 Cryptanalysis of LHL-key authentication scheme Source: Applied Mathematics and Computation, Vol. 152, pp. 721 -724, 2004 Authors: A. Peinado Speaker: Jui-Yi Kuo Date : 11/8/2004 1
Cryptanalysis of LHL-key authentication scheme Source: Applied Mathematics and Computation, Vol. 152, pp. 721 -724, 2004 Authors: A. Peinado Speaker: Jui-Yi Kuo Date : 11/8/2004 1
 Outline n n Review LHL scheme Cryptanalysis of LHL scheme Improved scheme Conclusions 2
Outline n n Review LHL scheme Cryptanalysis of LHL scheme Improved scheme Conclusions 2
 Flow chart of key authentication UA Cert, public key Secretly Cert, public key Server Data for UA UB Get non-repudiation public key 3
Flow chart of key authentication UA Cert, public key Secretly Cert, public key Server Data for UA UB Get non-repudiation public key 3
 Notation PW: password of UA x: private key of UA y: public key of UA ( y= gx mod p) C: certificate of UA r: random number generated by UA f(. ): one-way hash function f(m)=gm mod p 4
Notation PW: password of UA x: private key of UA y: public key of UA ( y= gx mod p) C: certificate of UA r: random number generated by UA f(. ): one-way hash function f(m)=gm mod p 4
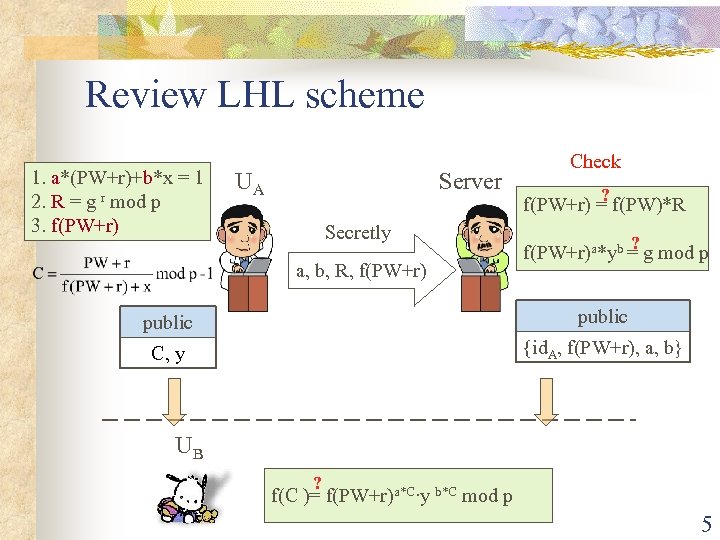 Review LHL scheme 1. a*(PW+r)+b*x = 1 2. R = g r mod p 3. f(PW+r) UA Server Secretly a, b, R, f(PW+r) Check ? f(PW+r) = f(PW)*R ? f(PW+r)a*yb = g mod p public C, y {id. A, f(PW+r), a, b} UB ? f(C )= f(PW+r)a*C∙y b*C mod p 5
Review LHL scheme 1. a*(PW+r)+b*x = 1 2. R = g r mod p 3. f(PW+r) UA Server Secretly a, b, R, f(PW+r) Check ? f(PW+r) = f(PW)*R ? f(PW+r)a*yb = g mod p public C, y {id. A, f(PW+r), a, b} UB ? f(C )= f(PW+r)a*C∙y b*C mod p 5
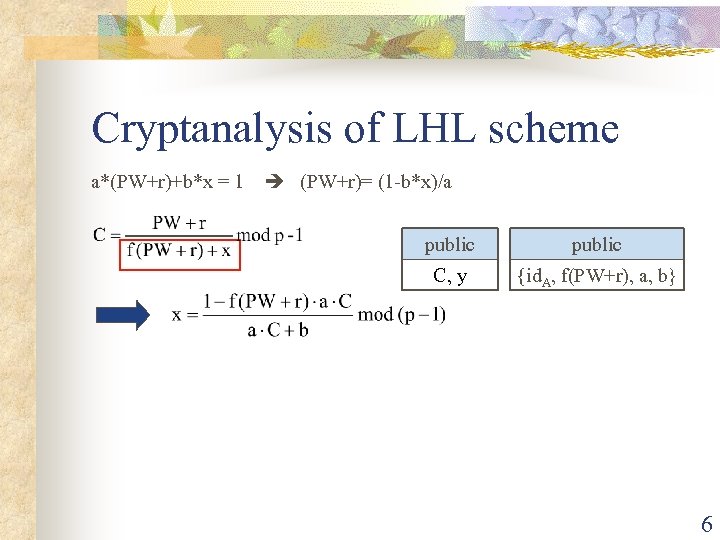 Cryptanalysis of LHL scheme a*(PW+r)+b*x = 1 (PW+r)= (1 -b*x)/a public C, y {id. A, f(PW+r), a, b} 6
Cryptanalysis of LHL scheme a*(PW+r)+b*x = 1 (PW+r)= (1 -b*x)/a public C, y {id. A, f(PW+r), a, b} 6
 Improved scheme 1. a*(PW+r)+b*x = 1 2. R = g r mod p 3. f(PW+r) Check ? Server f(PW+r) = f(PW)*R UA ? f(PW+r)a*yb = g mod p Secretly a, b, R, f(PW+r) public y public {id. A, f(PW+r), a, b} UB ? f(PW+r)a∙y b = g mod p 7
Improved scheme 1. a*(PW+r)+b*x = 1 2. R = g r mod p 3. f(PW+r) Check ? Server f(PW+r) = f(PW)*R UA ? f(PW+r)a*yb = g mod p Secretly a, b, R, f(PW+r) public y public {id. A, f(PW+r), a, b} UB ? f(PW+r)a∙y b = g mod p 7
 Cryptanalysis of Lee-Hwang-Li’s Key Authentication Scheme Source: to appear in Applied Mathematics and Computation. (accepted in November 2003) Authors: Fangguo Zhang and Kwangjo Kim 8
Cryptanalysis of Lee-Hwang-Li’s Key Authentication Scheme Source: to appear in Applied Mathematics and Computation. (accepted in November 2003) Authors: Fangguo Zhang and Kwangjo Kim 8
 Improved scheme (2) 1. a*(PW+r)+b*x = 1 2. R = g r mod p 3. f(PW+r) C=(PW+r)+x*y mod q, where q | (p-1) UA Server Secretly a, b, R, f(PW+r) Check ? f(PW+r) = f(PW)*R ? f(PW+r)a*yb = g mod p public C, y {id. A, f(PW+r), a, b} UB ? f(C )= f(PW+r)a∙y y mod p 9
Improved scheme (2) 1. a*(PW+r)+b*x = 1 2. R = g r mod p 3. f(PW+r) C=(PW+r)+x*y mod q, where q | (p-1) UA Server Secretly a, b, R, f(PW+r) Check ? f(PW+r) = f(PW)*R ? f(PW+r)a*yb = g mod p public C, y {id. A, f(PW+r), a, b} UB ? f(C )= f(PW+r)a∙y y mod p 9
 Conclusions n n n LHL-scheme is not security The modifications can be protected against this problem The modifications are still proposed the guessing attack prevention and the user’s key non-repudiation 10
Conclusions n n n LHL-scheme is not security The modifications can be protected against this problem The modifications are still proposed the guessing attack prevention and the user’s key non-repudiation 10