645b720994a482f4782d1844abad1938.ppt
- Количество слайдов: 105
 Creating, Using and Justifying the Auditor's Toolkit • Welcome • General announcements
Creating, Using and Justifying the Auditor's Toolkit • Welcome • General announcements
 Creating, Using and Justifying the Auditor's Toolkit ISACA Presentation April 2003 Ed Capizzi
Creating, Using and Justifying the Auditor's Toolkit ISACA Presentation April 2003 Ed Capizzi
 Schedule etc. • • Breakfast Intro, admin & Methodology Outside – In tools Unix Lunch Windows Hands on
Schedule etc. • • Breakfast Intro, admin & Methodology Outside – In tools Unix Lunch Windows Hands on
 Administrivia • • Location information Pagers and cell phones Fire escapes Food Start stop times Location of restrooms General room rules and mood
Administrivia • • Location information Pagers and cell phones Fire escapes Food Start stop times Location of restrooms General room rules and mood
 Assumptions • • Auditors have all the front end time & field work time they need Auditors have large budgets for tools and training • Auditors always get full cooperation of and unlimited access to audit areas • No one minds being audited • You are already experts on everything
Assumptions • • Auditors have all the front end time & field work time they need Auditors have large budgets for tools and training • Auditors always get full cooperation of and unlimited access to audit areas • No one minds being audited • You are already experts on everything
 Real World Assumptions • • • You have to become an expert at everything FAST (or at least brush up!) You need something you can apply now You probably run a Win. Tel based machine You probably don't have admin / root level access (of your own) to the systems you audit You have to be part tech, part teacher, part politician Even “free, industry best practices” require some selling
Real World Assumptions • • • You have to become an expert at everything FAST (or at least brush up!) You need something you can apply now You probably run a Win. Tel based machine You probably don't have admin / root level access (of your own) to the systems you audit You have to be part tech, part teacher, part politician Even “free, industry best practices” require some selling
 Real World Assumptions • • This is one way to do things, not THE way Linux (for this presentation) is Red. Hat Solaris (for this presentation) is 2. 6 HP (for this presentation) is 11. x
Real World Assumptions • • This is one way to do things, not THE way Linux (for this presentation) is Red. Hat Solaris (for this presentation) is 2. 6 HP (for this presentation) is 11. x
 Our Approach • • • Learn to fish Basics, basics Keep it simple Inside out, Outside in Creative use of “indigenous resources” (utilities included in the existing OS) • Audits (& auditors) must be “environmentally friendly and low impact”
Our Approach • • • Learn to fish Basics, basics Keep it simple Inside out, Outside in Creative use of “indigenous resources” (utilities included in the existing OS) • Audits (& auditors) must be “environmentally friendly and low impact”
 Our Approach 1. Subsystem(s) involved 2. Best practice examples/settings 3. Ramifications of settings or principles 4. How to sell to administrators and management 5. Which tool to use to accomplish which task
Our Approach 1. Subsystem(s) involved 2. Best practice examples/settings 3. Ramifications of settings or principles 4. How to sell to administrators and management 5. Which tool to use to accomplish which task
 15 Main Areas 1) Account Policies 9) Remote Access 2) Auditing 10) Scheduled Tasks 3) Device Drivers 11) System Info 4) Drives 12) Services 5) Event Log 13) Shares 6) Printer Permissions 14) Trusted Relationships 7) Processes 15) Users & Groups 8) Registry
15 Main Areas 1) Account Policies 9) Remote Access 2) Auditing 10) Scheduled Tasks 3) Device Drivers 11) System Info 4) Drives 12) Services 5) Event Log 13) Shares 6) Printer Permissions 14) Trusted Relationships 7) Processes 15) Users & Groups 8) Registry
 Account Policies What are the tools? – admintool (gui-Solaris) • /etc/default/passwd (sun) • /etc/passwd – sam (gui-HP) /etc/passwd – userconf or redhat-config-users (gui Red Hat Linux) • /etc/passwd (linux) What can they tell us?
Account Policies What are the tools? – admintool (gui-Solaris) • /etc/default/passwd (sun) • /etc/passwd – sam (gui-HP) /etc/passwd – userconf or redhat-config-users (gui Red Hat Linux) • /etc/passwd (linux) What can they tell us?
 Account Policies What can they tell us*: o login name o encrypted password o numerical user ID o numerical group ID o reserved gecos ID o initial working directory o program to use as shell BUT WE WANT MORE!
Account Policies What can they tell us*: o login name o encrypted password o numerical user ID o numerical group ID o reserved gecos ID o initial working directory o program to use as shell BUT WE WANT MORE!
 Account Policies To get more, the system has to be using: shadow passwords (Solaris / Linux) /etc/shadow or “trusted system” (HP) /tcb/files/auth/ More on this later, stay tuned. . .
Account Policies To get more, the system has to be using: shadow passwords (Solaris / Linux) /etc/shadow or “trusted system” (HP) /tcb/files/auth/ More on this later, stay tuned. . .
 Account Policies Where are the files? (review) Standard systems /etc/default/passwd (Sun) /etc/passwd (HP & Linux) Shadowed or trusted systems /etc/default/passwd (Sun) /etc/passwd (Sun & Linux) /tcb/files/auth/ (HP)
Account Policies Where are the files? (review) Standard systems /etc/default/passwd (Sun) /etc/passwd (HP & Linux) Shadowed or trusted systems /etc/default/passwd (Sun) /etc/passwd (Sun & Linux) /tcb/files/auth/ (HP)
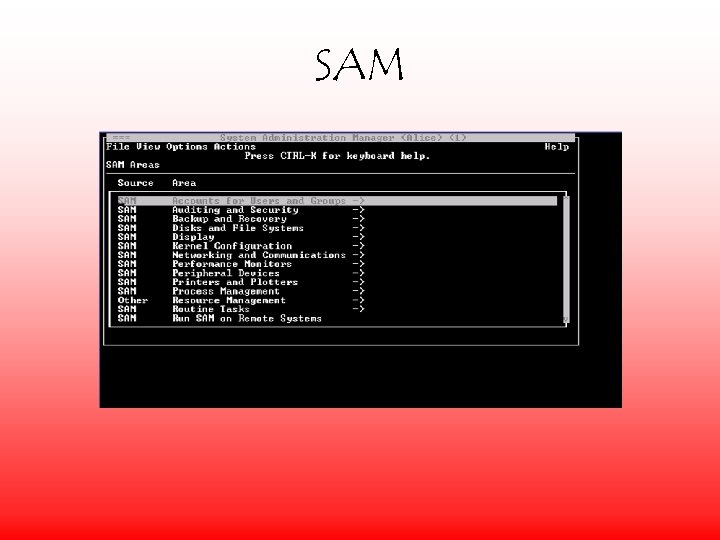 SAM
SAM
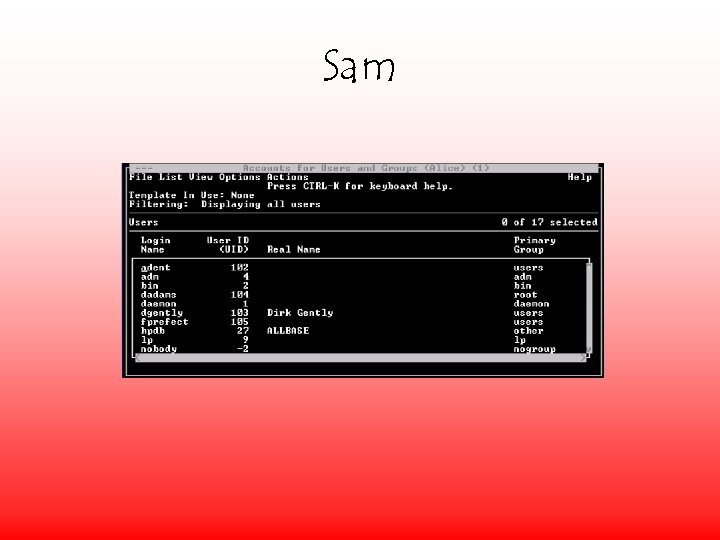 Sam
Sam
 Sam
Sam
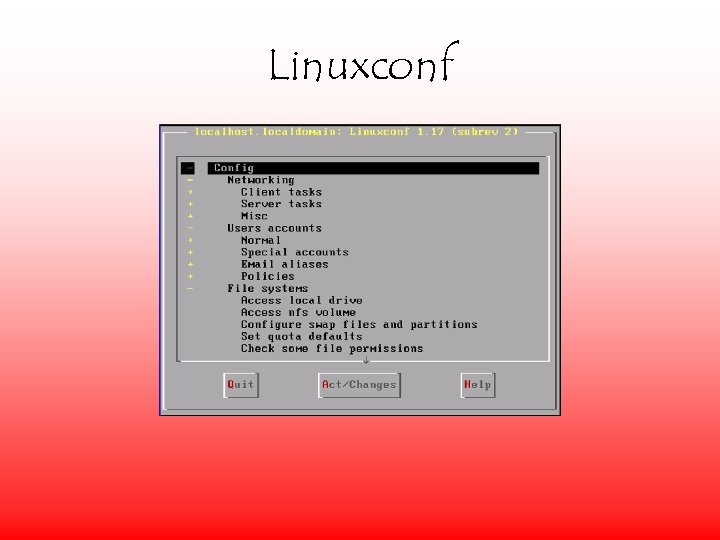 Linuxconf
Linuxconf
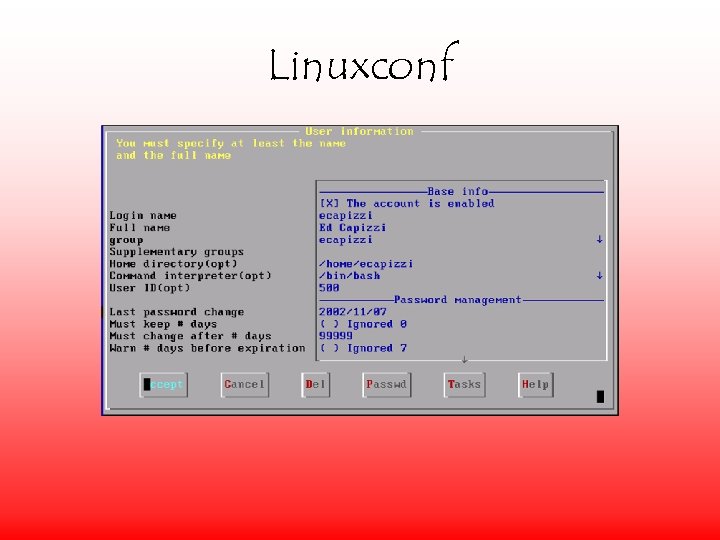 Linuxconf
Linuxconf
 Auditing • user logon / logoff • system restart, start up, shutdown • object access
Auditing • user logon / logoff • system restart, start up, shutdown • object access
 Auditing Linux – /etc/syslog. conf – /var/log/messages Sun – /etc/syslog. conf – /var/adm/message HPUX – /etc/syslog. conf – /var/adm/syslog. log
Auditing Linux – /etc/syslog. conf – /var/log/messages Sun – /etc/syslog. conf – /var/adm/message HPUX – /etc/syslog. conf – /var/adm/syslog. log
 Auditing Linux & HP dmesg -boot diagnostics & messages Sun prtdiag Cool tool alert!!! Rosetta Stone for Unix!
Auditing Linux & HP dmesg -boot diagnostics & messages Sun prtdiag Cool tool alert!!! Rosetta Stone for Unix!
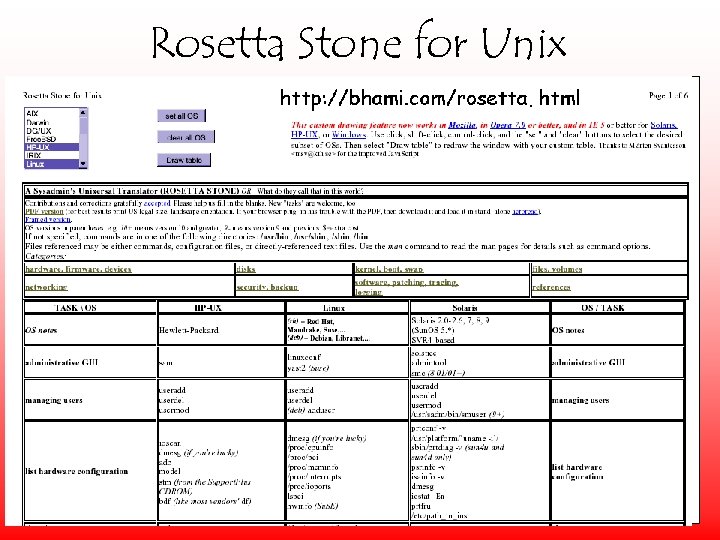 Rosetta Stone for Unix
Rosetta Stone for Unix
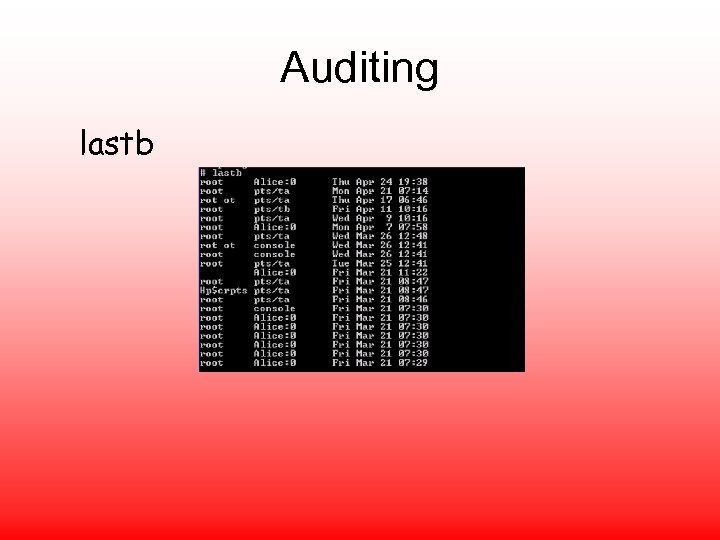 Auditing lastb
Auditing lastb
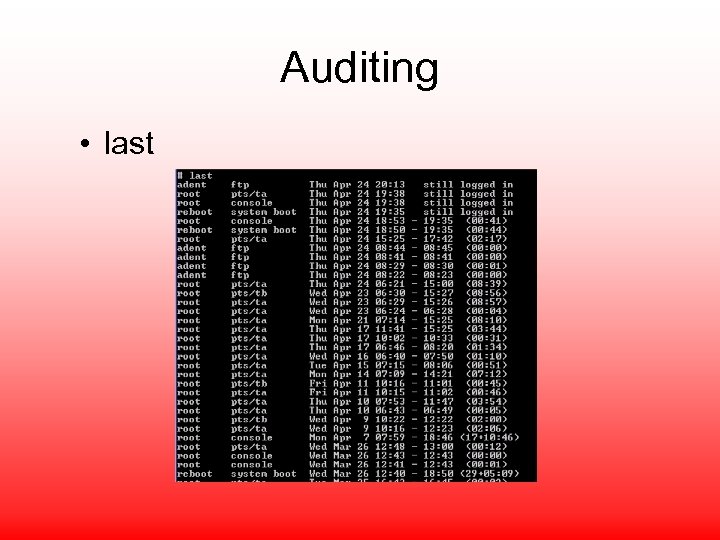 Auditing • last
Auditing • last
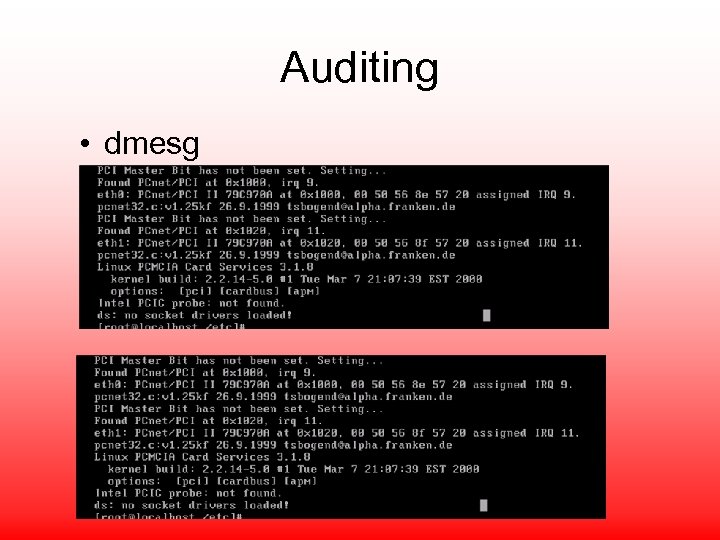 Auditing • dmesg
Auditing • dmesg
 Auditing • HPUX “Trusted System” – passwords moved from /etc/passwd – All users must have a password – Check /etc/rc. config. d/auditing & /sbin/rc 2. d/S 760 auditing. /etc/rc. config. d/auditing for auditing control parameters. – /tcb/files/ttys • uid of user log into terminal, logins & unsuccessful logins.
Auditing • HPUX “Trusted System” – passwords moved from /etc/passwd – All users must have a password – Check /etc/rc. config. d/auditing & /sbin/rc 2. d/S 760 auditing. /etc/rc. config. d/auditing for auditing control parameters. – /tcb/files/ttys • uid of user log into terminal, logins & unsuccessful logins.
 Auditing A. K. A Setting up syslog!
Auditing A. K. A Setting up syslog!
 Syslog. conf • Simple text file with format of daemon. loglevel
Syslog. conf • Simple text file with format of daemon. loglevel
 Syslog. conf (con't) # Log anything (except mail) of level info or higher. # Don't log private authentication messages! *. info; mail. none; authpriv. none /var/log/messages # The authpriv file has restricted access. authpriv. * /var/log/secure # Log all the mail messages in one place. mail. * /var/log/maillog # Save mail and news errors of level err and higher in a # special file. uucp, news. crit /var/log/spooler # Save boot messages also to boot. log local 7. * /var/log/boot. log
Syslog. conf (con't) # Log anything (except mail) of level info or higher. # Don't log private authentication messages! *. info; mail. none; authpriv. none /var/log/messages # The authpriv file has restricted access. authpriv. * /var/log/secure # Log all the mail messages in one place. mail. * /var/log/maillog # Save mail and news errors of level err and higher in a # special file. uucp, news. crit /var/log/spooler # Save boot messages also to boot. log local 7. * /var/log/boot. log
 Syslog logging Levels • • emerg alert crit err warning notice info debug System is unusable Action must be taken NOW Critical conditions Error conditions Warning conditions Normal but significant FYI More than you want to know (Programmers only)
Syslog logging Levels • • emerg alert crit err warning notice info debug System is unusable Action must be taken NOW Critical conditions Error conditions Warning conditions Normal but significant FYI More than you want to know (Programmers only)
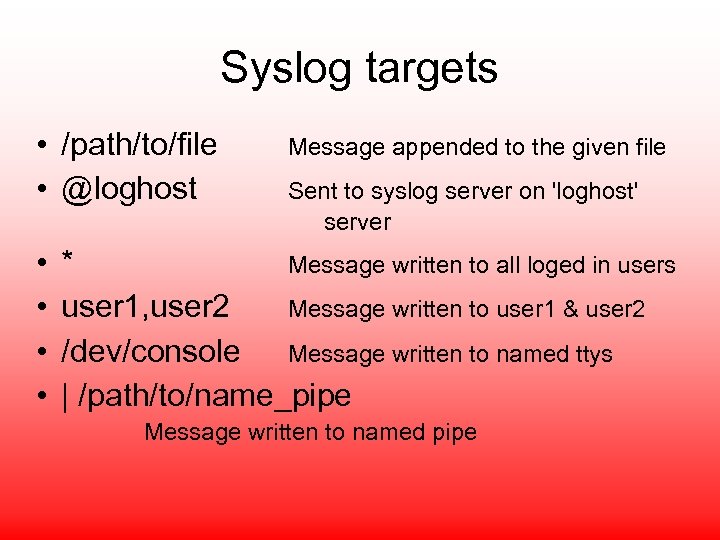 Syslog targets • /path/to/file • @loghost • • Message appended to the given file Sent to syslog server on 'loghost' server * Message written to all loged in users user 1, user 2 Message written to user 1 & user 2 /dev/console Message written to named ttys | /path/to/name_pipe Message written to named pipe
Syslog targets • /path/to/file • @loghost • • Message appended to the given file Sent to syslog server on 'loghost' server * Message written to all loged in users user 1, user 2 Message written to user 1 & user 2 /dev/console Message written to named ttys | /path/to/name_pipe Message written to named pipe
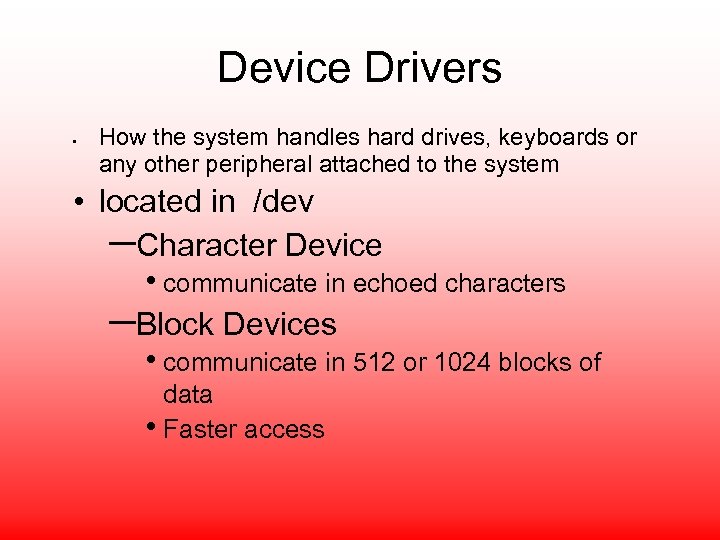 Device Drivers • How the system handles hard drives, keyboards or any other peripheral attached to the system • located in /dev –Character Device • communicate in echoed characters –Block Devices • communicate in 512 or 1024 blocks of data • Faster access
Device Drivers • How the system handles hard drives, keyboards or any other peripheral attached to the system • located in /dev –Character Device • communicate in echoed characters –Block Devices • communicate in 512 or 1024 blocks of data • Faster access
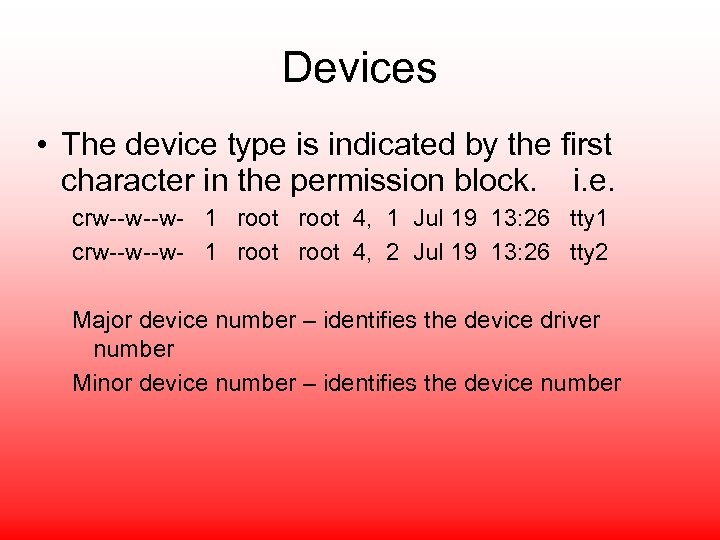 Devices • The device type is indicated by the first character in the permission block. i. e. crw--w--w- 1 root 4, 1 Jul 19 13: 26 tty 1 crw--w--w- 1 root 4, 2 Jul 19 13: 26 tty 2 Major device number – identifies the device driver number Minor device number – identifies the device number
Devices • The device type is indicated by the first character in the permission block. i. e. crw--w--w- 1 root 4, 1 Jul 19 13: 26 tty 1 crw--w--w- 1 root 4, 2 Jul 19 13: 26 tty 2 Major device number – identifies the device driver number Minor device number – identifies the device number
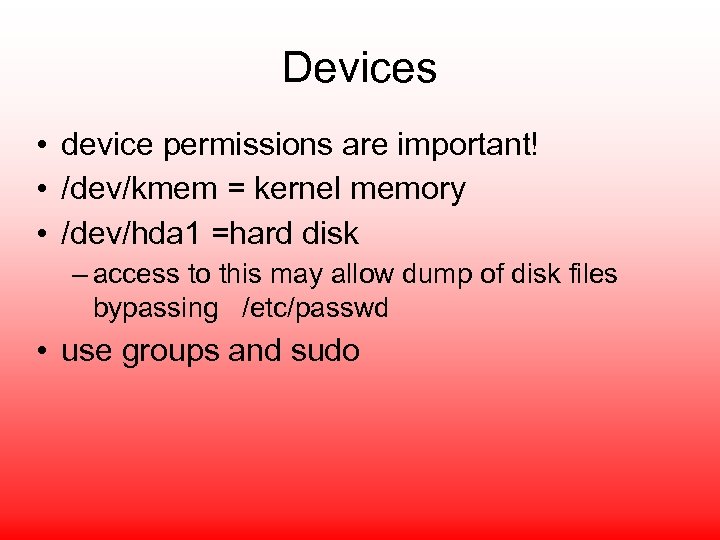 Devices • device permissions are important! • /dev/kmem = kernel memory • /dev/hda 1 =hard disk – access to this may allow dump of disk files bypassing /etc/passwd • use groups and sudo
Devices • device permissions are important! • /dev/kmem = kernel memory • /dev/hda 1 =hard disk – access to this may allow dump of disk files bypassing /etc/passwd • use groups and sudo
 Drives • mount – to show what is mounted • df- k, df -h to see free space • etc/fstab (/etc/vfstab - Solaris) to see file system mount point descriptions description of /dev/dsk -vs- /dev/rdsk
Drives • mount – to show what is mounted • df- k, df -h to see free space • etc/fstab (/etc/vfstab - Solaris) to see file system mount point descriptions description of /dev/dsk -vs- /dev/rdsk
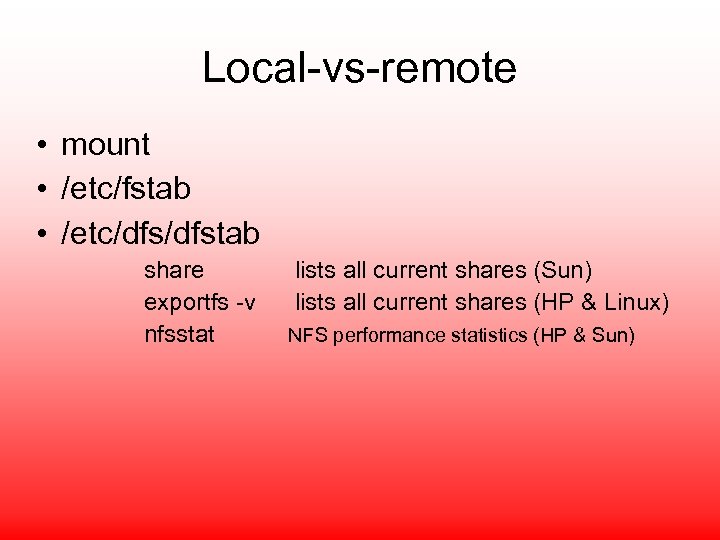 Local-vs-remote • mount • /etc/fstab • /etc/dfstab share exportfs -v nfsstat lists all current shares (Sun) lists all current shares (HP & Linux) NFS performance statistics (HP & Sun)
Local-vs-remote • mount • /etc/fstab • /etc/dfstab share exportfs -v nfsstat lists all current shares (Sun) lists all current shares (HP & Linux) NFS performance statistics (HP & Sun)
 Event Log • Syslog (and /etc/syslog. conf) /var/log/messages Linux /var/adm/messages HP & Sun tail and / or grep Ask if Swatch or logcheck may be running
Event Log • Syslog (and /etc/syslog. conf) /var/log/messages Linux /var/adm/messages HP & Sun tail and / or grep Ask if Swatch or logcheck may be running
 Printer Permission • /etc/hosts. lpd = hosts that can print – You can also put in /etc/hosts. equiv but that opens them to use rservices too! – lpadmin (solaris) ls. R -al /etc/lp Linux – cat /etc/printcap. local • shows all local printers • printtool (gui) – Hpux – lpadmin • /etc/lp/* • /var/adm/lp*
Printer Permission • /etc/hosts. lpd = hosts that can print – You can also put in /etc/hosts. equiv but that opens them to use rservices too! – lpadmin (solaris) ls. R -al /etc/lp Linux – cat /etc/printcap. local • shows all local printers • printtool (gui) – Hpux – lpadmin • /etc/lp/* • /var/adm/lp*
 Processes • Before we begin. . Policy Best Practices Goals of Security
Processes • Before we begin. . Policy Best Practices Goals of Security
 init Process init is always process #1 (all other things that happen before this are actually part of the kernel or kernel process) The “system father task” that propagates all child processes needed for operation. Configuration file: • /etc/inittab
init Process init is always process #1 (all other things that happen before this are actually part of the kernel or kernel process) The “system father task” that propagates all child processes needed for operation. Configuration file: • /etc/inittab
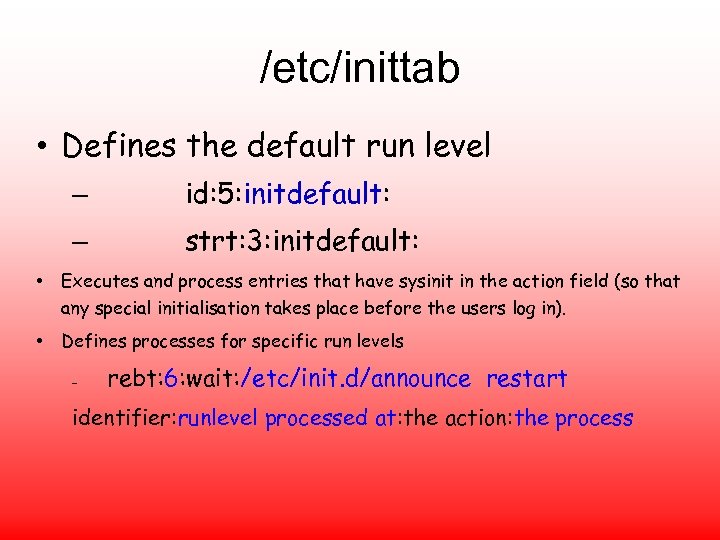 /etc/inittab • Defines the default run level – id: 5: initdefault: – strt: 3: initdefault: • Executes and process entries that have sysinit in the action field (so that any special initialisation takes place before the users log in). • Defines processes for specific run levels – rebt: 6: wait: /etc/init. d/announce restart identifier: runlevel processed at: the action: the process
/etc/inittab • Defines the default run level – id: 5: initdefault: – strt: 3: initdefault: • Executes and process entries that have sysinit in the action field (so that any special initialisation takes place before the users log in). • Defines processes for specific run levels – rebt: 6: wait: /etc/init. d/announce restart identifier: runlevel processed at: the action: the process
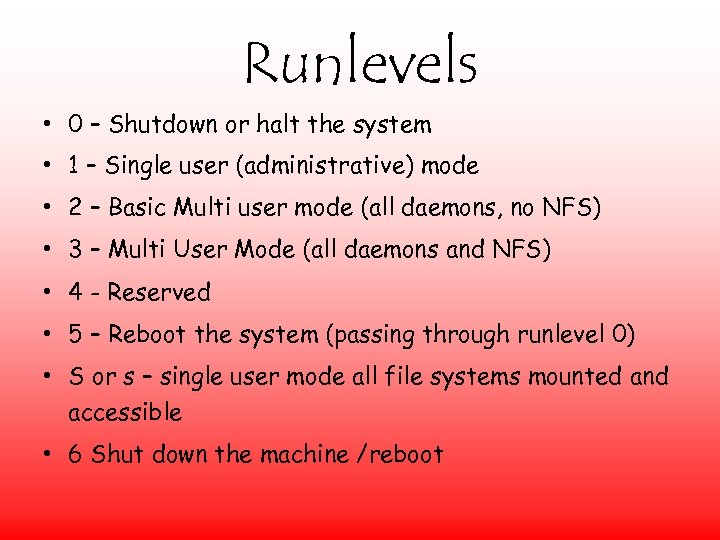 Runlevels • 0 – Shutdown or halt the system • 1 – Single user (administrative) mode • 2 – Basic Multi user mode (all daemons, no NFS) • 3 – Multi User Mode (all daemons and NFS) • 4 - Reserved • 5 – Reboot the system (passing through runlevel 0) • S or s – single user mode all file systems mounted and accessible • 6 Shut down the machine /reboot
Runlevels • 0 – Shutdown or halt the system • 1 – Single user (administrative) mode • 2 – Basic Multi user mode (all daemons, no NFS) • 3 – Multi User Mode (all daemons and NFS) • 4 - Reserved • 5 – Reboot the system (passing through runlevel 0) • S or s – single user mode all file systems mounted and accessible • 6 Shut down the machine /reboot
 Run Levels con't How do I display the current runlevel? • HP & Solaris – # who -r • run-level 3 Feb 28 10: 55 3 0 S • current run level date and time of run level change current run level number of times at this run level since last reboot previous run level • Linux – # /sbin/runlevel • N 5 or 3 5 (none before and now 5 or 3 before and 5 now)
Run Levels con't How do I display the current runlevel? • HP & Solaris – # who -r • run-level 3 Feb 28 10: 55 3 0 S • current run level date and time of run level change current run level number of times at this run level since last reboot previous run level • Linux – # /sbin/runlevel • N 5 or 3 5 (none before and now 5 or 3 before and 5 now)
 rc scripts Run Control Scripts exist for each run level Scripts start and/or stop all processes needed to put system into appropriate Run Level S start, K kill (stop) • processed sequentially 0 -99
rc scripts Run Control Scripts exist for each run level Scripts start and/or stop all processes needed to put system into appropriate Run Level S start, K kill (stop) • processed sequentially 0 -99
 Solaris rc scripts Run Control Scripts exist for each run level • /sbin/rc – directory for each script • /sbin/rc 3 – S 15 nfs. server -> /etc/rc 3. d/
Solaris rc scripts Run Control Scripts exist for each run level • /sbin/rc – directory for each script • /sbin/rc 3 – S 15 nfs. server -> /etc/rc 3. d/
 Linux rc scripts Run Control Scripts exist for each run level • /etc/rc. d/rc. local • /etc/rc. d/rc# – directory for each script • /etc/rc. d/rc 3 – K 20 nfs
Linux rc scripts Run Control Scripts exist for each run level • /etc/rc. d/rc. local • /etc/rc. d/rc# – directory for each script • /etc/rc. d/rc 3 – K 20 nfs
 rc scripts Run Control Scripts exist for each run level
rc scripts Run Control Scripts exist for each run level
 HP rc scripts Run Control Scripts exist for each run level • /sbin/rc#. d – directory for each script • /sbin/rc 3. d/ K 20 nfs
HP rc scripts Run Control Scripts exist for each run level • /sbin/rc#. d – directory for each script • /sbin/rc 3. d/ K 20 nfs
 Processes • ps -aef • ps -aux • inet. d /etc/inetd. conf • how to start, & stop /etc/init. d/name start or stop, restart • /proc directory cd /proc#; ls
Processes • ps -aef • ps -aux • inet. d /etc/inetd. conf • how to start, & stop /etc/init. d/name start or stop, restart • /proc directory cd /proc#; ls
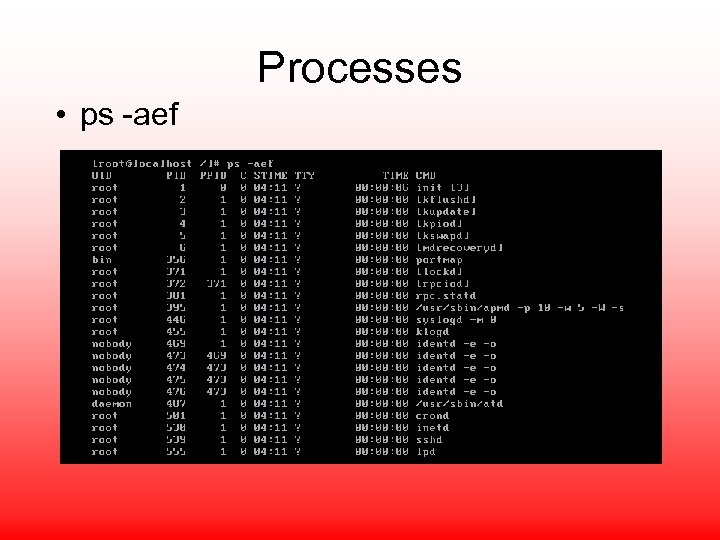 Processes • ps -aef
Processes • ps -aef
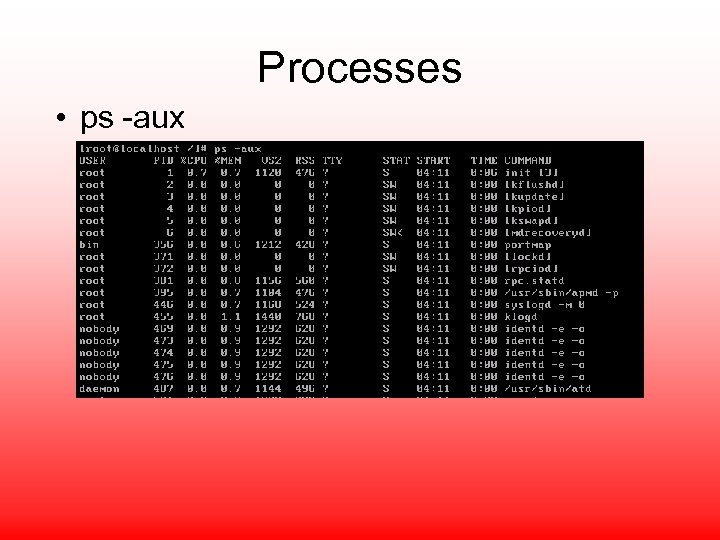 Processes • ps -aux
Processes • ps -aux
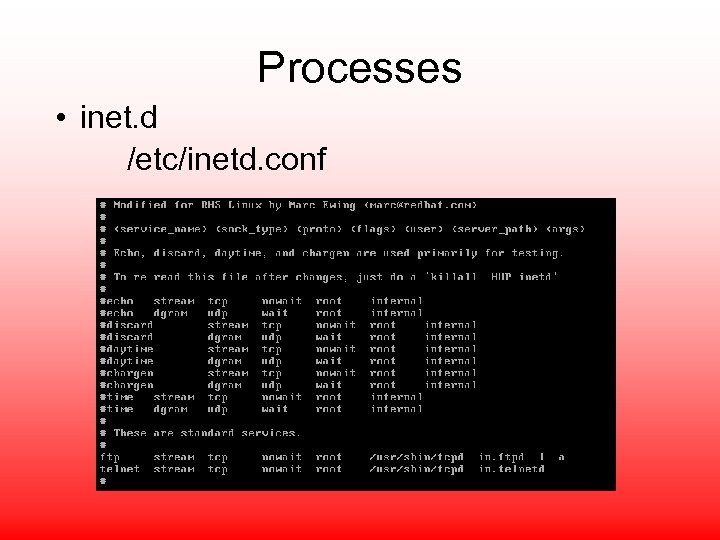 Processes • inet. d /etc/inetd. conf
Processes • inet. d /etc/inetd. conf
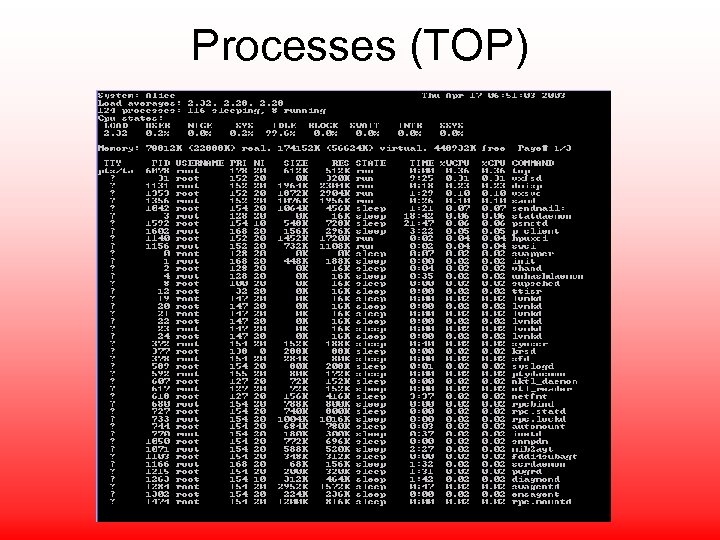 Processes (TOP)
Processes (TOP)
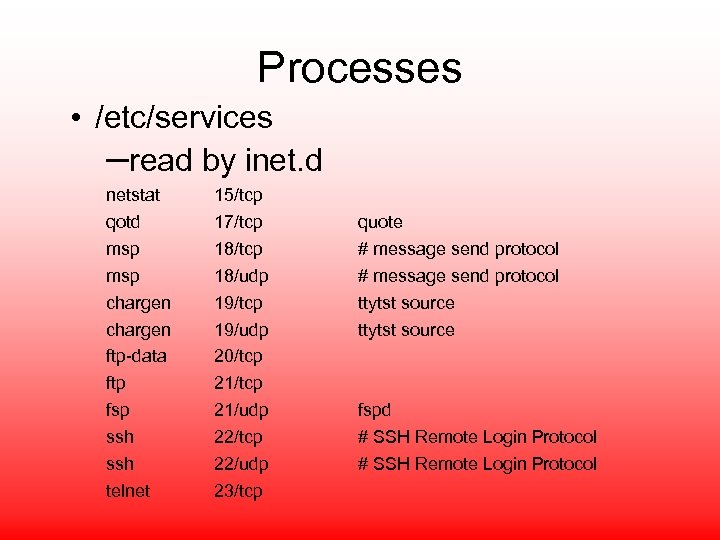 Processes • /etc/services –read by inet. d netstat qotd msp chargen ftp-data ftp fsp ssh telnet 15/tcp 17/tcp 18/udp 19/tcp 19/udp 20/tcp 21/udp 22/tcp 22/udp 23/tcp quote # message send protocol ttytst source fspd # SSH Remote Login Protocol
Processes • /etc/services –read by inet. d netstat qotd msp chargen ftp-data ftp fsp ssh telnet 15/tcp 17/tcp 18/udp 19/tcp 19/udp 20/tcp 21/udp 22/tcp 22/udp 23/tcp quote # message send protocol ttytst source fspd # SSH Remote Login Protocol
 Registry Bind, SMNP, HTTP • Bind • Snmp • HTTP
Registry Bind, SMNP, HTTP • Bind • Snmp • HTTP
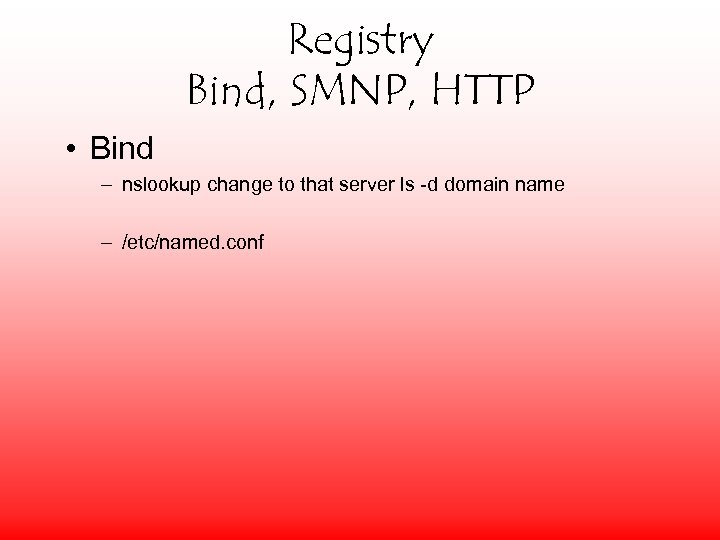 Registry Bind, SMNP, HTTP • Bind – nslookup change to that server ls -d domain name – /etc/named. conf
Registry Bind, SMNP, HTTP • Bind – nslookup change to that server ls -d domain name – /etc/named. conf
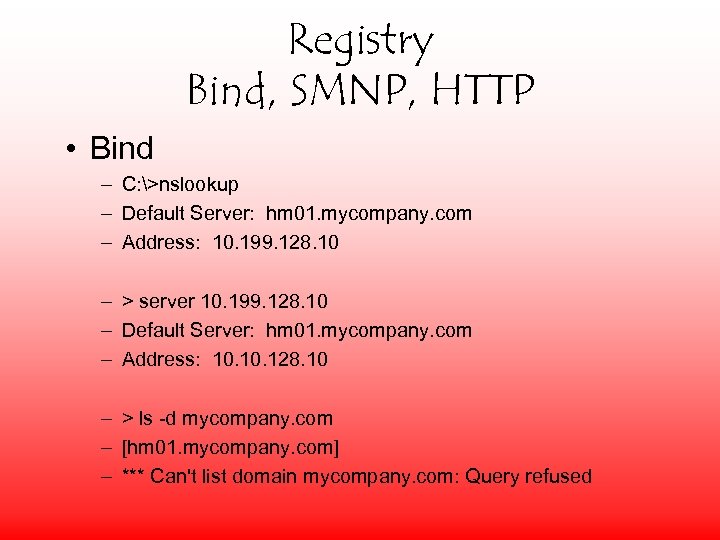 Registry Bind, SMNP, HTTP • Bind – C: >nslookup – Default Server: hm 01. mycompany. com – Address: 10. 199. 128. 10 – > server 10. 199. 128. 10 – Default Server: hm 01. mycompany. com – Address: 10. 128. 10 – > ls -d mycompany. com – [hm 01. mycompany. com] – *** Can't list domain mycompany. com: Query refused
Registry Bind, SMNP, HTTP • Bind – C: >nslookup – Default Server: hm 01. mycompany. com – Address: 10. 199. 128. 10 – > server 10. 199. 128. 10 – Default Server: hm 01. mycompany. com – Address: 10. 128. 10 – > ls -d mycompany. com – [hm 01. mycompany. com] – *** Can't list domain mycompany. com: Query refused
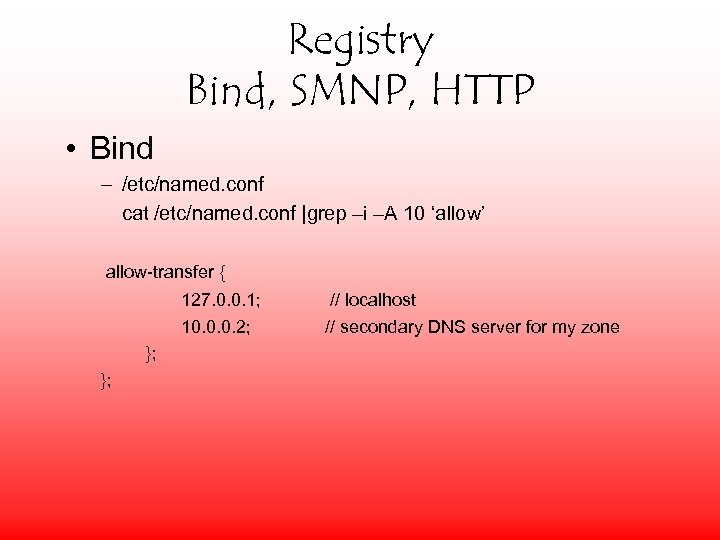 Registry Bind, SMNP, HTTP • Bind – /etc/named. conf cat /etc/named. conf |grep –i –A 10 ‘allow’ allow-transfer { 127. 0. 0. 1; 10. 0. 0. 2; }; }; // localhost // secondary DNS server for my zone
Registry Bind, SMNP, HTTP • Bind – /etc/named. conf cat /etc/named. conf |grep –i –A 10 ‘allow’ allow-transfer { 127. 0. 0. 1; 10. 0. 0. 2; }; }; // localhost // secondary DNS server for my zone
 ICAT Metabase
ICAT Metabase
 ICAT Metabase
ICAT Metabase
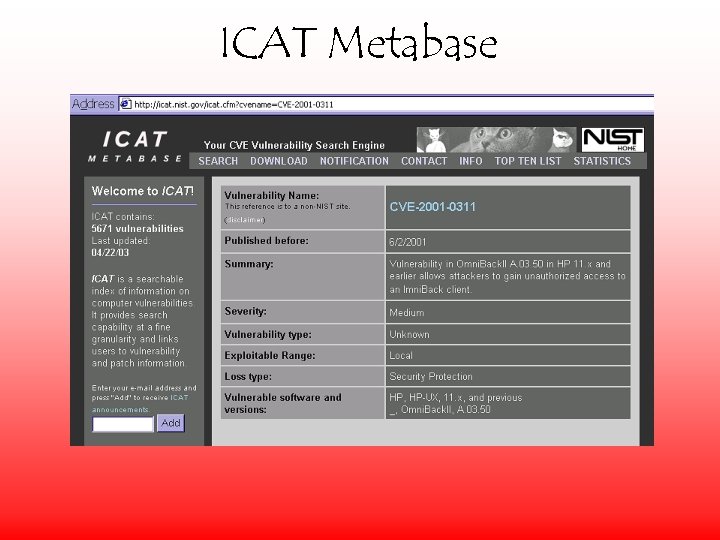 ICAT Metabase
ICAT Metabase
 SMNP • Smnp FILES • /usr/sbin/snmpdm • /usr/sbin/mib 2 agt • /usr/sbin/hp_unixagt • /usr/sbin/trapdestagt • /etc/Snmp. Agent. d/snmpd. conf • /var/adm/snmpd. log • /opt/OV/snmp_mibs/ • /sbin/Snmp. Agt. Start. d/
SMNP • Smnp FILES • /usr/sbin/snmpdm • /usr/sbin/mib 2 agt • /usr/sbin/hp_unixagt • /usr/sbin/trapdestagt • /etc/Snmp. Agent. d/snmpd. conf • /var/adm/snmpd. log • /opt/OV/snmp_mibs/ • /sbin/Snmp. Agt. Start. d/
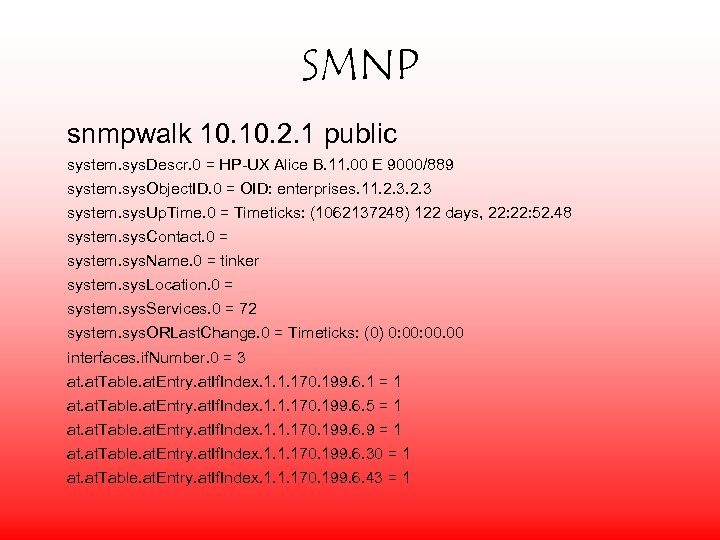 SMNP snmpwalk 10. 2. 1 public system. sys. Descr. 0 = HP-UX Alice B. 11. 00 E 9000/889 system. sys. Object. ID. 0 = OID: enterprises. 11. 2. 3 system. sys. Up. Time. 0 = Timeticks: (1062137248) 122 days, 22: 52. 48 system. sys. Contact. 0 = system. sys. Name. 0 = tinker system. sys. Location. 0 = system. sys. Services. 0 = 72 system. sys. ORLast. Change. 0 = Timeticks: (0) 0: 00. 00 interfaces. if. Number. 0 = 3 at. Table. at. Entry. at. If. Index. 1. 1. 170. 199. 6. 1 = 1 at. Table. at. Entry. at. If. Index. 1. 1. 170. 199. 6. 5 = 1 at. Table. at. Entry. at. If. Index. 1. 1. 170. 199. 6. 9 = 1 at. Table. at. Entry. at. If. Index. 1. 1. 170. 199. 6. 30 = 1 at. Table. at. Entry. at. If. Index. 1. 1. 170. 199. 6. 43 = 1
SMNP snmpwalk 10. 2. 1 public system. sys. Descr. 0 = HP-UX Alice B. 11. 00 E 9000/889 system. sys. Object. ID. 0 = OID: enterprises. 11. 2. 3 system. sys. Up. Time. 0 = Timeticks: (1062137248) 122 days, 22: 52. 48 system. sys. Contact. 0 = system. sys. Name. 0 = tinker system. sys. Location. 0 = system. sys. Services. 0 = 72 system. sys. ORLast. Change. 0 = Timeticks: (0) 0: 00. 00 interfaces. if. Number. 0 = 3 at. Table. at. Entry. at. If. Index. 1. 1. 170. 199. 6. 1 = 1 at. Table. at. Entry. at. If. Index. 1. 1. 170. 199. 6. 5 = 1 at. Table. at. Entry. at. If. Index. 1. 1. 170. 199. 6. 9 = 1 at. Table. at. Entry. at. If. Index. 1. 1. 170. 199. 6. 30 = 1 at. Table. at. Entry. at. If. Index. 1. 1. 170. 199. 6. 43 = 1
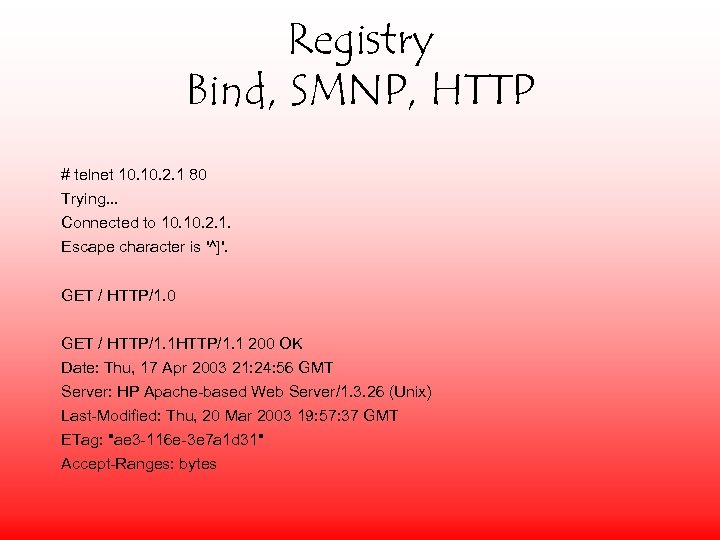 Registry Bind, SMNP, HTTP # telnet 10. 2. 1 80 Trying. . . Connected to 10. 2. 1. Escape character is '^]'. GET / HTTP/1. 0 GET / HTTP/1. 1 200 OK Date: Thu, 17 Apr 2003 21: 24: 56 GMT Server: HP Apache-based Web Server/1. 3. 26 (Unix) Last-Modified: Thu, 20 Mar 2003 19: 57: 37 GMT ETag: "ae 3 -116 e-3 e 7 a 1 d 31" Accept-Ranges: bytes
Registry Bind, SMNP, HTTP # telnet 10. 2. 1 80 Trying. . . Connected to 10. 2. 1. Escape character is '^]'. GET / HTTP/1. 0 GET / HTTP/1. 1 200 OK Date: Thu, 17 Apr 2003 21: 24: 56 GMT Server: HP Apache-based Web Server/1. 3. 26 (Unix) Last-Modified: Thu, 20 Mar 2003 19: 57: 37 GMT ETag: "ae 3 -116 e-3 e 7 a 1 d 31" Accept-Ranges: bytes
 Registry Bind, SMNP, HTTP Content-Length: 4462 Connection: close Content-Type: text/html
Registry Bind, SMNP, HTTP Content-Length: 4462 Connection: close Content-Type: text/html
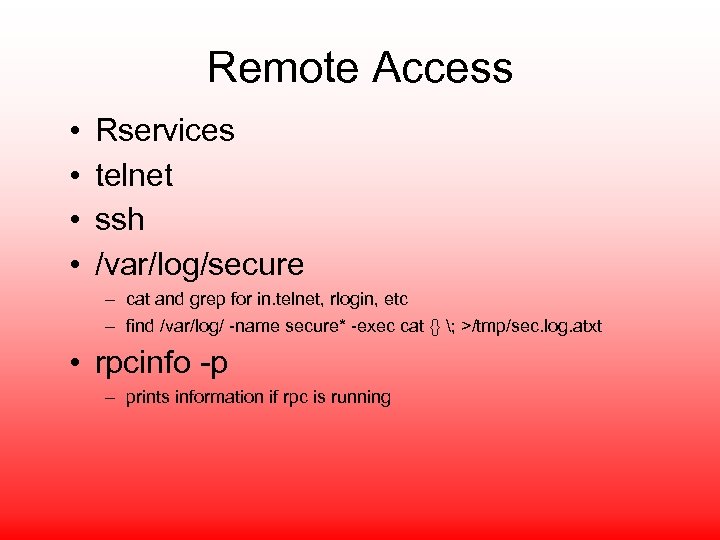 Remote Access • • Rservices telnet ssh /var/log/secure – cat and grep for in. telnet, rlogin, etc – find /var/log/ -name secure* -exec cat {} ; >/tmp/sec. log. atxt • rpcinfo -p – prints information if rpc is running
Remote Access • • Rservices telnet ssh /var/log/secure – cat and grep for in. telnet, rlogin, etc – find /var/log/ -name secure* -exec cat {} ; >/tmp/sec. log. atxt • rpcinfo -p – prints information if rpc is running
 Scheduled Tasks • Cron – Crontab -l 1 2345 21 14 * * 2 /path/to/whatever/bin/sh/etc/2 run 1 MINUTE(0 -59) 2 3 HOUR(0 -23) DAYOFMONTH(1 -31) 5 DAYOFWEEK(0 -6) Note 0 = Sun 2 = Tue 4 = Thr 6 = Sat 4 MONTHOFYEAR(1 -12)
Scheduled Tasks • Cron – Crontab -l 1 2345 21 14 * * 2 /path/to/whatever/bin/sh/etc/2 run 1 MINUTE(0 -59) 2 3 HOUR(0 -23) DAYOFMONTH(1 -31) 5 DAYOFWEEK(0 -6) Note 0 = Sun 2 = Tue 4 = Thr 6 = Sat 4 MONTHOFYEAR(1 -12)
 System Info • dmesg • prtconf -v (Solaris) • ioscan (HP)
System Info • dmesg • prtconf -v (Solaris) • ioscan (HP)
 System Info dmesg Variable size pages used to map 1000 graf pages at f 7000000 NOTICE: nfs 3_link(): File system was registered at index 3. NOTICE: autofs_link(): File system was registered at index 6. NOTICE: cachefs_link(): File system was registered at index 7. 8 ccio 8/4 c 720 8/4. 2 tgt 8/4. 2. 0 stape 8/4. 7. 0 sctl 8/4. 15. 0 sdisk 8/8 c 720 8/8. 7 tgt 8/8. 7. 0 sctl 8/16 bus_adapter
System Info dmesg Variable size pages used to map 1000 graf pages at f 7000000 NOTICE: nfs 3_link(): File system was registered at index 3. NOTICE: autofs_link(): File system was registered at index 6. NOTICE: cachefs_link(): File system was registered at index 7. 8 ccio 8/4 c 720 8/4. 2 tgt 8/4. 2. 0 stape 8/4. 7. 0 sctl 8/4. 15. 0 sdisk 8/8 c 720 8/8. 7 tgt 8/8. 7. 0 sctl 8/16 bus_adapter
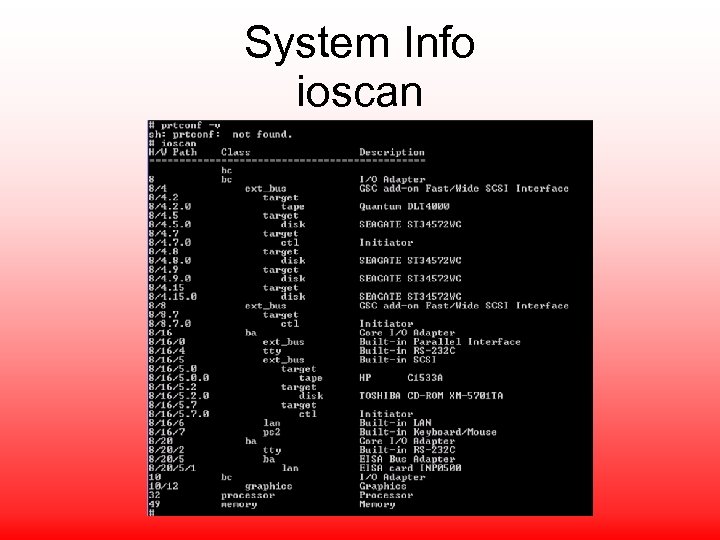 System Info ioscan
System Info ioscan
 Services • /etc/services • /etc/inetd – super daemon 1. checks the incoming port, 2. consults /etc/services to get the service name, 3. reads its configuration file, /etc/inetd. conf to determine what program to start to handle the incoming connection
Services • /etc/services • /etc/inetd – super daemon 1. checks the incoming port, 2. consults /etc/services to get the service name, 3. reads its configuration file, /etc/inetd. conf to determine what program to start to handle the incoming connection
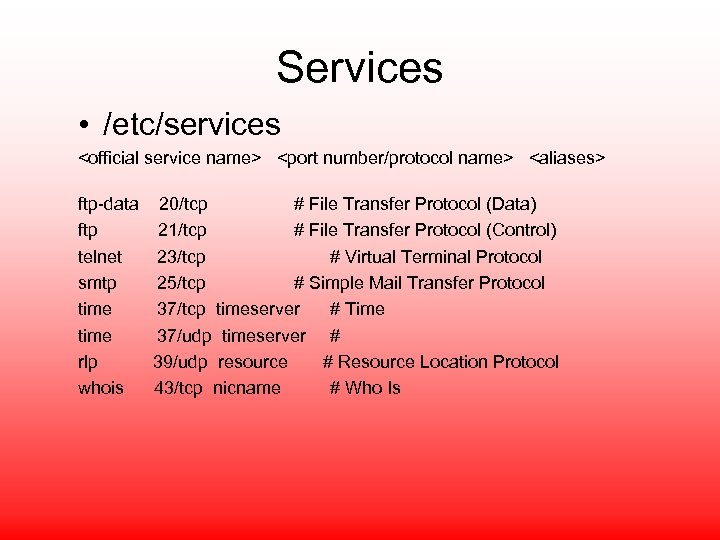 Services • /etc/services
Services • /etc/services
 Services ● /etc/inetd. conf # A line in the configuration file has the following fields separated by tabs and/or spaces: # service name as in /etc/services # socket type either "stream" or "dgram" # protocol as in /etc/protocols # wait/nowait only applies to datagram sockets, stream # sockets should specify nowait # user name of user as whom the server should run # server program absolute pathname for the server inetd will # execute # server program args. arguments server program uses as they normally # are starting with argv[0] which is the name of # ftp the server. stream tcp nowait root /usr/lbin/ftpd -l (Causes each FTP session to be logged in the syslog file. ) telnet stream tcp nowait root /usr/lbin/telnetd
Services ● /etc/inetd. conf # A line in the configuration file has the following fields separated by tabs and/or spaces: # service name as in /etc/services # socket type either "stream" or "dgram" # protocol as in /etc/protocols # wait/nowait only applies to datagram sockets, stream # sockets should specify nowait # user name of user as whom the server should run # server program absolute pathname for the server inetd will # execute # server program args. arguments server program uses as they normally # are starting with argv[0] which is the name of # ftp the server. stream tcp nowait root /usr/lbin/ftpd -l (Causes each FTP session to be logged in the syslog file. ) telnet stream tcp nowait root /usr/lbin/telnetd
 Shares • nis (Network Information Service) Formerly YP (Yellow Pages) • nfs (Network File System)
Shares • nis (Network Information Service) Formerly YP (Yellow Pages) • nfs (Network File System)
 NFS Server • Daemons mountd, nfsd, statd, nfslogd • Files /etc/dfstab /etc/dfs/rmtab /etc/dfs/nfslog. conf list of all local filesystems automatically shared table of nfs file systems mounted by clients defines path, filenames & logging options • Commands share, unshare, dfshares, dfmounts (all show share in use information)
NFS Server • Daemons mountd, nfsd, statd, nfslogd • Files /etc/dfstab /etc/dfs/rmtab /etc/dfs/nfslog. conf list of all local filesystems automatically shared table of nfs file systems mounted by clients defines path, filenames & logging options • Commands share, unshare, dfshares, dfmounts (all show share in use information)
 NFS Security • In general ● Only run NFS as needed, apply latest patches Careful use of /etc/exports (or /etc/dfstab for SUN) Read-only if possible No suid if possible ● Fully qualified hostnames ● ● ●
NFS Security • In general ● Only run NFS as needed, apply latest patches Careful use of /etc/exports (or /etc/dfstab for SUN) Read-only if possible No suid if possible ● Fully qualified hostnames ● ● ●
 NFS Client • Daemons (look for them) statd, lockd • Files (review) /etc/vfstab /etc/mnttab /etc/dfs/fstypes • Commands dfshares dfsmounts
NFS Client • Daemons (look for them) statd, lockd • Files (review) /etc/vfstab /etc/mnttab /etc/dfs/fstypes • Commands dfshares dfsmounts
 NIS • If you do NOT use NIS or NIS+, make your system a HP-UX trusted system for easier system security
NIS • If you do NOT use NIS or NIS+, make your system a HP-UX trusted system for easier system security
 NIS Daemon ypserv ypwhich ypcat -x Function Server process Lists name of the NIS server (client) Displays the contents of an NIS map (client)
NIS Daemon ypserv ypwhich ypcat -x Function Server process Lists name of the NIS server (client) Displays the contents of an NIS map (client)
 NIS What's exported # ypwhich the NIS domain name hasn't been set on this machine # exportfs -v (HP shows all exported) nothing exported
NIS What's exported # ypwhich the NIS domain name hasn't been set on this machine # exportfs -v (HP shows all exported) nothing exported
 NIS # ypwhich
NIS # ypwhich
 NIS # exportfs -v
NIS # exportfs -v
 NIS # ypcat -x or ypwhich -x Use "passwd" for map "passwd. byname" Use "group" for map "group. byname" Use "networks" for map "networks. byaddr" Use "hosts" for map "hosts. byaddr" Use "protocols" for map "protocols. bynumber" Use "services" for map "services. byname" Use "aliases" for map "mail. aliases" Use "ethers" for map "ethers. byname"
NIS # ypcat -x or ypwhich -x Use "passwd" for map "passwd. byname" Use "group" for map "group. byname" Use "networks" for map "networks. byaddr" Use "hosts" for map "hosts. byaddr" Use "protocols" for map "protocols. bynumber" Use "services" for map "services. byname" Use "aliases" for map "mail. aliases" Use "ethers" for map "ethers. byname"
 NIS • HP cat /var/yp/secureservers -defines trusted NIS servers 255 192. 1. 1. 1 255. 0. 0 128. 1. 0. 0 • -only one server -any server from the 128. 1 subnet HP cat /var/yp/securenets -defines trusted NIS clients 255 192. 1. 1. 2 -only one client 255. 0. 0 128. 1. 0. 0 -any client from the 128. 1 subnet
NIS • HP cat /var/yp/secureservers -defines trusted NIS servers 255 192. 1. 1. 1 255. 0. 0 128. 1. 0. 0 • -only one server -any server from the 128. 1 subnet HP cat /var/yp/securenets -defines trusted NIS clients 255 192. 1. 1. 2 -only one client 255. 0. 0 128. 1. 0. 0 -any client from the 128. 1 subnet
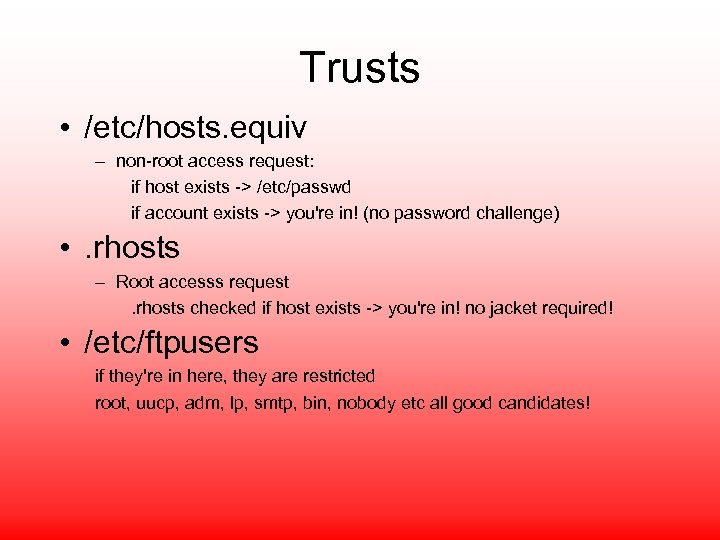 Trusts • /etc/hosts. equiv – non-root access request: if host exists -> /etc/passwd if account exists -> you're in! (no password challenge) • . rhosts – Root accesss request. rhosts checked if host exists -> you're in! no jacket required! • /etc/ftpusers if they're in here, they are restricted root, uucp, adm, lp, smtp, bin, nobody etc all good candidates!
Trusts • /etc/hosts. equiv – non-root access request: if host exists -> /etc/passwd if account exists -> you're in! (no password challenge) • . rhosts – Root accesss request. rhosts checked if host exists -> you're in! no jacket required! • /etc/ftpusers if they're in here, they are restricted root, uucp, adm, lp, smtp, bin, nobody etc all good candidates!
 Trusts TCP Wrappers only TCP Wrappers inserts itself into the middle of the relationship and acts as the server until the client/host is authenticated • /etc/hosts. deny (ALL: ALL) Hosts that will be denied access • /etc/hosts. allow (only trusted hosts!) Hosts that will be permitted access
Trusts TCP Wrappers only TCP Wrappers inserts itself into the middle of the relationship and acts as the server until the client/host is authenticated • /etc/hosts. deny (ALL: ALL) Hosts that will be denied access • /etc/hosts. allow (only trusted hosts!) Hosts that will be permitted access
 Trusts • /usr/adm/sulog – see who has been switching users • /var/log/messages – see who has been switching user • find / -nouser -print -o -nogroup -print • find / -user root -perm -004000 -print • • • find / -xdev -perm -004000 -exec ls -l {} ; find / -name. rhosts -exec cat {}; >audit. rh find / -name. netrc
Trusts • /usr/adm/sulog – see who has been switching users • /var/log/messages – see who has been switching user • find / -nouser -print -o -nogroup -print • find / -user root -perm -004000 -print • • • find / -xdev -perm -004000 -exec ls -l {} ; find / -name. rhosts -exec cat {}; >audit. rh find / -name. netrc
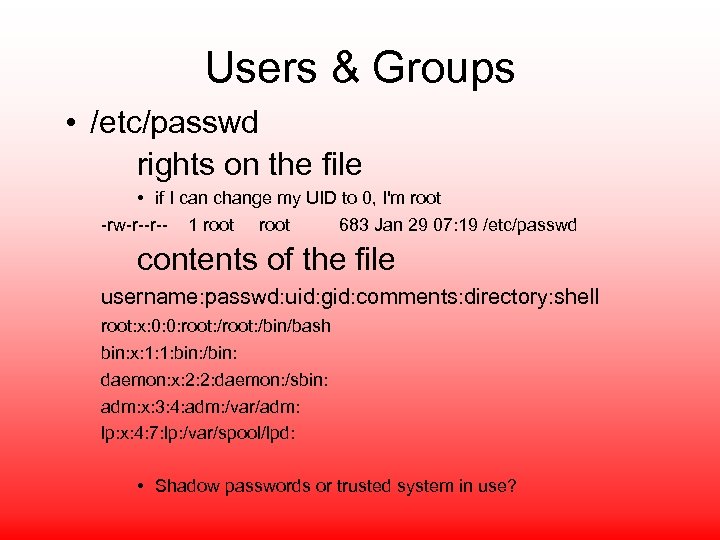 Users & Groups • /etc/passwd rights on the file • if I can change my UID to 0, I'm root -rw-r--r-- 1 root 683 Jan 29 07: 19 /etc/passwd contents of the file username: passwd: uid: gid: comments: directory: shell root: x: 0: 0: root: /bin/bash bin: x: 1: 1: bin: /bin: daemon: x: 2: 2: daemon: /sbin: adm: x: 3: 4: adm: /var/adm: lp: x: 4: 7: lp: /var/spool/lpd: • Shadow passwords or trusted system in use?
Users & Groups • /etc/passwd rights on the file • if I can change my UID to 0, I'm root -rw-r--r-- 1 root 683 Jan 29 07: 19 /etc/passwd contents of the file username: passwd: uid: gid: comments: directory: shell root: x: 0: 0: root: /bin/bash bin: x: 1: 1: bin: /bin: daemon: x: 2: 2: daemon: /sbin: adm: x: 3: 4: adm: /var/adm: lp: x: 4: 7: lp: /var/spool/lpd: • Shadow passwords or trusted system in use?
 Shadow Passwords • Solaris, Linux –/etc/shadow • HPUX –/tcb/files/auth
Shadow Passwords • Solaris, Linux –/etc/shadow • HPUX –/tcb/files/auth
 Shadow Passwords username: password: Date of last change (# days since 01/01/1970): minimum days between changes: maximum # days between changes: # days warning in advance of change: # days after required change before disabled: account expire date : reserved and empty root: $1$RY 7 BRRo 9$vb. JX 3 mu 0 ESe. UAhlf. YYupk 1: 12081: 0: 99999: 7: -1: 134539236 * bin: : 11926: 0: 99999: 7: : : daemon: *: 11926: 0: 99999: 7: : : adm: : 11926: 0: 99999: 7: : :
Shadow Passwords username: password: Date of last change (# days since 01/01/1970): minimum days between changes: maximum # days between changes: # days warning in advance of change: # days after required change before disabled: account expire date : reserved and empty root: $1$RY 7 BRRo 9$vb. JX 3 mu 0 ESe. UAhlf. YYupk 1: 12081: 0: 99999: 7: -1: 134539236 * bin: : 11926: 0: 99999: 7: : : daemon: *: 11926: 0: 99999: 7: : : adm: : 11926: 0: 99999: 7: : :
 Users & Groups • /etc/groups rights on the file • if I can change my GID to 0, I've got root -rw-r--r-- 1 root 455 Jan 29 07: 19 /etc/group contents of the file group_name: password: group_id: list root: x: 0: root bin: x: 1: root, bin, daemon: x: 2: root, bin, daemon sys: x: 3: root, bin, adm: x: 4: root, adm, daemon tty: x: 5:
Users & Groups • /etc/groups rights on the file • if I can change my GID to 0, I've got root -rw-r--r-- 1 root 455 Jan 29 07: 19 /etc/group contents of the file group_name: password: group_id: list root: x: 0: root bin: x: 1: root, bin, daemon: x: 2: root, bin, daemon sys: x: 3: root, bin, adm: x: 4: root, adm, daemon tty: x: 5:
 Putting it all together • Script to run commands and dump output to /tmp • tar all of the output files and transfer via network to your laptop • use Cygwin to evaluate the output files!
Putting it all together • Script to run commands and dump output to /tmp • tar all of the output files and transfer via network to your laptop • use Cygwin to evaluate the output files!
 Putting it all together • • Grep Telnet Cat Find
Putting it all together • • Grep Telnet Cat Find
 Putting it all together last >/tmp/last. atxt root tty 1 Sun Mar 16 12: 22 still logged in reboot system boot 2. 2. 14 -5. 0 Sun Mar 16 12: 21 (05: 51) root tty 1 Sat Mar 15 14: 20 - down (07: 12) root pts/1 : 0 Sat Mar 15 14: 14 - 14: 14 (00: 00) root pts/1 : 0 Sat Mar 15 13: 07 - 13: 07 (00: 00) root pts/0 : 0 Sat Mar 15 12: 27 - 14: 14 (01: 46) root tty 1 Sat Mar 15 12: 01 - 14: 19 (02: 18) reboot system boot 2. 2. 14 -5. 0 Sat Mar 15 11: 58 (09: 34) root tty 1 Thu Mar 13 06: 32 - down (08: 10) root tty 1 Thu Mar 13 06: 29 - 06: 32 (00: 02) reboot system boot 2. 2. 14 -5. 0 root tty 1 (08: 19) Tue Mar 11 07: 11 - down (02: 17) reboot system boot 2. 2. 14 -5. 0 root Thu Mar 13 06: 24 Tue Mar 11 07: 10 (02: 18) Sun Mar 9 18: 12 - down (00: 49) reboot system boot 2. 2. 14 -5. 0 Sun Mar 9 18: 09 (00: 51)
Putting it all together last >/tmp/last. atxt root tty 1 Sun Mar 16 12: 22 still logged in reboot system boot 2. 2. 14 -5. 0 Sun Mar 16 12: 21 (05: 51) root tty 1 Sat Mar 15 14: 20 - down (07: 12) root pts/1 : 0 Sat Mar 15 14: 14 - 14: 14 (00: 00) root pts/1 : 0 Sat Mar 15 13: 07 - 13: 07 (00: 00) root pts/0 : 0 Sat Mar 15 12: 27 - 14: 14 (01: 46) root tty 1 Sat Mar 15 12: 01 - 14: 19 (02: 18) reboot system boot 2. 2. 14 -5. 0 Sat Mar 15 11: 58 (09: 34) root tty 1 Thu Mar 13 06: 32 - down (08: 10) root tty 1 Thu Mar 13 06: 29 - 06: 32 (00: 02) reboot system boot 2. 2. 14 -5. 0 root tty 1 (08: 19) Tue Mar 11 07: 11 - down (02: 17) reboot system boot 2. 2. 14 -5. 0 root Thu Mar 13 06: 24 Tue Mar 11 07: 10 (02: 18) Sun Mar 9 18: 12 - down (00: 49) reboot system boot 2. 2. 14 -5. 0 Sun Mar 9 18: 09 (00: 51)
 Putting it all together • grep -a -i -f grep. txt target. txt -a = process the target file as text –i=ignore case –f=use input file grep. txt=name of input file target. txt= file being “grepped” Cygwin note: If you are using Cygwin, you can create the input file in a Windows editor (i. e. Notepad) but before using it to grep you must convert it to a unix file by using the ‘dos 2 unix’ command (dos 2 unix filename). i. e. dos 2 unix grep. txt will convert the dos text file grep. txt to unix text. The differences between the two are not great, but they are large enough to prevent grep from understanding the input file if you don’t convert it first!
Putting it all together • grep -a -i -f grep. txt target. txt -a = process the target file as text –i=ignore case –f=use input file grep. txt=name of input file target. txt= file being “grepped” Cygwin note: If you are using Cygwin, you can create the input file in a Windows editor (i. e. Notepad) but before using it to grep you must convert it to a unix file by using the ‘dos 2 unix’ command (dos 2 unix filename). i. e. dos 2 unix grep. txt will convert the dos text file grep. txt to unix text. The differences between the two are not great, but they are large enough to prevent grep from understanding the input file if you don’t convert it first!
 Putting it all together talk name finger uucp mouse tftp shell login exec comsat systat netstat admind
Putting it all together talk name finger uucp mouse tftp shell login exec comsat systat netstat admind
 Putting it all together $ grep -a -i -f grep. txt target. txt systat 11/tcp users # Active Users whois 43/tcp nicname # Who Is tftp 69/udp # Trivial File Transfer Protocol finger 79/tcp # Finger hostnames 101/tcp hostname uucp-path 117/tcp # UUCP Path Service netbios_ns 137/tcp # Net. BIOS Name Service exec 512/tcp # remote execution, passwd required login 513/tcp # remote login shell 514/tcp talk 517/udp # conversation ntalk 518/udp # new talk, conversation cmd # NIC Host Name Server # remote command, no passwd used
Putting it all together $ grep -a -i -f grep. txt target. txt systat 11/tcp users # Active Users whois 43/tcp nicname # Who Is tftp 69/udp # Trivial File Transfer Protocol finger 79/tcp # Finger hostnames 101/tcp hostname uucp-path 117/tcp # UUCP Path Service netbios_ns 137/tcp # Net. BIOS Name Service exec 512/tcp # remote execution, passwd required login 513/tcp # remote login shell 514/tcp talk 517/udp # conversation ntalk 518/udp # new talk, conversation cmd # NIC Host Name Server # remote command, no passwd used
![Putting it all together grep -o 'JM[0 -9][0 -9][0 -9][0 -9][0 -9]' leg_share. txt Putting it all together grep -o 'JM[0 -9][0 -9][0 -9][0 -9][0 -9]' leg_share. txt](https://present5.com/presentation/645b720994a482f4782d1844abad1938/image-99.jpg) Putting it all together grep -o 'JM[0 -9][0 -9][0 -9][0 -9][0 -9]' leg_share. txt |sort -u grep -o 'JM[0 -9][0 -9][0 -9]' leg_share. txt |sort -u >sorted. txt; grep -A 1 -f sorted. txt april_users. txt
Putting it all together grep -o 'JM[0 -9][0 -9][0 -9][0 -9][0 -9]' leg_share. txt |sort -u grep -o 'JM[0 -9][0 -9][0 -9]' leg_share. txt |sort -u >sorted. txt; grep -A 1 -f sorted. txt april_users. txt
 Putting it all together tar –cvf audit. tar /tmp/*atxt
Putting it all together tar –cvf audit. tar /tmp/*atxt
 Putting it all together • • • The following slides are a list of commands I use to audit Unix systems. This list is not “all encompassing”, well organized, 100% accurate, or 100% complete. Use at your own risk, no warranty expressed or implied. Void where prohibited. This list can be a place to start your own research. The goal is to place the output of these simple commands into the /tmp directory, tar them up and then transfer them back to the auditor’s workstation for analysis. Good luck and enjoy!
Putting it all together • • • The following slides are a list of commands I use to audit Unix systems. This list is not “all encompassing”, well organized, 100% accurate, or 100% complete. Use at your own risk, no warranty expressed or implied. Void where prohibited. This list can be a place to start your own research. The goal is to place the output of these simple commands into the /tmp directory, tar them up and then transfer them back to the auditor’s workstation for analysis. Good luck and enjoy!
 Putting it all together "the usual suspects" “the usual reasons” ls /etc/sam/custom/login-name. cf #config file that sets user’s rights for sam bdf >/tmp/bdf. atxt show mounts cat /etc/passwd |sort >/tmp/passwd. atxt users and passwd info cat group list and members /etc/group |sort >/tmp/groups. atxt cat /etc/shadow |sort >/tmp/shadow. atxt users and passwd info cat list content of services file /etc/services >/tmp/services. atxt cat /etc/aliases >/tmp/aliases. atxt system mail aliases cat /etc/default/useradd >/tmp/useradd. atxt show useradd template params cat /etc/dfstab >/tmp/dfstab. atxt list mount points cat /etc/fstab >/tmp/fstab. atxt list mount points cat /etc/exports >tmp/exports. atxt look for nfs cat /etc/ftpd/ftpusers |sort >/tmp/ftpusers. atxt restricted ftp users cat /etc/host. equiv >/tmp/host. equiv. atxt show priveleged hosts cat /etc/hosts show hosts resolve >/tmp/hosts. atxt (errors can be a good thing!) cat /etc/inetd. conf >/tmp/ined. conf. atxt show the configuration file for inetd cat /etc/xinetd. d/inetd. conf >/tmp/ined. conf. atxt show the configuration file for inetd cat /etc/inittab >/tmp/inittab. atxt show initialization tab cat /etc/nsswitch. conf >/tmp/nsswitch. atxt display name resolution order cat /etc/pam >/tmp/pam. atxt Pluggable Authentication Modules cat /etc/pam. conf >/tmp/pamconf. atxt Display Pam Settings cat /etc/PATH >/tmp/path. atxt display path echo $PATH >/tmp/path. atxt display path cat /etc/profile >/tmp/profile. atxt show profiles cat /etc/rc. config >/tmp/rcconfig. atxt show rc config * omit everything to the right of “>” for output to screen
Putting it all together "the usual suspects" “the usual reasons” ls /etc/sam/custom/login-name. cf #config file that sets user’s rights for sam bdf >/tmp/bdf. atxt show mounts cat /etc/passwd |sort >/tmp/passwd. atxt users and passwd info cat group list and members /etc/group |sort >/tmp/groups. atxt cat /etc/shadow |sort >/tmp/shadow. atxt users and passwd info cat list content of services file /etc/services >/tmp/services. atxt cat /etc/aliases >/tmp/aliases. atxt system mail aliases cat /etc/default/useradd >/tmp/useradd. atxt show useradd template params cat /etc/dfstab >/tmp/dfstab. atxt list mount points cat /etc/fstab >/tmp/fstab. atxt list mount points cat /etc/exports >tmp/exports. atxt look for nfs cat /etc/ftpd/ftpusers |sort >/tmp/ftpusers. atxt restricted ftp users cat /etc/host. equiv >/tmp/host. equiv. atxt show priveleged hosts cat /etc/hosts show hosts resolve >/tmp/hosts. atxt (errors can be a good thing!) cat /etc/inetd. conf >/tmp/ined. conf. atxt show the configuration file for inetd cat /etc/xinetd. d/inetd. conf >/tmp/ined. conf. atxt show the configuration file for inetd cat /etc/inittab >/tmp/inittab. atxt show initialization tab cat /etc/nsswitch. conf >/tmp/nsswitch. atxt display name resolution order cat /etc/pam >/tmp/pam. atxt Pluggable Authentication Modules cat /etc/pam. conf >/tmp/pamconf. atxt Display Pam Settings cat /etc/PATH >/tmp/path. atxt display path echo $PATH >/tmp/path. atxt display path cat /etc/profile >/tmp/profile. atxt show profiles cat /etc/rc. config >/tmp/rcconfig. atxt show rc config * omit everything to the right of “>” for output to screen
/tmp/rhosts. atxt" src="https://present5.com/presentation/645b720994a482f4782d1844abad1938/image-103.jpg" alt="Putting it all together "the usual suspects" “the usual reasons” cat /etc/rhosts >/tmp/rhosts. atxt" />
Putting it all together "the usual suspects" “the usual reasons” cat /etc/rhosts >/tmp/rhosts. atxt show hosts able to connect remote cat /etc/rpc >/tmp/rpc. atxt RPC program number database cat /etc/shadow >/tmp/shadow. atxt shadow password cat /etc/uucp/Devices >/tmp/uucp_devices. atxt look for uucp devices cat /etc/uucp/Dialers >/tmp/uucp_dialers. atxt check for modems cat /usr/lib/uucp/Devices >/tmp/uucp_devices. atxt list of uucp devices cat /usr/lib/uucp/Dialers >/tmp/uucp_dialers. atxt check for modem phone numbers cat /usr/lib/uucp/Systems >/tmp/uucp_systems. atxt list of uucp systems crontab -l >/tmp/crons. atxt list contents of the crontab df -h >/tmp/df. atxt disk space df -k >/tmp/dfk. atxt show disk space # df -k >/tmp/x. atxt show disk space env >/tmp/env. atxt display environment exportfs >/tmp/exportfs. atxt list currently exported files and directories last logins >/tmp/last. atxt lastb >/tmp/last. bad. atxt last bad logins ls /etc/rc/rc. 3 >/tmp/rc 3. atxt Show what is turned on/off for this runlevel ls /etc/rc/rc. 5 >/tmp/rc 5. atxt Show what is turned on/off for this runlevel ls -l /etc/exports >/tmp/exports. atxt show permissions on /etc/exports ls -l -R /tcb/files/auth >/tmp/hp_trusted. atxt show trusted systems “shadow ls -l -R rights on the (ugh) filesystem >/tmp/filesys. atxt mount >/tmp/mountpts. atxt * omit everything to the right of “>” for output to screen show drive mount points file”
 Putting it all together "the usual suspects" “the usual reasons” cat /etc/rc. config. d/netconf >/tmp/netconf. atxt config values for core networking subsystems cat /etc/rc. config. d/netconf /etc/rc. config. d/auditing >> >/ tmp/rc_configd. atxt #gets the rest cat /etc/resolv. conf # defines the domain the system client will use. >/tmp/resolvconf. atxt cat /etc/uucp/Systems >/tmp/uucp_systems. atxt belongs to and the name server the “Unix-to-Unix copy”. Lists and describes remote systems accessible to a local system using the Basic Networking Utilities " cat /var/adm/inetd. sec >/tmp/inetd_sec. atxt "# The lines in the file contain a service name permission field and the Internet addresses or names of the hosts and/or networks allowed to use that service in the local machine. cat for /etc/securetty >/tmp/. atxt "file with contents “console” if exists then root can only login from console all others must remote login as themselves and then su. " find / ( -perm -0200 -o -perm -0400 ) - ls >/tmp/uid. atxt find / -name. profile - >/ tmp/x. atxt find / -name. rhost -exec cat {} ; > rhosts. txt look for setuid or guid show profile (get cshell and korn shell too!) >/tmp/rhosts. atxt rhost search find / -perm -2000 -exec ls -al {} ; >/tmp/2000. atxt find permissions on files find / -perm -4000 -exec ls -al {} ; >/tmp/4000. atxt find permissions on files find /etc/rc. config. d/*conf* -exec cat {} ; > rc. configd. txt >/tmp/rc. config. atxt displays the config files from /rc. config. d/ find etc/rc. config. d/*config* -exec cat {} ; > config. txt >/tmp/hp_rc. config. d. atxt #list contents of the config files find etc/rc. config. d/audit* -exec cat {} ; > config. txt >/tmp/hp_rc. audit. atxt list contents of the auditing cofig xxx ypwhich Lists name of the NIS server and nickname translation table ypcat -x Displays the contents of an NIS map. exportfs -v >/tmp/exportfs. atxt Print each directory or file name as it is exported or unexported share >/tmp/share. atxt Print each directory or file name as it is exported or unexported cat /etc/hosts. allow Lists machines that the host will accept a connection coming in from (IP address) cat /etc/hosts. deny Lists machines that the host will NOT accept a connection coming in from (IP address) find / -name snmpd. conf -exec grep -l public {} ; * omit everything to the right of “>” for output to screen find snmpd config files where default password of public may exit
Putting it all together "the usual suspects" “the usual reasons” cat /etc/rc. config. d/netconf >/tmp/netconf. atxt config values for core networking subsystems cat /etc/rc. config. d/netconf /etc/rc. config. d/auditing >> >/ tmp/rc_configd. atxt #gets the rest cat /etc/resolv. conf # defines the domain the system client will use. >/tmp/resolvconf. atxt cat /etc/uucp/Systems >/tmp/uucp_systems. atxt belongs to and the name server the “Unix-to-Unix copy”. Lists and describes remote systems accessible to a local system using the Basic Networking Utilities " cat /var/adm/inetd. sec >/tmp/inetd_sec. atxt "# The lines in the file contain a service name permission field and the Internet addresses or names of the hosts and/or networks allowed to use that service in the local machine. cat for /etc/securetty >/tmp/. atxt "file with contents “console” if exists then root can only login from console all others must remote login as themselves and then su. " find / ( -perm -0200 -o -perm -0400 ) - ls >/tmp/uid. atxt find / -name. profile - >/ tmp/x. atxt find / -name. rhost -exec cat {} ; > rhosts. txt look for setuid or guid show profile (get cshell and korn shell too!) >/tmp/rhosts. atxt rhost search find / -perm -2000 -exec ls -al {} ; >/tmp/2000. atxt find permissions on files find / -perm -4000 -exec ls -al {} ; >/tmp/4000. atxt find permissions on files find /etc/rc. config. d/*conf* -exec cat {} ; > rc. configd. txt >/tmp/rc. config. atxt displays the config files from /rc. config. d/ find etc/rc. config. d/*config* -exec cat {} ; > config. txt >/tmp/hp_rc. config. d. atxt #list contents of the config files find etc/rc. config. d/audit* -exec cat {} ; > config. txt >/tmp/hp_rc. audit. atxt list contents of the auditing cofig xxx ypwhich Lists name of the NIS server and nickname translation table ypcat -x Displays the contents of an NIS map. exportfs -v >/tmp/exportfs. atxt Print each directory or file name as it is exported or unexported share >/tmp/share. atxt Print each directory or file name as it is exported or unexported cat /etc/hosts. allow Lists machines that the host will accept a connection coming in from (IP address) cat /etc/hosts. deny Lists machines that the host will NOT accept a connection coming in from (IP address) find / -name snmpd. conf -exec grep -l public {} ; * omit everything to the right of “>” for output to screen find snmpd config files where default password of public may exit
/tmp/netstata. atxt" src="https://present5.com/presentation/645b720994a482f4782d1844abad1938/image-105.jpg" alt="Putting it all together "the usual suspects" “the usual reasons” netstat -a >/tmp/netstata. atxt" />
Putting it all together "the usual suspects" “the usual reasons” netstat -a >/tmp/netstata. atxt all sockets netstat -in >/tmp/netstatin. atxt show interface info netstat -rv >/tmp/netstatrv. atxt route table nfs configs >/tmp/x. atxt Solaris package manager Pkginfo >/tmp/pkginfo. atxt solaris look for installed packages ps -aef >/tmp/psaef. atxt show those processes ps -aux >/tmp/psaux. atxt more processes rpm -qa >installed. pkgs. txt >/tmp/rpms. atxt Linux display installed pkgs showmount -e >/tmp/ex_mntpts. atxt show exported mount points swlist -l fileset >/tmp/hp_pkgs. atxt hp look for installed pkgs tail -300 /sr/adm/sulog >/tmp/sulog. atxt last 300 lines of su log uname -a >/tmp/uname. atxt id the system rpcinfo Show rpc services running (portmapper dump) on >/tmp/x. atxt cat /etc/printcap. local This file used to specify custom edited printers ioscan list hardware config umask display current umask settings * omit everything to the right of “>” for output to screen Some useful URLs: ICAT Metabase and Secunia http: //icat. nist. gov/icat. cfm and www. secunia. com Common Vulnerabilities and Exposures http: //cve. mitre. org/ Rosetta Stone for Unix http: //bhami. com/rosetta. html RPC port info http: //www. iss. net/security_center/advice/Exploits/Ports/RPC/default. htm


