cbd431fbd9966f69ea9a8f457a62249a.ppt
- Количество слайдов: 50
 CRYPTOGRAPHY: STATE OF THE SCIENCE ASIACRYPT 2003 invited talk Adi Shamir Computer Science Dept The Weizmann Institute Israel
CRYPTOGRAPHY: STATE OF THE SCIENCE ASIACRYPT 2003 invited talk Adi Shamir Computer Science Dept The Weizmann Institute Israel
 Cryptography: major trends
Cryptography: major trends
 Cryptography: major trends u From secret to public
Cryptography: major trends u From secret to public
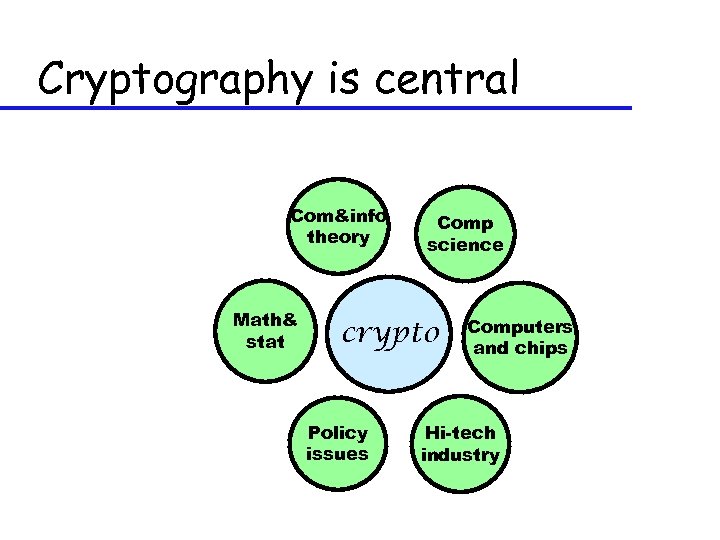 Cryptography is central Com&info theory Math& stat Comp science crypto Policy issues Computers and chips Hi-tech industry
Cryptography is central Com&info theory Math& stat Comp science crypto Policy issues Computers and chips Hi-tech industry
 Cryptography is fun u Gets lots of media attention u Attracts hackers u Is full of delightful ideas u Serves as an excellent educational tool
Cryptography is fun u Gets lots of media attention u Attracts hackers u Is full of delightful ideas u Serves as an excellent educational tool
 Cryptography: major trends u From secret to public u From national to international
Cryptography: major trends u From secret to public u From national to international
 The geography of cryptography u Publicly started in the US
The geography of cryptography u Publicly started in the US
 The geography of cryptography u Publicly started in the US u Followed by Europe
The geography of cryptography u Publicly started in the US u Followed by Europe
 The geography of cryptography u Publicly started in the US u Followed by Europe u Is rapidly expanding in Asia
The geography of cryptography u Publicly started in the US u Followed by Europe u Is rapidly expanding in Asia
 Cryptography: major trends u From secret to public u From national to international u From art to science
Cryptography: major trends u From secret to public u From national to international u From art to science
 Cryptography as a scientific discipline Is thriving as a scientific area of research: u u u Taught at most major universities Attracts many excellent students Discussed at many conferences (>25 in the next 6 months!) Published in hundreds of papers (e. g. , EPRINT) Major conferences have >500 attendees (Major trade shows have >10, 000 attendees) Received the ultimate seal of approval from the general CS community (the Turing award…)
Cryptography as a scientific discipline Is thriving as a scientific area of research: u u u Taught at most major universities Attracts many excellent students Discussed at many conferences (>25 in the next 6 months!) Published in hundreds of papers (e. g. , EPRINT) Major conferences have >500 attendees (Major trade shows have >10, 000 attendees) Received the ultimate seal of approval from the general CS community (the Turing award…)
 Should we rename the field? u u Cryptography means “secret writing” The official naming of the field: Cryptology = Cryptography + cryptanalysis
Should we rename the field? u u Cryptography means “secret writing” The official naming of the field: Cryptology = Cryptography + cryptanalysis
 Should we rename the field? u u Cryptography means “secret writing” The official naming of the field: Cryptology = Cryptography + cryptanalysis These terms have problematic conotations Many research subfields do not deal with the encryption or decryption of secret information
Should we rename the field? u u Cryptography means “secret writing” The official naming of the field: Cryptology = Cryptography + cryptanalysis These terms have problematic conotations Many research subfields do not deal with the encryption or decryption of secret information
 Should we rename the field? u u Cryptography means “secret writing” The official naming of the field: Cryptology = Cryptography + cryptanalysis u These terms have problematic conotations u Many research subfields do not deal with the encryption or decryption of secret information u I propose to call the broader field Adversity Theory = cryptology + other areas
Should we rename the field? u u Cryptography means “secret writing” The official naming of the field: Cryptology = Cryptography + cryptanalysis u These terms have problematic conotations u Many research subfields do not deal with the encryption or decryption of secret information u I propose to call the broader field Adversity Theory = cryptology + other areas
 Cryptography: major trends u From secret to public u From national to international u From art to science u From math to physics
Cryptography: major trends u From secret to public u From national to international u From art to science u From math to physics
 Related scientific fields: u OLD COMBINATIONS: u Probability and statistics u Algebra u Number Theory
Related scientific fields: u OLD COMBINATIONS: u Probability and statistics u Algebra u Number Theory
 Related scientific fields: u OLD COMBINATIONS: u Probability and statistics u Algebra u Number Theory u NEW COMBINATIONS: u Signal processing (in steg, fingerprinting) u Electronics (in side channel attacks) u Physics (in quantum computers and crypto)
Related scientific fields: u OLD COMBINATIONS: u Probability and statistics u Algebra u Number Theory u NEW COMBINATIONS: u Signal processing (in steg, fingerprinting) u Electronics (in side channel attacks) u Physics (in quantum computers and crypto)
 Cryptography: major trends u From secret to public u From national to international u From art to science u From math to physics u From theory to practice
Cryptography: major trends u From secret to public u From national to international u From art to science u From math to physics u From theory to practice
 Cryptography unites Theory & practice u u Practical theory: - using abstract math tools in cryptanalysis - proving the security of real protocols -developing new cryptographic schemes Theoretical practice: - developing new notions of security, complexity, logics, and randomness - turning cryptography from art to science
Cryptography unites Theory & practice u u Practical theory: - using abstract math tools in cryptanalysis - proving the security of real protocols -developing new cryptographic schemes Theoretical practice: - developing new notions of security, complexity, logics, and randomness - turning cryptography from art to science
 New challenges in cryptography u Payment systems u Cellular telephony u Wi-Fi networks u RFID tags u DRM systems
New challenges in cryptography u Payment systems u Cellular telephony u Wi-Fi networks u RFID tags u DRM systems
 Cryptography: major trends u From secret to public u From national to international u From art to science u From math to physics u From theory to practice u From political to legal issues
Cryptography: major trends u From secret to public u From national to international u From art to science u From math to physics u From theory to practice u From political to legal issues
 Cryptographic misconceptions u u u By policy makers: crypto is dangerous, but: - weak crypto is not a solution - controls can’t stop the inevitable By researchers: A provably secure system is secure, but: - proven false by indirect attacks - can be based on false assumptions - requires careful choice of parameters By implementers: Cryptography solves everything, but: - only basic ideas are successfully deployed - only simple attacks are avoided - bad crypto can provide a false sense of security
Cryptographic misconceptions u u u By policy makers: crypto is dangerous, but: - weak crypto is not a solution - controls can’t stop the inevitable By researchers: A provably secure system is secure, but: - proven false by indirect attacks - can be based on false assumptions - requires careful choice of parameters By implementers: Cryptography solves everything, but: - only basic ideas are successfully deployed - only simple attacks are avoided - bad crypto can provide a false sense of security
 The three laws of security: u Absolutely secure systems do not exist u To halve your vulnerability, you have to double your expenditure u Cryptography penetrated is typically bypassed, not
The three laws of security: u Absolutely secure systems do not exist u To halve your vulnerability, you have to double your expenditure u Cryptography penetrated is typically bypassed, not
 Cryptography: A rapidly moving field
Cryptography: A rapidly moving field
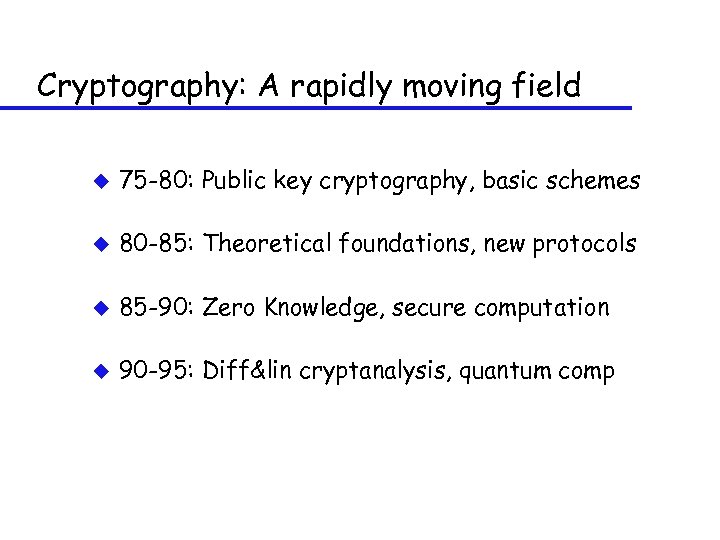
 Cryptography: A rapidly moving field u 75 -80: Public key cryptography, basic schemes
Cryptography: A rapidly moving field u 75 -80: Public key cryptography, basic schemes
 Cryptography: A rapidly moving field u 75 -80: Public key cryptography, basic schemes u 80 -85: Theoretical foundations, new protocols
Cryptography: A rapidly moving field u 75 -80: Public key cryptography, basic schemes u 80 -85: Theoretical foundations, new protocols
 Cryptography: A rapidly moving field u 75 -80: Public key cryptography, basic schemes u 80 -85: Theoretical foundations, new protocols u 85 -90: Zero Knowledge, secure computation
Cryptography: A rapidly moving field u 75 -80: Public key cryptography, basic schemes u 80 -85: Theoretical foundations, new protocols u 85 -90: Zero Knowledge, secure computation
 Cryptography: A rapidly moving field u 75 -80: Public key cryptography, basic schemes u 80 -85: Theoretical foundations, new protocols u 85 -90: Zero Knowledge, secure computation u 90 -95: Diff&lin cryptanalysis, quantum comp
Cryptography: A rapidly moving field u 75 -80: Public key cryptography, basic schemes u 80 -85: Theoretical foundations, new protocols u 85 -90: Zero Knowledge, secure computation u 90 -95: Diff&lin cryptanalysis, quantum comp
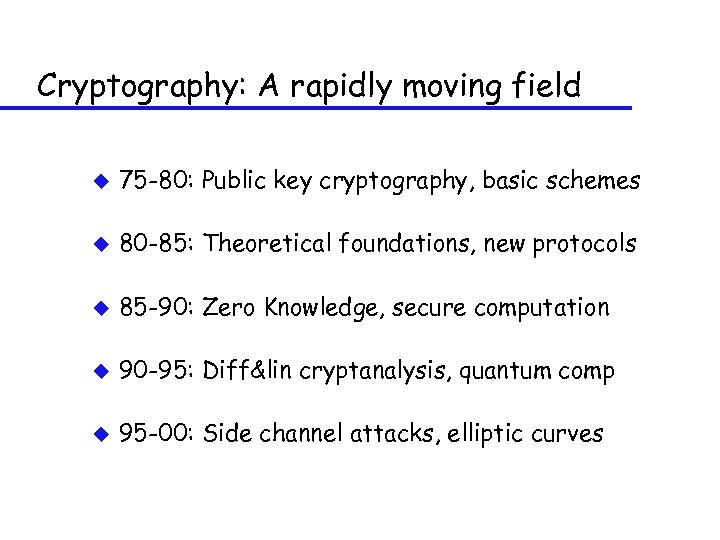 Cryptography: A rapidly moving field u 75 -80: Public key cryptography, basic schemes u 80 -85: Theoretical foundations, new protocols u 85 -90: Zero Knowledge, secure computation u 90 -95: Diff&lin cryptanalysis, quantum comp u 95 -00: Side channel attacks, elliptic curves
Cryptography: A rapidly moving field u 75 -80: Public key cryptography, basic schemes u 80 -85: Theoretical foundations, new protocols u 85 -90: Zero Knowledge, secure computation u 90 -95: Diff&lin cryptanalysis, quantum comp u 95 -00: Side channel attacks, elliptic curves
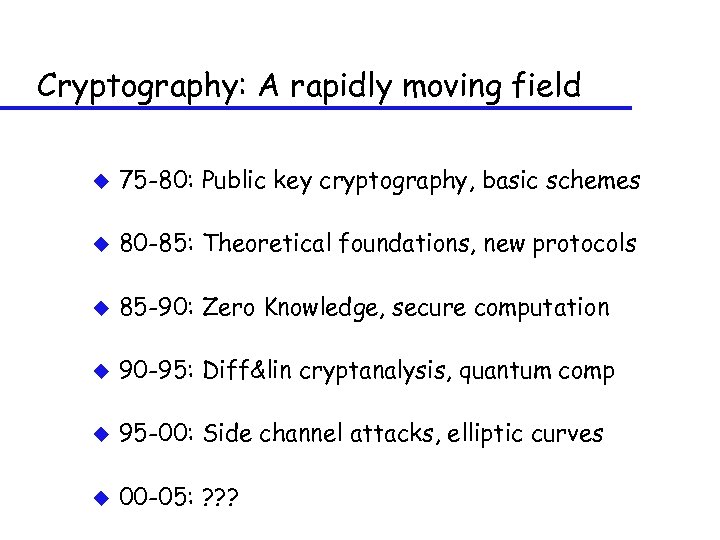 Cryptography: A rapidly moving field u 75 -80: Public key cryptography, basic schemes u 80 -85: Theoretical foundations, new protocols u 85 -90: Zero Knowledge, secure computation u 90 -95: Diff&lin cryptanalysis, quantum comp u 95 -00: Side channel attacks, elliptic curves u 00 -05: ? ? ?
Cryptography: A rapidly moving field u 75 -80: Public key cryptography, basic schemes u 80 -85: Theoretical foundations, new protocols u 85 -90: Zero Knowledge, secure computation u 90 -95: Diff&lin cryptanalysis, quantum comp u 95 -00: Side channel attacks, elliptic curves u 00 -05: ? ? ?
 The basic schemes: Major trends
The basic schemes: Major trends
 The basic schemes: Major trends u Secret key cryptography: DES out, AES in
The basic schemes: Major trends u Secret key cryptography: DES out, AES in
 The basic schemes: Major trends u u Secret key cryptography: DES out, AES in Public key cryptography: RSA steady, EC improving, faster schemes increasingly risky and less appealing. Should not be used for long term security.
The basic schemes: Major trends u u Secret key cryptography: DES out, AES in Public key cryptography: RSA steady, EC improving, faster schemes increasingly risky and less appealing. Should not be used for long term security.
 The basic schemes: Major trends u u u Secret key cryptography: DES out, AES in Public key cryptography: RSA steady, EC improving, faster schemes increasingly risky and less appealing. Should not be used for long term security. Quantum schemes: the wild card
The basic schemes: Major trends u u u Secret key cryptography: DES out, AES in Public key cryptography: RSA steady, EC improving, faster schemes increasingly risky and less appealing. Should not be used for long term security. Quantum schemes: the wild card
 Some of my controvertial positions:
Some of my controvertial positions:
 Some of my controvertial positions: When applied in practice:
Some of my controvertial positions: When applied in practice:
 Some of my controvertial positions: When applied in practice: u Security should not be overdone
Some of my controvertial positions: When applied in practice: u Security should not be overdone
 Some of my controvertial positions: When applied in practice: u Security should not be overdone u Security should not be overexposed
Some of my controvertial positions: When applied in practice: u Security should not be overdone u Security should not be overexposed
 Some of my controvertial positions: When applied in practice: u Security should not be overdone u Security should not be overexposed u Security should not be underregulated
Some of my controvertial positions: When applied in practice: u Security should not be overdone u Security should not be overexposed u Security should not be underregulated
 Some of my controvertial positions: When applied in practice: u Security should not be overdone u Security should not be overexposed u Security should not be underregulated u Security should be guided by an ethical code
Some of my controvertial positions: When applied in practice: u Security should not be overdone u Security should not be overexposed u Security should not be underregulated u Security should be guided by an ethical code
 Some of my controvertial positions: When applied in practice: u Security should not be overdone u Security should not be overexposed u Security should not be underregulated u Security should be guided by an ethical code u Security should be complemented by legal measures
Some of my controvertial positions: When applied in practice: u Security should not be overdone u Security should not be overexposed u Security should not be underregulated u Security should be guided by an ethical code u Security should be complemented by legal measures
 Cryptographic status report In each of the six major subareas I’ll summarize: u The major achievements so far u Strong and weak points, major challenges u A 1 -10 grade
Cryptographic status report In each of the six major subareas I’ll summarize: u The major achievements so far u Strong and weak points, major challenges u A 1 -10 grade
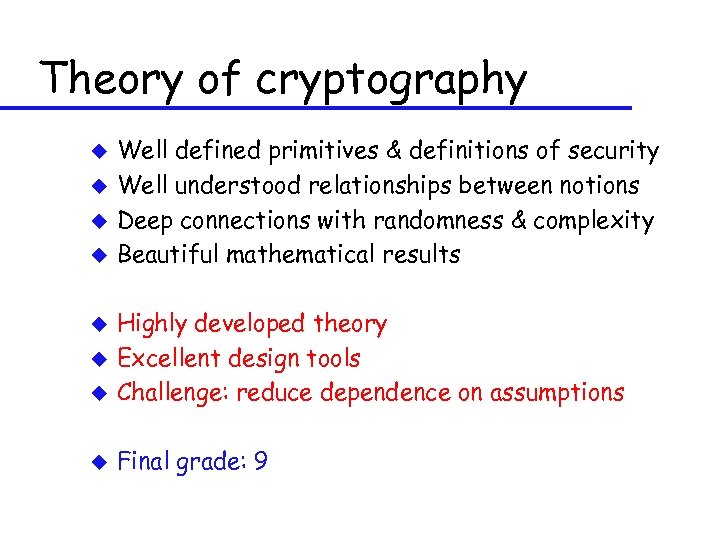 Theory of cryptography u u Well defined primitives & definitions of security Well understood relationships between notions Deep connections with randomness & complexity Beautiful mathematical results u Highly developed theory Excellent design tools Challenge: reduce dependence on assumptions u Final grade: 9 u u
Theory of cryptography u u Well defined primitives & definitions of security Well understood relationships between notions Deep connections with randomness & complexity Beautiful mathematical results u Highly developed theory Excellent design tools Challenge: reduce dependence on assumptions u Final grade: 9 u u
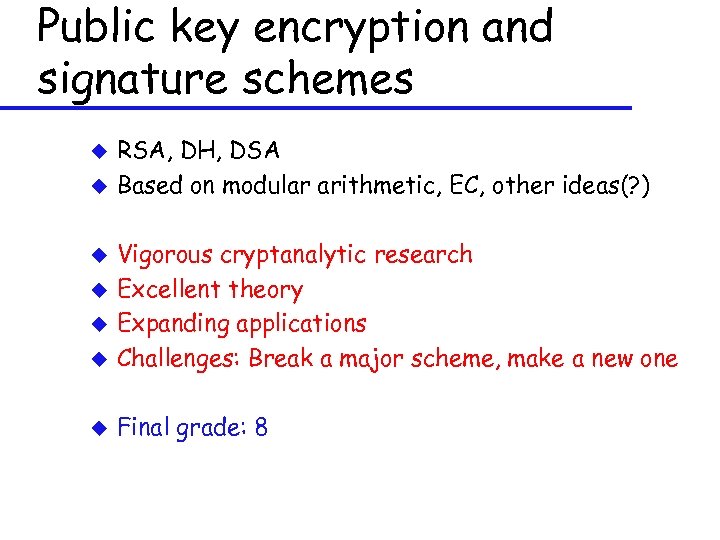 Public key encryption and signature schemes u u RSA, DH, DSA Based on modular arithmetic, EC, other ideas(? ) u Vigorous cryptanalytic research Excellent theory Expanding applications Challenges: Break a major scheme, make a new one u Final grade: 8 u u u
Public key encryption and signature schemes u u RSA, DH, DSA Based on modular arithmetic, EC, other ideas(? ) u Vigorous cryptanalytic research Excellent theory Expanding applications Challenges: Break a major scheme, make a new one u Final grade: 8 u u u
 Secret key cryptography – block ciphers u u DES, AES, modes of operation Differential and linear cryptanalysis u Good cryptanalytic tools Reasonable choice of primitives Many good schemes Challenge: Connect strong theory with strong practice u Final grade: 7 u u u
Secret key cryptography – block ciphers u u DES, AES, modes of operation Differential and linear cryptanalysis u Good cryptanalytic tools Reasonable choice of primitives Many good schemes Challenge: Connect strong theory with strong practice u Final grade: 7 u u u
 Secret key cryptography – stream ciphers u u Linear feedback shift registers Fast correlation attacks, algebraic attacks u Limited cryptanalytic tools Narrow choice of primitives Many insecure schemes Challenge: Improve weak theory and weak practice u Final grade: 4 u u u
Secret key cryptography – stream ciphers u u Linear feedback shift registers Fast correlation attacks, algebraic attacks u Limited cryptanalytic tools Narrow choice of primitives Many insecure schemes Challenge: Improve weak theory and weak practice u Final grade: 4 u u u
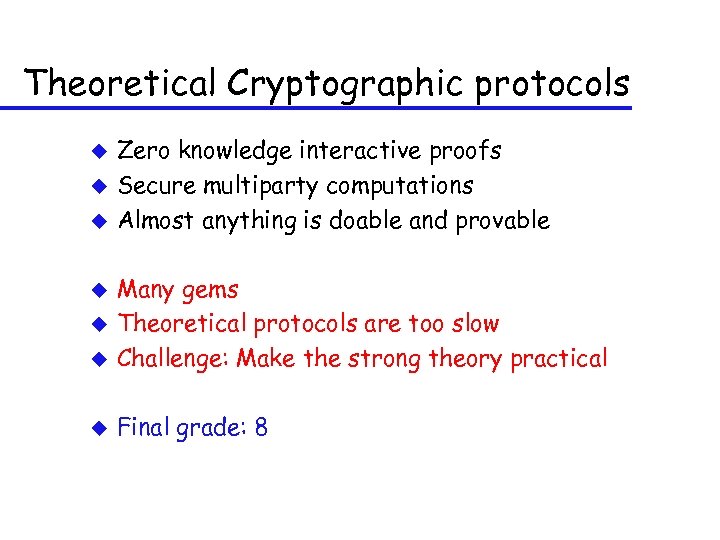 Theoretical Cryptographic protocols u u u Zero knowledge interactive proofs Secure multiparty computations Almost anything is doable and provable u Many gems Theoretical protocols are too slow Challenge: Make the strong theory practical u Final grade: 8 u u
Theoretical Cryptographic protocols u u u Zero knowledge interactive proofs Secure multiparty computations Almost anything is doable and provable u Many gems Theoretical protocols are too slow Challenge: Make the strong theory practical u Final grade: 8 u u
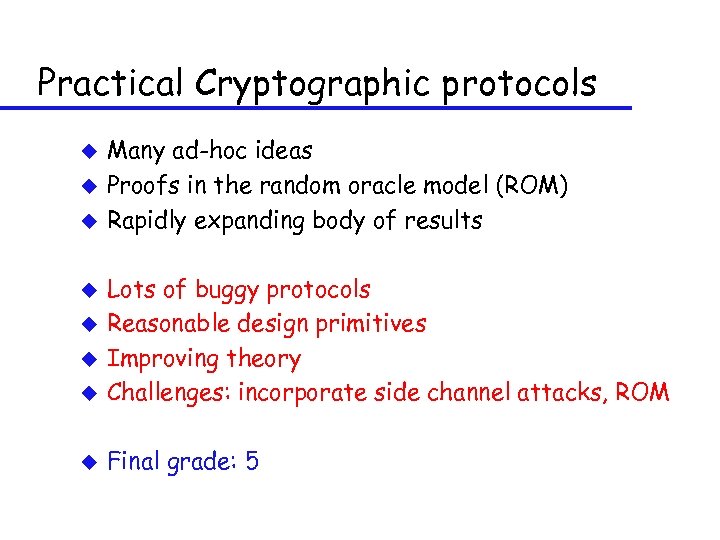 Practical Cryptographic protocols u u u Many ad-hoc ideas Proofs in the random oracle model (ROM) Rapidly expanding body of results u Lots of buggy protocols Reasonable design primitives Improving theory Challenges: incorporate side channel attacks, ROM u Final grade: 5 u u u
Practical Cryptographic protocols u u u Many ad-hoc ideas Proofs in the random oracle model (ROM) Rapidly expanding body of results u Lots of buggy protocols Reasonable design primitives Improving theory Challenges: incorporate side channel attacks, ROM u Final grade: 5 u u u
 Cryptographic predictions: u u u AES will remain secure for the forseeable future Some PK schemes and key sizes will be successfully attacked in the next few years Crypto will be invisibly everywhere Vulnerabilities will be visibly everywhere Crypto research will remain vigorous, but only its simplest ideas will become practically useful Non-crypto security will remain a mess
Cryptographic predictions: u u u AES will remain secure for the forseeable future Some PK schemes and key sizes will be successfully attacked in the next few years Crypto will be invisibly everywhere Vulnerabilities will be visibly everywhere Crypto research will remain vigorous, but only its simplest ideas will become practically useful Non-crypto security will remain a mess
 Summary u It was a thrilling 25 year journey u The best is yet to come u Thanks to everyone!
Summary u It was a thrilling 25 year journey u The best is yet to come u Thanks to everyone!


