cfa96db1666d084dea50cae626e2b90d.ppt
- Количество слайдов: 87
 Constructing a Theoretical Model for the Evolution of Law Relating to Telecommunication Privacy Vis -à-Vis Law Enforcement Surveillance In America A dissertation proposal donna Bair-Mundy
Constructing a Theoretical Model for the Evolution of Law Relating to Telecommunication Privacy Vis -à-Vis Law Enforcement Surveillance In America A dissertation proposal donna Bair-Mundy
 Structure of the presentation Research interest Impetus for study—Patriot Act Interception timeline ►Problem statement Research proposal—Methodology Theoretical foundation
Structure of the presentation Research interest Impetus for study—Patriot Act Interception timeline ►Problem statement Research proposal—Methodology Theoretical foundation
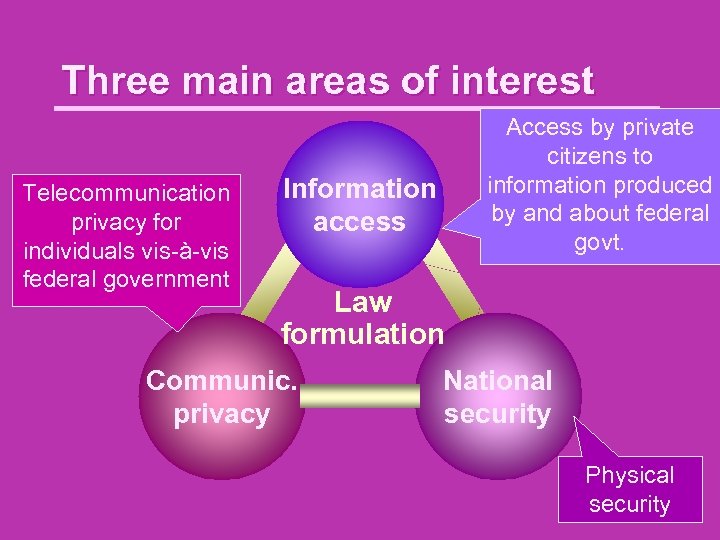 Three main areas of interest Telecommunication privacy for individuals vis-à-vis federal government Access by private citizens to information produced by and about federal govt. Information access Law formulation Communic. privacy National security Physical security
Three main areas of interest Telecommunication privacy for individuals vis-à-vis federal government Access by private citizens to information produced by and about federal govt. Information access Law formulation Communic. privacy National security Physical security
 Law as policy Development of law as a reflection of the process by which our society determines the boundary between public and private Constructing a theoretical model for this process
Law as policy Development of law as a reflection of the process by which our society determines the boundary between public and private Constructing a theoretical model for this process
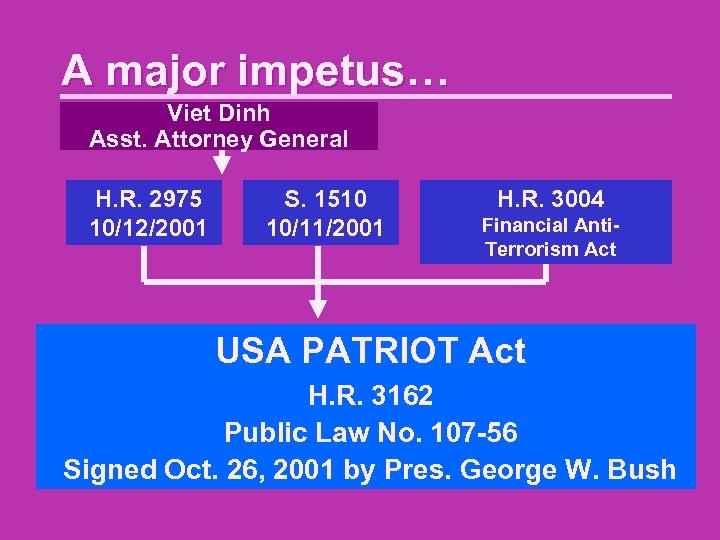 A major impetus… Viet Dinh Asst. Attorney General H. R. 2975 10/12/2001 S. 1510 10/11/2001 H. R. 3004 Financial Anti. Terrorism Act USA PATRIOT Act H. R. 3162 Public Law No. 107 -56 Signed Oct. 26, 2001 by Pres. George W. Bush
A major impetus… Viet Dinh Asst. Attorney General H. R. 2975 10/12/2001 S. 1510 10/11/2001 H. R. 3004 Financial Anti. Terrorism Act USA PATRIOT Act H. R. 3162 Public Law No. 107 -56 Signed Oct. 26, 2001 by Pres. George W. Bush
 The USA PATRIOT Act H. R. 3162 The Acronym Uniting and Strengthening America by Providing Appropriate Tools Required to Intercept and Obstruct Terrorism
The USA PATRIOT Act H. R. 3162 The Acronym Uniting and Strengthening America by Providing Appropriate Tools Required to Intercept and Obstruct Terrorism
 The USA PATRIOT Act H. R. 3162 The Purpose To deter and punish terrorist acts in the United States and around the world, to enhance law enforcement investigatory tools, and for other purposes.
The USA PATRIOT Act H. R. 3162 The Purpose To deter and punish terrorist acts in the United States and around the world, to enhance law enforcement investigatory tools, and for other purposes.
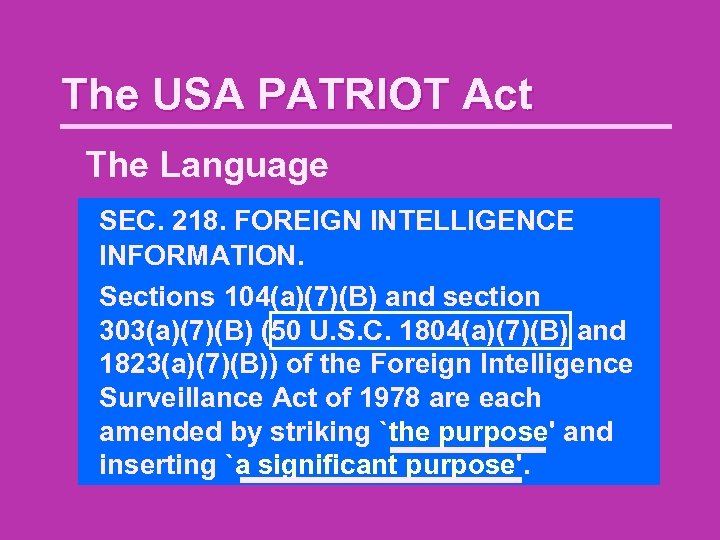 The USA PATRIOT Act The Language SEC. 218. FOREIGN INTELLIGENCE INFORMATION. Sections 104(a)(7)(B) and section 303(a)(7)(B) (50 U. S. C. 1804(a)(7)(B) and 1823(a)(7)(B)) of the Foreign Intelligence Surveillance Act of 1978 are each amended by striking `the purpose' and inserting `a significant purpose'.
The USA PATRIOT Act The Language SEC. 218. FOREIGN INTELLIGENCE INFORMATION. Sections 104(a)(7)(B) and section 303(a)(7)(B) (50 U. S. C. 1804(a)(7)(B) and 1823(a)(7)(B)) of the Foreign Intelligence Surveillance Act of 1978 are each amended by striking `the purpose' and inserting `a significant purpose'.
 The U. S. Code Sections 104(a)(7)(B) and section 303(a)(7)(B) (50 U. S. C. 1804(a)(7)(B) and 1823(a)(7)(B)) of the Foreign Intelligence Surveillance Act of 1978 are each amended by striking `the purpose' and inserting `a significant purpose'. TITLE 50 > CHAPTER 36 > SUBCHAPTER I > § 1804. Applications for court orders (7) a certification … (B) that a significant purpose of the (B) that the purpose of the surveillance is to obtain foreign intelligence information;
The U. S. Code Sections 104(a)(7)(B) and section 303(a)(7)(B) (50 U. S. C. 1804(a)(7)(B) and 1823(a)(7)(B)) of the Foreign Intelligence Surveillance Act of 1978 are each amended by striking `the purpose' and inserting `a significant purpose'. TITLE 50 > CHAPTER 36 > SUBCHAPTER I > § 1804. Applications for court orders (7) a certification … (B) that a significant purpose of the (B) that the purpose of the surveillance is to obtain foreign intelligence information;
 Federal Wiretapping Act 1968 The Omnibus Crime Control and Safe Streets Act of 1968 (“Federal Wiretapping Act”) U. S. Code 18 USC Section 2510 et seq. Federal Rules of Criminal Procedure Rule 41 Search and Seizure
Federal Wiretapping Act 1968 The Omnibus Crime Control and Safe Streets Act of 1968 (“Federal Wiretapping Act”) U. S. Code 18 USC Section 2510 et seq. Federal Rules of Criminal Procedure Rule 41 Search and Seizure
 FISA 1978 Foreign Intelligence Surveillance Act U. S. Code 50 USC Sections 1801 -1863
FISA 1978 Foreign Intelligence Surveillance Act U. S. Code 50 USC Sections 1801 -1863
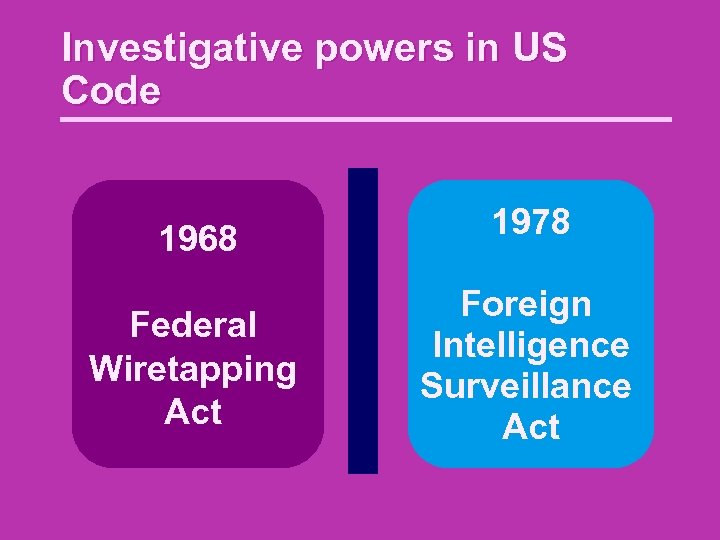 Investigative powers in US Code 1968 1978 Federal Wiretapping Act Foreign Intelligence Surveillance Act
Investigative powers in US Code 1968 1978 Federal Wiretapping Act Foreign Intelligence Surveillance Act
 The USA PATRIOT Act The Complaints—Freedom of Speech Section 215—Amending FISA 501(d) No person shall disclose to any other person (other than those persons necessary to produce the tangible things under this section) that the Federal Bureau of Investigation has sought or obtained tangible things under this section.
The USA PATRIOT Act The Complaints—Freedom of Speech Section 215—Amending FISA 501(d) No person shall disclose to any other person (other than those persons necessary to produce the tangible things under this section) that the Federal Bureau of Investigation has sought or obtained tangible things under this section.
 The USA PATRIOT Act The Complaints—Other Civil Liberties Freedom of association Right to due process Freedom to read
The USA PATRIOT Act The Complaints—Other Civil Liberties Freedom of association Right to due process Freedom to read
 Justice Louis Brandeis “Experience should teach us to be most on our guard to protect liberty when the Government's purposes are beneficent. Men born to freedom are naturally alert to repel invasion of their liberty by evil-minded rulers. The greatest dangers to liberty lurk in insidious encroachment by men of zeal, well-meaning but without understanding. ” Olmstead v. United States (dissent)
Justice Louis Brandeis “Experience should teach us to be most on our guard to protect liberty when the Government's purposes are beneficent. Men born to freedom are naturally alert to repel invasion of their liberty by evil-minded rulers. The greatest dangers to liberty lurk in insidious encroachment by men of zeal, well-meaning but without understanding. ” Olmstead v. United States (dissent)
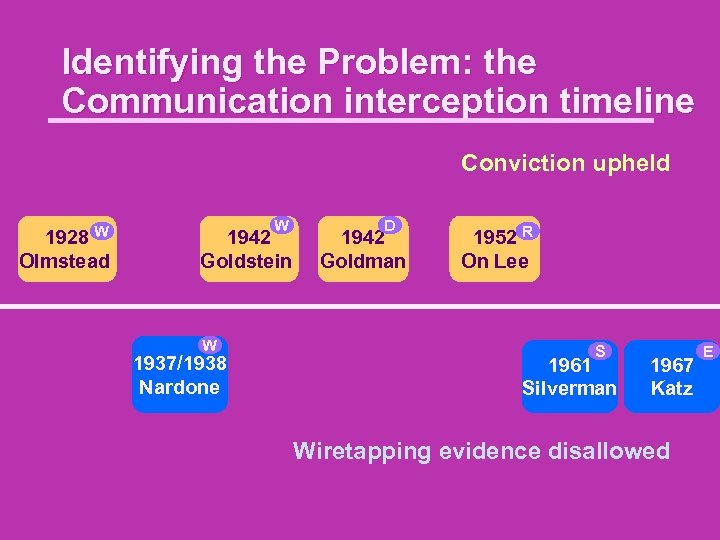 Identifying the Problem: the Communication interception timeline Conviction upheld W 1928 Olmstead W 1942 Goldstein W 1937/1938 Nardone D 1942 Goldman 1952 R On Lee S 1961 Silverman 1967 Katz Wiretapping evidence disallowed E
Identifying the Problem: the Communication interception timeline Conviction upheld W 1928 Olmstead W 1942 Goldstein W 1937/1938 Nardone D 1942 Goldman 1952 R On Lee S 1961 Silverman 1967 Katz Wiretapping evidence disallowed E
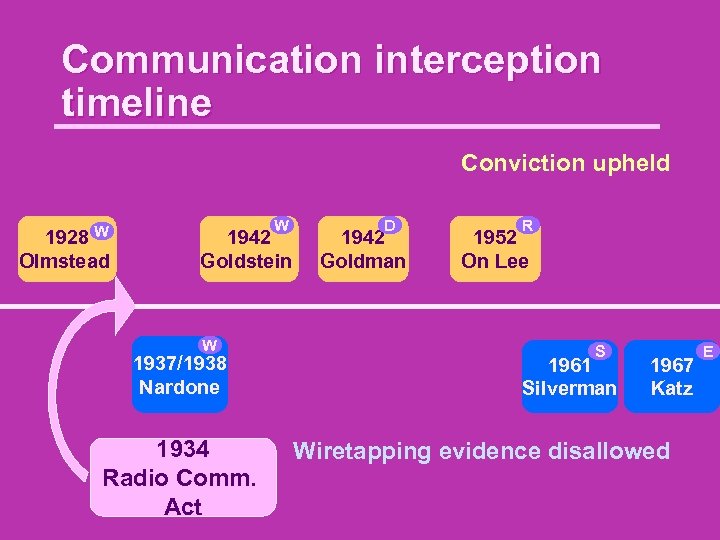 Communication interception timeline Conviction upheld W 1928 Olmstead W 1942 Goldstein W 1937/1938 Nardone 1934 Radio Comm. Act D 1942 Goldman R 1952 On Lee S 1961 Silverman 1967 Katz Wiretapping evidence disallowed E
Communication interception timeline Conviction upheld W 1928 Olmstead W 1942 Goldstein W 1937/1938 Nardone 1934 Radio Comm. Act D 1942 Goldman R 1952 On Lee S 1961 Silverman 1967 Katz Wiretapping evidence disallowed E
 Federal Communications Act 1934 Section 605 No person not being authorized by the sender shall intercept any radio communication and divulge or publish the existence, contents, substance, purport, effect, or meaning of such intercepted communication to any person.
Federal Communications Act 1934 Section 605 No person not being authorized by the sender shall intercept any radio communication and divulge or publish the existence, contents, substance, purport, effect, or meaning of such intercepted communication to any person.
 Nardone “…the plain words of § 605 forbid anyone, unless authorized by the sender, to intercept a telephone message, and direct in equally clear language that “no person” shall divulge or publish the message or its substance to “any person. ” To recite the contents of the message in testimony before a court is to divulge the message. The conclusion that the act forbids such testimony seems to us unshaken by the government’s arguments. ” Justice Roberts
Nardone “…the plain words of § 605 forbid anyone, unless authorized by the sender, to intercept a telephone message, and direct in equally clear language that “no person” shall divulge or publish the message or its substance to “any person. ” To recite the contents of the message in testimony before a court is to divulge the message. The conclusion that the act forbids such testimony seems to us unshaken by the government’s arguments. ” Justice Roberts
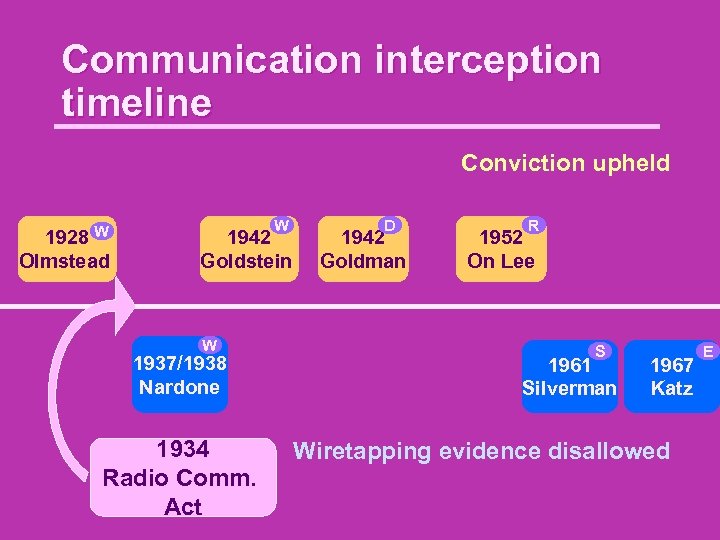 Communication interception timeline Conviction upheld W 1928 Olmstead W 1942 Goldstein W 1937/1938 Nardone 1934 Radio Comm. Act D 1942 Goldman R 1952 On Lee S 1961 Silverman 1967 Katz Wiretapping evidence disallowed E
Communication interception timeline Conviction upheld W 1928 Olmstead W 1942 Goldstein W 1937/1938 Nardone 1934 Radio Comm. Act D 1942 Goldman R 1952 On Lee S 1961 Silverman 1967 Katz Wiretapping evidence disallowed E
 Problem statement: Looking at the continuing saga of legislation and case laws dealing with telecommunication privacy, from Olmstead through Katz, from the Wiretapping Act and FISA to the Patriot Act, how can we understand the process by which society, through its laws, defines the boundary between inviolate personal space and legitimate law enforcement surveillance activities?
Problem statement: Looking at the continuing saga of legislation and case laws dealing with telecommunication privacy, from Olmstead through Katz, from the Wiretapping Act and FISA to the Patriot Act, how can we understand the process by which society, through its laws, defines the boundary between inviolate personal space and legitimate law enforcement surveillance activities?
 Relevant situations for different research strategies Requires Focuses on control over contembehavioral porary events? Strategy Form of research question Experiment How, why yes Survey Who, what, where, how many yes History How, why no no Case study How, why no yes Yin, Robert K. 1994. Case study research: design and methods. Thousand Oaks: Sage Publications.
Relevant situations for different research strategies Requires Focuses on control over contembehavioral porary events? Strategy Form of research question Experiment How, why yes Survey Who, what, where, how many yes History How, why no no Case study How, why no yes Yin, Robert K. 1994. Case study research: design and methods. Thousand Oaks: Sage Publications.
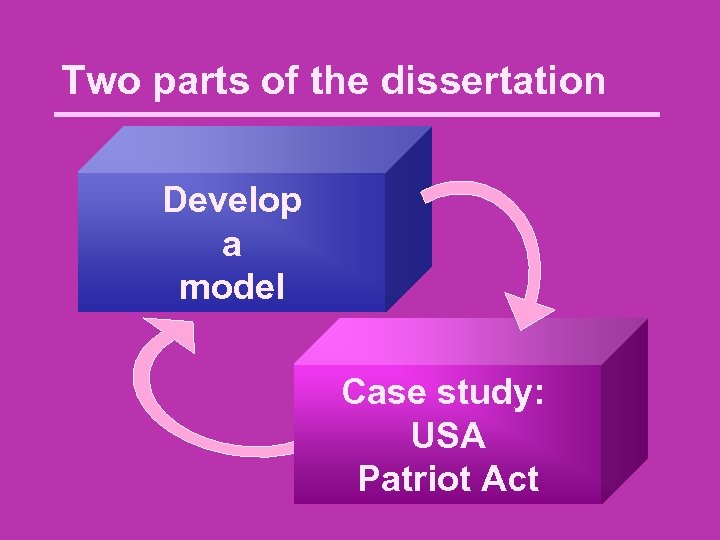 Two parts of the dissertation Develop a model Case study: USA Patriot Act
Two parts of the dissertation Develop a model Case study: USA Patriot Act
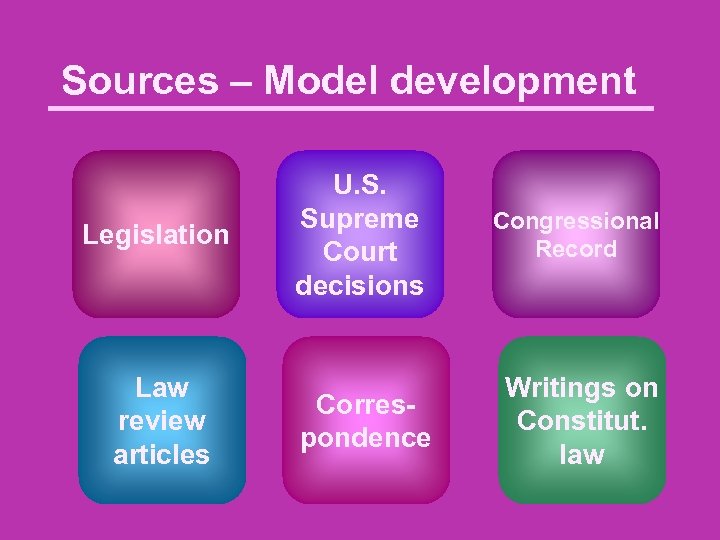 Sources – Model development Legislation Law review articles U. S. Supreme Court decisions Congressional Record Correspondence Writings on Constitut. law
Sources – Model development Legislation Law review articles U. S. Supreme Court decisions Congressional Record Correspondence Writings on Constitut. law
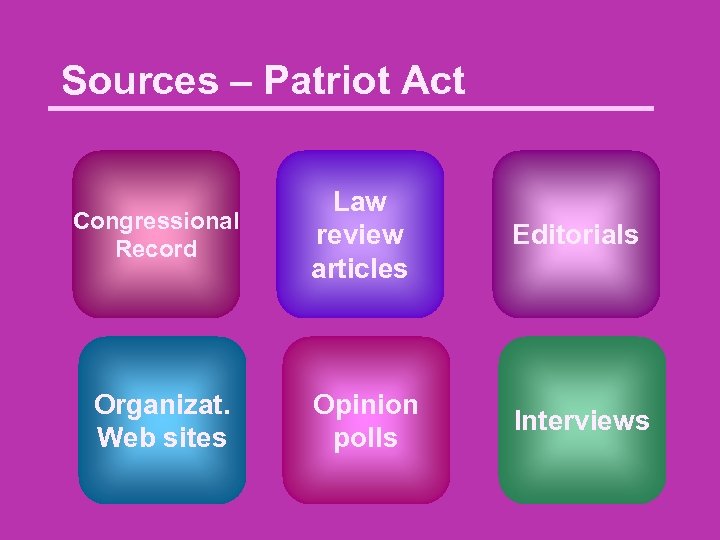 Sources – Patriot Act Congressional Record Law review articles Editorials Organizat. Web sites Opinion polls Interviews
Sources – Patriot Act Congressional Record Law review articles Editorials Organizat. Web sites Opinion polls Interviews
 Theoretical foundation Law Surveillance Privacy
Theoretical foundation Law Surveillance Privacy
 Theoretical foundation Legal H. L. A. Hart – Penumbral case William Banks and M. E. Bowman – privacy v. national security Laurence Tribe – Constitutional models
Theoretical foundation Legal H. L. A. Hart – Penumbral case William Banks and M. E. Bowman – privacy v. national security Laurence Tribe – Constitutional models
 Hart's penumbral case Law: No vehicles may be driven in the park. Park ? Is an airplane a vehicle? Hart, H. L. A. 1977. “Positivism and the separation of law and morals. ” In The philosophy of law, edited by R. M. Dworkin, 17 -37. London: Oxford University Press.
Hart's penumbral case Law: No vehicles may be driven in the park. Park ? Is an airplane a vehicle? Hart, H. L. A. 1977. “Positivism and the separation of law and morals. ” In The philosophy of law, edited by R. M. Dworkin, 17 -37. London: Oxford University Press.
 Is an airplane a vehicle? Methods of determination Determine everyday meaning of "vehicle" Meaning of "vehicle" in consensus of cases Take a standard case and arbitrarily select certain features (1) normally driven on land (2) capable of carrying a person (3) capable of being self-propelled
Is an airplane a vehicle? Methods of determination Determine everyday meaning of "vehicle" Meaning of "vehicle" in consensus of cases Take a standard case and arbitrarily select certain features (1) normally driven on land (2) capable of carrying a person (3) capable of being self-propelled
 Hart's penumbral case Law: No vehicles may be driven in the park. Vehicle: (1) normally driven on land (2) capable of carrying a person (3) capable of being self-propelled Park X Error of "formalism" or "literalism"
Hart's penumbral case Law: No vehicles may be driven in the park. Vehicle: (1) normally driven on land (2) capable of carrying a person (3) capable of being self-propelled Park X Error of "formalism" or "literalism"
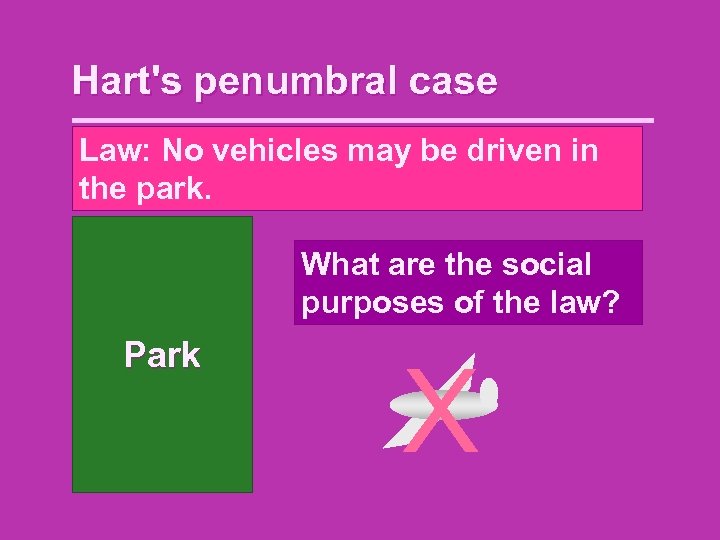 Hart's penumbral case Law: No vehicles may be driven in the park. What are the social purposes of the law? Park X
Hart's penumbral case Law: No vehicles may be driven in the park. What are the social purposes of the law? Park X
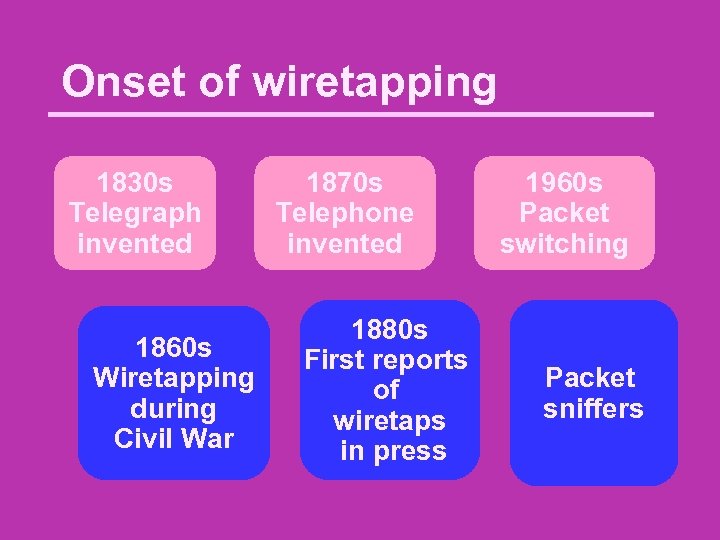 Onset of wiretapping 1830 s Telegraph invented 1860 s Wiretapping during Civil War 1870 s Telephone invented 1880 s First reports of wiretaps in press 1960 s Packet switching Packet sniffers
Onset of wiretapping 1830 s Telegraph invented 1860 s Wiretapping during Civil War 1870 s Telephone invented 1880 s First reports of wiretaps in press 1960 s Packet switching Packet sniffers
 Olmstead v. United States (1928) AMENDMENT XVIII Passed by Congress December 18, 1917. Ratified January 16, 1919. Repealed by amendment 21. Section 1. After one year from the ratification of this article the manufacture, sale, or transportation of intoxicating liquors within, the importation thereof into, or the exportation thereof from the United States and all territory subject to the jurisdiction thereof for beverage purposes is hereby prohibited.
Olmstead v. United States (1928) AMENDMENT XVIII Passed by Congress December 18, 1917. Ratified January 16, 1919. Repealed by amendment 21. Section 1. After one year from the ratification of this article the manufacture, sale, or transportation of intoxicating liquors within, the importation thereof into, or the exportation thereof from the United States and all territory subject to the jurisdiction thereof for beverage purposes is hereby prohibited.
 Olmstead v. United States (1928) Bootleggers >$176, 000 per month Evidence against them was obtained by wiretapping Convicted of a conspiracy to violate the National Prohibition Act
Olmstead v. United States (1928) Bootleggers >$176, 000 per month Evidence against them was obtained by wiretapping Convicted of a conspiracy to violate the National Prohibition Act
 Olmstead v. United States Question before the Court: Is warrantless wiretapping an illegal search and seizure and thus banned under the Fourth Amendment?
Olmstead v. United States Question before the Court: Is warrantless wiretapping an illegal search and seizure and thus banned under the Fourth Amendment?
 Fourth Amendment The right of the people to be secure in their persons, houses, papers, and effects, against unreasonable searches and seizures, shall not be violated, and no Warrants shall issue, but upon probable cause, supported by Oath or affirmation, and particularly describing the place to be searched, and the persons or things to be seized.
Fourth Amendment The right of the people to be secure in their persons, houses, papers, and effects, against unreasonable searches and seizures, shall not be violated, and no Warrants shall issue, but upon probable cause, supported by Oath or affirmation, and particularly describing the place to be searched, and the persons or things to be seized.
 Olmstead v. United States (1928) The reasonable view is that one who installs in his house a telephone instrument with connecting wires intends to project his voice to those quite outside, and that the wires beyond his house and messages while passing over them are not within the protection of the Fourth Amendment. Here those who intercepted the projected voices were not in the house of either party to the conversation. We think, therefore, that the wire tapping here disclosed did not amount to a search or seizure within the meaning of the Fourth Amendment. Mr. Chief Justice Taft
Olmstead v. United States (1928) The reasonable view is that one who installs in his house a telephone instrument with connecting wires intends to project his voice to those quite outside, and that the wires beyond his house and messages while passing over them are not within the protection of the Fourth Amendment. Here those who intercepted the projected voices were not in the house of either party to the conversation. We think, therefore, that the wire tapping here disclosed did not amount to a search or seizure within the meaning of the Fourth Amendment. Mr. Chief Justice Taft
 Olmstead v. United States (1928) Purpose of Fourth Amendment (Justice Taft) The well known historical purpose of the Fourth Amendment, directed against general warrants and writs of assistance, was to prevent the use of governmental force to search a man’s house, his papers and effects; and to prevent their seizure against his will. … The Amendment itself shows that the search is to be of material things…. Mr. Chief Justice Taft
Olmstead v. United States (1928) Purpose of Fourth Amendment (Justice Taft) The well known historical purpose of the Fourth Amendment, directed against general warrants and writs of assistance, was to prevent the use of governmental force to search a man’s house, his papers and effects; and to prevent their seizure against his will. … The Amendment itself shows that the search is to be of material things…. Mr. Chief Justice Taft
 Olmstead v. United States (1928) Purpose of Fourth Amendment (Justice Brandeis in dissent) The protection guaranteed by the Amendments is much broader in scope. The makers of our Constitution undertook to secure conditions favorable to the pursuit of happiness. … They knew that only a part of the pain, pleasure and satisfactions of life are to be found in material things. They sought to protect Americans in their beliefs, their thoughts, their emotions and their sensations.
Olmstead v. United States (1928) Purpose of Fourth Amendment (Justice Brandeis in dissent) The protection guaranteed by the Amendments is much broader in scope. The makers of our Constitution undertook to secure conditions favorable to the pursuit of happiness. … They knew that only a part of the pain, pleasure and satisfactions of life are to be found in material things. They sought to protect Americans in their beliefs, their thoughts, their emotions and their sensations.
 Olmstead v. United States (1928) Purpose of Fourth Amendment (Justice Brandeis in dissent) They conferred, as against the Government, the right to be let alone -- the most comprehensive of rights and the right most valued by civilized men. To protect that right, every unjustifiable intrusion by the Government upon the privacy of the individual, whatever the means employed, must be deemed a violation of the Fourth Amendment. Justice Brandeis
Olmstead v. United States (1928) Purpose of Fourth Amendment (Justice Brandeis in dissent) They conferred, as against the Government, the right to be let alone -- the most comprehensive of rights and the right most valued by civilized men. To protect that right, every unjustifiable intrusion by the Government upon the privacy of the individual, whatever the means employed, must be deemed a violation of the Fourth Amendment. Justice Brandeis
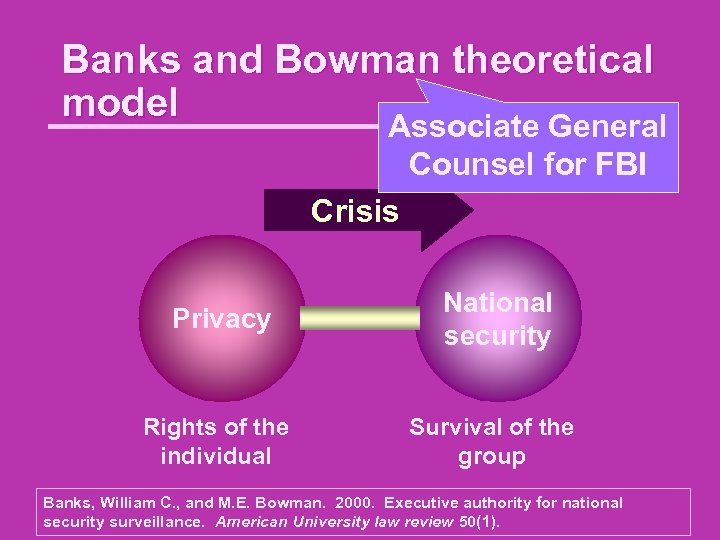 Banks and Bowman theoretical model Associate General Counsel for FBI Crisis Privacy National security Rights of the individual Survival of the group Banks, William C. , and M. E. Bowman. 2000. Executive authority for national security surveillance. American University law review 50(1).
Banks and Bowman theoretical model Associate General Counsel for FBI Crisis Privacy National security Rights of the individual Survival of the group Banks, William C. , and M. E. Bowman. 2000. Executive authority for national security surveillance. American University law review 50(1).
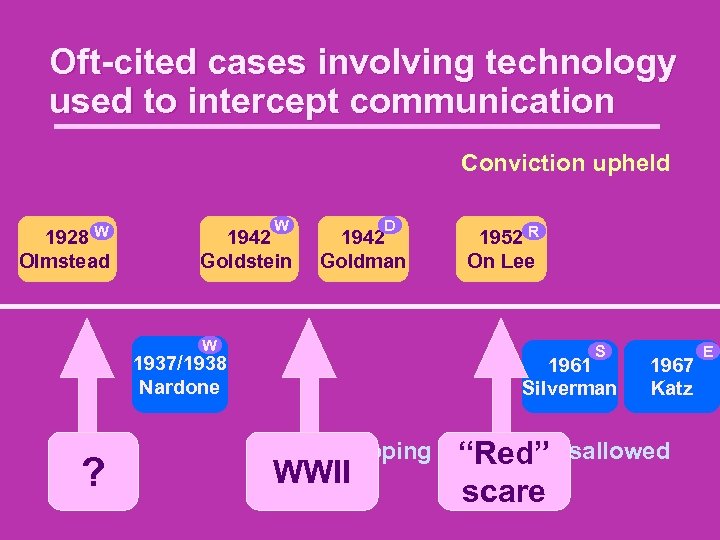 Oft-cited cases involving technology used to intercept communication Conviction upheld W 1928 Olmstead W 1942 Goldstein 1942 Goldman W 1952 R On Lee S 1937/1938 Nardone ? D 1961 Silverman 1967 Katz Wiretapping evidence disallowed “Red” WWII scare E
Oft-cited cases involving technology used to intercept communication Conviction upheld W 1928 Olmstead W 1942 Goldstein 1942 Goldman W 1952 R On Lee S 1937/1938 Nardone ? D 1961 Silverman 1967 Katz Wiretapping evidence disallowed “Red” WWII scare E
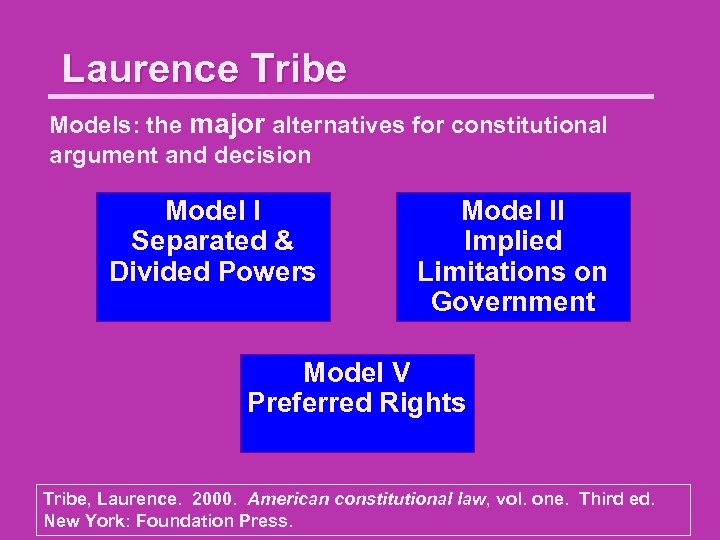 Laurence Tribe Models: the major alternatives for constitutional argument and decision Model I Separated & Divided Powers Model II Implied Limitations on Government Model V Preferred Rights Tribe, Laurence. 2000. American constitutional law, vol. one. Third ed. New York: Foundation Press.
Laurence Tribe Models: the major alternatives for constitutional argument and decision Model I Separated & Divided Powers Model II Implied Limitations on Government Model V Preferred Rights Tribe, Laurence. 2000. American constitutional law, vol. one. Third ed. New York: Foundation Press.
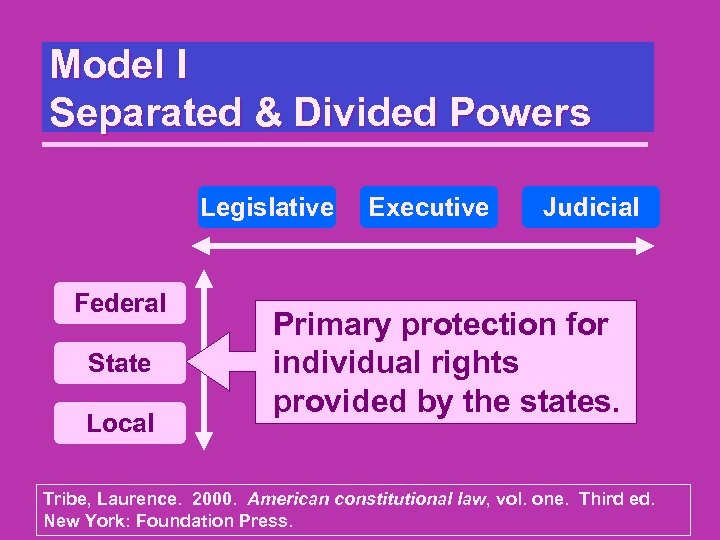 Model I Separated & Divided Powers Legislative Federal State Local Executive Judicial Primary protection for individual rights provided by the states. Tribe, Laurence. 2000. American constitutional law, vol. one. Third ed. New York: Foundation Press.
Model I Separated & Divided Powers Legislative Federal State Local Executive Judicial Primary protection for individual rights provided by the states. Tribe, Laurence. 2000. American constitutional law, vol. one. Third ed. New York: Foundation Press.
 Model II Implied Limitations on Gov’t Emphasis on preserving the “natural order” of society. Major role of the court was to restore natural order upset by state legislation. Tribe, Laurence. 2000. American constitutional law, vol. one. Third ed. New York: Foundation Press.
Model II Implied Limitations on Gov’t Emphasis on preserving the “natural order” of society. Major role of the court was to restore natural order upset by state legislation. Tribe, Laurence. 2000. American constitutional law, vol. one. Third ed. New York: Foundation Press.
 Model II (Decline) Concern for the underprivileged No natural order to be restored Need for positive governmental intervention to alleviate suffering Tribe, Laurence. 2000. American constitutional law, vol. one. Third ed. New York: Foundation Press.
Model II (Decline) Concern for the underprivileged No natural order to be restored Need for positive governmental intervention to alleviate suffering Tribe, Laurence. 2000. American constitutional law, vol. one. Third ed. New York: Foundation Press.
 Model V Preferred Rights Exclude governmental powers from certain spheres Identification of “preferred freedoms” Tribe, Laurence. 2000. American constitutional law, vol. one. Third ed. New York: Foundation Press.
Model V Preferred Rights Exclude governmental powers from certain spheres Identification of “preferred freedoms” Tribe, Laurence. 2000. American constitutional law, vol. one. Third ed. New York: Foundation Press.
 Model V Preferred Rights Emphasis on rights of: • Communication and expression • Political participation • Religious autonomy • Privacy and personhood Tribe, Laurence. 2000. American constitutional law, vol. one. Third ed. New York: Foundation Press.
Model V Preferred Rights Emphasis on rights of: • Communication and expression • Political participation • Religious autonomy • Privacy and personhood Tribe, Laurence. 2000. American constitutional law, vol. one. Third ed. New York: Foundation Press.
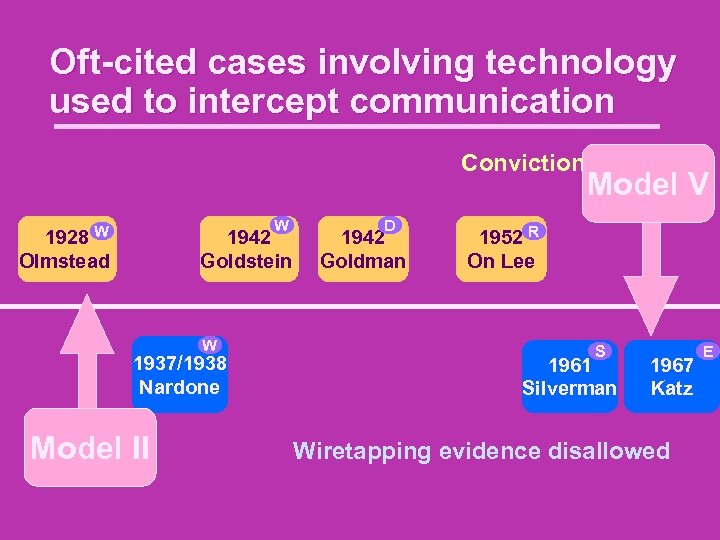 Oft-cited cases involving technology used to intercept communication Conviction upheld Model V W W 1928 Olmstead 1942 Goldstein W 1937/1938 Nardone Model II D 1942 Goldman 1952 R On Lee S 1961 Silverman 1967 Katz Wiretapping evidence disallowed E
Oft-cited cases involving technology used to intercept communication Conviction upheld Model V W W 1928 Olmstead 1942 Goldstein W 1937/1938 Nardone Model II D 1942 Goldman 1952 R On Lee S 1961 Silverman 1967 Katz Wiretapping evidence disallowed E
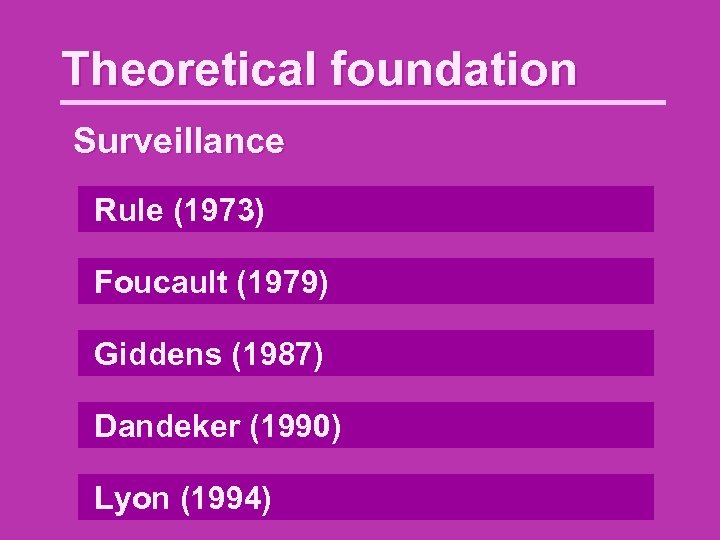 Theoretical foundation Surveillance Rule (1973) Foucault (1979) Giddens (1987) Dandeker (1990) Lyon (1994)
Theoretical foundation Surveillance Rule (1973) Foucault (1979) Giddens (1987) Dandeker (1990) Lyon (1994)
 Role of surveillance • Provision of services • Allows participation • Protection against threat • Means of social control • Discover and rout deviance • Threat of surveillance used to promote compliance with the law
Role of surveillance • Provision of services • Allows participation • Protection against threat • Means of social control • Discover and rout deviance • Threat of surveillance used to promote compliance with the law
 Privacy theories Alan F. Westin Irwin Altman Sandra Petronio
Privacy theories Alan F. Westin Irwin Altman Sandra Petronio
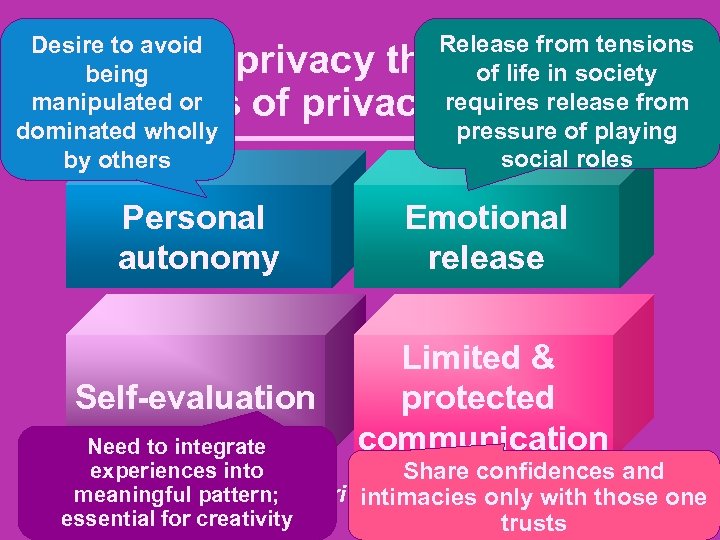 Desire to avoid being manipulated or dominated wholly by others Release from tensions of life in society requires release from pressure of playing social roles Westin's privacy theory: 4 functions of privacy Personal autonomy Emotional release Self-evaluation Limited & protected communication Need to integrate experiences into Share confidences and meaningful pattern; Westin, Alan F. 1970. Privacy and freedom. London: intimacies only with those one essential for creativity trusts Bodley Head.
Desire to avoid being manipulated or dominated wholly by others Release from tensions of life in society requires release from pressure of playing social roles Westin's privacy theory: 4 functions of privacy Personal autonomy Emotional release Self-evaluation Limited & protected communication Need to integrate experiences into Share confidences and meaningful pattern; Westin, Alan F. 1970. Privacy and freedom. London: intimacies only with those one essential for creativity trusts Bodley Head.
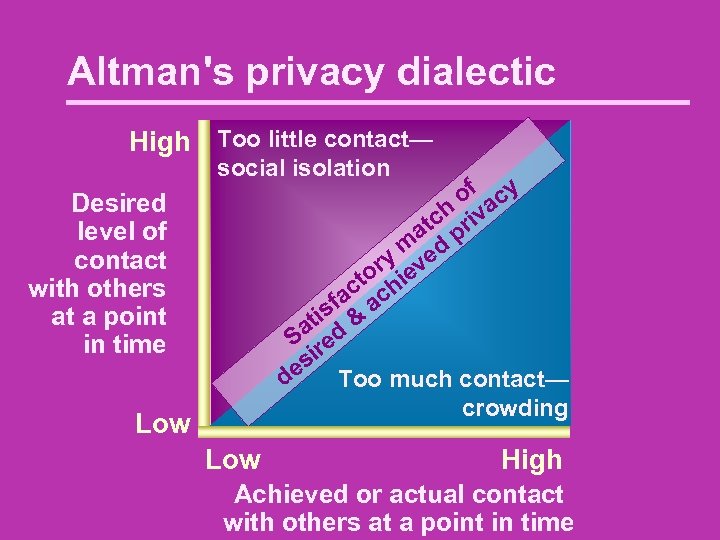 Altman's privacy dialectic High Too little contact— social isolation of acy h iv tc pr a m ed y v r to hie ac ac f is & at d S re si de Too much contact— crowding Desired level of contact with others at a point in time Low High Achieved or actual contact with others at a point in time
Altman's privacy dialectic High Too little contact— social isolation of acy h iv tc pr a m ed y v r to hie ac ac f is & at d S re si de Too much contact— crowding Desired level of contact with others at a point in time Low High Achieved or actual contact with others at a point in time
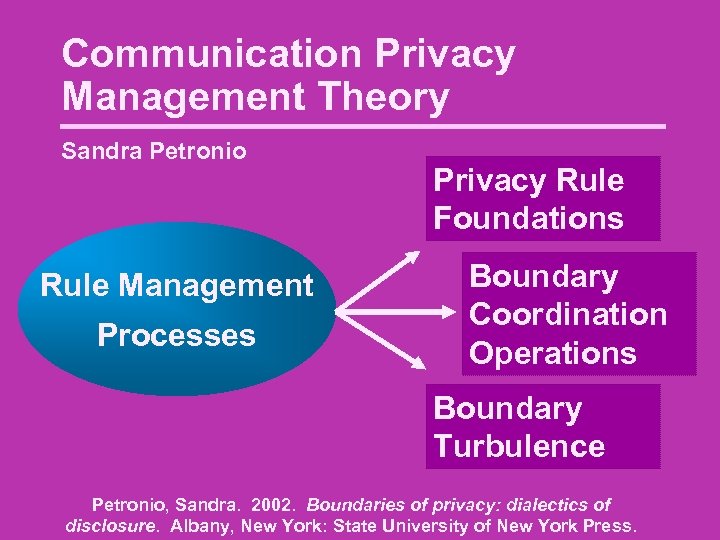 Communication Privacy Management Theory Sandra Petronio Rule Management Processes Privacy Rule Foundations Boundary Coordination Operations Boundary Turbulence Petronio, Sandra. 2002. Boundaries of privacy: dialectics of disclosure. Albany, New York: State University of New York Press.
Communication Privacy Management Theory Sandra Petronio Rule Management Processes Privacy Rule Foundations Boundary Coordination Operations Boundary Turbulence Petronio, Sandra. 2002. Boundaries of privacy: dialectics of disclosure. Albany, New York: State University of New York Press.
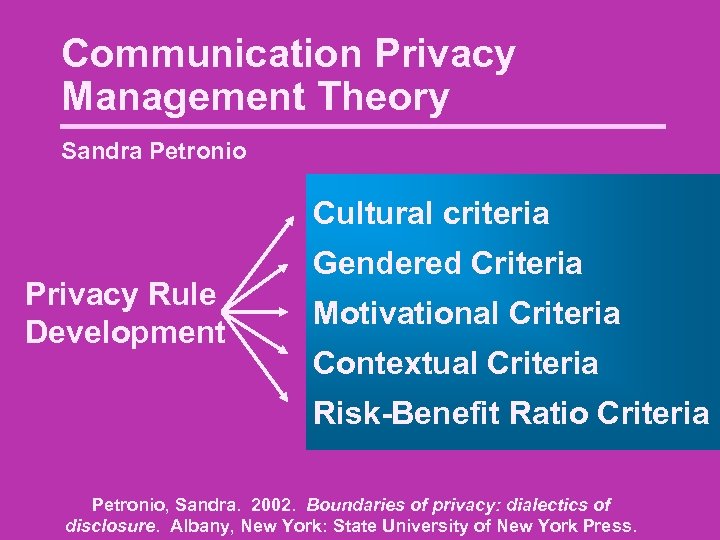 Communication Privacy Management Theory Sandra Petronio Cultural criteria Privacy Rule Development Gendered Criteria Motivational Criteria Contextual Criteria Risk-Benefit Ratio Criteria Petronio, Sandra. 2002. Boundaries of privacy: dialectics of disclosure. Albany, New York: State University of New York Press.
Communication Privacy Management Theory Sandra Petronio Cultural criteria Privacy Rule Development Gendered Criteria Motivational Criteria Contextual Criteria Risk-Benefit Ratio Criteria Petronio, Sandra. 2002. Boundaries of privacy: dialectics of disclosure. Albany, New York: State University of New York Press.
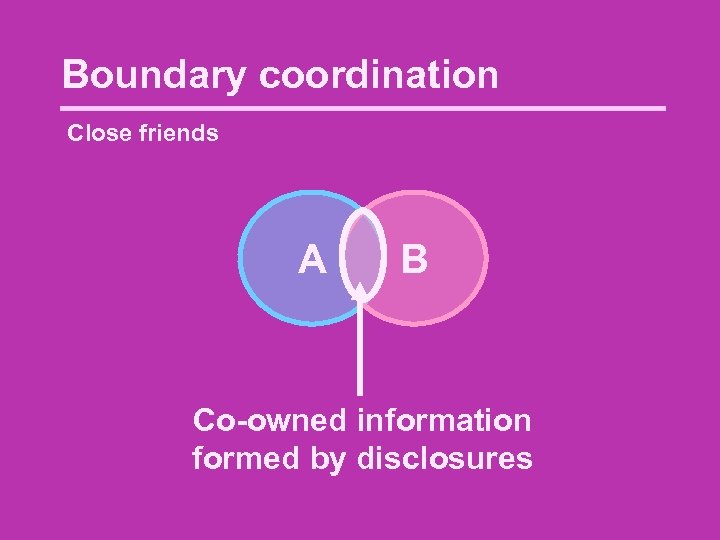 Boundary coordination Close friends A B Co-owned information formed by disclosures
Boundary coordination Close friends A B Co-owned information formed by disclosures
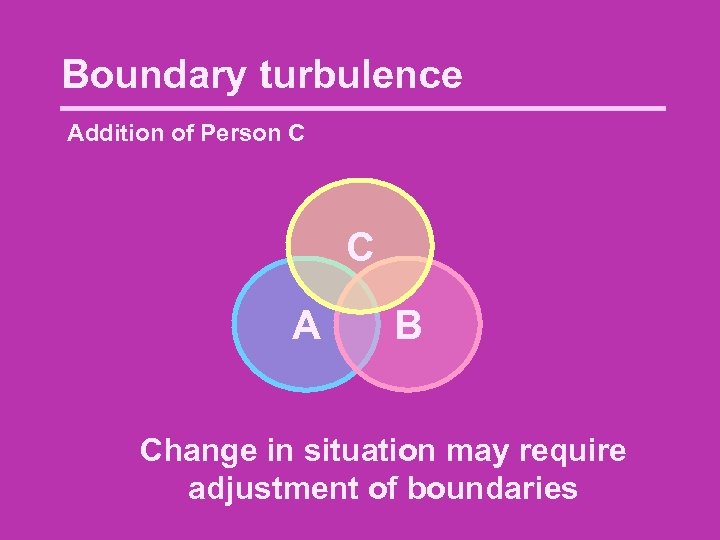 Boundary turbulence Addition of Person C C A B Change in situation may require adjustment of boundaries
Boundary turbulence Addition of Person C C A B Change in situation may require adjustment of boundaries
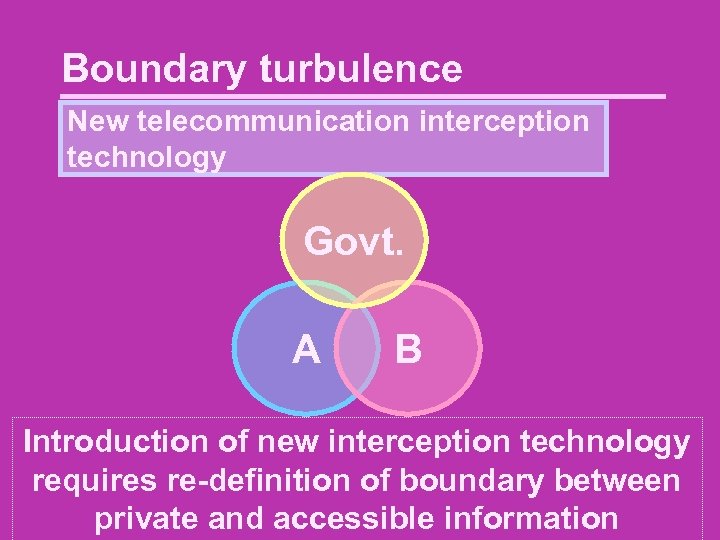 Boundary turbulence New telecommunication interception technology Govt. A B Introduction of new interception technology requires re-definition of boundary between private and accessible information
Boundary turbulence New telecommunication interception technology Govt. A B Introduction of new interception technology requires re-definition of boundary between private and accessible information
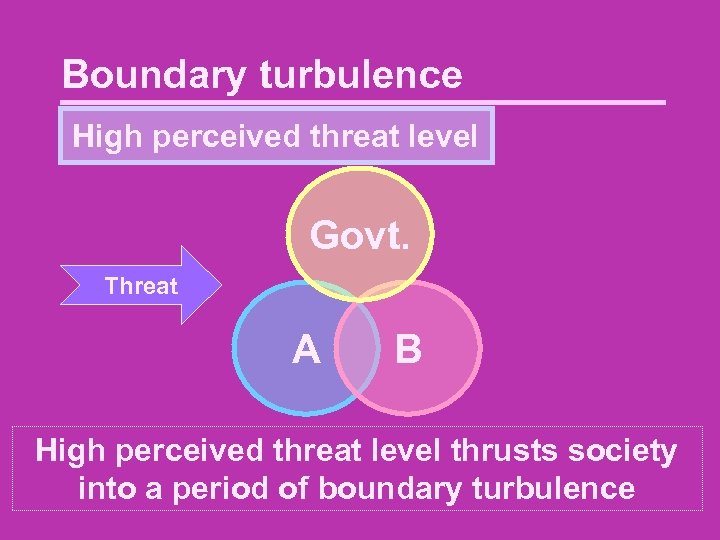 Boundary turbulence High perceived threat level Govt. Threat A B High perceived threat level thrusts society into a period of boundary turbulence
Boundary turbulence High perceived threat level Govt. Threat A B High perceived threat level thrusts society into a period of boundary turbulence
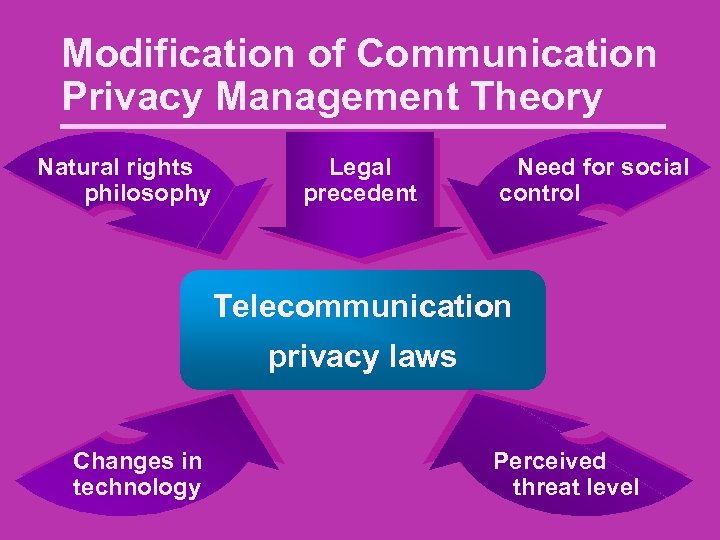 Modification of Communication Privacy Management Theory Natural rights philosophy Legal precedent Need for social control Telecommunication privacy laws Changes in technology Perceived threat level
Modification of Communication Privacy Management Theory Natural rights philosophy Legal precedent Need for social control Telecommunication privacy laws Changes in technology Perceived threat level
 Questions ?
Questions ?
 Mahalo
Mahalo
 Additional terms of interest discourse (lower case “d”) Language-in-use or stretches of languages (like conversations or stories) Discourse (upper case “D”) Language and non-language elements (symbols, tools, objects) used to enact and recognize different identities and activities. Societal or community-level. Represented and enacted by individuals in a variety of settings over time. E. g. physics as a scientific Discourse.
Additional terms of interest discourse (lower case “d”) Language-in-use or stretches of languages (like conversations or stories) Discourse (upper case “D”) Language and non-language elements (symbols, tools, objects) used to enact and recognize different identities and activities. Societal or community-level. Represented and enacted by individuals in a variety of settings over time. E. g. physics as a scientific Discourse.
 Congressional debate through the eyes of a religion major Ritual that includes stylized discourse (lower case “d”) that often makes reference to Discourses (upper case “D”)
Congressional debate through the eyes of a religion major Ritual that includes stylized discourse (lower case “d”) that often makes reference to Discourses (upper case “D”)
 HR 3162 House Discussion (Oct. 23, 2001) Some of us, who have a different history in America, with delegation of authority to the Government and the abuse of that authority, proceed a lot differently than others when we talk about giving authority to the Government that can be abused. And I think that is why we are having so much trouble in this debate. We cannot just come in the middle of a terrorism episode and forget all of the history that has occurred in our country.
HR 3162 House Discussion (Oct. 23, 2001) Some of us, who have a different history in America, with delegation of authority to the Government and the abuse of that authority, proceed a lot differently than others when we talk about giving authority to the Government that can be abused. And I think that is why we are having so much trouble in this debate. We cannot just come in the middle of a terrorism episode and forget all of the history that has occurred in our country.
 HR 3162 House Discussion (Oct. 23, 2001) Some groups in our country have had their rights violated, trampled on by the law enforcement authorities in this country; and so we do not have the luxury of being able to just sit back and give more authority than is warranted, the authority possibly to abuse due process through law enforcement, even in the context of what we are going through now. This is a very difficult time. I acknowledge that it is. But I think we are Reference to giving the Government and law Civil Rights enforcement too much authority in this Discourse bill.
HR 3162 House Discussion (Oct. 23, 2001) Some groups in our country have had their rights violated, trampled on by the law enforcement authorities in this country; and so we do not have the luxury of being able to just sit back and give more authority than is warranted, the authority possibly to abuse due process through law enforcement, even in the context of what we are going through now. This is a very difficult time. I acknowledge that it is. But I think we are Reference to giving the Government and law Civil Rights enforcement too much authority in this Discourse bill.
 Societal good Privacy isn't just for the good of the individual. Necessary component of a functioning society. Need privacy to form and maintain intimate relationships. These relationships in turn provide the ties that bind society together. Also liberal notion that in populist government need creativity, fostered by privacy. See John Stuart Mill.
Societal good Privacy isn't just for the good of the individual. Necessary component of a functioning society. Need privacy to form and maintain intimate relationships. These relationships in turn provide the ties that bind society together. Also liberal notion that in populist government need creativity, fostered by privacy. See John Stuart Mill.
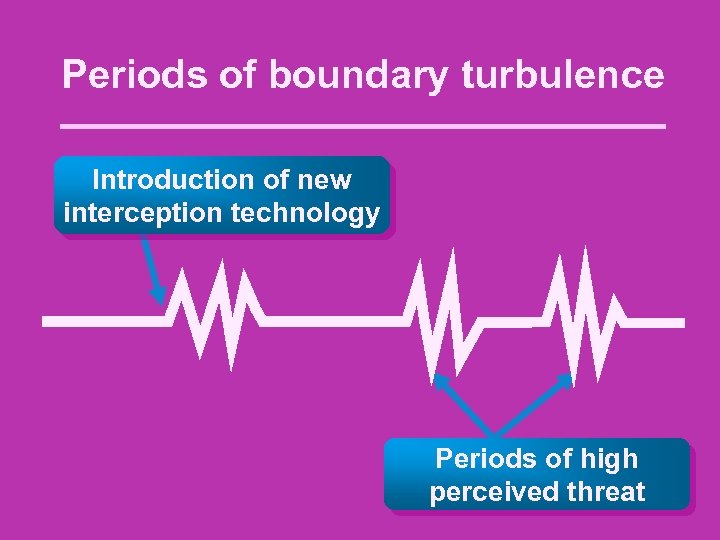 Periods of boundary turbulence Introduction of new interception technology Periods of high perceived threat
Periods of boundary turbulence Introduction of new interception technology Periods of high perceived threat
 R. M. Dworkin Rule Applicable in an all-or-nothing fashion. If the facts a rule stipulates are given, then either the rule is valid, in which case the answer it supplies must be accepted, or it is not, in which case it contributes nothing to the discussion. Principle States a reason that argues in one direction, but does not necessitate a particular decision. Dworkin, R. M. (ed. ). 1977. The philosophy of law. London: Oxford University Press.
R. M. Dworkin Rule Applicable in an all-or-nothing fashion. If the facts a rule stipulates are given, then either the rule is valid, in which case the answer it supplies must be accepted, or it is not, in which case it contributes nothing to the discussion. Principle States a reason that argues in one direction, but does not necessitate a particular decision. Dworkin, R. M. (ed. ). 1977. The philosophy of law. London: Oxford University Press.
 R. M. Dworkin’s definition of a principle “I call a ‘principle’ a standard that is to be observed, not because it will advance or secure an economic, political, or social situation deemed desirable, but because it is a requirement of justice or fairness or some other dimension of morality. ” Dworkin, R. M. (ed. ). 1977. The philosophy of law. London: Oxford University Press.
R. M. Dworkin’s definition of a principle “I call a ‘principle’ a standard that is to be observed, not because it will advance or secure an economic, political, or social situation deemed desirable, but because it is a requirement of justice or fairness or some other dimension of morality. ” Dworkin, R. M. (ed. ). 1977. The philosophy of law. London: Oxford University Press.
 R. M. Dworkin’s theory of fundamental principles Man murdered his grandfather Murderer tried to collect inheritance Judge ruled that murderer could not receive his inheritance despite being named in the will—ruling based on fundamental principle of law that person shouldn’t benefit from crime Dworkin, R. M. (ed. ). 1977. The philosophy of law. London: Oxford University Press. Case: Riggs v. Palmer 115 N. Y. 506 (1889)
R. M. Dworkin’s theory of fundamental principles Man murdered his grandfather Murderer tried to collect inheritance Judge ruled that murderer could not receive his inheritance despite being named in the will—ruling based on fundamental principle of law that person shouldn’t benefit from crime Dworkin, R. M. (ed. ). 1977. The philosophy of law. London: Oxford University Press. Case: Riggs v. Palmer 115 N. Y. 506 (1889)
 Question of interest Was there any indication that a fundamental principle was at stake in the majority decision in Olmstead?
Question of interest Was there any indication that a fundamental principle was at stake in the majority decision in Olmstead?
 Olmstead v. United States (1928) The evidence in the records discloses a conspiracy of amazing magnitude…. It involved the employment of not less than fifty persons, of two seagoing vessels for the transportation of liquor to British Columbia, of smaller vessels for coastwise transportation to the State of Washington. … In a bad month sales amounted to $176, 000; the aggregate for a year must have exceeded two millions of dollars. Mr. Chief Justice Taft
Olmstead v. United States (1928) The evidence in the records discloses a conspiracy of amazing magnitude…. It involved the employment of not less than fifty persons, of two seagoing vessels for the transportation of liquor to British Columbia, of smaller vessels for coastwise transportation to the State of Washington. … In a bad month sales amounted to $176, 000; the aggregate for a year must have exceeded two millions of dollars. Mr. Chief Justice Taft
 Individual privacy versus individual secrecy Privacy Allowed and in some cases required for socially-sanctioned acts. Stress reducing. Secrecy Often involves socially proscribed acts. Stress inducing. Margulis, Stephen T. 1977. Conceptions of privacy: current status and next steps. Journal of social issues 33(3): 5 -21, p. 10. Margulis, Stephen T. 2003. Privacy as a social issue and behavioral concept. Journal of social issues 59(2): 243 -261.
Individual privacy versus individual secrecy Privacy Allowed and in some cases required for socially-sanctioned acts. Stress reducing. Secrecy Often involves socially proscribed acts. Stress inducing. Margulis, Stephen T. 1977. Conceptions of privacy: current status and next steps. Journal of social issues 33(3): 5 -21, p. 10. Margulis, Stephen T. 2003. Privacy as a social issue and behavioral concept. Journal of social issues 59(2): 243 -261.
 Model I Separated & Divided Powers All lawful power derives from the people and must be held in check to preserve their freedom. Centralized accumulation of power in any person or single group of persons results in tyranny Tribe, Laurence. 2000. American constitutional law, vol. one. Third ed. New York: Foundation Press.
Model I Separated & Divided Powers All lawful power derives from the people and must be held in check to preserve their freedom. Centralized accumulation of power in any person or single group of persons results in tyranny Tribe, Laurence. 2000. American constitutional law, vol. one. Third ed. New York: Foundation Press.
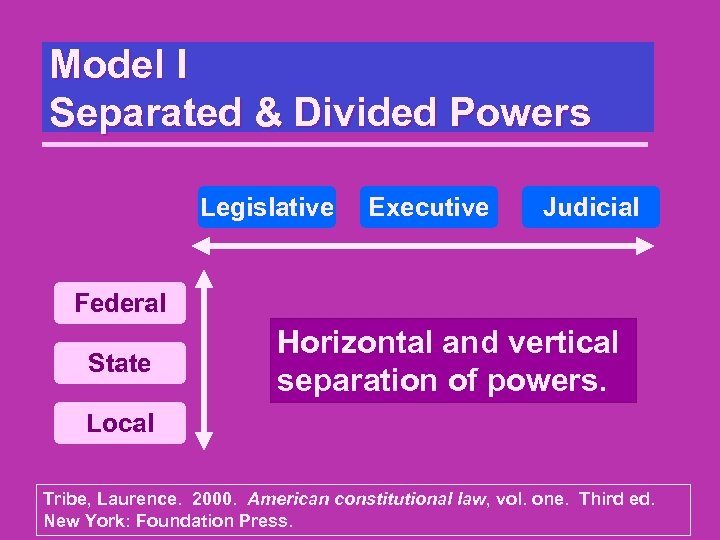 Model I Separated & Divided Powers Legislative Executive Judicial Federal State Horizontal and vertical separation of powers. Local Tribe, Laurence. 2000. American constitutional law, vol. one. Third ed. New York: Foundation Press.
Model I Separated & Divided Powers Legislative Executive Judicial Federal State Horizontal and vertical separation of powers. Local Tribe, Laurence. 2000. American constitutional law, vol. one. Third ed. New York: Foundation Press.
 Model II Implied Limitations on Governmental regulations must promote the general welfare, not promote private interests Tribe, Laurence. 2000. American constitutional law, vol. one. Third ed. New York: Foundation Press.
Model II Implied Limitations on Governmental regulations must promote the general welfare, not promote private interests Tribe, Laurence. 2000. American constitutional law, vol. one. Third ed. New York: Foundation Press.
 Question of interest Can we utilize Communications Privacy Management Theory in general and the concept of "boundary turbulence" in particular to model the development of laws regulating the use of telecommunication interception technology?
Question of interest Can we utilize Communications Privacy Management Theory in general and the concept of "boundary turbulence" in particular to model the development of laws regulating the use of telecommunication interception technology?
 Terms of interest Constitution—fundamental law of the nation Statutory law (also termed legislative law) Case law—Collection of reported cases that form the body of law within a given jurisdiction Agency-made law—administrative rules and regulations
Terms of interest Constitution—fundamental law of the nation Statutory law (also termed legislative law) Case law—Collection of reported cases that form the body of law within a given jurisdiction Agency-made law—administrative rules and regulations
 Informational privacy - Westin's definition - part 1 Privacy is the claim of individuals, groups, or institutions to determine for themselves when, how, and to what extent information about them is communicated to others. Westin, Alan F. 1970. Privacy and freedom. London: Bodley Head.
Informational privacy - Westin's definition - part 1 Privacy is the claim of individuals, groups, or institutions to determine for themselves when, how, and to what extent information about them is communicated to others. Westin, Alan F. 1970. Privacy and freedom. London: Bodley Head.
 Informational privacy - Westin's definition - part 2 Viewed in terms of the relation of the individual to social participation, privacy is the voluntary and temporary withdrawal of a person from the general society through physical or psychological means, either in a state of solitude or, when among larger groups, in a condition of anonymity or reserve.
Informational privacy - Westin's definition - part 2 Viewed in terms of the relation of the individual to social participation, privacy is the voluntary and temporary withdrawal of a person from the general society through physical or psychological means, either in a state of solitude or, when among larger groups, in a condition of anonymity or reserve.
 Informational privacy - Westin's definition - part 3 The individual's desire for privacy is never absolute, since participation in society is an equally powerful desire.
Informational privacy - Westin's definition - part 3 The individual's desire for privacy is never absolute, since participation in society is an equally powerful desire.
 Informational privacy - Westin's definition - part 4 Thus each individual is continually engaged in a personal adjustment process in which he balances the desire for privacy with the desire for disclosure and communication of himself to others, in light of the environmental conditions and social norms set by the society in which he lives.
Informational privacy - Westin's definition - part 4 Thus each individual is continually engaged in a personal adjustment process in which he balances the desire for privacy with the desire for disclosure and communication of himself to others, in light of the environmental conditions and social norms set by the society in which he lives.
 Informational privacy - Westin's definition - part 5 The individual does so in the face of pressures from the curiosity of others and from the processes of surveillance that every society sets in order to enforce its social norms.
Informational privacy - Westin's definition - part 5 The individual does so in the face of pressures from the curiosity of others and from the processes of surveillance that every society sets in order to enforce its social norms.
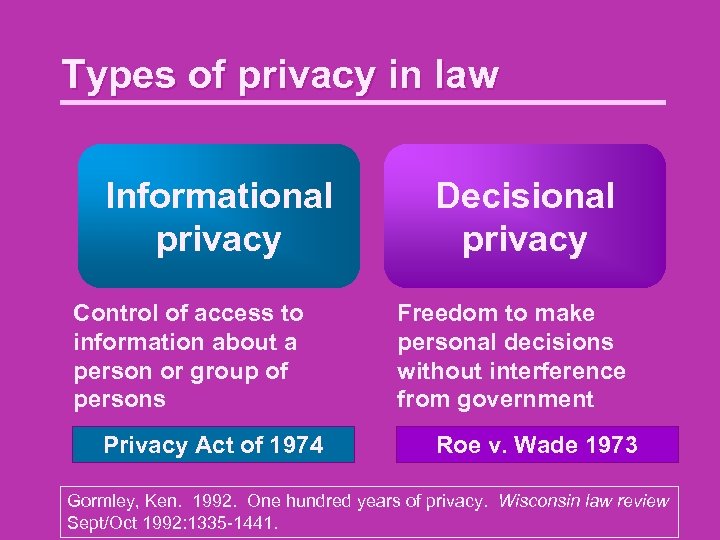 Types of privacy in law Informational privacy Control of access to information about a person or group of persons Privacy Act of 1974 Decisional privacy Freedom to make personal decisions without interference from government Roe v. Wade 1973 Gormley, Ken. 1992. One hundred years of privacy. Wisconsin law review Sept/Oct 1992: 1335 -1441.
Types of privacy in law Informational privacy Control of access to information about a person or group of persons Privacy Act of 1974 Decisional privacy Freedom to make personal decisions without interference from government Roe v. Wade 1973 Gormley, Ken. 1992. One hundred years of privacy. Wisconsin law review Sept/Oct 1992: 1335 -1441.
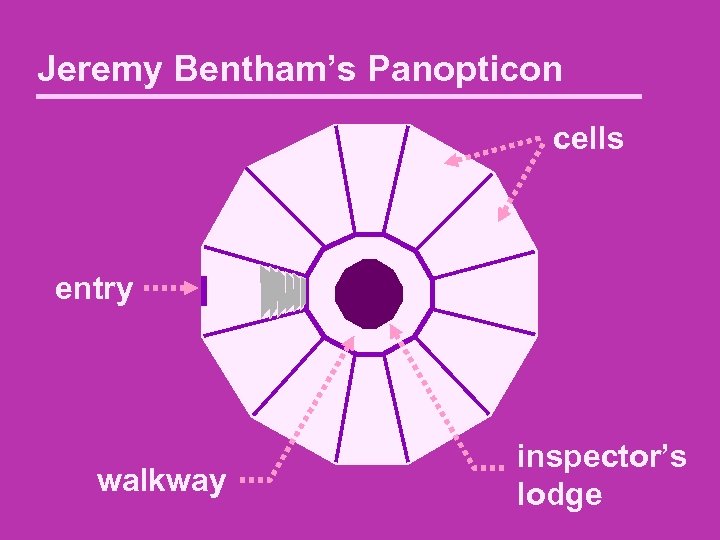 Jeremy Bentham’s Panopticon cells entry walkway inspector’s lodge
Jeremy Bentham’s Panopticon cells entry walkway inspector’s lodge


