4784a2e9e281c085c9a9626c9f53d153.ppt
- Количество слайдов: 82
 Cryptography Survey on Information Assurance TEL 581 Presented by Viswesh Prabhu Subramanian Gregory Michel Lincoln Jean Louis
Cryptography Survey on Information Assurance TEL 581 Presented by Viswesh Prabhu Subramanian Gregory Michel Lincoln Jean Louis
 Agenda Cryptography definition Cryptography history Hash algorithm and its uses Public Key Infrastructure
Agenda Cryptography definition Cryptography history Hash algorithm and its uses Public Key Infrastructure
 Encryption and Cryptography By using Encryption, a message in its original form (plaintext) is encrypted into an unintelligible form (ciphertext) by a set of procedures known as an encryption algorithm and a variable, called a key; and the ciphertext is transformed (decrypted) back into plaintext using the encryption algorithm and a key. Encryption forms the basis of many technological solutions to computer and communications security problems. http: //ocw. mit. edu/NR/rdonlyres/Electrical-Engineering-and-Computer-Science/6 -875 Spring-2005/0 F 52083 E-BDFB-45 A 5 -B 8043 C 186 AFC 80 B 3/0/chp_lock_binary. jpg
Encryption and Cryptography By using Encryption, a message in its original form (plaintext) is encrypted into an unintelligible form (ciphertext) by a set of procedures known as an encryption algorithm and a variable, called a key; and the ciphertext is transformed (decrypted) back into plaintext using the encryption algorithm and a key. Encryption forms the basis of many technological solutions to computer and communications security problems. http: //ocw. mit. edu/NR/rdonlyres/Electrical-Engineering-and-Computer-Science/6 -875 Spring-2005/0 F 52083 E-BDFB-45 A 5 -B 8043 C 186 AFC 80 B 3/0/chp_lock_binary. jpg
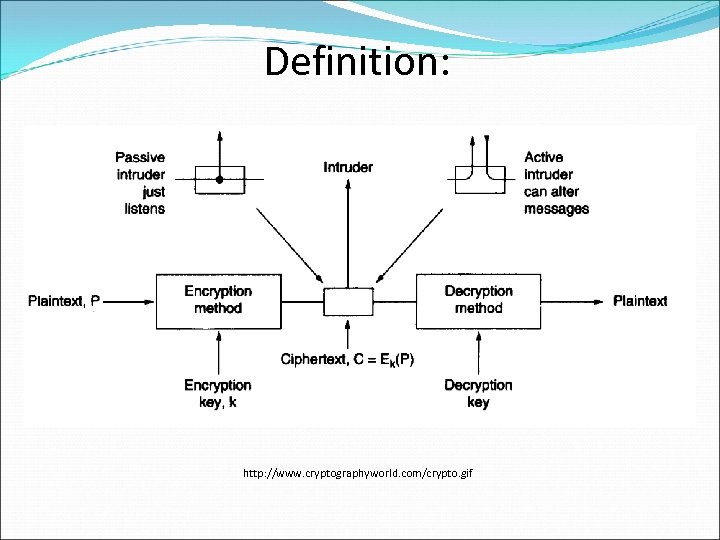 Definition: http: //www. cryptographyworld. com/crypto. gif
Definition: http: //www. cryptographyworld. com/crypto. gif
 Cryptography Through History • Cryptography has a history of at least 4000 years. • Ancient Egyptians enciphered some of their hieroglyphic writing on monuments. • Ancient Hebrews enciphered certain words in the scriptures. • 2000 years ago Julius Caesar used a simple substitution cipher, now known as the Caesar cipher.
Cryptography Through History • Cryptography has a history of at least 4000 years. • Ancient Egyptians enciphered some of their hieroglyphic writing on monuments. • Ancient Hebrews enciphered certain words in the scriptures. • 2000 years ago Julius Caesar used a simple substitution cipher, now known as the Caesar cipher.
 Cryptography Through History • Geoffrey Chaucer included several ciphers in his works (e. g. Canterbury Tales). • Leon Alberti devised a cipher wheel, and described the principles of frequency analysis in the 1460 s. • Blaise de Vigenère published a book on cryptology in 1585, & described the polyalphabetic substitution cipher. • Increasing use, especially in diplomacy & war over centuries. (UK and Germany)
Cryptography Through History • Geoffrey Chaucer included several ciphers in his works (e. g. Canterbury Tales). • Leon Alberti devised a cipher wheel, and described the principles of frequency analysis in the 1460 s. • Blaise de Vigenère published a book on cryptology in 1585, & described the polyalphabetic substitution cipher. • Increasing use, especially in diplomacy & war over centuries. (UK and Germany)
 History - Caesar Cipher • Julius Caesar used a simple alphabet (letter) substitution, offset by 3 letters. • Taking the word “cipher" you would move ahead in the alphabet 3 letters to get “FLSKHU”. c =3 3+3 = 6 F • This worked for a while, until more people learned to read and studied his secret cipher. 7
History - Caesar Cipher • Julius Caesar used a simple alphabet (letter) substitution, offset by 3 letters. • Taking the word “cipher" you would move ahead in the alphabet 3 letters to get “FLSKHU”. c =3 3+3 = 6 F • This worked for a while, until more people learned to read and studied his secret cipher. 7
 History - The Grille • In the 1600's Cardinal Richelieu invented the grille. • He created a card with holes in it and used it to write a secret message. • When he was done he removed the card and wrote a letter to fill in the blanks and make the message look like a normal letter. • The grille proved to be difficult to solve unless the decoder had the card which created the encrypted message.
History - The Grille • In the 1600's Cardinal Richelieu invented the grille. • He created a card with holes in it and used it to write a secret message. • When he was done he removed the card and wrote a letter to fill in the blanks and make the message look like a normal letter. • The grille proved to be difficult to solve unless the decoder had the card which created the encrypted message.
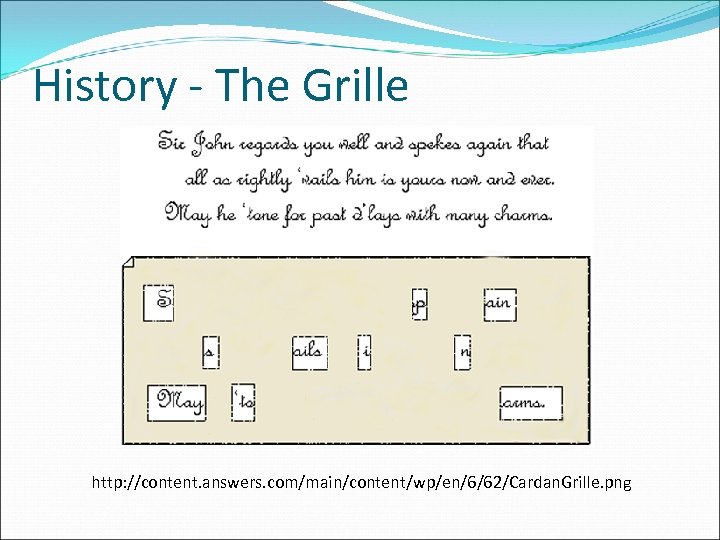 History - The Grille http: //content. answers. com/main/content/wp/en/6/62/Cardan. Grille. png
History - The Grille http: //content. answers. com/main/content/wp/en/6/62/Cardan. Grille. png
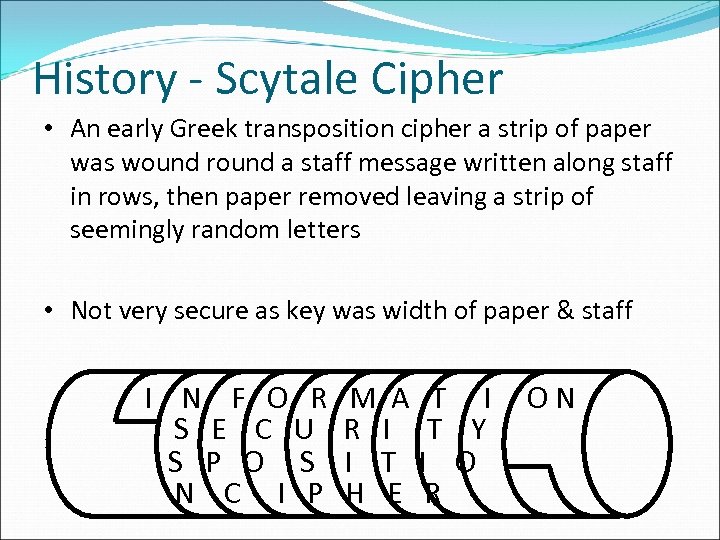 History - Scytale Cipher • An early Greek transposition cipher a strip of paper was wound round a staff message written along staff in rows, then paper removed leaving a strip of seemingly random letters • Not very secure as key was width of paper & staff I N F O R S E C U S P O S N C I P M A T I R I T Y I T I O H E R ON
History - Scytale Cipher • An early Greek transposition cipher a strip of paper was wound round a staff message written along staff in rows, then paper removed leaving a strip of seemingly random letters • Not very secure as key was width of paper & staff I N F O R S E C U S P O S N C I P M A T I R I T Y I T I O H E R ON
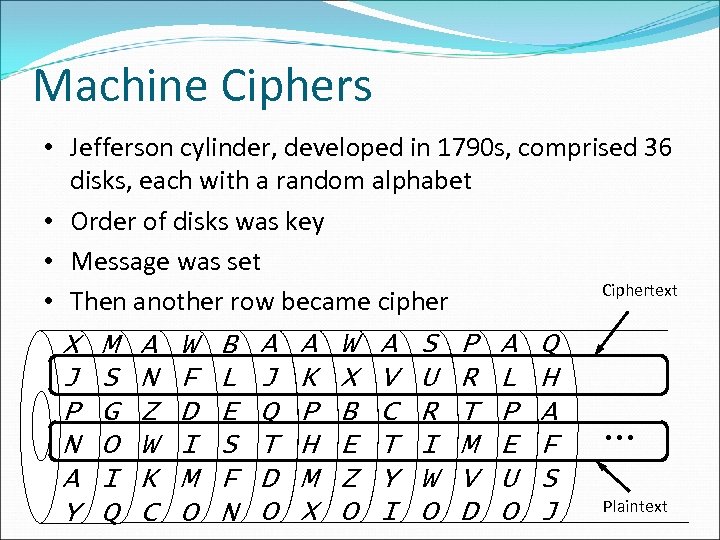 Machine Ciphers • Jefferson cylinder, developed in 1790 s, comprised 36 disks, each with a random alphabet • Order of disks was key • Message was set Ciphertext • Then another row became cipher X M A W B A A W A S P A Q J S N F L J K X V U R L H P G Z D E Q P B C R T P A N O W I S T H E T I M E F A I K M F D M Z Y W V U S Plaintext Y Q C O N O X O I O D O J …
Machine Ciphers • Jefferson cylinder, developed in 1790 s, comprised 36 disks, each with a random alphabet • Order of disks was key • Message was set Ciphertext • Then another row became cipher X M A W B A A W A S P A Q J S N F L J K X V U R L H P G Z D E Q P B C R T P A N O W I S T H E T I M E F A I K M F D M Z Y W V U S Plaintext Y Q C O N O X O I O D O J …
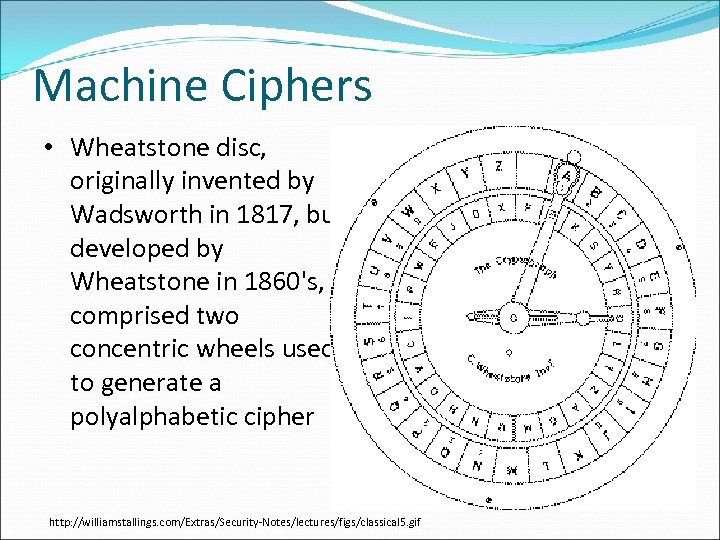 Machine Ciphers • Wheatstone disc, originally invented by Wadsworth in 1817, but developed by Wheatstone in 1860's, comprised two concentric wheels used to generate a polyalphabetic cipher http: //williamstallings. com/Extras/Security-Notes/lectures/figs/classical 5. gif
Machine Ciphers • Wheatstone disc, originally invented by Wadsworth in 1817, but developed by Wheatstone in 1860's, comprised two concentric wheels used to generate a polyalphabetic cipher http: //williamstallings. com/Extras/Security-Notes/lectures/figs/classical 5. gif
 Enigma • The Enigma Rotor machine, one of a very important class of cipher machines, heavily used during 2 nd world war. • Comprised a series of rotor wheels with internal cross-connections, providing a substitution using a continuously changing alphabet. Content source: www. fim. uni-linz. ac. at/lva/Informatikkonzepte_im_E_Business/ws 2004/Cryptography. pd
Enigma • The Enigma Rotor machine, one of a very important class of cipher machines, heavily used during 2 nd world war. • Comprised a series of rotor wheels with internal cross-connections, providing a substitution using a continuously changing alphabet. Content source: www. fim. uni-linz. ac. at/lva/Informatikkonzepte_im_E_Business/ws 2004/Cryptography. pd
 Enigma http: //www. armyradio. com/publish/Articles/The_Enigma_Code_Breach/Pictures/Enigma_3 -rotor_Polish. jpg 14
Enigma http: //www. armyradio. com/publish/Articles/The_Enigma_Code_Breach/Pictures/Enigma_3 -rotor_Polish. jpg 14
 History - Morse Code • Morse Code, developed by Samuel Morse in 1832, is not really a code at all. • It is a way of enciphering (cipher) letters of the alphabet into long and short sounds. • The invention of the telegraph, along with Morse code, helped people to communicate over long distances. • Morse code can be used in any language and takes only 1 to 10 hours of instruction/practice to learn! • The first Morse code sent by telegraph was “What hath God wrought? ”, in 1844. Source: http: //en. wikipedia. org/wiki/Morse_code
History - Morse Code • Morse Code, developed by Samuel Morse in 1832, is not really a code at all. • It is a way of enciphering (cipher) letters of the alphabet into long and short sounds. • The invention of the telegraph, along with Morse code, helped people to communicate over long distances. • Morse code can be used in any language and takes only 1 to 10 hours of instruction/practice to learn! • The first Morse code sent by telegraph was “What hath God wrought? ”, in 1844. Source: http: //en. wikipedia. org/wiki/Morse_code
 History - Morse Code http: //bp 3. blogger. com/_bx. PNX 2 u 34 g. U/Rl 5 m. C 0 fk 1 XI/AAAAAHs/B 8_Wd. QW 45 CM/s 1600 h/morse. png http: //storyrobot. com/improv/wpcontent/uploads/2007/11/morse. jpg
History - Morse Code http: //bp 3. blogger. com/_bx. PNX 2 u 34 g. U/Rl 5 m. C 0 fk 1 XI/AAAAAHs/B 8_Wd. QW 45 CM/s 1600 h/morse. png http: //storyrobot. com/improv/wpcontent/uploads/2007/11/morse. jpg
 Cryptanalaysis • Cryptanalysis - The study of principles and methods of transforming an unintelligible message back into an intelligible message without knowledge of the key. • Cryptographers - People who do cryptography are cryptographers. • Cryptoanalysis - practitioners of cryptanalysis.
Cryptanalaysis • Cryptanalysis - The study of principles and methods of transforming an unintelligible message back into an intelligible message without knowledge of the key. • Cryptographers - People who do cryptography are cryptographers. • Cryptoanalysis - practitioners of cryptanalysis.
 Cryptology • Cryptology is the branch of mathematics that studies the mathematical foundations of cryptographic methods. • Cryptology comes from the Greek words Kryptos, meaning hidden, and Graphen, meaning to write. Cryptology is actually the study of codes and ciphers. • Cryptology = both cryptography and cryptanalysis Content source: http: //www. jjtc. com/Security/crypto. htm
Cryptology • Cryptology is the branch of mathematics that studies the mathematical foundations of cryptographic methods. • Cryptology comes from the Greek words Kryptos, meaning hidden, and Graphen, meaning to write. Cryptology is actually the study of codes and ciphers. • Cryptology = both cryptography and cryptanalysis Content source: http: //www. jjtc. com/Security/crypto. htm
 Encryption Algorithm Types • There are two classes of key-based algorithms: – Symmetric (or secret-key) – Asymmetric (or public-key) algorithms
Encryption Algorithm Types • There are two classes of key-based algorithms: – Symmetric (or secret-key) – Asymmetric (or public-key) algorithms
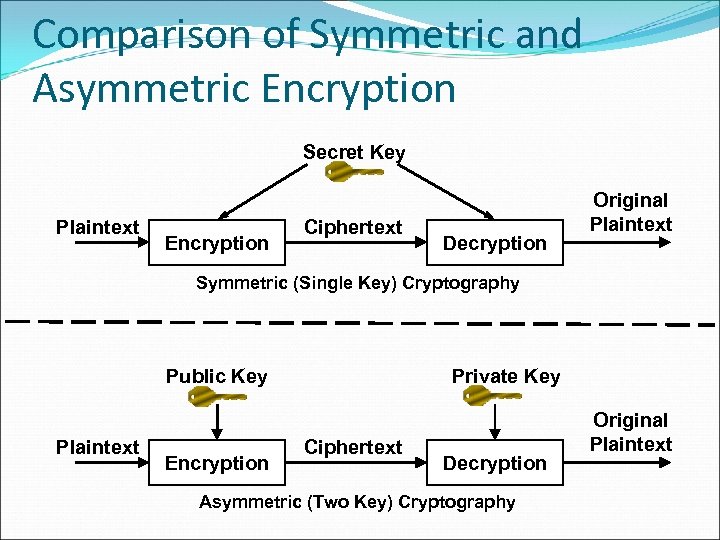 Comparison of Symmetric and Asymmetric Encryption Secret Key Plaintext Encryption Ciphertext Decryption Original Plaintext Symmetric (Single Key) Cryptography Private Key Public Key Plaintext Encryption Ciphertext Decryption Asymmetric (Two Key) Cryptography Original Plaintext
Comparison of Symmetric and Asymmetric Encryption Secret Key Plaintext Encryption Ciphertext Decryption Original Plaintext Symmetric (Single Key) Cryptography Private Key Public Key Plaintext Encryption Ciphertext Decryption Asymmetric (Two Key) Cryptography Original Plaintext
 Symmetric Algorithms • Symmetric algorithms can be divided into two categories: (1) stream ciphers (2) block ciphers. • Stream ciphers can encrypt a single bit/byte of plaintext at a time, whereas … • Block ciphers take a number of bits (typically 64 bits in modern ciphers), and encrypt them as a single unit. Content source: ww. secguru. com/link/cissp_ domain_5_cryptography_presentation_ppt
Symmetric Algorithms • Symmetric algorithms can be divided into two categories: (1) stream ciphers (2) block ciphers. • Stream ciphers can encrypt a single bit/byte of plaintext at a time, whereas … • Block ciphers take a number of bits (typically 64 bits in modern ciphers), and encrypt them as a single unit. Content source: ww. secguru. com/link/cissp_ domain_5_cryptography_presentation_ppt
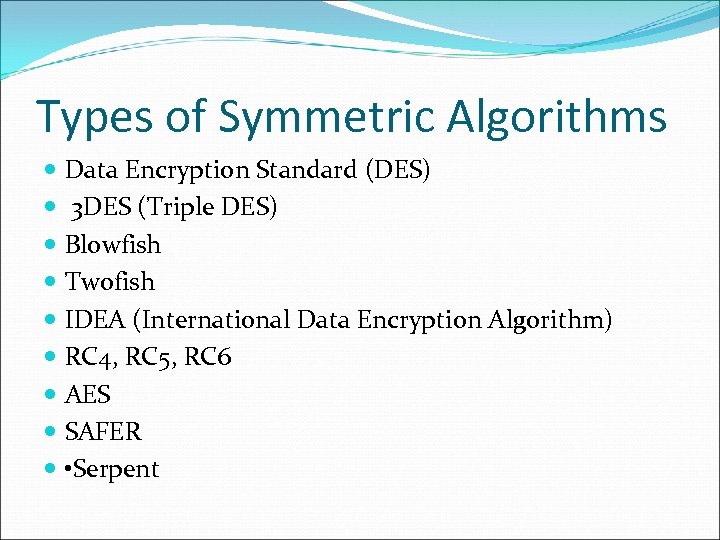 Types of Symmetric Algorithms Data Encryption Standard (DES) 3 DES (Triple DES) Blowfish Twofish IDEA (International Data Encryption Algorithm) RC 4, RC 5, RC 6 AES SAFER • Serpent
Types of Symmetric Algorithms Data Encryption Standard (DES) 3 DES (Triple DES) Blowfish Twofish IDEA (International Data Encryption Algorithm) RC 4, RC 5, RC 6 AES SAFER • Serpent
 Asymmetric Algorithms The encryption key is also called the Public Key and the decryption key the Private Key or Secret Key.
Asymmetric Algorithms The encryption key is also called the Public Key and the decryption key the Private Key or Secret Key.
 Types of Symmetric Algorithms The Diffie-Hellman Algorithm RSA El Gamal Elliptic Curve Cryptosystems
Types of Symmetric Algorithms The Diffie-Hellman Algorithm RSA El Gamal Elliptic Curve Cryptosystems
 HASH Algorithms and Uses
HASH Algorithms and Uses
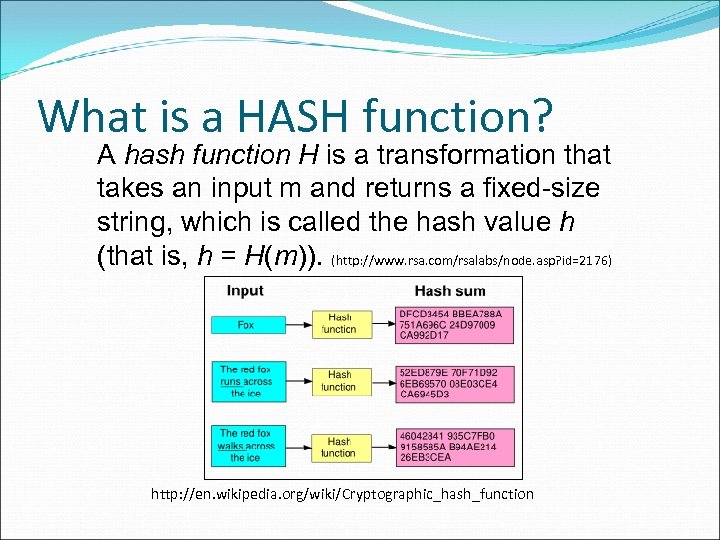 What is a HASH function? A hash function H is a transformation that takes an input m and returns a fixed-size string, which is called the hash value h (that is, h = H(m)). (http: //www. rsa. com/rsalabs/node. asp? id=2176) http: //en. wikipedia. org/wiki/Cryptographic_hash_function
What is a HASH function? A hash function H is a transformation that takes an input m and returns a fixed-size string, which is called the hash value h (that is, h = H(m)). (http: //www. rsa. com/rsalabs/node. asp? id=2176) http: //en. wikipedia. org/wiki/Cryptographic_hash_function
 HASH Algorithms One way HASH Message Authentication Code (MAC) HMAC CBCMAC MD 2 MD 4 MD 5
HASH Algorithms One way HASH Message Authentication Code (MAC) HMAC CBCMAC MD 2 MD 4 MD 5
 HASH Algorithms (cont) SHA HAVAL Tiger
HASH Algorithms (cont) SHA HAVAL Tiger
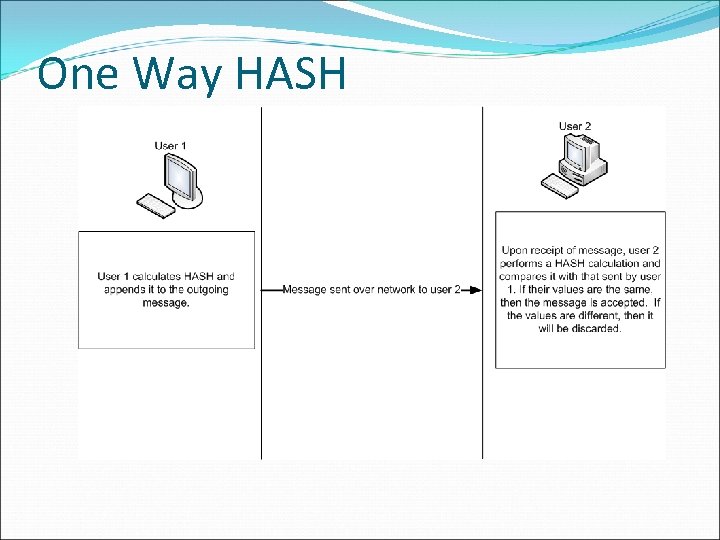
 ONE WAY HASH A one-way hash is a function that takes a variable-length string and a message and produces a fixed-length value called a hash value. (CISSP Certification All in One Exam Guide, Pg. 714)
ONE WAY HASH A one-way hash is a function that takes a variable-length string and a message and produces a fixed-length value called a hash value. (CISSP Certification All in One Exam Guide, Pg. 714)
 One Way HASH
One Way HASH
 One Way HASH A one way HASH is never reversed. The function is run in only one direction and not the other direction.
One Way HASH A one way HASH is never reversed. The function is run in only one direction and not the other direction.
 One Way HASH One Way Hash functions operate without any keys. Thus for better security, Message Authentication Code (MAC) will have to be implemented together with the Hashing function.
One Way HASH One Way Hash functions operate without any keys. Thus for better security, Message Authentication Code (MAC) will have to be implemented together with the Hashing function.
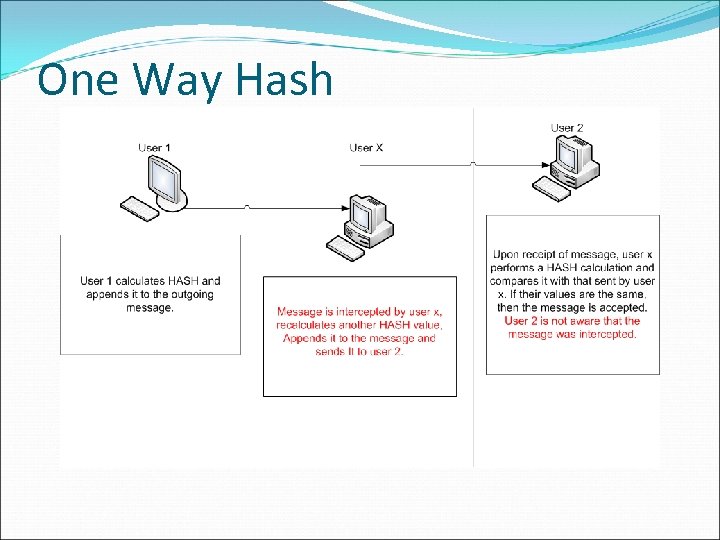 One Way Hash
One Way Hash
 Message Authentication Code (MAC) A MAC function is an authentication scheme derived by applying a secret key to a message in some form (CISSP Certification All in One Exam Guide, pg. 714)
Message Authentication Code (MAC) A MAC function is an authentication scheme derived by applying a secret key to a message in some form (CISSP Certification All in One Exam Guide, pg. 714)
 Message Authentication Code (MAC) Two types of MACs 1. Hash Message Authentication Code (HMAC) 2. Cipher Block Chaining Message Authentication Code(CBC-MAC)
Message Authentication Code (MAC) Two types of MACs 1. Hash Message Authentication Code (HMAC) 2. Cipher Block Chaining Message Authentication Code(CBC-MAC)
 HMAC • The sender concatenates a symmetric key with the message. • The result is put through a hashing algorithm. • A MAC value is generated. • The MAC value is appended to the message.
HMAC • The sender concatenates a symmetric key with the message. • The result is put through a hashing algorithm. • A MAC value is generated. • The MAC value is appended to the message.
 HMAC (con’t) • The sender sends the message to the receiver. (Just the message with the attached MAC value. The sender does not send the symmetric key with the message. ) • The receiver concatenates a symmetric key with the message.
HMAC (con’t) • The sender sends the message to the receiver. (Just the message with the attached MAC value. The sender does not send the symmetric key with the message. ) • The receiver concatenates a symmetric key with the message.
 HMAC (con’t) The receiver puts the results through a hashing algorithm and generates her own MAC value. The receiver compares the two MAC values. If they are the same, the message has not been modified.
HMAC (con’t) The receiver puts the results through a hashing algorithm and generates her own MAC value. The receiver compares the two MAC values. If they are the same, the message has not been modified.
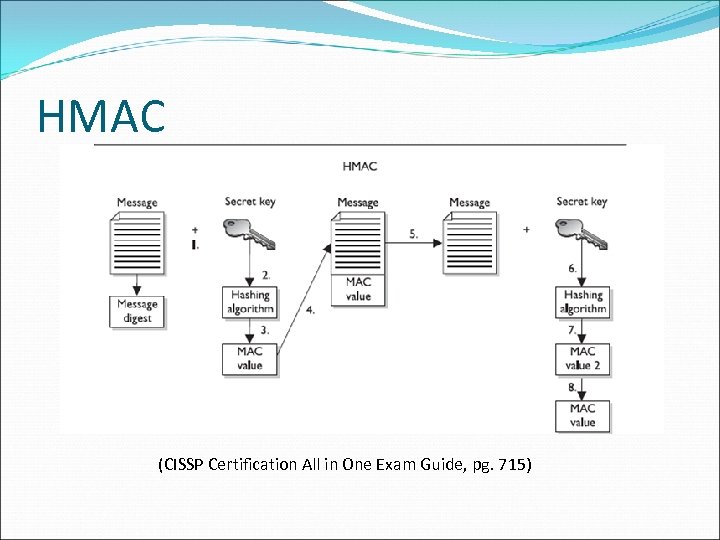 HMAC (CISSP Certification All in One Exam Guide, pg. 715)
HMAC (CISSP Certification All in One Exam Guide, pg. 715)
 CBC-MAC Sender encrypts a message with a symmetric block algorithm in CBC mode. The last block is used as the MAC. The plaintext message and the appended MAC are sent to the receiver. The receiver encrypts the message, creates a new MAC, and compares the two values. If they are the same, the receiver knows the message was not modified and from which system it came.
CBC-MAC Sender encrypts a message with a symmetric block algorithm in CBC mode. The last block is used as the MAC. The plaintext message and the appended MAC are sent to the receiver. The receiver encrypts the message, creates a new MAC, and compares the two values. If they are the same, the receiver knows the message was not modified and from which system it came.
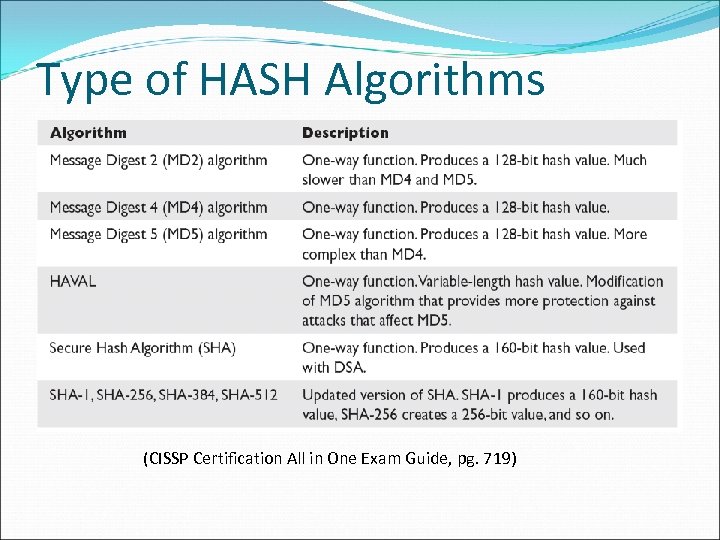 Type of HASH Algorithms (CISSP Certification All in One Exam Guide, pg. 719)
Type of HASH Algorithms (CISSP Certification All in One Exam Guide, pg. 719)
 Type of HASH Algorithms Tiger 1. Was developed in 1995 to operate on 64 bit systems. 2. Faster than MD 5 and SHA-1 3. Produces a HASH value of 192 bits.
Type of HASH Algorithms Tiger 1. Was developed in 1995 to operate on 64 bit systems. 2. Faster than MD 5 and SHA-1 3. Produces a HASH value of 192 bits.
 Attacks Against HASH Functions Birthday Attack
Attacks Against HASH Functions Birthday Attack
 Birthday Attack Collision A scenario where an algorithm produces the same value for two distinctly separate messages. With the birthday attack, an attacker attempts to force a collision. This is done through brute force.
Birthday Attack Collision A scenario where an algorithm produces the same value for two distinctly separate messages. With the birthday attack, an attacker attempts to force a collision. This is done through brute force.
 Characteristics of a good HASH The hash should be computed over the entire message. The hash should be a one-way function so messages are not disclosed by their values. Given a message and its hash value, computing another message with the same hash value should be impossible. The function should be resistant to birthday attacks.
Characteristics of a good HASH The hash should be computed over the entire message. The hash should be a one-way function so messages are not disclosed by their values. Given a message and its hash value, computing another message with the same hash value should be impossible. The function should be resistant to birthday attacks.
 Types of attacks on cryptosystems Cipher-Only Attack In this type of attack, the attacker has the ciphertext of several messages. Each of the messages has been encrypted using the same encryption algorithm. The attacker’s goal is to discover the key used in the encryption process. Once the attacker figures out the key, she can decrypt all other messages encrypted with the same key. This is the most common type of attack.
Types of attacks on cryptosystems Cipher-Only Attack In this type of attack, the attacker has the ciphertext of several messages. Each of the messages has been encrypted using the same encryption algorithm. The attacker’s goal is to discover the key used in the encryption process. Once the attacker figures out the key, she can decrypt all other messages encrypted with the same key. This is the most common type of attack.
 Types of attacks on cryptosystems Known-Plaintext Attacks In known-plaintext attacks, the attacker has the plaintext and ciphertext of one or more messages. Again, the goal is to discover the key used to encrypt the messages so other messages can be deciphered and read.
Types of attacks on cryptosystems Known-Plaintext Attacks In known-plaintext attacks, the attacker has the plaintext and ciphertext of one or more messages. Again, the goal is to discover the key used to encrypt the messages so other messages can be deciphered and read.
 Types of attacks on cryptosystems Chosen-Plaintext Attacks In chosen-plaintext attacks, the attacker has the plaintext and ciphertext, but can choose the plaintext that gets encrypted to see the corresponding ciphertext. This gives the attacker more power and possibly a deeper understanding of the way the encryption process works in order to gather more information about the key being used. Once the key is discovered, other messages encrypted with that key can be decrypted.
Types of attacks on cryptosystems Chosen-Plaintext Attacks In chosen-plaintext attacks, the attacker has the plaintext and ciphertext, but can choose the plaintext that gets encrypted to see the corresponding ciphertext. This gives the attacker more power and possibly a deeper understanding of the way the encryption process works in order to gather more information about the key being used. Once the key is discovered, other messages encrypted with that key can be decrypted.
 Types of attacks on cryptosystems Chosen-Ciphertext Attacks 1. In chosen-ciphertext attacks, the attacker chooses the ciphertext to be decrypted and has access to the resulting decrypted plaintext. 2. The goal is to figure out the key. This is a harder attack to carry out compared to the previously mentioned attacks, and the attacker may need to have control of the system that contains the cryptosystem.
Types of attacks on cryptosystems Chosen-Ciphertext Attacks 1. In chosen-ciphertext attacks, the attacker chooses the ciphertext to be decrypted and has access to the resulting decrypted plaintext. 2. The goal is to figure out the key. This is a harder attack to carry out compared to the previously mentioned attacks, and the attacker may need to have control of the system that contains the cryptosystem.
 Types of attacks on cryptosystems Differential Cryptanalysis The goal of this type of attack is to uncover the key that was used for encryption purposes. The attacker takes two messages of plaintext and follows the changes that take place to the blocks as they go through the different S-boxes. The differences identified in the resulting ciphertext values are used to map probability values to different possible key values.
Types of attacks on cryptosystems Differential Cryptanalysis The goal of this type of attack is to uncover the key that was used for encryption purposes. The attacker takes two messages of plaintext and follows the changes that take place to the blocks as they go through the different S-boxes. The differences identified in the resulting ciphertext values are used to map probability values to different possible key values.
 Public Key Infrastructure
Public Key Infrastructure
 Objective of PKI Confidentiality Keeps information secret Integrity Ensures that the information is not altered Authentication Be sure you know who you are communicating with Non-repudiation Have the evidence in the event of a dispute
Objective of PKI Confidentiality Keeps information secret Integrity Ensures that the information is not altered Authentication Be sure you know who you are communicating with Non-repudiation Have the evidence in the event of a dispute
 The need for PKI Meet Alice. She has a secret that she wants to send to Bob. Meet Bob. He looks forward to talking with his good friend Alice. http: //cups. cmu. edu/courses/ups-sp 06/slides/060418 -PKI. ppt
The need for PKI Meet Alice. She has a secret that she wants to send to Bob. Meet Bob. He looks forward to talking with his good friend Alice. http: //cups. cmu. edu/courses/ups-sp 06/slides/060418 -PKI. ppt
 The need for PKI 10 01 10 • Alice and Bob can use a secret key (symmetric cryptography) to communicate over the public channel. • They must have agreed on this key in advance. http: //cups. cmu. edu/courses/ups-sp 06/slides/060418 -PKI. ppt
The need for PKI 10 01 10 • Alice and Bob can use a secret key (symmetric cryptography) to communicate over the public channel. • They must have agreed on this key in advance. http: //cups. cmu. edu/courses/ups-sp 06/slides/060418 -PKI. ppt
 The need for PKI ? ? erofeb nekops reve ? noitacinummoc . tpp. IKP-814060/sedils/6
The need for PKI ? ? erofeb nekops reve ? noitacinummoc . tpp. IKP-814060/sedils/6
 The need for PKI • Both Alice and Bob have their own individual private and public keys signed by a certificate authority. – The CA might be an employer, Verisign, or some other organization. http: //cups. cmu. edu/courses/ups-sp 06/slides/060418 -PKI. ppt
The need for PKI • Both Alice and Bob have their own individual private and public keys signed by a certificate authority. – The CA might be an employer, Verisign, or some other organization. http: //cups. cmu. edu/courses/ups-sp 06/slides/060418 -PKI. ppt
 Public Key Infrastructure PKI arrangements enable computer users without prior contact to be authenticated to each other, and to use the public key information in their public key certificates to encrypt messages to each other.
Public Key Infrastructure PKI arrangements enable computer users without prior contact to be authenticated to each other, and to use the public key information in their public key certificates to encrypt messages to each other.
 Public Key Infrastructure The PKI includes the following elements: Certificate authority (CA) Digital certificates Registration authorities Certificate revocation
Public Key Infrastructure The PKI includes the following elements: Certificate authority (CA) Digital certificates Registration authorities Certificate revocation
 Certificate Authority An organization that issues digital certificates. Usually a trusted third party The CA also attests that the public key contained in the certificate belongs to the person, organization, server or other entity noted in the certificate.
Certificate Authority An organization that issues digital certificates. Usually a trusted third party The CA also attests that the public key contained in the certificate belongs to the person, organization, server or other entity noted in the certificate.
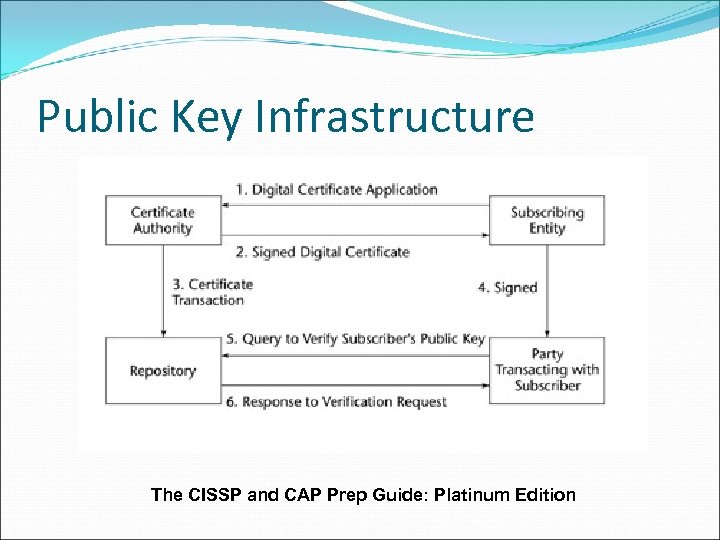 Public Key Infrastructure The CISSP and CAP Prep Guide: Platinum Edition
Public Key Infrastructure The CISSP and CAP Prep Guide: Platinum Edition
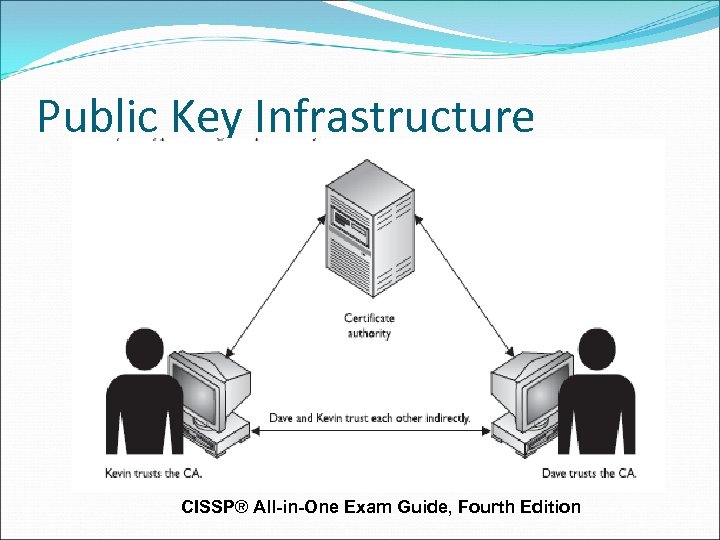 Public Key Infrastructure CISSP® All-in-One Exam Guide, Fourth Edition
Public Key Infrastructure CISSP® All-in-One Exam Guide, Fourth Edition
 Certificate Authority The CA constructs the certificate, signs it, sends it to the requester, and maintains the certificate over its lifetime. The CA can be internal to an organization or an external organization dedicated to this type of service Ex: Veri. Sign.
Certificate Authority The CA constructs the certificate, signs it, sends it to the requester, and maintains the certificate over its lifetime. The CA can be internal to an organization or an external organization dedicated to this type of service Ex: Veri. Sign.
 Certificate Authority The CA is responsible for creating and handing out certificates, maintaining them, and revoking them if necessary.
Certificate Authority The CA is responsible for creating and handing out certificates, maintaining them, and revoking them if necessary.
 Certificate Authority The CA is responsible for creating and handing out certificates, maintaining them, and revoking them if necessary Revocation is handled by the CA and the revoked certificate information is stored on a certificate revocation list (CRL)
Certificate Authority The CA is responsible for creating and handing out certificates, maintaining them, and revoking them if necessary Revocation is handled by the CA and the revoked certificate information is stored on a certificate revocation list (CRL)
 Public Key Infrastructure The PKI includes the following elements: Certificate authority (CA) Digital certificates Registration authorities Certificate revocation
Public Key Infrastructure The PKI includes the following elements: Certificate authority (CA) Digital certificates Registration authorities Certificate revocation
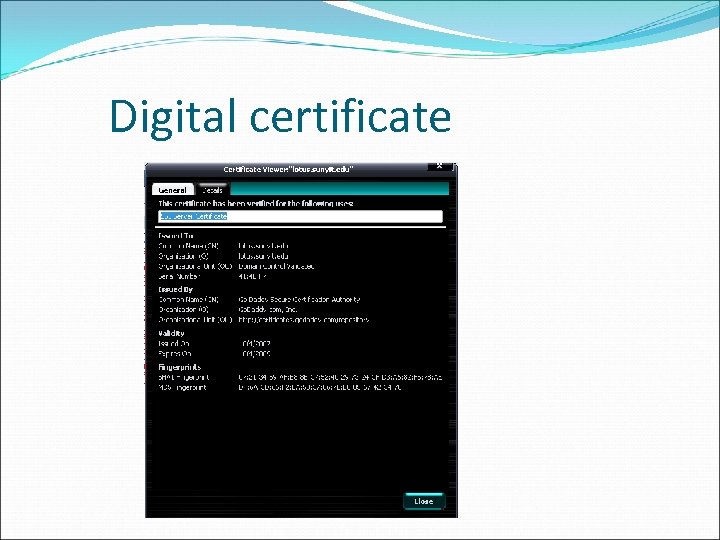
 Digital certificate The digital certificate and management of the certificate are major components of PKI Its purpose is to verify to all that an individual’s public key - posted on a public “key ring” - is actually his.
Digital certificate The digital certificate and management of the certificate are major components of PKI Its purpose is to verify to all that an individual’s public key - posted on a public “key ring” - is actually his.
 Digital certificate It associates a public key with a collection of components that is sufficient to identify the claimed owner. Digital certificates are based on the X. 509, which dictates the different fields used in the certificate
Digital certificate It associates a public key with a collection of components that is sufficient to identify the claimed owner. Digital certificates are based on the X. 509, which dictates the different fields used in the certificate
 Digital certificate
Digital certificate
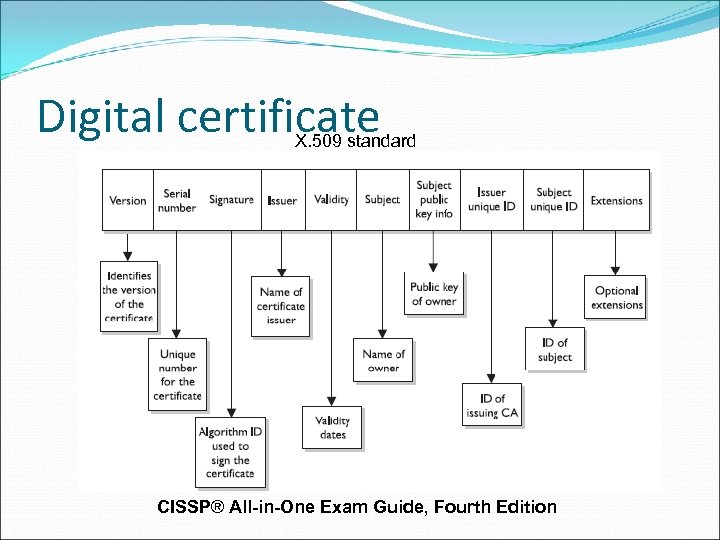
 Digital certificate X. 509 version currently implemented is version 4 denoted as X. 509 v 4 The certificate includes the serial number, version number, identity information, algorithm information, lifetime dates, and the signature of the issuing authority,
Digital certificate X. 509 version currently implemented is version 4 denoted as X. 509 v 4 The certificate includes the serial number, version number, identity information, algorithm information, lifetime dates, and the signature of the issuing authority,
 Digital certificate X. 509 standard CISSP® All-in-One Exam Guide, Fourth Edition
Digital certificate X. 509 standard CISSP® All-in-One Exam Guide, Fourth Edition
 Public Key Infrastructure The PKI includes the following elements: Certificate authority (CA) Digital certificates Registration authorities Certificate revocation
Public Key Infrastructure The PKI includes the following elements: Certificate authority (CA) Digital certificates Registration authorities Certificate revocation
 Registration authorities The RA establishes and confirms the identity of an individual The RA initiates the certification process with a CA on behalf of an end user, and performs certificate lifecycle management functions.
Registration authorities The RA establishes and confirms the identity of an individual The RA initiates the certification process with a CA on behalf of an end user, and performs certificate lifecycle management functions.
 Registration authorities The RA cannot issue certificates, but can act as a broker between the user and the CA. When users need new certificates, they make requests to the RA who verifies all necessary identification information before allowing a request to go to the CA
Registration authorities The RA cannot issue certificates, but can act as a broker between the user and the CA. When users need new certificates, they make requests to the RA who verifies all necessary identification information before allowing a request to go to the CA
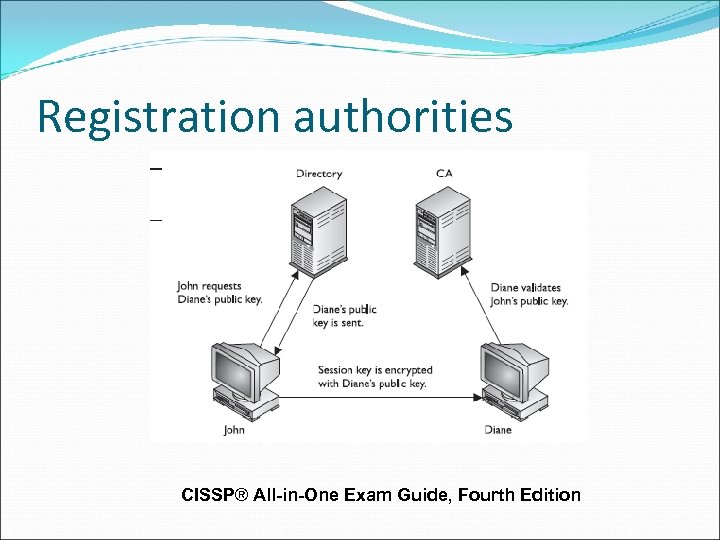 Registration authorities CISSP® All-in-One Exam Guide, Fourth Edition
Registration authorities CISSP® All-in-One Exam Guide, Fourth Edition
 Public Key Infrastructure The PKI includes the following elements: Certificate authority (CA) Digital certificates Registration authorities Certificate revocation
Public Key Infrastructure The PKI includes the following elements: Certificate authority (CA) Digital certificates Registration authorities Certificate revocation
 Certificate revocation Revocation is handled by the CA and the revoked certificate information is stored on a certificate revocation list (CRL). They check for the serial number of the signature. The CA signs the CRL for integrity and authentication purposes.
Certificate revocation Revocation is handled by the CA and the revoked certificate information is stored on a certificate revocation list (CRL). They check for the serial number of the signature. The CA signs the CRL for integrity and authentication purposes.
 Certification revocation list CISSP® All-in-One Exam Guide, Fourth Edition
Certification revocation list CISSP® All-in-One Exam Guide, Fourth Edition
 Rules for key management (cont. ) Rules for Keys and Key Management The key length should be long enough to provide the necessary level of protection. Keys should be stored and transmitted by secure means. Keys should be extremely random and the algorithm should use the full spectrum of the keyspace.
Rules for key management (cont. ) Rules for Keys and Key Management The key length should be long enough to provide the necessary level of protection. Keys should be stored and transmitted by secure means. Keys should be extremely random and the algorithm should use the full spectrum of the keyspace.
 Rules for key management (cont. ) The key’s lifetime should correspond with the sensitivity of the data it is protecting. (Less secure data may allow for a longer key lifetime, whereas more sensitive data might require a shorter key lifetime. )
Rules for key management (cont. ) The key’s lifetime should correspond with the sensitivity of the data it is protecting. (Less secure data may allow for a longer key lifetime, whereas more sensitive data might require a shorter key lifetime. )
 Rules for key management (cont. ) The more the key is used, the shorter its lifetime should be. Keys should be backed up or escrowed in case of emergencies. Keys should be properly destroyed when their lifetime comes to an end.
Rules for key management (cont. ) The more the key is used, the shorter its lifetime should be. Keys should be backed up or escrowed in case of emergencies. Keys should be properly destroyed when their lifetime comes to an end.
 Conclusion Information security Cryptography Security
Conclusion Information security Cryptography Security
 References http: //en. wikipedia. org/wiki/Encryption CISSP® All-in-One Exam Guide, Fourth Edition Computer Networks, Fourth Edition http: //cups. cmu. edu/courses/ups-sp 06/slides/060418 -PKI. ppt The CISSP and CAP Prep Guide: Platinum Edition www. fim. unilinz. ac. at/lva/Informatikonzepte_im_E_Business/ws 2004/Cryptogra phy. pdf
References http: //en. wikipedia. org/wiki/Encryption CISSP® All-in-One Exam Guide, Fourth Edition Computer Networks, Fourth Edition http: //cups. cmu. edu/courses/ups-sp 06/slides/060418 -PKI. ppt The CISSP and CAP Prep Guide: Platinum Edition www. fim. unilinz. ac. at/lva/Informatikonzepte_im_E_Business/ws 2004/Cryptogra phy. pdf


