63b149dfd91894603c7c170e30d051f5.ppt
- Количество слайдов: 50
 Critical Infrastructure and Automated Control Systems Security: A Strategy for Securing Against Cyber Attacks Dr. Thomas L. Pigg Director of the Tennessee CSEC
Critical Infrastructure and Automated Control Systems Security: A Strategy for Securing Against Cyber Attacks Dr. Thomas L. Pigg Director of the Tennessee CSEC
 CSEC Mission • The Cyber Security Education Consortium is a National Science Foundation ATE Regional Center of Excellence dedicated to building an information security workforce who will play a critical role in implementing the national strategy to secure cyberspace.
CSEC Mission • The Cyber Security Education Consortium is a National Science Foundation ATE Regional Center of Excellence dedicated to building an information security workforce who will play a critical role in implementing the national strategy to secure cyberspace.
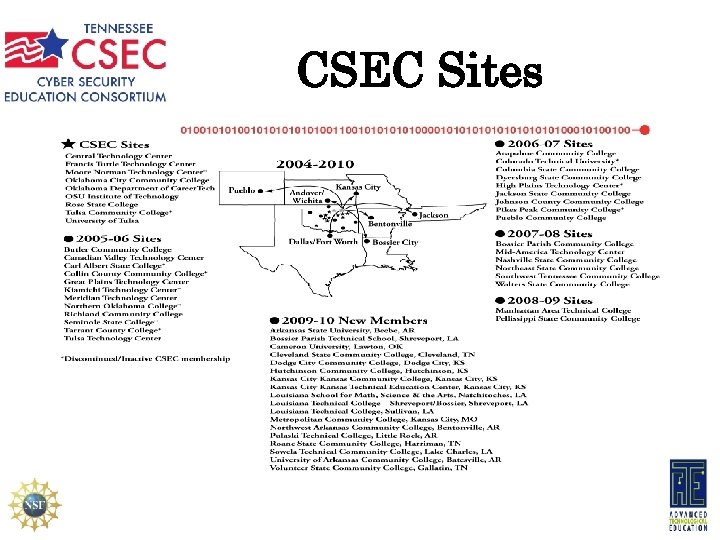 CSEC Sites
CSEC Sites
 Tennessee CSEC Mission • Phase 1 – Train the trainer • Phase 2 – Develop Student Curriculum/Courses/Concentrations • Phase 3 – Develop Partnerships with Business, Industry and Government
Tennessee CSEC Mission • Phase 1 – Train the trainer • Phase 2 – Develop Student Curriculum/Courses/Concentrations • Phase 3 – Develop Partnerships with Business, Industry and Government
 Core Train the Trainer Workshops • Principles of Information Assurance • Network Security • Enterprise Security Management • Secure E-Commerce • Digital Forensics
Core Train the Trainer Workshops • Principles of Information Assurance • Network Security • Enterprise Security Management • Secure E-Commerce • Digital Forensics
 New CSEC Courses • Automation and Control Systems – Control Systems Architecture – Control Systems Software Applications – Control Systems Security I and II • Mobile Communications Devices – Mobile Device Architecture – Mobile Device Programming – Mobile Device Hardware • Secure Coding – Secure Programming I and II – Software Testing – Software Security
New CSEC Courses • Automation and Control Systems – Control Systems Architecture – Control Systems Software Applications – Control Systems Security I and II • Mobile Communications Devices – Mobile Device Architecture – Mobile Device Programming – Mobile Device Hardware • Secure Coding – Secure Programming I and II – Software Testing – Software Security
 What are Control Systems • SCADA (Supervisory Control and Data Acquisition) • DCS (Distributed Control Systems) • ICS (Industrial Control Systems) • BAS (Building Automation Systems) • PLC (Programmable Logic Controllers) • Smart Grid
What are Control Systems • SCADA (Supervisory Control and Data Acquisition) • DCS (Distributed Control Systems) • ICS (Industrial Control Systems) • BAS (Building Automation Systems) • PLC (Programmable Logic Controllers) • Smart Grid
 Critical Infrastructures • Agriculture & Food • Banking & Finance • Chemical • Commercial Facilities • Communications • Critical Manufacturing
Critical Infrastructures • Agriculture & Food • Banking & Finance • Chemical • Commercial Facilities • Communications • Critical Manufacturing
 Critical Infrastructures • Dams • Defense Industrial Base • Emergency Services • Energy • Government Facilities • Healthcare & Public Health
Critical Infrastructures • Dams • Defense Industrial Base • Emergency Services • Energy • Government Facilities • Healthcare & Public Health
 Critical Infrastructures • Information Technology • National Monuments & Icons • Nuclear Reactors, Materials & Waste • Postal & Shipping • Transportation Systems • Water
Critical Infrastructures • Information Technology • National Monuments & Icons • Nuclear Reactors, Materials & Waste • Postal & Shipping • Transportation Systems • Water
 Key Critical Infrastructures • Key Sectors for Control Systems Security • Energy (Electricity, Oil, and Natural Gas) • Water & Wastewater • Nuclear • Chemical • Dams • Transportation • Critical Manufacturing
Key Critical Infrastructures • Key Sectors for Control Systems Security • Energy (Electricity, Oil, and Natural Gas) • Water & Wastewater • Nuclear • Chemical • Dams • Transportation • Critical Manufacturing
 Current Trends in Control Systems • Continued move to open protocols • Continued move to more COTS operating systems & applications • More remote control & management • More network access to systems • More widespread use of wireless
Current Trends in Control Systems • Continued move to open protocols • Continued move to more COTS operating systems & applications • More remote control & management • More network access to systems • More widespread use of wireless
 Current State of Security • Control Systems protocols with little or no security • Migration to TCP/IP networks with its inherent vulnerabilities • Interconnection with enterprise networks • Old operating systems & applications with poor patching practices • Little monitoring of Control Systems for attacks being done • Vendors not securing their product offerings adequately
Current State of Security • Control Systems protocols with little or no security • Migration to TCP/IP networks with its inherent vulnerabilities • Interconnection with enterprise networks • Old operating systems & applications with poor patching practices • Little monitoring of Control Systems for attacks being done • Vendors not securing their product offerings adequately
 Current State of Security • Increased risk of insider attacks by outsourced IT services • Experts seeing increased interest in Control Systems by terrorists & foreign governments • Evidence that nation-states have been taking remote control of Control Systems • Denial by some companies that there is a problem • Some companies are now starting to see the need and address the issues
Current State of Security • Increased risk of insider attacks by outsourced IT services • Experts seeing increased interest in Control Systems by terrorists & foreign governments • Evidence that nation-states have been taking remote control of Control Systems • Denial by some companies that there is a problem • Some companies are now starting to see the need and address the issues
 Real Control System Security Breaches • Diamler-Chrysler Plant Shutdown – Zotob worm – August 2005 • First Energy’s Nuclear Plant Infestation – Slammer worm – January 2003 • Maroochy Shire Sewage – Release of millions of gallons of sewage January 2000 – Perpetrator accessed system 46 times
Real Control System Security Breaches • Diamler-Chrysler Plant Shutdown – Zotob worm – August 2005 • First Energy’s Nuclear Plant Infestation – Slammer worm – January 2003 • Maroochy Shire Sewage – Release of millions of gallons of sewage January 2000 – Perpetrator accessed system 46 times
 Real Control System Security Breaches • Hacking the Industrial Network – http: //www. isa. org/File. Store/Intech/White Paper/Hacking-the-industrial-network. USversion. pdf • DHS Video – Idaho National Laboratory – AURORA Test – http: //www. cnn. com/2007/US/09/26/power. at. risk/index. html#cnn. STCVideo
Real Control System Security Breaches • Hacking the Industrial Network – http: //www. isa. org/File. Store/Intech/White Paper/Hacking-the-industrial-network. USversion. pdf • DHS Video – Idaho National Laboratory – AURORA Test – http: //www. cnn. com/2007/US/09/26/power. at. risk/index. html#cnn. STCVideo
 AURORA Test
AURORA Test
 Real Control System Security Breaches • Stuxnet – http: //www. tofinosecurity. com/stuxnetcentral – http: //www. exida. com/images/uploads/The _7_Things_Every_Plant_Manager_Should _Know_About_Control_System_Security. p df
Real Control System Security Breaches • Stuxnet – http: //www. tofinosecurity. com/stuxnetcentral – http: //www. exida. com/images/uploads/The _7_Things_Every_Plant_Manager_Should _Know_About_Control_System_Security. p df
 Current Threats • Internet Based Threats • Worms • Viruses • Denial of Service Attacks • Targeted Attacks • Terrorist • Foreign Nation • Former Insider
Current Threats • Internet Based Threats • Worms • Viruses • Denial of Service Attacks • Targeted Attacks • Terrorist • Foreign Nation • Former Insider
 Current Threats • Physical Threats • Natural Disasters • Man-made Disasters (War, Riots, etc. ) • Terrorist Attacks
Current Threats • Physical Threats • Natural Disasters • Man-made Disasters (War, Riots, etc. ) • Terrorist Attacks
 Current Threats • Internal Threats • Disgruntled employee • On-site contractor • Unintentional attack • IT worker • Curious Employee
Current Threats • Internal Threats • Disgruntled employee • On-site contractor • Unintentional attack • IT worker • Curious Employee
 Current Threats • Targeted Attacks • Can use any threat & threat agent • Internet • Internal • Physical • Social Engineering • Etc.
Current Threats • Targeted Attacks • Can use any threat & threat agent • Internet • Internal • Physical • Social Engineering • Etc.
 IT Security for Control Systems • CIA • Confidentiality • Integrity • Availability
IT Security for Control Systems • CIA • Confidentiality • Integrity • Availability
 IT Security for Control Systems • Technical Controls • Firewalls • IDS • Smart Cards • Access Controls
IT Security for Control Systems • Technical Controls • Firewalls • IDS • Smart Cards • Access Controls
 IT Security for Control Systems • Administrative Controls • Security Policies & Procedures • Security Awareness • People
IT Security for Control Systems • Administrative Controls • Security Policies & Procedures • Security Awareness • People
 IT Security for Control Systems • TCP/IP • Patches & Updates • Intrusion Detection Systems • Control Systems Monitoring • Signatures for Control Systems • Anti-Virus Software
IT Security for Control Systems • TCP/IP • Patches & Updates • Intrusion Detection Systems • Control Systems Monitoring • Signatures for Control Systems • Anti-Virus Software
 IT Security for Control Systems • Access Control Methods • Passwords • Multi-Factor • Smart Cards • RFID • Proximity • Biometric
IT Security for Control Systems • Access Control Methods • Passwords • Multi-Factor • Smart Cards • RFID • Proximity • Biometric
 IT Security for Control Systems • Authentication • Active Directory • Control Systems Integration • Certificates
IT Security for Control Systems • Authentication • Active Directory • Control Systems Integration • Certificates
 IT Security for Control Systems • Authorization • Role Based • Area of Responsibility • Station Access Control
IT Security for Control Systems • Authorization • Role Based • Area of Responsibility • Station Access Control
 Using an IDS with a Control System • Network based • Inspects all network traffic on that segment (incoming & outgoing) • Uses pattern based signatures • Anomaly based uses baseline • Uses network tap or mirrored port • Monitors multiple hosts
Using an IDS with a Control System • Network based • Inspects all network traffic on that segment (incoming & outgoing) • Uses pattern based signatures • Anomaly based uses baseline • Uses network tap or mirrored port • Monitors multiple hosts
 Using an IDS with a Control System • Host based • Inspects network traffic for a specific host • Better at protecting a machines specific function • Misses LAN based attacks
Using an IDS with a Control System • Host based • Inspects network traffic for a specific host • Better at protecting a machines specific function • Misses LAN based attacks
 Using an IDS with a Control System • Commercial • Pre-configured fee based IDS • CA e. Trust • Mc. Afee Intru. Shield & Entercept • Sonic. Wall • Still. Secure Strata Guard
Using an IDS with a Control System • Commercial • Pre-configured fee based IDS • CA e. Trust • Mc. Afee Intru. Shield & Entercept • Sonic. Wall • Still. Secure Strata Guard
 Using an IDS with a Control System • Open Source • Snort • Base • Sguil – Real-time GUI interface • OSSEC (Open Source Host-based Intrusion Detection System)
Using an IDS with a Control System • Open Source • Snort • Base • Sguil – Real-time GUI interface • OSSEC (Open Source Host-based Intrusion Detection System)
 Using an IDS with a Control System • IPS • Intrusion Prevention System • Automated Response • Dynamically change firewall ruleset • NIST IDS Guide (SP 800 -94)
Using an IDS with a Control System • IPS • Intrusion Prevention System • Automated Response • Dynamically change firewall ruleset • NIST IDS Guide (SP 800 -94)
 Security Solutions • Network Segmentation • DMZ Design • Can use ISA S 99 standard as guide • Design to protect each segment • Allows for centralized services
Security Solutions • Network Segmentation • DMZ Design • Can use ISA S 99 standard as guide • Design to protect each segment • Allows for centralized services
 Security Solutions • Network Segmentation • Centralized Services • Anti-Virus • Updates & Patches • Active Directory Services • Data Historians • System Management
Security Solutions • Network Segmentation • Centralized Services • Anti-Virus • Updates & Patches • Active Directory Services • Data Historians • System Management
 Security Solutions • Secure Remote Access • Secured VPN connections • Escorted Access for vendors • Require secured tokens • Call in by vendor with request • Issue 1 -time code for access
Security Solutions • Secure Remote Access • Secured VPN connections • Escorted Access for vendors • Require secured tokens • Call in by vendor with request • Issue 1 -time code for access
 Security Solutions • IDS/IPS for Control Systems • Which one to use? • Where to use? • HIDS or Application Whitelisting? • UTM – Unified Threat Management
Security Solutions • IDS/IPS for Control Systems • Which one to use? • Where to use? • HIDS or Application Whitelisting? • UTM – Unified Threat Management
 Security Solutions • Security Event Monitoring & Logging • Network Devices • Switches, Routers, Firewalls, IDS • Computing Devices • Historians, Servers, Operator consoles • Field Devices • RTU, PLC, Telemetry Devices, Embedded Devices
Security Solutions • Security Event Monitoring & Logging • Network Devices • Switches, Routers, Firewalls, IDS • Computing Devices • Historians, Servers, Operator consoles • Field Devices • RTU, PLC, Telemetry Devices, Embedded Devices
 Security Solutions • Security Framework • NIPP • NERC CIP • CSSP DHS • NIST
Security Solutions • Security Framework • NIPP • NERC CIP • CSSP DHS • NIST
 Security Solutions • Policy & Guidance • Developing Good Policies • Track Data • Points of Contact • Areas of Concern • Data Risk Assessment • Evaluate the Impact of Data Loss • Available Controls • Technical, Administrative, & Compensating
Security Solutions • Policy & Guidance • Developing Good Policies • Track Data • Points of Contact • Areas of Concern • Data Risk Assessment • Evaluate the Impact of Data Loss • Available Controls • Technical, Administrative, & Compensating
 Security Solutions • Policy & Guidance • Implementation • Roles & Responsibilities • Security Requirements • Change Management Process • Backup & Redundancy • Self Assessments
Security Solutions • Policy & Guidance • Implementation • Roles & Responsibilities • Security Requirements • Change Management Process • Backup & Redundancy • Self Assessments
 Control Systems Security Initiatives • NIPP (National Infrastructure Protection Plan) • CIPAC (Critical Infrastructure Partnership Advisory Council) • ICSJWG (Industrial Control Systems Joint Working Group) • ICS-Cert (Industrial Control Systems Cyber Emergency Response Team) • Strategy for Securing Control Systems
Control Systems Security Initiatives • NIPP (National Infrastructure Protection Plan) • CIPAC (Critical Infrastructure Partnership Advisory Council) • ICSJWG (Industrial Control Systems Joint Working Group) • ICS-Cert (Industrial Control Systems Cyber Emergency Response Team) • Strategy for Securing Control Systems
 Control Systems Security Initiatives • CSSP (Control Systems Security Program) • Idaho National Laboratory • National SCADA Test Bed Program • SCADA & Control Systems Procurement Project • Smart Grid Interoperability Standards Project • UK NISCC - Now CPNI (Centre for the Protection of National Infrastructure) • PCSF/SCy. SAG (SCADA Cyber Self Assessment Working Group) - Historical
Control Systems Security Initiatives • CSSP (Control Systems Security Program) • Idaho National Laboratory • National SCADA Test Bed Program • SCADA & Control Systems Procurement Project • Smart Grid Interoperability Standards Project • UK NISCC - Now CPNI (Centre for the Protection of National Infrastructure) • PCSF/SCy. SAG (SCADA Cyber Self Assessment Working Group) - Historical
 Control Systems Regulations • NERC (North American Electric Reliability Council) • Develop & enforce reliability standards • CIDX/ACC – Now Chem. ITC (American Chemistry Council) • CFATS guidance & assessment tools
Control Systems Regulations • NERC (North American Electric Reliability Council) • Develop & enforce reliability standards • CIDX/ACC – Now Chem. ITC (American Chemistry Council) • CFATS guidance & assessment tools
 Control Systems Regulations • ISA SP 99 (Industrial Automation & Control System Security) – International Society of Automation • Part 1 Standard: Concepts, Terminology & Models • Part 2 Standard: Establishing an Industrial Automation & Control Systems Security Program • Part 3 Standard: Technical Requirements for Industrial Control Systems (Currently in development
Control Systems Regulations • ISA SP 99 (Industrial Automation & Control System Security) – International Society of Automation • Part 1 Standard: Concepts, Terminology & Models • Part 2 Standard: Establishing an Industrial Automation & Control Systems Security Program • Part 3 Standard: Technical Requirements for Industrial Control Systems (Currently in development
 Control Systems Regulations • AGA 12 – Discontinued and used in IEEE 1711 Trial Standard • Encryption of Serial Communications • Serial Encrypting Transceivers now available • API Standard 1164 (American Petroleum Institute) • Standard on SCADA security for pipelines • NIST – National Institute of Standards and Technology
Control Systems Regulations • AGA 12 – Discontinued and used in IEEE 1711 Trial Standard • Encryption of Serial Communications • Serial Encrypting Transceivers now available • API Standard 1164 (American Petroleum Institute) • Standard on SCADA security for pipelines • NIST – National Institute of Standards and Technology
 Control Systems Regulations • SP 800 -82 – Guide to Industrial Control Systems (ICS) Security • NIST initiative on Critical Infrastructure Protection (CIP) • Uses ISO 15408 Common Criteria methodology
Control Systems Regulations • SP 800 -82 – Guide to Industrial Control Systems (ICS) Security • NIST initiative on Critical Infrastructure Protection (CIP) • Uses ISO 15408 Common Criteria methodology
 Control System Security Takeaway • The 7 Things Every Plant Manager Should Know About Control System Security – John Cusimano – Director of Security Solutions for exida – http: //www. exida. com/images/uploads/The_7_Things_Every _Plant_Manager_Should_Know_About_Control_System_Sec urity. pdf
Control System Security Takeaway • The 7 Things Every Plant Manager Should Know About Control System Security – John Cusimano – Director of Security Solutions for exida – http: //www. exida. com/images/uploads/The_7_Things_Every _Plant_Manager_Should_Know_About_Control_System_Sec urity. pdf
 Contact Information Dr. Thomas L. Pigg Professor of Computer Information Systems Jackson State Community College 2046 N. Parkway Jackson, TN 38305 (731) 424 -3520 Ext. 201 tpigg@jscc. edu
Contact Information Dr. Thomas L. Pigg Professor of Computer Information Systems Jackson State Community College 2046 N. Parkway Jackson, TN 38305 (731) 424 -3520 Ext. 201 tpigg@jscc. edu


