a37c650db06abdd8f067e2a6aba2bc71.ppt
- Количество слайдов: 26

Controlling Collaborative Systems -Srinivas Krishnan Dept of Computer Science UNC-Chapel Hill
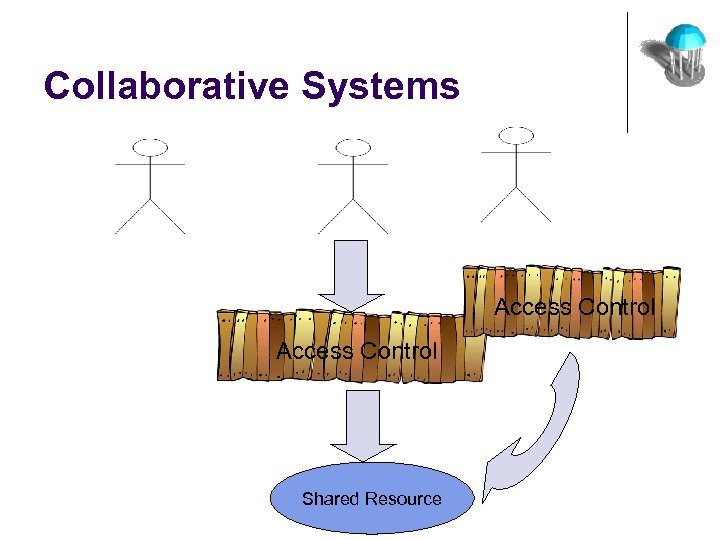
Collaborative Systems Access Control Shared Resource

Requirements for Access Control Systems l l The access control operations must be idempotent Scalability: l l Need to support N-users, as well as distributed resources Preferred Goals l l Transparency Ease of Administration
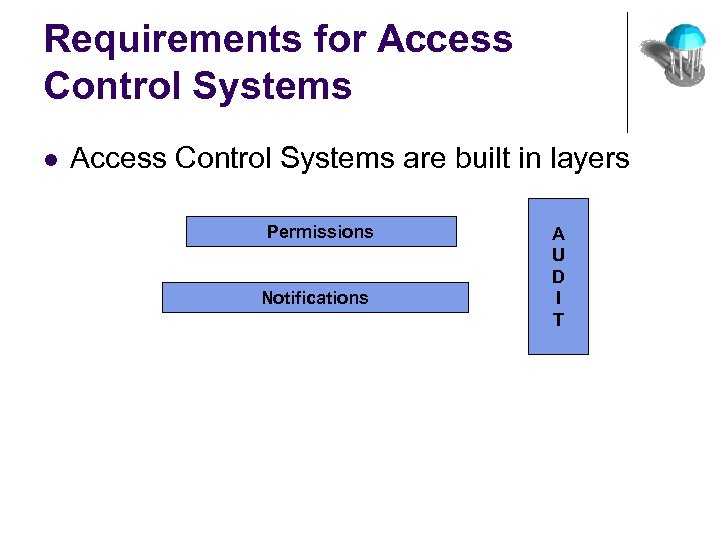
Requirements for Access Control Systems l Access Control Systems are built in layers Permissions Notifications A U D I T
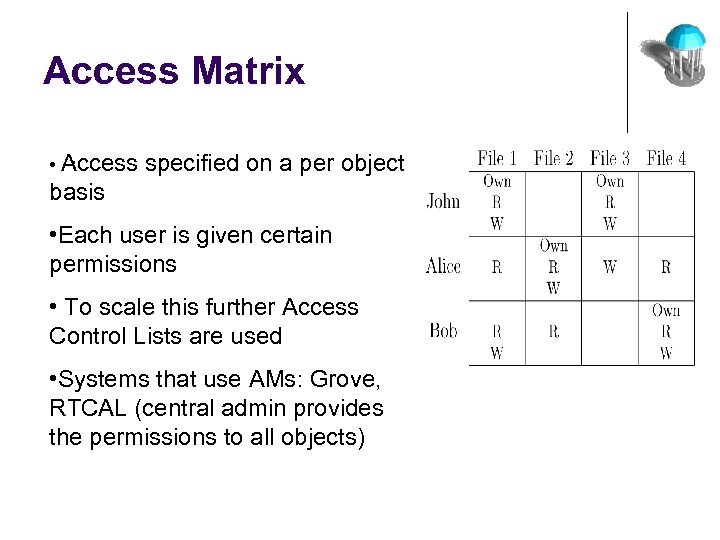
Access Matrix. • Access specified on a per object basis • Each user is given certain permissions • To scale this further Access Control Lists are used • Systems that use AMs: Grove, RTCAL (central admin provides the permissions to all objects)
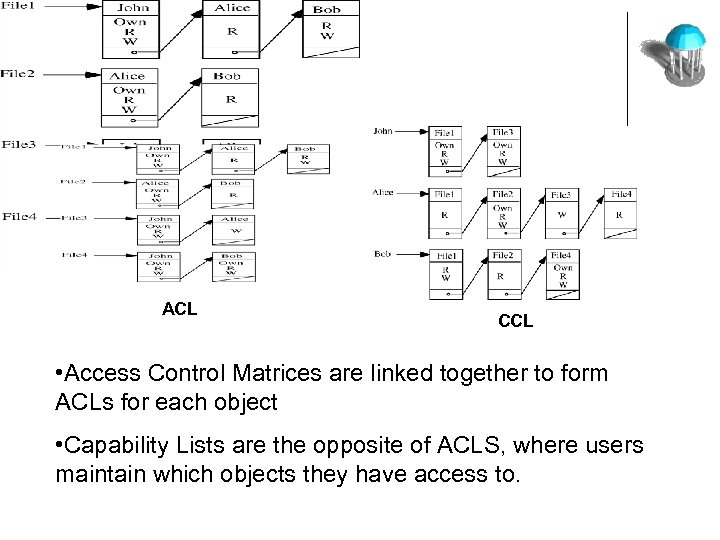
ACL and CCL ACL CCL • Access Control Matrices are linked together to form ACLs for each object • Capability Lists are the opposite of ACLS, where users maintain which objects they have access to.

Pros and Cons of ACLs l l l Easy to implement and maintain Dynamic changing of rights hard Needs knowledge of each users needs before hand. l l Not always possible in a collaborative environment Also each user/object needs to be explicitly given permissions
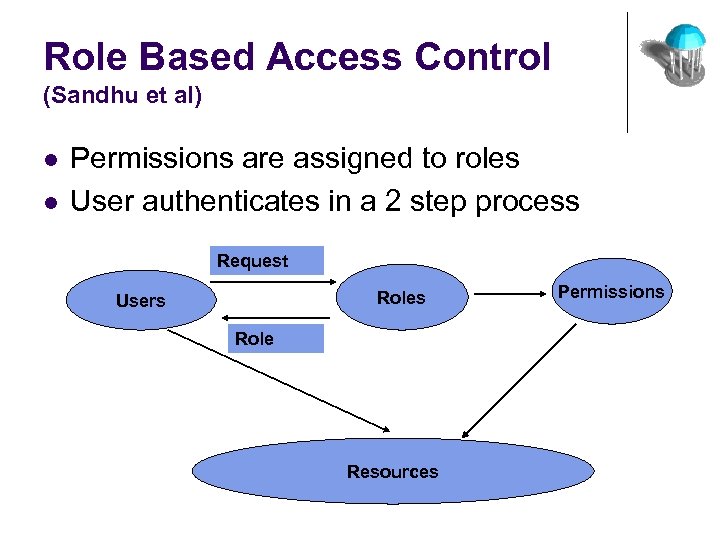
Role Based Access Control (Sandhu et al) l l Permissions are assigned to roles User authenticates in a 2 step process Request Roles Users Role Resources Permissions

RBAC (cont) l Notion of a session l l l Bound to a single user accessing the resource and the roles he needs Needs a policy in place generic enough to accommodate all accesses Did not allow for migration of roles within a single session
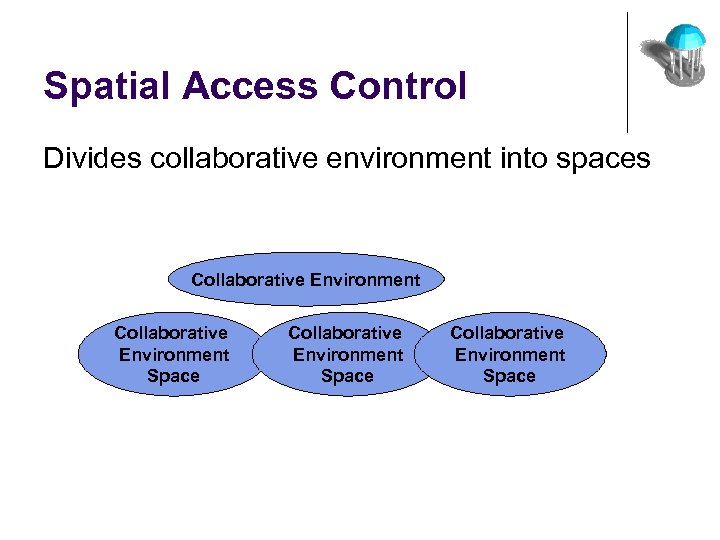
Spatial Access Control Divides collaborative environment into spaces Collaborative Environment Space
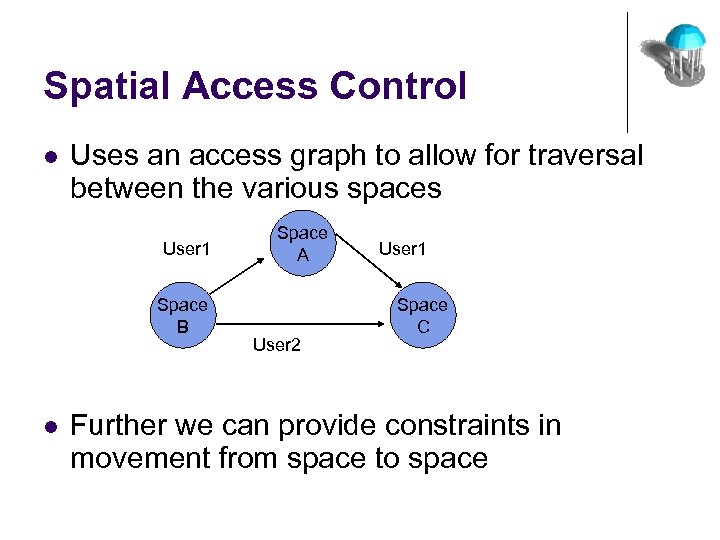
Spatial Access Control l Uses an access graph to allow for traversal between the various spaces User 1 Space B l Space A User 2 User 1 Space C Further we can provide constraints in movement from space to space
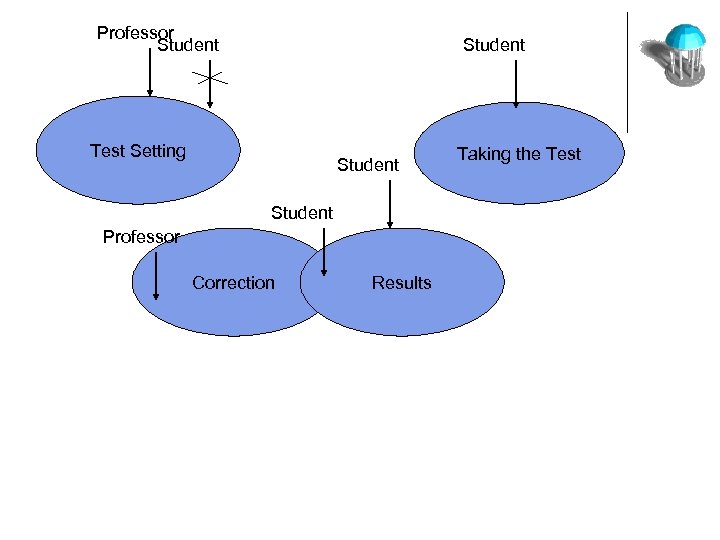
Professor Student Test Setting Student Professor Correction Results Taking the Test
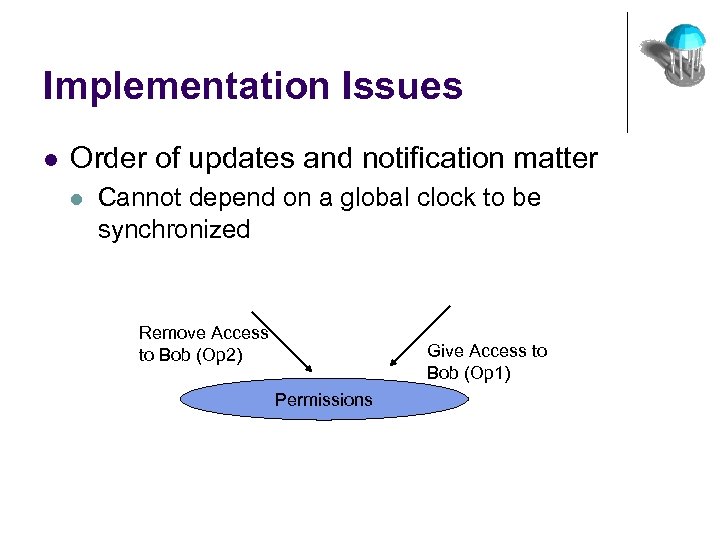
Implementation Issues l Order of updates and notification matter l Cannot depend on a global clock to be synchronized Remove Access to Bob (Op 2) Give Access to Bob (Op 1) Permissions
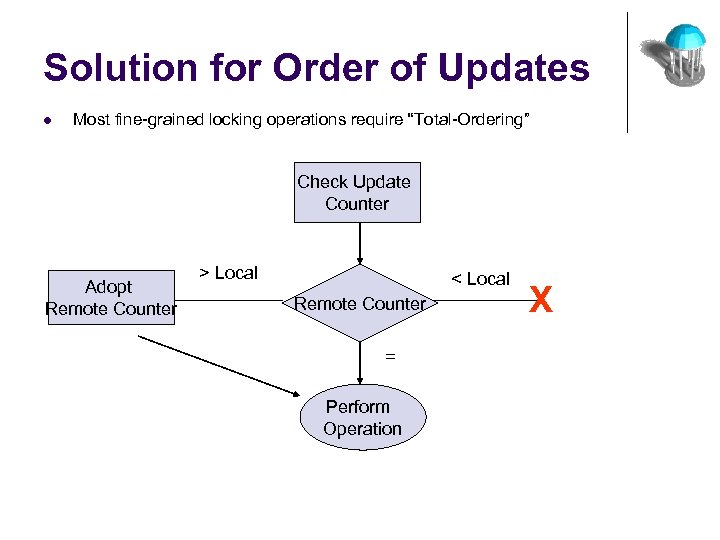
Solution for Order of Updates l Most fine-grained locking operations require “Total-Ordering” Check Update Counter Adopt Remote Counter > Local < Local Remote Counter = Perform Operation X

Fine-Grained Access Control l Traditional Modes do not scale too well for Nusers needing dynamic rights Fast provision of permissions Optimistic Locks and Access Control can provide native performance
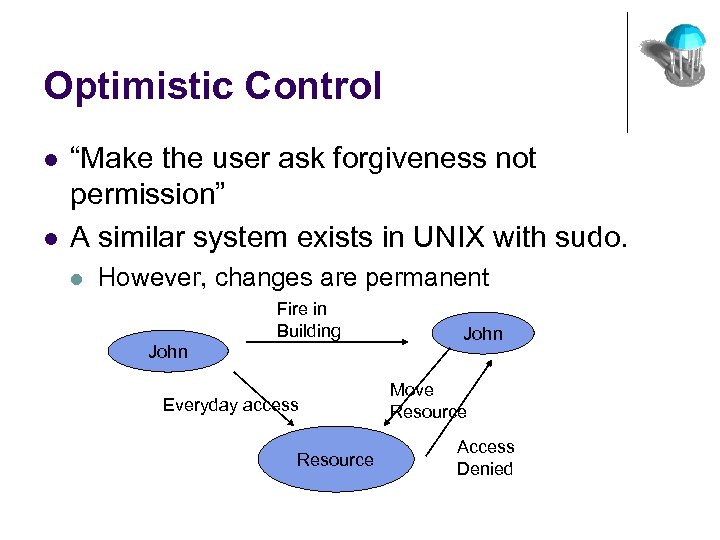
Optimistic Control l l “Make the user ask forgiveness not permission” A similar system exists in UNIX with sudo. l However, changes are permanent Fire in Building John Everyday access Resource John Move Resource Access Denied
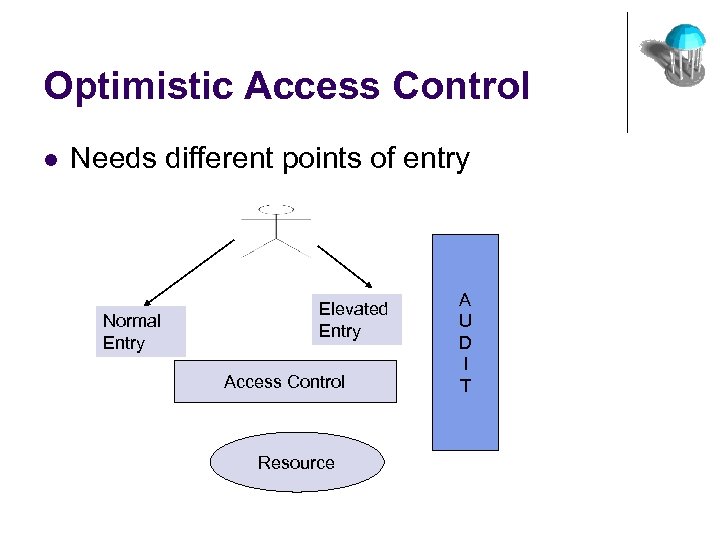
Optimistic Access Control l Needs different points of entry Normal Entry Elevated Entry Access Control Resource A U D I T
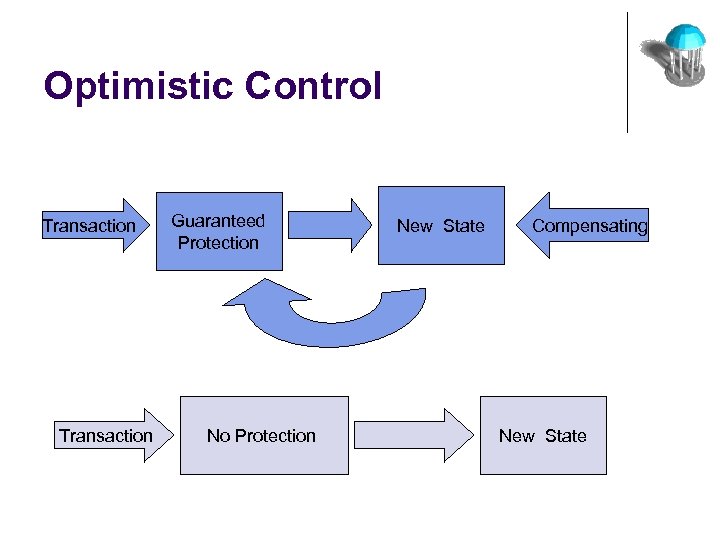
Optimistic Control Transaction Guaranteed Protection No Protection New State Compensating New State
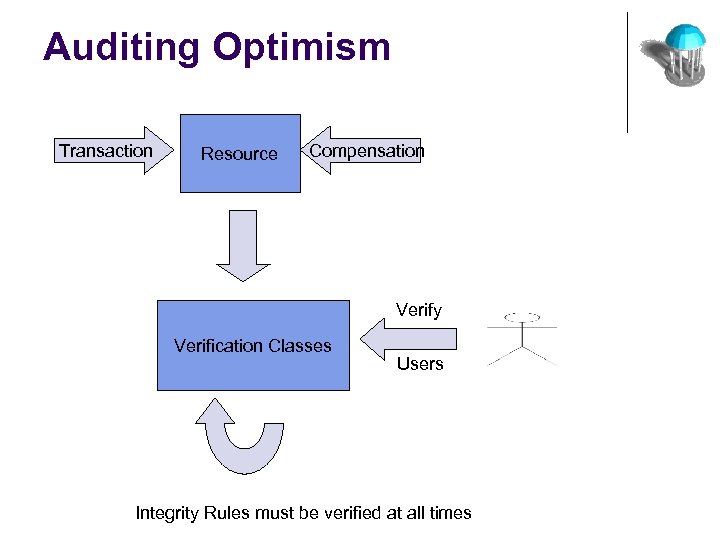
Auditing Optimism Transaction Resource Compensation Verify Verification Classes Users Integrity Rules must be verified at all times
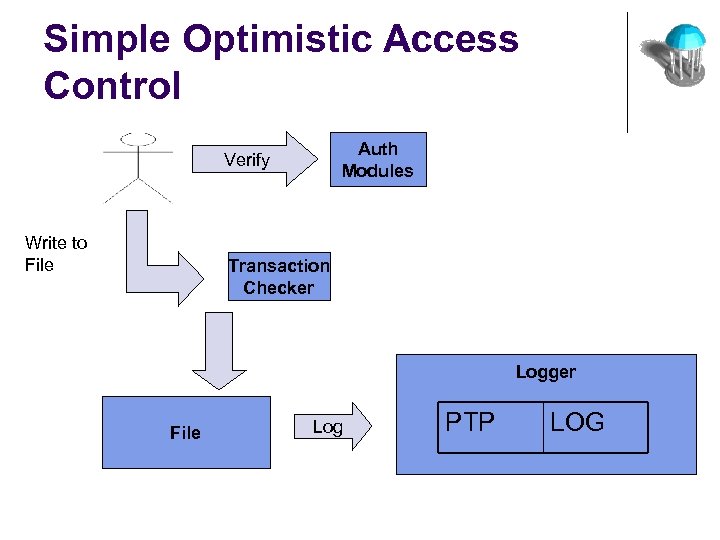
Simple Optimistic Access Control Auth Modules Verify Write to File Transaction Checker Logger File Log PTP LOG

Case-Study: P 2 P Collaborative Systems l MOTION: Provides Access Control in a P 2 P environment l No Centralized Access Control l Scalability: l l N-Users N-Auth Modules Dynamic Entry & Exit of Users Role Based Access Control l l L 1 peer & L 2 peer L 1 peers protect resources
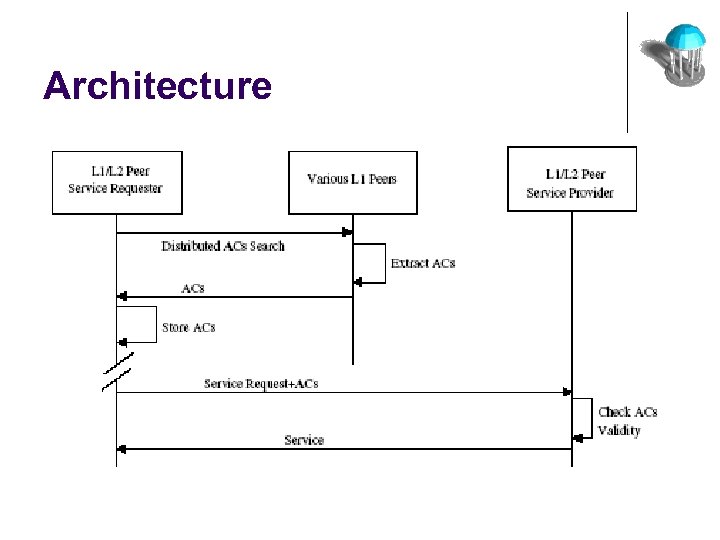
Architecture
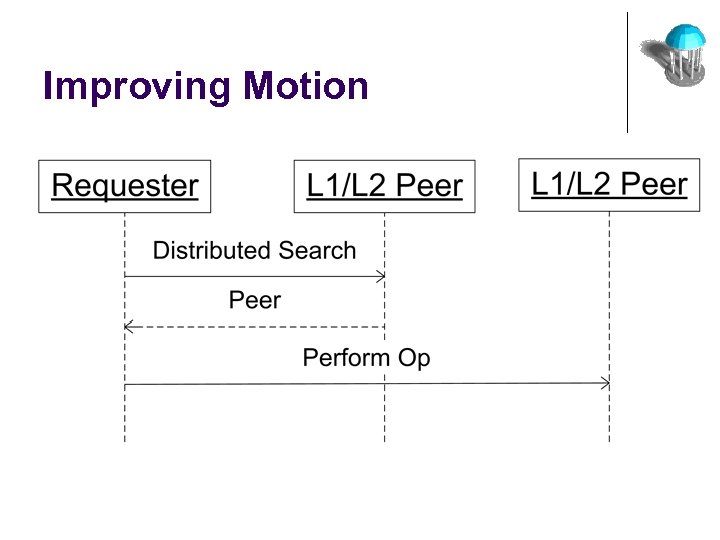
Improving Motion

Summary l l l Access Control essential for maintaining a secure Collaborative Environment Access Control can introduce lag and degrade a user’s experience Optimistic Access Control algorithms can be used to allow user’s to experience native performance

References: l l l Tolone, W. , Ahn, G. , Pai, T. , and Hong, S. 2005. Access control in collaborative systems. ACM Comput. Surv. 37, 1 (Mar. 2005), 29 -41. Povey, D. 2000. Optimistic security: a new access control paradigm. In Proceedings of the 1999 Workshop on New Security Paradigms (Caledon Hills, Ontario, Canada, September 22 - 24, 1999). NSPW '99. ACM Press, New York, NY, 40 -45. Chengzheng Sun, "Optional and Responsive Fine-Grain Locking in Internet. Based Collaborative Systems, " IEEE Transactions on Parallel and Distributed Systems , vol. 13, no. 9, pp. 994 -1008, September, 2002. Fenkam, P. ; Dustdar, S. ; Kirda, E. ; Reif, G. ; Gall, H. , "Towards an access control system for mobile peer-to-peer collaborative environments, " Enabling Technologies: Infrastructure for Collaborative Enterprises, 2002. WET ICE 2002. Proceedings. Eleventh IEEE International Workshops on , vol. , no. pp. 95 - 100, 2002 Strom, R. ; Banavar, G. ; Miller, K. ; Prakash, A. ; Ward, M. , "Concurrency control and view notification algorithms for collaborative replicated objects, " Computers, IEEE Transactions on , vol. 47, no. 4 pp. 458 -471, Apr 1998

Questions ?
a37c650db06abdd8f067e2a6aba2bc71.ppt