2097f7bf56c99a66bf86f8fa3fba4a0b.ppt
- Количество слайдов: 38

Control Systems Under Attack !!? …about the Need for Industrial Cyber-Security Dr. Stefan Lüders (CERN IT/CO) 5ème Journées Informatiques de l’IN 2 P 3 et du DAPNIA September 20 th 2006
Dr. Stefan Lüders (CERN IT/CO) ― 5ème Journées Informatiques de l’IN 2 P 3 et du DAPNIA ― September 20 th 2006
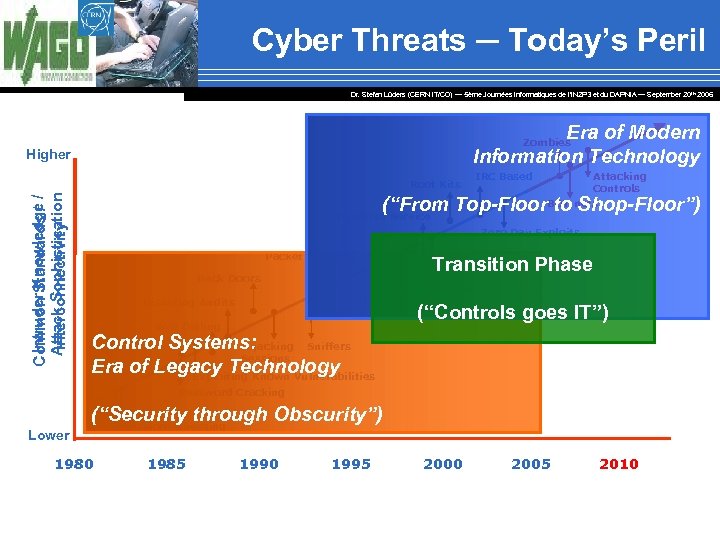
Cyber Threats ─ Today’s Peril Dr. Stefan Lüders (CERN IT/CO) ― 5ème Journées Informatiques de l’IN 2 P 3 et du DAPNIA ― September 20 th 2006 Era of Modern Information Technology Zombies Higher Intruder Knowledge Common Standards / / Attack Sophistication Interconnectivity Root Kits IRC Based Attacking Controls BOT nets (“From Top-Floor to Shop-Floor”) Denial of Service Zero Day Exploits Packet Spoofing Back Doors Disabling Audits Transition Phase Worms Automated Probes/Scans Viruses (“Controls goes IT”) War Dialing Control Systems: Hijacking Sniffers Sessions Era of Legacy Technology Exploiting Known Vulnerabilities Password Cracking Lower (“Security through Obscurity”) Password Guessing 1980 1985 1990 1995 2000 2005 2010

Controls Goes IT Dr. Stefan Lüders (CERN IT/CO) ― 5ème Journées Informatiques de l’IN 2 P 3 et du DAPNIA ― September 20 th 2006 Controls networks mate campus / business networks ► ► Proprietary field busses replaced by Ethernet & TCP/IP Field devices connect to Ethernet & TCP/IP Real time applications based on TCP/IP VPN connections from the outside onto the controls network Use of IT protocols & gadgets ► ► SNMP, SMTP, FTP, Telnet, HTTP (WWW), … Wireless LAN, notebooks, USB sticks, webcams, … Migration to the Microsoft Windows platform ► ► MS Windows not designed for industrial / control systems OPC/DCOM runs on port 135 (heavily used for RPC)

Threats due to Technique Dr. Stefan Lüders (CERN IT/CO) ― 5ème Journées Informatiques de l’IN 2 P 3 et du DAPNIA ― September 20 th 2006 Poorly secured systems are being targeted ► ► Unpatched systems, OS & applications Missing anti-virus software or old virus signature files No firewall protection Worms are spreading within seconds Zero Day Exploits: security holes without patches ► Break-ins occur before patch and/or anti-virus signature available …but how to patch/update control / engineering PCs ? …what about anti-virus software & local firewalls ?

Threats due to People Dr. Stefan Lüders (CERN IT/CO) ― 5ème Journées Informatiques de l’IN 2 P 3 et du DAPNIA ― September 20 th 2006 Passwords are known to several (many? ) people ► No traceability, ergo no responsibility People are increasingly the weakest link ► ► ► Use of weak passwords Infected notebooks are physically carried on site Users download malware and open “tricked” attachments Missing/default/weak passwords in applications …but how to handle Operator accounts ? …what about password rules ?
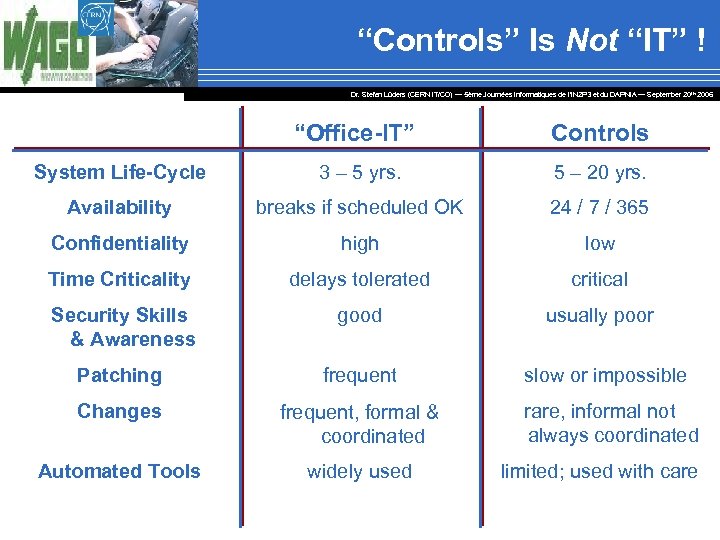
“Controls” Is Not “IT” ! Dr. Stefan Lüders (CERN IT/CO) ― 5ème Journées Informatiques de l’IN 2 P 3 et du DAPNIA ― September 20 th 2006 “Office-IT” Controls System Life-Cycle 3 – 5 yrs. 5 – 20 yrs. Availability breaks if scheduled OK 24 / 7 / 365 Confidentiality high low Time Criticality delays tolerated critical Security Skills & Awareness good usually poor Patching frequent slow or impossible Changes frequent, formal & coordinated rare, informal not always coordinated Automated Tools widely used limited; used with care
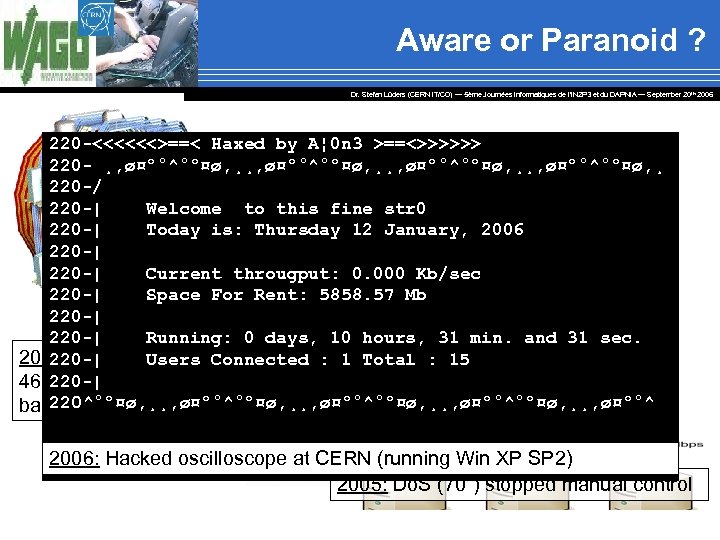
Aware or Paranoid ? Dr. Stefan Lüders (CERN IT/CO) ― 5ème Journées Informatiques de l’IN 2 P 3 et du DAPNIA ― September 20 th 2006 220 -<<<<<<>==< Haxed by A¦ 0 n 3 >==<>>>>>> 2003/08/11: W 32. Blaster. Worm 220 - ¸, ø¤º°^°º¤ø, ¸¸, ø¤º°^°º¤ø, ¸ 220 -/ 220 -| Welcome to this fine str 0 220 -| Today is: Thursday 12 January, 2006 220 -| Current througput: 0. 000 Kb/sec 220 -| Space For Rent: 5858. 57 Mb 220 -| Running: 0 days, 10 hours, 31 min. and 31 sec. 2000: Ex-Employee hacks “wirelessly” Total : 15 220 -| Users Connected : 1 220 -|into sewage plant and spills 46 times 2003: The “Slammer” worm disables 220^°º¤ø, ¸¸, ø¤º°^°º¤ø, ¸¸, ø¤º°^ safety monitoring system basement of Hyatt Regency hotel. of the Davis- 2004: IT intervention, hardware failure Besse nuclear power plant for 5 h. and use of ISO protocol stopped 2006: Hacked oscilloscope at magnet(running Win XP SP 2) SM 18 CERN test stand for 24 h. 2005: Do. S (70”) stopped manual control
Dr. Stefan Lüders (CERN IT/CO) ― 5ème Journées Informatiques de l’IN 2 P 3 et du DAPNIA ― September 20 th 2006

The “Large Hadron Collider” Dr. Stefan Lüders (CERN IT/CO) ― 5ème Journées Informatiques de l’IN 2 P 3 et du DAPNIA ― September 20 th 2006 Steer a beam of 85 kg TNT through a 3 mm hole 10000 times per second ! Beam Bunch Proton 50 - 150 m World’s largest superconducting installation (27 km @ 1. 9°K) worth 2 B€
The “ATLAS” Experiment Dr. Stefan Lüders (CERN IT/CO) ― 5ème Journées Informatiques de l’IN 2 P 3 et du DAPNIA ― September 20 th 2006 2000 members of 151 institutions from 34 countries The ATLAS Experiment 7000 tons Ø 22 m × 43 m 500 M€ pure hardware http: //atlas. ch

Control Systems for Experiments Dr. Stefan Lüders (CERN IT/CO) ― 5ème Journées Informatiques de l’IN 2 P 3 et du DAPNIA ― September 20 th 2006 The CMS Experiment 500 M€ pure hardware 12500 tons, Ø 15 m × 22 m http: //cmsinfo. cern. ch

Standards, if possible ! Dr. Stefan Lüders (CERN IT/CO) ― 5ème Journées Informatiques de l’IN 2 P 3 et du DAPNIA ― September 20 th 2006 standard desktop PCs

Concerned about Cyber-Security Dr. Stefan Lüders (CERN IT/CO) ― 5ème Journées Informatiques de l’IN 2 P 3 et du DAPNIA ― September 20 th 2006

Dr. Stefan Lüders (CERN IT/CO) ― 5ème Journées Informatiques de l’IN 2 P 3 et du DAPNIA ― September 20 th 2006
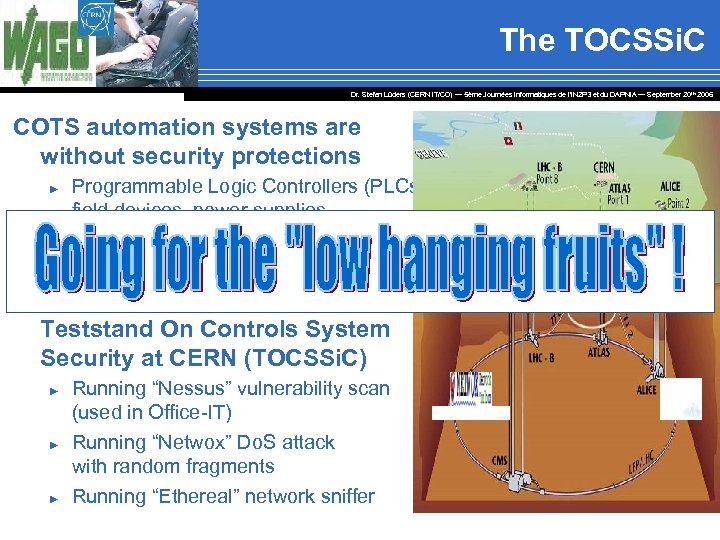
The TOCSSi. C Dr. Stefan Lüders (CERN IT/CO) ― 5ème Journées Informatiques de l’IN 2 P 3 et du DAPNIA ― September 20 th 2006 COTS automation systems are without security protections ► ► Programmable Logic Controllers (PLCs), field devices, power supplies, … Security not integrated into their designs Creation of the Teststand On Controls System Security at CERN (TOCSSi. C) ► ► ► Running “Nessus” vulnerability scan (used in Office-IT) Running “Netwox” Do. S attack with random fragments Running “Ethereal” network sniffer
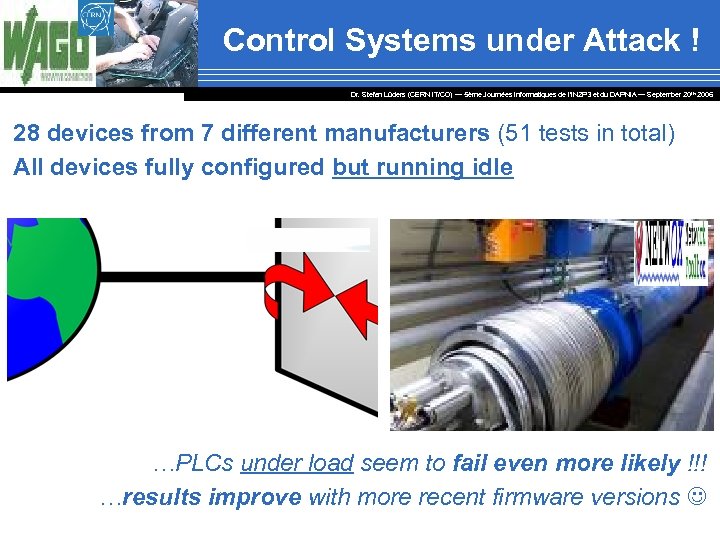
Control Systems under Attack ! Dr. Stefan Lüders (CERN IT/CO) ― 5ème Journées Informatiques de l’IN 2 P 3 et du DAPNIA ― September 20 th 2006 28 devices from 7 different manufacturers (51 tests in total) All devices fully configured but running idle …PLCs under load seem to fail even more likely !!! …results improve with more recent firmware versions
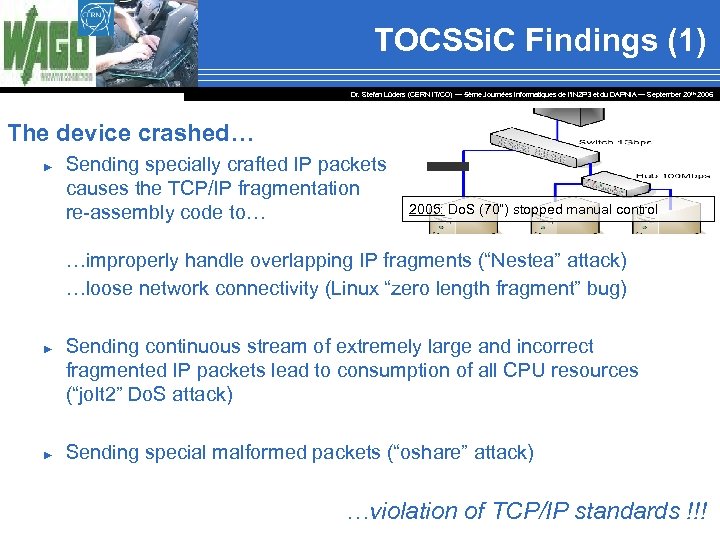
TOCSSi. C Findings (1) Dr. Stefan Lüders (CERN IT/CO) ― 5ème Journées Informatiques de l’IN 2 P 3 et du DAPNIA ― September 20 th 2006 The device crashed… ► Sending specially crafted IP packets causes the TCP/IP fragmentation re-assembly code to… 2005: Do. S (70”) stopped manual control …improperly handle overlapping IP fragments (“Nestea” attack) …loose network connectivity (Linux “zero length fragment” bug) ► ► Sending continuous stream of extremely large and incorrect fragmented IP packets lead to consumption of all CPU resources (“jolt 2” Do. S attack) Sending special malformed packets (“oshare” attack) …violation of TCP/IP standards !!!

TOCSSi. C Findings (2) Dr. Stefan Lüders (CERN IT/CO) ― 5ème Journées Informatiques de l’IN 2 P 3 et du DAPNIA ― September 20 th 2006 FTP server crashed ► ► Sending a too long command or argument Issuing a “CEL aaa…aaa” command (Vx. Works) FTP server allows to connect to third party hosts (i. e. provides an attacker platform) FTP server allows anonymous login Telnet server crashed ► ► ► After flooding it with “^D” characters Sending a too long user name Sending too many “Are you there ? ” commands …both are legacy protocols w/o encryption !

TOCSSi. C Findings (3) Dr. Stefan Lüders (CERN IT/CO) ― 5ème Journées Informatiques de l’IN 2 P 3 et du DAPNIA ― September 20 th 2006 HTTP server crashed ► ► Requesting a URL with too many characters (e. g. “http: //<IP>/cgi-bin/aaa…aaa” or “http: //<IP>/jsp/aaa. . . aaa”) Using up all resources (“WWW infinite request” attack) HTTP server directory available ► Using “http: //<IP>/. . ” GET request (directory traversal) …who needs web servers & e-mailing on PLCs ? Mod. Bus server crashed by scanning port 502 …protocols are well documented (“Google hacking”) !

TOCSSi. C Findings (4) Dr. Stefan Lüders (CERN IT/CO) ― 5ème Journées Informatiques de l’IN 2 P 3 et du DAPNIA ― September 20 th 2006 PLCs are unprotected ► ► ► Can be stopped w/o problems (needs just a bit “googling”) Passwords are not encrypted PLC might even come without authorization schemes …authorization, data integrity checks and encryption must become mandatory ! PLCs are really unprotected ► ► Services (HTTP, SMTP, FTP, Telnet, …) can not be disabled Neither local firewall nor antivirus software … lock the configuration down by default ! Fixed SNMP community names “public” & “private” …community names must be changeable !
Dr. Stefan Lüders (CERN IT/CO) ― 5ème Journées Informatiques de l’IN 2 P 3 et du DAPNIA ― September 20 th 2006
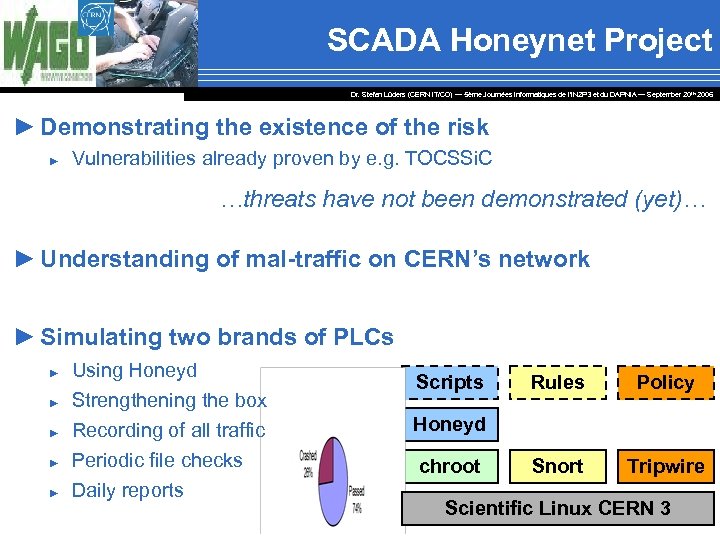
SCADA Honeynet Project Dr. Stefan Lüders (CERN IT/CO) ― 5ème Journées Informatiques de l’IN 2 P 3 et du DAPNIA ― September 20 th 2006 ► Demonstrating the existence of the risk ► Vulnerabilities already proven by e. g. TOCSSi. C …threats have not been demonstrated (yet)… ► Understanding of mal-traffic on CERN’s network ► Simulating two brands of PLCs ► ► ► Using Honeyd Strengthening the box Recording of all traffic Periodic file checks Daily reports Scripts Rules Policy Snort Tripwire Honeyd chroot Scientific Linux CERN 3
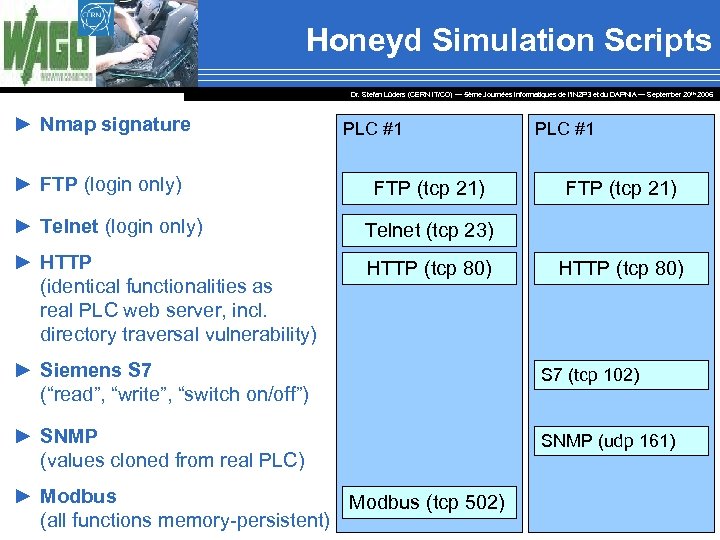
Honeyd Simulation Scripts Dr. Stefan Lüders (CERN IT/CO) ― 5ème Journées Informatiques de l’IN 2 P 3 et du DAPNIA ― September 20 th 2006 ► Nmap signature ► FTP (login only) PLC #1 FTP (tcp 21) ► Telnet (login only) HTTP (tcp 80) FTP (tcp 21) Telnet (tcp 23) ► HTTP (identical functionalities as real PLC web server, incl. directory traversal vulnerability) PLC #1 HTTP (tcp 80) ► Siemens S 7 (“read”, “write”, “switch on/off”) S 7 (tcp 102) ► SNMP (values cloned from real PLC) SNMP (udp 161) ► Modbus (tcp 502) (all functions memory-persistent)
(No) Results so far… Dr. Stefan Lüders (CERN IT/CO) ― 5ème Journées Informatiques de l’IN 2 P 3 et du DAPNIA ― September 20 th 2006 ► Nov. 2005: 4 pots (à two PLCs) deployed inside CERN ► Only observation: the usual “slight fever” on CERN’s campus network 3 pots deployed on controls network ► No interactions observed ► Mar. 2006: 3 pots visible on ports 102/tcp & 502/tcp from the Internet ► Lots of “noise” observed, e. g. SSH scans, but nothing on 102 nor 502
Panic or Don’t Panic ? Dr. Stefan Lüders (CERN IT/CO) ― 5ème Journées Informatiques de l’IN 2 P 3 et du DAPNIA ― September 20 th 2006

Dr. Stefan Lüders (CERN IT/CO) ― 5ème Journées Informatiques de l’IN 2 P 3 et du DAPNIA ― September 20 th 2006

Defense-In-Depth Dr. Stefan Lüders (CERN IT/CO) ― 5ème Journées Informatiques de l’IN 2 P 3 et du DAPNIA ― September 20 th 2006 “Defence-in-Depth” means security on each layer ! ► ► ► …the security of the device itself, …the firmware and operating system, …the network connections & protocols, …the software applications (e. g. PLC programming software), …third party software, and …users, developers & operators Manufacturers and vendors are part of the solution ! ► Security demands should be included into orders and call for tenders

(Too? ) Many Standards, Guidelines, … Dr. Stefan Lüders (CERN IT/CO) ― 5ème Journées Informatiques de l’IN 2 P 3 et du DAPNIA ― September 20 th 2006 ► “Security for Manufacturing and Control Systems” “Integrating Electronic Security into Manufacturing…” (American National Standards Institute & Int'l Society for Measurement and Control) (ANSI/ISA SP 99 TR 1 & TR 2) ► “Code of Practice for Information Security Management” (Int'l Organization for Standardization / Int'l Electrotechnical Commission / British Standard) (ISO/IEC 17799: 2005, BS 7799, ISO 27000) ► Common Criteria (ISO/IEC 15408) ► “System Protection Profile for Industrial Control Systems” (U. S. National Institute of Standards and Technology NIST) ► “Cyber-Security Vulnerability Assessment Methodology Guidance” (U. S. Chemical Industry Data Exchange CIDX) ► “Good Automated Manufacturing Practices: Guideline for Automated System Security” (Int’l Society for Pharmaceutical Engineering ISPE) ► NERC standards (North American Electric Reliability Council) ► AGA standards (American Gas Association)
Ground Rules for Cyber-Security Dr. Stefan Lüders (CERN IT/CO) ― 5ème Journées Informatiques de l’IN 2 P 3 et du DAPNIA ― September 20 th 2006 Use centrally managed systems wherever possible ► Ensure prompt security updates: applications, anti-virus, OS, etc. ytiruces eka. M evitcejbo na eht ni ssenerawa esia. R ytinummoc res. U ► gniggol tneicif ssecc )erehw : terces tp ”gnikc
Network Segregation Dr. Stefan Lüders (CERN IT/CO) ― 5ème Journées Informatiques de l’IN 2 P 3 et du DAPNIA ― September 20 th 2006 Campus network for desktop computing Controls networks / domains ► ► Domain Manager with technical responsibility Authorization procedure for new connections Only operational devices, but neither laptops nor wireless Additional protection for PLCs, etc. Network monitoring ► ► Statistics & intrusion detection Disconnection if threat for others Restricted cross-communication ► ► Filter traffic (firewall or ACLs) Use application gateways or a DMZ
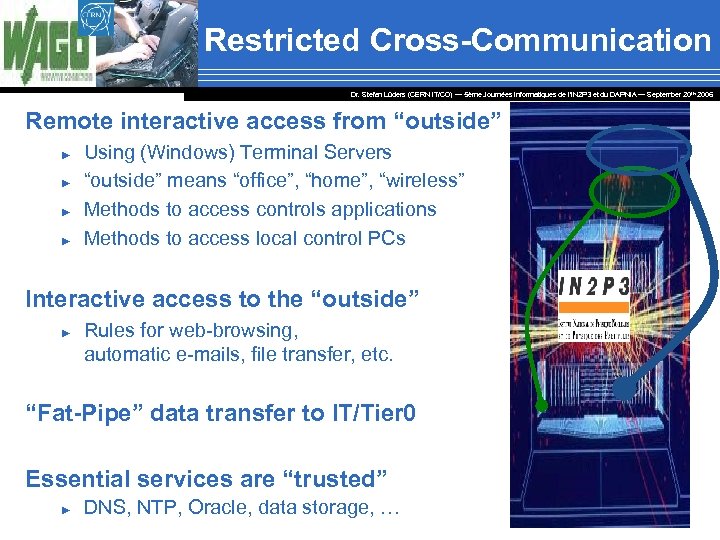
Restricted Cross-Communication Dr. Stefan Lüders (CERN IT/CO) ― 5ème Journées Informatiques de l’IN 2 P 3 et du DAPNIA ― September 20 th 2006 Remote interactive access from “outside” ► ► Using (Windows) Terminal Servers “outside” means “office”, “home”, “wireless” Methods to access controls applications Methods to access local control PCs Interactive access to the “outside” ► Rules for web-browsing, automatic e-mails, file transfer, etc. “Fat-Pipe” data transfer to IT/Tier 0 Essential services are “trusted” ► DNS, NTP, Oracle, data storage, …

Central Software Installation Dr. Stefan Lüders (CERN IT/CO) ― 5ème Journées Informatiques de l’IN 2 P 3 et du DAPNIA ― September 20 th 2006 User-driven PC management ► ► ► 220 -<<<<<<>==< Haxed by A¦ 0 n 3 >==<>>>>>> 220 - ¸, ø¤º°^°º¤ø, ¸¸, ø¤º°^°º¤ø , ¸ 220 -/ 220 -| Welcome to this fine str 0 220 -| Today is: Thursday 12 January, 2006 220 -| Current througput: 0. 000 Kb/sec 220 -| Space For Rent: 5858. 57 Mb 220 -| Running: 0 days, 10 hours, 31 min. and 31 sec. 220 -| Users Connected : 1 Total : 15 220 -| 220 ^°º¤ø, ¸¸, ø¤º°^°º¤ø, ¸¸, ø ¤º° Pass flexibility and responsibility to the User (S)HE decides WHEN to install WHAT on WHICH control PCs (instead of the IT department) IT will send out email notifications of new patches to be installed (S)HE has to ensure security However, PCs might be blocked if threat for others Implementations for ► ► Windows XP, Windows Server (web-based interface) CERN Scientific Linux 3/4/5 (terminal-based) using
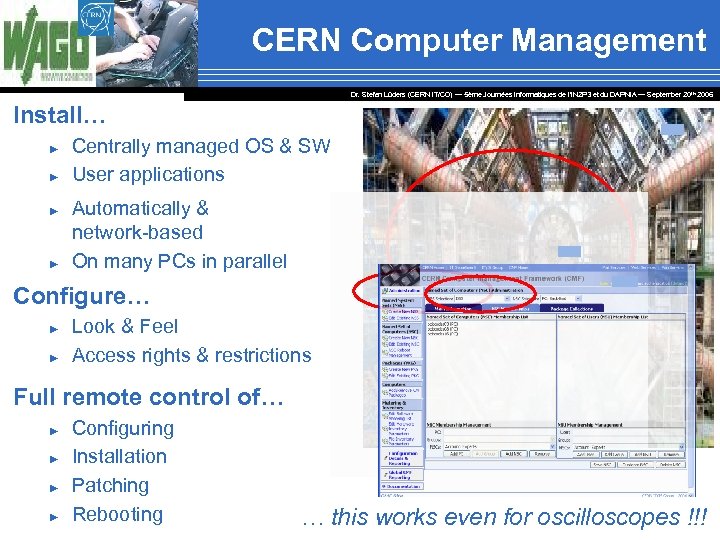
CERN Computer Management Dr. Stefan Lüders (CERN IT/CO) ― 5ème Journées Informatiques de l’IN 2 P 3 et du DAPNIA ― September 20 th 2006 Install… ► ► Centrally managed OS & SW User applications Automatically & network-based On many PCs in parallel Configure… ► ► Look & Feel Access rights & restrictions Full remote control of… ► ► Configuring Installation Patching Rebooting … this works even for oscilloscopes !!!

Policies on Access Control Dr. Stefan Lüders (CERN IT/CO) ― 5ème Journées Informatiques de l’IN 2 P 3 et du DAPNIA ― September 20 th 2006 No emailing on the controls networks Strategy for operator accounts ► ► ► Role Based Access Control User credentials for authentication Role assignment for authorization Dependent on accelerator status Strict rules for remote access However, still problematic areas ► ► User privileges in commercial controls applications Security of OPC

Raising User Awareness Dr. Stefan Lüders (CERN IT/CO) ― 5ème Journées Informatiques de l’IN 2 P 3 et du DAPNIA ― September 20 th 2006 Awareness raising ► ► Campaigns to inform Users of control systems about ‘Industrial Security’ At CERN and in the HEP community Interaction with vendors of control systems ► ► Discussion on the TOCSSi. C results and their mitigation Discussions on “Requirements for the Cyber-Security of Control Systems” Dialog with other Users, researchers, and government bodies
Summary Dr. Stefan Lüders (CERN IT/CO) ― 5ème Journées Informatiques de l’IN 2 P 3 et du DAPNIA ― September 20 th 2006
Nature is beautiful !!! Dr. Stefan Lüders (CERN IT/CO) ― 5ème Journées Informatiques de l’IN 2 P 3 et du DAPNIA ― September 20 th 2006 1970 1973 1982 1979 1992 1986 2008? 1995 2000 2001
2097f7bf56c99a66bf86f8fa3fba4a0b.ppt