fe3b13d2e9af6137398b5cb51271b3b9.ppt
- Количество слайдов: 57
 Cryptography and. NET Symmetric Cryptography Asymmetric Cryptography Digital Signatures XML Digital Signatures MSCF/CMU 1
Cryptography and. NET Symmetric Cryptography Asymmetric Cryptography Digital Signatures XML Digital Signatures MSCF/CMU 1
 Symmetric Cryptography • A single key is used to encrypt and decrypt data. • To encrypt a message M with key k compute C = Ek(M) • To decrypt a message C compute M = Dk(C) MSCF/CMU 2
Symmetric Cryptography • A single key is used to encrypt and decrypt data. • To encrypt a message M with key k compute C = Ek(M) • To decrypt a message C compute M = Dk(C) MSCF/CMU 2
 Symmetric Cryptography • A few important algorithms: DES (used in ATM machines) 56 -bit key Triple DES (important in banking) uses DES three times with three keys Rijndal (AES) 128 -, 192 -, or 256 -bit keys • In general, symmetric cryptography is fast and asymmetric cryptography is slow. • There is a key exchange problem MSCF/CMU 3
Symmetric Cryptography • A few important algorithms: DES (used in ATM machines) 56 -bit key Triple DES (important in banking) uses DES three times with three keys Rijndal (AES) 128 -, 192 -, or 256 -bit keys • In general, symmetric cryptography is fast and asymmetric cryptography is slow. • There is a key exchange problem MSCF/CMU 3
 . NET Symmetric Cryptography • In 1996 Microsoft introduced the Win 32 Crypto API for Windows NT • Written in old C • Not object oriented • Hard to use • . NET introduced an easy to use set of classes MSCF/CMU 4
. NET Symmetric Cryptography • In 1996 Microsoft introduced the Win 32 Crypto API for Windows NT • Written in old C • Not object oriented • Hard to use • . NET introduced an easy to use set of classes MSCF/CMU 4
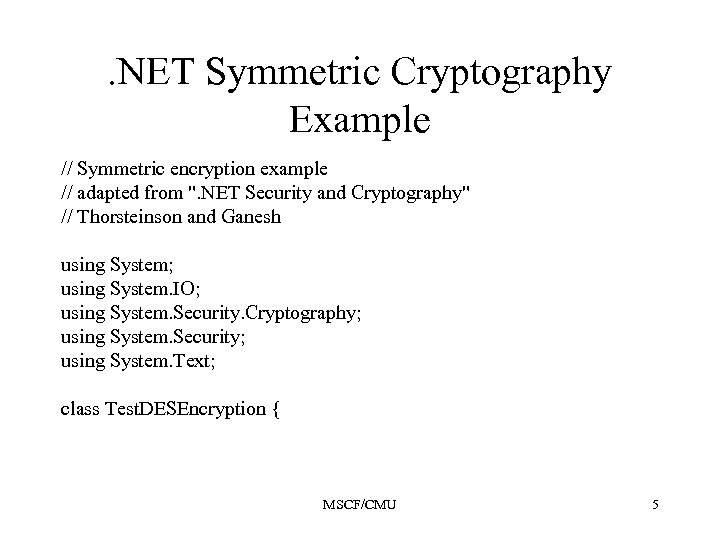 . NET Symmetric Cryptography Example // Symmetric encryption example // adapted from ". NET Security and Cryptography" // Thorsteinson and Ganesh using System; using System. IO; using System. Security. Cryptography; using System. Security; using System. Text; class Test. DESEncryption { MSCF/CMU 5
. NET Symmetric Cryptography Example // Symmetric encryption example // adapted from ". NET Security and Cryptography" // Thorsteinson and Ganesh using System; using System. IO; using System. Security. Cryptography; using System. Security; using System. Text; class Test. DESEncryption { MSCF/CMU 5
![// display byte array in Hex public static void Display. Bytes(byte[] b) { String. // display byte array in Hex public static void Display. Bytes(byte[] b) { String.](https://present5.com/presentation/fe3b13d2e9af6137398b5cb51271b3b9/image-6.jpg) // display byte array in Hex public static void Display. Bytes(byte[] b) { String. Builder sb = new String. Builder(); for (int i=0; i
// display byte array in Hex public static void Display. Bytes(byte[] b) { String. Builder sb = new String. Builder(); for (int i=0; i
![public static void Main(string[] args) { // four values to use for encryption and public static void Main(string[] args) { // four values to use for encryption and](https://present5.com/presentation/fe3b13d2e9af6137398b5cb51271b3b9/image-7.jpg) public static void Main(string[] args) { // four values to use for encryption and decryption byte[] key; byte[] iv; Cipher. Mode mode; Padding. Mode padding; // set the mode and padding mode = Cipher. Mode. CBC; padding = Padding. Mode. PKCS 7; MSCF/CMU 7
public static void Main(string[] args) { // four values to use for encryption and decryption byte[] key; byte[] iv; Cipher. Mode mode; Padding. Mode padding; // set the mode and padding mode = Cipher. Mode. CBC; padding = Padding. Mode. PKCS 7; MSCF/CMU 7
 // create the algorithm with a mode and padding Symmetric. Algorithm sa = DES. Create(); sa. Mode = mode; sa. Padding = padding; // ask the algorithm for an initialization vector and hold it sa. Generate. IV(); iv = sa. IV; // ask the algorithm for a random key and hold it sa. Generate. Key(); key = sa. Key; MSCF/CMU 8
// create the algorithm with a mode and padding Symmetric. Algorithm sa = DES. Create(); sa. Mode = mode; sa. Padding = padding; // ask the algorithm for an initialization vector and hold it sa. Generate. IV(); iv = sa. IV; // ask the algorithm for a random key and hold it sa. Generate. Key(); key = sa. Key; MSCF/CMU 8
![// experiment byte[] plainbytes; byte[] cipherbytes; // set up to write to an encrypted // experiment byte[] plainbytes; byte[] cipherbytes; // set up to write to an encrypted](https://present5.com/presentation/fe3b13d2e9af6137398b5cb51271b3b9/image-9.jpg) // experiment byte[] plainbytes; byte[] cipherbytes; // set up to write to an encrypted stream in memory Memory. Stream ms = new Memory. Stream(); Crypto. Stream cs = new Crypto. Stream(ms, sa. Create. Encryptor(), Crypto. Stream. Mode. Write); // get some bytes to write plainbytes = Encoding. UTF 8. Get. Bytes("Hello Mike!"); Display. Bytes(plainbytes); // write the bytes to the stream cs. Write(plainbytes, 0, plainbytes. Length); cs. Close(); MSCF/CMU 9
// experiment byte[] plainbytes; byte[] cipherbytes; // set up to write to an encrypted stream in memory Memory. Stream ms = new Memory. Stream(); Crypto. Stream cs = new Crypto. Stream(ms, sa. Create. Encryptor(), Crypto. Stream. Mode. Write); // get some bytes to write plainbytes = Encoding. UTF 8. Get. Bytes("Hello Mike!"); Display. Bytes(plainbytes); // write the bytes to the stream cs. Write(plainbytes, 0, plainbytes. Length); cs. Close(); MSCF/CMU 9
 // get the encrypted bytes cipherbytes = ms. To. Array(); Display. Bytes(cipherbytes); ms. Close(); // set up to read from and decrypt an encrypted stream in memory Memory. Stream cms = new Memory. Stream(cipherbytes); Crypto. Stream ccs = new Crypto. Stream( cms, sa. Create. Decryptor(), Crypto. Stream. Mode. Read); // make room for the resulting clear text byte[] resulting. Plain. Bytes = new Byte[cipherbytes. Length]; MSCF/CMU 10
// get the encrypted bytes cipherbytes = ms. To. Array(); Display. Bytes(cipherbytes); ms. Close(); // set up to read from and decrypt an encrypted stream in memory Memory. Stream cms = new Memory. Stream(cipherbytes); Crypto. Stream ccs = new Crypto. Stream( cms, sa. Create. Decryptor(), Crypto. Stream. Mode. Read); // make room for the resulting clear text byte[] resulting. Plain. Bytes = new Byte[cipherbytes. Length]; MSCF/CMU 10
 // decryption ccs. Read(resulting. Plain. Bytes, 0, cipherbytes. Length); ccs. Close(); cms. Close(); Display. Bytes(plainbytes); } } MSCF/CMU 11
// decryption ccs. Read(resulting. Plain. Bytes, 0, cipherbytes. Length); ccs. Close(); cms. Close(); Display. Bytes(plainbytes); } } MSCF/CMU 11
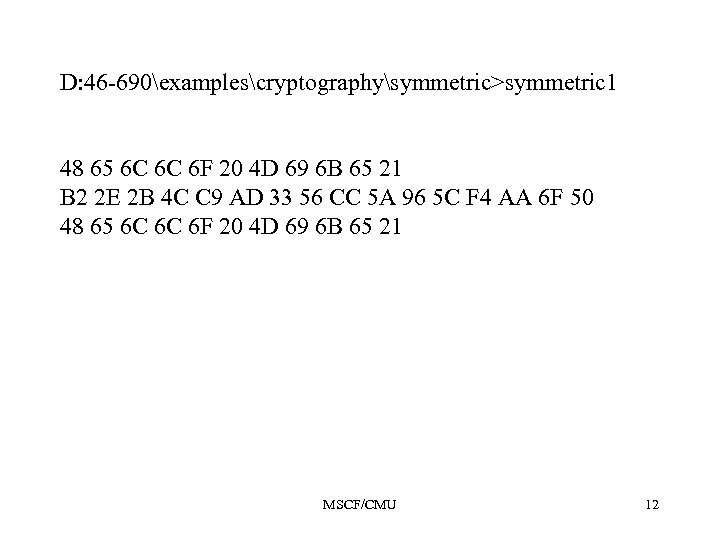 D: 46 -690examplescryptographysymmetric>symmetric 1 48 65 6 C 6 C 6 F 20 4 D 69 6 B 65 21 B 2 2 E 2 B 4 C C 9 AD 33 56 CC 5 A 96 5 C F 4 AA 6 F 50 48 65 6 C 6 C 6 F 20 4 D 69 6 B 65 21 MSCF/CMU 12
D: 46 -690examplescryptographysymmetric>symmetric 1 48 65 6 C 6 C 6 F 20 4 D 69 6 B 65 21 B 2 2 E 2 B 4 C C 9 AD 33 56 CC 5 A 96 5 C F 4 AA 6 F 50 48 65 6 C 6 C 6 F 20 4 D 69 6 B 65 21 MSCF/CMU 12
 Asymmetric Cryptography • Two keys rather than one • Public Key Cryptography was first introduced by Diffie and Hellman in 1976 • To encrypt a message M with key Public. Key compute C = E(M, Public. Key) • To decrypt a message C compute M = D(C, Private. Key) • There is a mathematical relationship between the Public. Key and the Private. Key and they are produced as a pair. Presumably, it is hard. MSCF/CMU to compute one from the other. 13
Asymmetric Cryptography • Two keys rather than one • Public Key Cryptography was first introduced by Diffie and Hellman in 1976 • To encrypt a message M with key Public. Key compute C = E(M, Public. Key) • To decrypt a message C compute M = D(C, Private. Key) • There is a mathematical relationship between the Public. Key and the Private. Key and they are produced as a pair. Presumably, it is hard. MSCF/CMU to compute one from the other. 13
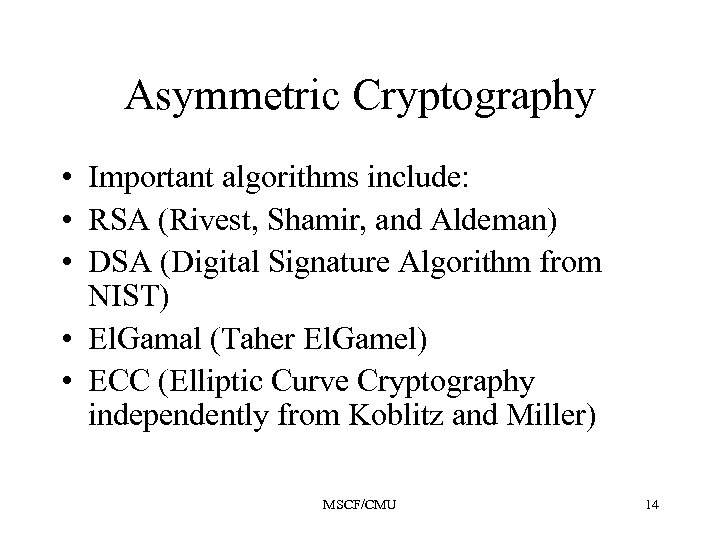 Asymmetric Cryptography • Important algorithms include: • RSA (Rivest, Shamir, and Aldeman) • DSA (Digital Signature Algorithm from NIST) • El. Gamal (Taher El. Gamel) • ECC (Elliptic Curve Cryptography independently from Koblitz and Miller) MSCF/CMU 14
Asymmetric Cryptography • Important algorithms include: • RSA (Rivest, Shamir, and Aldeman) • DSA (Digital Signature Algorithm from NIST) • El. Gamal (Taher El. Gamel) • ECC (Elliptic Curve Cryptography independently from Koblitz and Miller) MSCF/CMU 14
 Asymmetric Crytography RSA Toy Example Adapted From: Introduction to Algorithms Cormen, Leiserson and Rivest MSCF/CMU 15
Asymmetric Crytography RSA Toy Example Adapted From: Introduction to Algorithms Cormen, Leiserson and Rivest MSCF/CMU 15
 Purpose To send encrypted messages over an insecure channel To include an unforgeable “digital signature” with electronic messages. It’s the perfect tool for electronically signed business contracts, electronic checks, and any documents that need to be private or authenticated. MSCF/CMU 16
Purpose To send encrypted messages over an insecure channel To include an unforgeable “digital signature” with electronic messages. It’s the perfect tool for electronically signed business contracts, electronic checks, and any documents that need to be private or authenticated. MSCF/CMU 16
 The RSA Public-Key Cryptosystem • Developed by Rivest, Shamir, and Aldeman in 1977 • Since then the field of cryptography has blossomed MSCF/CMU 17
The RSA Public-Key Cryptosystem • Developed by Rivest, Shamir, and Aldeman in 1977 • Since then the field of cryptography has blossomed MSCF/CMU 17
 The RSA Public-Key Cryptosystem 1. Select at random two large prime numbers p and q. These numbers would normally be about 500 digits in length. 2. Compute n by the equation n = p X q. 3. Compute (n) = (p – 1) X (q – 1) 4. Select a small odd integer e that is relatively prime to (n) MSCF/CMU 18
The RSA Public-Key Cryptosystem 1. Select at random two large prime numbers p and q. These numbers would normally be about 500 digits in length. 2. Compute n by the equation n = p X q. 3. Compute (n) = (p – 1) X (q – 1) 4. Select a small odd integer e that is relatively prime to (n) MSCF/CMU 18
 The RSA Public-Key Cryptosystem 5. Compute d as the multiplicative inverse of e modulo (n). A theorem in number theory asserts that d exists and is uniquely defined. 6. Publish the pair P = (e, n) as the RSA public key. 7. Keep secret the pair S = (d, n) as the RSA secret key. MSCF/CMU 19
The RSA Public-Key Cryptosystem 5. Compute d as the multiplicative inverse of e modulo (n). A theorem in number theory asserts that d exists and is uniquely defined. 6. Publish the pair P = (e, n) as the RSA public key. 7. Keep secret the pair S = (d, n) as the RSA secret key. MSCF/CMU 19
 The RSA Public-Key Cryptosystem 8. To encrypt a message M compute C = Me (mod n) // e and n are public 9. To decrypt a message C compute M = Cd (mod n) // d is private MSCF/CMU 20
The RSA Public-Key Cryptosystem 8. To encrypt a message M compute C = Me (mod n) // e and n are public 9. To decrypt a message C compute M = Cd (mod n) // d is private MSCF/CMU 20
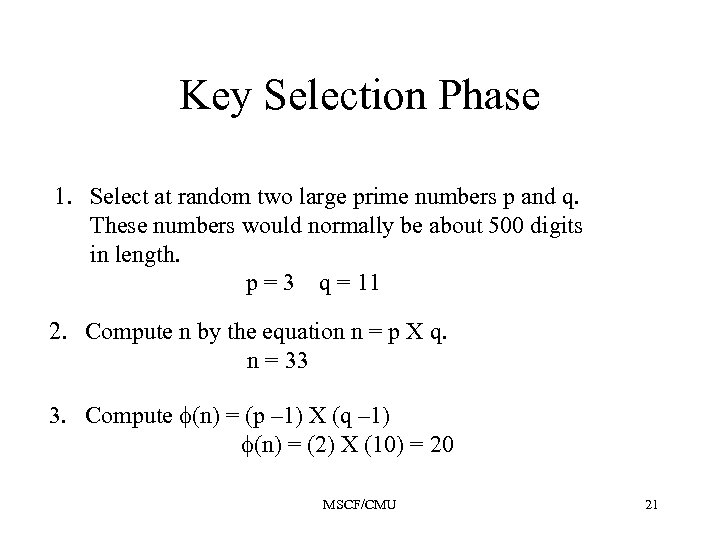 Key Selection Phase 1. Select at random two large prime numbers p and q. These numbers would normally be about 500 digits in length. p = 3 q = 11 2. Compute n by the equation n = p X q. n = 33 3. Compute (n) = (p – 1) X (q – 1) (n) = (2) X (10) = 20 MSCF/CMU 21
Key Selection Phase 1. Select at random two large prime numbers p and q. These numbers would normally be about 500 digits in length. p = 3 q = 11 2. Compute n by the equation n = p X q. n = 33 3. Compute (n) = (p – 1) X (q – 1) (n) = (2) X (10) = 20 MSCF/CMU 21
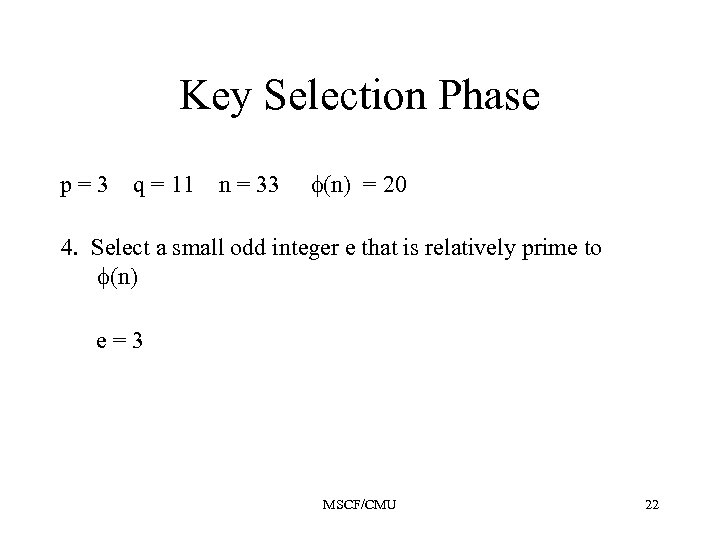 Key Selection Phase p=3 q = 11 n = 33 (n) = 20 4. Select a small odd integer e that is relatively prime to (n) e=3 MSCF/CMU 22
Key Selection Phase p=3 q = 11 n = 33 (n) = 20 4. Select a small odd integer e that is relatively prime to (n) e=3 MSCF/CMU 22
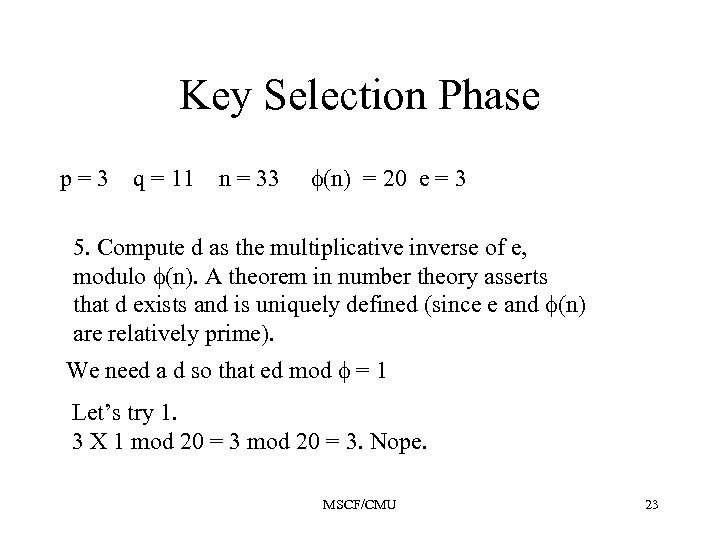 Key Selection Phase p=3 q = 11 n = 33 (n) = 20 e = 3 5. Compute d as the multiplicative inverse of e, modulo (n). A theorem in number theory asserts that d exists and is uniquely defined (since e and (n) are relatively prime). We need a d so that ed mod = 1 Let’s try 1. 3 X 1 mod 20 = 3. Nope. MSCF/CMU 23
Key Selection Phase p=3 q = 11 n = 33 (n) = 20 e = 3 5. Compute d as the multiplicative inverse of e, modulo (n). A theorem in number theory asserts that d exists and is uniquely defined (since e and (n) are relatively prime). We need a d so that ed mod = 1 Let’s try 1. 3 X 1 mod 20 = 3. Nope. MSCF/CMU 23
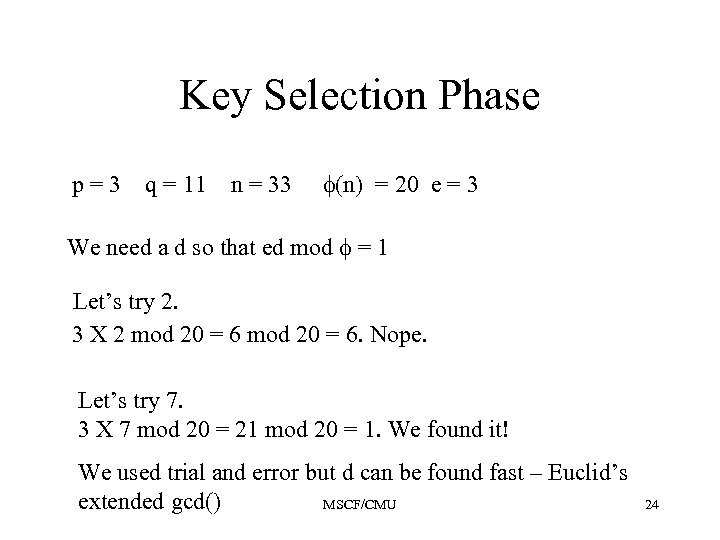 Key Selection Phase p=3 q = 11 n = 33 (n) = 20 e = 3 We need a d so that ed mod = 1 Let’s try 2. 3 X 2 mod 20 = 6. Nope. Let’s try 7. 3 X 7 mod 20 = 21 mod 20 = 1. We found it! We used trial and error but d can be found fast – Euclid’s extended gcd() MSCF/CMU 24
Key Selection Phase p=3 q = 11 n = 33 (n) = 20 e = 3 We need a d so that ed mod = 1 Let’s try 2. 3 X 2 mod 20 = 6. Nope. Let’s try 7. 3 X 7 mod 20 = 21 mod 20 = 1. We found it! We used trial and error but d can be found fast – Euclid’s extended gcd() MSCF/CMU 24
 Key Selection Phase p=3 q = 11 n = 33 (n) = 20 e = 3 d = 7 6. Publish the pair P = (e, n) as the RSA public key. “Hey everyone, my key pair is 3 and 33” 7. Keep secret the pair S = (d, n) as the RSA secret key. “I’m not telling anyone about 7 and 33!!” MSCF/CMU 25
Key Selection Phase p=3 q = 11 n = 33 (n) = 20 e = 3 d = 7 6. Publish the pair P = (e, n) as the RSA public key. “Hey everyone, my key pair is 3 and 33” 7. Keep secret the pair S = (d, n) as the RSA secret key. “I’m not telling anyone about 7 and 33!!” MSCF/CMU 25
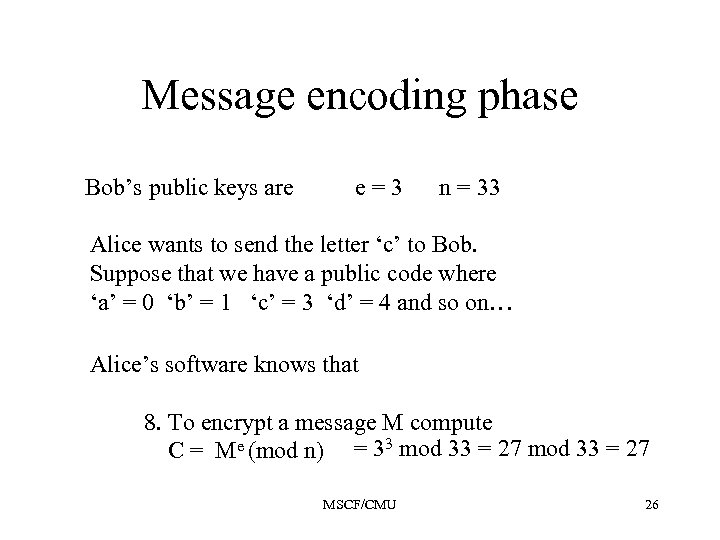 Message encoding phase Bob’s public keys are e=3 n = 33 Alice wants to send the letter ‘c’ to Bob. Suppose that we have a public code where ‘a’ = 0 ‘b’ = 1 ‘c’ = 3 ‘d’ = 4 and so on… Alice’s software knows that 8. To encrypt a message M compute C = Me (mod n) = 33 mod 33 = 27 MSCF/CMU 26
Message encoding phase Bob’s public keys are e=3 n = 33 Alice wants to send the letter ‘c’ to Bob. Suppose that we have a public code where ‘a’ = 0 ‘b’ = 1 ‘c’ = 3 ‘d’ = 4 and so on… Alice’s software knows that 8. To encrypt a message M compute C = Me (mod n) = 33 mod 33 = 27 MSCF/CMU 26
 Message decoding phase Bob’s private keys are d=7 n = 33 Bob receives a 27 from someone (he thinks it may be Alice? ) 9. To decrypt a message C compute M = Cd (mod n) = 277 mod 33 = 10460353203 mod 33 =3 MSCF/CMU 27
Message decoding phase Bob’s private keys are d=7 n = 33 Bob receives a 27 from someone (he thinks it may be Alice? ) 9. To decrypt a message C compute M = Cd (mod n) = 277 mod 33 = 10460353203 mod 33 =3 MSCF/CMU 27
 . NET Asymmetric Cryptography • . NET supports RSA, DSA • . NET provides the capability to add ECC and El. Gamal from third parties • Is very similar to Java’s Cryptography API MSCF/CMU 28
. NET Asymmetric Cryptography • . NET supports RSA, DSA • . NET provides the capability to add ECC and El. Gamal from third parties • Is very similar to Java’s Cryptography API MSCF/CMU 28
 . NET Asymmetric Cryptography Example // RSA Asymmetric encryption example // adapted from ". NET Security and Cryptography" // Thorsteinson and Ganesh using System; using System. IO; using System. Security. Cryptography; using System. Security; using System. Text; MSCF/CMU 29
. NET Asymmetric Cryptography Example // RSA Asymmetric encryption example // adapted from ". NET Security and Cryptography" // Thorsteinson and Ganesh using System; using System. IO; using System. Security. Cryptography; using System. Security; using System. Text; MSCF/CMU 29
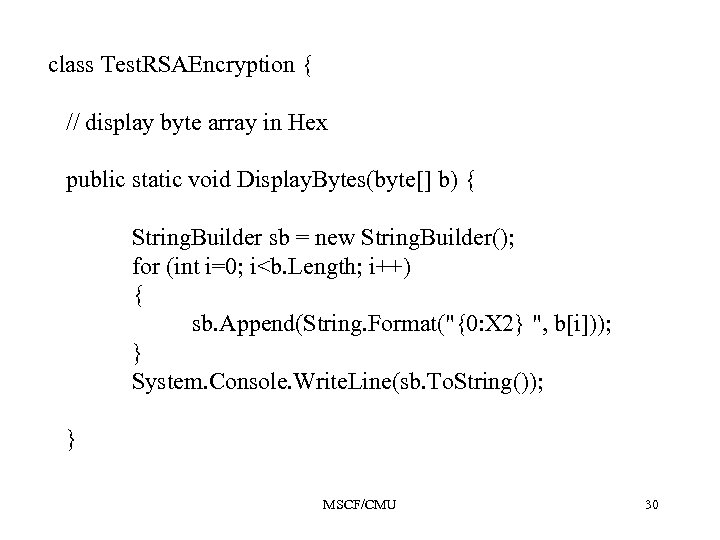 class Test. RSAEncryption { // display byte array in Hex public static void Display. Bytes(byte[] b) { String. Builder sb = new String. Builder(); for (int i=0; i
class Test. RSAEncryption { // display byte array in Hex public static void Display. Bytes(byte[] b) { String. Builder sb = new String. Builder(); for (int i=0; i
![public static void Main(string[] args) { //public modulus and exponent used in encryption RSAParameters public static void Main(string[] args) { //public modulus and exponent used in encryption RSAParameters](https://present5.com/presentation/fe3b13d2e9af6137398b5cb51271b3b9/image-31.jpg) public static void Main(string[] args) { //public modulus and exponent used in encryption RSAParameters rsa. Params. Exclude. Private; //public and private RSA params use in decryption RSAParameters rsa. Params. Include. Private; //establish RSA asymmetric algorithm RSACrypto. Service. Provider rsa = new RSACrypto. Service. Provider(); //provide public and private RSA params rsa. Params. Include. Private = rsa. Export. Parameters(true); MSCF/CMU 31
public static void Main(string[] args) { //public modulus and exponent used in encryption RSAParameters rsa. Params. Exclude. Private; //public and private RSA params use in decryption RSAParameters rsa. Params. Include. Private; //establish RSA asymmetric algorithm RSACrypto. Service. Provider rsa = new RSACrypto. Service. Provider(); //provide public and private RSA params rsa. Params. Include. Private = rsa. Export. Parameters(true); MSCF/CMU 31
 //provide public only RSA params rsa. Params. Exclude. Private = rsa. Export. Parameters(false); //display RSA parameter details in hex format String. Builder sb; // display public e sb = new String. Builder(); for (int i=0; i
//provide public only RSA params rsa. Params. Exclude. Private = rsa. Export. Parameters(false); //display RSA parameter details in hex format String. Builder sb; // display public e sb = new String. Builder(); for (int i=0; i
 // display public Modulus sb = new String. Builder(); for (int i=0; i
// display public Modulus sb = new String. Builder(); for (int i=0; i
 // display private d sb = new String. Builder(); for (int i=0; i
// display private d sb = new String. Builder(); for (int i=0; i
 // encrypt some text RSACrypto. Service. Provider newrsa = new RSACrypto. Service. Provider(); //import public only RSA parameters for encrypt newrsa. Import. Parameters(rsa. Params. Exclude. Private); //read plaintext, encrypt it to ciphertext byte[] plainbytes = Encoding. UTF 8. Get. Bytes("Buy IBM"); byte[] cipherbytes = newrsa. Encrypt(plainbytes, false); //display ciphertext as text string Display. Bytes(cipherbytes); MSCF/CMU 35
// encrypt some text RSACrypto. Service. Provider newrsa = new RSACrypto. Service. Provider(); //import public only RSA parameters for encrypt newrsa. Import. Parameters(rsa. Params. Exclude. Private); //read plaintext, encrypt it to ciphertext byte[] plainbytes = Encoding. UTF 8. Get. Bytes("Buy IBM"); byte[] cipherbytes = newrsa. Encrypt(plainbytes, false); //display ciphertext as text string Display. Bytes(cipherbytes); MSCF/CMU 35
 RSACrypto. Service. Provider anotherrsa = new RSACrypto. Service. Provider(); //import RSA parameters for decrypt anotherrsa. Import. Parameters(rsa. Params. Include. Private); //read ciphertext, decrypt it to plaintext plainbytes = anotherrsa. Decrypt(cipherbytes, false); //display recovered plaintext string recovered = Encoding. UTF 8. Get. String(plainbytes); Console. Write. Line(recovered); } MSCF/CMU } 36
RSACrypto. Service. Provider anotherrsa = new RSACrypto. Service. Provider(); //import RSA parameters for decrypt anotherrsa. Import. Parameters(rsa. Params. Include. Private); //read ciphertext, decrypt it to plaintext plainbytes = anotherrsa. Decrypt(cipherbytes, false); //display recovered plaintext string recovered = Encoding. UTF 8. Get. String(plainbytes); Console. Write. Line(recovered); } MSCF/CMU } 36
 D: cryptographyRSAExample>RSAExample e = 01 00 01 n = D 4 C 5 A 7 94 D 6 55 93 00 C 5 47 2 D 8 D DA 78 BF 4 F E 9 42 BF 9 B 47 21 93 69 4 F C 7 43 D 1 37 B 8 1 E A 8 B 6 D 5 69 D 4 D 1 C 7 F 5 B 4 D 7 13 02 EB 98 A 6 1 F 56 87 95 68 8 A 12 A 1 C 0 14 33 01 9 B 02 31 E 5 89 39 DD A 6 62 6 C 07 38 BA 22 71 18 BD 87 6 F 37 F 5 A 4 6 F F 1 13 CE 1 E BF D 7 BC 8 F 91 15 ED 52 22 01 63 09 C 1 66 F 6 5 B 57 88 F 6 AC 35 05 EA 3 B 76 76 E 8 FB 6 C 97 52 0 B F 3 51 37 8 C 88 6 D 12 7 F 91 7 B 67 MSCF/CMU 37
D: cryptographyRSAExample>RSAExample e = 01 00 01 n = D 4 C 5 A 7 94 D 6 55 93 00 C 5 47 2 D 8 D DA 78 BF 4 F E 9 42 BF 9 B 47 21 93 69 4 F C 7 43 D 1 37 B 8 1 E A 8 B 6 D 5 69 D 4 D 1 C 7 F 5 B 4 D 7 13 02 EB 98 A 6 1 F 56 87 95 68 8 A 12 A 1 C 0 14 33 01 9 B 02 31 E 5 89 39 DD A 6 62 6 C 07 38 BA 22 71 18 BD 87 6 F 37 F 5 A 4 6 F F 1 13 CE 1 E BF D 7 BC 8 F 91 15 ED 52 22 01 63 09 C 1 66 F 6 5 B 57 88 F 6 AC 35 05 EA 3 B 76 76 E 8 FB 6 C 97 52 0 B F 3 51 37 8 C 88 6 D 12 7 F 91 7 B 67 MSCF/CMU 37
 d = 88 57 3 B 82 51 31 B 6 A 8 18 C 1 FA 7 B DA 91 E 3 2 D 86 B 0 41 ED 73 50 1 D 90 AF 11 65 F 0 8 B BE CC CE 99 91 F 9 65 E 9 23 33 DC 34 B 1 36 FE D 6 EB 24 4 B A 3 47 E 7 1 C 0 A C 2 61 3 D D 0 4 D 68 11 A 8 FD 87 C 7 44 60 AB 2 B 5 B 5 C B 0 E 0 D 3 F 0 A 6 FB 8 F 37 D 8 D 1 01 48 AA CD 81 6 A 79 E 2 F 4 83 74 13 B 3 46 DF 6 B 56 4 B CC 3 C 94 D 9 19 47 B 4 02 63 AD C 5 FB 20 31 04 6 B BE 5 C E 8 15 2 C DE C 9 B 7 9 C 28 5 D A 0 5 D A 1 Encrypted data (added to slide) 2 D 2 D E 2 E 7 F 4 1 D 93 1 D 18 72 77 5 B 31 73 43 6 B 33 54 EB 5 D BC C 0 56 25 29 42 3 F B 9 A 1 34 5 E 20 FF 8 E 6 A 9 D 06 36 01 42 91 32 D 6 24 EE CC D 6 C 4 D 5 2 A 7 B 7 C 2 D 18 99 BC 72 9 F 55 B 5 A 8 BB A 9 50 3 D 11 61 3 E 5 F 78 32 38 F 6 93 53 E 6 FF 42 28 03 0 D B 7 AE 52 77 3 F BC 48 97 21 5 E 32 79 2 A 6 B 77 34 26 2 F 30 2 E 72 83 D 6 57 F 4 3 F C 6 30 12 28 68 62 0 A 2 F EF 04 16 94 81 CE 78 46 36 67 C 7 93 DA Buy IBM MSCF/CMU 38
d = 88 57 3 B 82 51 31 B 6 A 8 18 C 1 FA 7 B DA 91 E 3 2 D 86 B 0 41 ED 73 50 1 D 90 AF 11 65 F 0 8 B BE CC CE 99 91 F 9 65 E 9 23 33 DC 34 B 1 36 FE D 6 EB 24 4 B A 3 47 E 7 1 C 0 A C 2 61 3 D D 0 4 D 68 11 A 8 FD 87 C 7 44 60 AB 2 B 5 B 5 C B 0 E 0 D 3 F 0 A 6 FB 8 F 37 D 8 D 1 01 48 AA CD 81 6 A 79 E 2 F 4 83 74 13 B 3 46 DF 6 B 56 4 B CC 3 C 94 D 9 19 47 B 4 02 63 AD C 5 FB 20 31 04 6 B BE 5 C E 8 15 2 C DE C 9 B 7 9 C 28 5 D A 0 5 D A 1 Encrypted data (added to slide) 2 D 2 D E 2 E 7 F 4 1 D 93 1 D 18 72 77 5 B 31 73 43 6 B 33 54 EB 5 D BC C 0 56 25 29 42 3 F B 9 A 1 34 5 E 20 FF 8 E 6 A 9 D 06 36 01 42 91 32 D 6 24 EE CC D 6 C 4 D 5 2 A 7 B 7 C 2 D 18 99 BC 72 9 F 55 B 5 A 8 BB A 9 50 3 D 11 61 3 E 5 F 78 32 38 F 6 93 53 E 6 FF 42 28 03 0 D B 7 AE 52 77 3 F BC 48 97 21 5 E 32 79 2 A 6 B 77 34 26 2 F 30 2 E 72 83 D 6 57 F 4 3 F C 6 30 12 28 68 62 0 A 2 F EF 04 16 94 81 CE 78 46 36 67 C 7 93 DA Buy IBM MSCF/CMU 38
 Digital Signatures • Suppose M is the message “Transfer $500. 00 from my account to Joe’s account” • Anyone may compute a hash of M called h(M) • Sign by computing S = E(h(M), Private. Key) • To verify a signature compute h’(M) = D(S, Public. Key) and check if h(M) == h’(M) MSCF/CMU 39
Digital Signatures • Suppose M is the message “Transfer $500. 00 from my account to Joe’s account” • Anyone may compute a hash of M called h(M) • Sign by computing S = E(h(M), Private. Key) • To verify a signature compute h’(M) = D(S, Public. Key) and check if h(M) == h’(M) MSCF/CMU 39
 . NET Digital Signatures • The two most widely used hash algorithms are: • SHA-1 from NIST (mid 1990’s) • MD 5 from Rivest (early 1990’s) • . NET supports these and others • Output is a small, fixed length series of bits that is hard to generate with any other message MSCF/CMU 40
. NET Digital Signatures • The two most widely used hash algorithms are: • SHA-1 from NIST (mid 1990’s) • MD 5 from Rivest (early 1990’s) • . NET supports these and others • Output is a small, fixed length series of bits that is hard to generate with any other message MSCF/CMU 40
 . NET Digital Signature Example // Digital signature example // Code adapted from ". NET Security and Cryptography" // Thorsteinson and Ganesh using System; using System. IO; using System. Security. Cryptography; using System. Security; using System. Text; class Test. RSADigital. Signature { // display byte array in Hex MSCF/CMU 41
. NET Digital Signature Example // Digital signature example // Code adapted from ". NET Security and Cryptography" // Thorsteinson and Ganesh using System; using System. IO; using System. Security. Cryptography; using System. Security; using System. Text; class Test. RSADigital. Signature { // display byte array in Hex MSCF/CMU 41
![public static void Display. Bytes(byte[] b) { String. Builder sb = new String. Builder(); public static void Display. Bytes(byte[] b) { String. Builder sb = new String. Builder();](https://present5.com/presentation/fe3b13d2e9af6137398b5cb51271b3b9/image-42.jpg) public static void Display. Bytes(byte[] b) { String. Builder sb = new String. Builder(); for (int i=0; i
public static void Display. Bytes(byte[] b) { String. Builder sb = new String. Builder(); for (int i=0; i
![public static void Main(string[] args) { //get original message as byte array string msg public static void Main(string[] args) { //get original message as byte array string msg](https://present5.com/presentation/fe3b13d2e9af6137398b5cb51271b3b9/image-43.jpg) public static void Main(string[] args) { //get original message as byte array string msg = "Transfer $500. 00 from my account to Joe's account"; byte[] messagebytes = Encoding. UTF 8. Get. Bytes(msg); Console. Write. Line("nn. Original message"); Console. Write. Line(msg + "n"); Console. Write. Line("Message bytes"); Display. Bytes(messagebytes); byte[] signaturebytes; MSCF/CMU 43
public static void Main(string[] args) { //get original message as byte array string msg = "Transfer $500. 00 from my account to Joe's account"; byte[] messagebytes = Encoding. UTF 8. Get. Bytes(msg); Console. Write. Line("nn. Original message"); Console. Write. Line(msg + "n"); Console. Write. Line("Message bytes"); Display. Bytes(messagebytes); byte[] signaturebytes; MSCF/CMU 43
 //create digest of original message using SHA 1 sha 1 = new SHA 1 Crypto. Service. Provider(); byte[] hashbytes = sha 1. Compute. Hash(messagebytes); Console. Write. Line("Hash of message"); Display. Bytes(hashbytes); //create RSA object using default key RSACrypto. Service. Provider rsa = new RSACrypto. Service. Provider(); //sign hash using OID (Object IDentifier) for SHA-1 signaturebytes = rsa. Sign. Hash(hashbytes, "1. 3. 14. 3. 2. 26"); MSCF/CMU 44
//create digest of original message using SHA 1 sha 1 = new SHA 1 Crypto. Service. Provider(); byte[] hashbytes = sha 1. Compute. Hash(messagebytes); Console. Write. Line("Hash of message"); Display. Bytes(hashbytes); //create RSA object using default key RSACrypto. Service. Provider rsa = new RSACrypto. Service. Provider(); //sign hash using OID (Object IDentifier) for SHA-1 signaturebytes = rsa. Sign. Hash(hashbytes, "1. 3. 14. 3. 2. 26"); MSCF/CMU 44
 //provide RSA parameters to verification RSAParameters rsaparams = rsa. Export. Parameters(false); //display digital signature in hex format Console. Write. Line( "n. RSA Signature = (Hash of message)^d mod n n"); Display. Bytes(signaturebytes); //display modulus Console. Write. Line("n Public modulus needed for verificationn"); Display. Bytes(rsaparams. Modulus); Console. Write. Line("n. Public exponent (e) needed for verificationn"); // display exponent Display. Bytes(rsaparams. Exponent); MSCF/CMU 45
//provide RSA parameters to verification RSAParameters rsaparams = rsa. Export. Parameters(false); //display digital signature in hex format Console. Write. Line( "n. RSA Signature = (Hash of message)^d mod n n"); Display. Bytes(signaturebytes); //display modulus Console. Write. Line("n Public modulus needed for verificationn"); Display. Bytes(rsaparams. Modulus); Console. Write. Line("n. Public exponent (e) needed for verificationn"); // display exponent Display. Bytes(rsaparams. Exponent); MSCF/CMU 45
![// verify signature //get possibly modified message as byte array byte[] newmessagebytes = Encoding. // verify signature //get possibly modified message as byte array byte[] newmessagebytes = Encoding.](https://present5.com/presentation/fe3b13d2e9af6137398b5cb51271b3b9/image-46.jpg) // verify signature //get possibly modified message as byte array byte[] newmessagebytes = Encoding. UTF 8. Get. Bytes(msg); //create digest of original message using SHA 1 newsha 1 = new SHA 1 Crypto. Service. Provider(); byte[] newhashbytes = sha 1. Compute. Hash(newmessagebytes); //create RSA object using parameters from signing RSACrypto. Service. Provider newrsa = new RSACrypto. Service. Provider(); newrsa. Import. Parameters(rsaparams); MSCF/CMU 46
// verify signature //get possibly modified message as byte array byte[] newmessagebytes = Encoding. UTF 8. Get. Bytes(msg); //create digest of original message using SHA 1 newsha 1 = new SHA 1 Crypto. Service. Provider(); byte[] newhashbytes = sha 1. Compute. Hash(newmessagebytes); //create RSA object using parameters from signing RSACrypto. Service. Provider newrsa = new RSACrypto. Service. Provider(); newrsa. Import. Parameters(rsaparams); MSCF/CMU 46
 //do verification on hash using OID for SHA-1 bool match = newrsa. Verify. Hash( newhashbytes, "1. 3. 14. 3. 2. 26", signaturebytes); if (match) Console. Write. Line("Signature verified"); else Console. Write. Line("Signature not verified"); } } MSCF/CMU 47
//do verification on hash using OID for SHA-1 bool match = newrsa. Verify. Hash( newhashbytes, "1. 3. 14. 3. 2. 26", signaturebytes); if (match) Console. Write. Line("Signature verified"); else Console. Write. Line("Signature not verified"); } } MSCF/CMU 47
 Original message Transfer $500. 00 from my account to Joe's account Message bytes 54 72 61 6 E 73 66 65 72 20 24 35 30 30 2 E 30 30 20 66 72 6 F 6 D 20 6 D 79 20 61 63 63 6 F 75 6 E 74 20 74 6 F 20 4 A 6 F 65 27 73 20 61 63 63 6 F 75 6 E 74 Hash of message 79 0 F 47 A 5 00 6 A 40 91 9 F 65 93 A 8 13 69 7 F 17 23 0 A 7 A 81 MSCF/CMU 48
Original message Transfer $500. 00 from my account to Joe's account Message bytes 54 72 61 6 E 73 66 65 72 20 24 35 30 30 2 E 30 30 20 66 72 6 F 6 D 20 6 D 79 20 61 63 63 6 F 75 6 E 74 20 74 6 F 20 4 A 6 F 65 27 73 20 61 63 63 6 F 75 6 E 74 Hash of message 79 0 F 47 A 5 00 6 A 40 91 9 F 65 93 A 8 13 69 7 F 17 23 0 A 7 A 81 MSCF/CMU 48
 RSA Signature = (Hash of message)^d mod n 6 A 4 E 27 3 D A 6 76 C 4 0 F 38 1 E 14 57 6 E 45 83 7 F 62 D 3 85 20 4 C 5 C EA B 2 98 10 CF AE 85 0 C 8 D 70 BA 73 FE 54 79 60 88 D 7 2 B 44 70 01 EE 70 0 F D 2 D 7 A 6 90 C 1 B 0 2 A 17 97 E 2 1 A E 5 5 F EB F 7 C 5 83 F 1 4 F CD AD EB FD 40 E 1 AF 9 E F 7 A 9 1 D 25 F 3 46 4 F 31 84 7 C 8 B 01 BB 72 80 63 25 04 D 5 15 A 9 71 CC F 8 66 6 E 5 D F 3 00 E 8 68 D 3 D 6 7 C CE 24 69 93 66 76 B 5 88 A 4 08 9 C ED AE 98 CC 66 45 F 6 F 8 BC MSCF/CMU 49
RSA Signature = (Hash of message)^d mod n 6 A 4 E 27 3 D A 6 76 C 4 0 F 38 1 E 14 57 6 E 45 83 7 F 62 D 3 85 20 4 C 5 C EA B 2 98 10 CF AE 85 0 C 8 D 70 BA 73 FE 54 79 60 88 D 7 2 B 44 70 01 EE 70 0 F D 2 D 7 A 6 90 C 1 B 0 2 A 17 97 E 2 1 A E 5 5 F EB F 7 C 5 83 F 1 4 F CD AD EB FD 40 E 1 AF 9 E F 7 A 9 1 D 25 F 3 46 4 F 31 84 7 C 8 B 01 BB 72 80 63 25 04 D 5 15 A 9 71 CC F 8 66 6 E 5 D F 3 00 E 8 68 D 3 D 6 7 C CE 24 69 93 66 76 B 5 88 A 4 08 9 C ED AE 98 CC 66 45 F 6 F 8 BC MSCF/CMU 49
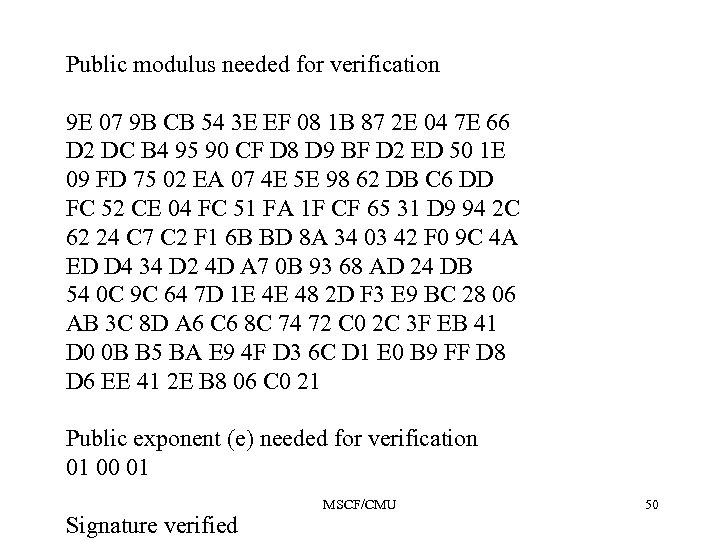 Public modulus needed for verification 9 E 07 9 B CB 54 3 E EF 08 1 B 87 2 E 04 7 E 66 D 2 DC B 4 95 90 CF D 8 D 9 BF D 2 ED 50 1 E 09 FD 75 02 EA 07 4 E 5 E 98 62 DB C 6 DD FC 52 CE 04 FC 51 FA 1 F CF 65 31 D 9 94 2 C 62 24 C 7 C 2 F 1 6 B BD 8 A 34 03 42 F 0 9 C 4 A ED D 4 34 D 2 4 D A 7 0 B 93 68 AD 24 DB 54 0 C 9 C 64 7 D 1 E 4 E 48 2 D F 3 E 9 BC 28 06 AB 3 C 8 D A 6 C 6 8 C 74 72 C 0 2 C 3 F EB 41 D 0 0 B B 5 BA E 9 4 F D 3 6 C D 1 E 0 B 9 FF D 8 D 6 EE 41 2 E B 8 06 C 0 21 Public exponent (e) needed for verification 01 00 01 Signature verified MSCF/CMU 50
Public modulus needed for verification 9 E 07 9 B CB 54 3 E EF 08 1 B 87 2 E 04 7 E 66 D 2 DC B 4 95 90 CF D 8 D 9 BF D 2 ED 50 1 E 09 FD 75 02 EA 07 4 E 5 E 98 62 DB C 6 DD FC 52 CE 04 FC 51 FA 1 F CF 65 31 D 9 94 2 C 62 24 C 7 C 2 F 1 6 B BD 8 A 34 03 42 F 0 9 C 4 A ED D 4 34 D 2 4 D A 7 0 B 93 68 AD 24 DB 54 0 C 9 C 64 7 D 1 E 4 E 48 2 D F 3 E 9 BC 28 06 AB 3 C 8 D A 6 C 6 8 C 74 72 C 0 2 C 3 F EB 41 D 0 0 B B 5 BA E 9 4 F D 3 6 C D 1 E 0 B 9 FF D 8 D 6 EE 41 2 E B 8 06 C 0 21 Public exponent (e) needed for verification 01 00 01 Signature verified MSCF/CMU 50
 XML Digital Signatures • . NET supports XMLDSIG • XMLDSIG is a standard from the W 3 C • This example was taken from “. NET Security and Cryptography” by Thorsteinson and Ganesh • The following slides contain linebreaks so they can be read MSCF/CMU 51
XML Digital Signatures • . NET supports XMLDSIG • XMLDSIG is a standard from the W 3 C • This example was taken from “. NET Security and Cryptography” by Thorsteinson and Ganesh • The following slides contain linebreaks so they can be read MSCF/CMU 51
 Initial Document To Be Signed
Initial Document To Be Signed




