6a722e6f88b3eab5eaf33a68490d8d70.ppt
- Количество слайдов: 15
 Corso referenti S. I. R. A. – Modulo 2 Local Security 20/11 – 27/11 – 05/12 11/12 – 13/12 (gruppo 1) 12/12 – 15/12 (gruppo 2) Cristiano Gentili, Massimiliano Viola (CSIA)
Corso referenti S. I. R. A. – Modulo 2 Local Security 20/11 – 27/11 – 05/12 11/12 – 13/12 (gruppo 1) 12/12 – 15/12 (gruppo 2) Cristiano Gentili, Massimiliano Viola (CSIA)
 Overview Securing Desktops and Services by Using Security Policies Auditing Access to System Resources
Overview Securing Desktops and Services by Using Security Policies Auditing Access to System Resources
 Securing Desktops and Services by Using Security Policies Implementing Security Policies Modifying Security Settings Using Predefined Security Templates Creating Custom Security Templates Analyzing Security Configuring and Analyzing Security from a Command Line
Securing Desktops and Services by Using Security Policies Implementing Security Policies Modifying Security Settings Using Predefined Security Templates Creating Custom Security Templates Analyzing Security Configuring and Analyzing Security from a Command Line
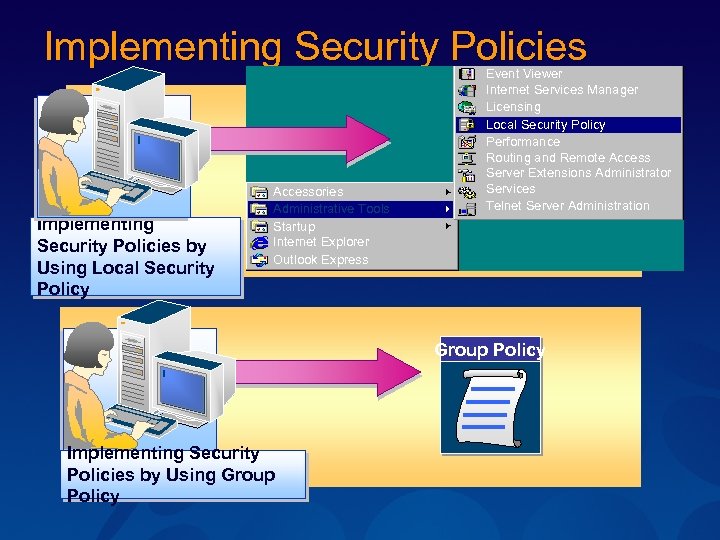 Implementing Security Policies by Using Local Security Policy Accessories Administrative Tools Startup Internet Explorer Outlook Express Event Viewer Internet Services Manager Licensing Local Security Policy Performance Routing and Remote Access Server Extensions Administrator Services Telnet Server Administration Group Policy Implementing Security Policies by Using Group Policy
Implementing Security Policies by Using Local Security Policy Accessories Administrative Tools Startup Internet Explorer Outlook Express Event Viewer Internet Services Manager Licensing Local Security Policy Performance Routing and Remote Access Server Extensions Administrator Services Telnet Server Administration Group Policy Implementing Security Policies by Using Group Policy
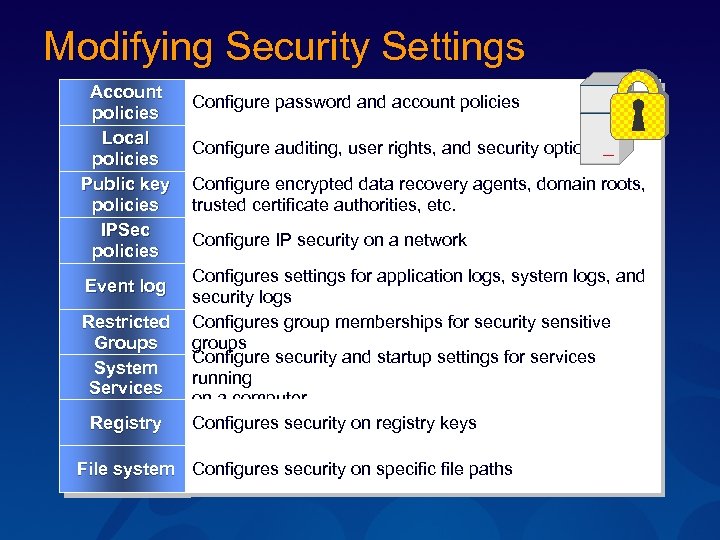 Modifying Security Settings Account policies Local policies Public key policies IPSec policies Configure password and account policies Configure auditing, user rights, and security options Configure encrypted data recovery agents, domain roots, trusted certificate authorities, etc. Configure IP security on a network Configures settings for application logs, system logs, and security logs Restricted Configures group memberships for security sensitive Groups groups Configure security and startup settings for services System running Services on a computer Registry Configures security on registry keys Event log File system Configures security on specific file paths
Modifying Security Settings Account policies Local policies Public key policies IPSec policies Configure password and account policies Configure auditing, user rights, and security options Configure encrypted data recovery agents, domain roots, trusted certificate authorities, etc. Configure IP security on a network Configures settings for application logs, system logs, and security logs Restricted Configures group memberships for security sensitive Groups groups Configure security and startup settings for services System running Services on a computer Registry Configures security on registry keys Event log File system Configures security on specific file paths
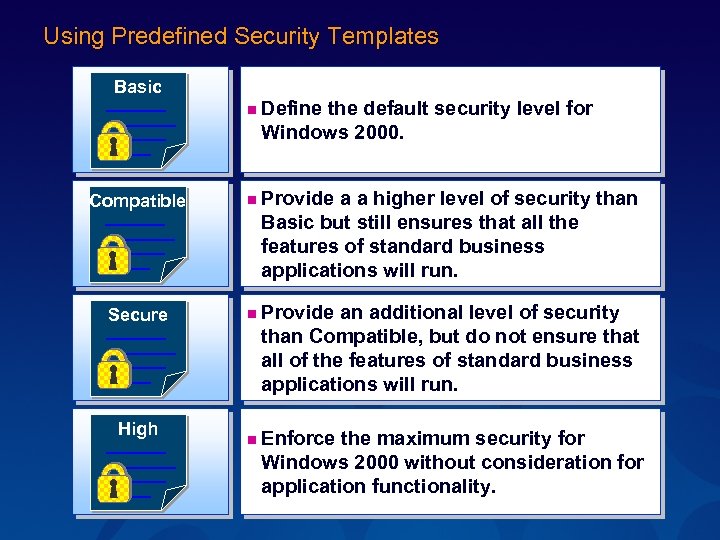 Using Predefined Security Templates Basic n Define the default security level for Windows 2000. Compatible Secure High n Provide a a higher level of security than Basic but still ensures that all the features of standard business applications will run. n Provide an additional level of security than Compatible, but do not ensure that all of the features of standard business applications will run. n Enforce the maximum security for Windows 2000 without consideration for application functionality.
Using Predefined Security Templates Basic n Define the default security level for Windows 2000. Compatible Secure High n Provide a a higher level of security than Basic but still ensures that all the features of standard business applications will run. n Provide an additional level of security than Compatible, but do not ensure that all of the features of standard business applications will run. n Enforce the maximum security for Windows 2000 without consideration for application functionality.
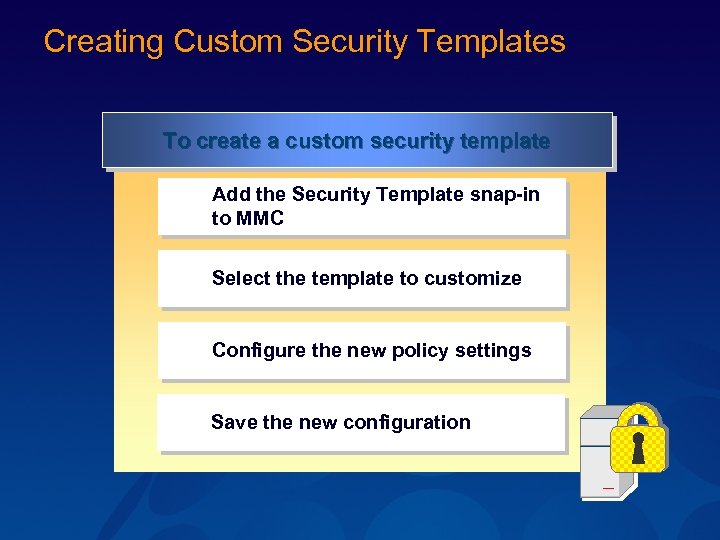 Creating Custom Security Templates To create a custom security template Add the Security Template snap-in to MMC Select the template to customize Configure the new policy settings Save the new configuration
Creating Custom Security Templates To create a custom security template Add the Security Template snap-in to MMC Select the template to customize Configure the new policy settings Save the new configuration
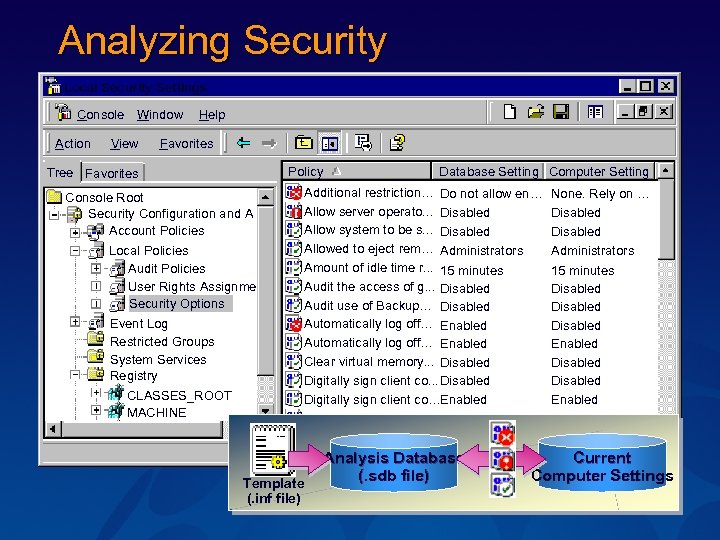 Analyzing Security Local Security Settings Console Window Action View Help Favorites Policy Tree Favorites Console Root Security Configuration and A Account Policies Local Policies Audit Policies User Rights Assignme Security Options Event Log Restricted Groups System Services Registry CLASSES_ROOT MACHINE Database Setting Computer Setting Additional restriction… Do not allow en… Allow server operato. . . Disabled Allow system to be s. . . Disabled Allowed to eject rem… Administrators Amount of idle time r. . . 15 minutes Audit the access of g. . . Disabled Audit use of Backup… Disabled Automatically log off… Enabled Clear virtual memory. . . Disabled Digitally sign client co…Enabled Template (. inf file) Analysis Database (. sdb file) None. Rely on … Disabled Administrators 15 minutes Disabled Enabled Disabled Enabled Current Computer Settings
Analyzing Security Local Security Settings Console Window Action View Help Favorites Policy Tree Favorites Console Root Security Configuration and A Account Policies Local Policies Audit Policies User Rights Assignme Security Options Event Log Restricted Groups System Services Registry CLASSES_ROOT MACHINE Database Setting Computer Setting Additional restriction… Do not allow en… Allow server operato. . . Disabled Allow system to be s. . . Disabled Allowed to eject rem… Administrators Amount of idle time r. . . 15 minutes Audit the access of g. . . Disabled Audit use of Backup… Disabled Automatically log off… Enabled Clear virtual memory. . . Disabled Digitally sign client co…Enabled Template (. inf file) Analysis Database (. sdb file) None. Rely on … Disabled Administrators 15 minutes Disabled Enabled Disabled Enabled Current Computer Settings
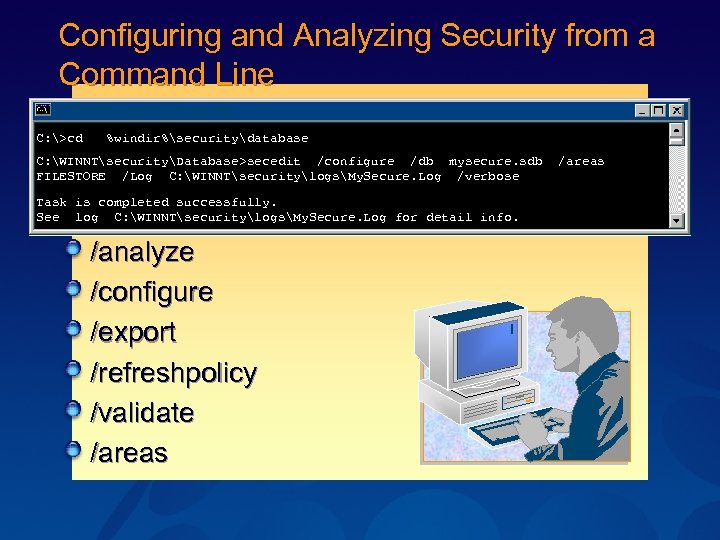 Configuring and Analyzing Security from a Command Line C: WINNTSystem 32cmd. exe C: >cd %windir%securitydatabase C: WINNTsecurityDatabase>secedit /configure /db mysecure. sdb FILESTORE /Log C: WINNTsecuritylogsMy. Secure. Log /verbose Task is completed successfully. See log C: WINNTsecuritylogsMy. Secure. Log for detail info. /analyze /configure /export /refreshpolicy /validate /areas FILESTORE
Configuring and Analyzing Security from a Command Line C: WINNTSystem 32cmd. exe C: >cd %windir%securitydatabase C: WINNTsecurityDatabase>secedit /configure /db mysecure. sdb FILESTORE /Log C: WINNTsecuritylogsMy. Secure. Log /verbose Task is completed successfully. See log C: WINNTsecuritylogsMy. Secure. Log for detail info. /analyze /configure /export /refreshpolicy /validate /areas FILESTORE
 Auditing Access to System Resources Introduction to Auditing Selecting Events to Audit Planning an Audit Policy Setting Up an Audit Policy Auditing Access to Resources
Auditing Access to System Resources Introduction to Auditing Selecting Events to Audit Planning an Audit Policy Setting Up an Audit Policy Auditing Access to Resources
 Introduction to Auditing Use of Resourc es Success or Failure Logged Event Viewer User 1 logon failed Access denied Printing successful Auditing Tracks User and Operating System Activities Audit Entries Contain Actions Performed, Users Who Performed the Actions, and Success or Failure of the Events Audit Policy Defines the Types of Security Events That Windows 2000 Records You Set Up an Audit Policy to Track Success or Failure of Events, Identify Unauthorized Use of Resources, and Maintain a Record Activity You View Security Logs in Event Viewer
Introduction to Auditing Use of Resourc es Success or Failure Logged Event Viewer User 1 logon failed Access denied Printing successful Auditing Tracks User and Operating System Activities Audit Entries Contain Actions Performed, Users Who Performed the Actions, and Success or Failure of the Events Audit Policy Defines the Types of Security Events That Windows 2000 Records You Set Up an Audit Policy to Track Success or Failure of Events, Identify Unauthorized Use of Resources, and Maintain a Record Activity You View Security Logs in Event Viewer
 Selecting Events to Audit Event Example Domain controller receives a request to validate a user Account logon account Administrator creates, changes, or deletes a user account management or group Directory User gains access to an Active Directory object service access User logs on or off a local computer Logon Object access User gains access to a file, folder, or printer Change is made to the user security options, user rights, or Policy change Audit policies Privilege use User exercises a right, such taking ownership of a file Process tracking Application performs an action System User restarts or shuts down the computer
Selecting Events to Audit Event Example Domain controller receives a request to validate a user Account logon account Administrator creates, changes, or deletes a user account management or group Directory User gains access to an Active Directory object service access User logs on or off a local computer Logon Object access User gains access to a file, folder, or printer Change is made to the user security options, user rights, or Policy change Audit policies Privilege use User exercises a right, such taking ownership of a file Process tracking Application performs an action System User restarts or shuts down the computer
 Planning an Audit Policy Determine the Computers on Which to Set Up Auditing Determine Which Events to Audit Determine Whether to Audit the Success or Failure of Even Both Determine Whether You Need to Track Trends Review Security Logs Frequently
Planning an Audit Policy Determine the Computers on Which to Set Up Auditing Determine Which Events to Audit Determine Whether to Audit the Success or Failure of Even Both Determine Whether You Need to Track Trends Review Security Logs Frequently
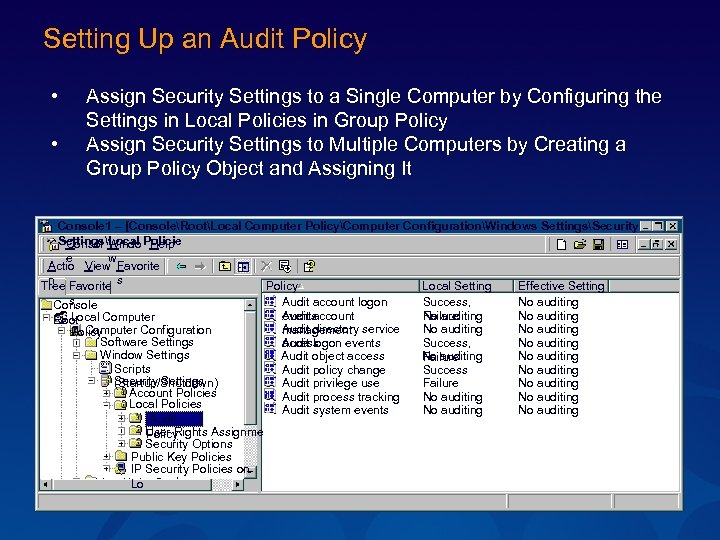 Setting Up an Audit Policy • • Assign Security Settings to a Single Computer by Configuring the Settings in Local Policies in Group Policy Assign Security Settings to Multiple Computers by Creating a Group Policy Object and Assigning It Console 1 – [ConsoleRootLocal Computer PolicyComputer ConfigurationWindows SettingsSecurity SettingsLocal Policie Consol Windo Help e w Actio View Favorite n Policy Local Setting Effective Setting Tree Favorite s s Console Local Computer Root Computer Configuration Policy Software Settings Window Settings Scripts Security Settings (Startup/Shutdown) Account Policies Local Policies Audit User Rights Assignme Policy Security Options Public Key Policies IP Security Policies on Lo Audit account logon Audit account events Audit directory service management Audit logon events access Audit object access Audit policy change Audit privilege use Audit process tracking Audit system events Success, No auditing Failure No auditing Success, No auditing Failure Success Failure No auditing No auditing No auditing
Setting Up an Audit Policy • • Assign Security Settings to a Single Computer by Configuring the Settings in Local Policies in Group Policy Assign Security Settings to Multiple Computers by Creating a Group Policy Object and Assigning It Console 1 – [ConsoleRootLocal Computer PolicyComputer ConfigurationWindows SettingsSecurity SettingsLocal Policie Consol Windo Help e w Actio View Favorite n Policy Local Setting Effective Setting Tree Favorite s s Console Local Computer Root Computer Configuration Policy Software Settings Window Settings Scripts Security Settings (Startup/Shutdown) Account Policies Local Policies Audit User Rights Assignme Policy Security Options Public Key Policies IP Security Policies on Lo Audit account logon Audit account events Audit directory service management Audit logon events access Audit object access Audit policy change Audit privilege use Audit process tracking Audit system events Success, No auditing Failure No auditing Success, No auditing Failure Success Failure No auditing No auditing No auditing
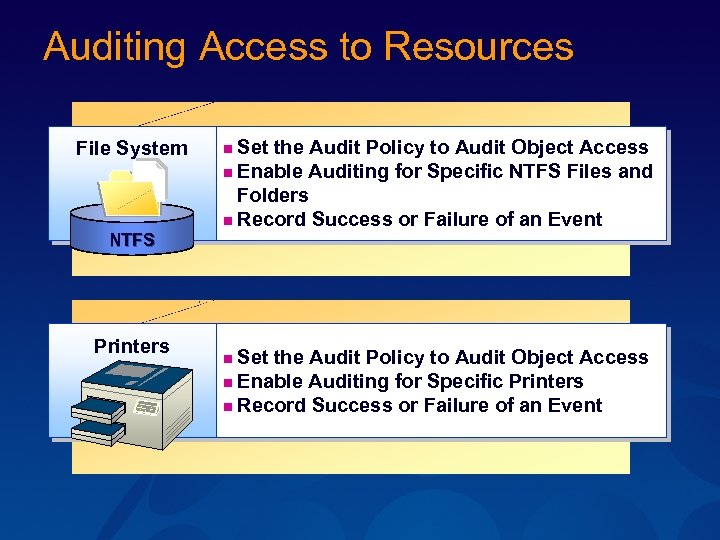 Auditing Access to Resources File System n Set the Audit Policy to Audit Object Access n Enable Auditing for Specific NTFS Files and NTFS Printers Folders n Record Success or Failure of an Event n Set the Audit Policy to Audit Object Access n Enable Auditing for Specific Printers n Record Success or Failure of an Event
Auditing Access to Resources File System n Set the Audit Policy to Audit Object Access n Enable Auditing for Specific NTFS Files and NTFS Printers Folders n Record Success or Failure of an Event n Set the Audit Policy to Audit Object Access n Enable Auditing for Specific Printers n Record Success or Failure of an Event


