da72bce8a288520009ba2bf308cc3b22.ppt
- Количество слайдов: 34

Context-aware Computing

CSCI 6990: Topics in Mobile Computing @ The University of New Orleans -- Prof. Golden G. Richard III Context-aware Computing ü Beyond application-aware adaptation ü Instead of adapting only to resource levels, adapt to contexts ü Context: – Enumeration-based (categories) – Role-based (roles of context in building mobile applications) 2
CSCI 6990: Topics in Mobile Computing @ The University of New Orleans -- Prof. Golden G. Richard III Types of Context ü Computing context includes network connectivity, ü ü 3 communication costs, communication bandwidth, and local resources, such as printers, displays, and workstations User context includes user profiles, location, and people in the vicinity of the user Physical context includes lighting and noise levels, traffic conditions, and temperature Temporal context includes time of day, week, month, and season of the year Context history is the recording of computing, user, and physical context over time

CSCI 6990: Topics in Mobile Computing @ The University of New Orleans -- Prof. Golden G. Richard III The 5 W’s… ü Who is the user? Who are the people with 4 which the user is interacting, or who is nearby? ü What is the user doing? ü Where is the user? Home? Work? Bathroom? Familiar coffee shop? ü When? What time is it? ü Why? Why is the user performing a certain task? What is the task’s priority in the “grand scheme”? ü Low-level vs. High-level details
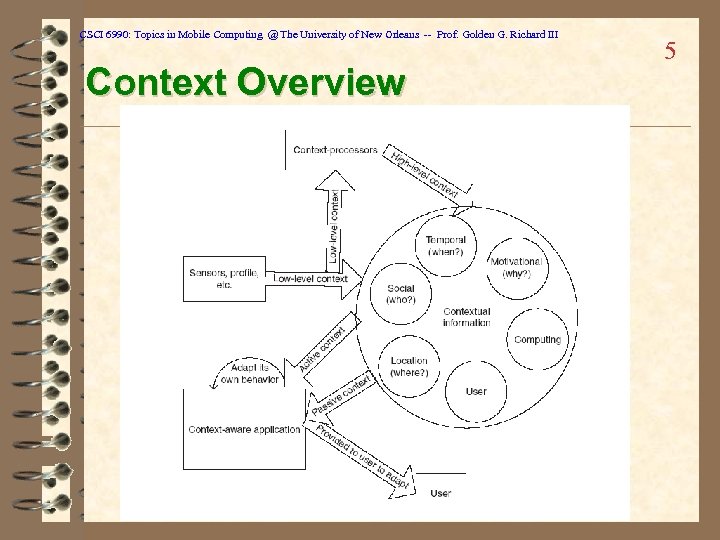
CSCI 6990: Topics in Mobile Computing @ The University of New Orleans -- Prof. Golden G. Richard III Context Overview 5

CSCI 6990: Topics in Mobile Computing @ The University of New Orleans -- Prof. Golden G. Richard III Context-aware Requirements 6 ü Contextual sensing – detection of environmental states ü Contextual adaptation – capability of the system to adapt its behavior by using contextual information ü Contextual resource discovery – capability to discover available resources in an environment ü Contextual augmentation – capability to associate contextual information with some digital data – Example: association of a particular meeting place and attendees with a set of minutes – Example: association of a digital photo with a specific location

CSCI 6990: Topics in Mobile Computing @ The University of New Orleans -- Prof. Golden G. Richard III Designing CA Applications ü Build list of relevant contexts – e. g. , “home”, “office”, “traveling”, “sleeping”, … ü Specify context-aware behaviors – Presentation of context-sensitive information – Automatic discovery of relevant objects (e. g. , 7 nearby people for transmission of business cards) – Modification of the physical and digital environments ü Integration of application with methods for sensing context

CSCI 6990: Topics in Mobile Computing @ The University of New Orleans -- Prof. Golden G. Richard III Simple Example: stick-e notes 8 ü Context-aware Post-it notes ü Build list of relevant contexts – Based on location (latitude/longitude via GPS) – Temperature, whatever else can be sensed ü Specify context-aware behaviors – stick-e notes “pop up” on a PDA when contextual info is appropriate – Reminder to return a library book when near the library – Reminder to buy a new winter jacket when temperature drops below 60 F ü Integration of application with methods for sensing context – Most difficult part – Ubiquitous sensing of environmental characteristics, such as location, temperature, number of human beings nearby, the cat is near, not widespread
CSCI 6990: Topics in Mobile Computing @ The University of New Orleans -- Prof. Golden G. Richard III Where Does Context Come From? ü Returning to the “difficulty” point on the previous slide ü Environmental sensors – – Temperature, humidity, location, noise, motion Cat sensor Potential need for multiple types of sensors GPS vs. indoor location sensors ü History – Recording user actions and previous contexts ü User’s personal computing environment – Schedules, notes, address books, financial info ü Need real-time analysis to provide context 9

CSCI 6990: Topics in Mobile Computing @ The University of New Orleans -- Prof. Golden G. Richard III Example: Location 10 ü Indoor locating systems – e. g. , infrared or ultrasound ü Wireless nanocell communication activity – Association with short-range base stations ü GPS ü Associations with nearby computers ü Motion sensors and cameras, computer vision ü Ask the user!

CSCI 6990: Topics in Mobile Computing @ The University of New Orleans -- Prof. Golden G. Richard III Service-oriented Architecture 11 ü Provide services to context-aware applications ü Context subscription and delivery service – Delivers contextual information as available ü Context query service – Delivers contextual information on-demand ü Context transformation and synthesis services – Transforms low-level contextual information (location, temperature, lighting levels) into high-level (“YOU’RE IN THE CLOSET IN YOUR BEDROOM”) ü Service discovery – Discovery of nearby services – We’ll examine service discovery protocols next!

Mobile Agents

CSCI 6990: Topics in Mobile Computing @ The University of New Orleans -- Prof. Golden G. Richard III Mobile Agents: Motivation ü Mobile agent systems support dynamic migration of bits of software ü These “bits of software” are agents, and perform tasks remotely in support of some local computation ü Some advantages: – Disconnected operation – Customized, “do once” operations without customizing server software – Attacks resource-poverty problem for mobile computing • Less bandwidth, power, CPU needed 13
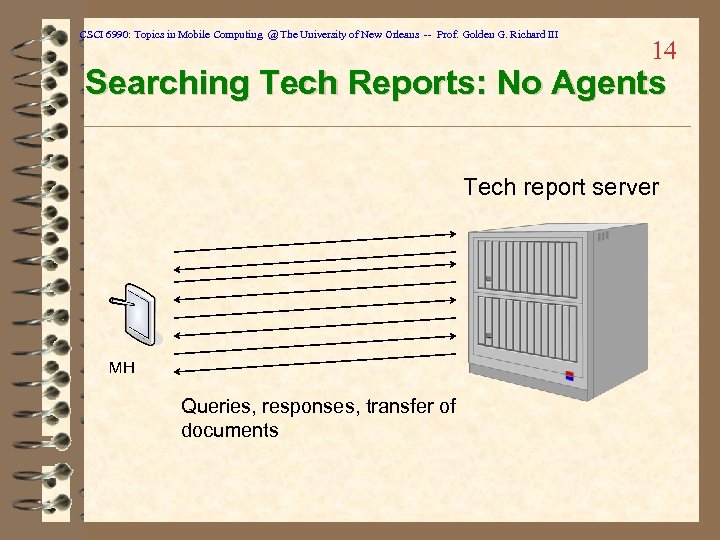
CSCI 6990: Topics in Mobile Computing @ The University of New Orleans -- Prof. Golden G. Richard III 14 Searching Tech Reports: No Agents Tech report server MH Queries, responses, transfer of documents
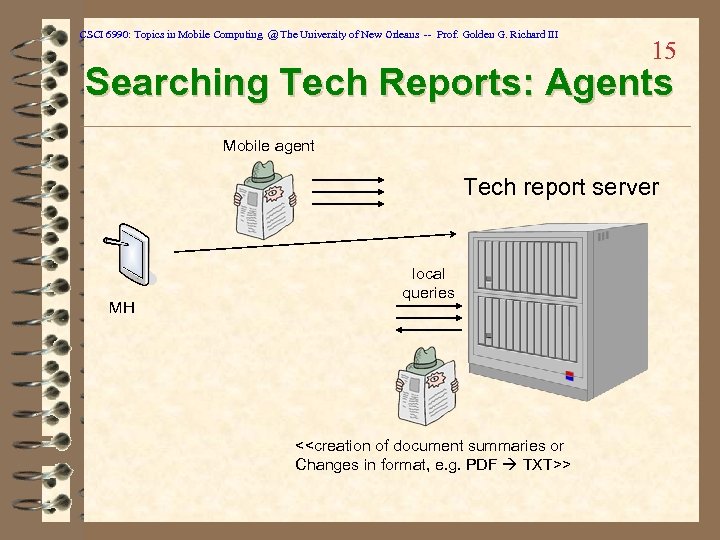
CSCI 6990: Topics in Mobile Computing @ The University of New Orleans -- Prof. Golden G. Richard III 15 Searching Tech Reports: Agents Mobile agent Tech report server MH local queries <<creation of document summaries or Changes in format, e. g. PDF TXT>>
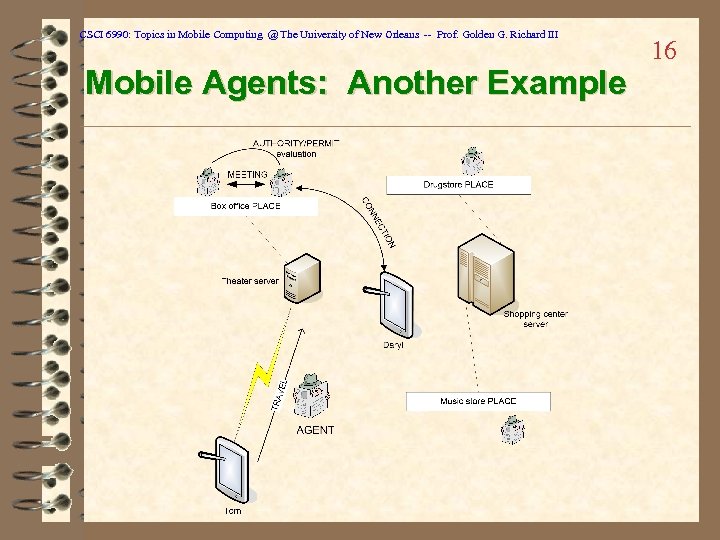
CSCI 6990: Topics in Mobile Computing @ The University of New Orleans -- Prof. Golden G. Richard III Mobile Agents: Another Example 16

CSCI 6990: Topics in Mobile Computing @ The University of New Orleans -- Prof. Golden G. Richard III Mobile Agents: Roadblocks 17 ü Security ü Users’ trust in mobile code has been badly damaged – Applets, Javascript, other scripting languages are far less sophisticated than agents, but… ü Infrastructure ü Lack of a “killer” application ü Standardization ü (Security)

CSCI 6990: Topics in Mobile Computing @ The University of New Orleans -- Prof. Golden G. Richard III Mobile Agents: Technical Issues ü Security! ü Implementation language for agents – Interpreted languages easier – Don’t want to insist on homogeneous architectures! ü Migration strategy – Again, easier with languages like Java – Otherwise, becomes a process checkpointing problem ü Communication strategy – Temporal locality: must communicate with other agents while they’re around, or not? – Spatial locality: must be able to name and locate other agents to communicate 18

CSCI 6990: Topics in Mobile Computing @ The University of New Orleans -- Prof. Golden G. Richard III Agent Communication: Traditional 19 ü Sockets, RMI, … ü Strong temporal locality ü Other guy must be around to communicate ü Other guy’s “name” reveals his location

CSCI 6990: Topics in Mobile Computing @ The University of New Orleans -- Prof. Golden G. Richard III 20 Agent Communication: Meeting Places ü A “meeting room” for agents ü Agents must migrate to the meeting room to communicate ü Temporal locality—other agents must be present to communicate ü Spatial locality—communicate with other agents in the meeting place, can dynamically determine who’s there

CSCI 6990: Topics in Mobile Computing @ The University of New Orleans -- Prof. Golden G. Richard III 21 Agent Communication: Tuple Spaces ü Communicate by dropping objects into a shared space ü Relaxes temporal and spatial locality ü Can drop objects for other agents whether they’re around or not ü Don’t have to know their names or locations ü Simpler to use local tuple spaces (one per place? ) ü Can use reactions, which cause code to be executed when a certain type of object (e. g. , a “cash” object) is dropped into the space

Ad hoc / sensor networks (Ch 8 )
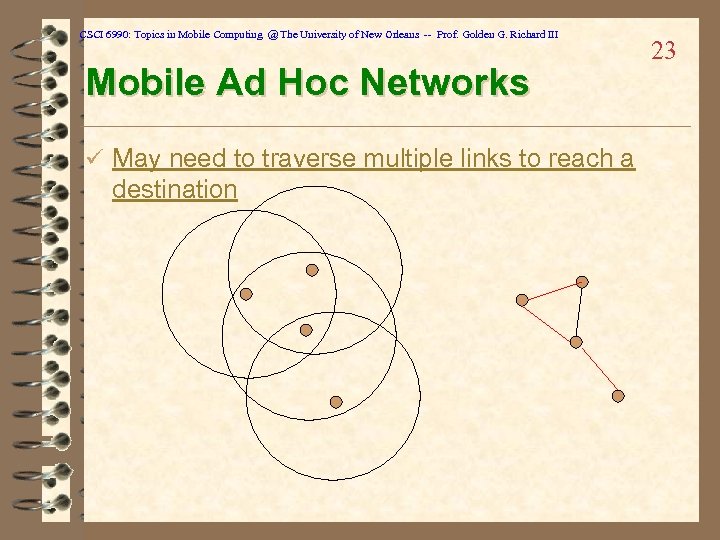
CSCI 6990: Topics in Mobile Computing @ The University of New Orleans -- Prof. Golden G. Richard III Mobile Ad Hoc Networks ü May need to traverse multiple links to reach a destination 23
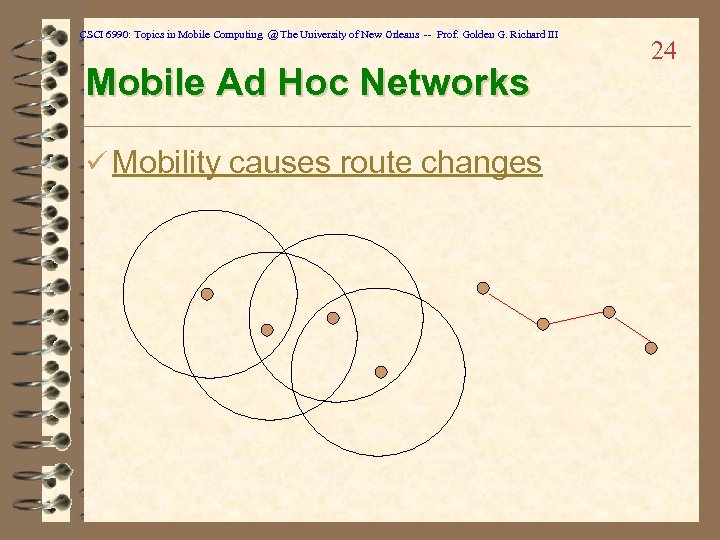
CSCI 6990: Topics in Mobile Computing @ The University of New Orleans -- Prof. Golden G. Richard III Mobile Ad Hoc Networks ü Mobility causes route changes 24

CSCI 6990: Topics in Mobile Computing @ The University of New Orleans -- Prof. Golden G. Richard III Mobile Ad Hoc Networks 25 ü Formed by wireless hosts which may be mobile ü Don’t need a pre-existing infrastructure – ie, don’t need a backbone network, routers, etc. ü Routes between nodes potentially contain multiple hops ü Why MANET? – Ease, speed of deployment – Decreased dependence on infrastructure – Can use in many scenarios where deployment of a wired network is impractical or impossible – Lots of military applications, but there are others… ,

CSCI 6990: Topics in Mobile Computing @ The University of New Orleans -- Prof. Golden G. Richard III Many Applications 26 ü Personal area networking – cell phone, laptop, ear phone, wrist watch ü Civilian environments – meeting rooms – sports stadiums – groups of boats, small aircraft (wired REALLY impractical!!) ü Emergency operations – search-and-rescue – policing and fire fighting ü Sensor networks – Groups of sensors embedded in the environment or scattered over a target area
CSCI 6990: Topics in Mobile Computing @ The University of New Orleans -- Prof. Golden G. Richard III Many Variations ü Fully Symmetric Environment – all nodes have identical capabilities and responsibilities ü Asymmetric Capabilities – – transmission ranges and radios may differ battery life at different nodes may differ processing capacity may be different at different nodes speed of movement different ü Asymmetric Responsibilities – only some nodes may route packets – some nodes may act as leaders of nearby nodes (e. g. , “cluster head”) 27
CSCI 6990: Topics in Mobile Computing @ The University of New Orleans -- Prof. Golden G. Richard III Many Variations ü Traffic characteristics may differ – bandwidth – timeliness constraints – reliability requirements – unicast / broadcast / multicast / geocast ü May co-exist (and co-operate) with an infrastructure-based network 28
CSCI 6990: Topics in Mobile Computing @ The University of New Orleans -- Prof. Golden G. Richard III Many Variations 29 ü Mobility patterns may be different – people sitting at an airport lounge (little mobility) – taxi cabs (highly mobile) – military movements (mostly clustered? ) – personal area network (again, mostly clustered? ) ü Mobility characteristics – speed – predictability • direction of movement • pattern of movement – uniformity (or lack thereof) of mobility characteristics among different nodes

CSCI 6990: Topics in Mobile Computing @ The University of New Orleans -- Prof. Golden G. Richard III Challenges 30 Limited wireless transmission range Broadcast nature of the wireless medium Packet losses due to transmission errors Environmental issues (“chop that tree!!”) Mobility-induced route changes Mobility-induced packet losses Battery constraints Potentially frequent network partitions Ease of snooping on wireless transmissions (security hazard) ü Sensor networks: very resource-constrained! ü ü ü ü ü
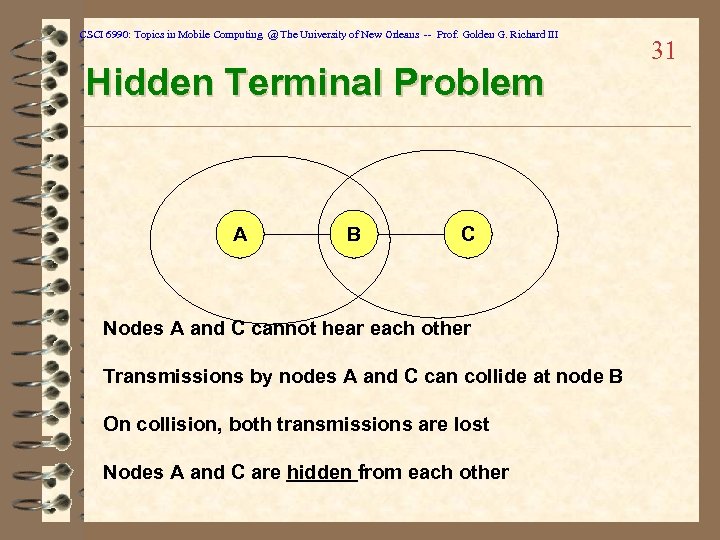
CSCI 6990: Topics in Mobile Computing @ The University of New Orleans -- Prof. Golden G. Richard III Hidden Terminal Problem A B C Nodes A and C cannot hear each other Transmissions by nodes A and C can collide at node B On collision, both transmissions are lost Nodes A and C are hidden from each other 31

CSCI 6990: Topics in Mobile Computing @ The University of New Orleans -- Prof. Golden G. Richard III First Issue: Routing 32 ü Why is Ad hoc Routing Different? ü Host mobility – link failure/repair due to mobility may have different characteristics than those due to other causes – traditional routing algorithms assume relatively stable network topology, few router failures ü Rate of link failure/repair may be high when nodes move fast ü New performance criteria may be used – route stability despite mobility – energy consumption

CSCI 6990: Topics in Mobile Computing @ The University of New Orleans -- Prof. Golden G. Richard III Routing Protocols ü Proactive protocols – Determine routes independent of traffic pattern – Traditional routing protocols for wired networks are proactive ü Reactive protocols – Discover/maintain routes only if needed 33

CSCI 6990: Topics in Mobile Computing @ The University of New Orleans -- Prof. Golden G. Richard III 34 Trade-Off: Proactive vs. Reactive ü Latency of route discovery – Proactive protocols may have lower latency since routes are maintained at all times – Reactive protocols may have higher latency because a route from X to Y will be found only when X attempts to send to Y ü Overhead of route discovery/maintenance – Reactive protocols may have lower overhead since routes are determined only if needed – Proactive protocols can (but not necessarily) result in higher overhead due to continuous route updating ü Which approach achieves a better tradeoff depends on the traffic and mobility patterns, but most ad hoc routing protocols are reactive
da72bce8a288520009ba2bf308cc3b22.ppt