7ed37db0437448a9d556232b5613228f.ppt
- Количество слайдов: 132
 Cryptography and Network Security UNIT IV - NETWORK SECURITY
Cryptography and Network Security UNIT IV - NETWORK SECURITY
 Authentication Functions Ø Message authentication or digital signature mechanism can be viewed as having two levels At lower level: there must be some sort of functions producing an authenticator – a value to be used to authenticate a message l This lower level functions is used as primitive in a higher level authentication protocol l
Authentication Functions Ø Message authentication or digital signature mechanism can be viewed as having two levels At lower level: there must be some sort of functions producing an authenticator – a value to be used to authenticate a message l This lower level functions is used as primitive in a higher level authentication protocol l
 Authentication Functions Ø Three classes of functions that may be used to produce an authenticator l Message encryption • Ciphertext itself serves as authenticator l Message authentication code (MAC) • A public function of the message and a secret key that produces a fixed-length value that serves as the authenticator l Hash function • A public function that maps a message of any length into a fixed-length hash value, which serves as the authenticator
Authentication Functions Ø Three classes of functions that may be used to produce an authenticator l Message encryption • Ciphertext itself serves as authenticator l Message authentication code (MAC) • A public function of the message and a secret key that produces a fixed-length value that serves as the authenticator l Hash function • A public function that maps a message of any length into a fixed-length hash value, which serves as the authenticator
 KERBEROS In Greek mythology, a many headed dog, the guardian of the entrance of Hades
KERBEROS In Greek mythology, a many headed dog, the guardian of the entrance of Hades
 KERBEROS Ø Users wish to access services on servers. Ø Three threats exist: l User pretends to be another user. l User alters the network address of a workstation. l User eavesdrops on exchanges and uses a replay attack.
KERBEROS Ø Users wish to access services on servers. Ø Three threats exist: l User pretends to be another user. l User alters the network address of a workstation. l User eavesdrops on exchanges and uses a replay attack.
 KERBEROS Ø Provides a centralized authentication server to authenticate users to servers and servers to users. Ø Relies on conventional encryption, making no use of public-key encryption Ø Two versions: version 4 and 5 Ø Version 4 makes use of DES
KERBEROS Ø Provides a centralized authentication server to authenticate users to servers and servers to users. Ø Relies on conventional encryption, making no use of public-key encryption Ø Two versions: version 4 and 5 Ø Version 4 makes use of DES
 Kerberos Version 4 Ø Terms: l l l l l C = Client AS = authentication server V = server IDc = identifier of user on C IDv = identifier of V Pc = password of user on C ADc = network address of C Kv = secret encryption key shared by AS and V TS = timestamp || = concatenation
Kerberos Version 4 Ø Terms: l l l l l C = Client AS = authentication server V = server IDc = identifier of user on C IDv = identifier of V Pc = password of user on C ADc = network address of C Kv = secret encryption key shared by AS and V TS = timestamp || = concatenation
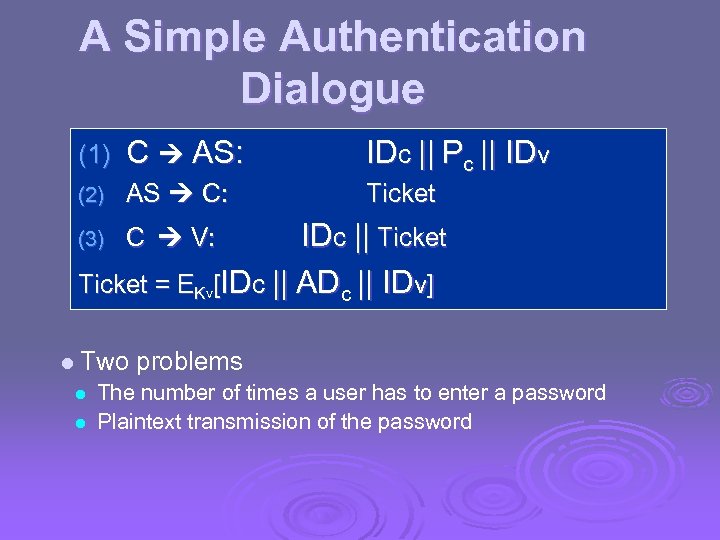 A Simple Authentication Dialogue (1) C AS: IDc || Pc || IDv (2) AS C: Ticket (3) C V: IDc || Ticket = EKv[IDc || ADc || IDv] l Two problems l l The number of times a user has to enter a password Plaintext transmission of the password
A Simple Authentication Dialogue (1) C AS: IDc || Pc || IDv (2) AS C: Ticket (3) C V: IDc || Ticket = EKv[IDc || ADc || IDv] l Two problems l l The number of times a user has to enter a password Plaintext transmission of the password
 The Idea towards Solution Ø Introducing a ticket-granting server (TGS) l The user first requests a ticket-granting ticket (Tickettgs) from the AS; l The user then authenticates itself to TGS for a ticket (Ticketv) for accessing new service; l The user finally authenticate itself to V for requesting a particular service.
The Idea towards Solution Ø Introducing a ticket-granting server (TGS) l The user first requests a ticket-granting ticket (Tickettgs) from the AS; l The user then authenticates itself to TGS for a ticket (Ticketv) for accessing new service; l The user finally authenticate itself to V for requesting a particular service.
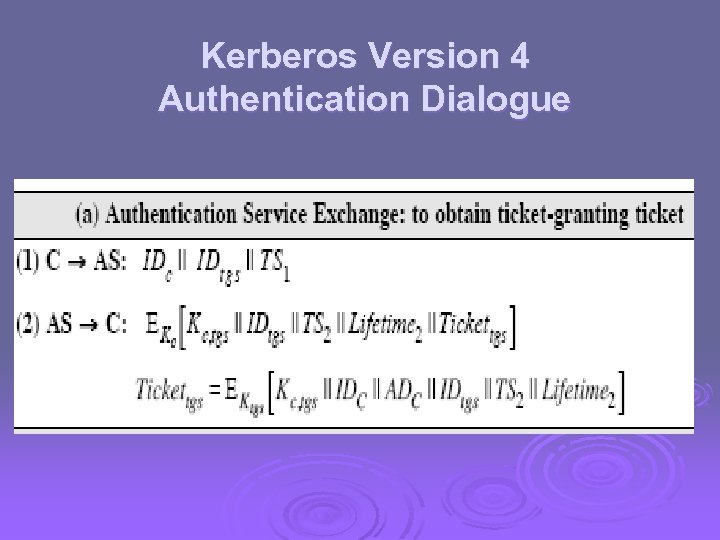 Kerberos Version 4 Authentication Dialogue
Kerberos Version 4 Authentication Dialogue
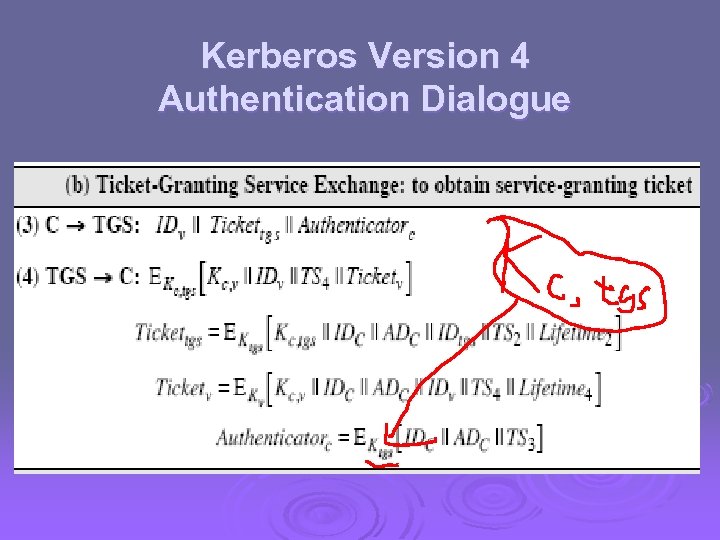 Kerberos Version 4 Authentication Dialogue
Kerberos Version 4 Authentication Dialogue
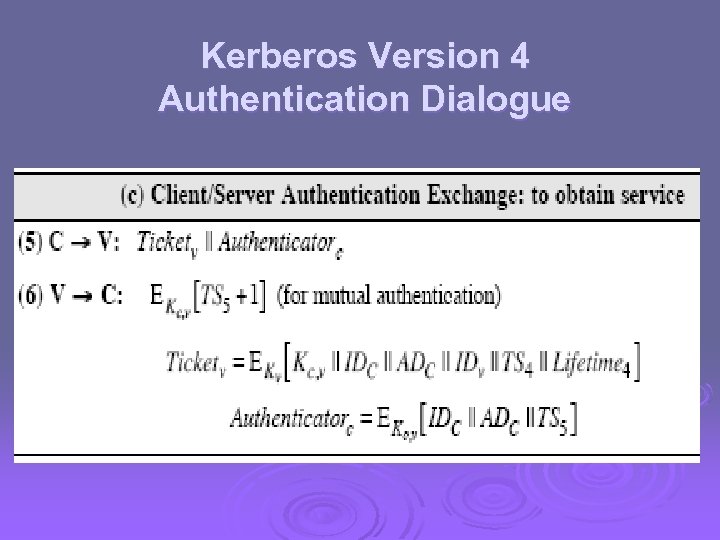 Kerberos Version 4 Authentication Dialogue
Kerberos Version 4 Authentication Dialogue
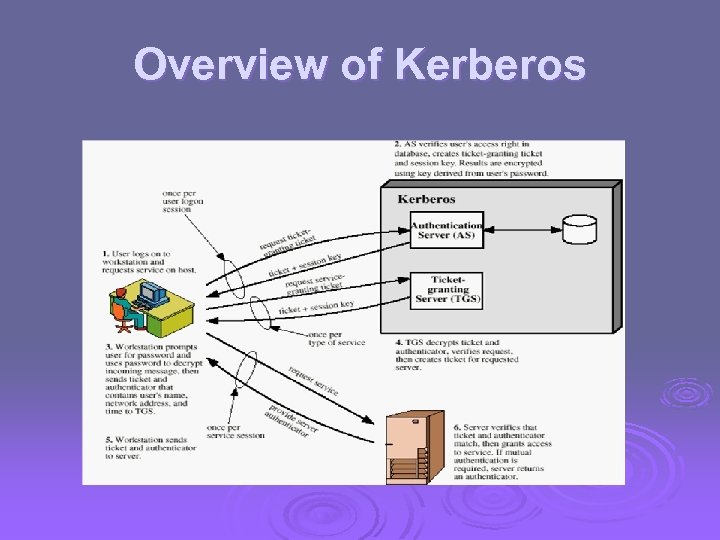 Overview of Kerberos
Overview of Kerberos
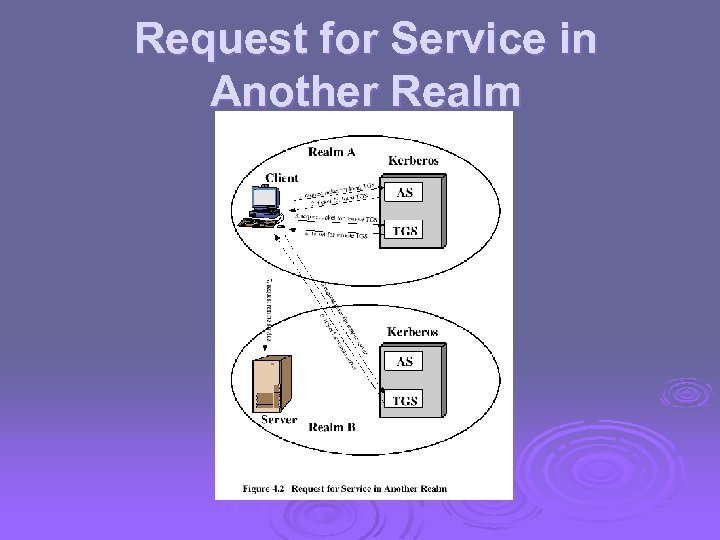 Request for Service in Another Realm
Request for Service in Another Realm
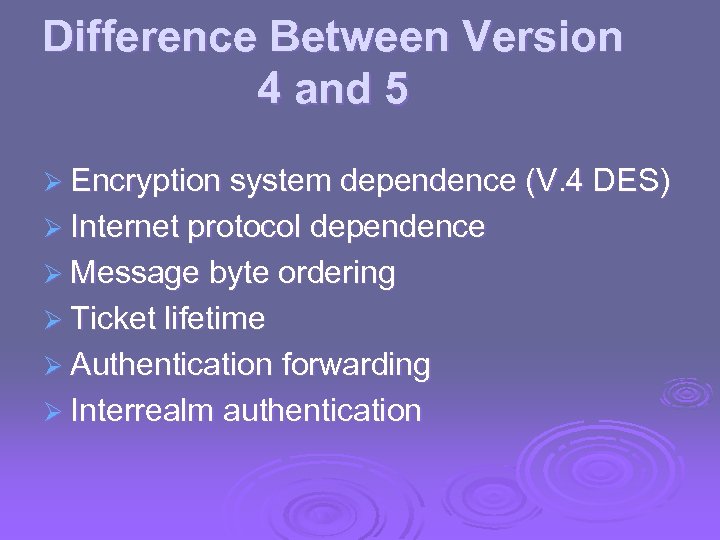 Difference Between Version 4 and 5 Ø Encryption system dependence (V. 4 DES) Ø Internet protocol dependence Ø Message byte ordering Ø Ticket lifetime Ø Authentication forwarding Ø Interrealm authentication
Difference Between Version 4 and 5 Ø Encryption system dependence (V. 4 DES) Ø Internet protocol dependence Ø Message byte ordering Ø Ticket lifetime Ø Authentication forwarding Ø Interrealm authentication
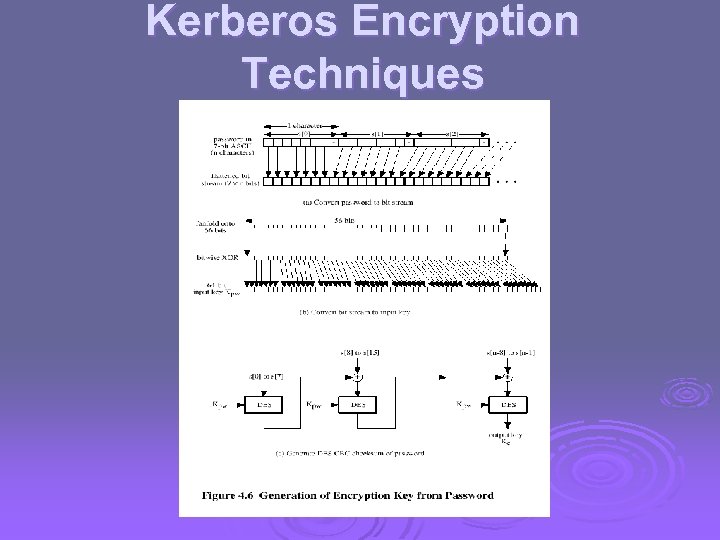 Kerberos Encryption Techniques
Kerberos Encryption Techniques
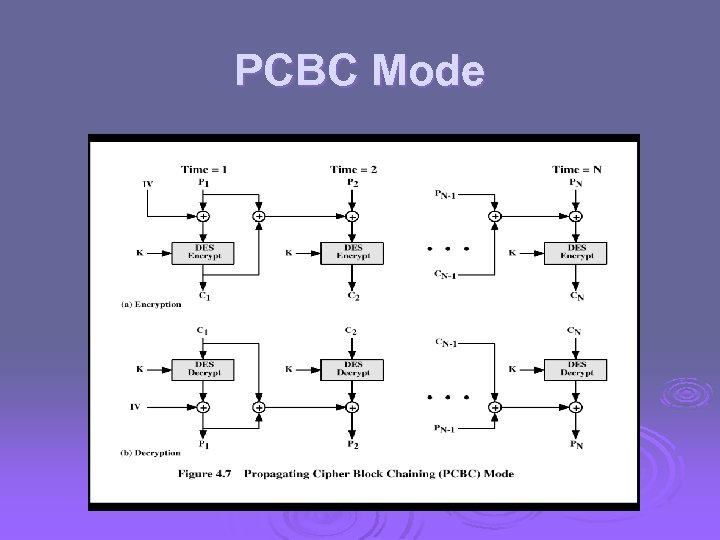 PCBC Mode
PCBC Mode
 Ø Kerberos - in practice Currently have two Kerberos versions: 4 : restricted to a single realm l 5 : allows inter-realm authentication, in beta test l Kerberos v 5 is an Internet standard l specified in RFC 1510, and used by many utilities l Ø To use Kerberos: l l l need to have a KDC on your network need to have Kerberised applications running on all participating systems major problem - US export restrictions Kerberos cannot be directly distributed outside the US in source format (& binary versions must obscure crypto routine entry points and have no encryption) else crypto libraries must be reimplemented locally
Ø Kerberos - in practice Currently have two Kerberos versions: 4 : restricted to a single realm l 5 : allows inter-realm authentication, in beta test l Kerberos v 5 is an Internet standard l specified in RFC 1510, and used by many utilities l Ø To use Kerberos: l l l need to have a KDC on your network need to have Kerberised applications running on all participating systems major problem - US export restrictions Kerberos cannot be directly distributed outside the US in source format (& binary versions must obscure crypto routine entry points and have no encryption) else crypto libraries must be reimplemented locally
 X. 509 Authentication Service Distributed set of servers that maintains a database about users. Ø Each certificate contains the public key of a user and is signed with the private key of a CA. Ø Is used in S/MIME, IP Security, SSL/TLS and SET. Ø RSA is recommended to use. Ø
X. 509 Authentication Service Distributed set of servers that maintains a database about users. Ø Each certificate contains the public key of a user and is signed with the private key of a CA. Ø Is used in S/MIME, IP Security, SSL/TLS and SET. Ø RSA is recommended to use. Ø
 X. 509 Authentication Service Distributed set of servers that maintains a database about users. Ø Each certificate contains the public key of a user and is signed with the private key of a CA. Ø Is used in S/MIME, IP Security, SSL/TLS and SET. Ø RSA is recommended to use. Ø
X. 509 Authentication Service Distributed set of servers that maintains a database about users. Ø Each certificate contains the public key of a user and is signed with the private key of a CA. Ø Is used in S/MIME, IP Security, SSL/TLS and SET. Ø RSA is recommended to use. Ø
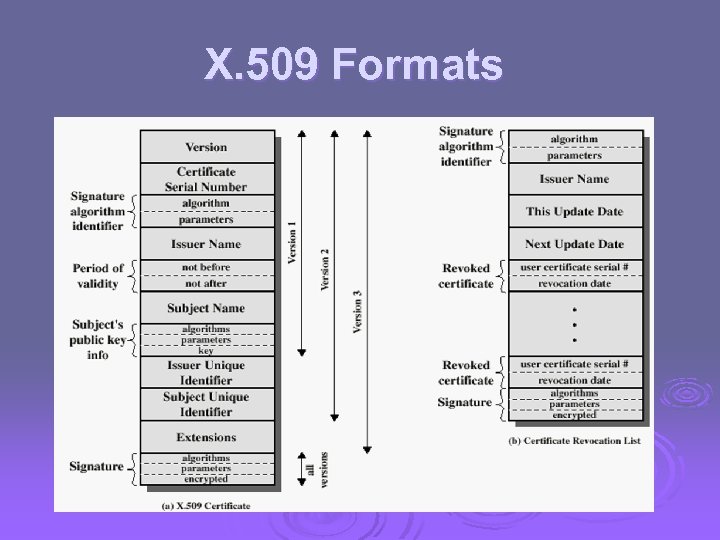 X. 509 Formats
X. 509 Formats
 Obtaining a User’s Certificate Ø Characteristics of certificates generated by CA: l Any user with access to the public key of the CA can recover the user public key that was certified. l No part other than the CA can modify the certificate without this being detected.
Obtaining a User’s Certificate Ø Characteristics of certificates generated by CA: l Any user with access to the public key of the CA can recover the user public key that was certified. l No part other than the CA can modify the certificate without this being detected.
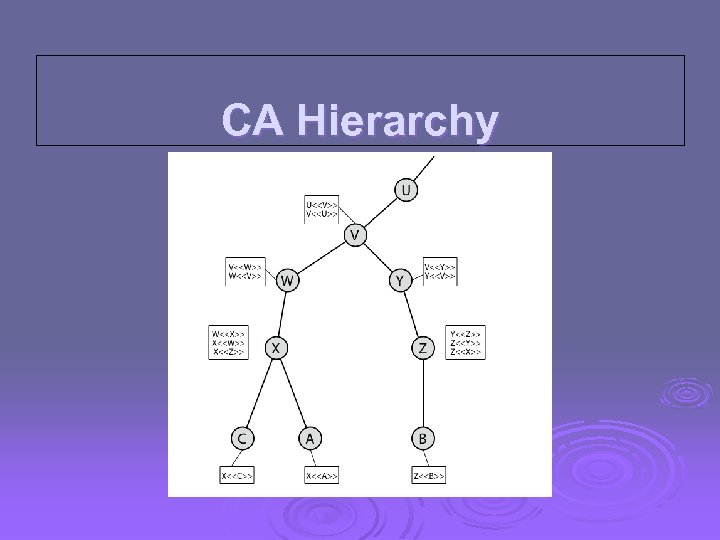
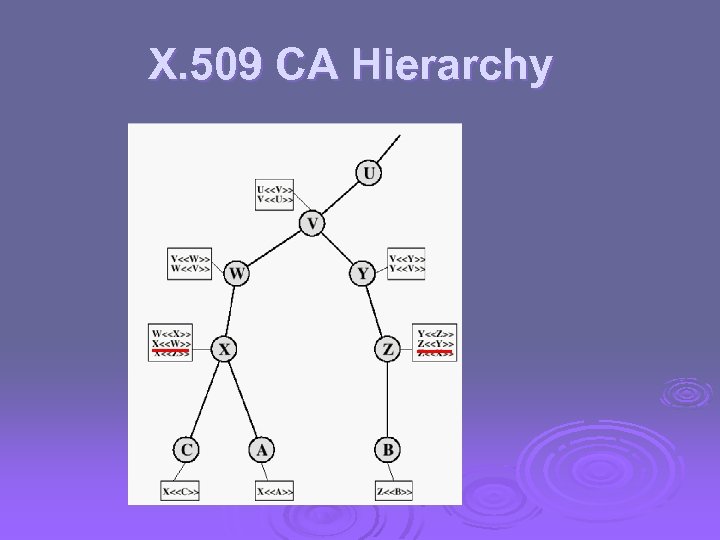 X. 509 CA Hierarchy
X. 509 CA Hierarchy
 Revocation of Certificates Ø Reasons for revocation: l The users secret key is assumed to be compromised. l The user is no longer certified by this CA. l The CA’s certificate is assumed to be compromised.
Revocation of Certificates Ø Reasons for revocation: l The users secret key is assumed to be compromised. l The user is no longer certified by this CA. l The CA’s certificate is assumed to be compromised.
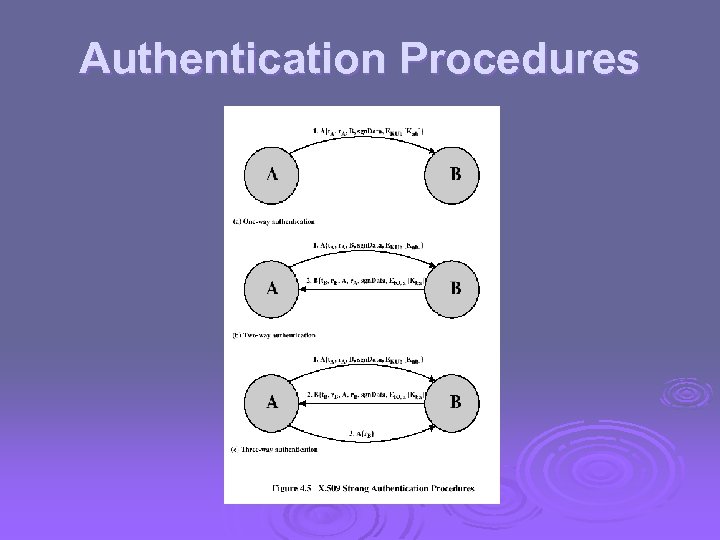 Authentication Procedures
Authentication Procedures
 Summary Ø have considered: l message authentication using message encryption • MACs • hash functions • l Kerberos l X. 509 Authentication Service
Summary Ø have considered: l message authentication using message encryption • MACs • hash functions • l Kerberos l X. 509 Authentication Service

 Authentication Applications Ø Developed to support application-level authentication and digital signatures Ø Most widely used services: l Kerberos l X. 509 Ø Kerberos – a private-key authentication service Ø X. 509 – a public-key directory authentication service
Authentication Applications Ø Developed to support application-level authentication and digital signatures Ø Most widely used services: l Kerberos l X. 509 Ø Kerberos – a private-key authentication service Ø X. 509 – a public-key directory authentication service
 Kerberos
Kerberos
 Kerberos Ø Developed as part of Project Athena at MIT Ø Symmetric encryption l using no public keys Ø Provides centralised private-key third-party authentication in a distributed network Ø Version 4 and 5
Kerberos Ø Developed as part of Project Athena at MIT Ø Symmetric encryption l using no public keys Ø Provides centralised private-key third-party authentication in a distributed network Ø Version 4 and 5
 Kerberos Motivation Ø Provide security in a distributed architecture consisting of dedicated user workstations (clients), and distributed or centralized servers Ø Require the user to prove his identity for each service invoked Ø Require that servers prove their identity to clients Ø Secure, Reliable, Transparent, and
Kerberos Motivation Ø Provide security in a distributed architecture consisting of dedicated user workstations (clients), and distributed or centralized servers Ø Require the user to prove his identity for each service invoked Ø Require that servers prove their identity to clients Ø Secure, Reliable, Transparent, and
 Kerberos Scheme Ø Trusted third party authentication service Ø Uses a protocol based on Needham and Schroeder [NEED 78], see Chapter 7 Ø Clients and servers trust Kerberos to mediate their mutual authentication
Kerberos Scheme Ø Trusted third party authentication service Ø Uses a protocol based on Needham and Schroeder [NEED 78], see Chapter 7 Ø Clients and servers trust Kerberos to mediate their mutual authentication
 Kerberos Version 4 Ø Uses DES, in a rather elaborate protocol, to provide authentication Ø Uses an Authentication Server (AS) l Knows all user passwords, and stores in a DB l Shares a unique secret key with each server l Send an encrypted ticket granting ticket l TGT contains a lifetime and timestamp
Kerberos Version 4 Ø Uses DES, in a rather elaborate protocol, to provide authentication Ø Uses an Authentication Server (AS) l Knows all user passwords, and stores in a DB l Shares a unique secret key with each server l Send an encrypted ticket granting ticket l TGT contains a lifetime and timestamp
 Kerberos Version 4 Ø Uses a Ticket Granting Server (TGS) l Issues tickets to users authenticated by AS l Encrypted with a key only known by AS and TGS l Returns a service granting ticket Ø Service granting ticket contains timestamp and lifetime
Kerberos Version 4 Ø Uses a Ticket Granting Server (TGS) l Issues tickets to users authenticated by AS l Encrypted with a key only known by AS and TGS l Returns a service granting ticket Ø Service granting ticket contains timestamp and lifetime
 Kerberos Dialog Ø Problem: lifetime and no server authenticate to user Ø Uses a session key Ø Message Exchanges (see table 14. 1) l AS exchange to obtain ticket-granting ticket l TGS exchange to obtain service granting ticket l Client/Server authentication exchange to obtain service
Kerberos Dialog Ø Problem: lifetime and no server authenticate to user Ø Uses a session key Ø Message Exchanges (see table 14. 1) l AS exchange to obtain ticket-granting ticket l TGS exchange to obtain service granting ticket l Client/Server authentication exchange to obtain service
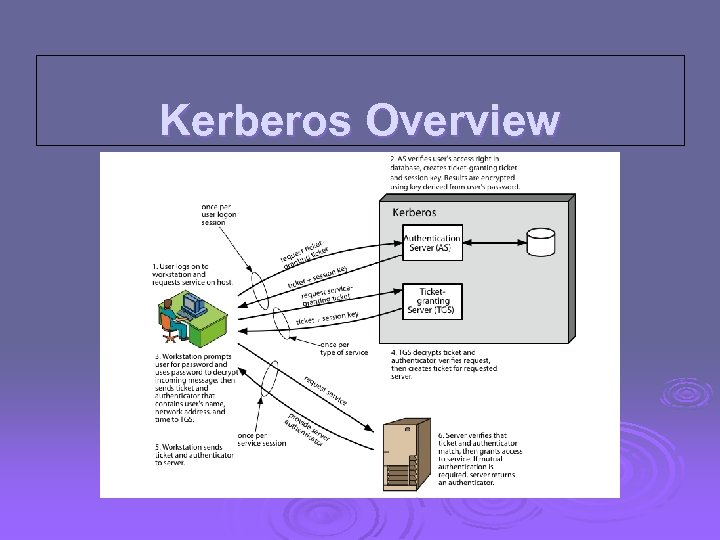 Kerberos Overview
Kerberos Overview
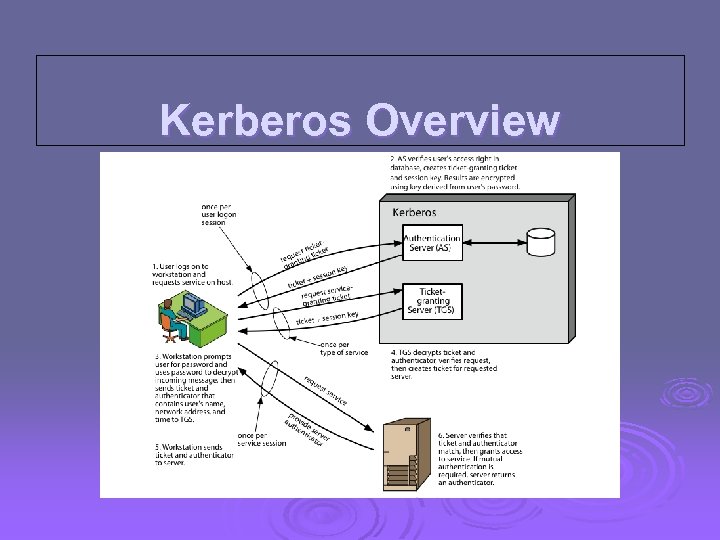 Kerberos Overview
Kerberos Overview
 Multiple Kerberi Ø Kerberos server in each realm shares a secret key with one another Ø There must be trust between the servers Ø i. e. each server are registered with one another Ø Does not scale well
Multiple Kerberi Ø Kerberos server in each realm shares a secret key with one another Ø There must be trust between the servers Ø i. e. each server are registered with one another Ø Does not scale well
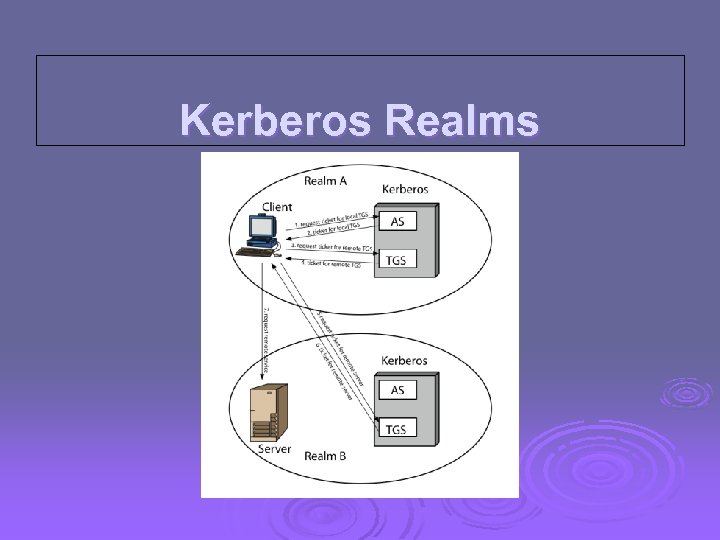 Kerberos Realms
Kerberos Realms
 Kerberos Version 5 Ø Fixes version 4 environmental shortcomings Ø New elements for AS exchange: l Realm, Options, Times, Nonce Ø Client/server authentication exchange l Subkey, sequence number Ø Kerberos Ticket Flags (see table 14. 4)
Kerberos Version 5 Ø Fixes version 4 environmental shortcomings Ø New elements for AS exchange: l Realm, Options, Times, Nonce Ø Client/server authentication exchange l Subkey, sequence number Ø Kerberos Ticket Flags (see table 14. 4)
 X. 509 part of X. 500 series l distributed servers maintaining user information database Ø defines framework for authentication services l directory may store public-key certificates l with public key of user signed by certification authority Ø also defines authentication protocols Ø
X. 509 part of X. 500 series l distributed servers maintaining user information database Ø defines framework for authentication services l directory may store public-key certificates l with public key of user signed by certification authority Ø also defines authentication protocols Ø
 X. 509 uses public-key cryptology & digital signatures l algorithms not standardised, but RSA recommended Ø X. 509 certificates are widely used Ø Public key certificate associated with each user l Generated by some trusted CA Ø Certification Authority (CA) issues certificates Ø The notation CA<> represents a certificate for a client A signed by CA Ø
X. 509 uses public-key cryptology & digital signatures l algorithms not standardised, but RSA recommended Ø X. 509 certificates are widely used Ø Public key certificate associated with each user l Generated by some trusted CA Ø Certification Authority (CA) issues certificates Ø The notation CA<> represents a certificate for a client A signed by CA Ø
 X. 509 Certificates Ø issued by a Certification Authority (CA), containing: l l l version 1, 2, or 3 serial number (unique within CA) identifying certificate signature algorithm identifier issuer X. 500 name (CA) period of validity (from - to dates) subject X. 500 name (name of owner) subject public-key info (algorithm, parameters, key) issuer unique identifier (v 2+) subject unique identifier (v 2+) extension fields (v 3) signature (of hash of all fields in certificate)
X. 509 Certificates Ø issued by a Certification Authority (CA), containing: l l l version 1, 2, or 3 serial number (unique within CA) identifying certificate signature algorithm identifier issuer X. 500 name (CA) period of validity (from - to dates) subject X. 500 name (name of owner) subject public-key info (algorithm, parameters, key) issuer unique identifier (v 2+) subject unique identifier (v 2+) extension fields (v 3) signature (of hash of all fields in certificate)
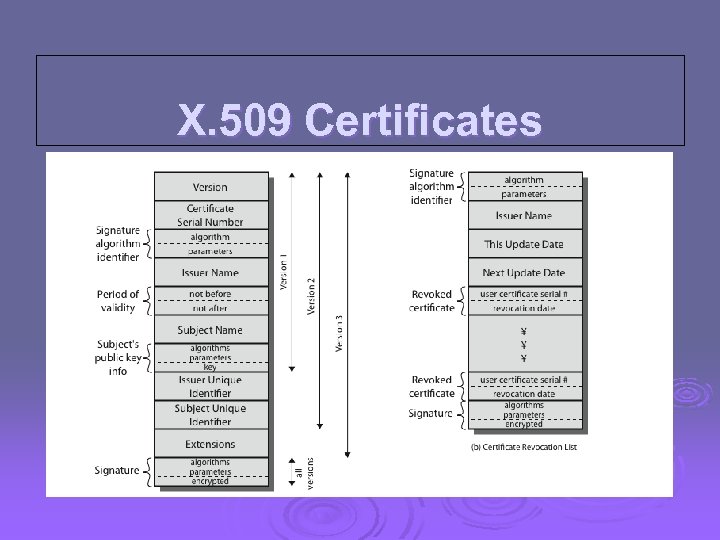 X. 509 Certificates
X. 509 Certificates
 Obtaining a User Certificate Ø Certificate notation: CA{…} Ø Any user with CA’s public key can verify the user public key that was certified Ø No party other than the CA can modify the certificate without being detected Ø because cannot be forged, certificates can be placed in a public directory
Obtaining a User Certificate Ø Certificate notation: CA{…} Ø Any user with CA’s public key can verify the user public key that was certified Ø No party other than the CA can modify the certificate without being detected Ø because cannot be forged, certificates can be placed in a public directory
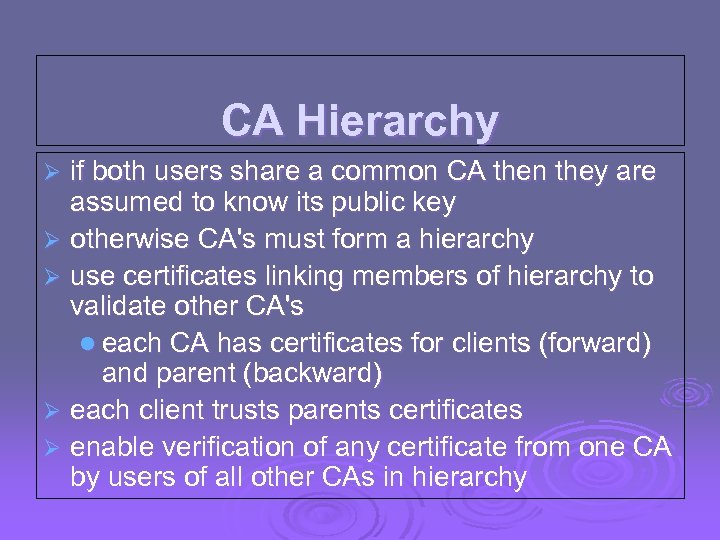 CA Hierarchy if both users share a common CA then they are assumed to know its public key Ø otherwise CA's must form a hierarchy Ø use certificates linking members of hierarchy to validate other CA's l each CA has certificates for clients (forward) and parent (backward) Ø each client trusts parents certificates Ø enable verification of any certificate from one CA by users of all other CAs in hierarchy Ø
CA Hierarchy if both users share a common CA then they are assumed to know its public key Ø otherwise CA's must form a hierarchy Ø use certificates linking members of hierarchy to validate other CA's l each CA has certificates for clients (forward) and parent (backward) Ø each client trusts parents certificates Ø enable verification of any certificate from one CA by users of all other CAs in hierarchy Ø
 CA Hierarchy
CA Hierarchy
 Certificate Revocation Ø Ø certificates have a period of validity may need to revoke before expiry: 1. user's private key is compromised 2. user is no longer certified by this CA 3. CA's certificate is compromised CA’s maintain list of revoked certificates l the Certificate Revocation List (CRL) users should check certificates with CA’s CRL
Certificate Revocation Ø Ø certificates have a period of validity may need to revoke before expiry: 1. user's private key is compromised 2. user is no longer certified by this CA 3. CA's certificate is compromised CA’s maintain list of revoked certificates l the Certificate Revocation List (CRL) users should check certificates with CA’s CRL
 Authentication Procedures Ø X. 509 includes three alternative authentication procedures: Ø One-Way Authentication Ø Two-Way Authentication Ø Three-Way Authentication Ø all use public-key signatures Ø See Figure 14. 6 for Authentication
Authentication Procedures Ø X. 509 includes three alternative authentication procedures: Ø One-Way Authentication Ø Two-Way Authentication Ø Three-Way Authentication Ø all use public-key signatures Ø See Figure 14. 6 for Authentication
 One-Way Authentication Ø 1 message ( A->B) used to establish l the identity of A and that message is from A l message was intended for B l integrity & originality of message Ø message must include timestamp, nonce, B's identity and is signed by A Ø may include additional info for B l eg session key
One-Way Authentication Ø 1 message ( A->B) used to establish l the identity of A and that message is from A l message was intended for B l integrity & originality of message Ø message must include timestamp, nonce, B's identity and is signed by A Ø may include additional info for B l eg session key
 Two-Way Authentication Ø 2 messages (A->B, B->A) which also establishes in addition: l the identity of B and that reply is from B l that reply is intended for A l integrity & originality of reply Ø reply includes original nonce from A, also timestamp and nonce from B Ø may include additional info for A
Two-Way Authentication Ø 2 messages (A->B, B->A) which also establishes in addition: l the identity of B and that reply is from B l that reply is intended for A l integrity & originality of reply Ø reply includes original nonce from A, also timestamp and nonce from B Ø may include additional info for A
 Three-Way Authentication Ø 3 messages (A->B, B->A, A->B) which enables above authentication without synchronized clocks Ø has reply from A back to B containing signed copy of nonce from B Ø means that timestamps need not be checked or relied upon
Three-Way Authentication Ø 3 messages (A->B, B->A, A->B) which enables above authentication without synchronized clocks Ø has reply from A back to B containing signed copy of nonce from B Ø means that timestamps need not be checked or relied upon
 X. 509 Version 3 Ø has been recognised that additional information is needed in a certificate l email/URL, policy details, usage constraints Ø rather than explicitly naming new fields defined a general extension method Ø extensions consist of: l extension identifier l criticality indicator l extension value
X. 509 Version 3 Ø has been recognised that additional information is needed in a certificate l email/URL, policy details, usage constraints Ø rather than explicitly naming new fields defined a general extension method Ø extensions consist of: l extension identifier l criticality indicator l extension value
 Certificate Extensions Ø key and policy information l convey info about subject & issuer keys, plus indicators of certificate policy Ø certificate subject and issuer attributes l support alternative names, in alternative formats for certificate subject and/or issuer Ø certificate path constraints l allow constraints on use of certificates by other CA’s
Certificate Extensions Ø key and policy information l convey info about subject & issuer keys, plus indicators of certificate policy Ø certificate subject and issuer attributes l support alternative names, in alternative formats for certificate subject and/or issuer Ø certificate path constraints l allow constraints on use of certificates by other CA’s
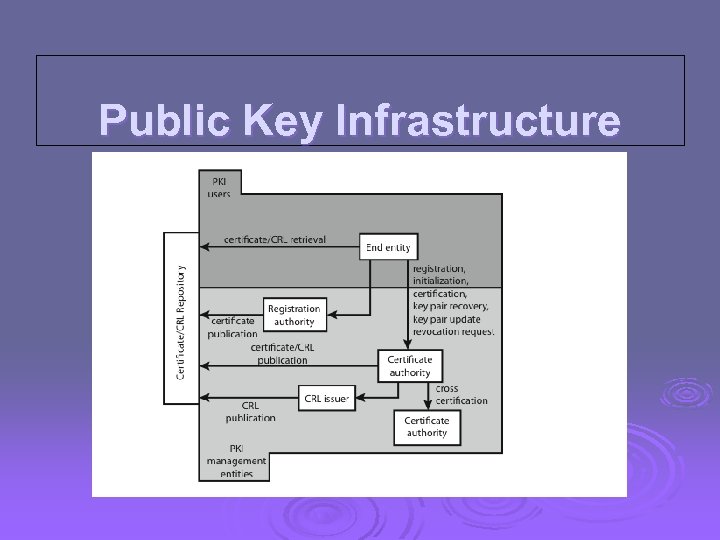 Public Key Infrastructure
Public Key Infrastructure
 Chapter 15 – Electronic Mail Security Despite the refusal of VADM Poindexter and Lt. Col North to appear, the Board's access to other sources of information filled much of this gap. The FBI provided documents taken from the files of the National Security Advisor and relevant NSC staff members, including messages from the PROF system between VADM Poindexter and Lt. Col North. The PROF messages were conversations by computer, written at the time events occurred and presumed by the writers to be protected from disclosure. In this sense, they provide a first-hand, contemporaneous account of events. —The Tower Commission Report to President Reagan on the Iran-Contra Affair, 1987
Chapter 15 – Electronic Mail Security Despite the refusal of VADM Poindexter and Lt. Col North to appear, the Board's access to other sources of information filled much of this gap. The FBI provided documents taken from the files of the National Security Advisor and relevant NSC staff members, including messages from the PROF system between VADM Poindexter and Lt. Col North. The PROF messages were conversations by computer, written at the time events occurred and presumed by the writers to be protected from disclosure. In this sense, they provide a first-hand, contemporaneous account of events. —The Tower Commission Report to President Reagan on the Iran-Contra Affair, 1987
 Email Security Ø email is one of the most widely used and regarded network services Ø currently message contents are not secure l may be inspected either in transit l or by suitably privileged users on destination system
Email Security Ø email is one of the most widely used and regarded network services Ø currently message contents are not secure l may be inspected either in transit l or by suitably privileged users on destination system
 Email Security Enhancements Ø confidentiality l protection from disclosure Ø authentication l of sender of message Ø message integrity l protection from modification Ø non-repudiation of origin l protection from denial by sender
Email Security Enhancements Ø confidentiality l protection from disclosure Ø authentication l of sender of message Ø message integrity l protection from modification Ø non-repudiation of origin l protection from denial by sender
 Pretty Good Privacy (PGP) Ø widely used de facto secure email Ø developed by Phil Zimmermann Ø selected best available crypto algs to use Ø integrated into a single program Ø on Unix, PC, Macintosh and other systems Ø originally free, now also have commercial versions available
Pretty Good Privacy (PGP) Ø widely used de facto secure email Ø developed by Phil Zimmermann Ø selected best available crypto algs to use Ø integrated into a single program Ø on Unix, PC, Macintosh and other systems Ø originally free, now also have commercial versions available
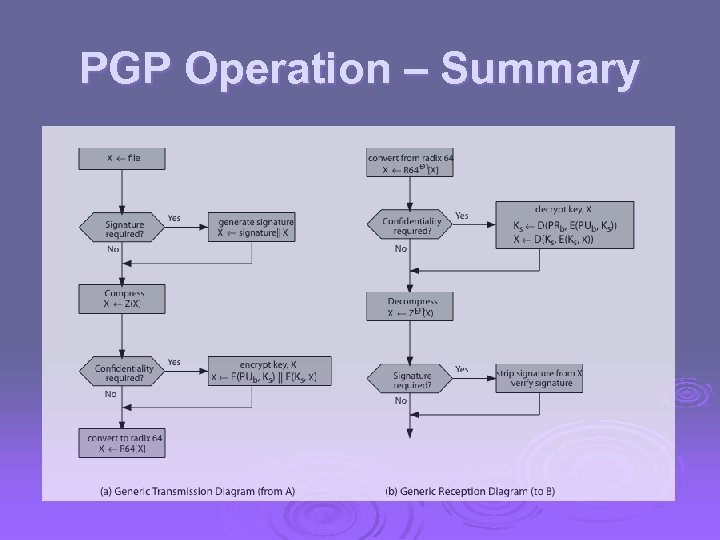
 PGP Operation – Authentication sender creates message use SHA-1 to generate 160 -bit hash of message 3. signed hash with RSA using sender's private key, and is attached to message 4. receiver uses RSA with sender's public key to decrypt and recover hash code 5. receiver verifies received message using hash of it and compares with decrypted hash code 1. 2.
PGP Operation – Authentication sender creates message use SHA-1 to generate 160 -bit hash of message 3. signed hash with RSA using sender's private key, and is attached to message 4. receiver uses RSA with sender's public key to decrypt and recover hash code 5. receiver verifies received message using hash of it and compares with decrypted hash code 1. 2.
 PGP Operation – Confidentiality 1. 2. 3. 4. 5. sender generates message and 128 bit random number as session key for it encrypt message using CAST-128 / IDEA / 3 DES in CBC mode with session key encrypted using RSA with recipient's public key, & attached to msg receiver uses RSA with private key to decrypt and recover session key is used to decrypt message
PGP Operation – Confidentiality 1. 2. 3. 4. 5. sender generates message and 128 bit random number as session key for it encrypt message using CAST-128 / IDEA / 3 DES in CBC mode with session key encrypted using RSA with recipient's public key, & attached to msg receiver uses RSA with private key to decrypt and recover session key is used to decrypt message
 PGP Operation – Confidentiality & Authentication Ø can use both services on same message l create signature & attach to message l encrypt both message & signature l attach RSA/El. Gamal encrypted session key
PGP Operation – Confidentiality & Authentication Ø can use both services on same message l create signature & attach to message l encrypt both message & signature l attach RSA/El. Gamal encrypted session key
 PGP Operation – Compression Ø by default PGP compresses message after signing but before encrypting l so can store uncompressed message & signature for later verification l & because compression is non deterministic Ø uses ZIP compression algorithm
PGP Operation – Compression Ø by default PGP compresses message after signing but before encrypting l so can store uncompressed message & signature for later verification l & because compression is non deterministic Ø uses ZIP compression algorithm
 PGP Operation – Email Compatibility when using PGP will have binary data to send (encrypted message etc) Ø however email was designed only for text Ø hence PGP must encode raw binary data into printable ASCII characters Ø uses radix-64 algorithm Ø maps 3 bytes to 4 printable chars l also appends a CRC l Ø PGP also segments messages if too big
PGP Operation – Email Compatibility when using PGP will have binary data to send (encrypted message etc) Ø however email was designed only for text Ø hence PGP must encode raw binary data into printable ASCII characters Ø uses radix-64 algorithm Ø maps 3 bytes to 4 printable chars l also appends a CRC l Ø PGP also segments messages if too big
 PGP Operation – Summary
PGP Operation – Summary
 PGP Session Keys Ø need a session key for each message l of varying sizes: 56 -bit DES, 128 -bit CAST or IDEA, 168 -bit Triple-DES Ø generated using ANSI X 12. 17 mode Ø uses random inputs taken from previous uses and from keystroke timing of user
PGP Session Keys Ø need a session key for each message l of varying sizes: 56 -bit DES, 128 -bit CAST or IDEA, 168 -bit Triple-DES Ø generated using ANSI X 12. 17 mode Ø uses random inputs taken from previous uses and from keystroke timing of user
 PGP Public & Private Keys Ø since many public/private keys may be in use, need to identify which is actually used to encrypt session key in a message could send full public-key with every message l but this is inefficient l Ø rather use a key identifier based on key is least significant 64 -bits of the key l will very likely be unique l Ø also use key ID in signatures
PGP Public & Private Keys Ø since many public/private keys may be in use, need to identify which is actually used to encrypt session key in a message could send full public-key with every message l but this is inefficient l Ø rather use a key identifier based on key is least significant 64 -bits of the key l will very likely be unique l Ø also use key ID in signatures
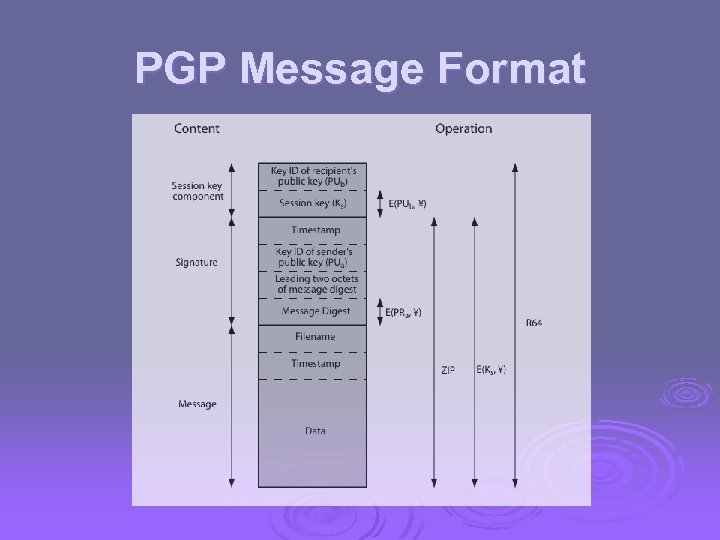 PGP Message Format
PGP Message Format
 PGP Key Rings Ø each PGP user has a pair of keyrings: l public-key ring contains all the public-keys of other PGP users known to this user, indexed by key ID l private-key ring contains the public/private key pair(s) for this user, indexed by key ID & encrypted keyed from a hashed passphrase Ø security of private keys thus depends on the pass-phrase security
PGP Key Rings Ø each PGP user has a pair of keyrings: l public-key ring contains all the public-keys of other PGP users known to this user, indexed by key ID l private-key ring contains the public/private key pair(s) for this user, indexed by key ID & encrypted keyed from a hashed passphrase Ø security of private keys thus depends on the pass-phrase security
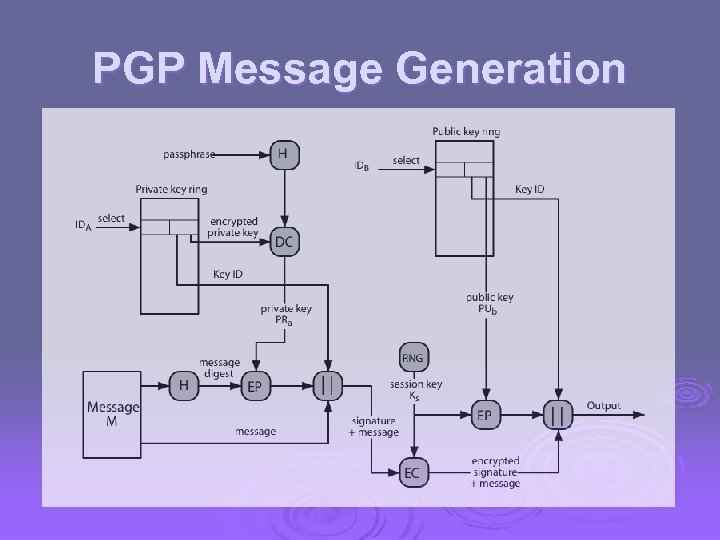 PGP Message Generation
PGP Message Generation
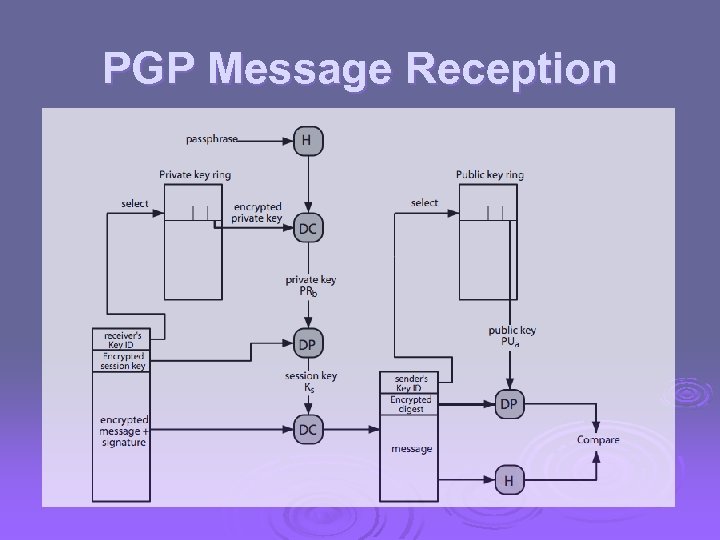 PGP Message Reception
PGP Message Reception
 PGP Key Management rather than relying on certificate authorities Ø in PGP every user is own CA Ø l Ø can sign keys for users they know directly forms a “web of trust” trust keys have signed l can trust keys others have signed if have a chain of signatures to them l key ring includes trust indicators Ø users can also revoke their keys Ø
PGP Key Management rather than relying on certificate authorities Ø in PGP every user is own CA Ø l Ø can sign keys for users they know directly forms a “web of trust” trust keys have signed l can trust keys others have signed if have a chain of signatures to them l key ring includes trust indicators Ø users can also revoke their keys Ø
 S/MIME (Secure/Multipurpose Internet Mail Extensions) Ø security enhancement to MIME email l original Internet RFC 822 email was text only l MIME provided support for varying content types and multi-part messages l with encoding of binary data to textual form l S/MIME added security enhancements Ø have S/MIME support in many mail agents l eg MS Outlook, Mozilla, Mac Mail etc
S/MIME (Secure/Multipurpose Internet Mail Extensions) Ø security enhancement to MIME email l original Internet RFC 822 email was text only l MIME provided support for varying content types and multi-part messages l with encoding of binary data to textual form l S/MIME added security enhancements Ø have S/MIME support in many mail agents l eg MS Outlook, Mozilla, Mac Mail etc
 S/MIME Functions Ø enveloped data l encrypted content and associated keys Ø signed data l encoded message + signed digest Ø clear-signed data l cleartext message + encoded signed digest Ø signed & enveloped data l nesting of signed & encrypted entities
S/MIME Functions Ø enveloped data l encrypted content and associated keys Ø signed data l encoded message + signed digest Ø clear-signed data l cleartext message + encoded signed digest Ø signed & enveloped data l nesting of signed & encrypted entities
 S/MIME Cryptographic Algorithms Ø digital signatures: DSS & RSA Ø hash functions: SHA-1 & MD 5 Ø session key encryption: El. Gamal & RSA Ø message encryption: AES, Triple-DES, RC 2/40 and others Ø MAC: HMAC with SHA-1 Ø have process to decide which algs to use
S/MIME Cryptographic Algorithms Ø digital signatures: DSS & RSA Ø hash functions: SHA-1 & MD 5 Ø session key encryption: El. Gamal & RSA Ø message encryption: AES, Triple-DES, RC 2/40 and others Ø MAC: HMAC with SHA-1 Ø have process to decide which algs to use
 S/MIME Messages Ø S/MIME secures a MIME entity with a signature, encryption, or both Ø forming a MIME wrapped PKCS object Ø have a range of content-types: l enveloped data l signed data l clear-signed data l registration request l certificate only message
S/MIME Messages Ø S/MIME secures a MIME entity with a signature, encryption, or both Ø forming a MIME wrapped PKCS object Ø have a range of content-types: l enveloped data l signed data l clear-signed data l registration request l certificate only message
 S/MIME Certificate Processing Ø S/MIME uses X. 509 v 3 certificates Ø managed using a hybrid of a strict X. 509 CA hierarchy & PGP’s web of trust Ø each client has a list of trusted CA’s certs Ø and own public/private key pairs & certs Ø certificates must be signed by trusted CA’s
S/MIME Certificate Processing Ø S/MIME uses X. 509 v 3 certificates Ø managed using a hybrid of a strict X. 509 CA hierarchy & PGP’s web of trust Ø each client has a list of trusted CA’s certs Ø and own public/private key pairs & certs Ø certificates must be signed by trusted CA’s
 Certificate Authorities Ø have several well-known CA’s Ø Verisign one of most widely used Ø Verisign issues several types of Digital IDs Ø increasing levels of checks & hence trust Class 1 2 3 Identity Checks name/email check + enroll/addr check + ID documents Usage web browsing/email, subs, s/w validate e-banking/service access
Certificate Authorities Ø have several well-known CA’s Ø Verisign one of most widely used Ø Verisign issues several types of Digital IDs Ø increasing levels of checks & hence trust Class 1 2 3 Identity Checks name/email check + enroll/addr check + ID documents Usage web browsing/email, subs, s/w validate e-banking/service access
 Summary Ø have considered: l secure email l PGP l S/MIME
Summary Ø have considered: l secure email l PGP l S/MIME
 IP Security -
IP Security -
 Outline Internetworking and Internet Protocols Ø IP Security Overview Ø IP Security Architecture Ø Authentication Header Ø Encapsulating Security Payload Ø Combinations of Security Associations Ø Key Management Ø
Outline Internetworking and Internet Protocols Ø IP Security Overview Ø IP Security Architecture Ø Authentication Header Ø Encapsulating Security Payload Ø Combinations of Security Associations Ø Key Management Ø
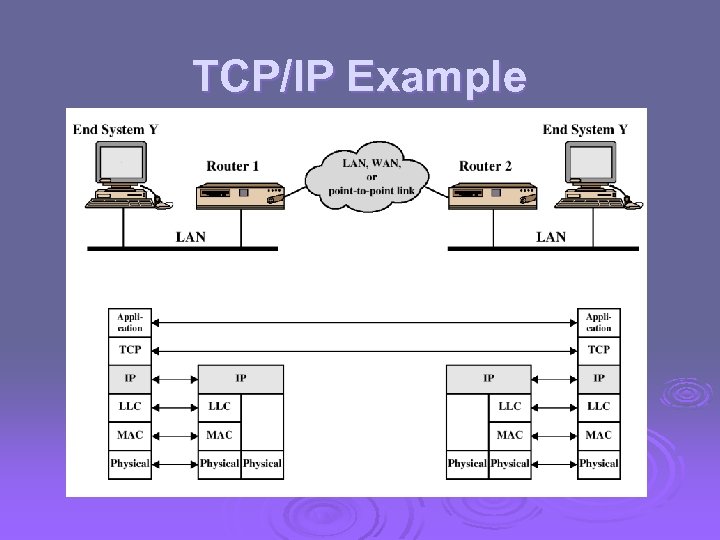 TCP/IP Example
TCP/IP Example
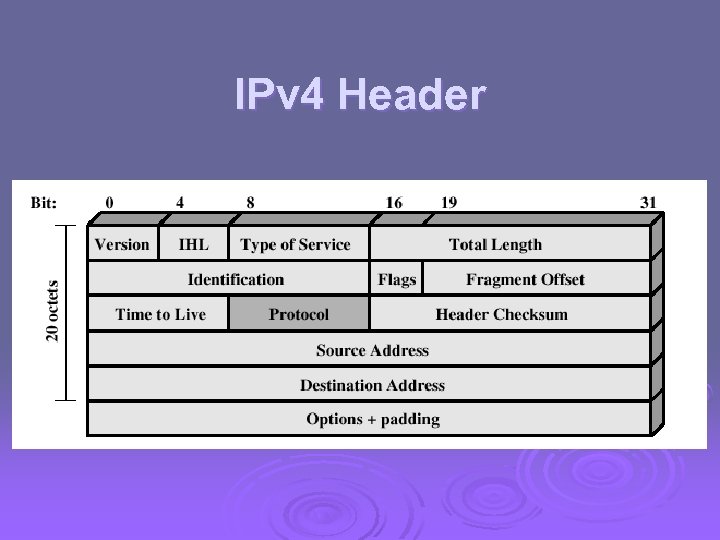 IPv 4 Header
IPv 4 Header
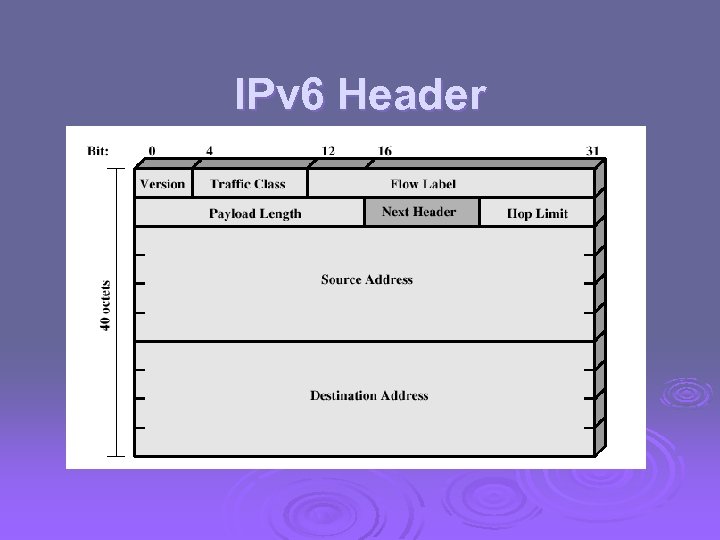 IPv 6 Header
IPv 6 Header
 IP Security Overview Ø Ø IPSec is not a single protocol. Instead, IPSec provides a set of security algorithms plus a general framework that allows a pair of communicating entities to use whichever algorithms to provide security appropriate for the communication. Ø Applications of IPSec Secure branch office connectivity over the Internet l Secure remote access over the Internet l Establsihing extranet and intranet connectivity with partners l Enhancing electronic commerce security l
IP Security Overview Ø Ø IPSec is not a single protocol. Instead, IPSec provides a set of security algorithms plus a general framework that allows a pair of communicating entities to use whichever algorithms to provide security appropriate for the communication. Ø Applications of IPSec Secure branch office connectivity over the Internet l Secure remote access over the Internet l Establsihing extranet and intranet connectivity with partners l Enhancing electronic commerce security l
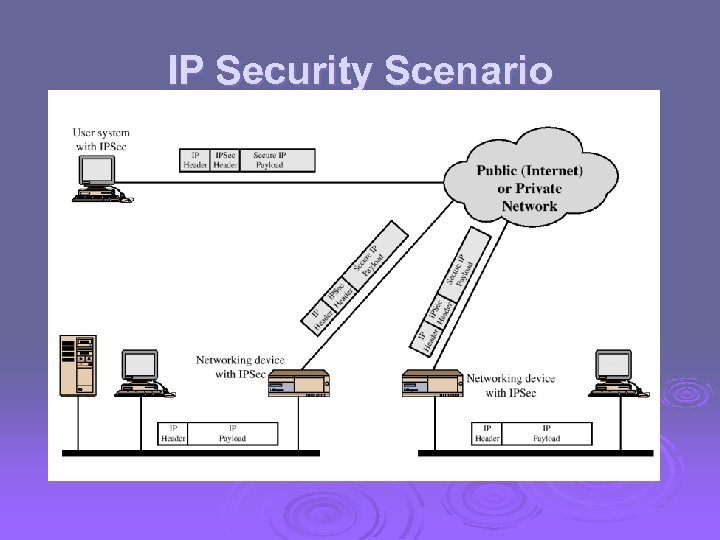 IP Security Scenario
IP Security Scenario
 IP Security Overview Ø Benefits of IPSec Transparent to applications - below transport layer (TCP, UDP) l Provide security for individual users l Ø IPSec can assure that: A router or neighbor advertisement comes from an authorized router l A redirect message comes from the router to which the initial packet was sent l A routing update is not forged l
IP Security Overview Ø Benefits of IPSec Transparent to applications - below transport layer (TCP, UDP) l Provide security for individual users l Ø IPSec can assure that: A router or neighbor advertisement comes from an authorized router l A redirect message comes from the router to which the initial packet was sent l A routing update is not forged l
 IP Security Architecture Ø IPSec documents: NEW updates in 2005! l RFC 2401: Security Architecture for the Internet Protocol. S. Kent, R. Atkinson. November 1998. (An overview of security architecture) RFC 4301 (12/2005) l RFC 2402: IP Authentication Header. S. Kent, R. Atkinson. November 1998. (Description of a packet encryption extension to IPv 4 and IPv 6) RFC 4302 (12/2005) l RFC 2406: IP Encapsulating Security Payload (ESP). S. Kent, R. Atkinson. November 1998. (Description of a packet emcryption extension to IPv 4 and IPv 6) RFC 4303 (12/2005) l RFC 2407 The Internet IP Security Domain of Interpretation for ISAKMP D. Piper. November 1998. PROPOSED STANDARD. (Obsoleted by RFC 4306) l RFC 2408: Internet Security Association and Key Management Protocol (ISAKMP). D. Maughan, M. Schertler, M. Schneider, J. Turner. November 1998. (Specification of key managament capabilities) (Obsoleted by RFC 4306) l RFC 2409 The Internet Key Exchange (IKE) D. Harkins, D. Carrel. November 1998. PROPOSED STANDARD. (Obsoleted by RFC 4306, Updated by RFC 4109)
IP Security Architecture Ø IPSec documents: NEW updates in 2005! l RFC 2401: Security Architecture for the Internet Protocol. S. Kent, R. Atkinson. November 1998. (An overview of security architecture) RFC 4301 (12/2005) l RFC 2402: IP Authentication Header. S. Kent, R. Atkinson. November 1998. (Description of a packet encryption extension to IPv 4 and IPv 6) RFC 4302 (12/2005) l RFC 2406: IP Encapsulating Security Payload (ESP). S. Kent, R. Atkinson. November 1998. (Description of a packet emcryption extension to IPv 4 and IPv 6) RFC 4303 (12/2005) l RFC 2407 The Internet IP Security Domain of Interpretation for ISAKMP D. Piper. November 1998. PROPOSED STANDARD. (Obsoleted by RFC 4306) l RFC 2408: Internet Security Association and Key Management Protocol (ISAKMP). D. Maughan, M. Schertler, M. Schneider, J. Turner. November 1998. (Specification of key managament capabilities) (Obsoleted by RFC 4306) l RFC 2409 The Internet Key Exchange (IKE) D. Harkins, D. Carrel. November 1998. PROPOSED STANDARD. (Obsoleted by RFC 4306, Updated by RFC 4109)
 IP Security Architecture Ø Internet Key Exchange (IKE) A method for establishing a security association (SA) that authenticates users, negotiates the encryption method and exchanges the secret key. IKE is used in the IPsec protocol. Derived from the ISAKMP framework for key exchange and the Oakley and SKEME key exchange techniques, IKE uses public key cryptography to provide the secure transmission of the secret key to the recipient so that the encrypted data may be decrypted at the other end. (http: //computing-dictionary. thefreedictionary. com/IKE) RFC 4306 Internet Key Exchange (IKEv 2) Protocol C. Kaufman, Ed. December 2005 (Obsoletes RFC 2407, RFC 2408, RFC 2409) PROPOSED STANDARD Ø RFC 4109 Algorithms for Internet Key Exchange version 1 (IKEv 1) P. Hoffman. May 2005 (Updates RFC 2409) PROPOSED STANDARD Ø
IP Security Architecture Ø Internet Key Exchange (IKE) A method for establishing a security association (SA) that authenticates users, negotiates the encryption method and exchanges the secret key. IKE is used in the IPsec protocol. Derived from the ISAKMP framework for key exchange and the Oakley and SKEME key exchange techniques, IKE uses public key cryptography to provide the secure transmission of the secret key to the recipient so that the encrypted data may be decrypted at the other end. (http: //computing-dictionary. thefreedictionary. com/IKE) RFC 4306 Internet Key Exchange (IKEv 2) Protocol C. Kaufman, Ed. December 2005 (Obsoletes RFC 2407, RFC 2408, RFC 2409) PROPOSED STANDARD Ø RFC 4109 Algorithms for Internet Key Exchange version 1 (IKEv 1) P. Hoffman. May 2005 (Updates RFC 2409) PROPOSED STANDARD Ø
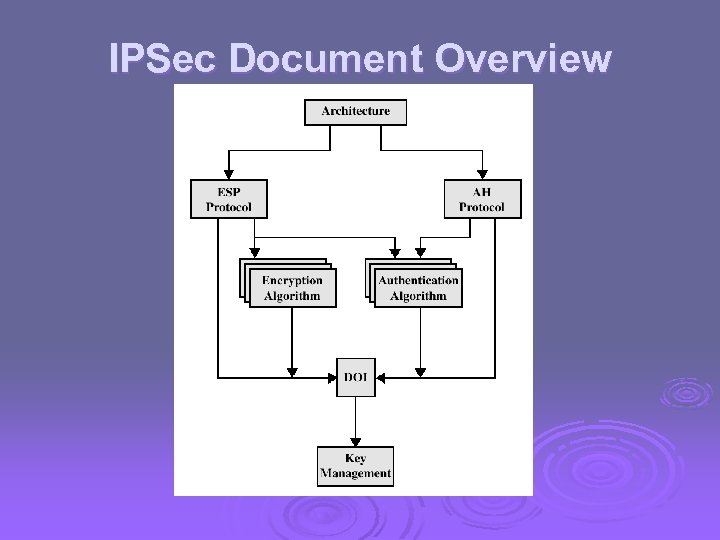 IPSec Document Overview
IPSec Document Overview
 IPSec Services Ø Access Control Ø Connectionless integrity Ø Data origin authentication Ø Rejection of replayed packets Ø Confidentiality (encryption) Ø Limited traffic flow confidentiallity
IPSec Services Ø Access Control Ø Connectionless integrity Ø Data origin authentication Ø Rejection of replayed packets Ø Confidentiality (encryption) Ø Limited traffic flow confidentiallity
 Security Associations (SA) Ø A one way relationsship between a sender and a receiver. Ø Identified by three parameters: l Security Parameter Index (SPI) l IP Destination address l Security Protocol Identifier
Security Associations (SA) Ø A one way relationsship between a sender and a receiver. Ø Identified by three parameters: l Security Parameter Index (SPI) l IP Destination address l Security Protocol Identifier
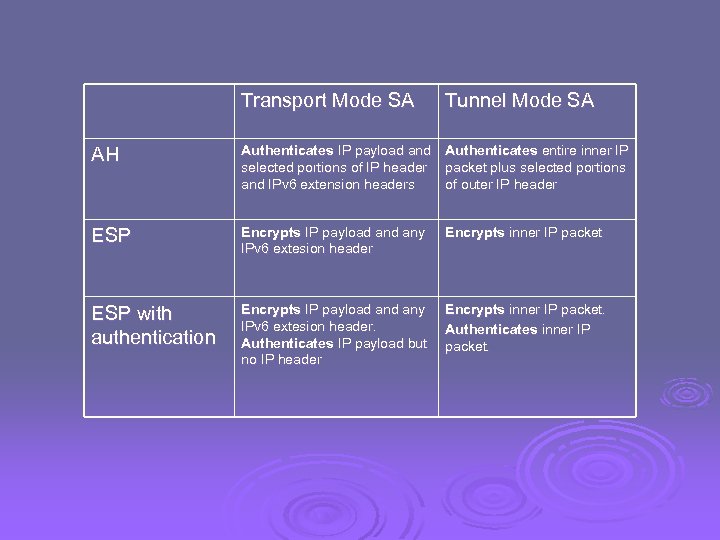 Transport Mode SA Tunnel Mode SA AH Authenticates IP payload and Authenticates entire inner IP selected portions of IP header packet plus selected portions and IPv 6 extension headers of outer IP header ESP Encrypts IP payload any IPv 6 extesion header ESP with authentication Encrypts IP payload any Encrypts inner IP packet. IPv 6 extesion header. Authenticates inner IP Authenticates IP payload but packet. no IP header Encrypts inner IP packet
Transport Mode SA Tunnel Mode SA AH Authenticates IP payload and Authenticates entire inner IP selected portions of IP header packet plus selected portions and IPv 6 extension headers of outer IP header ESP Encrypts IP payload any IPv 6 extesion header ESP with authentication Encrypts IP payload any Encrypts inner IP packet. IPv 6 extesion header. Authenticates inner IP Authenticates IP payload but packet. no IP header Encrypts inner IP packet
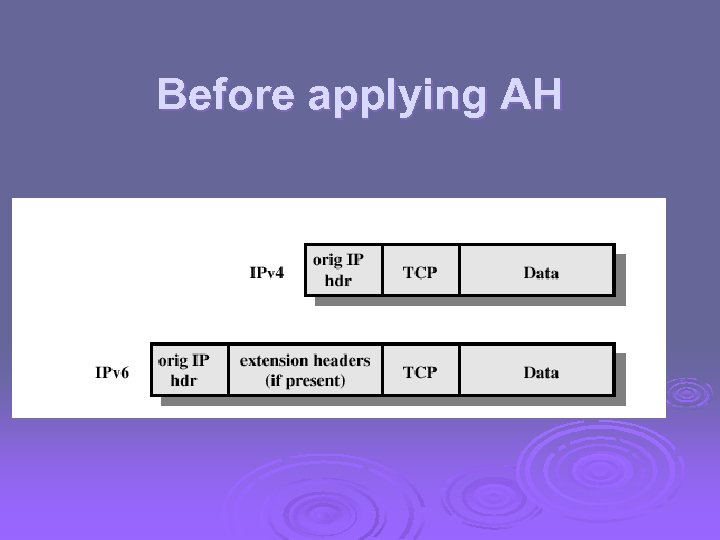 Before applying AH
Before applying AH
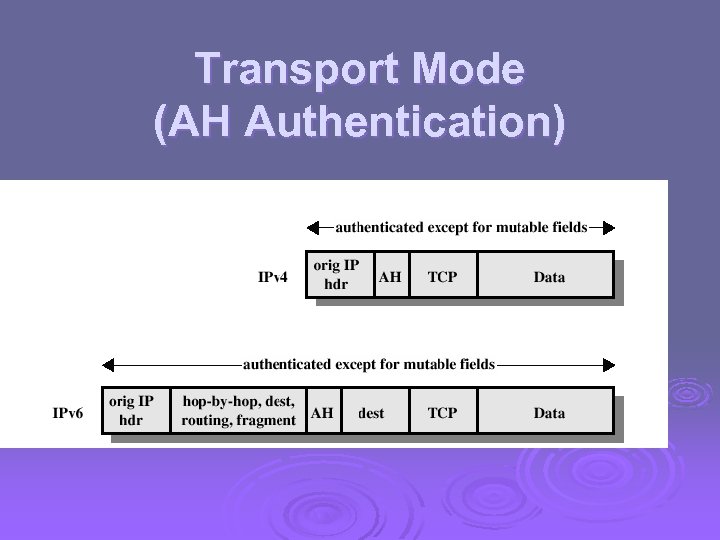 Transport Mode (AH Authentication)
Transport Mode (AH Authentication)
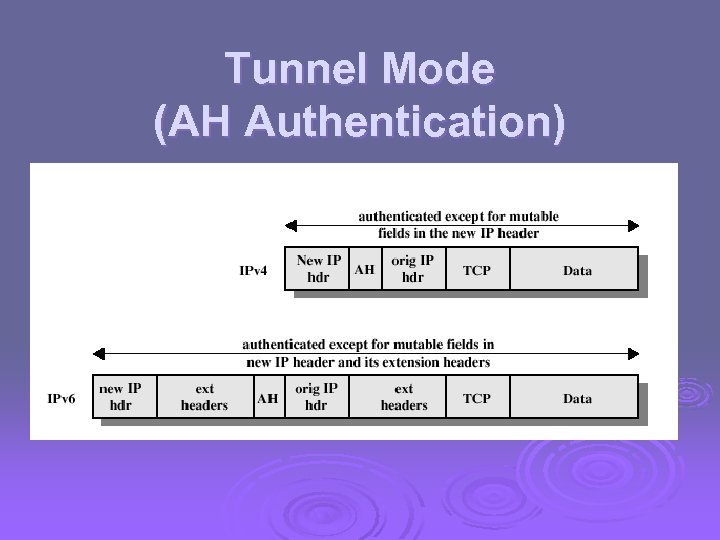 Tunnel Mode (AH Authentication)
Tunnel Mode (AH Authentication)
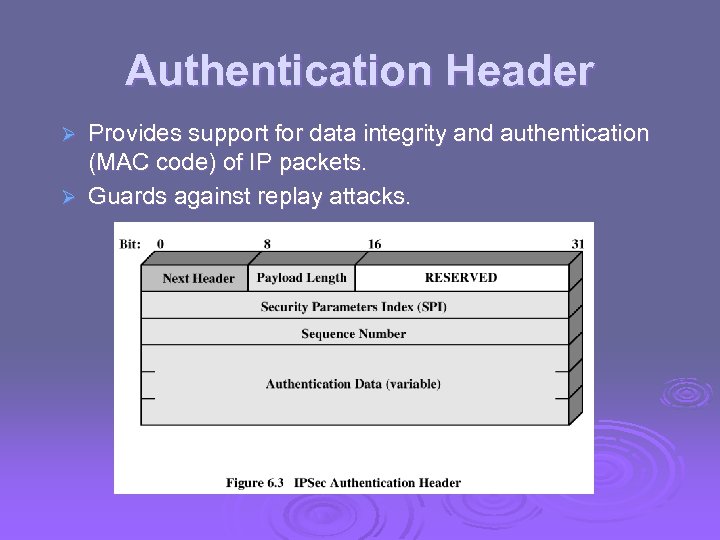 Authentication Header Provides support for data integrity and authentication (MAC code) of IP packets. Ø Guards against replay attacks. Ø
Authentication Header Provides support for data integrity and authentication (MAC code) of IP packets. Ø Guards against replay attacks. Ø
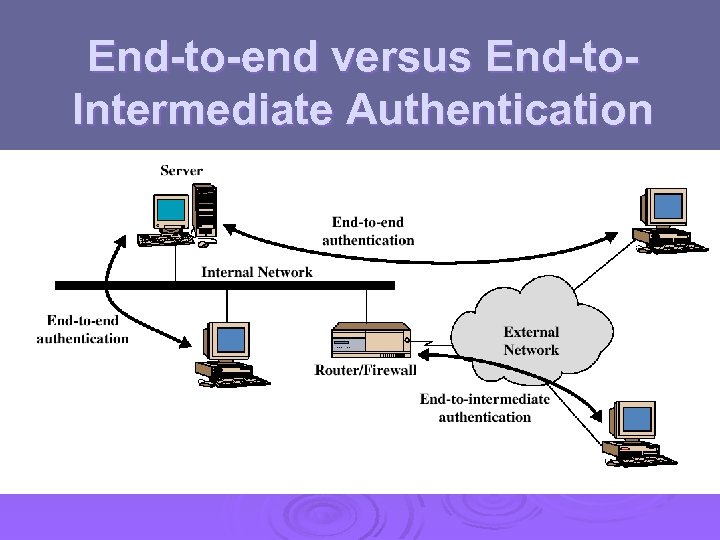 End-to-end versus End-to. Intermediate Authentication
End-to-end versus End-to. Intermediate Authentication
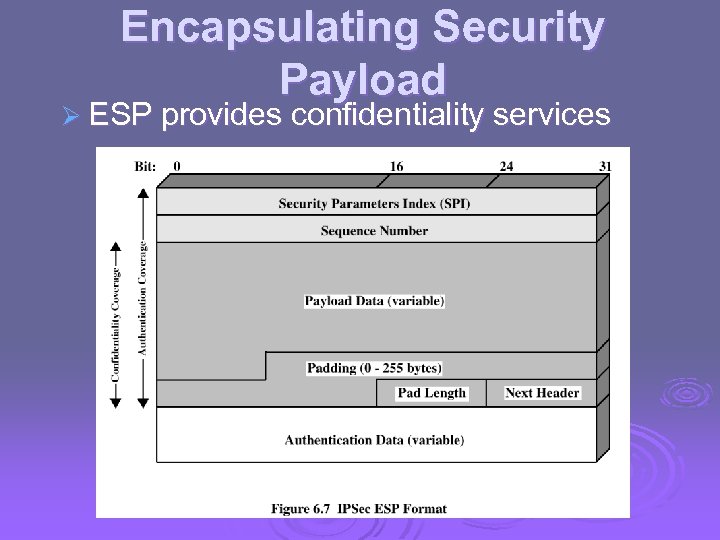 Encapsulating Security Payload Ø ESP provides confidentiality services
Encapsulating Security Payload Ø ESP provides confidentiality services
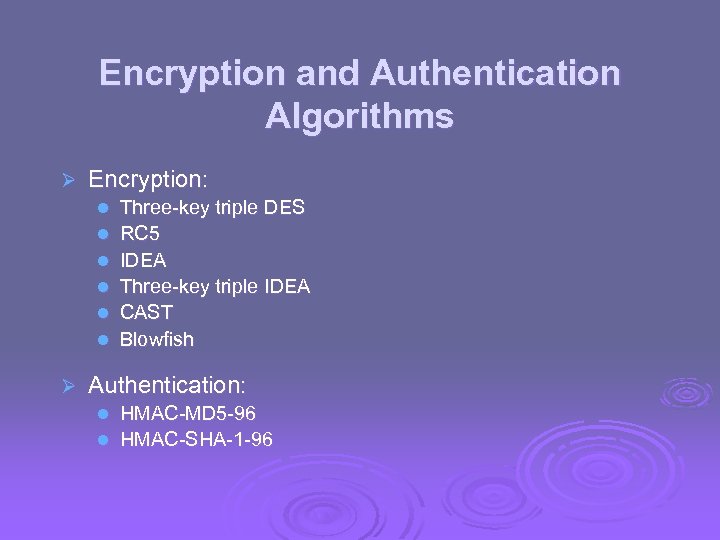 Encryption and Authentication Algorithms Ø Encryption: l l l Ø Three-key triple DES RC 5 IDEA Three-key triple IDEA CAST Blowfish Authentication: HMAC-MD 5 -96 l HMAC-SHA-1 -96 l
Encryption and Authentication Algorithms Ø Encryption: l l l Ø Three-key triple DES RC 5 IDEA Three-key triple IDEA CAST Blowfish Authentication: HMAC-MD 5 -96 l HMAC-SHA-1 -96 l
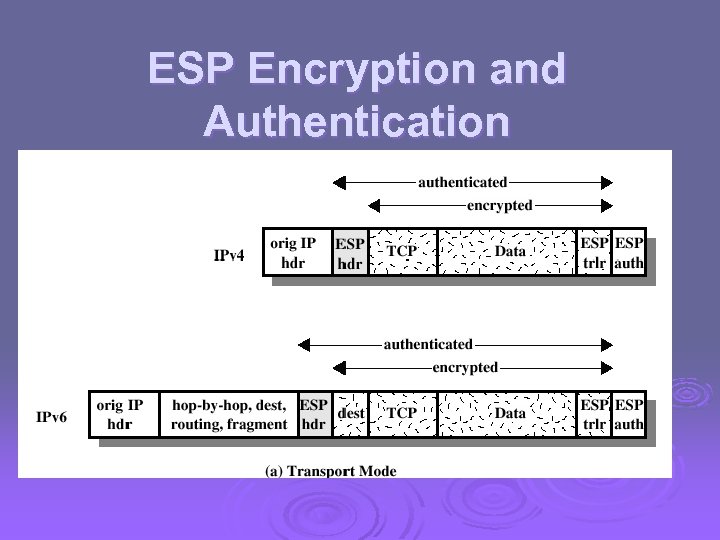 ESP Encryption and Authentication
ESP Encryption and Authentication
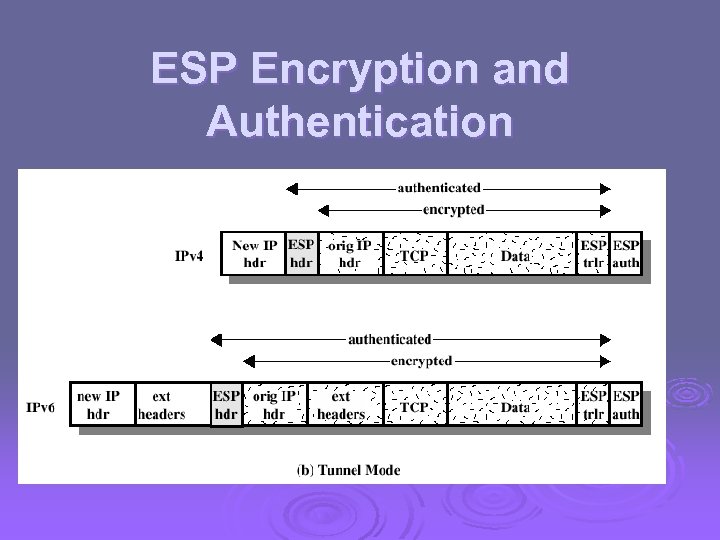 ESP Encryption and Authentication
ESP Encryption and Authentication
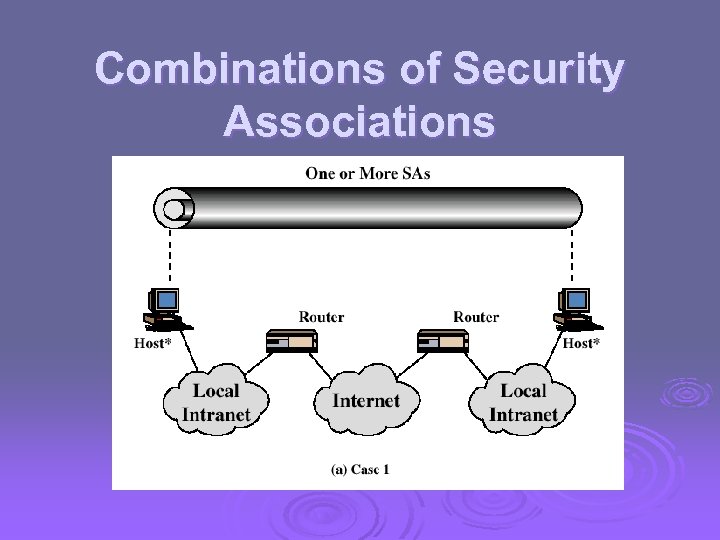 Combinations of Security Associations
Combinations of Security Associations
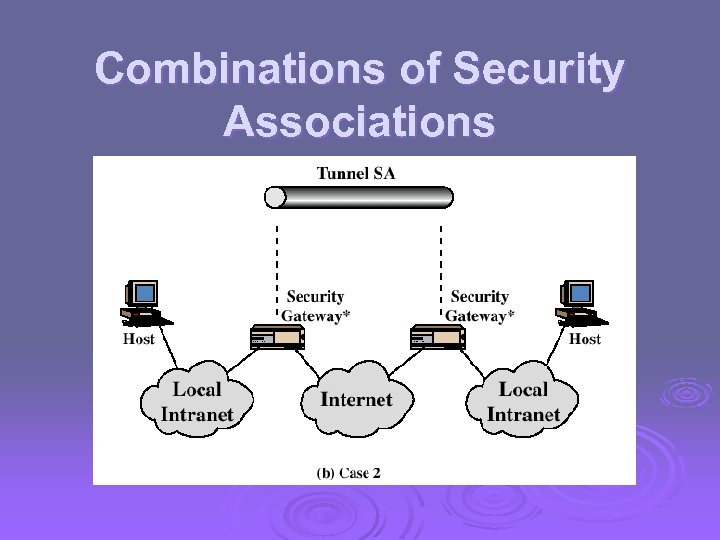 Combinations of Security Associations
Combinations of Security Associations
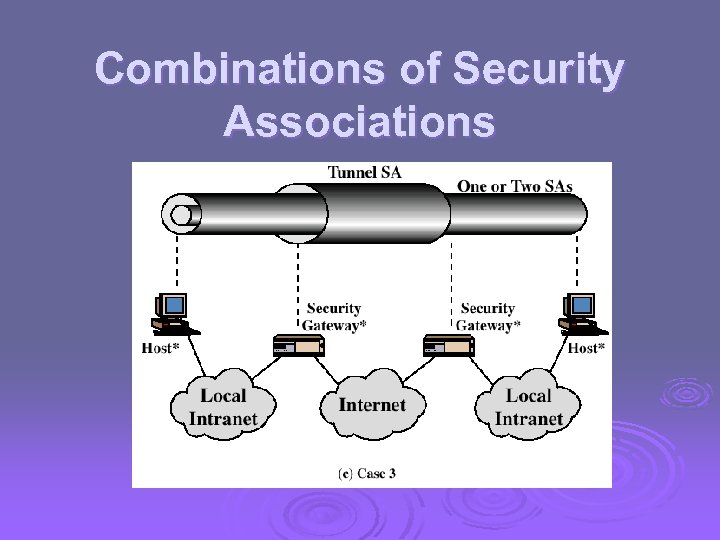 Combinations of Security Associations
Combinations of Security Associations
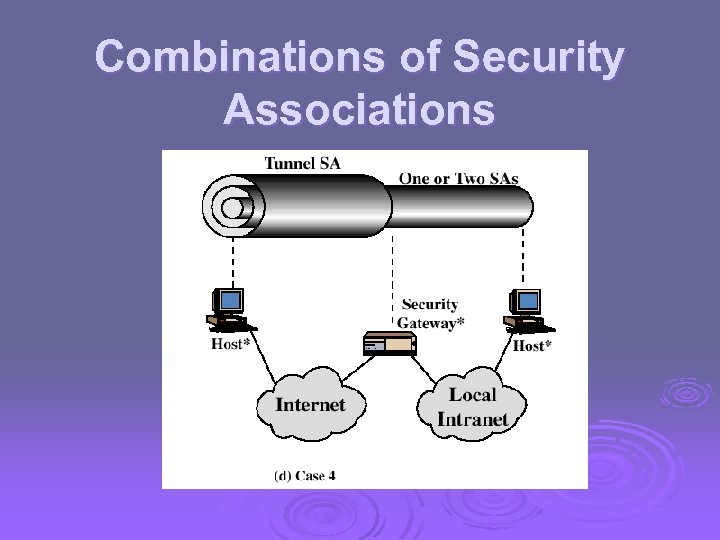 Combinations of Security Associations
Combinations of Security Associations
 Key Management Ø Two types: l Manual l Automated Oakley Key Determination Protocol • Internet Security Association and Key Management Protocol (ISAKMP) •
Key Management Ø Two types: l Manual l Automated Oakley Key Determination Protocol • Internet Security Association and Key Management Protocol (ISAKMP) •
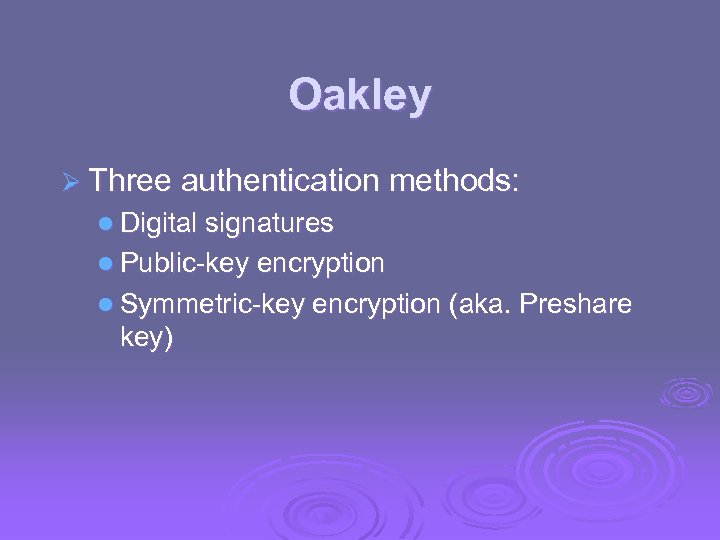 Oakley Ø Three authentication methods: l Digital signatures l Public-key encryption l Symmetric-key encryption (aka. Preshare key)
Oakley Ø Three authentication methods: l Digital signatures l Public-key encryption l Symmetric-key encryption (aka. Preshare key)
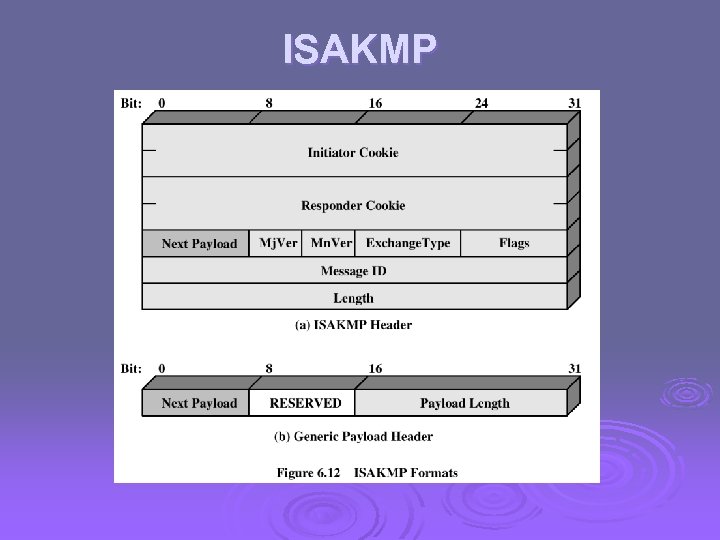 ISAKMP
ISAKMP
 Cryptography and Network Security Third Edition by William Stallings Lecture slides by Lawrie Brown Edited by Dick Steflik
Cryptography and Network Security Third Edition by William Stallings Lecture slides by Lawrie Brown Edited by Dick Steflik
 Web Security Ø Ø Web now widely used by business, government, individuals but Internet & Web are vulnerable have a variety of threats l integrity l confidentiality l denial of service l authentication need added security mechanisms
Web Security Ø Ø Web now widely used by business, government, individuals but Internet & Web are vulnerable have a variety of threats l integrity l confidentiality l denial of service l authentication need added security mechanisms
 SSL (Secure Socket Layer) Ø transport layer security service Ø originally developed by Netscape Ø version 3 designed with public input Ø subsequently became Internet standard known as TLS (Transport Layer Security) Ø uses TCP to provide a reliable end-to-end service Ø SSL has two layers of protocols
SSL (Secure Socket Layer) Ø transport layer security service Ø originally developed by Netscape Ø version 3 designed with public input Ø subsequently became Internet standard known as TLS (Transport Layer Security) Ø uses TCP to provide a reliable end-to-end service Ø SSL has two layers of protocols
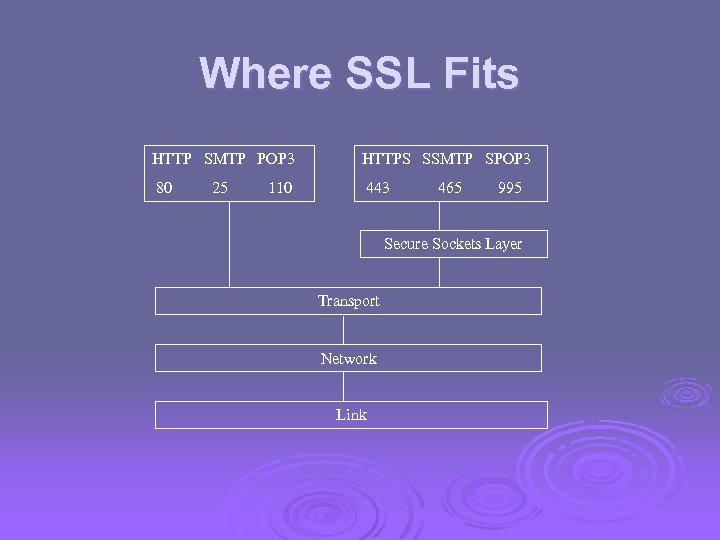 Where SSL Fits HTTP SMTP POP 3 HTTPS SSMTP SPOP 3 80 443 25 110 465 995 Secure Sockets Layer Transport Network Link
Where SSL Fits HTTP SMTP POP 3 HTTPS SSMTP SPOP 3 80 443 25 110 465 995 Secure Sockets Layer Transport Network Link
 Uses Public Key Scheme Ø Each client-server pair uses l 2 public keys • one for client (browser) l • created when browser is installed on client machine one for server (http server) l created when server is installed on server hardware l 2 private keys one for client browser • one for server (http server) •
Uses Public Key Scheme Ø Each client-server pair uses l 2 public keys • one for client (browser) l • created when browser is installed on client machine one for server (http server) l created when server is installed on server hardware l 2 private keys one for client browser • one for server (http server) •
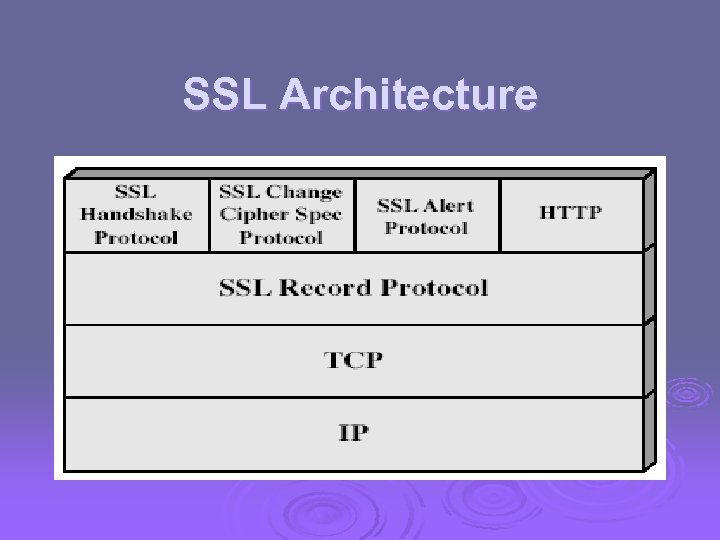 SSL Architecture
SSL Architecture
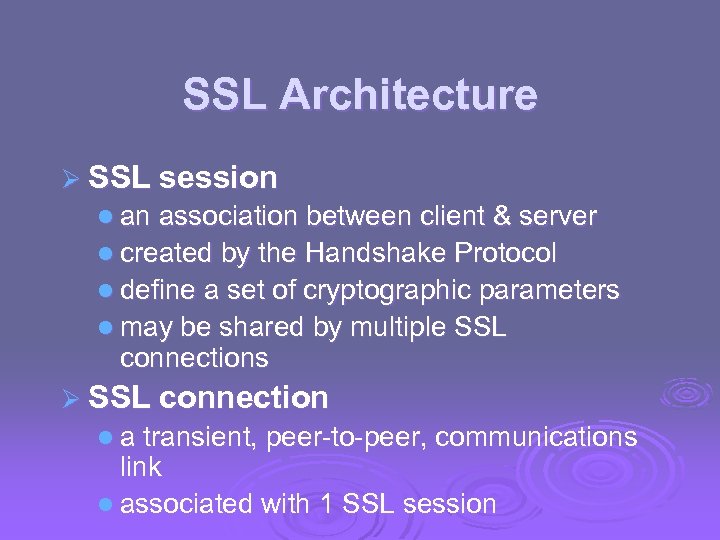 SSL Architecture Ø SSL session l an association between client & server l created by the Handshake Protocol l define a set of cryptographic parameters l may be shared by multiple SSL connections Ø SSL connection l a transient, peer-to-peer, communications link l associated with 1 SSL session
SSL Architecture Ø SSL session l an association between client & server l created by the Handshake Protocol l define a set of cryptographic parameters l may be shared by multiple SSL connections Ø SSL connection l a transient, peer-to-peer, communications link l associated with 1 SSL session
 SSL Record Protocol Ø confidentiality using symmetric encryption with a shared secret key defined by Handshake Protocol l IDEA, RC 2 -40, DES, 3 DES, Fortezza, RC 4 -40, RC 4 -128 l message is compressed before encryption l Ø message integrity l using a MAC (Message Authentication Code) created using a shared secret key and a short message
SSL Record Protocol Ø confidentiality using symmetric encryption with a shared secret key defined by Handshake Protocol l IDEA, RC 2 -40, DES, 3 DES, Fortezza, RC 4 -40, RC 4 -128 l message is compressed before encryption l Ø message integrity l using a MAC (Message Authentication Code) created using a shared secret key and a short message
 SSL Change Cipher Spec Protocol Ø one of 3 SSL specific protocols which use the SSL Record protocol Ø a single message Ø causes pending state to become current Ø hence updating the cipher suite in use
SSL Change Cipher Spec Protocol Ø one of 3 SSL specific protocols which use the SSL Record protocol Ø a single message Ø causes pending state to become current Ø hence updating the cipher suite in use
 SSL Alert Protocol conveys SSL-related alerts to peer entity Ø severity Ø • Ø warning or fatal specific alert unexpected message, bad record mac, decompression failure, handshake failure, illegal parameter • close notify, no certificate, bad certificate, unsupported certificate, certificate revoked, certificate expired, certificate unknown • Ø compressed & encrypted like all SSL data
SSL Alert Protocol conveys SSL-related alerts to peer entity Ø severity Ø • Ø warning or fatal specific alert unexpected message, bad record mac, decompression failure, handshake failure, illegal parameter • close notify, no certificate, bad certificate, unsupported certificate, certificate revoked, certificate expired, certificate unknown • Ø compressed & encrypted like all SSL data
 SSL Handshake Protocol Ø allows server & client to: authenticate each other l to negotiate encryption & MAC algorithms l to negotiate cryptographic keys to be used l Ø comprises a series of messages in phases Establish Security Capabilities l Server Authentication and Key Exchange l Client Authentication and Key Exchange l Finish l
SSL Handshake Protocol Ø allows server & client to: authenticate each other l to negotiate encryption & MAC algorithms l to negotiate cryptographic keys to be used l Ø comprises a series of messages in phases Establish Security Capabilities l Server Authentication and Key Exchange l Client Authentication and Key Exchange l Finish l
 SSL Handshake Protocol
SSL Handshake Protocol
 TLS (Transport Layer Security) IETF standard RFC 2246 similar to SSLv 3 Ø with minor differences Ø in record format version number l uses HMAC for MAC l a pseudo-random function expands secrets l has additional alert codes l some changes in supported ciphers l changes in certificate negotiations l changes in use of padding l
TLS (Transport Layer Security) IETF standard RFC 2246 similar to SSLv 3 Ø with minor differences Ø in record format version number l uses HMAC for MAC l a pseudo-random function expands secrets l has additional alert codes l some changes in supported ciphers l changes in certificate negotiations l changes in use of padding l
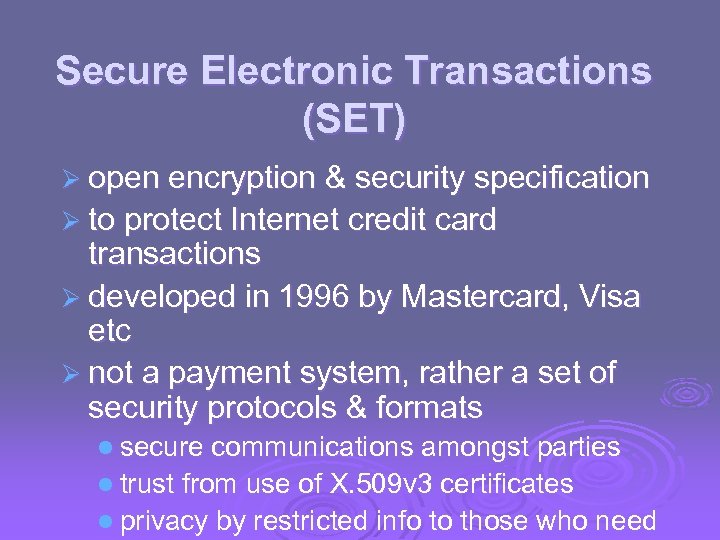 Secure Electronic Transactions (SET) Ø open encryption & security specification Ø to protect Internet credit card transactions Ø developed in 1996 by Mastercard, Visa etc Ø not a payment system, rather a set of security protocols & formats l secure communications amongst parties l trust from use of X. 509 v 3 certificates l privacy by restricted info to those who need
Secure Electronic Transactions (SET) Ø open encryption & security specification Ø to protect Internet credit card transactions Ø developed in 1996 by Mastercard, Visa etc Ø not a payment system, rather a set of security protocols & formats l secure communications amongst parties l trust from use of X. 509 v 3 certificates l privacy by restricted info to those who need
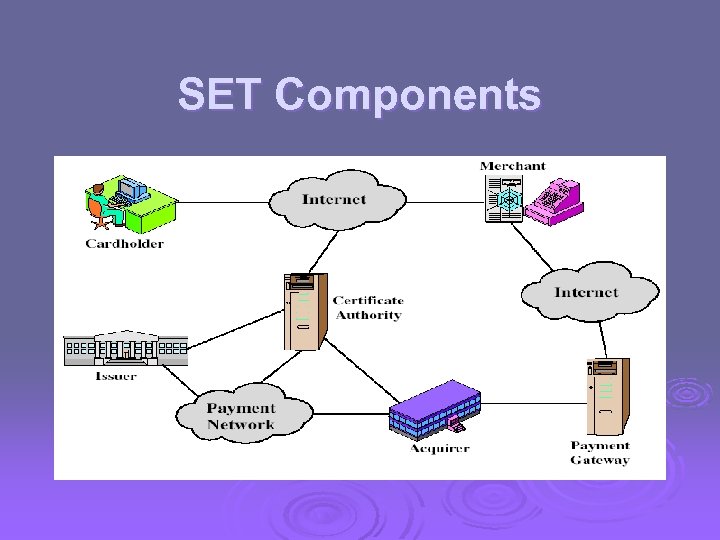 SET Components
SET Components
 SET Transaction 1. 2. 3. 4. 5. 6. 7. 8. 9. 10. customer opens account customer receives a certificate merchants have their own certificates customer places an order merchant is verified order and payment are sent merchant requests payment authorization merchant confirms order merchant provides goods or service merchant requests payment
SET Transaction 1. 2. 3. 4. 5. 6. 7. 8. 9. 10. customer opens account customer receives a certificate merchants have their own certificates customer places an order merchant is verified order and payment are sent merchant requests payment authorization merchant confirms order merchant provides goods or service merchant requests payment
 Dual Signature Ø customer creates dual messages l order information (OI) for merchant l payment information (PI) for bank Ø neither party needs details of other Ø but must know they are linked Ø use a dual signature for this l signed concatenated hashes of OI & PI
Dual Signature Ø customer creates dual messages l order information (OI) for merchant l payment information (PI) for bank Ø neither party needs details of other Ø but must know they are linked Ø use a dual signature for this l signed concatenated hashes of OI & PI
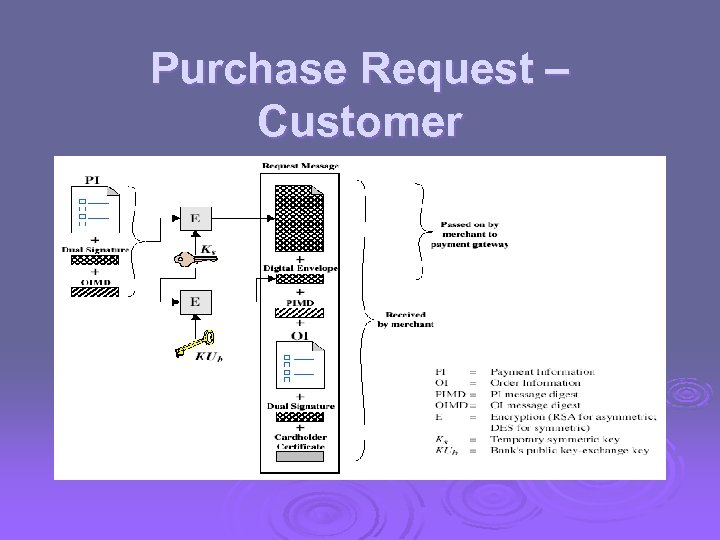 Purchase Request – Customer
Purchase Request – Customer
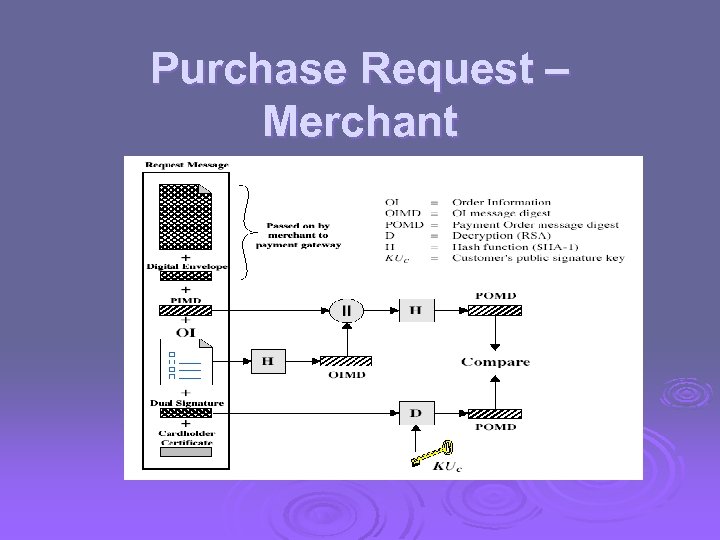 Purchase Request – Merchant
Purchase Request – Merchant
 Purchase Request – Merchant 1. 2. 3. 4. verifies cardholder certificates using CA sigs verifies dual signature using customer's public signature key to ensure order has not been tampered with in transit & that it was signed using cardholder's private signature key processes order and forwards the payment information to the payment gateway for authorization (described later) sends a purchase response to cardholder
Purchase Request – Merchant 1. 2. 3. 4. verifies cardholder certificates using CA sigs verifies dual signature using customer's public signature key to ensure order has not been tampered with in transit & that it was signed using cardholder's private signature key processes order and forwards the payment information to the payment gateway for authorization (described later) sends a purchase response to cardholder
 Payment Gateway Authorization 1. 2. 3. 4. 5. 6. 7. 8. verifies all certificates decrypts digital envelope of authorization block to obtain symmetric key & then decrypts authorization block verifies merchant's signature on authorization block decrypts digital envelope of payment block to obtain symmetric key & then decrypts payment block verifies dual signature on payment block verifies that transaction ID received from merchant matches that in PI received (indirectly) from customer requests & receives an authorization from issuer sends authorization response back to merchant
Payment Gateway Authorization 1. 2. 3. 4. 5. 6. 7. 8. verifies all certificates decrypts digital envelope of authorization block to obtain symmetric key & then decrypts authorization block verifies merchant's signature on authorization block decrypts digital envelope of payment block to obtain symmetric key & then decrypts payment block verifies dual signature on payment block verifies that transaction ID received from merchant matches that in PI received (indirectly) from customer requests & receives an authorization from issuer sends authorization response back to merchant
 Payment Capture Ø merchant sends payment gateway a payment capture request Ø gateway checks request Ø then causes funds to be transferred to merchants account Ø notifies merchant using capture response
Payment Capture Ø merchant sends payment gateway a payment capture request Ø gateway checks request Ø then causes funds to be transferred to merchants account Ø notifies merchant using capture response
 Summary Ø have considered: l need for web security l SSL/TLS transport layer security protocols l SET secure credit card payment protocols
Summary Ø have considered: l need for web security l SSL/TLS transport layer security protocols l SET secure credit card payment protocols


