e58ee59e796ff331a9320984a6fa9b4f.ppt
- Количество слайдов: 53

Cryptography Purpose: to protect transmitted information from being read or altered by non authorized subjects 1

Definitions Cipher – transformation program Ciphertext – translated message Block Cipher – message transformed into blocks then enciphered XOR – binary translation Key – info that controls encipherment Plaintext – clear text message Steganography – message in pictures or other binary forms 2
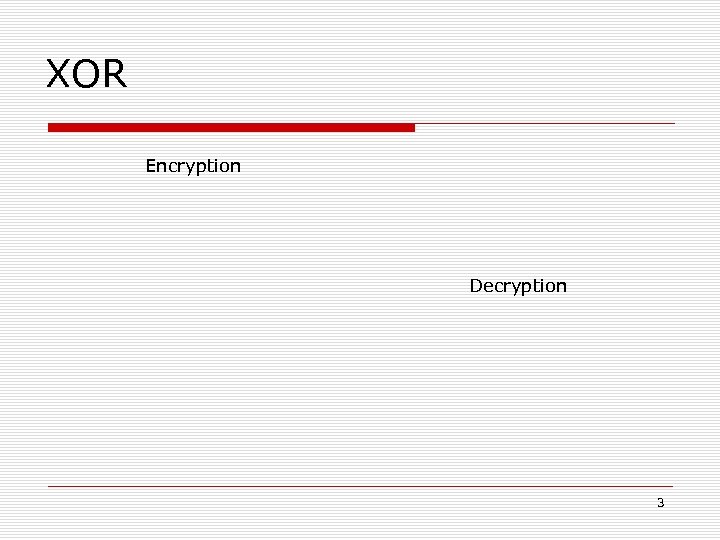
XOR Encryption Decryption 3
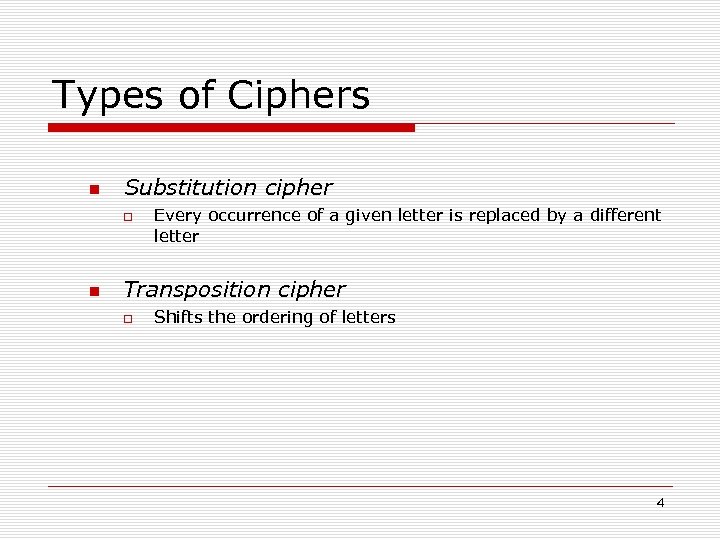
Types of Ciphers Substitution cipher Every occurrence of a given letter is replaced by a different letter Transposition cipher Shifts the ordering of letters 4

History of Cryptosystems Cryptography Secures information by encrypting it Early instances 3000 BC hieroglyphics 50 BC Julius Caesar: Substitution Cipher (C 3) 400 BC Spartans: text on a stick 1523 Polyalphabetic substitution cipher More Modern cryptosystems Vernam or One-time pad cypher Book cypher Codes (526 = Attack at Dawn) 5
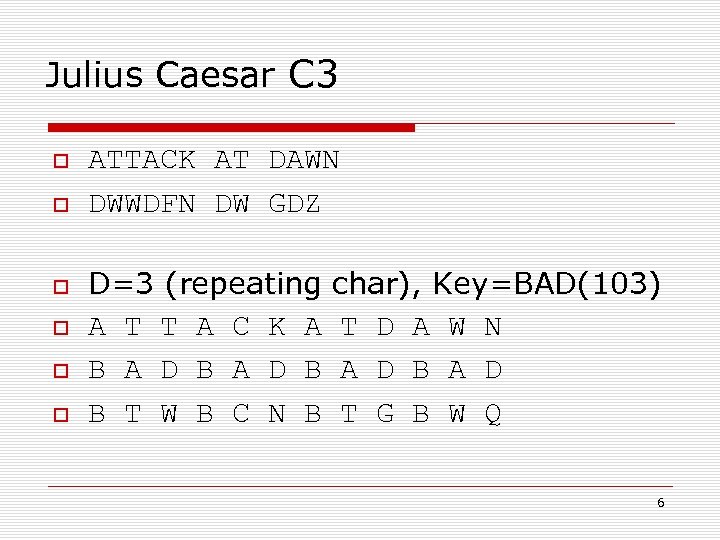
Julius Caesar C 3 ATTACK AT DAWN DWWDFN DW GDZ D=3 (repeating A T T A C K A B A D B B T W B C N B char), Key=BAD(103) T D A W N A D B A D T G B W Q 6
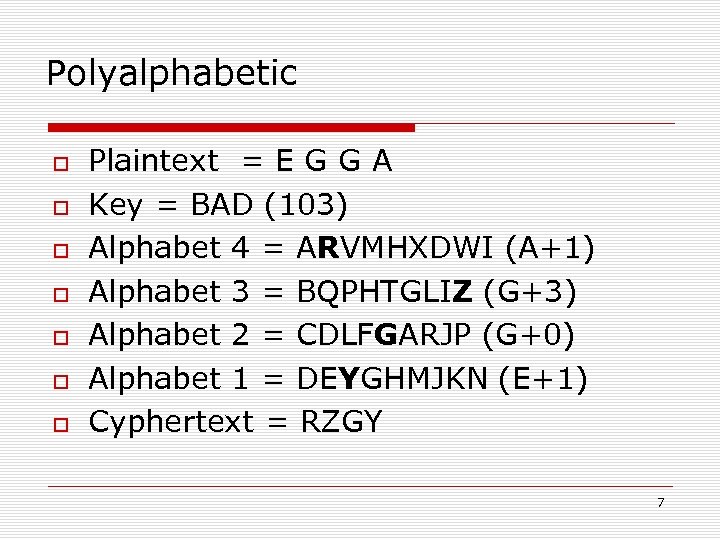
Polyalphabetic Plaintext = E G G A Key = BAD (103) Alphabet 4 = ARVMHXDWI (A+1) Alphabet 3 = BQPHTGLIZ (G+3) Alphabet 2 = CDLFGARJP (G+0) Alphabet 1 = DEYGHMJKN (E+1) Cyphertext = RZGY 7
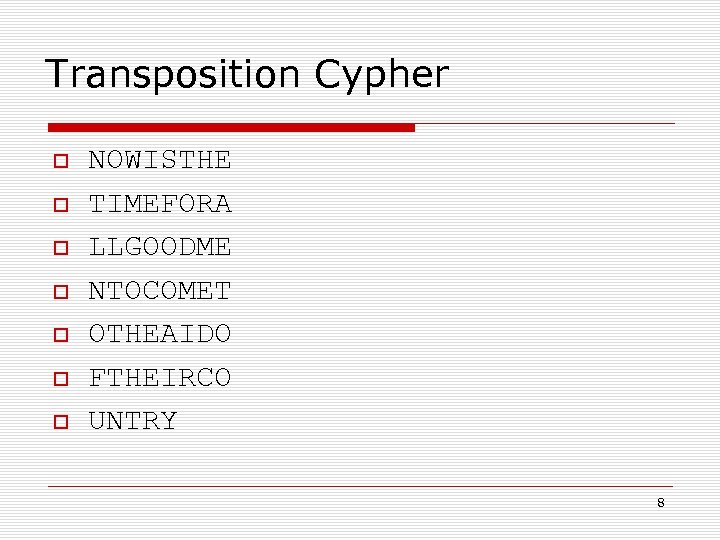
Transposition Cypher NOWISTHE TIMEFORA LLGOODME NTOCOMET OTHEAIDO FTHEIRCO UNTRY 8
Outline of Encryption Secret-key encryption Public-key encryption Digital signature Digital certificate Certificate authority Key Agreement Protocols Key Management 9
Encryption Methods The essential technology underlying virtually all automated network and computer security applications is cryptography Two fundamental approaches are in use: conventional encryption, also known as symmetric encryption public-key encryption, also known as asymmetric encryption 10

Secret-key Encryption Secret-key cryptography Same key to encrypt and decrypt message Sender sends message and key to receiver Problems with secret-key cryptography Key must be transmitted to receiver Different key for every receiver Key distribution centers used to reduce these problems Generates session key and sends it to sender and receiver encrypted with the unique key Encryption algorithms Dunn Encryption Standard (DES), Triple DES, Advanced Encryption Standard (AES) 11
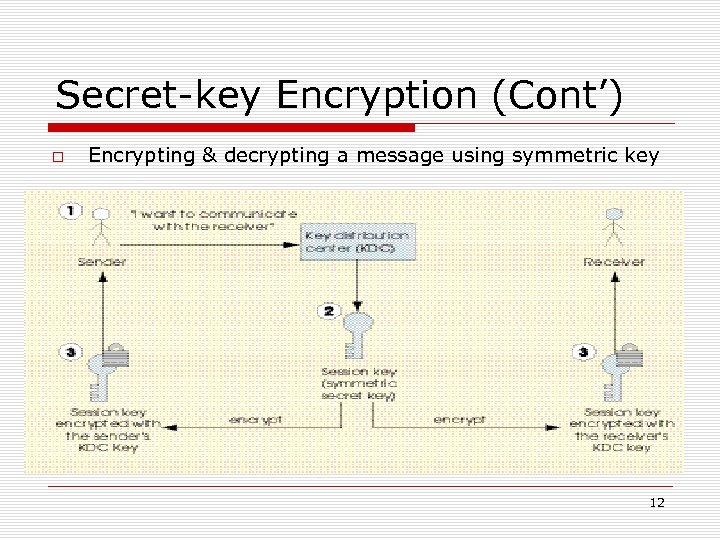
Secret-key Encryption (Cont’) Encrypting & decrypting a message using symmetric key 12

Public Key Encryption Asymmetric, involving the use of two separate keys Based on mathematical “one-way” functions rather than on simple operations on bit patterns Misconceptions about public key encryption it is more secure from cryptanalysis it is a general-purpose technique that has made conventional encryption obsolete Trap doors ? 13
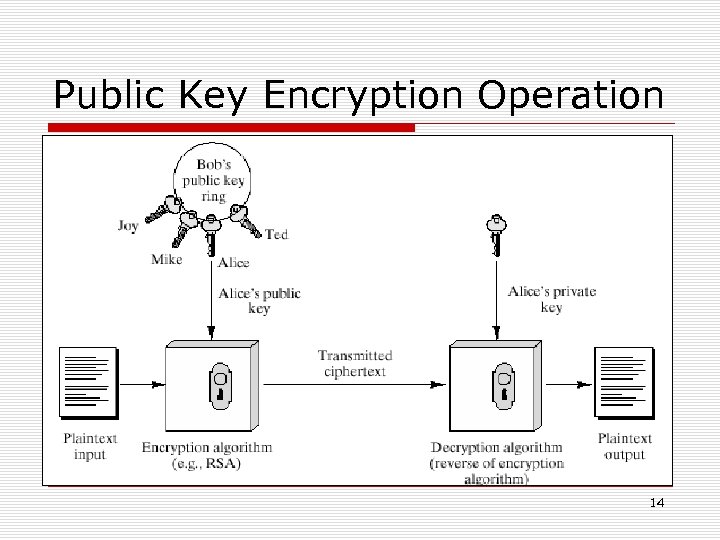
Public Key Encryption Operation 14
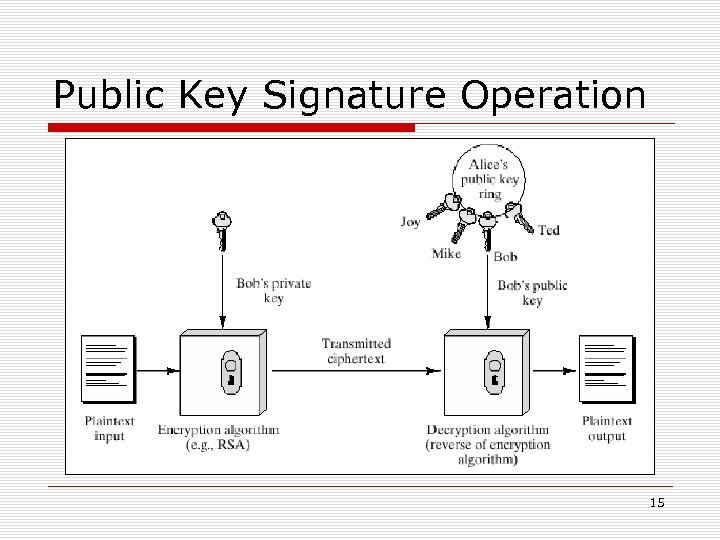
Public Key Signature Operation 15
Characteristics of Public-Key Infeasible to determine the decryption key given knowledge of the cryptographic algorithm and the encryption key. Either of the two related keys can be used for encryption, with the other used for decryption. Slow, but provides tremendous flexibility to perform a number of security-related functions Most widely used algorithm is RSA http: //www. rsasecurity. com/, invented by Ron Rivest, Adi Shamir and Len Adleman at MIT in 1977. Based on factoring of large number that is the product of two prime numbers (the keys) 16
Asymmetric - Symmetric Asymmetric (public key) cryptography is 1000 to 10000 times slower than symmetric 17

Conventional Encryption Key Distribution Both parties must have the secret key Key should be changed frequently Requires either manual delivery of keys, or a third-party encrypted channel Most effective method is a Key Distribution Center (e. g. Kerberos) 18

Public-Key Encryption Key Distribution 1. 2. 3. 4. Parties create a pair of keys; public key is broadly distributed, private key is not To reduce computational overhead, the following process is then used: Prepare a message. Encrypt that message using conventional encryption with a one-time conventional session key. Encrypt the session key using public-key encryption with recipient’s public key. Attach the encrypted session key to the message and send it. 19

Digital Signature An electronic message that can be used by someone to authenticate the identity of the sender of a message or of the signer of a document. Can also be used to ensure that the original content of the message or document that has been conveyed is unchanged. Additional benefits: Easy transportation, not easily repudiated, not imitated by someone else, and automatically timestamped. Hash algorithms: Digital Signature Standard (DSS), Secure Hash Standard (SHS), MD 5 20
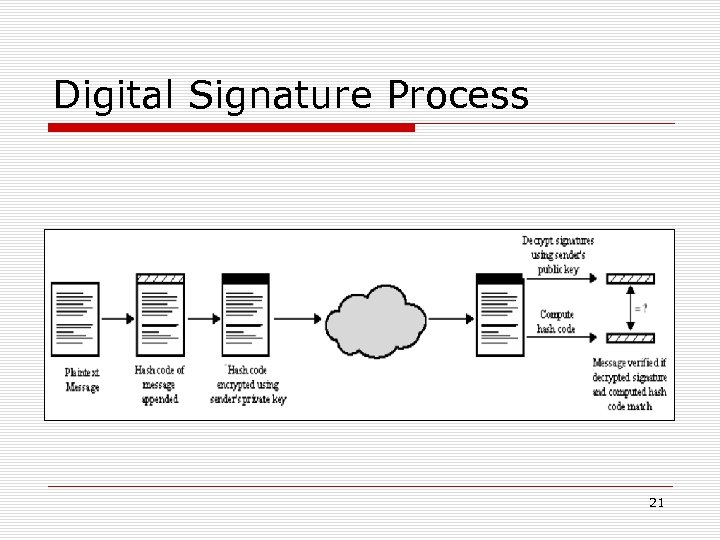
Digital Signature Process 21

Public Key Certificates 1. A public key is generated by the user and submitted to Agency X for certification. 2. X determines by some procedure, such as a face-toface meeting, that this is authentically the user’s public key. 3. X appends a timestamp to the public key, generates the hash code of the result, and encrypts that result with X’s private key forming the signature. 4. The signature is attached to the public key. 22
X. 500 Standard & X. 509 Certificates LDAP uses Directories store Names, addresses, phone numbers, public key certificates X. 509 Certificate format <--link 23
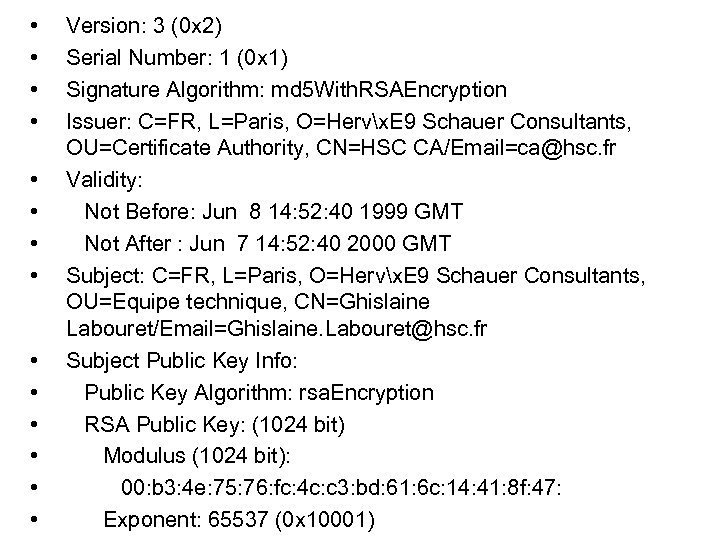
• • • • Version: 3 (0 x 2) Serial Number: 1 (0 x 1) Signature Algorithm: md 5 With. RSAEncryption Issuer: C=FR, L=Paris, O=Hervx. E 9 Schauer Consultants, OU=Certificate Authority, CN=HSC CA/Email=ca@hsc. fr Validity: Not Before: Jun 8 14: 52: 40 1999 GMT Not After : Jun 7 14: 52: 40 2000 GMT Subject: C=FR, L=Paris, O=Hervx. E 9 Schauer Consultants, OU=Equipe technique, CN=Ghislaine Labouret/Email=Ghislaine. Labouret@hsc. fr Subject Public Key Info: Public Key Algorithm: rsa. Encryption RSA Public Key: (1024 bit) Modulus (1024 bit): 00: b 3: 4 e: 75: 76: fc: 4 c: c 3: bd: 61: 6 c: 14: 41: 8 f: 47: Exponent: 65537 (0 x 10001)

LDAP • To simplify the overhead needed to provide secure directory services based on X. 500 • Relevant RFCs: – 2252 - LDAP framework – 2256 – User schema for LDAPv 3 – 1274, 2079, 2247, 2307, 2589 Specs for user attributes, URIs, NIS, PKI, etc • LDAP Schema: Object classes Attributes

Certificate Authority A certificate authority is a trusted organization that can vouch for the authenticity of the person or organization using authentication. A person wanting to use a CA registers with the CA and must provide some proof of identify. The CA issues a digital certificate that is the requester's public key encrypted using the CA's private key as proof of identify. This certificate is then attached to the user's email or Web transactions in addition to the authentication information. The receiver then verifies the certificate by decrypting it with the CA's public key -- and must also contact the CA to ensure that the user's certificate has not been revoked by the CA. For higher level security certification, the CA requires that a unique “fingerprint” (key) be issued by the CA for each message sent by the user. 26
Veri. Sign, Inc Headquartered in Mountain View, California, a leading provider of Internet trust services authentication, validation and payment - needed by Web sites, enterprises, and e-commerce service providers to conduct trusted and secure electronic commerce and communications over IP networks. To date (2007), Veri. Sign has issued over 215, 000 Web site digital certificates and over 3. 9 million digital certificates for individuals. 27
Key Agreement Protocols Key agreement protocol Process by which parties can exchange keys Use public-key cryptography to transmit symmetric keys Digital envelope Encrypted message using symmetric key Symmetric key encrypted with the public key Digital signature 28

CA Functionality Certificate Revocation Lists Key Management Key Distribution Key Revocation Key Recovery Key Renewal Key Distruction Multiple Keys 29
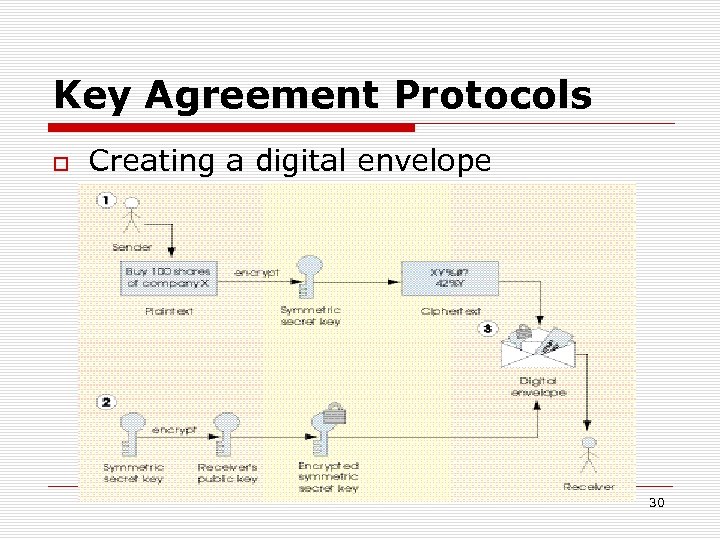
Key Agreement Protocols Creating a digital envelope 30
Key Management Key management Handling and security of private keys Key generation The process by which keys are created Must be truly random 31

Steganography Practice of hiding information within other information Dates back to 440 BC Digital watermarks Hidden within documents and can be shown to prove ownership 32

Steganography (Example 1) Example of a conventional watermark 33

Steganography (Example 2) An example of steganography: Blue Spike’s Giovanni digital watermarking process 34

Modern Steganographic Techniques Concealing Message within noise Chaffing & winnowing Invisible Ink Hidden within encrypted data: (True. Crypt) Null cipher Concealed in executable files Packet delays over network 35
Cryptographic Attacks 36

Escrowed Encryption Need for law enforcement to have access Privacy Trap doors Escrowed Encryption Standard Divide key into two parts Escrow portions with different orgs Fair Cryptosystems Divide key into multiple, verifiable, parts Store key with various trustees Banker’s Trust purchased copyright 37

Identity-based Encryption String used as key can be anything Four components Setup – generate individual’s master-key Extracting – both parties gen private key using own public key with master Encrypting – based on recipient’s public key (john@durrett. org) create ciphertext Decrypting – using recipient’s private key decrypt message 38
e. Mail Issues S/MIME – digital signs, encry, X. 509 Privacy Enhanced Mail – dig sigs, encr PGP Symmetric Cipher, RSA “Web of Trust” 39
Internet Security SSL / TLS (transaction layer security) SET Ip. Sec https Mondex ssh 2 40

SSL / TLS Size of key decides strength of encryption. (40 -bit, 56 -bit encryptions are considered weak. They can be cracked in about a week) Private Certificate Authorities: Public Certificate Authorities: Used when certain kind of trust relation exists between the client and the server Used when no other relation exists between the client and the server 41
HTTPS Secure Hypertext Transfer Protocol Client requests a secure transaction by accessing an HTTPS URL and informs server about the encryption algorithm and key sizes it supports Server sends back its digital certificate issued by CA Client verifies the certificate, generates a session key, encrypts t with server’s public key and sends it back to server Server decrypts the session key and uses it for symmetric encryption during further communication in the session 42

Wireless Security Physical security of wireless devices PDAs, cellphones: limited processing power & no few standards Wireless Application Protocol (WAP) WML, WAE, WSP, WTSL, WDP Can be PKI enabled IEEE 802. 11 b, a, g (e draft) 11 & b, a, g security bad thus 11 i working group 43
IEEE Wireless Standards 802. 11 – 1 or 2 Mbp on 2. 4 Ghz 802. 11 b – 11 to 1 Mbp on 2. 4 Ghz 802. 11 a – up to 54 Mbp at 5 Ghz 802. 11 g – 20 to 54 @ 2. 4 802. 11 e – Qo. S 802. 15, 802. 16 – Wireless broadband WAN 44

Wireless Vulnerabilities Denial of Service Attacks “WAP Gap” – protocol change at carrier’s gateway (Soft AP) Insertion attack & rogue access points WEP weaknesses – not designed for directed crypto attack SSID issues Scanning & War Driving Wireless Packet sniffers & neighbours Physical Loss 45

Wireless Vulnerabilities conti. Accidental Association Ad-hoc networks Non-traditional networks MAC spoofing Man-in-the-middle Network injection 46

Countering Risks All LAN devices should be secured All Users should be Educated LAN systems should be monitored 47
Countering Risks conti. MAC filtering Static IPs 48

Wireless Application Protocol (WAP) Layers Wireless Transport Layer Security Application, Session, Transaction, Security, Transport 3 classes of authentication – anonymous, server, client-server WEP (Wired Equivalent Privacy) WPA 49

WEP 40 bit shared key, Rivest Code 4 (RC 4) Intended to be “as secure as wired” Never happen aircrack-ng, Weplab, WEPCrack, Airsnort Problems: does not deal with key management Weaknesses in RC 4 50

Wi. Fi Protected Access (WPA) Temporal Key Integrity Protocol (TKIP) IV increased from 24 bits to 48 bits Rollover of counter eliminated IVs used as sequence counter (replay attack) Avoids weak IV values different keys for each packet Master keys never used directly Secure key management built-in Message Integrity Check Validates mess. 51

Instant Messaging Security Issues IM systems can transport sensitive and confidential data over public networks in unencrypted form. IM systems do not prevent transportation of files containing viruses Misconfigured file sharing can provide access to system files, passwords, etc. To monitor and prevent IM traffic network can be configured to deny access to certain domains (e. g. block yahoo. com for Yahoo messenger) 52
References: 1. e-Business & e-Commerce for Manageers, Deitel and Steinbuhler, Prentice-Hall, 2002 2. www. extremetech. com & pcmag. com 4. www. rsasecurity. com 5. www. seruritysearch. net 6. How ssl works (verisign) (how stuff works) 53
e58ee59e796ff331a9320984a6fa9b4f.ppt