35754ea6a2e2d8f14a207fbbcf3d229e.ppt
- Количество слайдов: 113
 CRYPTOGRAPHY & NETWORK SECURITY UNIT-III AUTHENTICATION & HASH FUNCTION
CRYPTOGRAPHY & NETWORK SECURITY UNIT-III AUTHENTICATION & HASH FUNCTION
 Message Authentication and Hash Functions • • • Authentication Requirements Authentication Functions Message Authentication Codes Hash Functions Security of Hash Functions and MACs
Message Authentication and Hash Functions • • • Authentication Requirements Authentication Functions Message Authentication Codes Hash Functions Security of Hash Functions and MACs
 What is authentication? • Positive verification of identity (man or machine) • Verification of a person’s claimed identity • Who are you? Prove it. • 3 Categories: – What you know – What you have – Who you are
What is authentication? • Positive verification of identity (man or machine) • Verification of a person’s claimed identity • Who are you? Prove it. • 3 Categories: – What you know – What you have – Who you are
 What you know • Password • Passphrase • PIN
What you know • Password • Passphrase • PIN
 What you have • Digital authentication – physical devices to aid authentication • Common examples: – e. Token – smart cards – RFID
What you have • Digital authentication – physical devices to aid authentication • Common examples: – e. Token – smart cards – RFID
 e. Token • Can be implemented on a USB key fob or a smart card • Data physically protected on the device itself • On the client side, the token is accessed via password • Successful client-side authentication with the password invokes the token to generate a stored or generated passcode, which is sent to the server-side for authentication.
e. Token • Can be implemented on a USB key fob or a smart card • Data physically protected on the device itself • On the client side, the token is accessed via password • Successful client-side authentication with the password invokes the token to generate a stored or generated passcode, which is sent to the server-side for authentication.
 e. Token • May store credentials such as passwords, digital signatures and certificates, and private keys • Can offer on-board authentication and digital signing
e. Token • May store credentials such as passwords, digital signatures and certificates, and private keys • Can offer on-board authentication and digital signing
 Smart cards • Size of a credit card • Usually an embedded microprocessor with computational and storage capabilities • Programmable platforms: – C/C++ – Visual Basic – Java –. Net (beta)
Smart cards • Size of a credit card • Usually an embedded microprocessor with computational and storage capabilities • Programmable platforms: – C/C++ – Visual Basic – Java –. Net (beta)
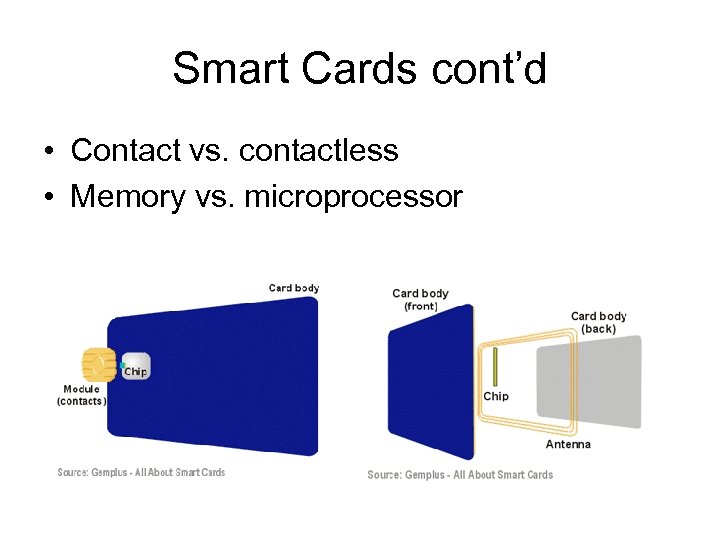 Smart Cards cont’d • Contact vs. contactless • Memory vs. microprocessor
Smart Cards cont’d • Contact vs. contactless • Memory vs. microprocessor
 RFID • RFID - Radio Frequency IDentification • Integrated circuit(s) with an antenna that can respond to an RF signal with identity information • No power supply necessary—IC uses the RF signal to power itself • Susceptible to replay attacks and theft • Examples: – Smart Tag, EZPass – Garage parking permits
RFID • RFID - Radio Frequency IDentification • Integrated circuit(s) with an antenna that can respond to an RF signal with identity information • No power supply necessary—IC uses the RF signal to power itself • Susceptible to replay attacks and theft • Examples: – Smart Tag, EZPass – Garage parking permits
 RFID • 13. 56 Mhz read/write support • May communicate with a variety of transponders (ISO 15693, ISO 14443 Type A & B, Tag. It, Icode, etc. ) • Reader is controlled via PCMCIA interface using an ASCII protocol
RFID • 13. 56 Mhz read/write support • May communicate with a variety of transponders (ISO 15693, ISO 14443 Type A & B, Tag. It, Icode, etc. ) • Reader is controlled via PCMCIA interface using an ASCII protocol
 Who you are • Biometric authentication – Use of a biometric reading to confirm that a person is who he/she claims to be • Biometric reading – A recording of some physical or behavioral attribute of a person
Who you are • Biometric authentication – Use of a biometric reading to confirm that a person is who he/she claims to be • Biometric reading – A recording of some physical or behavioral attribute of a person
 Physical Biometrics • • Fingerprint Iris Hand Geometry Finger Geometry Face Geometry Ear Shape Retina • • • Smell Thermal Face Hand Vein Nail Bed DNA Palm Print
Physical Biometrics • • Fingerprint Iris Hand Geometry Finger Geometry Face Geometry Ear Shape Retina • • • Smell Thermal Face Hand Vein Nail Bed DNA Palm Print
 Behavioral Biometrics • • Signature Voice Keystroke Gait
Behavioral Biometrics • • Signature Voice Keystroke Gait
 Fingerprints • Vast amount of data available on fingerprint pattern matching • Data originally from forensics • Over 100 years of data to draw on – Thus far all prints obtained have been unique
Fingerprints • Vast amount of data available on fingerprint pattern matching • Data originally from forensics • Over 100 years of data to draw on – Thus far all prints obtained have been unique
 Fingerprint Basics • Global features – Features that can be seen with the naked eye – Basic ridge patterns • Local features – Minutia points – Tiny unique characteristics of fingerprint ridges used for positive identification
Fingerprint Basics • Global features – Features that can be seen with the naked eye – Basic ridge patterns • Local features – Minutia points – Tiny unique characteristics of fingerprint ridges used for positive identification
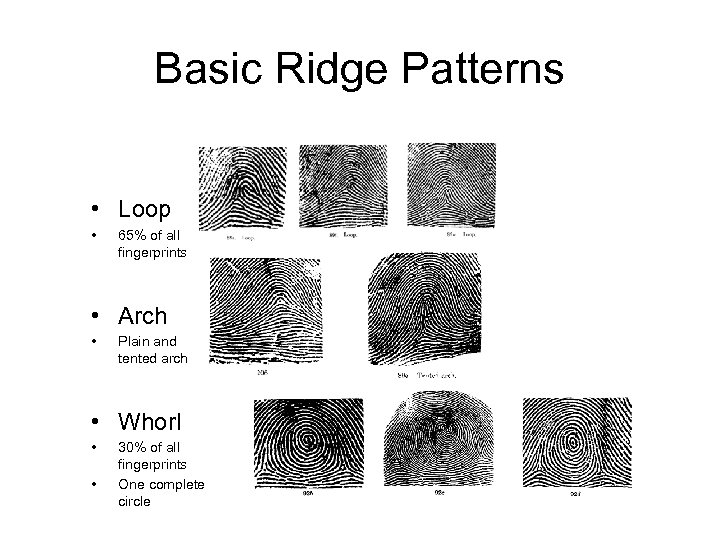 Basic Ridge Patterns • Loop • 65% of all fingerprints • Arch • Plain and tented arch • Whorl • • 30% of all fingerprints One complete circle
Basic Ridge Patterns • Loop • 65% of all fingerprints • Arch • Plain and tented arch • Whorl • • 30% of all fingerprints One complete circle
 Local Features • Also known as minutia points • Used for positive identification • Two or more individuals may have the same global features, but different minutia • Minutia points do not have to be inside the pattern area
Local Features • Also known as minutia points • Used for positive identification • Two or more individuals may have the same global features, but different minutia • Minutia points do not have to be inside the pattern area
 Types of Minutia • • Ridge ending Ridge bifurcation Ridge divergence Dot or island – ridge so short it appears to be a dot • Enclosure – ridge separates and then reunites around an area of ridge-less skin • Short ridge – bigger than a dot
Types of Minutia • • Ridge ending Ridge bifurcation Ridge divergence Dot or island – ridge so short it appears to be a dot • Enclosure – ridge separates and then reunites around an area of ridge-less skin • Short ridge – bigger than a dot
 Minutia Characteristics • Orientation – The direction the minutia is facing • Spatial frequency – How far apart the ridges are around the point • Curvature – Rate of change of orientation • Position – X, Y location relative to some fixed points
Minutia Characteristics • Orientation – The direction the minutia is facing • Spatial frequency – How far apart the ridges are around the point • Curvature – Rate of change of orientation • Position – X, Y location relative to some fixed points
 Algorithms • Image-based • Pattern-based • Minutia-based
Algorithms • Image-based • Pattern-based • Minutia-based
 Fingerprint Scanners Digital Persona U. are. U Pro HP IPAQ IBM Thinkpad T 42
Fingerprint Scanners Digital Persona U. are. U Pro HP IPAQ IBM Thinkpad T 42
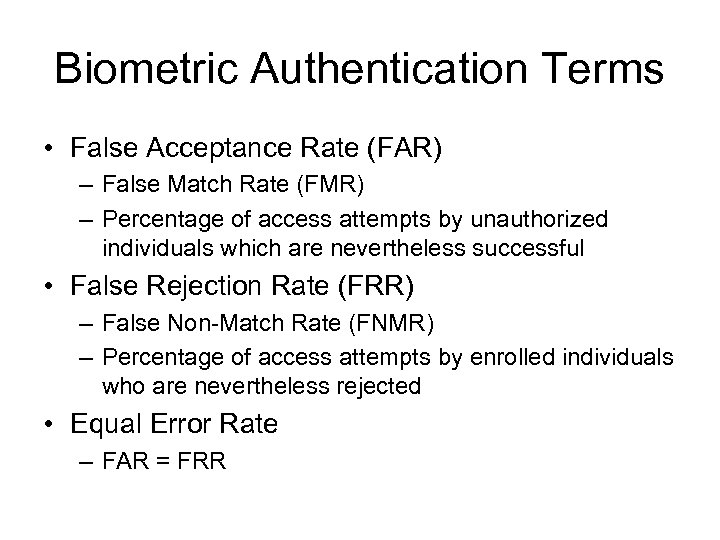 Biometric Authentication Terms • False Acceptance Rate (FAR) – False Match Rate (FMR) – Percentage of access attempts by unauthorized individuals which are nevertheless successful • False Rejection Rate (FRR) – False Non-Match Rate (FNMR) – Percentage of access attempts by enrolled individuals who are nevertheless rejected • Equal Error Rate – FAR = FRR
Biometric Authentication Terms • False Acceptance Rate (FAR) – False Match Rate (FMR) – Percentage of access attempts by unauthorized individuals which are nevertheless successful • False Rejection Rate (FRR) – False Non-Match Rate (FNMR) – Percentage of access attempts by enrolled individuals who are nevertheless rejected • Equal Error Rate – FAR = FRR
 Review: Three Categories • What you know – Password – PIN • What you have – e-Token – RFID • Who you are – Biometrics
Review: Three Categories • What you know – Password – PIN • What you have – e-Token – RFID • Who you are – Biometrics
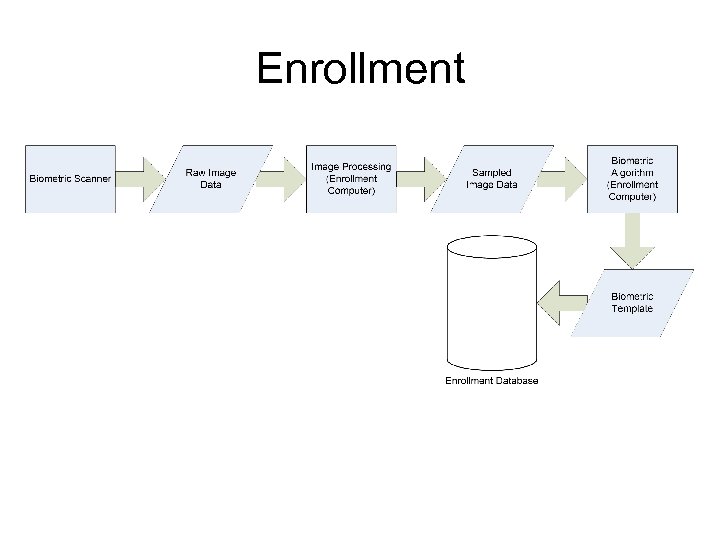 Enrollment
Enrollment
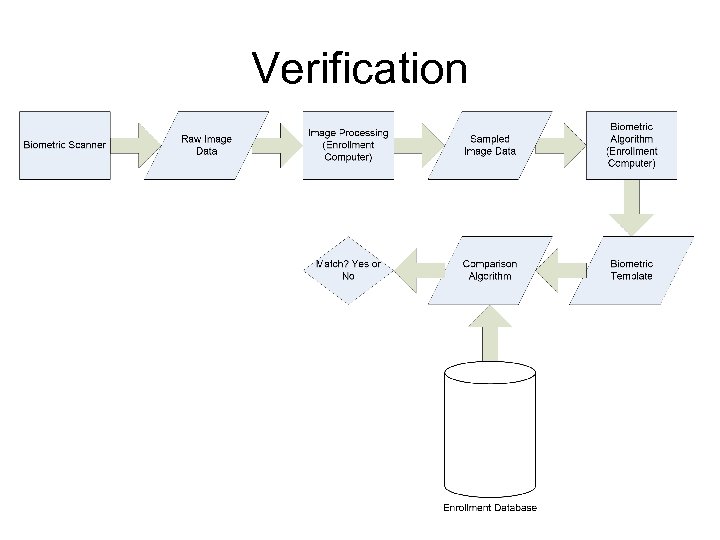 Verification
Verification
 Motivation • Real-world considerations: – What you know and what you have • Can be stolen or forgotten • Susceptible to replay attacks – Who you are • Unique biometrics that hinder replay attacks and imposters • Privacy issues arise
Motivation • Real-world considerations: – What you know and what you have • Can be stolen or forgotten • Susceptible to replay attacks – Who you are • Unique biometrics that hinder replay attacks and imposters • Privacy issues arise
 Authentication Token Formats • A security token (authentication token) is a representation of security-related data (not to be confused with an e-Token) • Examples: – X. 509 certificates – Kerberos tickets – Custom security tokens
Authentication Token Formats • A security token (authentication token) is a representation of security-related data (not to be confused with an e-Token) • Examples: – X. 509 certificates – Kerberos tickets – Custom security tokens
 X. 509 Certificates • Use of digital certificates issued by a trusted Certificate Authority (e. g. Veri. Sign) • A Digital Certificate contains information to assert an identity claim – – Name Serial number Expiration dates Certificate holder’s public key (used for encrypting/decrypting messages and digital signatures) – Digital signature of Certificate Authority (so recipient knows that the certificate is valid) • The recipient may confirm the identity of the sender with the Certificate Authority
X. 509 Certificates • Use of digital certificates issued by a trusted Certificate Authority (e. g. Veri. Sign) • A Digital Certificate contains information to assert an identity claim – – Name Serial number Expiration dates Certificate holder’s public key (used for encrypting/decrypting messages and digital signatures) – Digital signature of Certificate Authority (so recipient knows that the certificate is valid) • The recipient may confirm the identity of the sender with the Certificate Authority
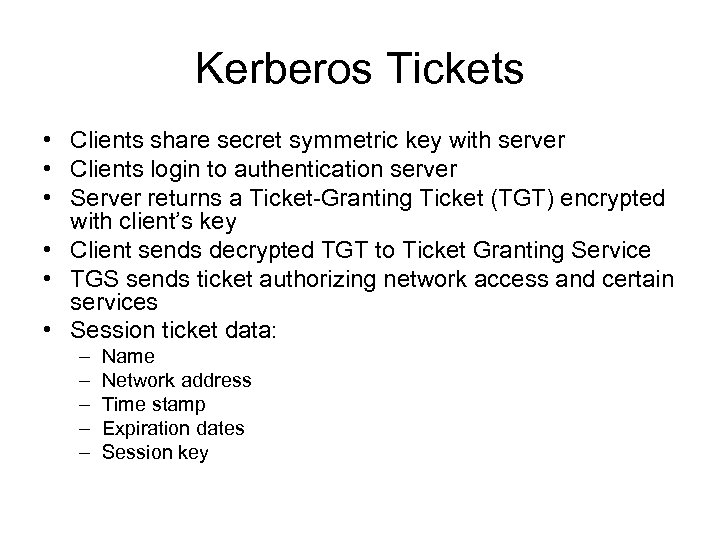 Kerberos Tickets • Clients share secret symmetric key with server • Clients login to authentication server • Server returns a Ticket-Granting Ticket (TGT) encrypted with client’s key • Client sends decrypted TGT to Ticket Granting Service • TGS sends ticket authorizing network access and certain services • Session ticket data: – – – Name Network address Time stamp Expiration dates Session key
Kerberos Tickets • Clients share secret symmetric key with server • Clients login to authentication server • Server returns a Ticket-Granting Ticket (TGT) encrypted with client’s key • Client sends decrypted TGT to Ticket Granting Service • TGS sends ticket authorizing network access and certain services • Session ticket data: – – – Name Network address Time stamp Expiration dates Session key
 Custom Security Tokens • May contain additional context information: – Access method • wired, local terminal • wired remote terminal • wireless PDA – Authentication method • Password • e-Token • Fingerprint – Trust level
Custom Security Tokens • May contain additional context information: – Access method • wired, local terminal • wired remote terminal • wireless PDA – Authentication method • Password • e-Token • Fingerprint – Trust level
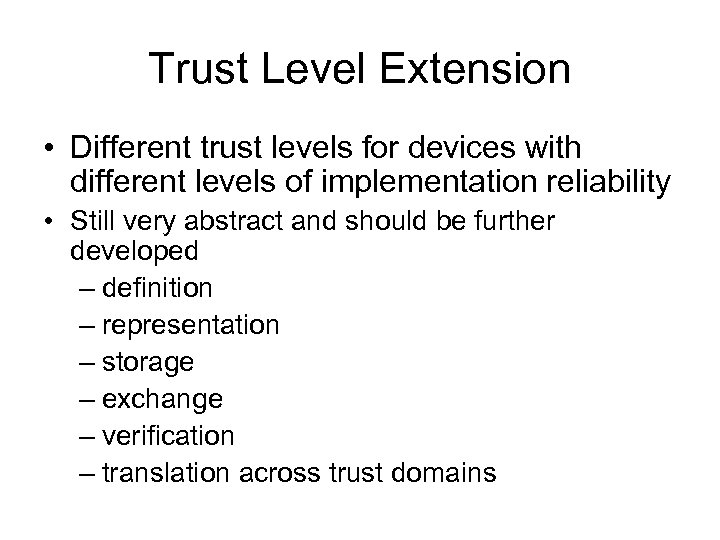 Trust Level Extension • Different trust levels for devices with different levels of implementation reliability • Still very abstract and should be further developed – definition – representation – storage – exchange – verification – translation across trust domains
Trust Level Extension • Different trust levels for devices with different levels of implementation reliability • Still very abstract and should be further developed – definition – representation – storage – exchange – verification – translation across trust domains
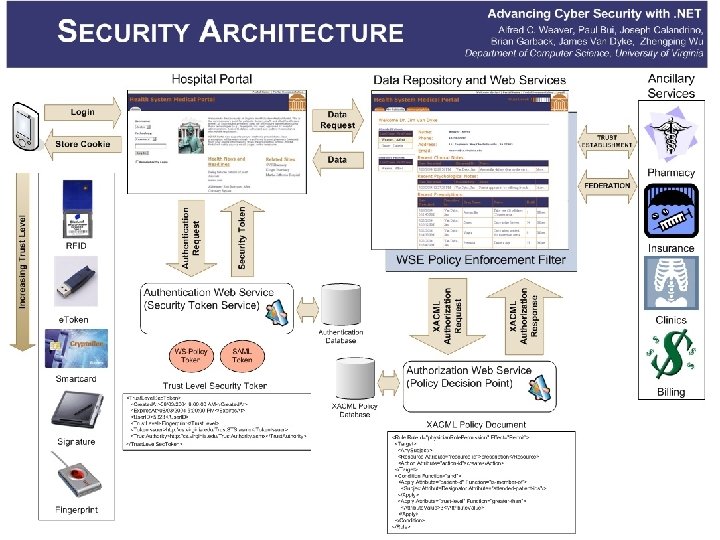
 Example Authentication (Security) Token Request
Example Authentication (Security) Token Request
 Example Authentication (Security) Token Reply
Example Authentication (Security) Token Reply
 AUTHENTICATION REQUIREMENTS
AUTHENTICATION REQUIREMENTS
 Authentication Requirements • Kind of attacks (threats) in the context of communications across a network 1. 2. 3. 4. 5. 6. 7. • Disclosure Traffic analysis Masquerade Content modification Sequence modification Timing modification Repudiation Measures to deal with first two attacks: – In the realm of message confidentiality, and are addressed with encryption • Measures to deal with items 3 thru 6 – Message authentication • Measures to deal with items 7 – Digital signature
Authentication Requirements • Kind of attacks (threats) in the context of communications across a network 1. 2. 3. 4. 5. 6. 7. • Disclosure Traffic analysis Masquerade Content modification Sequence modification Timing modification Repudiation Measures to deal with first two attacks: – In the realm of message confidentiality, and are addressed with encryption • Measures to deal with items 3 thru 6 – Message authentication • Measures to deal with items 7 – Digital signature
 Authentication Requirements • Message authentication – A procedure to verify that messages come from the alleged source and have not been altered – Message authentication may also verify sequencing and timeliness • Digital signature – An authentication technique that also includes measures to counter repudiation by either source or destination
Authentication Requirements • Message authentication – A procedure to verify that messages come from the alleged source and have not been altered – Message authentication may also verify sequencing and timeliness • Digital signature – An authentication technique that also includes measures to counter repudiation by either source or destination
 Authentication • Requirements - must be able to verify that: – Message came from its alleged source or author, – Contents have not been altered, – Sometimes, it was sent at a certain time or sequence. • • Protection against active attack (falsification of data and transactions) Two levels for message authentication mechanism – Lower level: authenticator – a value to be used to authenticate a message – Higher level: an authentication protocol that enables a receiver to verify the authenticity of the message
Authentication • Requirements - must be able to verify that: – Message came from its alleged source or author, – Contents have not been altered, – Sometimes, it was sent at a certain time or sequence. • • Protection against active attack (falsification of data and transactions) Two levels for message authentication mechanism – Lower level: authenticator – a value to be used to authenticate a message – Higher level: an authentication protocol that enables a receiver to verify the authenticity of the message
 Message Authentication
Message Authentication
 Approaches to Message Authentication • Authentication Using Conventional Encryption – Only the sender and receiver should share a key • Message Authentication without Message Encryption – An authentication tag is generated and appended to each message – Two ways • Message Authentication Code (MAC) • Hash function (or message digest)
Approaches to Message Authentication • Authentication Using Conventional Encryption – Only the sender and receiver should share a key • Message Authentication without Message Encryption – An authentication tag is generated and appended to each message – Two ways • Message Authentication Code (MAC) • Hash function (or message digest)
 Message Authentication • message authentication is concerned with: – – – protecting the integrity of a message validating identity of originator non-repudiation of origin (dispute resolution) • will consider the security requirements • then three alternative functions used: – hash function (see Ch 11) – message encryption – message authentication code (MAC)
Message Authentication • message authentication is concerned with: – – – protecting the integrity of a message validating identity of originator non-repudiation of origin (dispute resolution) • will consider the security requirements • then three alternative functions used: – hash function (see Ch 11) – message encryption – message authentication code (MAC)
 Message Security Requirements • • disclosure traffic analysis masquerade content modification sequence modification timing modification source repudiation destination repudiation
Message Security Requirements • • disclosure traffic analysis masquerade content modification sequence modification timing modification source repudiation destination repudiation
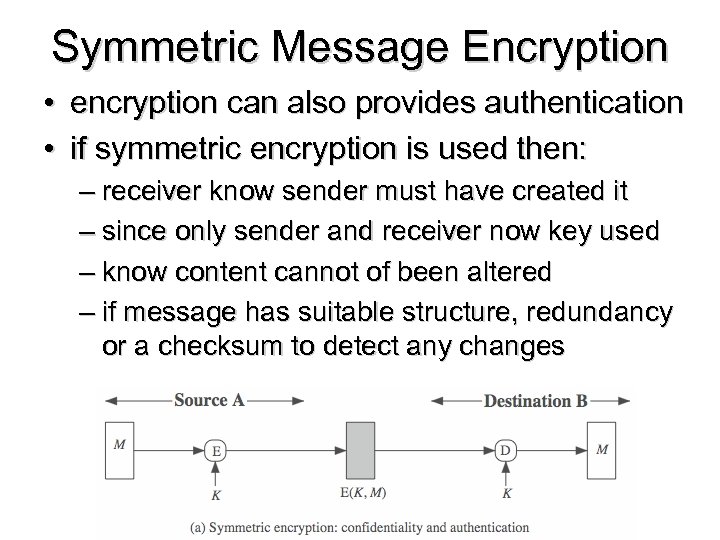 Symmetric Message Encryption • encryption can also provides authentication • if symmetric encryption is used then: – receiver know sender must have created it – since only sender and receiver now key used – know content cannot of been altered – if message has suitable structure, redundancy or a checksum to detect any changes
Symmetric Message Encryption • encryption can also provides authentication • if symmetric encryption is used then: – receiver know sender must have created it – since only sender and receiver now key used – know content cannot of been altered – if message has suitable structure, redundancy or a checksum to detect any changes
 Public-Key Message Encryption • if public-key encryption is used: – encryption provides no confidence of sender • since anyone potentially knows public-key – however if • sender signs message using their private-key • then encrypts with recipients public key • have both secrecy and authentication – again need to recognize corrupted messages – but at cost of two public-key uses on message
Public-Key Message Encryption • if public-key encryption is used: – encryption provides no confidence of sender • since anyone potentially knows public-key – however if • sender signs message using their private-key • then encrypts with recipients public key • have both secrecy and authentication – again need to recognize corrupted messages – but at cost of two public-key uses on message
 Message Authentication Code (MAC) • generated by an algorithm that creates a small fixed-sized block – depending on both message and some key – like encryption though need not be reversible • appended to message as a signature • receiver performs same computation on message and checks it matches the MAC • provides assurance that message is unaltered and comes from sender
Message Authentication Code (MAC) • generated by an algorithm that creates a small fixed-sized block – depending on both message and some key – like encryption though need not be reversible • appended to message as a signature • receiver performs same computation on message and checks it matches the MAC • provides assurance that message is unaltered and comes from sender
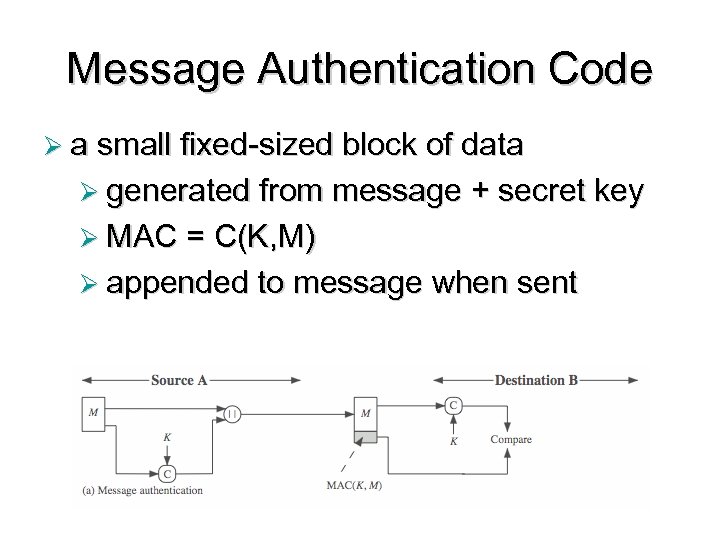 Message Authentication Code Ø a small fixed-sized block of data Ø generated from message + secret key Ø MAC = C(K, M) Ø appended to message when sent
Message Authentication Code Ø a small fixed-sized block of data Ø generated from message + secret key Ø MAC = C(K, M) Ø appended to message when sent
 Message Authentication Codes • as shown the MAC provides authentication • can also use encryption for secrecy – generally use separate keys for each – can compute MAC either before or after encryption – is generally regarded as better done before • why use a MAC? – sometimes only authentication is needed – sometimes need authentication to persist longer than the encryption (eg. archival use) • note that a MAC is not a digital signature
Message Authentication Codes • as shown the MAC provides authentication • can also use encryption for secrecy – generally use separate keys for each – can compute MAC either before or after encryption – is generally regarded as better done before • why use a MAC? – sometimes only authentication is needed – sometimes need authentication to persist longer than the encryption (eg. archival use) • note that a MAC is not a digital signature
 MAC Properties • a MAC is a cryptographic checksum MAC = CK(M) – condenses a variable-length message M – using a secret key K – to a fixed-sized authenticator • is a many-to-one function – potentially many messages have same MAC – but finding these needs to be very difficult
MAC Properties • a MAC is a cryptographic checksum MAC = CK(M) – condenses a variable-length message M – using a secret key K – to a fixed-sized authenticator • is a many-to-one function – potentially many messages have same MAC – but finding these needs to be very difficult
 Requirements for MACs • • taking into account the types of attacks need the MAC to satisfy the following: 1. knowing a message and MAC, is infeasible to find another message with same MAC 2. MACs should be uniformly distributed 3. MAC should depend equally on all bits of the message
Requirements for MACs • • taking into account the types of attacks need the MAC to satisfy the following: 1. knowing a message and MAC, is infeasible to find another message with same MAC 2. MACs should be uniformly distributed 3. MAC should depend equally on all bits of the message
 Security of MACs • like block ciphers have: • brute-force attacks exploiting – strong collision resistance hash have cost m/ 2 2 • 128 -bit hash looks vulnerable, 160 -bits better – MACs with known message-MAC pairs • can either attack keyspace (cf key search) or MAC • at least 128 -bit MAC is needed for security
Security of MACs • like block ciphers have: • brute-force attacks exploiting – strong collision resistance hash have cost m/ 2 2 • 128 -bit hash looks vulnerable, 160 -bits better – MACs with known message-MAC pairs • can either attack keyspace (cf key search) or MAC • at least 128 -bit MAC is needed for security
 Security of MACs • cryptanalytic attacks exploit structure – like block ciphers want brute-force attacks to be the best alternative • more variety of MACs so harder to generalize about cryptanalysis
Security of MACs • cryptanalytic attacks exploit structure – like block ciphers want brute-force attacks to be the best alternative • more variety of MACs so harder to generalize about cryptanalysis
 Keyed Hash Functions as MACs • want a MAC based on a hash function – because hash functions are generally faster – crypto hash function code is widely available • hash includes a key along with message • original proposal: Keyed. Hash = Hash(Key|Message) – some weaknesses were found with this • eventually led to development of HMAC
Keyed Hash Functions as MACs • want a MAC based on a hash function – because hash functions are generally faster – crypto hash function code is widely available • hash includes a key along with message • original proposal: Keyed. Hash = Hash(Key|Message) – some weaknesses were found with this • eventually led to development of HMAC
 Authentication Functions Message Encryption • Conventional encryption can serve as authenticator – Conventional encryption provides authentication as well as confidentiality – Requires recognizable plaintext or other structure to distinguish between well-formed legitimate plaintext and meaningless random bits • e. g. , ASCII text, an appended checksum, or use of layered protocols
Authentication Functions Message Encryption • Conventional encryption can serve as authenticator – Conventional encryption provides authentication as well as confidentiality – Requires recognizable plaintext or other structure to distinguish between well-formed legitimate plaintext and meaningless random bits • e. g. , ASCII text, an appended checksum, or use of layered protocols
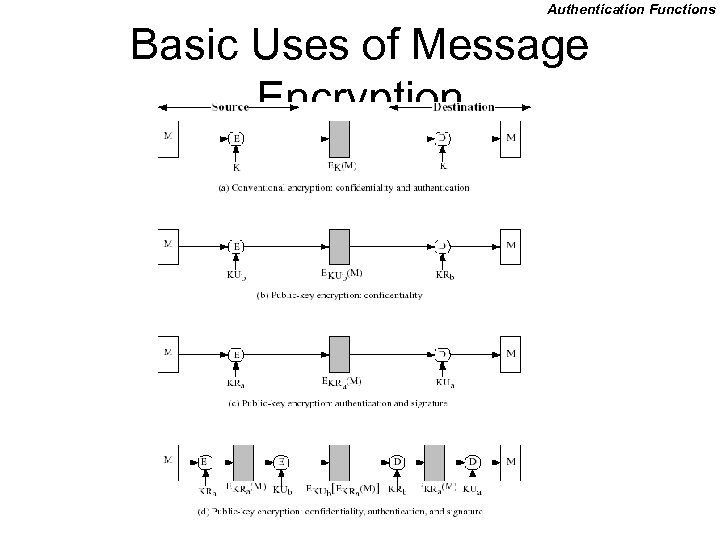 Authentication Functions Basic Uses of Message Encryption
Authentication Functions Basic Uses of Message Encryption
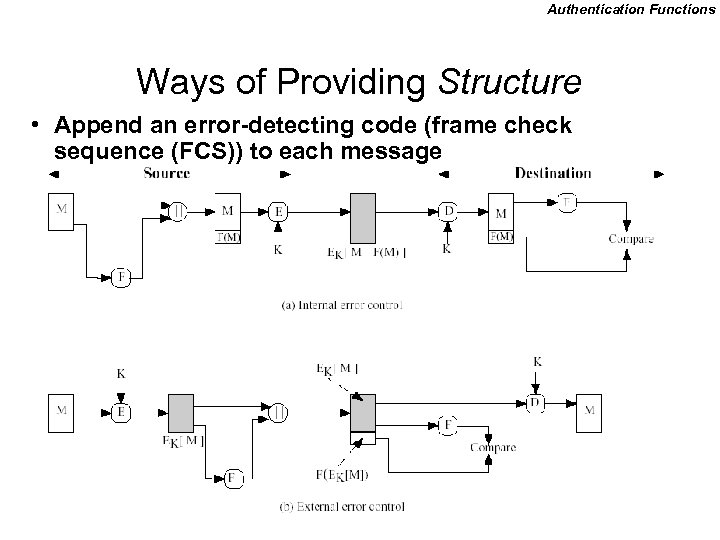 Authentication Functions Ways of Providing Structure • Append an error-detecting code (frame check sequence (FCS)) to each message
Authentication Functions Ways of Providing Structure • Append an error-detecting code (frame check sequence (FCS)) to each message
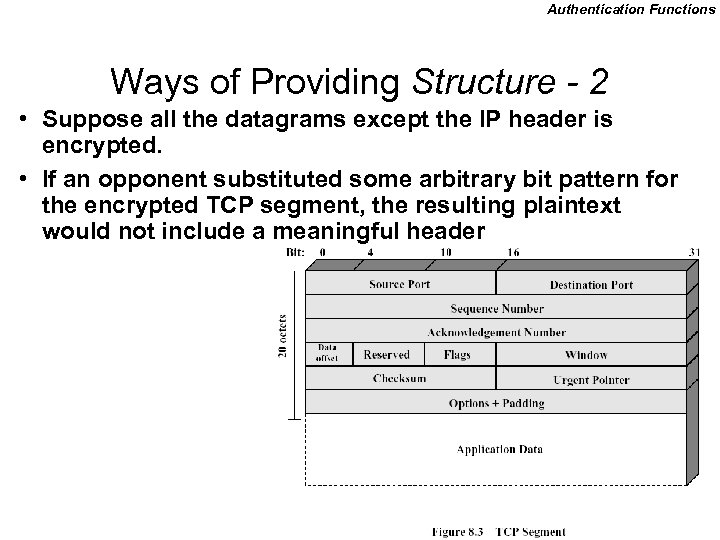 Authentication Functions Ways of Providing Structure - 2 • Suppose all the datagrams except the IP header is encrypted. • If an opponent substituted some arbitrary bit pattern for the encrypted TCP segment, the resulting plaintext would not include a meaningful header
Authentication Functions Ways of Providing Structure - 2 • Suppose all the datagrams except the IP header is encrypted. • If an opponent substituted some arbitrary bit pattern for the encrypted TCP segment, the resulting plaintext would not include a meaningful header
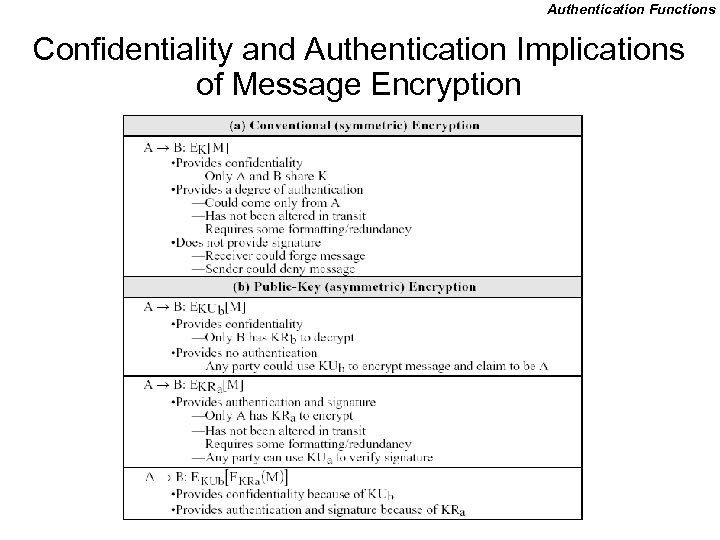 Authentication Functions Confidentiality and Authentication Implications of Message Encryption
Authentication Functions Confidentiality and Authentication Implications of Message Encryption
 Authentication Functions Message Authentication Code • Uses a shared secret key to generate a fixed-size block of data (known as a cryptographic checksum or MAC) that is appended to the message • MAC = CK(M) • Assurances: – Message has not been altered – Message is from alleged sender – Message sequence is unaltered (requires internal sequencing) • Similar to encryption but MAC algorithm
Authentication Functions Message Authentication Code • Uses a shared secret key to generate a fixed-size block of data (known as a cryptographic checksum or MAC) that is appended to the message • MAC = CK(M) • Assurances: – Message has not been altered – Message is from alleged sender – Message sequence is unaltered (requires internal sequencing) • Similar to encryption but MAC algorithm
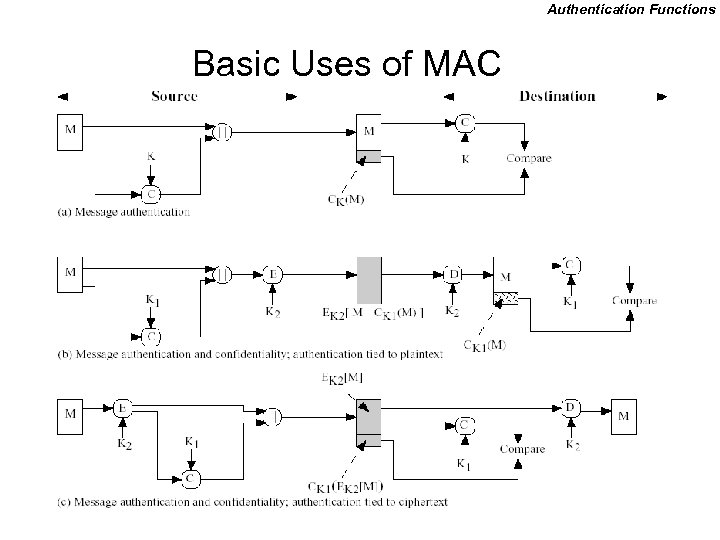 Authentication Functions Basic Uses of MAC
Authentication Functions Basic Uses of MAC
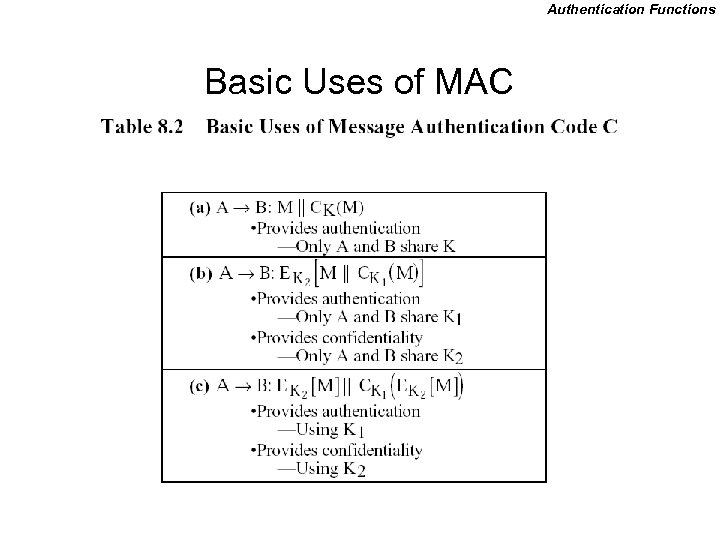 Authentication Functions Basic Uses of MAC
Authentication Functions Basic Uses of MAC
 Authentication Functions Why Use MACs? – i. e. , why not just use encryption? • • • Cleartext stays clear MAC might be cheaper Broadcast Authentication of executable codes Architectural flexibility Separation of authentication check from message use
Authentication Functions Why Use MACs? – i. e. , why not just use encryption? • • • Cleartext stays clear MAC might be cheaper Broadcast Authentication of executable codes Architectural flexibility Separation of authentication check from message use
 Authentication Functions Hash Function • Converts a variable size message M into fixed size hash code H(M) (Sometimes called a message digest) • Can be used with encryption for authentication – E(M || H) – M || E(H) – M || signed H – E( M || signed H ) gives confidentiality – M || H( M || K )
Authentication Functions Hash Function • Converts a variable size message M into fixed size hash code H(M) (Sometimes called a message digest) • Can be used with encryption for authentication – E(M || H) – M || E(H) – M || signed H – E( M || signed H ) gives confidentiality – M || H( M || K )
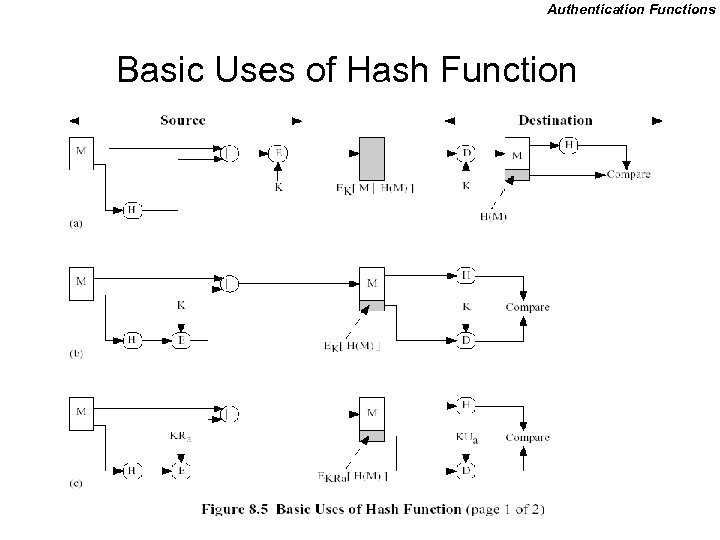 Authentication Functions Basic Uses of Hash Function
Authentication Functions Basic Uses of Hash Function
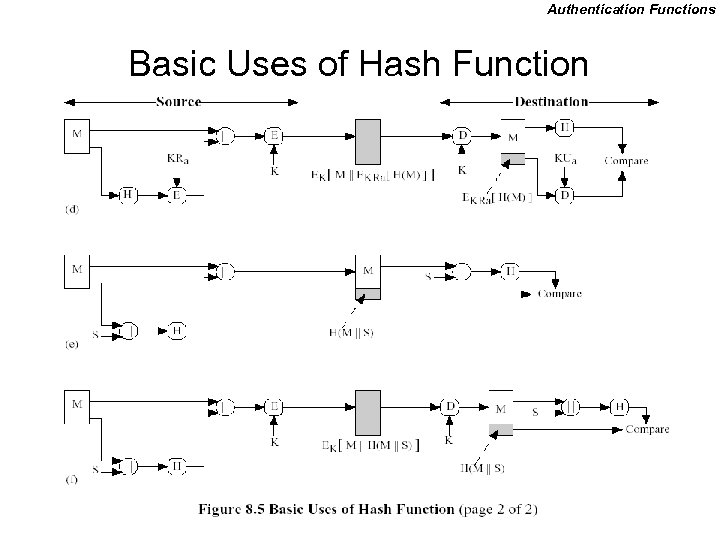 Authentication Functions Basic Uses of Hash Function
Authentication Functions Basic Uses of Hash Function
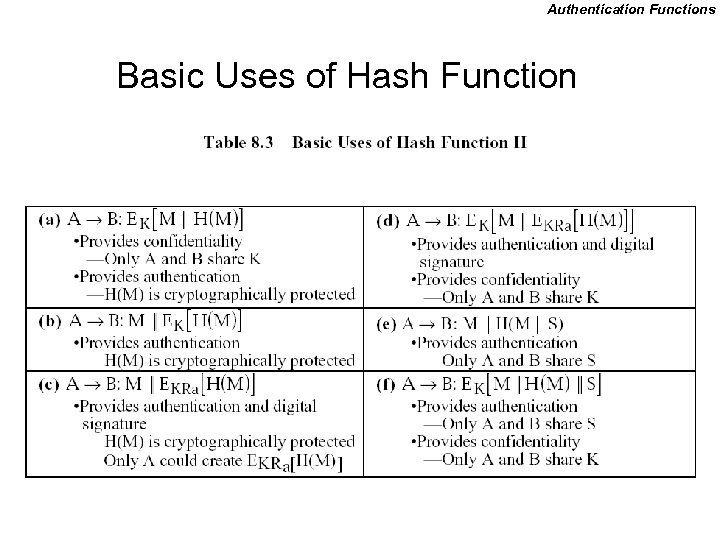 Authentication Functions Basic Uses of Hash Function
Authentication Functions Basic Uses of Hash Function
 MACs Message Authentication Codes • MAC= CK(M) • Key length requirements – Sufficient key length to thwart brute force attack
MACs Message Authentication Codes • MAC= CK(M) • Key length requirements – Sufficient key length to thwart brute force attack
 Hash Functions • h = H(M) • M is a variable-length message, h is a fixed-length hash value, H is a hash function • The hash value is appended at the source • The receiver authenticates the message by recomputing the hash value • Because the hash function itself is not considered to be secret, some means is required to protect the hash value
Hash Functions • h = H(M) • M is a variable-length message, h is a fixed-length hash value, H is a hash function • The hash value is appended at the source • The receiver authenticates the message by recomputing the hash value • Because the hash function itself is not considered to be secret, some means is required to protect the hash value
 Hash Functions Hash Function Requirements 1. 2. 3. 4. H can be applied to any size data block H produces fixed-length output H(x) is relatively easy to compute for any given x H is one-way, i. e. , given h, it is computationally infeasible to find any x s. t. h = H(x) 5. H is weakly collision resistant: given x, it is computationally infeasible to find any y x s. t. H(x) = H(y) 6. H is strongly collision resistant: it is computationally infeasible to find any x and y s. t. H(x) = H(y)
Hash Functions Hash Function Requirements 1. 2. 3. 4. H can be applied to any size data block H produces fixed-length output H(x) is relatively easy to compute for any given x H is one-way, i. e. , given h, it is computationally infeasible to find any x s. t. h = H(x) 5. H is weakly collision resistant: given x, it is computationally infeasible to find any y x s. t. H(x) = H(y) 6. H is strongly collision resistant: it is computationally infeasible to find any x and y s. t. H(x) = H(y)
 Hash Functions Hash Function Requirements • One-way property is essential for authentication • Weak collision resistance is necessary to prevent forgery • Strong collision resistance is important for resistance to birthday attack
Hash Functions Hash Function Requirements • One-way property is essential for authentication • Weak collision resistance is necessary to prevent forgery • Strong collision resistance is important for resistance to birthday attack
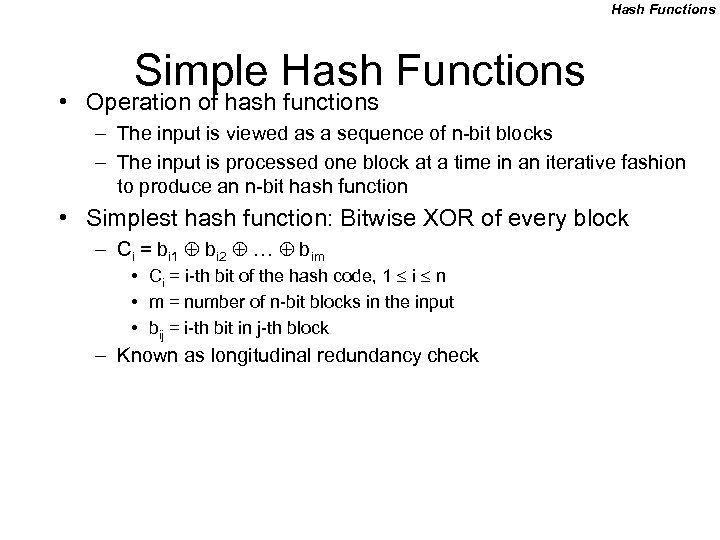 Hash Functions Simple Hash Functions • Operation of hash functions – The input is viewed as a sequence of n-bit blocks – The input is processed one block at a time in an iterative fashion to produce an n-bit hash function • Simplest hash function: Bitwise XOR of every block – Ci = bi 1 bi 2 … bim • Ci = i-th bit of the hash code, 1 i n • m = number of n-bit blocks in the input • bij = i-th bit in j-th block – Known as longitudinal redundancy check
Hash Functions Simple Hash Functions • Operation of hash functions – The input is viewed as a sequence of n-bit blocks – The input is processed one block at a time in an iterative fashion to produce an n-bit hash function • Simplest hash function: Bitwise XOR of every block – Ci = bi 1 bi 2 … bim • Ci = i-th bit of the hash code, 1 i n • m = number of n-bit blocks in the input • bij = i-th bit in j-th block – Known as longitudinal redundancy check
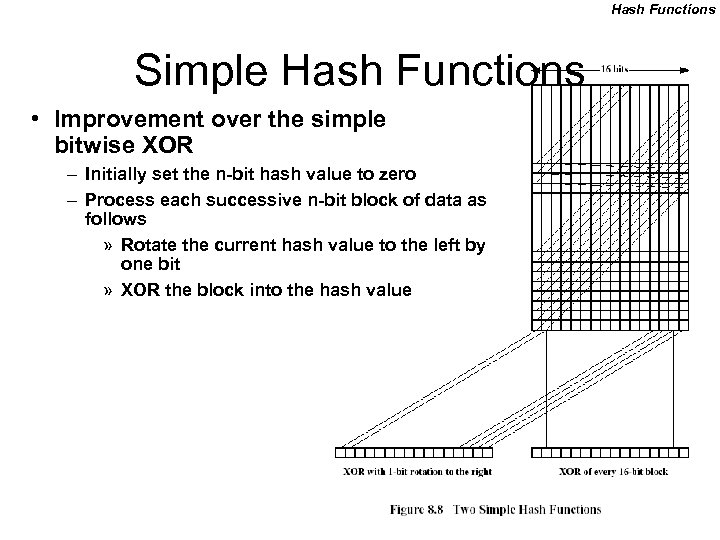 Hash Functions Simple Hash Functions • Improvement over the simple bitwise XOR – Initially set the n-bit hash value to zero – Process each successive n-bit block of data as follows » Rotate the current hash value to the left by one bit » XOR the block into the hash value
Hash Functions Simple Hash Functions • Improvement over the simple bitwise XOR – Initially set the n-bit hash value to zero – Process each successive n-bit block of data as follows » Rotate the current hash value to the left by one bit » XOR the block into the hash value
 Birthday Attack • If the adversary can generate 2 m/2 variants of a valid message and an equal number of fraudulent messages • The two sets are compared to find one message from each set with a common hash value • The valid message is offered for signature • The fraudulent message with the same hash value is inserted in its place • If a 64 -bit hash code is used, the level of effort is only on the order of 232 • Conclusion: the length of the hash code must be substantial
Birthday Attack • If the adversary can generate 2 m/2 variants of a valid message and an equal number of fraudulent messages • The two sets are compared to find one message from each set with a common hash value • The valid message is offered for signature • The fraudulent message with the same hash value is inserted in its place • If a 64 -bit hash code is used, the level of effort is only on the order of 232 • Conclusion: the length of the hash code must be substantial
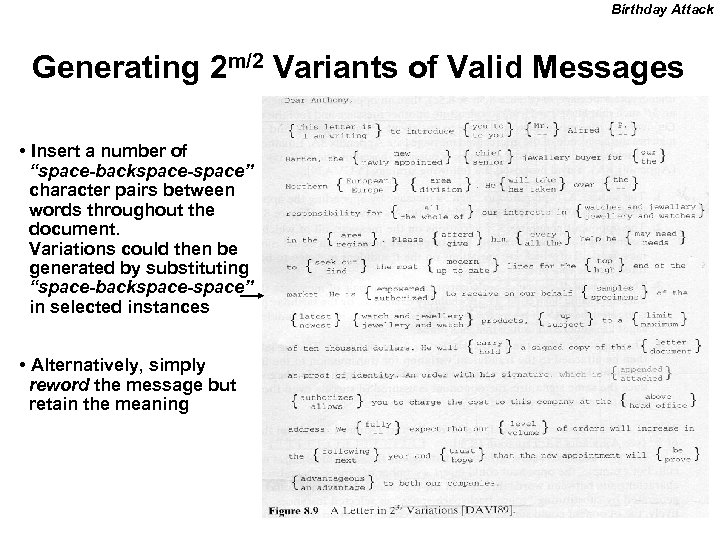 Birthday Attack Generating 2 m/2 Variants of Valid Messages • Insert a number of “space-backspace-space” character pairs between words throughout the document. Variations could then be generated by substituting “space-backspace-space” in selected instances • Alternatively, simply reword the message but retain the meaning
Birthday Attack Generating 2 m/2 Variants of Valid Messages • Insert a number of “space-backspace-space” character pairs between words throughout the document. Variations could then be generated by substituting “space-backspace-space” in selected instances • Alternatively, simply reword the message but retain the meaning
 Security of Hash Functions and MACs • Brute-Force Attack of Hash Functions Three desirable properties of hash functions – One-way: For any given code h, it is computationally infeasible to find x s. t. H(x) = h – Weak collision resistance: For any given block x, it is computationally infeasible to find y x s. t. H(y) = H(x) – Strong collision resistance: It is computationally infeasible to find any pair (x, y) s. t. H(y) = H(x) • Brute-force attack on n-bit hash code – One-way and weak collision require 2 n effort – Strong collision requires 2 n/2 effort – If strong collision resistance is required (and this is desirable for a general-purpose secure hash code), 2 n/2 determines the strength of hash code against brute-force attack – Currently, two most popular hash codes, SHA-1 and RIPEMD 160, provide a 160 -bit hash code length
Security of Hash Functions and MACs • Brute-Force Attack of Hash Functions Three desirable properties of hash functions – One-way: For any given code h, it is computationally infeasible to find x s. t. H(x) = h – Weak collision resistance: For any given block x, it is computationally infeasible to find y x s. t. H(y) = H(x) – Strong collision resistance: It is computationally infeasible to find any pair (x, y) s. t. H(y) = H(x) • Brute-force attack on n-bit hash code – One-way and weak collision require 2 n effort – Strong collision requires 2 n/2 effort – If strong collision resistance is required (and this is desirable for a general-purpose secure hash code), 2 n/2 determines the strength of hash code against brute-force attack – Currently, two most popular hash codes, SHA-1 and RIPEMD 160, provide a 160 -bit hash code length
 Message Authentication Code • generated by an algorithm that creates a small fixed-sized block – depending on both message and some key – like encryption though need not be reversible • appended to message as a signature • receiver performs same computation on message and checks it matches the MAC • provides assurance that message is unaltered and comes from sender
Message Authentication Code • generated by an algorithm that creates a small fixed-sized block – depending on both message and some key – like encryption though need not be reversible • appended to message as a signature • receiver performs same computation on message and checks it matches the MAC • provides assurance that message is unaltered and comes from sender
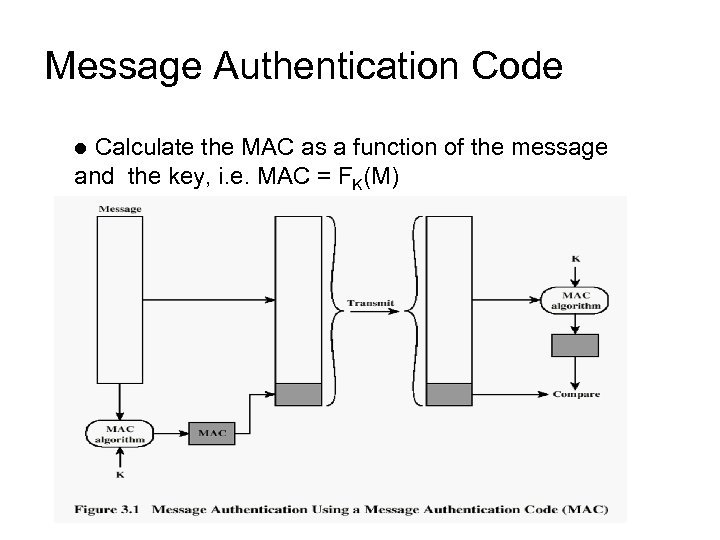 Message Authentication Code Calculate the MAC as a function of the message and the key, i. e. MAC = FK(M) l
Message Authentication Code Calculate the MAC as a function of the message and the key, i. e. MAC = FK(M) l
 MAC Properties • a MAC is a cryptographic checksum MAC = FK(M) – condenses a variable-length message M – using a secret key K – to a fixed-sized authenticator • is a many-to-one function – potentially many messages have same MAC – but finding these needs to be very difficult
MAC Properties • a MAC is a cryptographic checksum MAC = FK(M) – condenses a variable-length message M – using a secret key K – to a fixed-sized authenticator • is a many-to-one function – potentially many messages have same MAC – but finding these needs to be very difficult
 Requirements for MACs • • • taking into account the types of attacks need the MAC to satisfy the following: 1. knowing a message and MAC, is infeasible to find another message with same MAC 2. MACs should be uniformly distributed 3. MAC should depend equally on all bits of the message Approaches to constructing MACs – Using DES – HMAC
Requirements for MACs • • • taking into account the types of attacks need the MAC to satisfy the following: 1. knowing a message and MAC, is infeasible to find another message with same MAC 2. MACs should be uniformly distributed 3. MAC should depend equally on all bits of the message Approaches to constructing MACs – Using DES – HMAC
 Hash Functions • condenses arbitrary message to fixed size • usually assume that the hash function is public and not keyed – cf. MAC which is keyed • hash used to detect changes to message • can use in various ways with message • most often to create a digital signature
Hash Functions • condenses arbitrary message to fixed size • usually assume that the hash function is public and not keyed – cf. MAC which is keyed • hash used to detect changes to message • can use in various ways with message • most often to create a digital signature
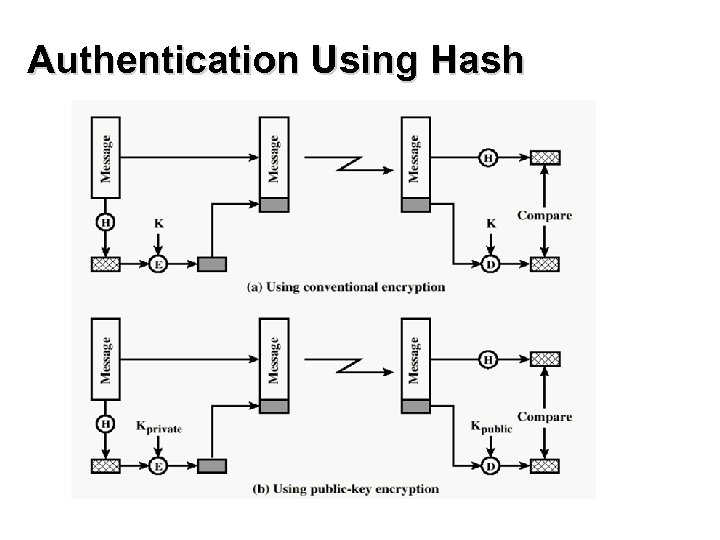 Authentication Using Hash
Authentication Using Hash
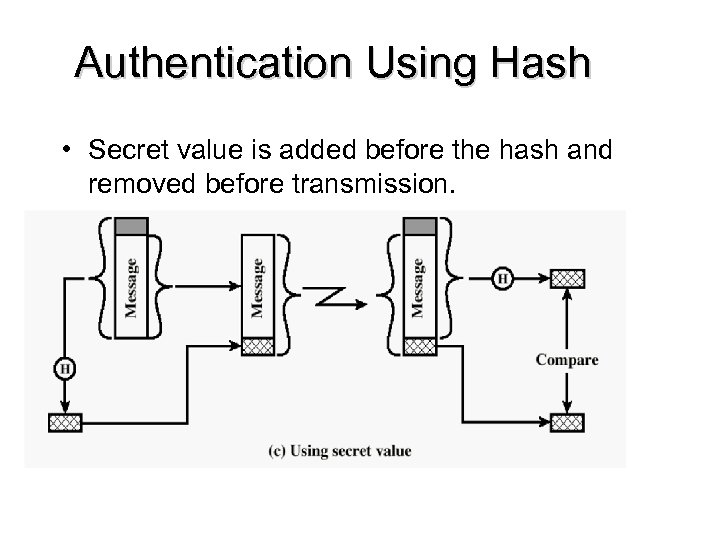 Authentication Using Hash • Secret value is added before the hash and removed before transmission.
Authentication Using Hash • Secret value is added before the hash and removed before transmission.
 Hash Function Properties • a Hash Function produces a fingerprint of some file/message/data h = H(M) – condenses a variable-length message M – to a fixed-sized fingerprint • Hash function assumed to be public
Hash Function Properties • a Hash Function produces a fingerprint of some file/message/data h = H(M) – condenses a variable-length message M – to a fixed-sized fingerprint • Hash function assumed to be public
 Requirements for Hash Functions 1. 2. 3. 4. can be applied to any sized message M produces fixed-length output h is easy to compute h=H(M) for any message M given h is infeasible to find x s. t. H(x)=h • one-way property 5. given x is infeasible to find y s. t. H(y)=H(x) • weak collision resistance 6. is infeasible to find any x, y s. t. H(y)=H(x) • strong collision resistance
Requirements for Hash Functions 1. 2. 3. 4. can be applied to any sized message M produces fixed-length output h is easy to compute h=H(M) for any message M given h is infeasible to find x s. t. H(x)=h • one-way property 5. given x is infeasible to find y s. t. H(y)=H(x) • weak collision resistance 6. is infeasible to find any x, y s. t. H(y)=H(x) • strong collision resistance
 Secure Hash Functions and HMAC • Secure Hash Functions – Secure Hash Algorithm (SHA-1) • NIST standard (FIPS 180 -1), issued in 1995 • Input: message length (<264); Output: 160 -bit MD – MD 5 – RIPEMD-160 • HMAC – Developing a MAC derived from a cryptographic hash code, such as SHA-1. – Used in IP security, Transport Layer Security (TLS) and Secure Electronic Transaction (SET).
Secure Hash Functions and HMAC • Secure Hash Functions – Secure Hash Algorithm (SHA-1) • NIST standard (FIPS 180 -1), issued in 1995 • Input: message length (<264); Output: 160 -bit MD – MD 5 – RIPEMD-160 • HMAC – Developing a MAC derived from a cryptographic hash code, such as SHA-1. – Used in IP security, Transport Layer Security (TLS) and Secure Electronic Transaction (SET).
 Authentication Applications • will consider authentication functions • developed to support application-level authentication & digital signatures • will consider Kerberos – a private-key authentication service • then X. 509 directory authentication service
Authentication Applications • will consider authentication functions • developed to support application-level authentication & digital signatures • will consider Kerberos – a private-key authentication service • then X. 509 directory authentication service
 Hash Algorithms
Hash Algorithms
 Hash Algorithms • see similarities in the evolution of hash functions & block ciphers – increasing power of brute-force attacks – leading to evolution in algorithms – from DES to AES in block ciphers – from MD 4 & MD 5 to SHA-1 & RIPEMD-160 in hash algorithms • likewise tend to use common iterative structure as do block ciphers
Hash Algorithms • see similarities in the evolution of hash functions & block ciphers – increasing power of brute-force attacks – leading to evolution in algorithms – from DES to AES in block ciphers – from MD 4 & MD 5 to SHA-1 & RIPEMD-160 in hash algorithms • likewise tend to use common iterative structure as do block ciphers
 MD 5 • • designed by Ronald Rivest (the R in RSA) latest in a series of MD 2, MD 4 produces a 128 -bit hash value until recently was the most widely used hash algorithm – in recent times have both brute-force & cryptanalytic concerns • specified as Internet standard RFC 1321
MD 5 • • designed by Ronald Rivest (the R in RSA) latest in a series of MD 2, MD 4 produces a 128 -bit hash value until recently was the most widely used hash algorithm – in recent times have both brute-force & cryptanalytic concerns • specified as Internet standard RFC 1321
 MD 5 Overview 1. 2. 3. 4. pad message so its length is 448 mod 512 append a 64 -bit length value to message initialise 4 -word (128 -bit) MD buffer (A, B, C, D) process message in 16 -word (512 -bit) blocks: – using 4 rounds of 16 bit operations on message block & buffer – add output to buffer input to form new buffer value 5. output hash value is the final buffer value
MD 5 Overview 1. 2. 3. 4. pad message so its length is 448 mod 512 append a 64 -bit length value to message initialise 4 -word (128 -bit) MD buffer (A, B, C, D) process message in 16 -word (512 -bit) blocks: – using 4 rounds of 16 bit operations on message block & buffer – add output to buffer input to form new buffer value 5. output hash value is the final buffer value
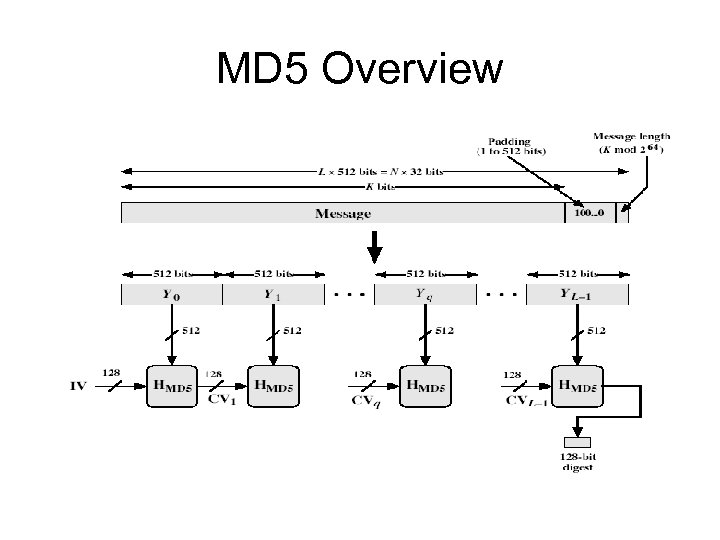 MD 5 Overview
MD 5 Overview
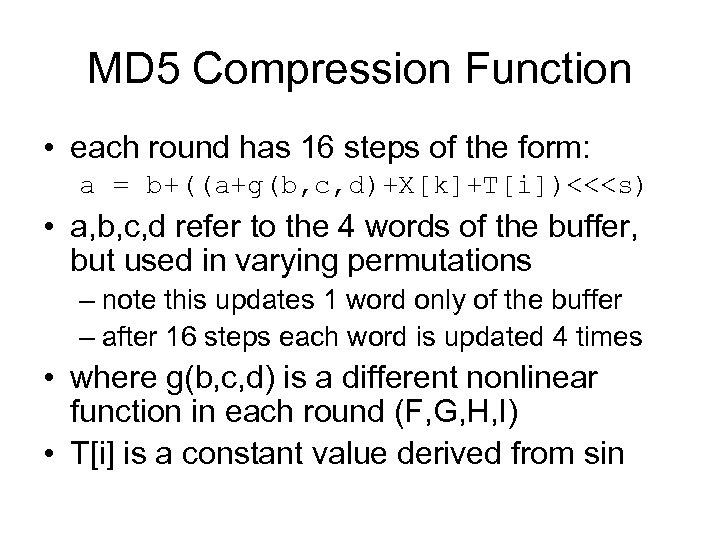 MD 5 Compression Function • each round has 16 steps of the form: a = b+((a+g(b, c, d)+X[k]+T[i])<<
MD 5 Compression Function • each round has 16 steps of the form: a = b+((a+g(b, c, d)+X[k]+T[i])<<
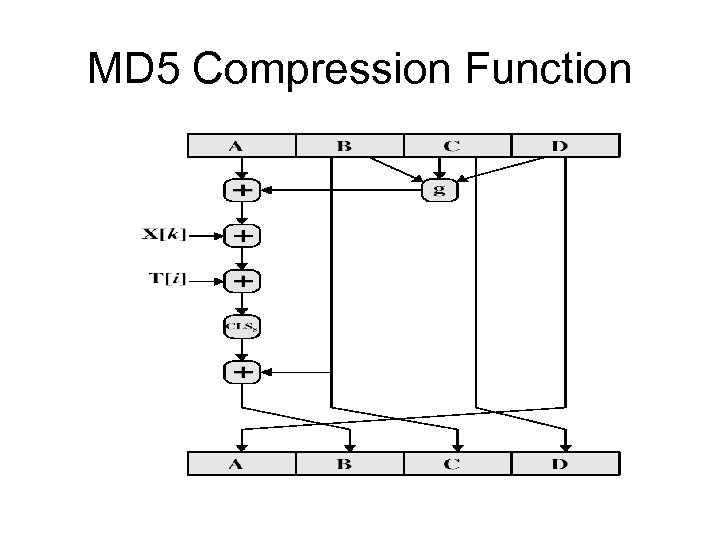 MD 5 Compression Function
MD 5 Compression Function
 MD 4 • • precursor to MD 5 also produces a 128 -bit hash of message has 3 rounds of 16 steps vs 4 in MD 5 design goals: – collision resistant (hard to find collisions) – direct security (no dependence on "hard" problems) – fast, simple, compact – favours little-endian systems (eg PCs)
MD 4 • • precursor to MD 5 also produces a 128 -bit hash of message has 3 rounds of 16 steps vs 4 in MD 5 design goals: – collision resistant (hard to find collisions) – direct security (no dependence on "hard" problems) – fast, simple, compact – favours little-endian systems (eg PCs)
 Strength of MD 5 • MD 5 hash is dependent on all message bits • Rivest claims security is good as can be • known attacks are: – Berson 92 attacked any 1 round using differential cryptanalysis (but can’t extend) – Boer & Bosselaers 93 found a pseudo collision (again unable to extend) – Dobbertin 96 created collisions on MD compression function (but initial constants prevent exploit) • conclusion is that MD 5 looks vulnerable soon
Strength of MD 5 • MD 5 hash is dependent on all message bits • Rivest claims security is good as can be • known attacks are: – Berson 92 attacked any 1 round using differential cryptanalysis (but can’t extend) – Boer & Bosselaers 93 found a pseudo collision (again unable to extend) – Dobbertin 96 created collisions on MD compression function (but initial constants prevent exploit) • conclusion is that MD 5 looks vulnerable soon
 Secure Hash Algorithm (SHA-1) • SHA was designed by NIST & NSA in 1993, revised 1995 as SHA-1 • US standard for use with DSA signature scheme – standard is FIPS 180 -1 1995, also Internet RFC 3174 – nb. the algorithm is SHA, the standard is SHS • produces 160 -bit hash values • now the generally preferred hash algorithm • based on design of MD 4 with key differences
Secure Hash Algorithm (SHA-1) • SHA was designed by NIST & NSA in 1993, revised 1995 as SHA-1 • US standard for use with DSA signature scheme – standard is FIPS 180 -1 1995, also Internet RFC 3174 – nb. the algorithm is SHA, the standard is SHS • produces 160 -bit hash values • now the generally preferred hash algorithm • based on design of MD 4 with key differences
 SHA Overview 1. pad message so its length is 448 mod 512 2. append a 64 -bit length value to message 3. initialise 5 -word (160 -bit) buffer (A, B, C, D, E) to (67452301, efcdab 89, 98 badcfe, 10325476, c 3 d 2 e 1 f 0) 4. process message in 16 -word (512 -bit) chunks: – expand 16 words into 80 words by mixing & shifting – use 4 rounds of 20 bit operations on message block & buffer – add output to input to form new buffer value 5. output hash value is the final buffer value
SHA Overview 1. pad message so its length is 448 mod 512 2. append a 64 -bit length value to message 3. initialise 5 -word (160 -bit) buffer (A, B, C, D, E) to (67452301, efcdab 89, 98 badcfe, 10325476, c 3 d 2 e 1 f 0) 4. process message in 16 -word (512 -bit) chunks: – expand 16 words into 80 words by mixing & shifting – use 4 rounds of 20 bit operations on message block & buffer – add output to input to form new buffer value 5. output hash value is the final buffer value
 SHA-1 Compression Function • each round has 20 steps which replaces the 5 buffer words thus: (A, B, C, D, E) <(E+f(t, B, C, D)+(A<<5)+Wt+Kt), A, (B<<30), C, D) • a, b, c, d refer to the 4 words of the buffer • t is the step number • f(t, B, C, D) is nonlinear function for round • Wt is derived from the message block • Kt is a constant value derived from sin
SHA-1 Compression Function • each round has 20 steps which replaces the 5 buffer words thus: (A, B, C, D, E) <(E+f(t, B, C, D)+(A<<5)+Wt+Kt), A, (B<<30), C, D) • a, b, c, d refer to the 4 words of the buffer • t is the step number • f(t, B, C, D) is nonlinear function for round • Wt is derived from the message block • Kt is a constant value derived from sin
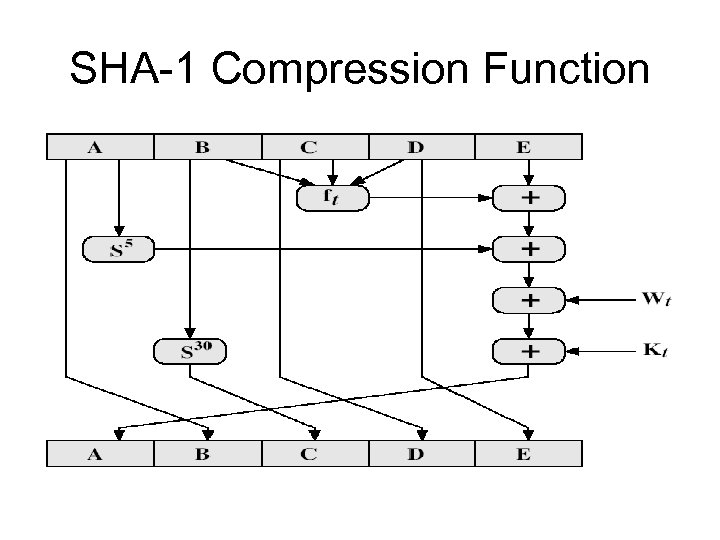 SHA-1 Compression Function
SHA-1 Compression Function
 SHA-1 verses MD 5 • brute force attack is harder (160 vs 128 bits for MD 5) • not vulnerable to any known attacks (compared to MD 4/5) • a little slower than MD 5 (80 vs 64 steps) • both designed as simple and compact • optimised for big endian CPU's (vs MD 5 which is optimised for little endian CPU’s)
SHA-1 verses MD 5 • brute force attack is harder (160 vs 128 bits for MD 5) • not vulnerable to any known attacks (compared to MD 4/5) • a little slower than MD 5 (80 vs 64 steps) • both designed as simple and compact • optimised for big endian CPU's (vs MD 5 which is optimised for little endian CPU’s)
 Hash Algorithms
Hash Algorithms
 Revised Secure Hash Standard • • NIST have issued a revision FIPS 180 -2 adds 3 additional hash algorithms SHA-256, SHA-384, SHA-512 designed for compatibility with increased security provided by the AES cipher • structure & detail is similar to SHA-1 • hence analysis should be similar
Revised Secure Hash Standard • • NIST have issued a revision FIPS 180 -2 adds 3 additional hash algorithms SHA-256, SHA-384, SHA-512 designed for compatibility with increased security provided by the AES cipher • structure & detail is similar to SHA-1 • hence analysis should be similar
 RIPEMD-160 • RIPEMD-160 was developed in Europe as part of RIPE project in 96 • by researchers involved in attacks on MD 4/5 • initial proposal strengthen following analysis to become RIPEMD-160 • somewhat similar to MD 5/SHA • uses 2 parallel lines of 5 rounds of 16 steps • creates a 160 -bit hash value • slower, but probably more secure, than SHA
RIPEMD-160 • RIPEMD-160 was developed in Europe as part of RIPE project in 96 • by researchers involved in attacks on MD 4/5 • initial proposal strengthen following analysis to become RIPEMD-160 • somewhat similar to MD 5/SHA • uses 2 parallel lines of 5 rounds of 16 steps • creates a 160 -bit hash value • slower, but probably more secure, than SHA
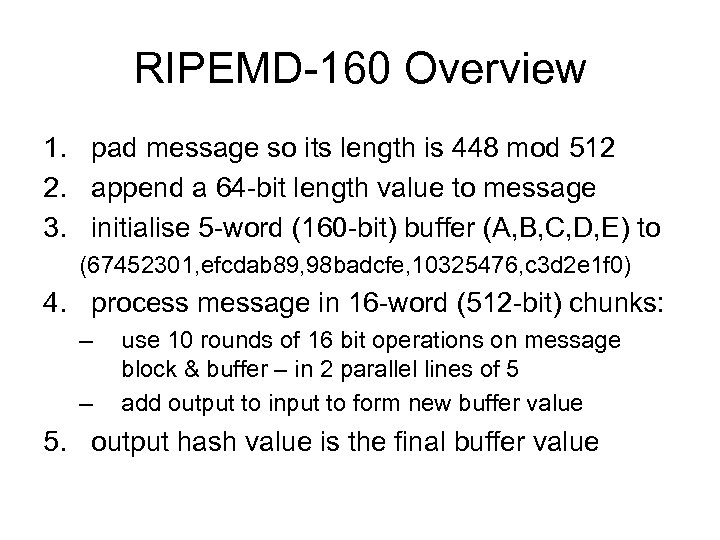 RIPEMD-160 Overview 1. pad message so its length is 448 mod 512 2. append a 64 -bit length value to message 3. initialise 5 -word (160 -bit) buffer (A, B, C, D, E) to (67452301, efcdab 89, 98 badcfe, 10325476, c 3 d 2 e 1 f 0) 4. process message in 16 -word (512 -bit) chunks: – – use 10 rounds of 16 bit operations on message block & buffer – in 2 parallel lines of 5 add output to input to form new buffer value 5. output hash value is the final buffer value
RIPEMD-160 Overview 1. pad message so its length is 448 mod 512 2. append a 64 -bit length value to message 3. initialise 5 -word (160 -bit) buffer (A, B, C, D, E) to (67452301, efcdab 89, 98 badcfe, 10325476, c 3 d 2 e 1 f 0) 4. process message in 16 -word (512 -bit) chunks: – – use 10 rounds of 16 bit operations on message block & buffer – in 2 parallel lines of 5 add output to input to form new buffer value 5. output hash value is the final buffer value
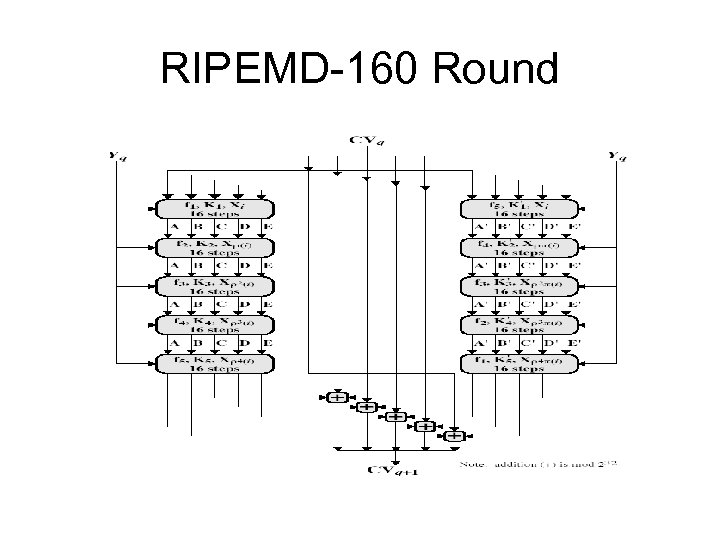 RIPEMD-160 Round
RIPEMD-160 Round
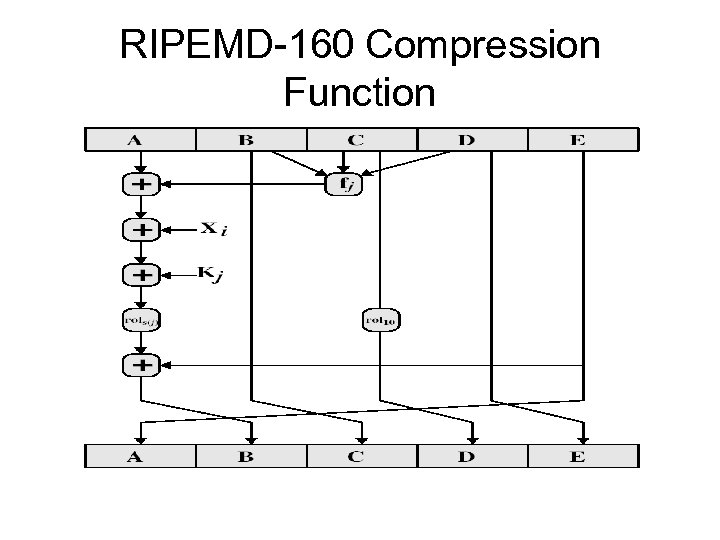 RIPEMD-160 Compression Function
RIPEMD-160 Compression Function
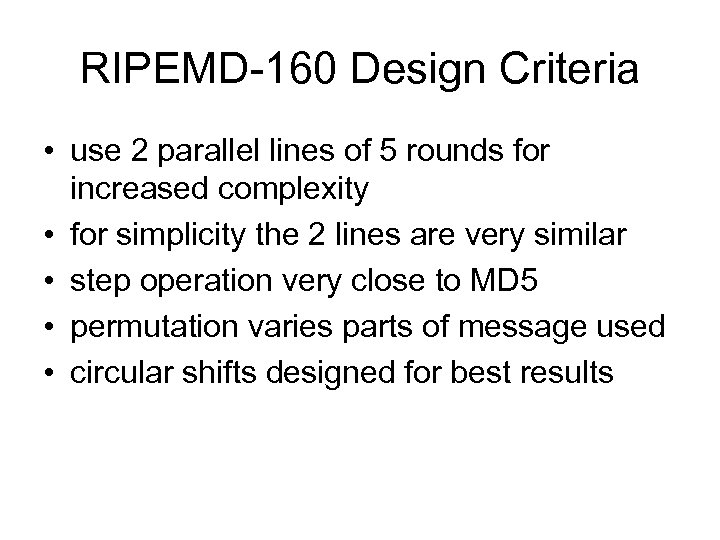 RIPEMD-160 Design Criteria • use 2 parallel lines of 5 rounds for increased complexity • for simplicity the 2 lines are very similar • step operation very close to MD 5 • permutation varies parts of message used • circular shifts designed for best results
RIPEMD-160 Design Criteria • use 2 parallel lines of 5 rounds for increased complexity • for simplicity the 2 lines are very similar • step operation very close to MD 5 • permutation varies parts of message used • circular shifts designed for best results
 RIPEMD-160 verses MD 5 & SHA-1 • brute force attack harder (160 like SHA-1 vs 128 bits for MD 5) • not vulnerable to known attacks, like SHA 1 though stronger (compared to MD 4/5) • slower than MD 5 (more steps) • all designed as simple and compact • SHA-1 optimised for big endian CPU's vs RIPEMD-160 & MD 5 optimised for little endian CPU’s
RIPEMD-160 verses MD 5 & SHA-1 • brute force attack harder (160 like SHA-1 vs 128 bits for MD 5) • not vulnerable to known attacks, like SHA 1 though stronger (compared to MD 4/5) • slower than MD 5 (more steps) • all designed as simple and compact • SHA-1 optimised for big endian CPU's vs RIPEMD-160 & MD 5 optimised for little endian CPU’s
 Keyed Hash Functions as MACs • have desire to create a MAC using a hash function rather than a block cipher – because hash functions are generally faster – not limited by export controls unlike block ciphers • hash includes a key along with the message • original proposal: Keyed. Hash = Hash(Key|Message) – some weaknesses were found with this • eventually led to development of HMAC
Keyed Hash Functions as MACs • have desire to create a MAC using a hash function rather than a block cipher – because hash functions are generally faster – not limited by export controls unlike block ciphers • hash includes a key along with the message • original proposal: Keyed. Hash = Hash(Key|Message) – some weaknesses were found with this • eventually led to development of HMAC
 HMAC • specified as Internet standard RFC 2104 • uses hash function on the message: HMACK = Hash[(K+ XOR opad) || Hash[(K+ XOR ipad)||M)]] • where K+ is the key padded out to size • and opad, ipad are specified padding constants • overhead is just 3 more hash calculations than the message needs alone • any of MD 5, SHA-1, RIPEMD-160 can be used
HMAC • specified as Internet standard RFC 2104 • uses hash function on the message: HMACK = Hash[(K+ XOR opad) || Hash[(K+ XOR ipad)||M)]] • where K+ is the key padded out to size • and opad, ipad are specified padding constants • overhead is just 3 more hash calculations than the message needs alone • any of MD 5, SHA-1, RIPEMD-160 can be used
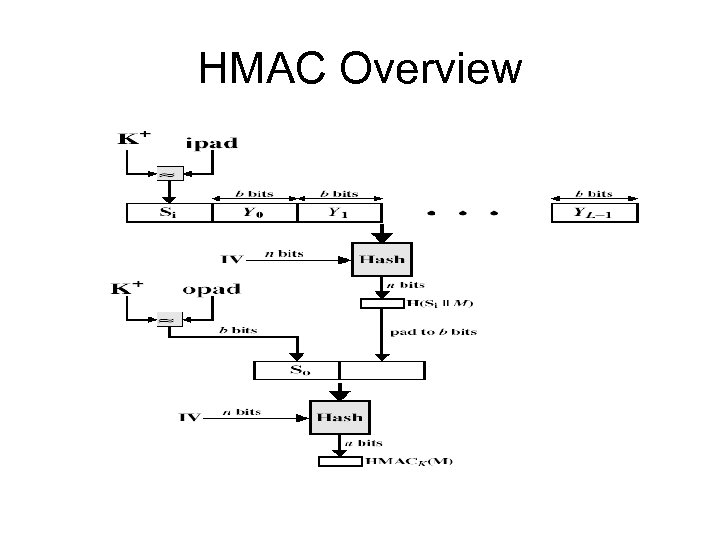 HMAC Overview
HMAC Overview
 HMAC Security • know that the security of HMAC relates to that of the underlying hash algorithm • attacking HMAC requires either: – brute force attack on key used – birthday attack (but since keyed would need to observe a very large number of messages) • choose hash function used based on speed verses security constraints
HMAC Security • know that the security of HMAC relates to that of the underlying hash algorithm • attacking HMAC requires either: – brute force attack on key used – birthday attack (but since keyed would need to observe a very large number of messages) • choose hash function used based on speed verses security constraints
 Summary • have considered: – some current hash algorithms: MD 5, SHA-1, RIPEMD-160 – HMAC authentication using hash function
Summary • have considered: – some current hash algorithms: MD 5, SHA-1, RIPEMD-160 – HMAC authentication using hash function


