8b1831ff9d668caf76200f593b611f22.ppt
- Количество слайдов: 57
 CS 117: Computer Communications Networks: The Physical Layer Winter 2014 Internet Protocol Primer (See Tanenbaum or Kurose/Ross) 1
CS 117: Computer Communications Networks: The Physical Layer Winter 2014 Internet Protocol Primer (See Tanenbaum or Kurose/Ross) 1
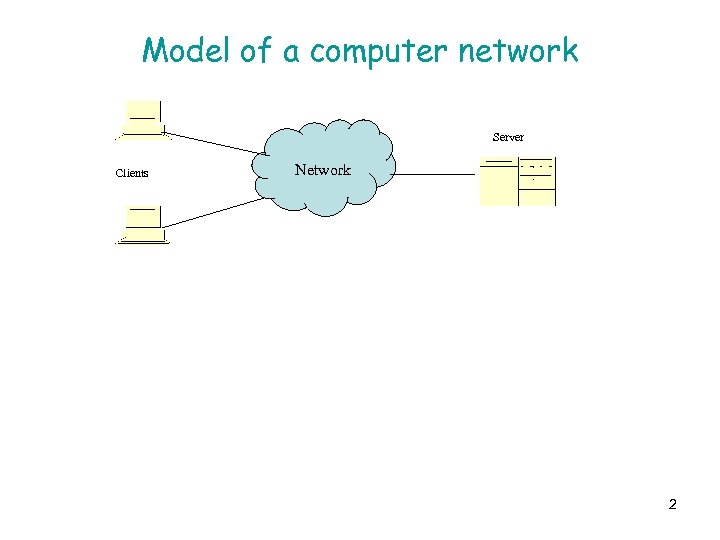 Model of a computer network Server Clients Network 2
Model of a computer network Server Clients Network 2
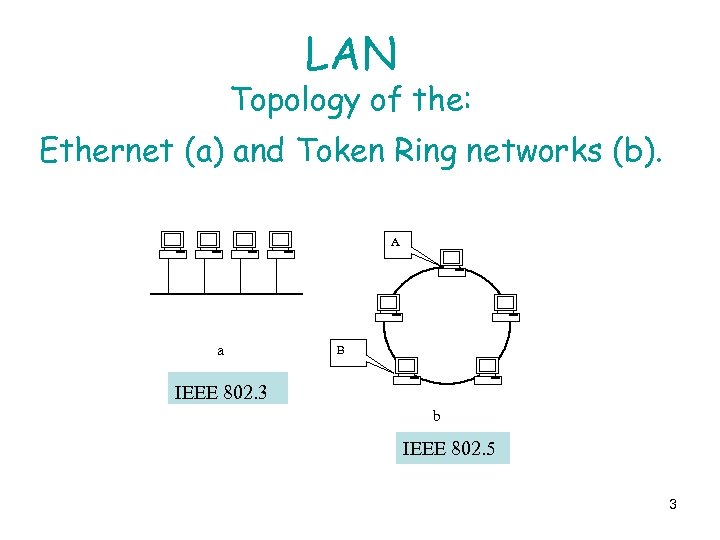 LAN Topology of the: Ethernet (a) and Token Ring networks (b). A a B IEEE 802. 3 b IEEE 802. 5 3
LAN Topology of the: Ethernet (a) and Token Ring networks (b). A a B IEEE 802. 3 b IEEE 802. 5 3
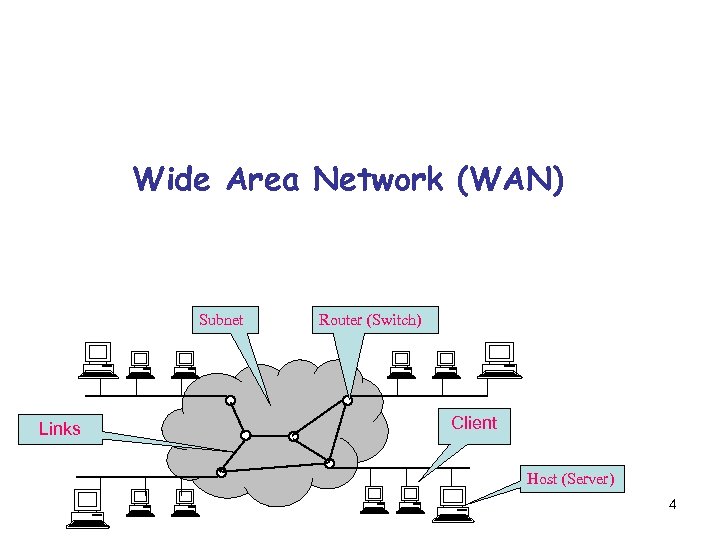 Wide Area Network (WAN) Subnet Links Router (Switch) Client Host (Server) 4
Wide Area Network (WAN) Subnet Links Router (Switch) Client Host (Server) 4
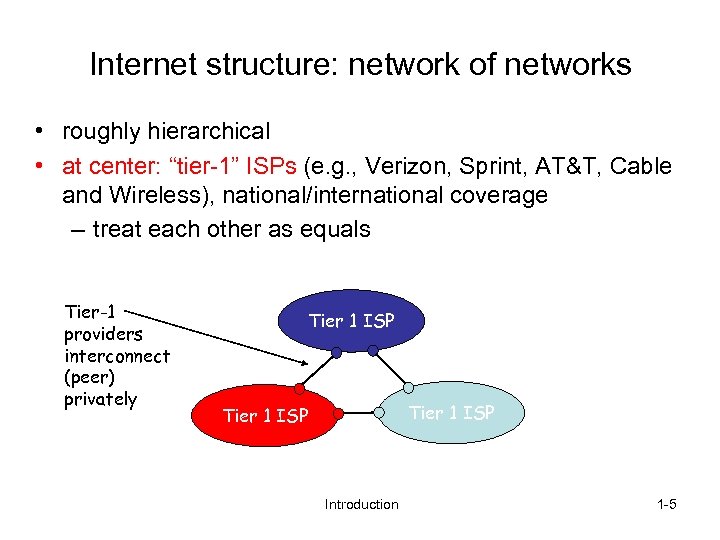 Internet structure: network of networks • roughly hierarchical • at center: “tier-1” ISPs (e. g. , Verizon, Sprint, AT&T, Cable and Wireless), national/international coverage – treat each other as equals Tier-1 providers interconnect (peer) privately Tier 1 ISP Introduction 1 -5
Internet structure: network of networks • roughly hierarchical • at center: “tier-1” ISPs (e. g. , Verizon, Sprint, AT&T, Cable and Wireless), national/international coverage – treat each other as equals Tier-1 providers interconnect (peer) privately Tier 1 ISP Introduction 1 -5
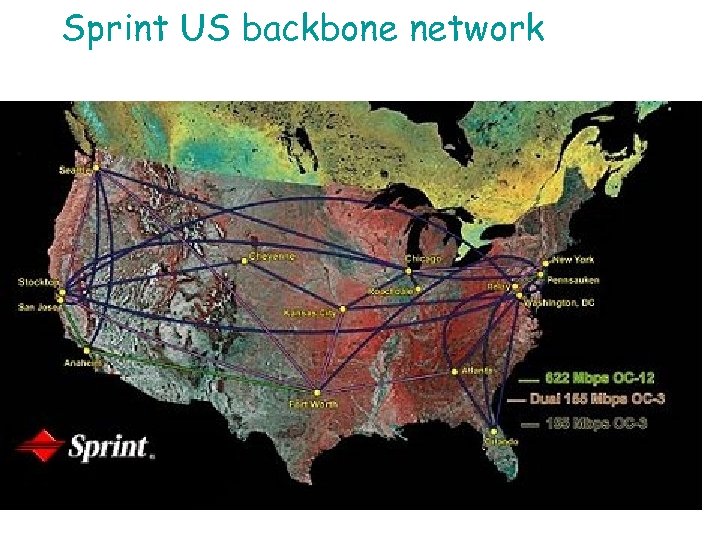 Sprint US backbone network 6
Sprint US backbone network 6
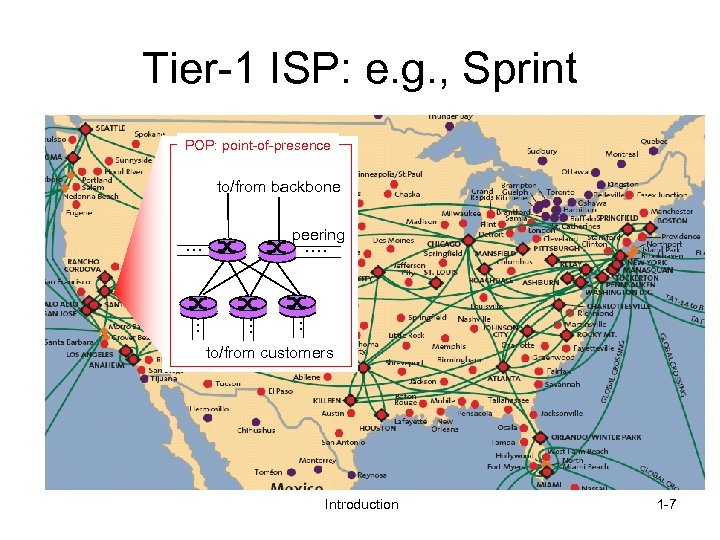 Tier-1 ISP: e. g. , Sprint POP: point-of-presence to/from backbone peering … … … to/from customers Introduction 1 -7
Tier-1 ISP: e. g. , Sprint POP: point-of-presence to/from backbone peering … … … to/from customers Introduction 1 -7
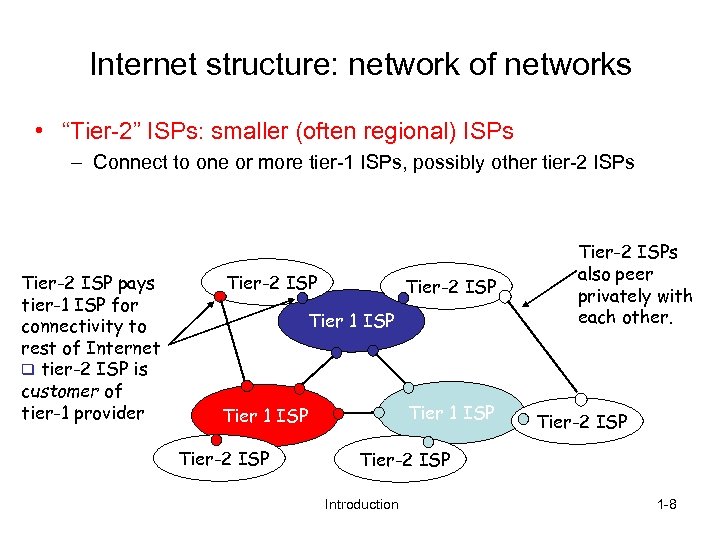 Internet structure: network of networks • “Tier-2” ISPs: smaller (often regional) ISPs – Connect to one or more tier-1 ISPs, possibly other tier-2 ISPs Tier-2 ISP pays tier-1 ISP for connectivity to rest of Internet q tier-2 ISP is customer of tier-1 provider Tier-2 ISP Tier 1 ISP Tier-2 ISPs also peer privately with each other. Tier-2 ISP Introduction 1 -8
Internet structure: network of networks • “Tier-2” ISPs: smaller (often regional) ISPs – Connect to one or more tier-1 ISPs, possibly other tier-2 ISPs Tier-2 ISP pays tier-1 ISP for connectivity to rest of Internet q tier-2 ISP is customer of tier-1 provider Tier-2 ISP Tier 1 ISP Tier-2 ISPs also peer privately with each other. Tier-2 ISP Introduction 1 -8
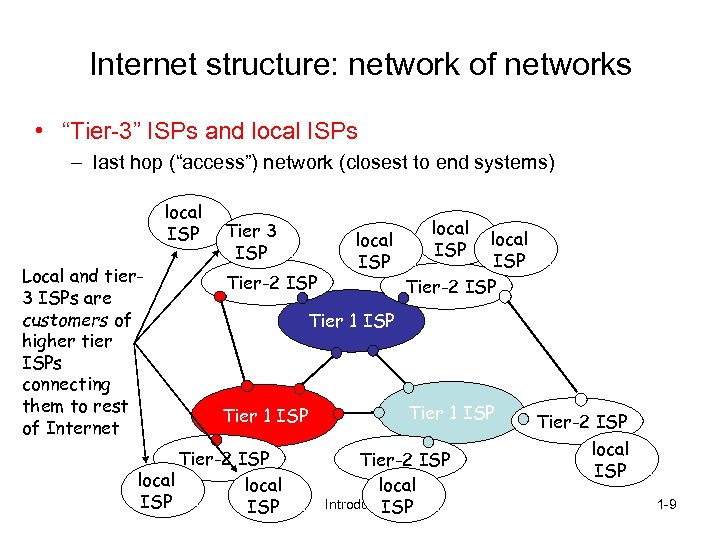 Internet structure: network of networks • “Tier-3” ISPs and local ISPs – last hop (“access”) network (closest to end systems) local ISP Local and tier 3 ISPs are customers of higher tier ISPs connecting them to rest of Internet Tier 3 ISP Tier-2 ISP local ISP Tier-2 ISP Tier 1 ISP Tier-2 ISP local Introduction ISP Tier-2 ISP local ISP 1 -9
Internet structure: network of networks • “Tier-3” ISPs and local ISPs – last hop (“access”) network (closest to end systems) local ISP Local and tier 3 ISPs are customers of higher tier ISPs connecting them to rest of Internet Tier 3 ISP Tier-2 ISP local ISP Tier-2 ISP Tier 1 ISP Tier-2 ISP local Introduction ISP Tier-2 ISP local ISP 1 -9
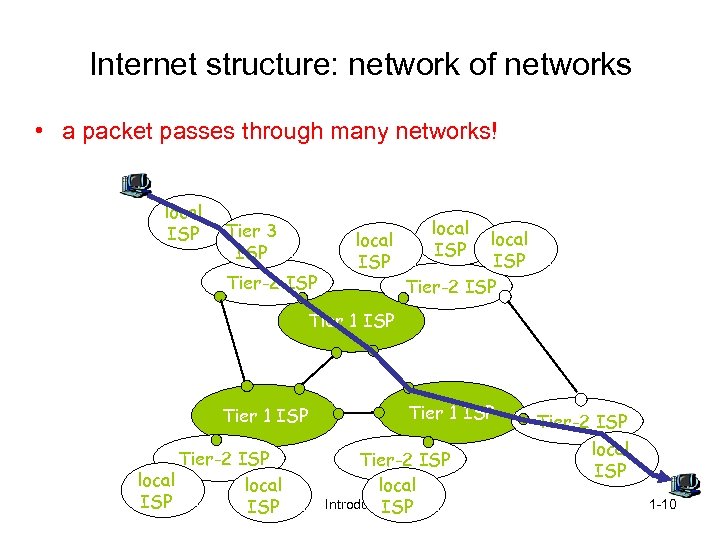 Internet structure: network of networks • a packet passes through many networks! local ISP Tier 3 ISP Tier-2 ISP local ISP Tier-2 ISP Tier 1 ISP Tier-2 ISP local Introduction ISP Tier-2 ISP local ISP 1 -10
Internet structure: network of networks • a packet passes through many networks! local ISP Tier 3 ISP Tier-2 ISP local ISP Tier-2 ISP Tier 1 ISP Tier-2 ISP local Introduction ISP Tier-2 ISP local ISP 1 -10
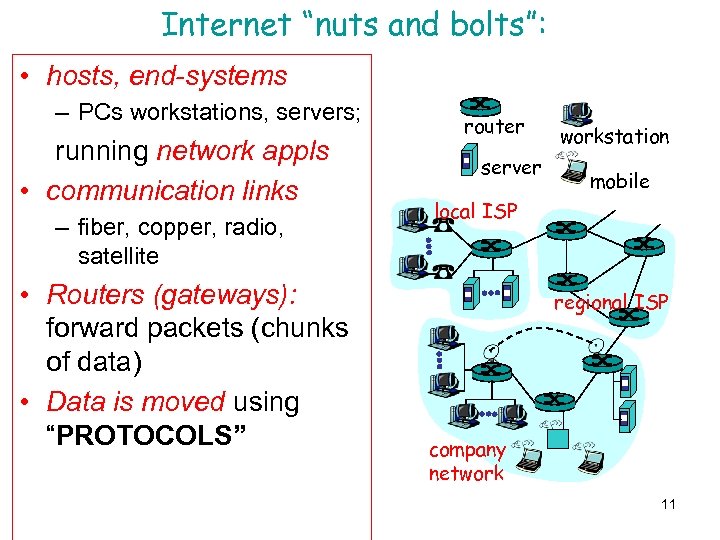 Internet “nuts and bolts”: • hosts, end-systems – PCs workstations, servers; running network appls • communication links – fiber, copper, radio, satellite • Routers (gateways): forward packets (chunks of data) • Data is moved using “PROTOCOLS” router server workstation mobile local ISP regional ISP company network 11
Internet “nuts and bolts”: • hosts, end-systems – PCs workstations, servers; running network appls • communication links – fiber, copper, radio, satellite • Routers (gateways): forward packets (chunks of data) • Data is moved using “PROTOCOLS” router server workstation mobile local ISP regional ISP company network 11
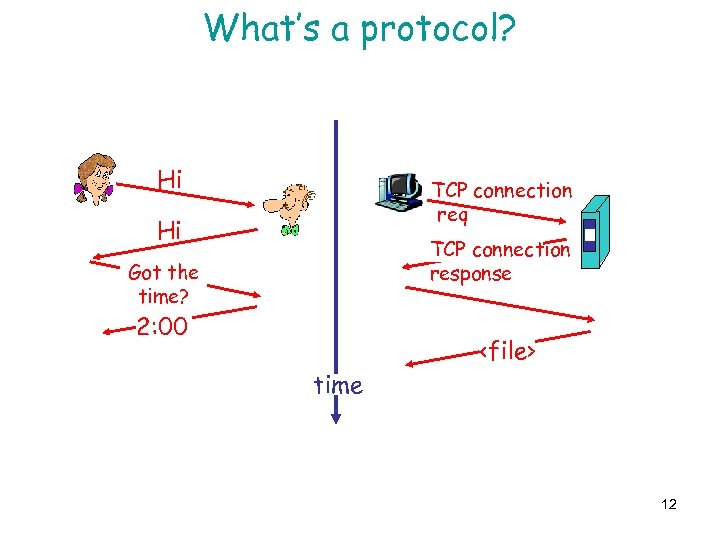 What’s a protocol? Hi TCP connection req Hi TCP connection response Got the time? 2: 00
What’s a protocol? Hi TCP connection req Hi TCP connection response Got the time? 2: 00
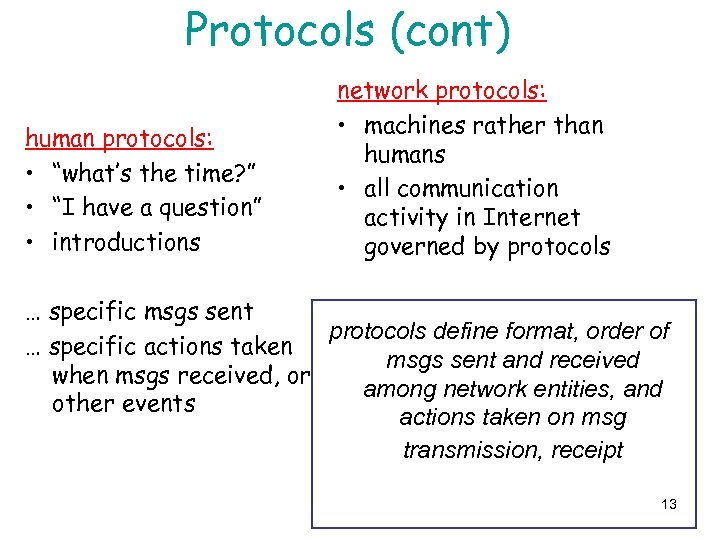 Protocols (cont) human protocols: • “what’s the time? ” • “I have a question” • introductions network protocols: • machines rather than humans • all communication activity in Internet governed by protocols … specific msgs sent protocols define format, order of … specific actions taken msgs sent and received when msgs received, or among network entities, and other events actions taken on msg transmission, receipt 13
Protocols (cont) human protocols: • “what’s the time? ” • “I have a question” • introductions network protocols: • machines rather than humans • all communication activity in Internet governed by protocols … specific msgs sent protocols define format, order of … specific actions taken msgs sent and received when msgs received, or among network entities, and other events actions taken on msg transmission, receipt 13
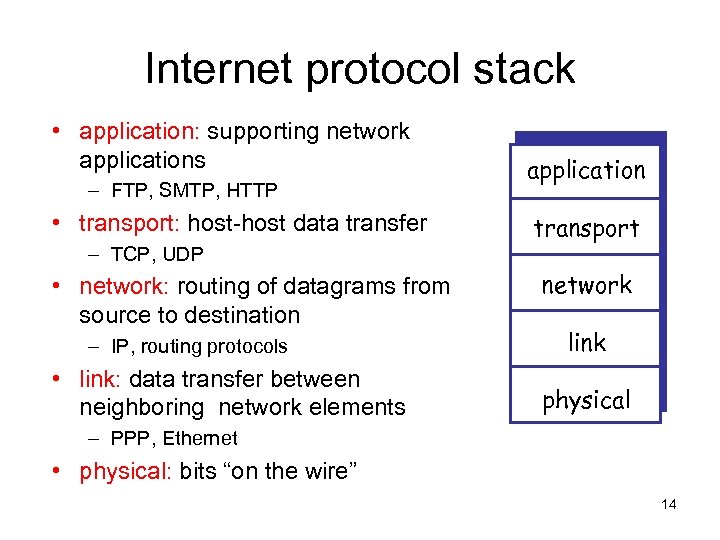 Internet protocol stack • application: supporting network applications – FTP, SMTP, HTTP • transport: host-host data transfer – TCP, UDP • network: routing of datagrams from source to destination – IP, routing protocols • link: data transfer between neighboring network elements application transport network link physical – PPP, Ethernet • physical: bits “on the wire” 14
Internet protocol stack • application: supporting network applications – FTP, SMTP, HTTP • transport: host-host data transfer – TCP, UDP • network: routing of datagrams from source to destination – IP, routing protocols • link: data transfer between neighboring network elements application transport network link physical – PPP, Ethernet • physical: bits “on the wire” 14
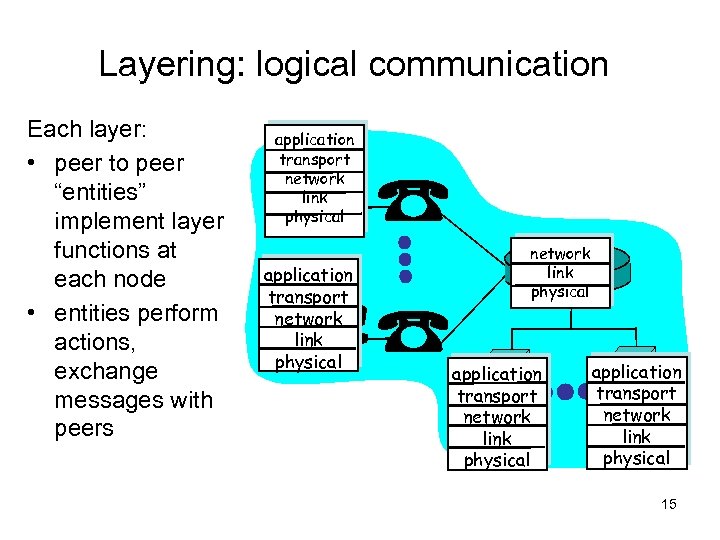 Layering: logical communication Each layer: • peer to peer “entities” implement layer functions at each node • entities perform actions, exchange messages with peers application transport network link physical application transport network link physical 15
Layering: logical communication Each layer: • peer to peer “entities” implement layer functions at each node • entities perform actions, exchange messages with peers application transport network link physical application transport network link physical 15
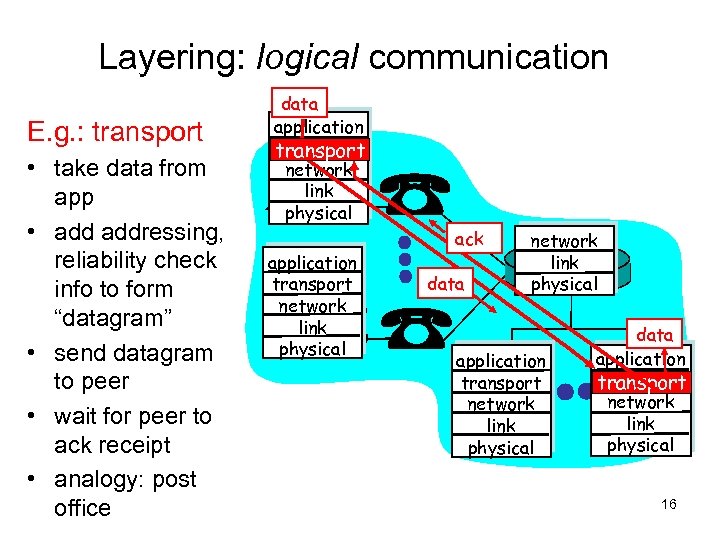 Layering: logical communication E. g. : transport • take data from app • addressing, reliability check info to form “datagram” • send datagram to peer • wait for peer to ack receipt • analogy: post office data application transport network link physical ack data network link physical application transport network link physical data application transport network link physical 16
Layering: logical communication E. g. : transport • take data from app • addressing, reliability check info to form “datagram” • send datagram to peer • wait for peer to ack receipt • analogy: post office data application transport network link physical ack data network link physical application transport network link physical data application transport network link physical 16
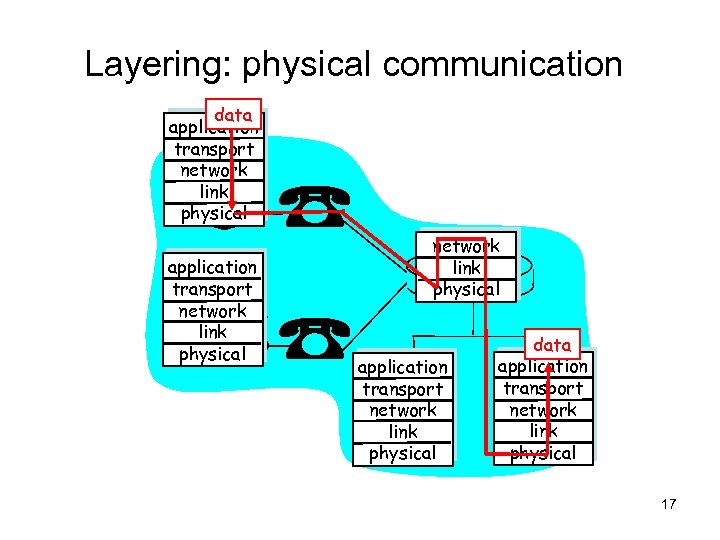 Layering: physical communication data application transport network link physical application transport network link physical data application transport network link physical 17
Layering: physical communication data application transport network link physical application transport network link physical data application transport network link physical 17
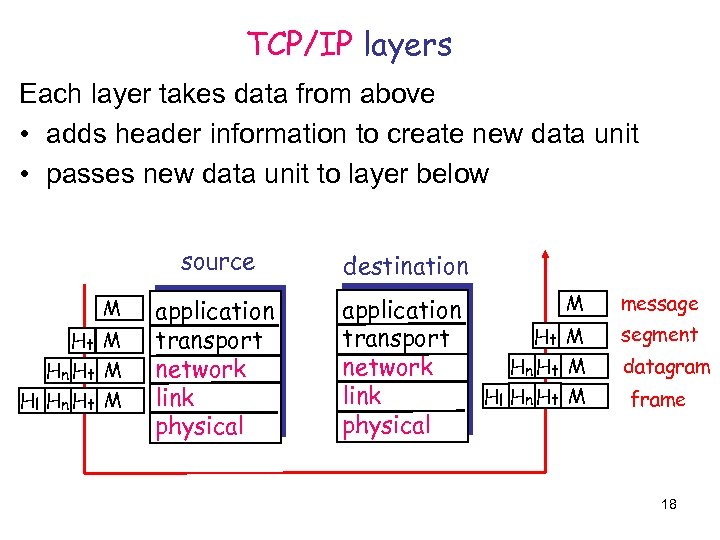 TCP/IP layers Each layer takes data from above • adds header information to create new data unit • passes new data unit to layer below source M Ht M Hn Ht M Hl Hn Ht M application transport network link physical destination application Ht transport Hn Ht network Hl Hn Ht link physical M message M segment M datagram M frame 18
TCP/IP layers Each layer takes data from above • adds header information to create new data unit • passes new data unit to layer below source M Ht M Hn Ht M Hl Hn Ht M application transport network link physical destination application Ht transport Hn Ht network Hl Hn Ht link physical M message M segment M datagram M frame 18
 Why layering? Dealing with complex systems: • modularization eases maintenance, updating of system – change of implementation of layer’s service transparent to rest of system – e. g. , change in gate procedure doesn’t affect rest of system • layering considered harmful? Introduction 1 -19
Why layering? Dealing with complex systems: • modularization eases maintenance, updating of system – change of implementation of layer’s service transparent to rest of system – e. g. , change in gate procedure doesn’t affect rest of system • layering considered harmful? Introduction 1 -19
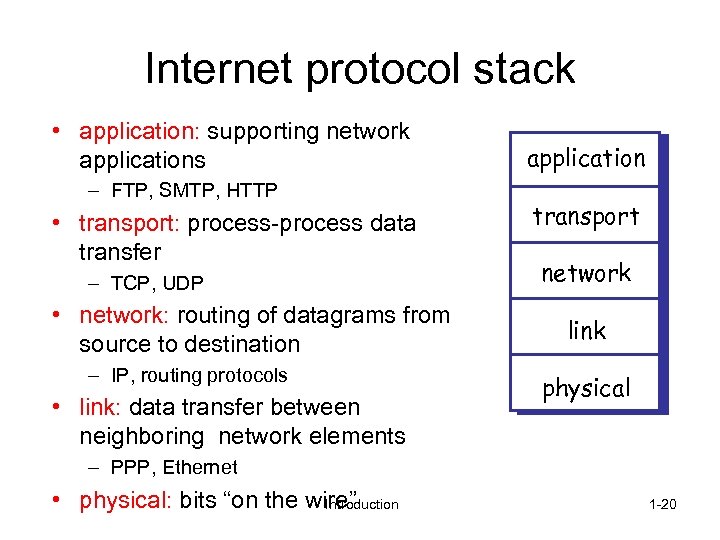 Internet protocol stack • application: supporting network applications – FTP, SMTP, HTTP • transport: process-process data transfer – TCP, UDP • network: routing of datagrams from source to destination – IP, routing protocols • link: data transfer between neighboring network elements application transport network link physical – PPP, Ethernet • physical: bits “on the wire” Introduction 1 -20
Internet protocol stack • application: supporting network applications – FTP, SMTP, HTTP • transport: process-process data transfer – TCP, UDP • network: routing of datagrams from source to destination – IP, routing protocols • link: data transfer between neighboring network elements application transport network link physical – PPP, Ethernet • physical: bits “on the wire” Introduction 1 -20
 Application architectures • Client-server • Peer-to-peer (P 2 P) • Hybrid of client-server and P 2 P 2: Application Layer 22
Application architectures • Client-server • Peer-to-peer (P 2 P) • Hybrid of client-server and P 2 P 2: Application Layer 22
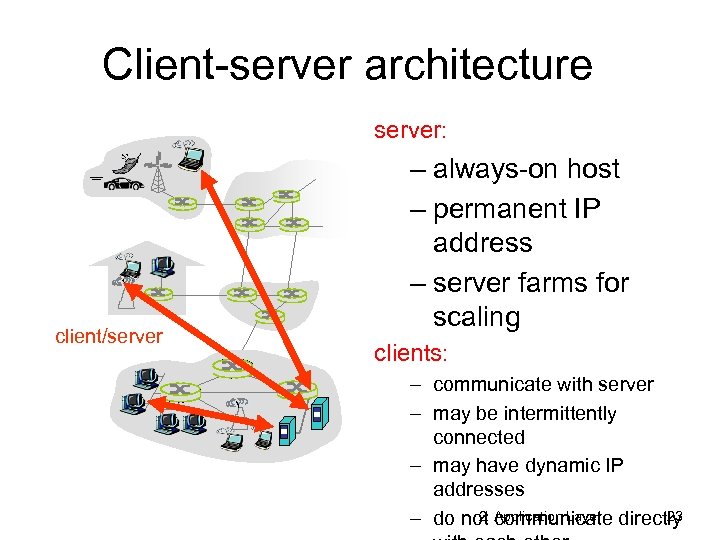 Client-server architecture server: client/server – always-on host – permanent IP address – server farms for scaling clients: – communicate with server – may be intermittently connected – may have dynamic IP addresses 2: Application Layer 23 – do not communicate directly
Client-server architecture server: client/server – always-on host – permanent IP address – server farms for scaling clients: – communicate with server – may be intermittently connected – may have dynamic IP addresses 2: Application Layer 23 – do not communicate directly
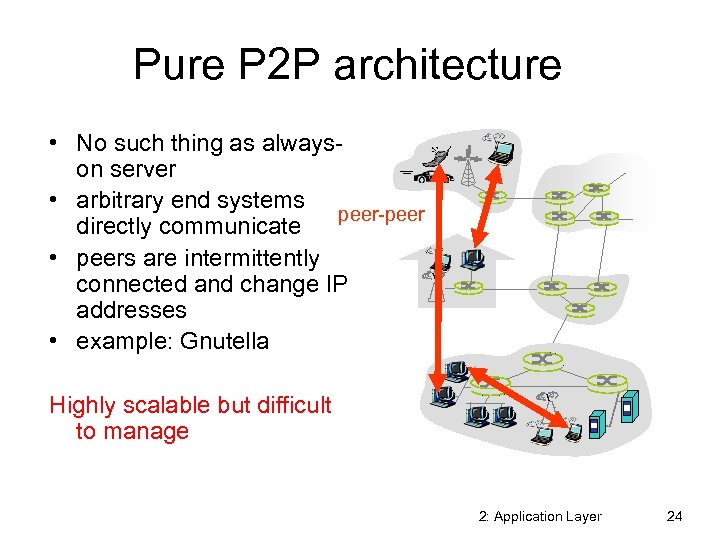 Pure P 2 P architecture • No such thing as alwayson server • arbitrary end systems peer-peer directly communicate • peers are intermittently connected and change IP addresses • example: Gnutella Highly scalable but difficult to manage 2: Application Layer 24
Pure P 2 P architecture • No such thing as alwayson server • arbitrary end systems peer-peer directly communicate • peers are intermittently connected and change IP addresses • example: Gnutella Highly scalable but difficult to manage 2: Application Layer 24
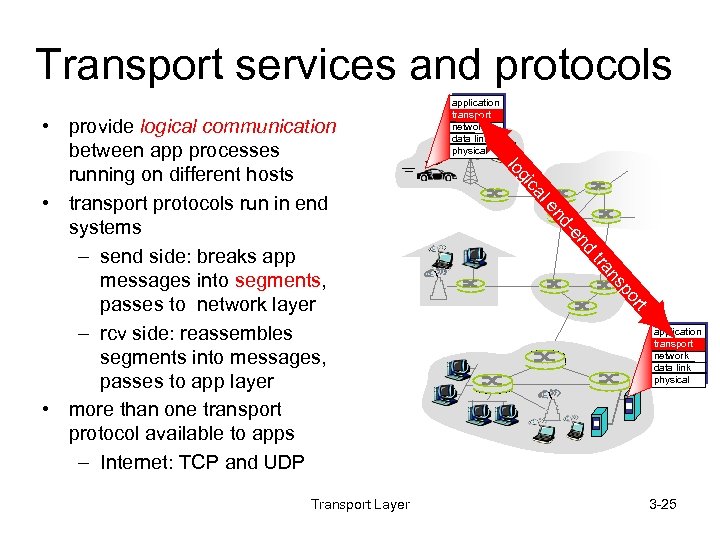 Transport services and protocols nd -e nd le ca gi rt po ns tra Transport Layer lo • provide logical communication between app processes running on different hosts • transport protocols run in end systems – send side: breaks app messages into segments, passes to network layer – rcv side: reassembles segments into messages, passes to app layer • more than one transport protocol available to apps – Internet: TCP and UDP application transport network data link physical 3 -25
Transport services and protocols nd -e nd le ca gi rt po ns tra Transport Layer lo • provide logical communication between app processes running on different hosts • transport protocols run in end systems – send side: breaks app messages into segments, passes to network layer – rcv side: reassembles segments into messages, passes to app layer • more than one transport protocol available to apps – Internet: TCP and UDP application transport network data link physical 3 -25
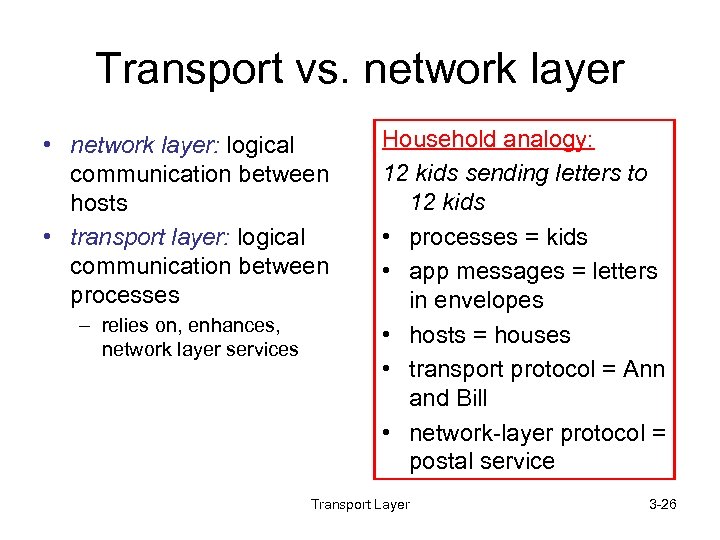 Transport vs. network layer • network layer: logical communication between hosts • transport layer: logical communication between processes – relies on, enhances, network layer services Household analogy: 12 kids sending letters to 12 kids • processes = kids • app messages = letters in envelopes • hosts = houses • transport protocol = Ann and Bill • network-layer protocol = postal service Transport Layer 3 -26
Transport vs. network layer • network layer: logical communication between hosts • transport layer: logical communication between processes – relies on, enhances, network layer services Household analogy: 12 kids sending letters to 12 kids • processes = kids • app messages = letters in envelopes • hosts = houses • transport protocol = Ann and Bill • network-layer protocol = postal service Transport Layer 3 -26
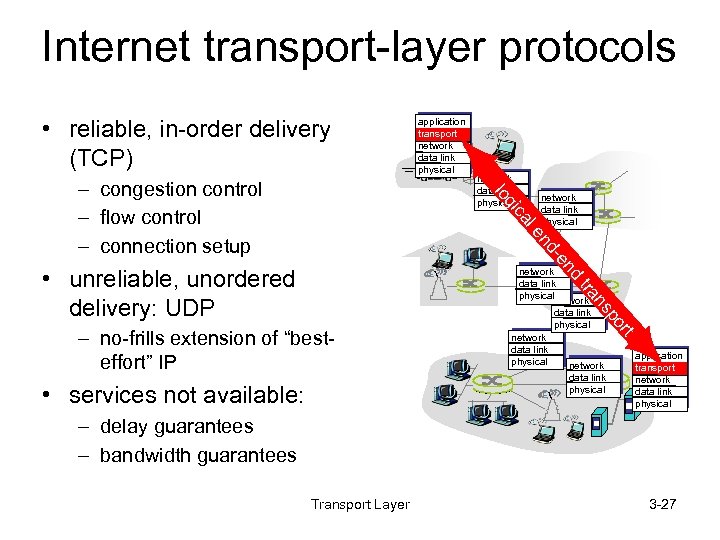 Internet transport-layer protocols • reliable, in-order delivery (TCP) network data link physical nd -e nd le ca gi lo – congestion control – flow control – connection setup application transport network data link physical • unreliable, unordered delivery: UDP network data link physical t • services not available: data link physical or – no-frills extension of “besteffort” IP p ns tra network data link physicalnetwork data link physical application transport network data link physical – delay guarantees – bandwidth guarantees Transport Layer 3 -27
Internet transport-layer protocols • reliable, in-order delivery (TCP) network data link physical nd -e nd le ca gi lo – congestion control – flow control – connection setup application transport network data link physical • unreliable, unordered delivery: UDP network data link physical t • services not available: data link physical or – no-frills extension of “besteffort” IP p ns tra network data link physicalnetwork data link physical application transport network data link physical – delay guarantees – bandwidth guarantees Transport Layer 3 -27
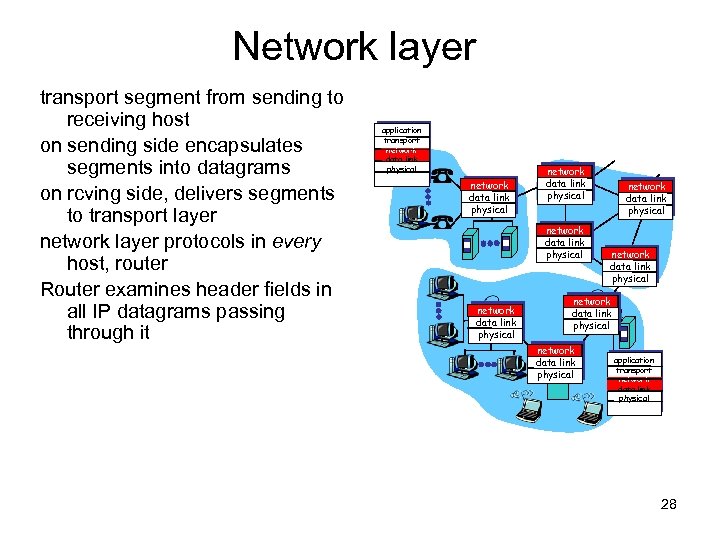 Network layer transport segment from sending to receiving host on sending side encapsulates segments into datagrams on rcving side, delivers segments to transport layer network layer protocols in every host, router Router examines header fields in all IP datagrams passing through it application transport network data link physical network data link physical network data link physical application transport network data link physical 28
Network layer transport segment from sending to receiving host on sending side encapsulates segments into datagrams on rcving side, delivers segments to transport layer network layer protocols in every host, router Router examines header fields in all IP datagrams passing through it application transport network data link physical network data link physical network data link physical application transport network data link physical 28
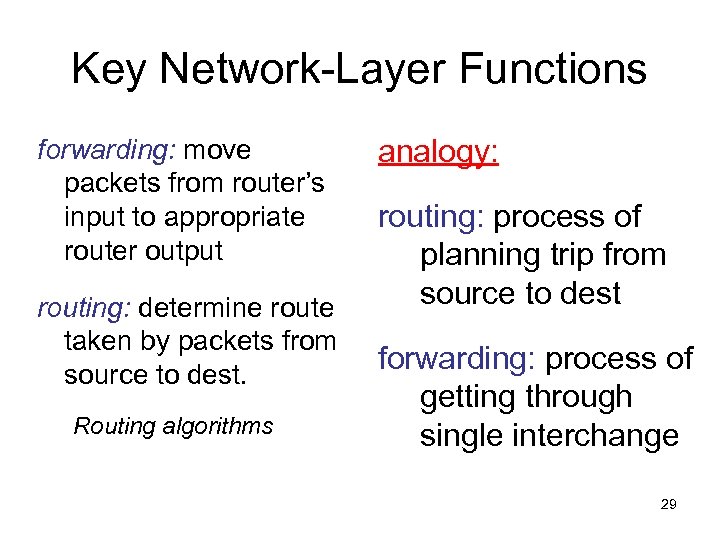 Key Network-Layer Functions forwarding: move packets from router’s input to appropriate router output routing: determine route taken by packets from source to dest. Routing algorithms analogy: routing: process of planning trip from source to dest forwarding: process of getting through single interchange 29
Key Network-Layer Functions forwarding: move packets from router’s input to appropriate router output routing: determine route taken by packets from source to dest. Routing algorithms analogy: routing: process of planning trip from source to dest forwarding: process of getting through single interchange 29
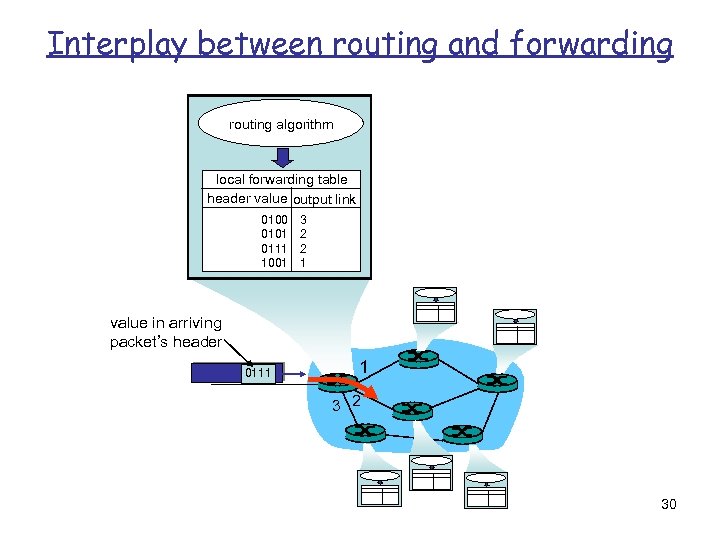 Interplay between routing and forwarding routing algorithm local forwarding table header value output link 0100 0101 0111 1001 3 2 2 1 value in arriving packet’s header 0111 1 3 2 30
Interplay between routing and forwarding routing algorithm local forwarding table header value output link 0100 0101 0111 1001 3 2 2 1 value in arriving packet’s header 0111 1 3 2 30
 • Datagram network: connectionless service • Virtual Circuit network: connection service Network Layer 4 -31
• Datagram network: connectionless service • Virtual Circuit network: connection service Network Layer 4 -31
 “Virtual circuit” connection source-to-dest connection is set up much like a telephone circuit • call setup for each connection before data can flow • each packet carries VC identifier • every intermediate router maintains state of the connection • resources (bandwidth, buffers) may be allocated to the VC at each intermediate router Network Layer 4 -32
“Virtual circuit” connection source-to-dest connection is set up much like a telephone circuit • call setup for each connection before data can flow • each packet carries VC identifier • every intermediate router maintains state of the connection • resources (bandwidth, buffers) may be allocated to the VC at each intermediate router Network Layer 4 -32
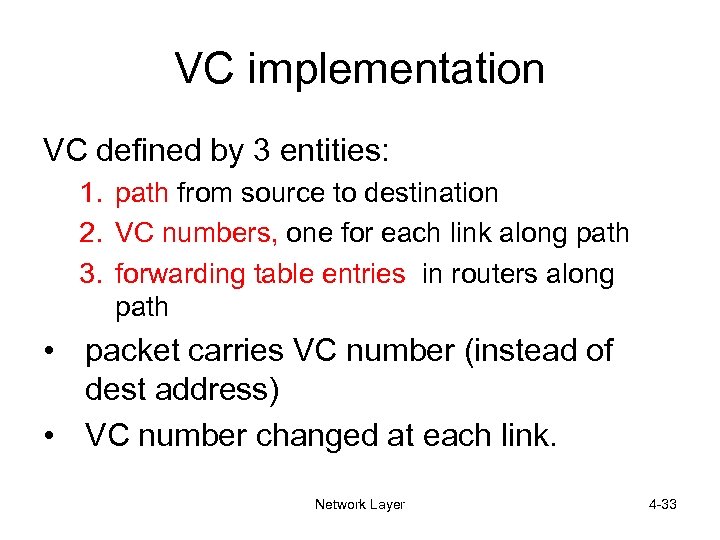 VC implementation VC defined by 3 entities: 1. path from source to destination 2. VC numbers, one for each link along path 3. forwarding table entries in routers along path • packet carries VC number (instead of dest address) • VC number changed at each link. Network Layer 4 -33
VC implementation VC defined by 3 entities: 1. path from source to destination 2. VC numbers, one for each link along path 3. forwarding table entries in routers along path • packet carries VC number (instead of dest address) • VC number changed at each link. Network Layer 4 -33
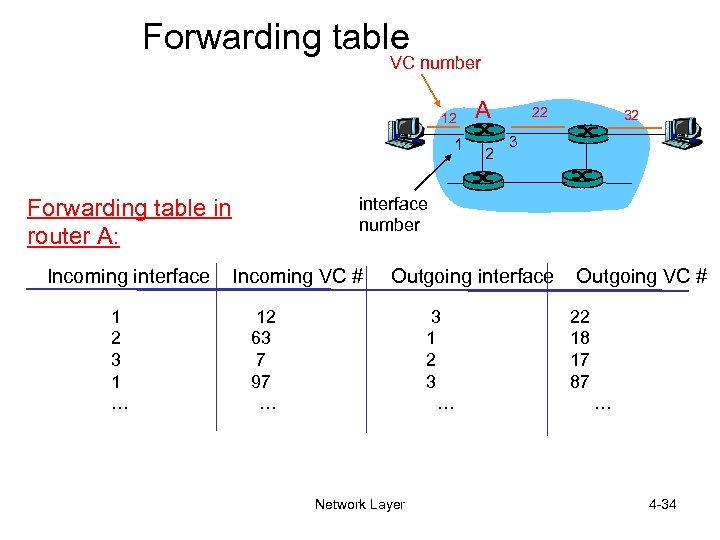 Forwarding table VC number 12 1 1 2 3 1 … 2 22 32 3 interface number Forwarding table in router A: Incoming interface A Incoming VC # Outgoing interface 12 63 7 97 … 3 1 2 3 … Network Layer Outgoing VC # 22 18 17 87 … 4 -34
Forwarding table VC number 12 1 1 2 3 1 … 2 22 32 3 interface number Forwarding table in router A: Incoming interface A Incoming VC # Outgoing interface 12 63 7 97 … 3 1 2 3 … Network Layer Outgoing VC # 22 18 17 87 … 4 -34
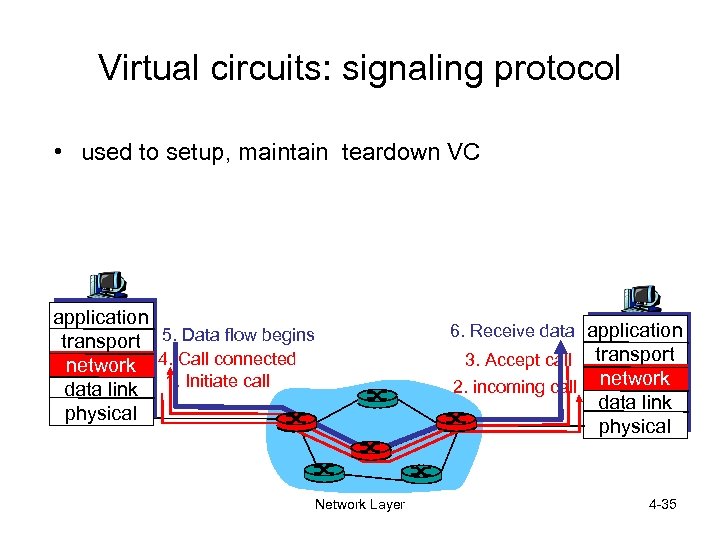 Virtual circuits: signaling protocol • used to setup, maintain teardown VC application transport 5. Data flow begins network 4. Call connected data link 1. Initiate call physical Network Layer 6. Receive data application 3. Accept call 2. incoming call transport network data link physical 4 -35
Virtual circuits: signaling protocol • used to setup, maintain teardown VC application transport 5. Data flow begins network 4. Call connected data link 1. Initiate call physical Network Layer 6. Receive data application 3. Accept call 2. incoming call transport network data link physical 4 -35
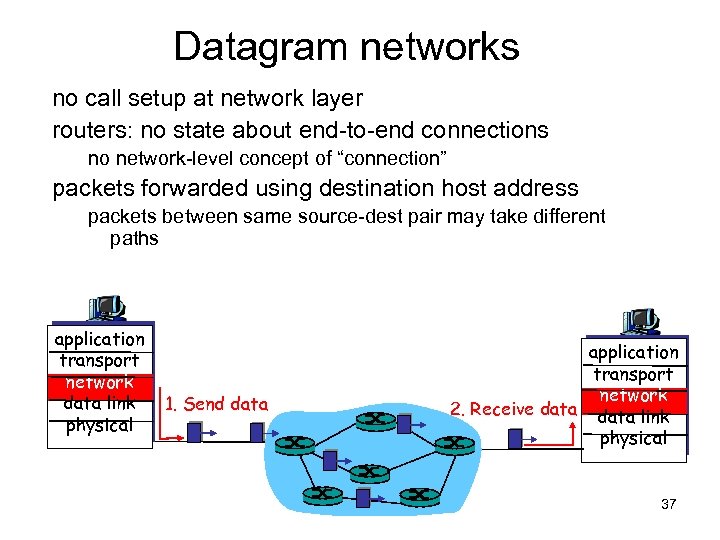 Datagram networks no call setup at network layer routers: no state about end-to-end connections no network-level concept of “connection” packets forwarded using destination host address packets between same source-dest pair may take different paths application transport network data link physical 1. Send data application transport network 2. Receive data link physical 37
Datagram networks no call setup at network layer routers: no state about end-to-end connections no network-level concept of “connection” packets forwarded using destination host address packets between same source-dest pair may take different paths application transport network data link physical 1. Send data application transport network 2. Receive data link physical 37
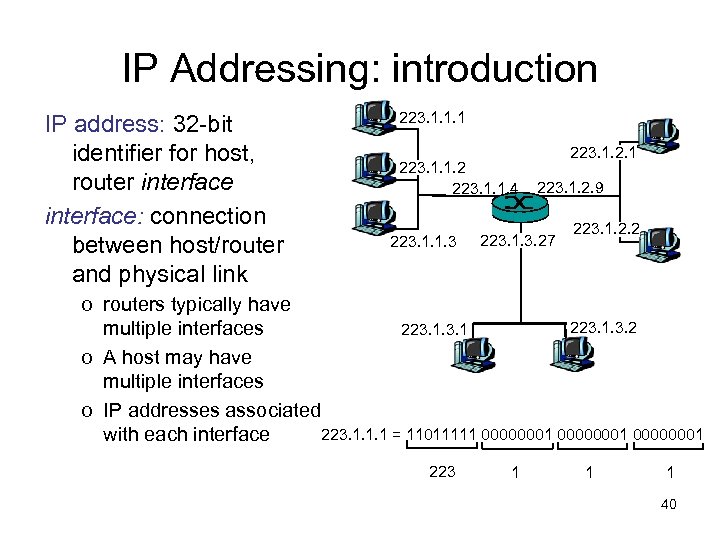 IP Addressing: introduction IP address: 32 -bit identifier for host, router interface: connection between host/router and physical link 223. 1. 1. 1 223. 1. 1. 2 223. 1. 1. 4 223. 1. 1. 3 223. 1. 2. 1 223. 1. 2. 9 223. 1. 3. 27 223. 1. 2. 2 o routers typically have 223. 1. 3. 2 223. 1 multiple interfaces o A host may have multiple interfaces o IP addresses associated 223. 1. 1. 1 = 11011111 00000001 with each interface 223 1 1 1 40
IP Addressing: introduction IP address: 32 -bit identifier for host, router interface: connection between host/router and physical link 223. 1. 1. 1 223. 1. 1. 2 223. 1. 1. 4 223. 1. 1. 3 223. 1. 2. 1 223. 1. 2. 9 223. 1. 3. 27 223. 1. 2. 2 o routers typically have 223. 1. 3. 2 223. 1 multiple interfaces o A host may have multiple interfaces o IP addresses associated 223. 1. 1. 1 = 11011111 00000001 with each interface 223 1 1 1 40
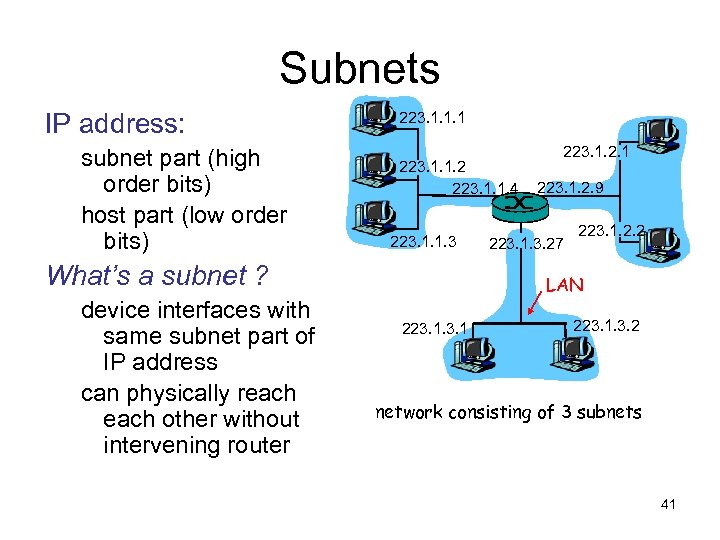 Subnets IP address: subnet part (high order bits) host part (low order bits) 223. 1. 1. 1 223. 1. 1. 2 223. 1. 1. 4 223. 1. 1. 3 What’s a subnet ? device interfaces with same subnet part of IP address can physically reach other without intervening router 223. 1. 2. 1 223. 1. 2. 9 223. 1. 3. 27 223. 1. 2. 2 LAN 223. 1. 3. 2 network consisting of 3 subnets 41
Subnets IP address: subnet part (high order bits) host part (low order bits) 223. 1. 1. 1 223. 1. 1. 2 223. 1. 1. 4 223. 1. 1. 3 What’s a subnet ? device interfaces with same subnet part of IP address can physically reach other without intervening router 223. 1. 2. 1 223. 1. 2. 9 223. 1. 3. 27 223. 1. 2. 2 LAN 223. 1. 3. 2 network consisting of 3 subnets 41
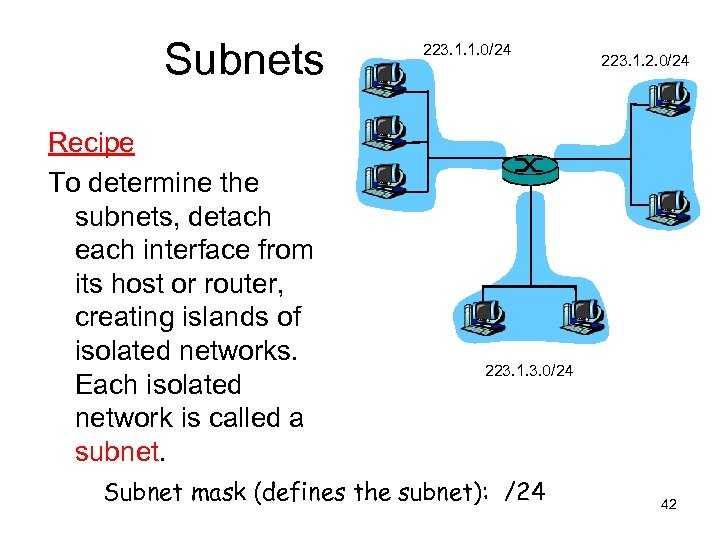 Subnets Recipe To determine the subnets, detach each interface from its host or router, creating islands of isolated networks. Each isolated network is called a subnet. 223. 1. 1. 0/24 223. 1. 2. 0/24 223. 1. 3. 0/24 Subnet mask (defines the subnet): /24 42
Subnets Recipe To determine the subnets, detach each interface from its host or router, creating islands of isolated networks. Each isolated network is called a subnet. 223. 1. 1. 0/24 223. 1. 2. 0/24 223. 1. 3. 0/24 Subnet mask (defines the subnet): /24 42
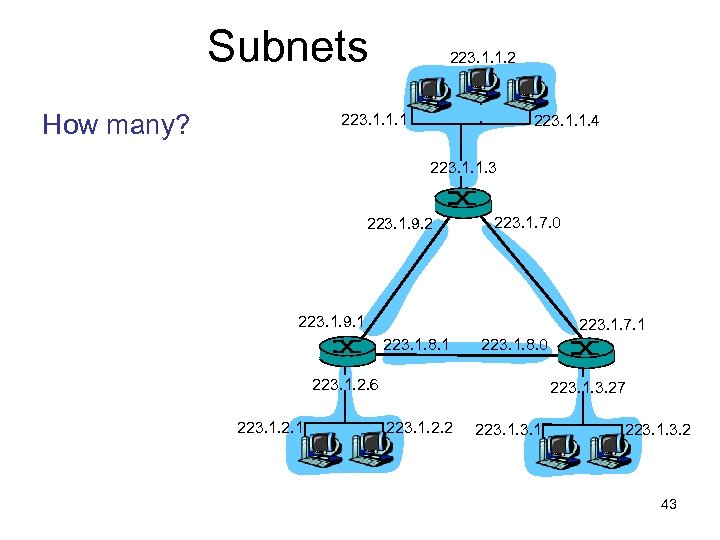 Subnets How many? 223. 1. 1. 2 223. 1. 1. 1 223. 1. 1. 4 223. 1. 1. 3 223. 1. 9. 2 223. 1. 7. 0 223. 1. 9. 1 223. 1. 7. 1 223. 1. 8. 0 223. 1. 2. 6 223. 1. 2. 1 223. 1. 3. 27 223. 1. 2. 2 223. 1. 3. 2 43
Subnets How many? 223. 1. 1. 2 223. 1. 1. 1 223. 1. 1. 4 223. 1. 1. 3 223. 1. 9. 2 223. 1. 7. 0 223. 1. 9. 1 223. 1. 7. 1 223. 1. 8. 0 223. 1. 2. 6 223. 1. 2. 1 223. 1. 3. 27 223. 1. 2. 2 223. 1. 3. 2 43
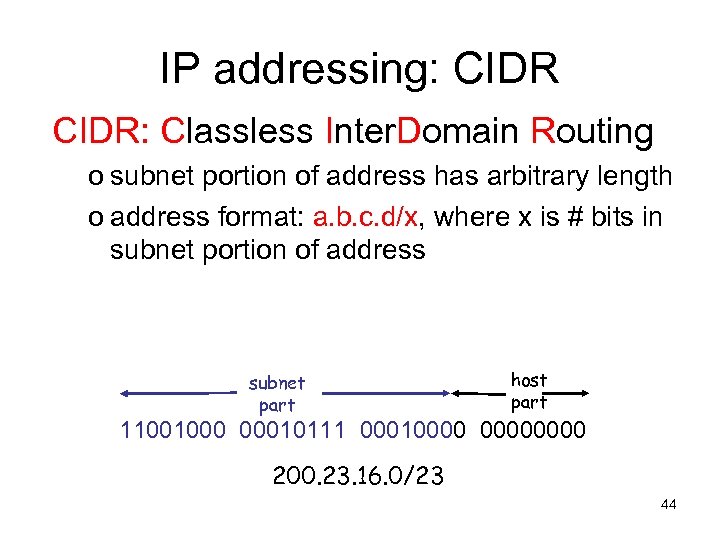 IP addressing: CIDR: Classless Inter. Domain Routing o subnet portion of address has arbitrary length o address format: a. b. c. d/x, where x is # bits in subnet portion of address subnet part host part 11001000 00010111 00010000 200. 23. 16. 0/23 44
IP addressing: CIDR: Classless Inter. Domain Routing o subnet portion of address has arbitrary length o address format: a. b. c. d/x, where x is # bits in subnet portion of address subnet part host part 11001000 00010111 00010000 200. 23. 16. 0/23 44
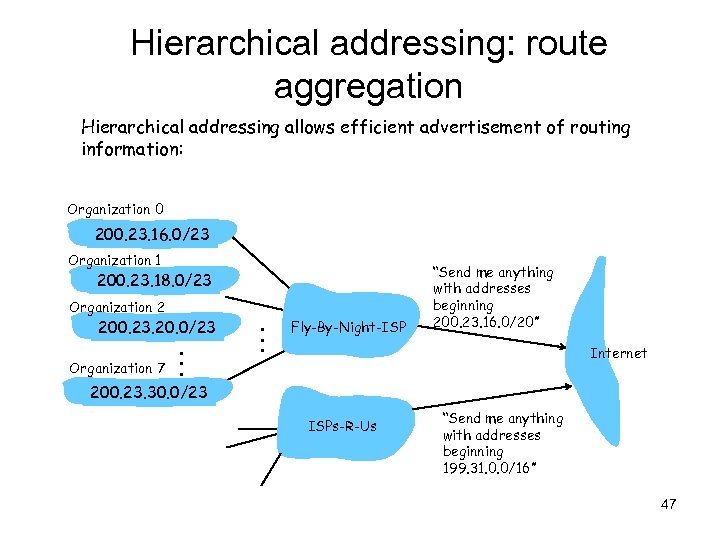 Hierarchical addressing: route aggregation Hierarchical addressing allows efficient advertisement of routing information: Organization 0 200. 23. 16. 0/23 Organization 1 200. 23. 18. 0/23 Organization 2 200. 23. 20. 0/23 Organization 7 . . . Fly-By-Night-ISP “Send me anything with addresses beginning 200. 23. 16. 0/20” Internet 200. 23. 30. 0/23 ISPs-R-Us “Send me anything with addresses beginning 199. 31. 0. 0/16” 47
Hierarchical addressing: route aggregation Hierarchical addressing allows efficient advertisement of routing information: Organization 0 200. 23. 16. 0/23 Organization 1 200. 23. 18. 0/23 Organization 2 200. 23. 20. 0/23 Organization 7 . . . Fly-By-Night-ISP “Send me anything with addresses beginning 200. 23. 16. 0/20” Internet 200. 23. 30. 0/23 ISPs-R-Us “Send me anything with addresses beginning 199. 31. 0. 0/16” 47
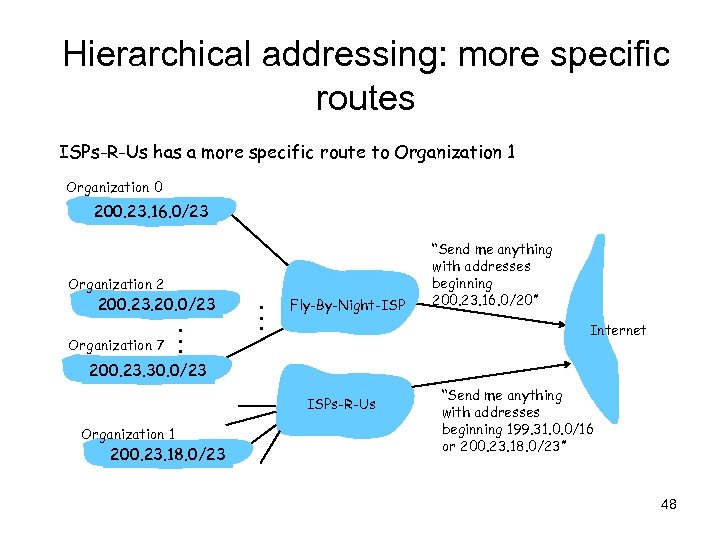 Hierarchical addressing: more specific routes ISPs-R-Us has a more specific route to Organization 1 Organization 0 200. 23. 16. 0/23 Organization 2 200. 23. 20. 0/23 Organization 7 . . . Fly-By-Night-ISP “Send me anything with addresses beginning 200. 23. 16. 0/20” Internet 200. 23. 30. 0/23 ISPs-R-Us Organization 1 200. 23. 18. 0/23 “Send me anything with addresses beginning 199. 31. 0. 0/16 or 200. 23. 18. 0/23” 48
Hierarchical addressing: more specific routes ISPs-R-Us has a more specific route to Organization 1 Organization 0 200. 23. 16. 0/23 Organization 2 200. 23. 20. 0/23 Organization 7 . . . Fly-By-Night-ISP “Send me anything with addresses beginning 200. 23. 16. 0/20” Internet 200. 23. 30. 0/23 ISPs-R-Us Organization 1 200. 23. 18. 0/23 “Send me anything with addresses beginning 199. 31. 0. 0/16 or 200. 23. 18. 0/23” 48
 IP addressing: the last word. . . Q: How does an ISP get block of addresses? A: ICANN: Internet Corporation for Assigned Names and Numbers o allocates addresses o manages DNS o assigns domain names, resolves disputes 49
IP addressing: the last word. . . Q: How does an ISP get block of addresses? A: ICANN: Internet Corporation for Assigned Names and Numbers o allocates addresses o manages DNS o assigns domain names, resolves disputes 49
 Link Layer: Introduction Some terminology: • hosts and routers are nodes • communication channels that connect adjacent nodes along communication path are links – wired links – wireless links – LANs • layer-2 packet is a frame, encapsulates datagram data-link layer has responsibility of transferring datagram from one node to adjacent node over a link Data. Link Layer 5: 5 -50
Link Layer: Introduction Some terminology: • hosts and routers are nodes • communication channels that connect adjacent nodes along communication path are links – wired links – wireless links – LANs • layer-2 packet is a frame, encapsulates datagram data-link layer has responsibility of transferring datagram from one node to adjacent node over a link Data. Link Layer 5: 5 -50
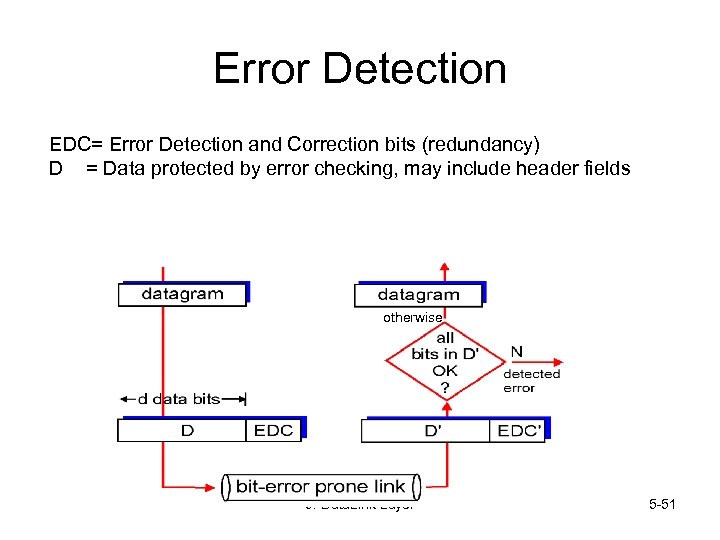 Error Detection EDC= Error Detection and Correction bits (redundancy) D = Data protected by error checking, may include header fields otherwise 5: Data. Link Layer 5 -51
Error Detection EDC= Error Detection and Correction bits (redundancy) D = Data protected by error checking, may include header fields otherwise 5: Data. Link Layer 5 -51
 Wireless Networks • In recent years, there has been an explosion of wireless applications • Three wireless “waves”: – Cellular networks (ie, cellphones) – Wireless LANs – Ad Hoc Networks; Personal Area Networks; sensor networks 52
Wireless Networks • In recent years, there has been an explosion of wireless applications • Three wireless “waves”: – Cellular networks (ie, cellphones) – Wireless LANs – Ad Hoc Networks; Personal Area Networks; sensor networks 52
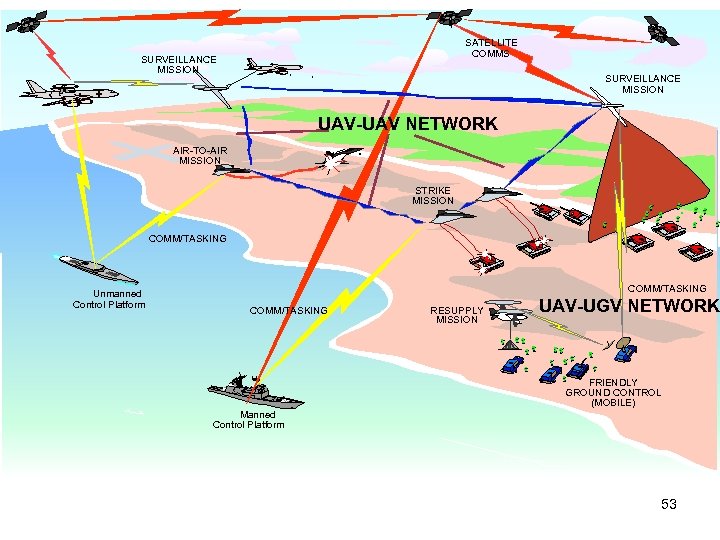 SATELLITE COMMS SURVEILLANCE MISSION UAV-UAV NETWORK AIR-TO-AIR MISSION STRIKE MISSION COMM/TASKING Unmanned Control Platform COMM/TASKING RESUPPLY MISSION UAV-UGV NETWORK FRIENDLY GROUND CONTROL (MOBILE) Manned Control Platform AINS Scenario: Network of Autonomous Agents 53
SATELLITE COMMS SURVEILLANCE MISSION UAV-UAV NETWORK AIR-TO-AIR MISSION STRIKE MISSION COMM/TASKING Unmanned Control Platform COMM/TASKING RESUPPLY MISSION UAV-UGV NETWORK FRIENDLY GROUND CONTROL (MOBILE) Manned Control Platform AINS Scenario: Network of Autonomous Agents 53
 Ad Hoc Deployment of Sensors… 54
Ad Hoc Deployment of Sensors… 54
 Self-Configuration… 55
Self-Configuration… 55
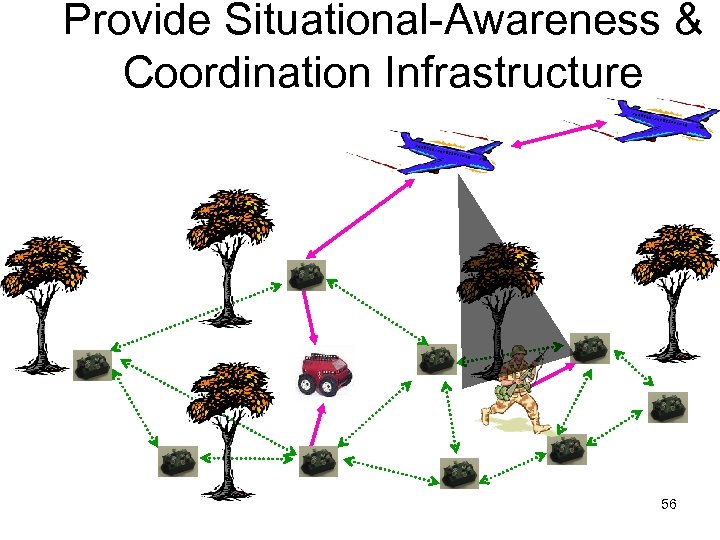 Provide Situational-Awareness & Coordination Infrastructure 56
Provide Situational-Awareness & Coordination Infrastructure 56
 Why are wireless nets so difficult to design? • It is all in the physical layer! • In a wired network, the physical layer is a cable, fiber, twisted pair, electric wire, etc: – Static; properties can be easily abstracted with few parameters (eg, bandwidth, delay) – The wired network (Internet) protocols are designed independently of the physical layer – Traditional Networking courses (like CS 118) focus on Internet protocols above physical layer 57
Why are wireless nets so difficult to design? • It is all in the physical layer! • In a wired network, the physical layer is a cable, fiber, twisted pair, electric wire, etc: – Static; properties can be easily abstracted with few parameters (eg, bandwidth, delay) – The wired network (Internet) protocols are designed independently of the physical layer – Traditional Networking courses (like CS 118) focus on Internet protocols above physical layer 57
 Why wireless so difficult…? In the wireless network: • Nodes can move • Nodes may run out of power • Nodes can be “compromised” by the enemy • Radio channel can be jammed, eavesdropped • Reception properties continually change (in unpredictable way) • The wireless physical layer has a major impact on the way the MAC, Network, Transport and even Application layers are designed! • Cross-layer interaction is the “mantra”! 58
Why wireless so difficult…? In the wireless network: • Nodes can move • Nodes may run out of power • Nodes can be “compromised” by the enemy • Radio channel can be jammed, eavesdropped • Reception properties continually change (in unpredictable way) • The wireless physical layer has a major impact on the way the MAC, Network, Transport and even Application layers are designed! • Cross-layer interaction is the “mantra”! 58
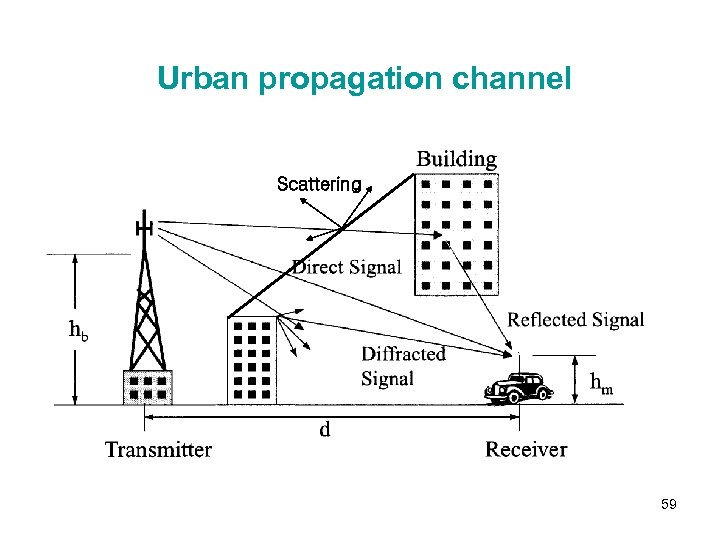 Urban propagation channel Scattering 59
Urban propagation channel Scattering 59
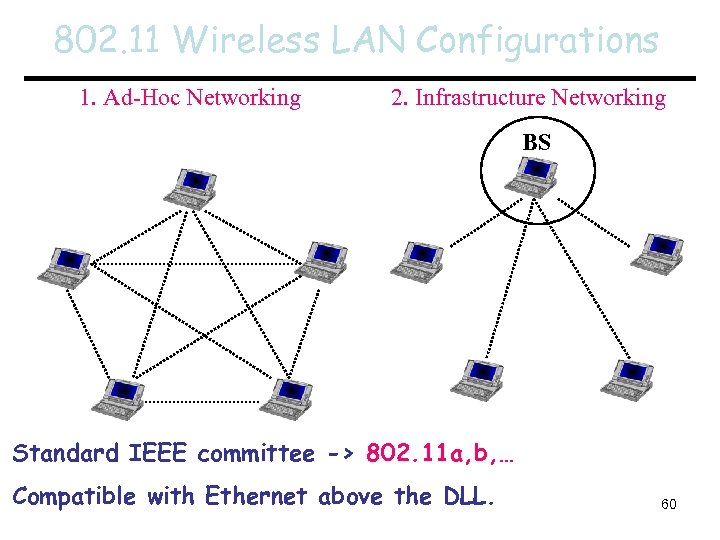 802. 11 Wireless LAN Configurations 1. Ad-Hoc Networking 2. Infrastructure Networking BS Standard IEEE committee -> 802. 11 a, b, … Compatible with Ethernet above the DLL. 60
802. 11 Wireless LAN Configurations 1. Ad-Hoc Networking 2. Infrastructure Networking BS Standard IEEE committee -> 802. 11 a, b, … Compatible with Ethernet above the DLL. 60
 Bluetooth “personal net” application 61
Bluetooth “personal net” application 61
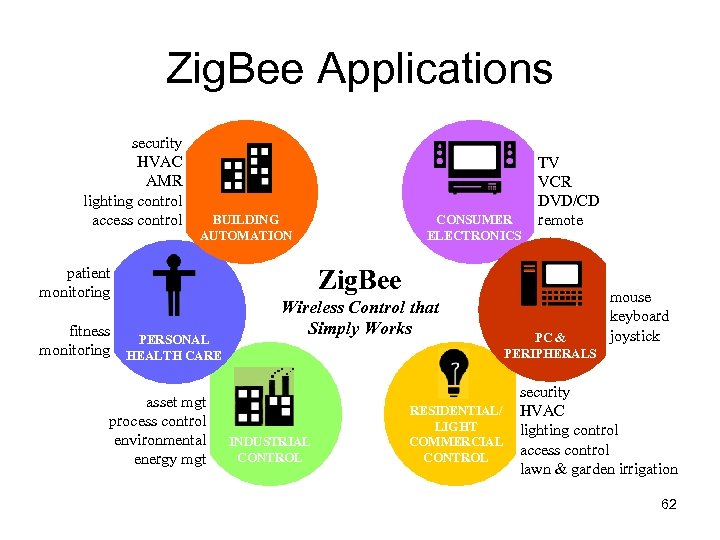 Zig. Bee Applications security HVAC AMR lighting control access control BUILDING AUTOMATION patient monitoring fitness PERSONAL monitoring HEALTH CARE asset mgt process control environmental energy mgt CONSUMER ELECTRONICS TV VCR DVD/CD remote Zig. Bee Wireless Control that Simply Works INDUSTRIAL CONTROL RESIDENTIAL/ LIGHT COMMERCIAL CONTROL PC & PERIPHERALS mouse keyboard joystick security HVAC lighting control access control lawn & garden irrigation 62
Zig. Bee Applications security HVAC AMR lighting control access control BUILDING AUTOMATION patient monitoring fitness PERSONAL monitoring HEALTH CARE asset mgt process control environmental energy mgt CONSUMER ELECTRONICS TV VCR DVD/CD remote Zig. Bee Wireless Control that Simply Works INDUSTRIAL CONTROL RESIDENTIAL/ LIGHT COMMERCIAL CONTROL PC & PERIPHERALS mouse keyboard joystick security HVAC lighting control access control lawn & garden irrigation 62
 63
63


