7bc112faaac6b92f44d6d7c767b2ebf9.ppt
- Количество слайдов: 43

Cosc 4750 Networking
The basics • Machine A and Machine B have a connection to a network • When Machine A wants to “talk” to machine B, it creates a packet of information with a destination address of machine B, and sends it out into the network. • Machine B receives the packets and responds if it needs to. • In UNIX, Machine A can also send a message to itself. (localhost, IP 127. 0. 0. 1)

TCP/IP and the Internet • brief history – Not created by Microsoft or Vice President Gore – Established by DARPA in 1969 for the US Department of Defense, called ARPANET – By 1980’s it was used in research by Universities – 1994: Internet went private

Who “manages” the Internet • ICANN, The Internet Corporation for Assigned Names and Numbers: – can be said to be in charge of the internet • IETF, the Internet Engineering Task Force – Oversee development and standardization. • ISOC, the Internet Society – Membership organization that represents Internet users.

The IP address Crisis • • Class A IP, example 129. X. X. X Class B IP, example 129. 72. X. X Class C IP, example 129. 72. 216. X Where never allocated “fairly”. US government holds half the Class A IPs from 1 -126. X. X. X, many unused or badly allocated. • http: //www. caida. org/outreach/learn/ipv 4 space for more information

Ethernet • Uses CSMA/CD: – Carrier Sense: you can tell whether anyone is talking. – Multiple Access: everyone can talk – Collision Detection: you know when you interrupt someone else.

Evolution • • Year 1973 80 -93 1994 1998 2008 Speed 3 Mb/s 10 Mb/s Name media Xerox coax Ethernet coax cat 3 10 Base 2/10 Base. T 100 Mb/s 100 Base Cat 5, fiber 1 Gb/s 1000 Base fiber, Cat 5 e 1 Tb/s ? ?
Networking for your machine • Static or manual – You set the network information the machine needs. • DHCP – Your machine asks for the networking information from a Server. • BOOTP – A server give you an IP number and gateway • PPP – Dailup version of DHCP or could be static

• DHCP and bootp – Each asks a server for networking information for your machine. It is based off a mac address • a MAC address – a hard coded number that you network card has. – It is 6 segment Hex number – example: 08: 00: 20: 79: 4 F: 49
loopback interface • lo (or lo 0) is the loopback interface • It has an IP address of 127. 0. 0. 1 and name of localhost. (Don’t EVER changed this). • On a unix machine, it's active even the network card is not. Used for testing of networking applications and other things.

Using arp • arp is a program that will display know mac addresses, IP number, and machine name. • Each machine has a table of know machines, called an arp table • arp –a xor. com (192. 108. 21. 1) at 08: 00: 20: 77: 5 E: A 0 earth. xor. com (129. 108. 21. 180) at 00: 50: DA: 12: 4 E: E 5

Using ifconfig • ifconfig allows you to configure your network and look at a specific network device • ifconfig eth 0 (network card) – displays flags, IP number, netmask, broadcast, mac address, and stat’s – netmask tells the computer which IP address class you have (A, B, C). Class C: 255. 0 – broadcast, has to do with IP class. Class C: 10. 216. 218. 255 (for computer Science).

PPP and IP forwarding • When a machine makes a PPP (dial-up) connection to a server, the server then forwards on IP packets from the client into the network (internet). • Also, the client’s IP is associated with the servers mac address. • IP forwarding is for routing (dial-up and network). If your machine is not a dial-up server, it should be turned off.
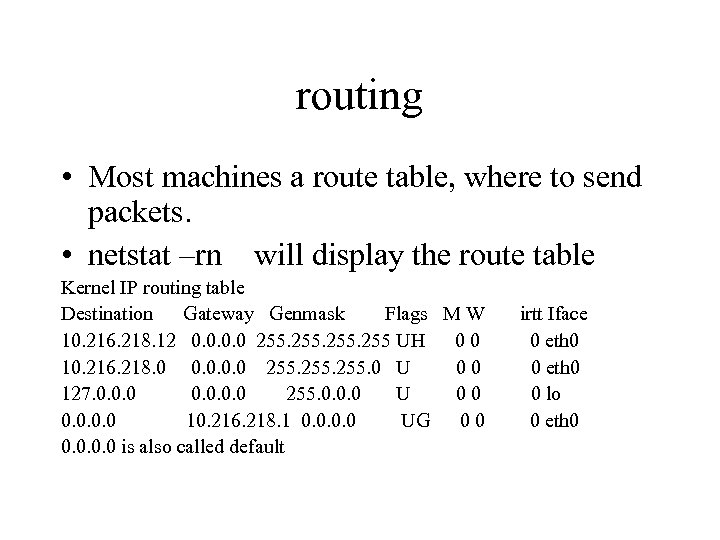
routing • Most machines a route table, where to send packets. • netstat –rn will display the route table Kernel IP routing table Destination Gateway Genmask Flags M W 10. 216. 218. 12 0. 0 255 UH 00 10. 216. 218. 0 0. 0 255. 0 U 00 127. 0. 0 255. 0. 0. 0 U 00 0. 0 10. 216. 218. 1 0. 0 UG 00 0. 0 is also called default irtt Iface 0 eth 0 0 lo 0 eth 0
Adding routes • The most common route to add to a machine is the default route. – This is the one that gets your network packets outside of IP domain • Normally to a router. • route add default 10. 216. 218. 1 – Since that is where our “router” is located.

Security • Networking is one of the most vulnerable parts of a computer for attacks. • firewalls and filters. • Basically, UNIX firewalls and filters are weak (and Microsoft’s are far worse). • firewalls allow you block network traffic to a machine (or set of machines) • filtering allows you block a set of IPs or only allow a set of IPs into your machine.

• For true hardware firewalls and filters, buy a dedicated router or switch (probably from CISCO, current leader network hardware, 70% of the market, but there are other very good vendors [and cheaper] as well. ). • Denial of Service and various other attacks can be blocked by routers/switches and IDSs, but not by a UNIX machine • Why? The computer is spending time to deal with the problem, instead of normal work. – We will return to security later on.

Cosc 4750 Networking commands

More Networking commands • hostname – allows you to determined the name of the machine • nslookup <name> Or nslookup IP number – Determine an IP for a given name or a name for a given IP number – More later with DNS

• finger <username> – check to see if they are logined • finger – check to who is logged to the machine • finger <user>@machine or finger @machine – See who is logged in or if a given user is logged into a remote machine

• tcpdump, must be run as root – prints out the packets received by an interface (network card) • ping <machine> or ping –c # machine – Allows to check to see if a machine is alive – And check to see if your networking is working – -c is how many packets to send/receive before stopping
• traceroute <machine> – Displays all immediate steps between your machine and a remote machine – Good way to find out where the network broken down between you and a remote machine – Also useful in tracking an IP address
• telnet <machine> <port> – connect to a remote machine, if port is left off, then the default is port 23, which is for telnet logins • rlogin <machine> – login to a remote machine, with the current username (-l <username> to specify another username) – normally some environment variables are “carried” to the remote machine. – Must use a password (unless. rhost file)

• . rhosts file – a listing of machines that a user can rlogin (rcp and rsh) from with using a password. A security problem. – Example of the file meru. cs. uwyo. edu seker k 2. cs. uwyo. edu seker asdf. cs. uwyo. edu bob

• rcp (remote copy), normally need a. rhosts file for it work. – rcp <file> <machine: path> – rcp test meru: /meru 3/seker/. • rsh (remote shell), will work without a. rhosts file. – rsh meru ls display the my directory on meru – rsh meru xterm –display k 2. cs. uwyo. edu: 0. 0

• xhost + <host> – xhost is one way in which you allow a remote machine to display (access) “console” – For the preceeding rsh meru xterm command – xhost + meru is needed in order for meru to display an xterm window on my console (display). – xhost + (with a machine) allows any remote host to access your console. Very insecure.

• All the r commands are considered insecure and should be avoided. – rsh, rlogin, rcp, etc. – Instead you want to use a secure problem

• ssh (secure shell) is replace program for rlogin and rsh. Provides encrypted communication between two untrusted hosts over an insecure network. (from the man pages) – ssh meru Will create a secure connection between my machine and meru – see the man pages (man ssh) for more information

• Use ssh instead of rsh – ssh <host> command • Use scp instead of rcp • And sshd will accept secure ftp connections – use sftp instead of ftp

Why use the S programs? • ssh creates a secure connections – passwords are not passed between machines in clear text, instead they are encrypted • Since the connection is encrypted, packet sniffers and other similar devices can “see” what you are doing. • Offers machine better security. – Xhost + for example, allows ANYONE to “view” your screen and could capture keystrokes.
More on netstat • netstat –a displays all active TCP and UDP ports • netstat –i displays each interface and stat’s • netstat –i –c display continuing stat’s • netstat –rn displays the route tables • netstat –s displays stat’s for each section: IP, ICMP, TCP, and UDP

Packet Sniffers • Listen to the traffic on the network, record and/or print packets with certain criteria – Changes the network card to "promiscuous mode", so that it can intercept all the network packets. – tcpdump is installed on most linux machines and is a packet sniffer, command line – Ethereal, use a GUI interface and allows a point and click • see the man pages for use of these programs.

Packet Sniffers (2) • There a lot of packet sniffer packages available. – They should be used with caution, since you are bordering on hacking, as well as intercepting "private" information.
SNMP • The Simple Network Management Protocol • Can be used for gathering stat’s and managing network hardware • Some applications that been created with SNMP protocol – mrtg, multi-router traffic grapher • demo in class • perl also has several modules for snmp.

Iptables • How the firewall treats packets leaving, entering, or passing through your computer. There is a chain for each of these. – Any packet entering your computer goes through the INPUT chain. – Any packet that your computer sends out to the network goes through the OUTPUT chain. – Any packet that your computer picks up on one network and sends to another goes through the FORWARD chain. • The chains are half of the logic behind iptables themselves.
Iptables (2) • Iptables can be configured through the command iptables – And configured on startup from /etc/sysconfig/iptables • The basics – You specify based on a number of different attributes whether a packet should be accepted or dropped for each chain. • You can drop an incoming packet from one packet, but allow an outbound packet to it.
Iptables (3) • Examples: • Iptables –A INPUT -s 200. 1 -j DROP – Drop any input bound packet from ip number 200. 1 – Still allows outbound packets to that ip.
![Iptables (4) • -p [protocol] – tcp, udp, icmp, or all • -s IPaddress[/mask] Iptables (4) • -p [protocol] – tcp, udp, icmp, or all • -s IPaddress[/mask]](https://present5.com/presentation/7bc112faaac6b92f44d6d7c767b2ebf9/image-38.jpg)
Iptables (4) • -p [protocol] – tcp, udp, icmp, or all • -s IPaddress[/mask] – Source IP address or part with a mask, like 129. 72. 0. 0/16 • -d Ipaddress[/mask] – Destination IP addresss or part with mask. • -i name network interface name packet received on • -o name network interface name packet send out on • --dportnumber – used with –p and others to specify a port number.
Iptables (5) • Other commands • -A INPUT -m state –state RELATED, ESTABLISHED –j ACCEPT – Allows processes already talking to establish new connections • iptables –P INPUT drop – The default is to drop packets on the input chain. • There are many more.
![iptables example *filter : INPUT DROP [0: 0] : FORWARD DROP [0: 0] : iptables example *filter : INPUT DROP [0: 0] : FORWARD DROP [0: 0] :](https://present5.com/presentation/7bc112faaac6b92f44d6d7c767b2ebf9/image-40.jpg)
iptables example *filter : INPUT DROP [0: 0] : FORWARD DROP [0: 0] : OUTPUT ACCEPT [0: 0] -A INPUT –I lo –j ACCEPT -A INPUT -s 10. 10. 1 -i eth 0 -j ACCEPT -A INPUT -p tcp -m tcp --dport 22 -j ACCEPT -A INPUT –s 10. 82. 0. 0/16 -p tcp -m tcp --dport 80 -j ACCEPT -A INPUT -m state --state RELATED, ESTABLISHED -j ACCEPT -A OUTPUT -o lo -j ACCEPT -A OUTPUT -o eth 0 -j ACCEPT COMMIT
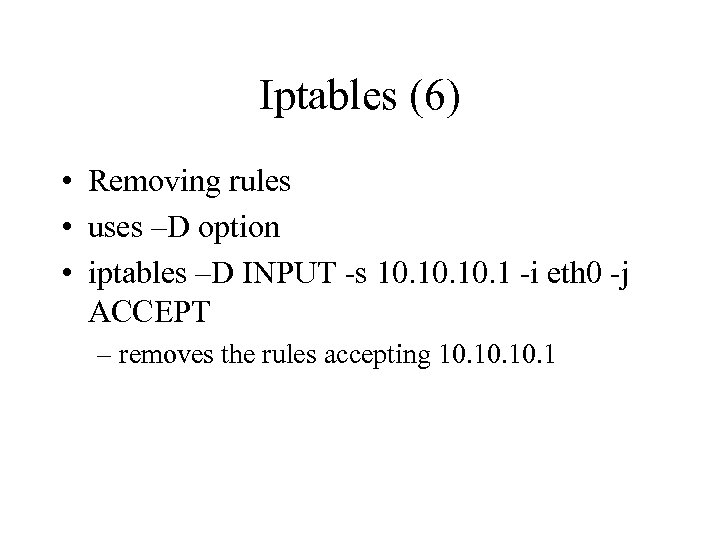
Iptables (6) • Removing rules • uses –D option • iptables –D INPUT -s 10. 10. 1 -i eth 0 -j ACCEPT – removes the rules accepting 10. 10. 1

iptables conclusion • This covers only the basics of iptables – This should be enough to get you started with a good set of rules. • You can create more chains and more rules. • I didn’t cover all the options • Find a good site or book that covers more detail and explanations.

Q&A
7bc112faaac6b92f44d6d7c767b2ebf9.ppt