16a4c3e818b5446298d436a7b45dca84.ppt
- Количество слайдов: 71



Course Topics

Course Outline: Basic topics

Course Outline: Network Security

Course Objectives

Course Objectives

Text Books

Text Books

Text Books

Other Books

Occasional Assigned Reading

Main Themes of the Course

Main Themes of the Course

What This Course is Not About

What This Course is Not About


Peek at the Dark Side
Motivation
“Privacy and Security”


What Do You Think?

Desirable Security Properties

What Drives the Attackers?
Network Stack
Network Defenses … all defense mechanisms must work correctly and securely

Correctness versus Security

Bad News

Better News

Reading Assignment

Why study computer security?

Why study computer security?

What is cryptology?

Steganography

Cryptology and Security
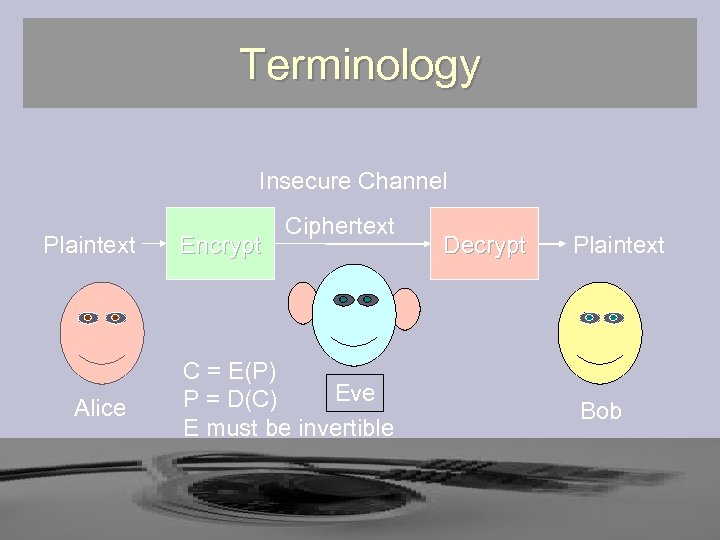
Terminology Insecure Channel Plaintext Alice Encrypt Ciphertext C = E(P) Eve P = D(C) E must be invertible Decrypt Plaintext Bob

Cryptography
Alice and Bob Plaintext Alice Encrypt Ciphertext Decrypt Plaintext Bob

Substitution Cipher If every person on earth tried one per second, it would take 5 B years.

Monoalphabetic Cipher

Frequency Analysis
Pattern Analysis

Guessing

Guessing

Guessing

Guessing

Guessing

Monoalphabetic Cipher

Why was it so easy?

How to make it harder?

Network Security

Network Layer Vulnerabilities

IP Addresses

Other IP Addresses

Junctions

Special Networks

CIDR Addresses

IP Packet

IP Spoofing

IP Spoofing with Amplification

ICMP

Basic ICMP Message Types

ICMP Echo

Scans and Recon

Smurf Attack

Other Ping Abuse

Why Do You Need Pings?

About These Slides

Questions adeel. akram@uettaxila. edu. pk
16a4c3e818b5446298d436a7b45dca84.ppt