 Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
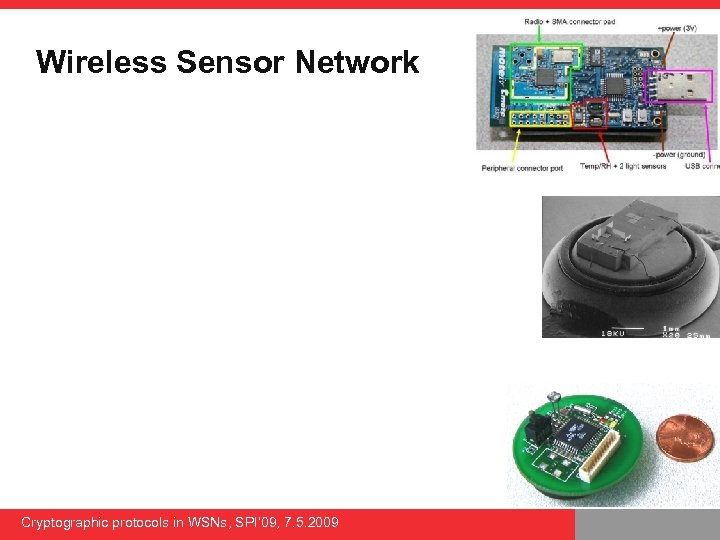 Wireless Sensor Network Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
Wireless Sensor Network Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
 Large scale Wireless Sensor Networks Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
Large scale Wireless Sensor Networks Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
 Where do we need security in WSN? Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
Where do we need security in WSN? Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
 Differences from classical networks Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
Differences from classical networks Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
 Security threats Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
Security threats Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
 Why not use “classical” solutions? Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
Why not use “classical” solutions? Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
 Power analysis device Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
Power analysis device Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
 Reverse engineering Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
Reverse engineering Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
 Probabilistic key pre-distribution Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
Probabilistic key pre-distribution Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
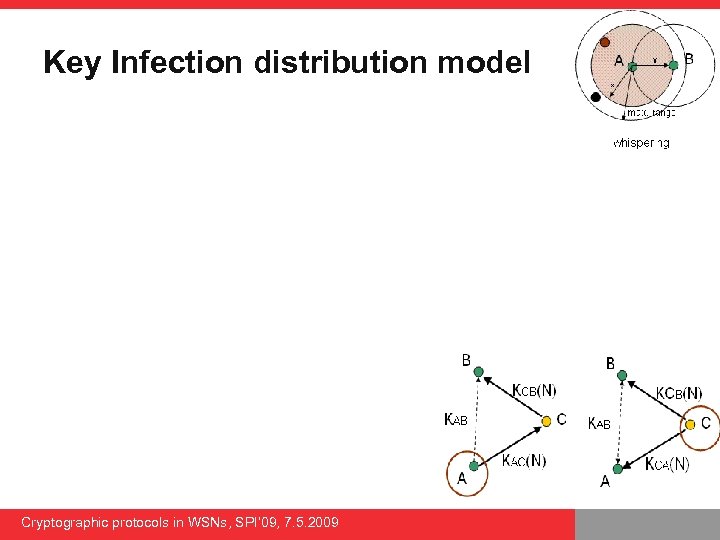 Key Infection distribution model Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
Key Infection distribution model Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
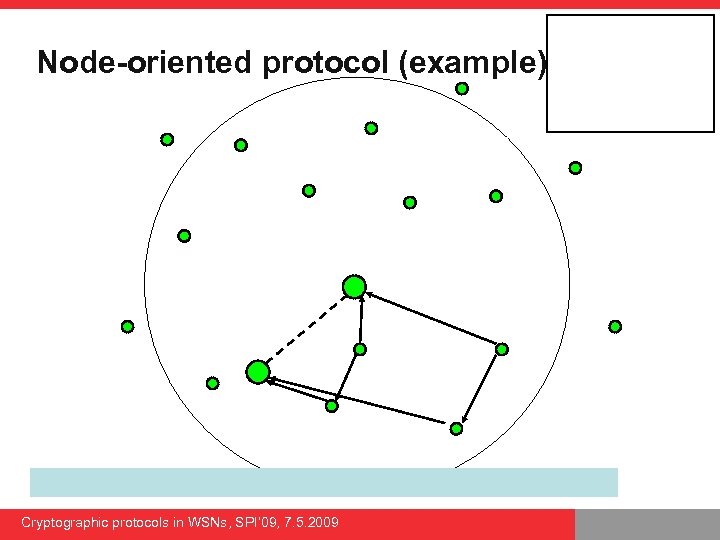 Node-oriented protocol (example) Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
Node-oriented protocol (example) Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
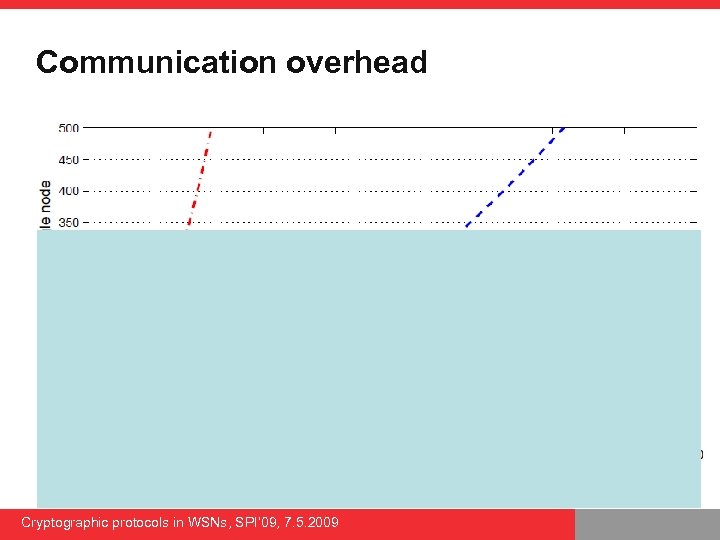 Communication overhead Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
Communication overhead Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
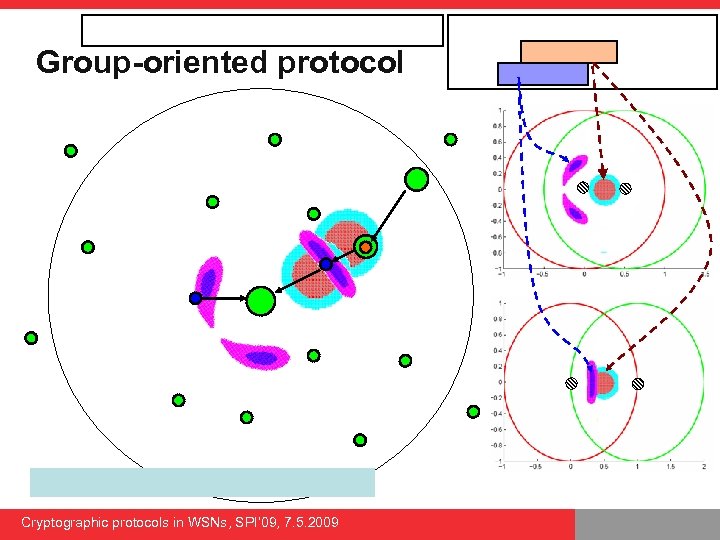 Group-oriented protocol Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
Group-oriented protocol Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
![Evolution of SA protocols [SSM 09] Cryptographic protocols in WSNs, SPI’ 09, 7. 5. Evolution of SA protocols [SSM 09] Cryptographic protocols in WSNs, SPI’ 09, 7. 5.](https://present5.com/presentation/63f5fbffd46bbff23bd5b6839bc00442/image-15.jpg) Evolution of SA protocols [SSM 09] Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
Evolution of SA protocols [SSM 09] Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
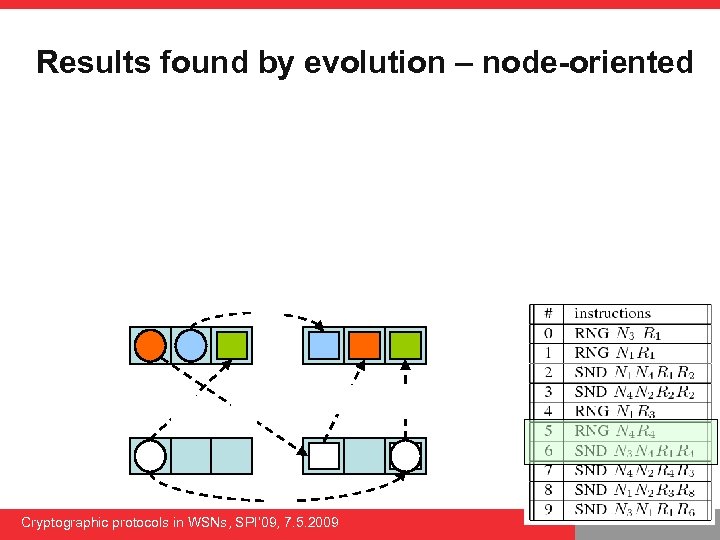 Results found by evolution – node-oriented Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
Results found by evolution – node-oriented Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
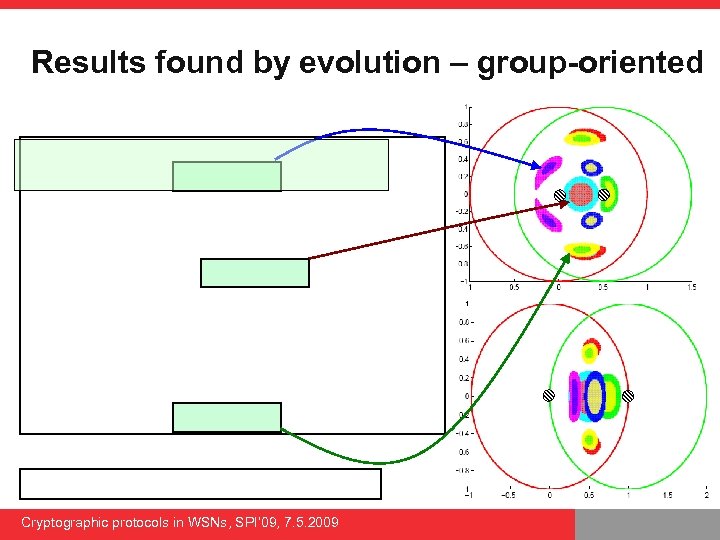 Results found by evolution – group-oriented Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
Results found by evolution – group-oriented Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
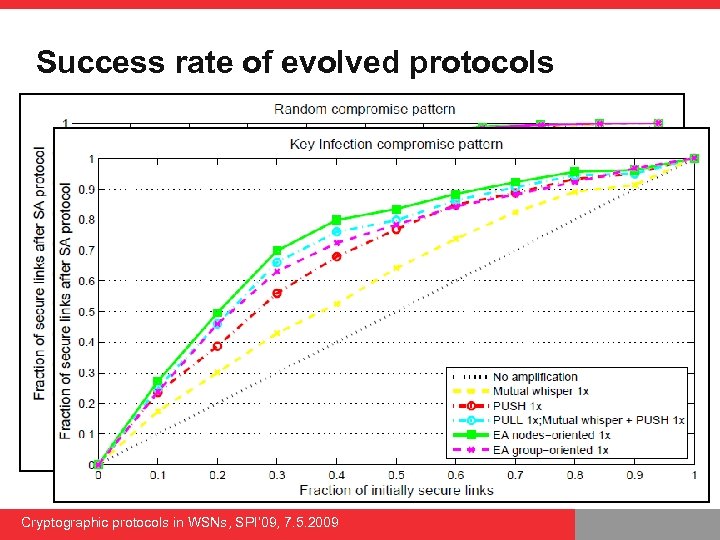 Success rate of evolved protocols Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
Success rate of evolved protocols Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
 Automatic attack strategy - motivation Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
Automatic attack strategy - motivation Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
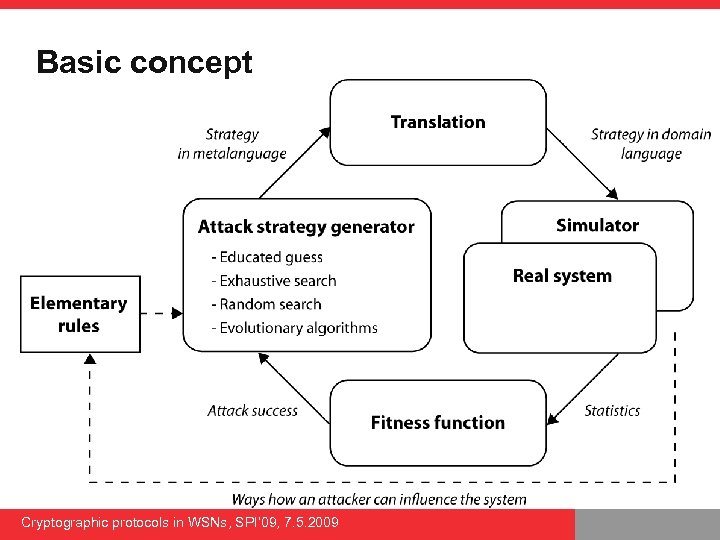 Basic concept Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
Basic concept Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
 Malicious routing in WSNs Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
Malicious routing in WSNs Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
 Malicious routing - results Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
Malicious routing - results Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
 Conclusions Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
Conclusions Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
 References Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
References Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
 Thank you for your attention. Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
Thank you for your attention. Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
 Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
 Automatic attack strategy concept Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
Automatic attack strategy concept Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
 Attack 2: Malicious routing Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
Attack 2: Malicious routing Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
 Attack 1: Selective node capture Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
Attack 1: Selective node capture Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
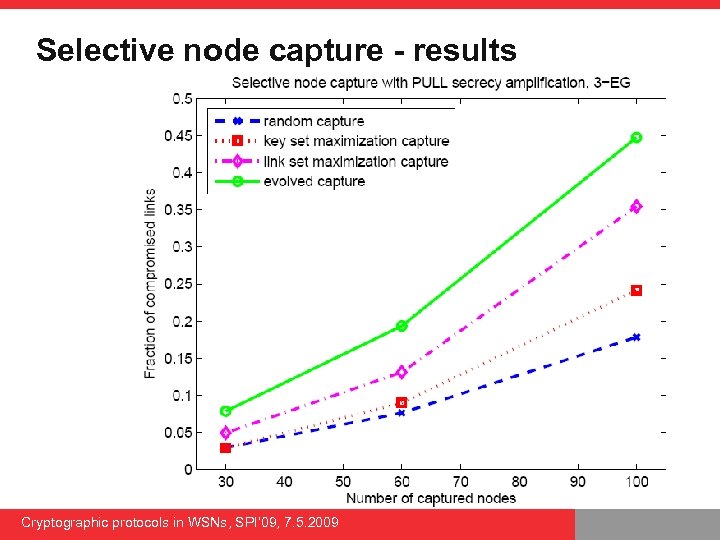 Selective node capture - results Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009
Selective node capture - results Cryptographic protocols in WSNs, SPI’ 09, 7. 5. 2009