and Hypermedia Browser Architecture Static Document/HTML Dynamic Document/CGI Active Document/Java
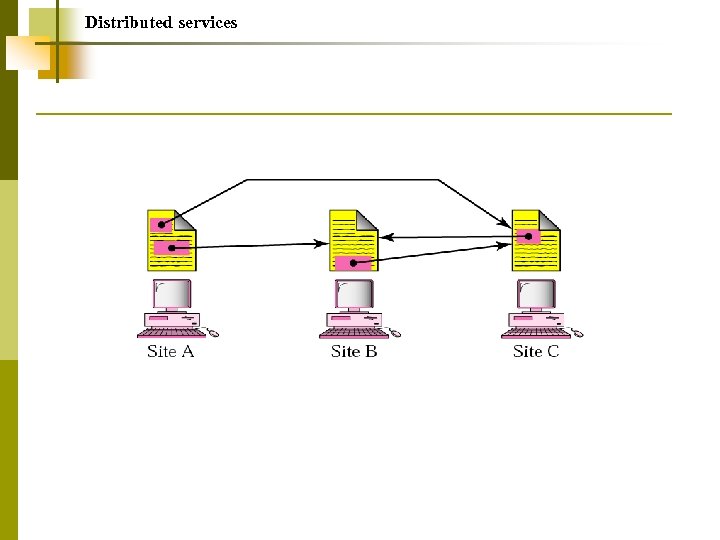 Distributed services
Distributed services
 Hypertext
Hypertext
 Browser architecture
Browser architecture
 Categories of Web documents
Categories of Web documents
 Static document
Static document
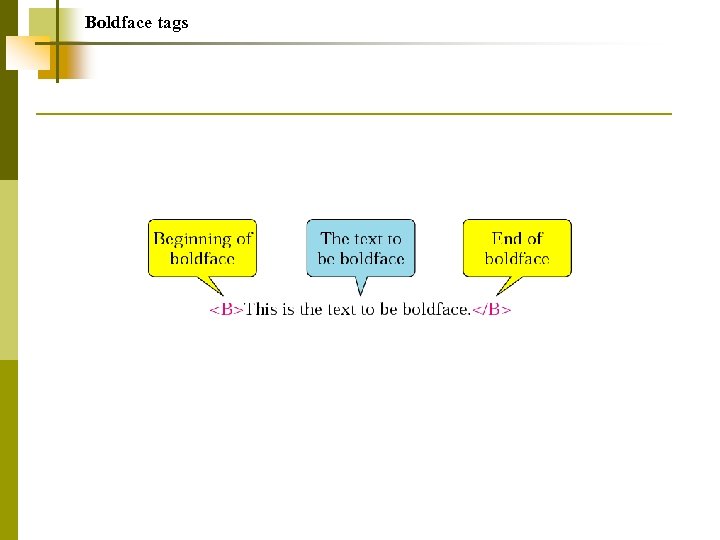 Boldface tags
Boldface tags
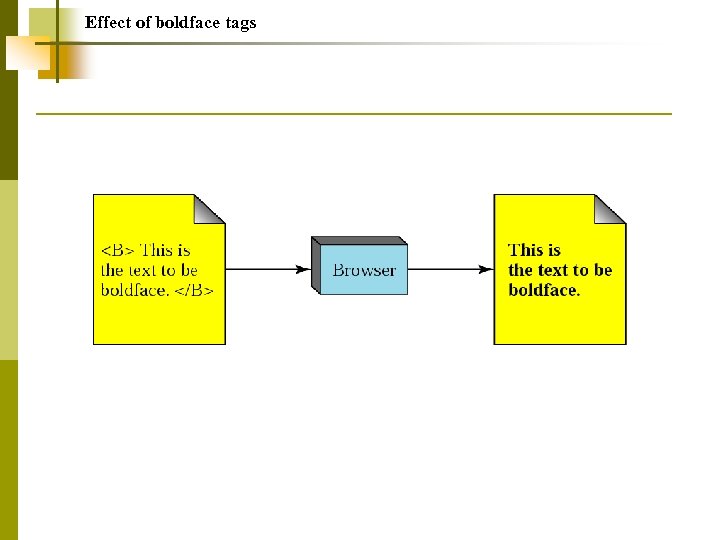 Effect of boldface tags
Effect of boldface tags
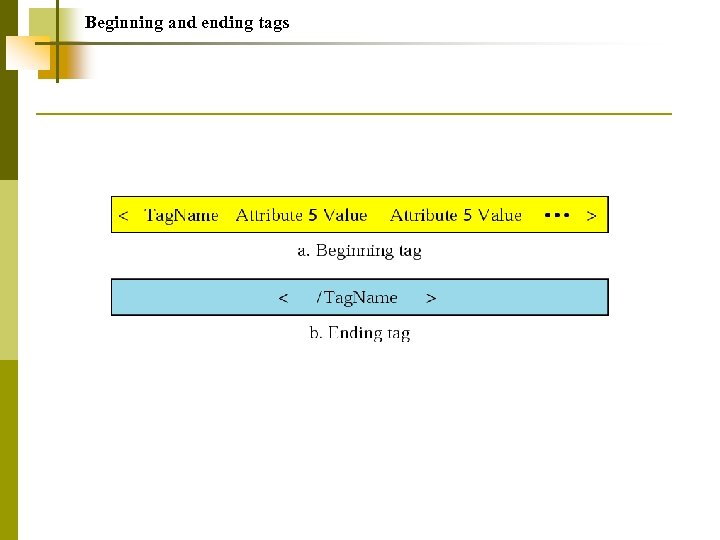 Beginning and ending tags
Beginning and ending tags
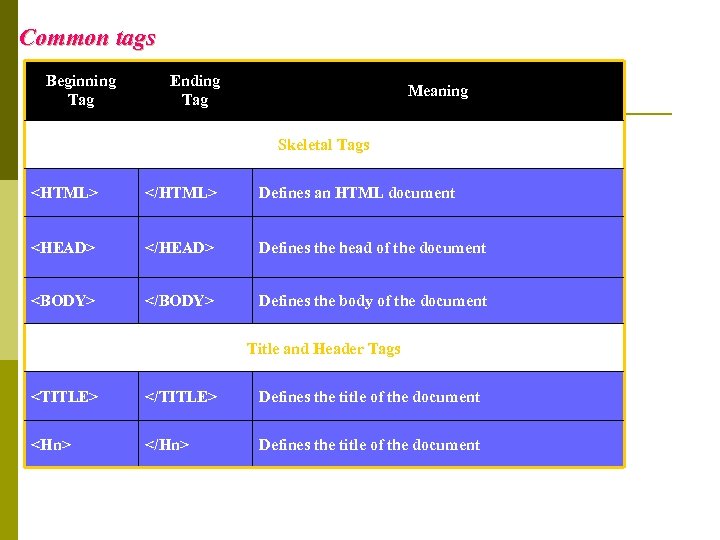 Common tags Beginning Tag Ending Tag Meaning Skeletal Tags Defines an HTML document
Common tags Beginning Tag Ending Tag Meaning Skeletal Tags Defines an HTML document
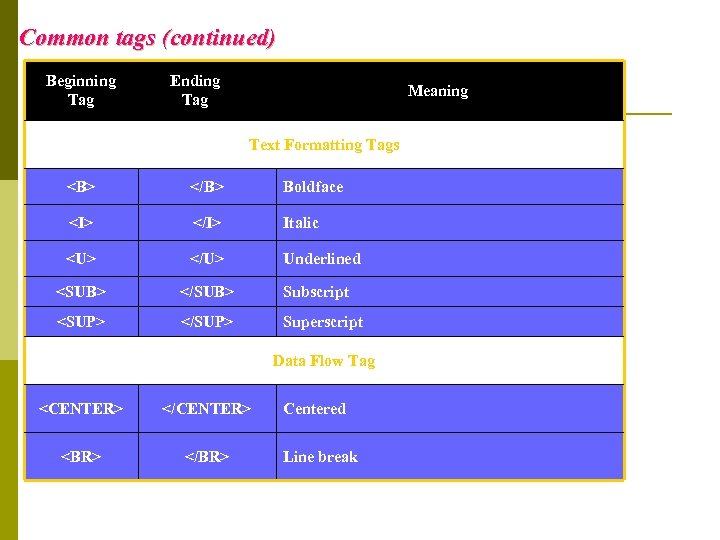 Common tags (continued) Beginning Tag Ending Tag Meaning Text Formatting Tags Boldface Italic Underlined Subscript Superscript Data Flow Tag
Common tags (continued) Beginning Tag Ending Tag Meaning Text Formatting Tags Boldface Italic Underlined Subscript Superscript Data Flow Tag
Centered Line break
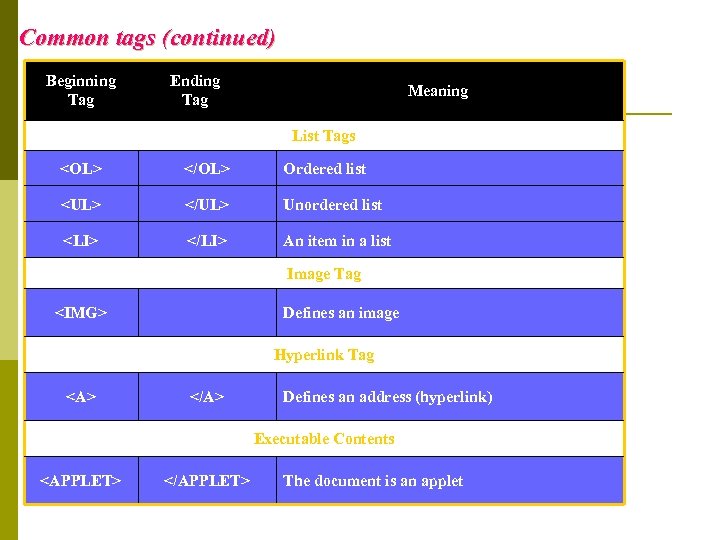 Common tags (continued) Beginning Tag Ending Tag Meaning List Tags
Common tags (continued) Beginning Tag Ending Tag Meaning List Tags
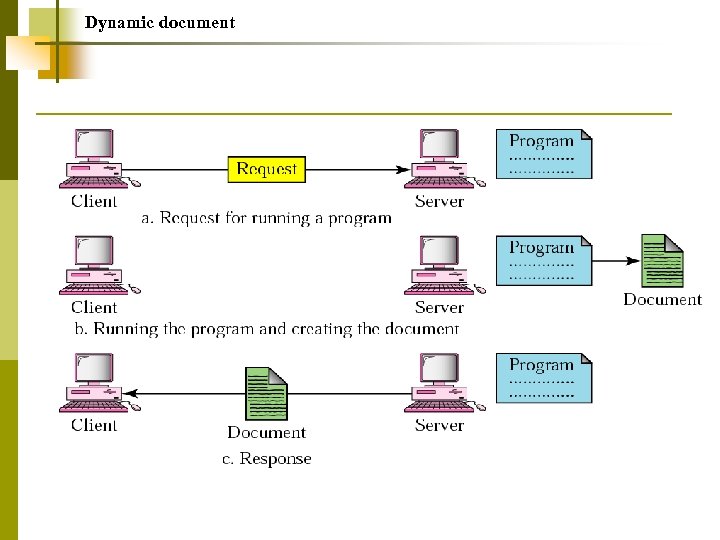 Dynamic document
Dynamic document
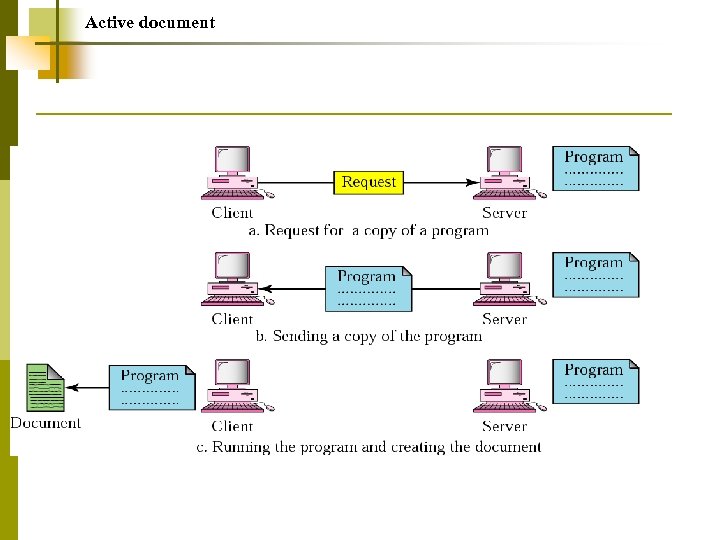 Active document
Active document
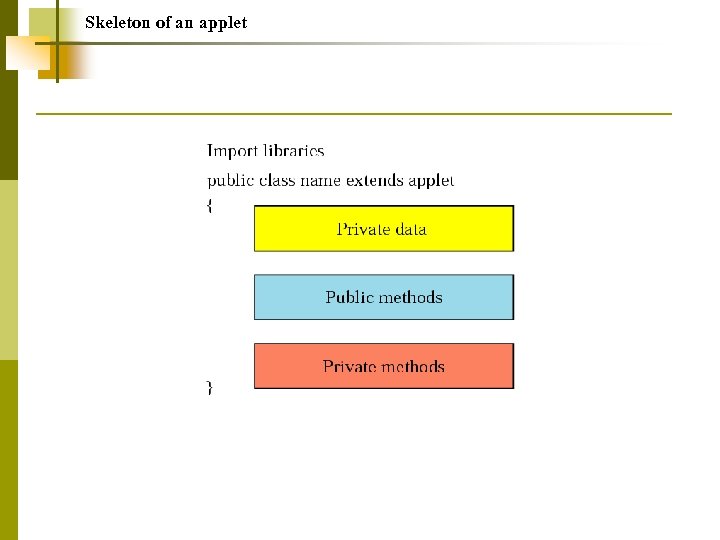 Skeleton of an applet
Skeleton of an applet
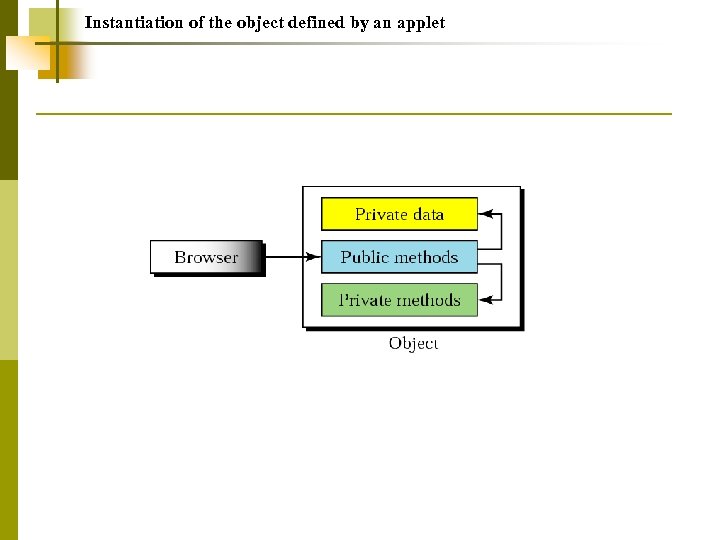 Instantiation of the object defined by an applet
Instantiation of the object defined by an applet
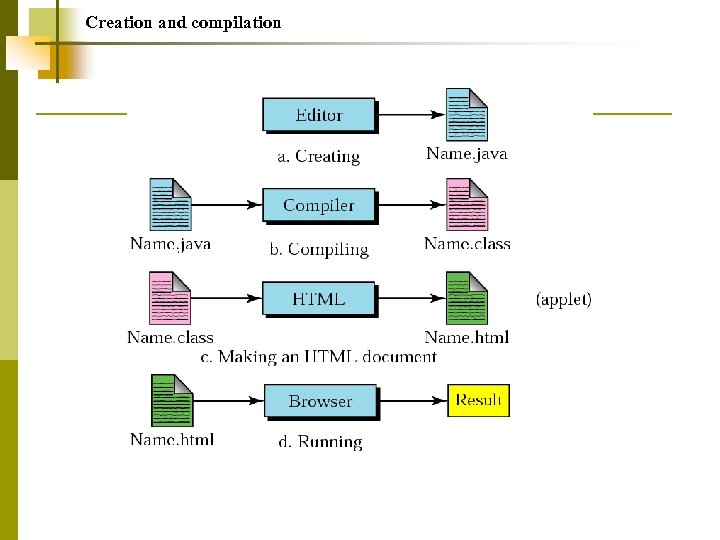 Creation and compilation
Creation and compilation
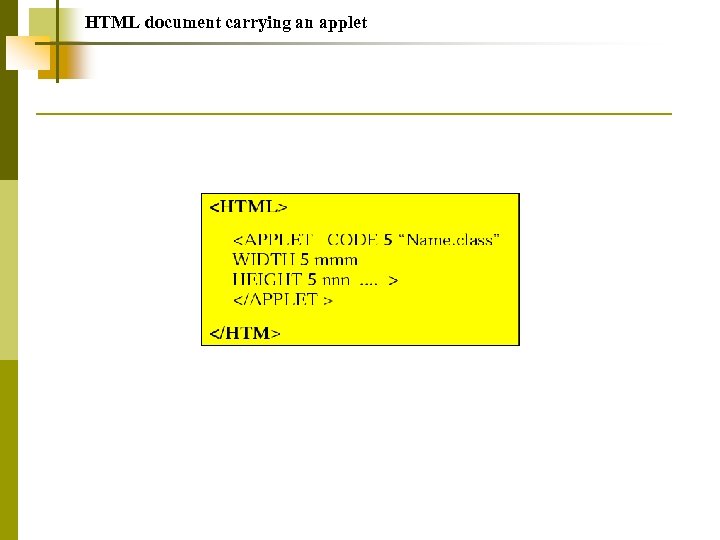 HTML document carrying an applet
HTML document carrying an applet
 File Transfer Connections Communication File Transfer User Interface Anonymous
File Transfer Connections Communication File Transfer User Interface Anonymous
 Note: FTP uses the services of TCP. It needs two TCP connections. The well-known port 21 is used for the control connection, and the well-known port 20 is used for the data connection.
Note: FTP uses the services of TCP. It needs two TCP connections. The well-known port 21 is used for the control connection, and the well-known port 20 is used for the data connection.
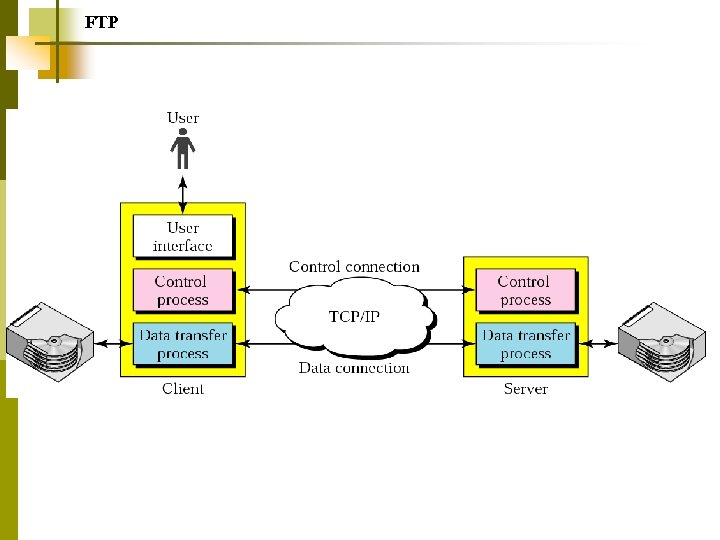 FTP
FTP
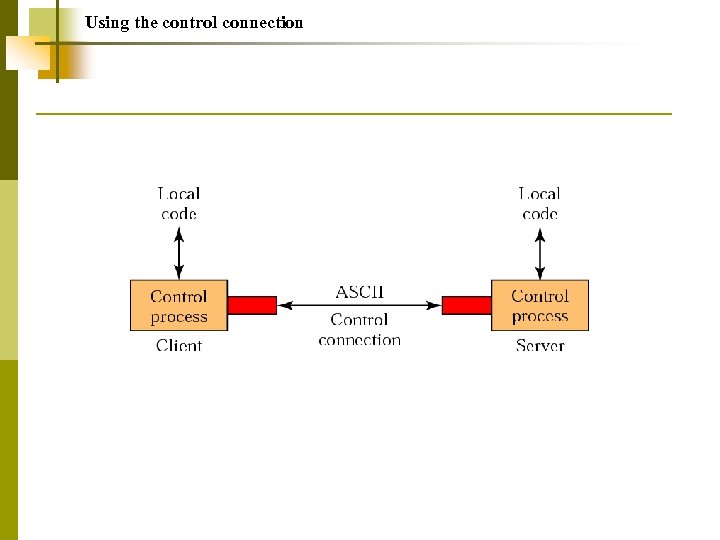 Using the control connection
Using the control connection
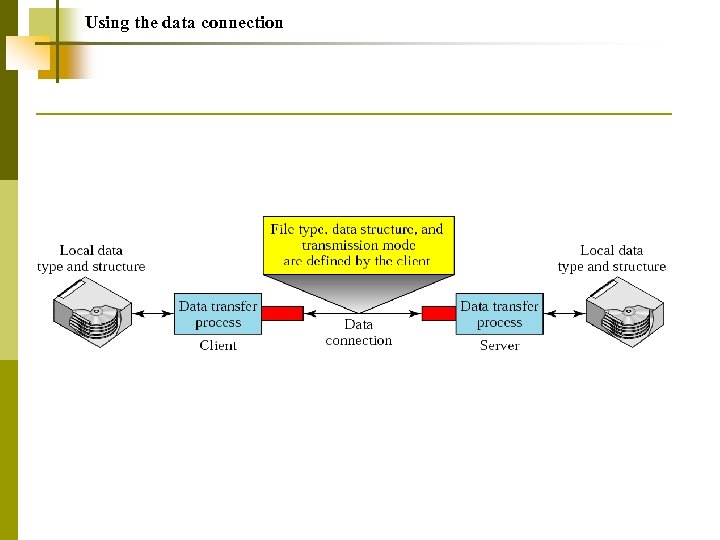 Using the data connection
Using the data connection
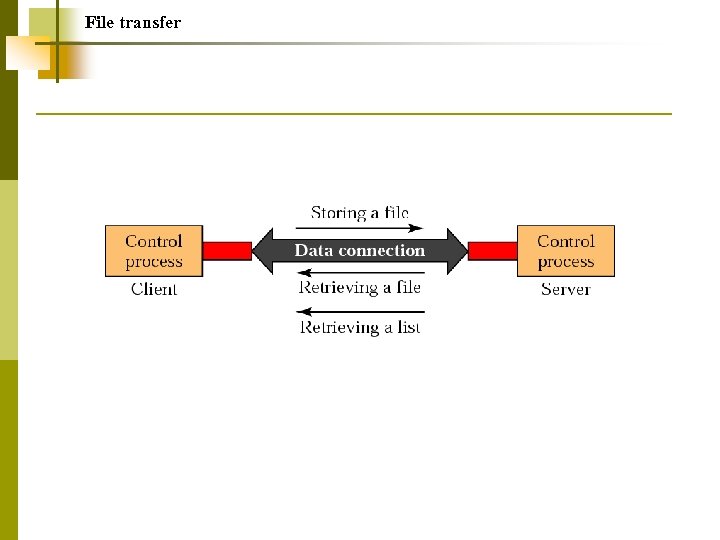 File transfer
File transfer


