 Cryptanalysis on Mu– Varadharajan's e-voting schemes Source: Applied Mathematics and Computation, Vol 139, Issue 2 -3, July, 2003, pp. 525530 Author: Hung-Yua Chien, Jinn-Ke Jan, Yuh-Min Tseng Speaker: Chang-Chu Chen Date: 10/13/2004
Cryptanalysis on Mu– Varadharajan's e-voting schemes Source: Applied Mathematics and Computation, Vol 139, Issue 2 -3, July, 2003, pp. 525530 Author: Hung-Yua Chien, Jinn-Ke Jan, Yuh-Min Tseng Speaker: Chang-Chu Chen Date: 10/13/2004
 Outlines n n Introduction Review Proposed scheme Conclusions 2
Outlines n n Introduction Review Proposed scheme Conclusions 2
 Introduction Y. Mu, V. Varadharajan, Anonymous secure e-voting over a network. Proceedings of the 14 th Annual Computer Security Applications Conference, CACSAC’ 98, 1998, pp. 293– 299. n Mu and Varadharajan claimed 1. 2. 3. n protect voter’s anonymity detect double voting authenticate the voters This paper show the failures 1. 2. 3. the authority can easily identify the owner of a cast ballot a valid voter or any one can vote more than once without being detected any one can forge ballot without being authenticated 3
Introduction Y. Mu, V. Varadharajan, Anonymous secure e-voting over a network. Proceedings of the 14 th Annual Computer Security Applications Conference, CACSAC’ 98, 1998, pp. 293– 299. n Mu and Varadharajan claimed 1. 2. 3. n protect voter’s anonymity detect double voting authenticate the voters This paper show the failures 1. 2. 3. the authority can easily identify the owner of a cast ballot a valid voter or any one can vote more than once without being detected any one can forge ballot without being authenticated 3
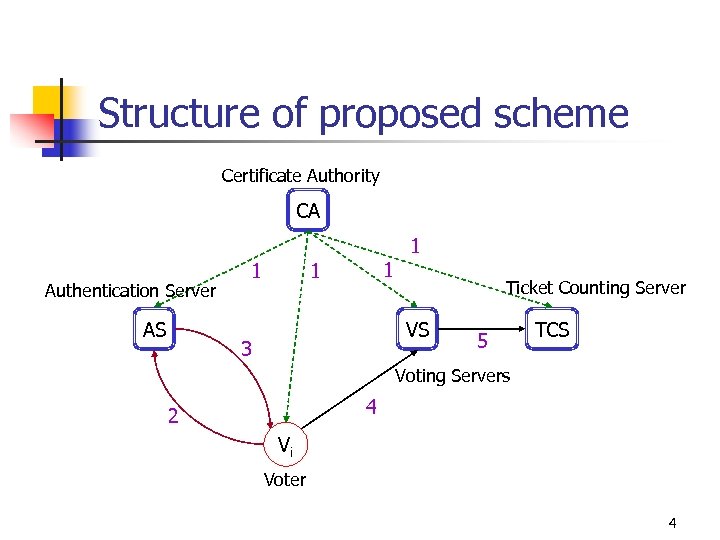 Structure of proposed scheme Certificate Authority CA 1 Authentication Server AS 1 1 1 Ticket Counting Server VS 3 5 TCS Voting Servers 4 2 Vi Voter 4
Structure of proposed scheme Certificate Authority CA 1 Authentication Server AS 1 1 1 Ticket Counting Server VS 3 5 TCS Voting Servers 4 2 Vi Voter 4
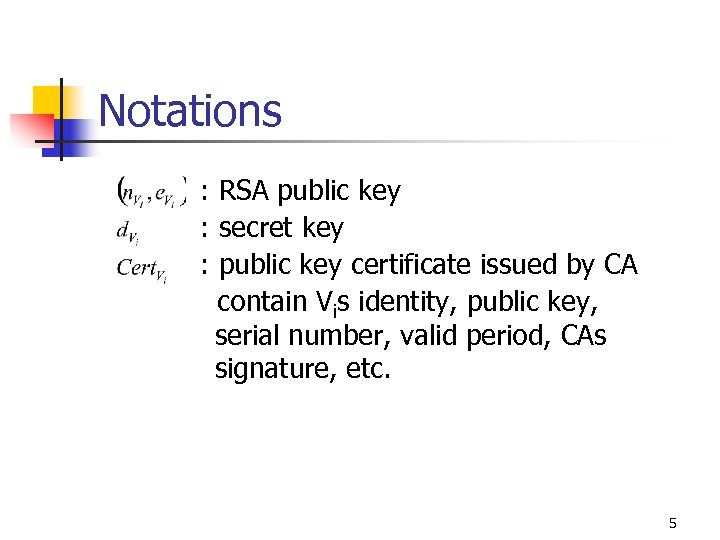 Notations : RSA public key : secret key : public key certificate issued by CA contain Vis identity, public key, serial number, valid period, CAs signature, etc. 5
Notations : RSA public key : secret key : public key certificate issued by CA contain Vis identity, public key, serial number, valid period, CAs signature, etc. 5
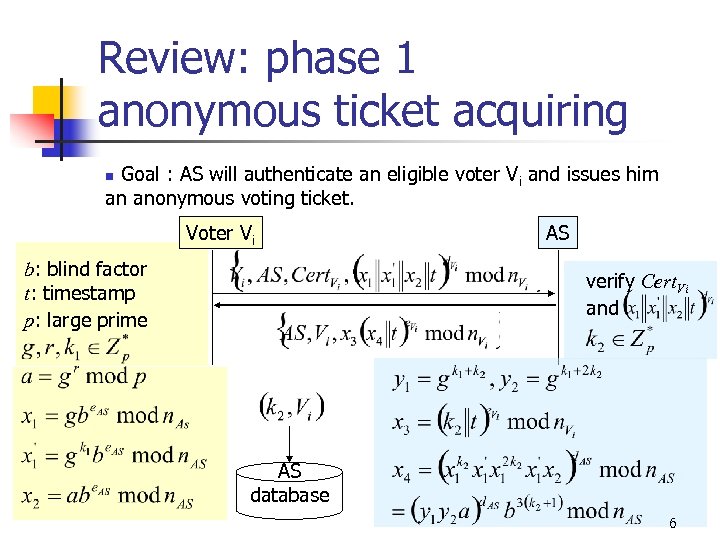 Review: phase 1 anonymous ticket acquiring Goal : AS will authenticate an eligible voter Vi and issues him an anonymous voting ticket. n Voter Vi b: blind factor t: timestamp p: large prime AS verify Cert. Vi and AS database 6
Review: phase 1 anonymous ticket acquiring Goal : AS will authenticate an eligible voter Vi and issues him an anonymous voting ticket. n Voter Vi b: blind factor t: timestamp p: large prime AS verify Cert. Vi and AS database 6
 Review: phase 1 (cont. ) anonymous ticket acquiring Voter Vi m: voting intention get k 2 by decrypt x 3 voting ticket 7
Review: phase 1 (cont. ) anonymous ticket acquiring Voter Vi m: voting intention get k 2 by decrypt x 3 voting ticket 7
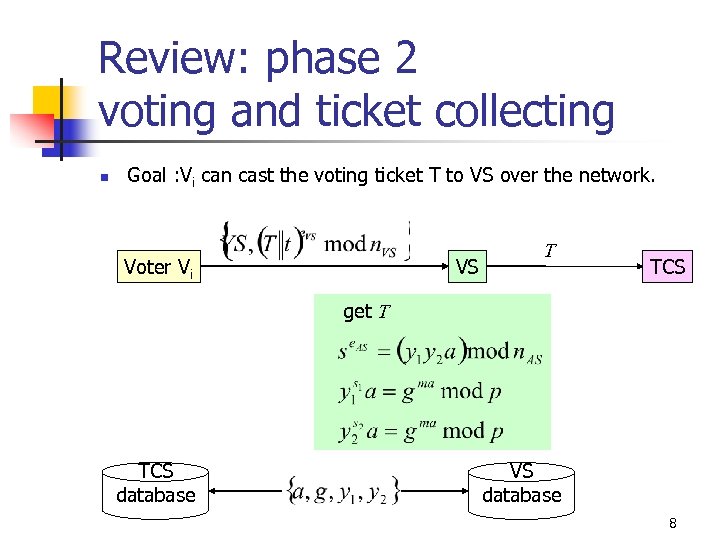 Review: phase 2 voting and ticket collecting n Goal : Vi can cast the voting ticket T to VS over the network. Voter Vi VS T TCS get T TCS database VS database 8
Review: phase 2 voting and ticket collecting n Goal : Vi can cast the voting ticket T to VS over the network. Voter Vi VS T TCS get T TCS database VS database 8
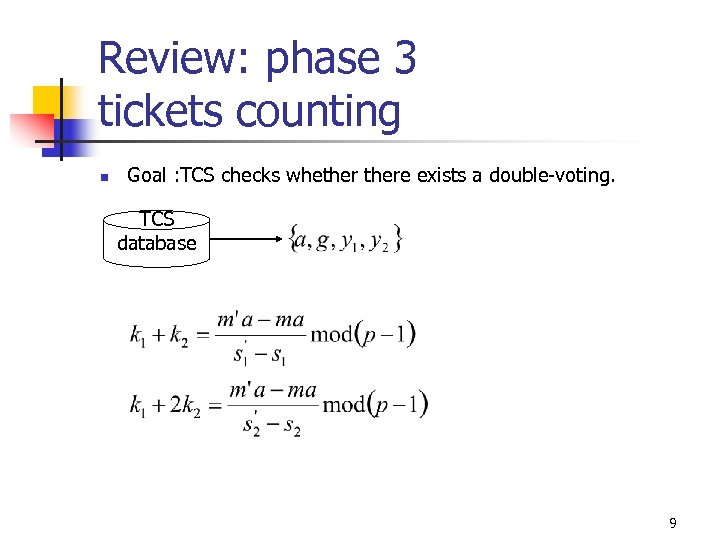 Review: phase 3 tickets counting n Goal : TCS checks whethere exists a double-voting. TCS database 9
Review: phase 3 tickets counting n Goal : TCS checks whethere exists a double-voting. TCS database 9
 Cryptanalysis 1 Failure of protecting voter’s anonymity from n 10
Cryptanalysis 1 Failure of protecting voter’s anonymity from n 10
 Cryptanalysis 2 Authenticated voter vote more than once without being detected from where let then n 11
Cryptanalysis 2 Authenticated voter vote more than once without being detected from where let then n 11
 Cryptanalysis 3 Forging valid anonymous tickets without being authenticated attacker choose k 1, k 2, r n satisfy get then can pass VS and TCS 12
Cryptanalysis 3 Forging valid anonymous tickets without being authenticated attacker choose k 1, k 2, r n satisfy get then can pass VS and TCS 12
 Conclusions n Mu and Varadharajan fail 1. protect voter’s anonymity 2. detect double voting 3. authenticate the voters 13
Conclusions n Mu and Varadharajan fail 1. protect voter’s anonymity 2. detect double voting 3. authenticate the voters 13