717b74ccc8b58f1fb0cbc4a001efb66e.ppt
- Количество слайдов: 26
 Consorzio COMETA - Progetto PI 2 S 2 FESR Authorization and Authentication Marcello Iacono-Manno Catania, 23 gennaio 2008 Grid Open Day ai Laboratori Nazionali del Sud www. consorzio-cometa. it
Consorzio COMETA - Progetto PI 2 S 2 FESR Authorization and Authentication Marcello Iacono-Manno Catania, 23 gennaio 2008 Grid Open Day ai Laboratori Nazionali del Sud www. consorzio-cometa. it
 Outline • Glossary • Encryption – Symmetric algorithms – Asymmetric algorithms: PKI • Certification Authorities – Digital Signatures – X 509 certificates • Grid Security – Basic concepts – Grid Security Infrastructure – Proxy certificates – Commands used in UI • Virtual Organization – Concept of VO and authorization – VOMS, LCAS, LCMAPS Grid Open Day at LNS, Catania, 2008, January 23 rd 2
Outline • Glossary • Encryption – Symmetric algorithms – Asymmetric algorithms: PKI • Certification Authorities – Digital Signatures – X 509 certificates • Grid Security – Basic concepts – Grid Security Infrastructure – Proxy certificates – Commands used in UI • Virtual Organization – Concept of VO and authorization – VOMS, LCAS, LCMAPS Grid Open Day at LNS, Catania, 2008, January 23 rd 2
 Glossary • Principal – An entity: a user, a program, or a machine • Credentials – Some data providing a proof of identity • Authentication – Verification of the identity for an end-entity • Authorization – Map an entity to some set of privileges • Confidentiality – Encrypt the message so that only the recipient can understand it • Integrity – Ensure that the message has not been altered during the transmission • Non-repudiation – Impossibility of denying the authenticity of a digital signature Grid Open Day at LNS, Catania, 2008, January 23 rd 3
Glossary • Principal – An entity: a user, a program, or a machine • Credentials – Some data providing a proof of identity • Authentication – Verification of the identity for an end-entity • Authorization – Map an entity to some set of privileges • Confidentiality – Encrypt the message so that only the recipient can understand it • Integrity – Ensure that the message has not been altered during the transmission • Non-repudiation – Impossibility of denying the authenticity of a digital signature Grid Open Day at LNS, Catania, 2008, January 23 rd 3
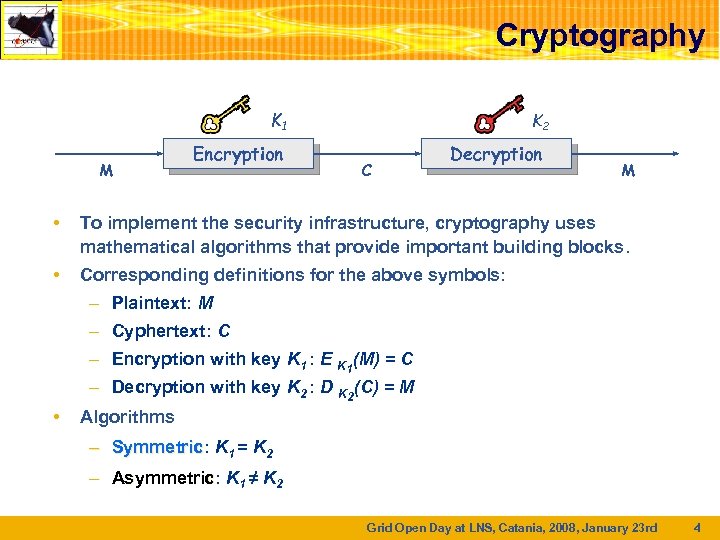 Cryptography K 1 M Encryption K 2 C Decryption M • To implement the security infrastructure, cryptography uses mathematical algorithms that provide important building blocks. • Corresponding definitions for the above symbols: – Plaintext: M – Cyphertext: C – Encryption with key K 1 : E K 1(M) = C – Decryption with key K 2 : D K 2(C) = M • Algorithms – Symmetric: K 1 = K 2 Symmetric – Asymmetric: K 1 ≠ K 2 Asymmetric Grid Open Day at LNS, Catania, 2008, January 23 rd 4
Cryptography K 1 M Encryption K 2 C Decryption M • To implement the security infrastructure, cryptography uses mathematical algorithms that provide important building blocks. • Corresponding definitions for the above symbols: – Plaintext: M – Cyphertext: C – Encryption with key K 1 : E K 1(M) = C – Decryption with key K 2 : D K 2(C) = M • Algorithms – Symmetric: K 1 = K 2 Symmetric – Asymmetric: K 1 ≠ K 2 Asymmetric Grid Open Day at LNS, Catania, 2008, January 23 rd 4
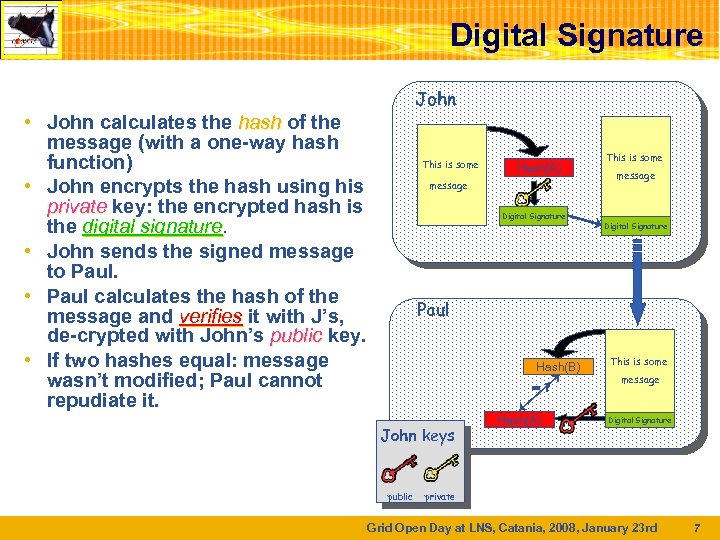 Digital Signature John • John calculates the hash of the message (with a one-way hash function) • John encrypts the hash using his private key: the encrypted hash is the digital signature • John sends the signed message to Paul. • Paul calculates the hash of the message and verifies it with J’s, de-crypted with John’s public key. • If two hashes equal: message wasn’t modified; Paul cannot repudiate it. This is some Hash(A) message Digital Signature This is some message Digital Signature Paul Hash(B) =? John keys public Hash(A) This is some message Digital Signature private Grid Open Day at LNS, Catania, 2008, January 23 rd 7
Digital Signature John • John calculates the hash of the message (with a one-way hash function) • John encrypts the hash using his private key: the encrypted hash is the digital signature • John sends the signed message to Paul. • Paul calculates the hash of the message and verifies it with J’s, de-crypted with John’s public key. • If two hashes equal: message wasn’t modified; Paul cannot repudiate it. This is some Hash(A) message Digital Signature This is some message Digital Signature Paul Hash(B) =? John keys public Hash(A) This is some message Digital Signature private Grid Open Day at LNS, Catania, 2008, January 23 rd 7
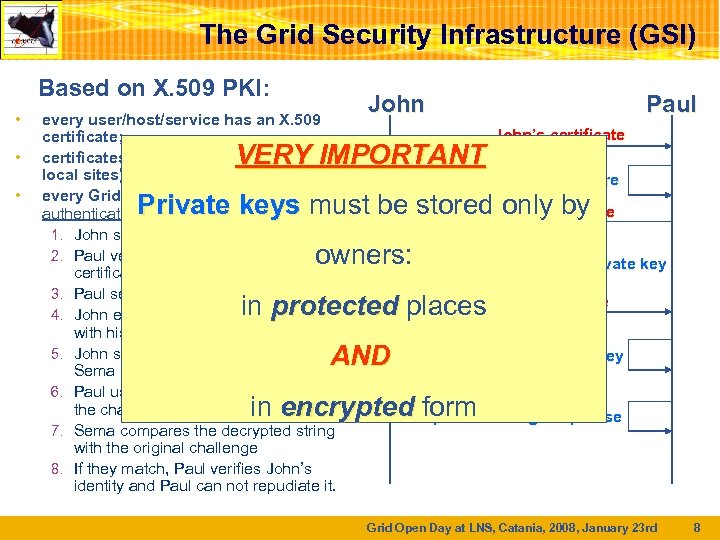 The Grid Security Infrastructure (GSI) Based on X. 509 PKI: • • • every user/host/service has an X. 509 certificate; certificates are signed by trusted (by the local sites) CA’s; every Grid transaction is mutually authenticated: 1. John sends his certificate; 2. Paul verifies signature in John’s certificate; 3. Paul sends John a challenge string; 4. John encrypts the challenge string with his private key; 5. John sends encrypted challenge to Sema 6. Paul uses John’s public key to decrypt the challenge. 7. Sema compares the decrypted string with the original challenge 8. If they match, Paul verifies John’s identity and Paul can not repudiate it. John Paul VERY IMPORTANT John’s certificate Verify CA signature Private keys must be stored. Random by only phrase owners: Encrypt with J. ’ s private key Encrypted phrase in protected places AND Decrypt with J. ’ s public key in encrypted form original phrase Compare with Grid Open Day at LNS, Catania, 2008, January 23 rd 8
The Grid Security Infrastructure (GSI) Based on X. 509 PKI: • • • every user/host/service has an X. 509 certificate; certificates are signed by trusted (by the local sites) CA’s; every Grid transaction is mutually authenticated: 1. John sends his certificate; 2. Paul verifies signature in John’s certificate; 3. Paul sends John a challenge string; 4. John encrypts the challenge string with his private key; 5. John sends encrypted challenge to Sema 6. Paul uses John’s public key to decrypt the challenge. 7. Sema compares the decrypted string with the original challenge 8. If they match, Paul verifies John’s identity and Paul can not repudiate it. John Paul VERY IMPORTANT John’s certificate Verify CA signature Private keys must be stored. Random by only phrase owners: Encrypt with J. ’ s private key Encrypted phrase in protected places AND Decrypt with J. ’ s public key in encrypted form original phrase Compare with Grid Open Day at LNS, Catania, 2008, January 23 rd 8
 Digital Certificates • John’s digital signature is safe if: 1. John’s private key is not compromised 2. Paul knows John’s public key • How can Paul be sure that John’s public key is really the John’s public key and not someone else? – A third party guarantees the correspondence between public key and owner’s identity. – Both parties must trust this third party • Two models proposed to build trust: – X. 509: hierarchical organization (used in Grid) – PGP: “web of trust”. (person to person) Grid Open Day at LNS, Catania, 2008, January 23 rd 9
Digital Certificates • John’s digital signature is safe if: 1. John’s private key is not compromised 2. Paul knows John’s public key • How can Paul be sure that John’s public key is really the John’s public key and not someone else? – A third party guarantees the correspondence between public key and owner’s identity. – Both parties must trust this third party • Two models proposed to build trust: – X. 509: hierarchical organization (used in Grid) – PGP: “web of trust”. (person to person) Grid Open Day at LNS, Catania, 2008, January 23 rd 9
 X. 509 and Certification Authorities The “third party” is called Certification Authority (CA). Responsibilities of CA: • Issue Digital Certificates (containing public key and owner’s identity) for users, programs and machines • Check identity and the personal data of the requestor – Registration Authorities (RAs) do the actual validation • Revoke certificates in case of abuse • Renew certificates in case of expiration • Periodically publish a list of revoked certificates through web repository – Certificate Revocation Lists (CRL): contain all the revoked certificates • CA certificates are self-signed Grid Open Day at LNS, Catania, 2008, January 23 rd 10
X. 509 and Certification Authorities The “third party” is called Certification Authority (CA). Responsibilities of CA: • Issue Digital Certificates (containing public key and owner’s identity) for users, programs and machines • Check identity and the personal data of the requestor – Registration Authorities (RAs) do the actual validation • Revoke certificates in case of abuse • Renew certificates in case of expiration • Periodically publish a list of revoked certificates through web repository – Certificate Revocation Lists (CRL): contain all the revoked certificates • CA certificates are self-signed Grid Open Day at LNS, Catania, 2008, January 23 rd 10
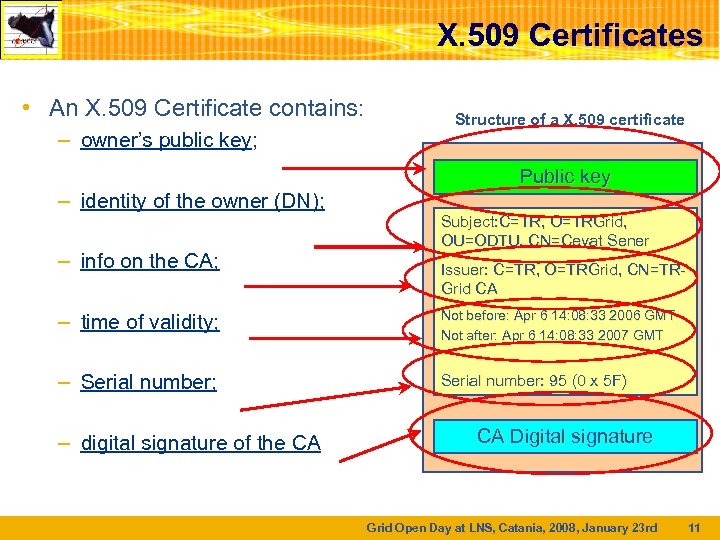 X. 509 Certificates • An X. 509 Certificate contains: – owner’s public key; – identity of the owner (DN); – info on the CA; Structure of a X. 509 certificate Public key Subject: C=TR, O=TRGrid, OU=ODTU, CN=Cevat Sener Issuer: C=TR, O=TRGrid, CN=TRGrid CA – time of validity; Not before: Apr 6 14: 08: 33 2006 GMT Not after: Apr 6 14: 08: 33 2007 GMT – Serial number; Serial number: 95 (0 x 5 F) – digital signature of the CA CA Digital signature Grid Open Day at LNS, Catania, 2008, January 23 rd 11
X. 509 Certificates • An X. 509 Certificate contains: – owner’s public key; – identity of the owner (DN); – info on the CA; Structure of a X. 509 certificate Public key Subject: C=TR, O=TRGrid, OU=ODTU, CN=Cevat Sener Issuer: C=TR, O=TRGrid, CN=TRGrid CA – time of validity; Not before: Apr 6 14: 08: 33 2006 GMT Not after: Apr 6 14: 08: 33 2007 GMT – Serial number; Serial number: 95 (0 x 5 F) – digital signature of the CA CA Digital signature Grid Open Day at LNS, Catania, 2008, January 23 rd 11
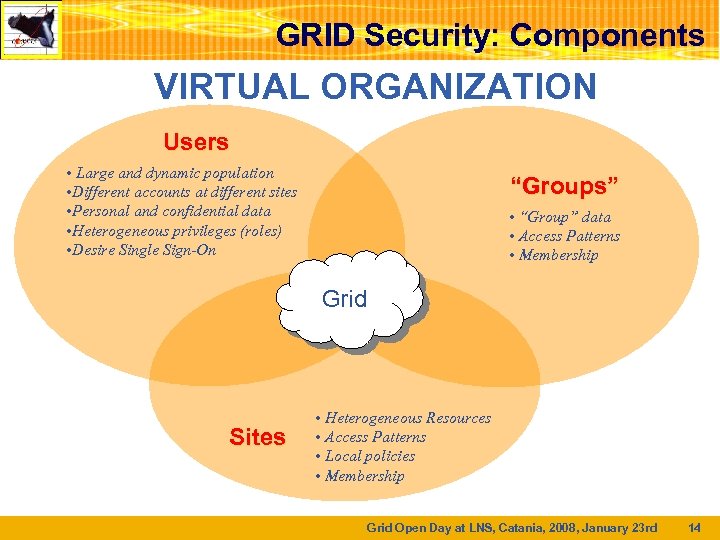 GRID Security: Components VIRTUAL ORGANIZATION Users • Large and dynamic population • Different accounts at different sites • Personal and confidential data • Heterogeneous privileges (roles) • Desire Single Sign-On “Groups” • “Group” data • Access Patterns • Membership Grid Sites • Heterogeneous Resources • Access Patterns • Local policies • Membership Grid Open Day at LNS, Catania, 2008, January 23 rd 14
GRID Security: Components VIRTUAL ORGANIZATION Users • Large and dynamic population • Different accounts at different sites • Personal and confidential data • Heterogeneous privileges (roles) • Desire Single Sign-On “Groups” • “Group” data • Access Patterns • Membership Grid Sites • Heterogeneous Resources • Access Patterns • Local policies • Membership Grid Open Day at LNS, Catania, 2008, January 23 rd 14
 Certificate Request User goes to the nearest Registration Authority (RA): - RA identifies him/her; - RA connects with the URL: https: //security. fi. infn. it/cgi-bin/RAvfy. pl - RA fills the form with name, institution, email address , etc - a random number is given to the user in order to mark the certification request - within 48 hours the user submits his/her request to the CA (link: https: //security. fi. infn. it/CA/mgt/restricted/ucert. php) - after the request is processed (usually within 48 hours), the user receives a mail with the instructions for certificate download - certificate download (from the same browser) - certificate backup (new password for certificate protection) - store in a safe place (possibly not reachable from the net) Grid Open Day at LNS, Catania, 2008, January 23 rd 15
Certificate Request User goes to the nearest Registration Authority (RA): - RA identifies him/her; - RA connects with the URL: https: //security. fi. infn. it/cgi-bin/RAvfy. pl - RA fills the form with name, institution, email address , etc - a random number is given to the user in order to mark the certification request - within 48 hours the user submits his/her request to the CA (link: https: //security. fi. infn. it/CA/mgt/restricted/ucert. php) - after the request is processed (usually within 48 hours), the user receives a mail with the instructions for certificate download - certificate download (from the same browser) - certificate backup (new password for certificate protection) - store in a safe place (possibly not reachable from the net) Grid Open Day at LNS, Catania, 2008, January 23 rd 15
 Inscription to the VO, to the support http: //www. pi 2 s 2. it/tecn/index. php? option=com_content&task= view&id=34&Itemid=67 User submits request and receives answer by email http: //support. consorzio-cometa. it/ User submits request and receives answer by email - ask for an account on a User Interface (UI) specifying: - a public IP address - user email address - Download Virtual UI: http: //www. pi 2 s 2. it/tecn/index. php? option=com_content&task= view&id=26&Itemid=57 Grid Open Day at LNS, Catania, 2008, January 23 rd 16
Inscription to the VO, to the support http: //www. pi 2 s 2. it/tecn/index. php? option=com_content&task= view&id=34&Itemid=67 User submits request and receives answer by email http: //support. consorzio-cometa. it/ User submits request and receives answer by email - ask for an account on a User Interface (UI) specifying: - a public IP address - user email address - Download Virtual UI: http: //www. pi 2 s 2. it/tecn/index. php? option=com_content&task= view&id=26&Itemid=57 Grid Open Day at LNS, Catania, 2008, January 23 rd 16
 Certificate Request http: //www. pi 2 s 2. it/tecn/index. php? option= com_content&task=view&id=32&Itemid=65 Grid Open Day at LNS, Catania, 2008, January 23 rd 17
Certificate Request http: //www. pi 2 s 2. it/tecn/index. php? option= com_content&task=view&id=32&Itemid=65 Grid Open Day at LNS, Catania, 2008, January 23 rd 17
 Inscription to the COMETA VO http: //www. pi 2 s 2. it/tecn/index. php? option= com_content&task=view&id=34&Itemid=67 Grid Open Day at LNS, Catania, 2008, January 23 rd 18
Inscription to the COMETA VO http: //www. pi 2 s 2. it/tecn/index. php? option= com_content&task=view&id=34&Itemid=67 Grid Open Day at LNS, Catania, 2008, January 23 rd 18
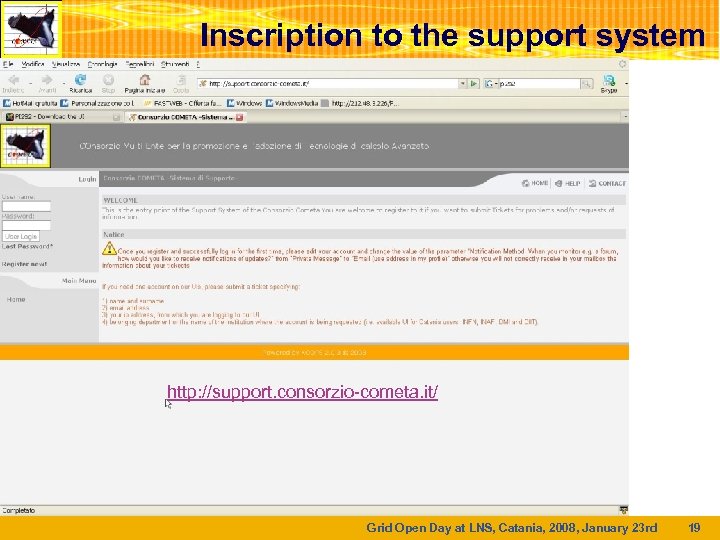 Inscription to the support system http: //support. consorzio-cometa. it/ Grid Open Day at LNS, Catania, 2008, January 23 rd 19
Inscription to the support system http: //support. consorzio-cometa. it/ Grid Open Day at LNS, Catania, 2008, January 23 rd 19
 Certificate management • Import your certificate into your account on the UI: – create the. globus sub-directory under the user home directory § mkdir $HOME/. globus – copy the. p 12 certificate file into the. globus directory – use openssl command line (available in each egee/LCG UI) § openssl pkcs 12 -nocerts -in my_cert. p 12 -out userkey. pem § openssl pkcs 12 -clcerts -nokeys -in my_cert. p 12 -out usercert. pem – requires certificate protection password – input the PEM passphrase (more than a simple password) during the second commmand Grid Open Day at LNS, Catania, 2008, January 23 rd 20
Certificate management • Import your certificate into your account on the UI: – create the. globus sub-directory under the user home directory § mkdir $HOME/. globus – copy the. p 12 certificate file into the. globus directory – use openssl command line (available in each egee/LCG UI) § openssl pkcs 12 -nocerts -in my_cert. p 12 -out userkey. pem § openssl pkcs 12 -clcerts -nokeys -in my_cert. p 12 -out usercert. pem – requires certificate protection password – input the PEM passphrase (more than a simple password) during the second commmand Grid Open Day at LNS, Catania, 2008, January 23 rd 20
 X. 509 Proxy Certificate • Proxy: GSI extension to X. 509 Identity Certificates – signed by the normal end entity cert (or by another proxy). • It enables single sign-on • It supports some important features: – Delegation – Mutual authentication • It has a limited lifetime (minimized risk of “compromised credentials”) • It is created by the voms-proxy-init command (“voms”: see next slides): – voms-proxy-init Enter PEM pass phrase: ****** – Options for voms-proxy-init: § -hours
X. 509 Proxy Certificate • Proxy: GSI extension to X. 509 Identity Certificates – signed by the normal end entity cert (or by another proxy). • It enables single sign-on • It supports some important features: – Delegation – Mutual authentication • It has a limited lifetime (minimized risk of “compromised credentials”) • It is created by the voms-proxy-init command (“voms”: see next slides): – voms-proxy-init Enter PEM pass phrase: ****** – Options for voms-proxy-init: § -hours
 VOs and authorization • Grid users MUST belong to virtual organizations – It was called “groups” previously. – It defines sets of users belonging to a collaboration – User must sign the usage guidelines for the VO – You will be registered in the VO-LDAP server (wait for notification) – List of supported VOs: § https: //lcg-registrar. cern. ch/virtual_organization. html • VOs maintain a list of their members on a LDAP Server – The list is downloaded by Grid machines to map user certificate subjects to local “pool” accounts – Sites decide which VOs to support § /etc/grid-security/grid-mapfile • "/C=TR/O=TRGrid/OU=TUBITAK-ULAKBIM/CN=Birsen Omay". seegrid • "/C=TR/O=TRGrid/OU=TUBITAK-ULAKBIM/CN=Hakan Bayindir". trgridb • "/C=TR/O=TRGrid/OU=TUBITAK-ULAKBIM/CN=Onur Temizsoylu". dteam Grid Open Day at LNS, Catania, 2008, January 23 rd 22
VOs and authorization • Grid users MUST belong to virtual organizations – It was called “groups” previously. – It defines sets of users belonging to a collaboration – User must sign the usage guidelines for the VO – You will be registered in the VO-LDAP server (wait for notification) – List of supported VOs: § https: //lcg-registrar. cern. ch/virtual_organization. html • VOs maintain a list of their members on a LDAP Server – The list is downloaded by Grid machines to map user certificate subjects to local “pool” accounts – Sites decide which VOs to support § /etc/grid-security/grid-mapfile • "/C=TR/O=TRGrid/OU=TUBITAK-ULAKBIM/CN=Birsen Omay". seegrid • "/C=TR/O=TRGrid/OU=TUBITAK-ULAKBIM/CN=Hakan Bayindir". trgridb • "/C=TR/O=TRGrid/OU=TUBITAK-ULAKBIM/CN=Onur Temizsoylu". dteam Grid Open Day at LNS, Catania, 2008, January 23 rd 22
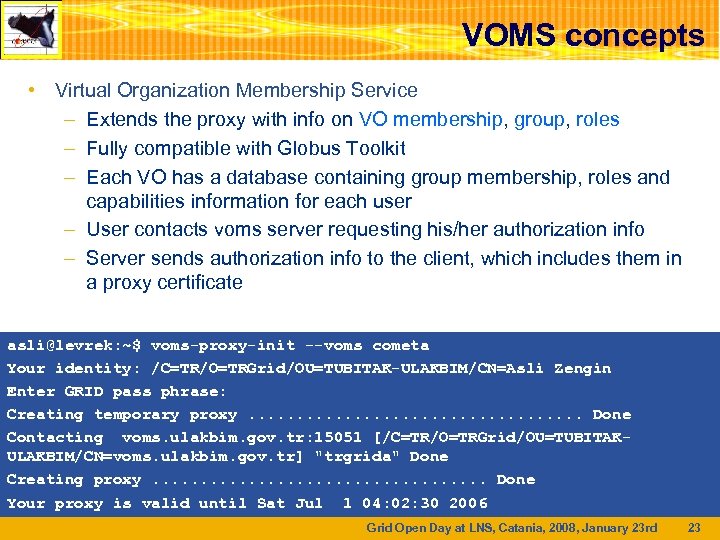 VOMS concepts • Virtual Organization Membership Service – Extends the proxy with info on VO membership, group, roles – Fully compatible with Globus Toolkit – Each VO has a database containing group membership, roles and capabilities information for each user – User contacts voms server requesting his/her authorization info – Server sends authorization info to the client, which includes them in a proxy certificate asli@levrek: ~$ voms-proxy-init --voms cometa Your identity: /C=TR/O=TRGrid/OU=TUBITAK-ULAKBIM/CN=Asli Zengin Enter GRID pass phrase: Creating temporary proxy. . . . . Done Contacting voms. ulakbim. gov. tr: 15051 [/C=TR/O=TRGrid/OU=TUBITAKULAKBIM/CN=voms. ulakbim. gov. tr] "trgrida" Done Creating proxy. . . . . Done Your proxy is valid until Sat Jul 1 04: 02: 30 2006 Grid Open Day at LNS, Catania, 2008, January 23 rd 23
VOMS concepts • Virtual Organization Membership Service – Extends the proxy with info on VO membership, group, roles – Fully compatible with Globus Toolkit – Each VO has a database containing group membership, roles and capabilities information for each user – User contacts voms server requesting his/her authorization info – Server sends authorization info to the client, which includes them in a proxy certificate asli@levrek: ~$ voms-proxy-init --voms cometa Your identity: /C=TR/O=TRGrid/OU=TUBITAK-ULAKBIM/CN=Asli Zengin Enter GRID pass phrase: Creating temporary proxy. . . . . Done Contacting voms. ulakbim. gov. tr: 15051 [/C=TR/O=TRGrid/OU=TUBITAKULAKBIM/CN=voms. ulakbim. gov. tr] "trgrida" Done Creating proxy. . . . . Done Your proxy is valid until Sat Jul 1 04: 02: 30 2006 Grid Open Day at LNS, Catania, 2008, January 23 rd 23
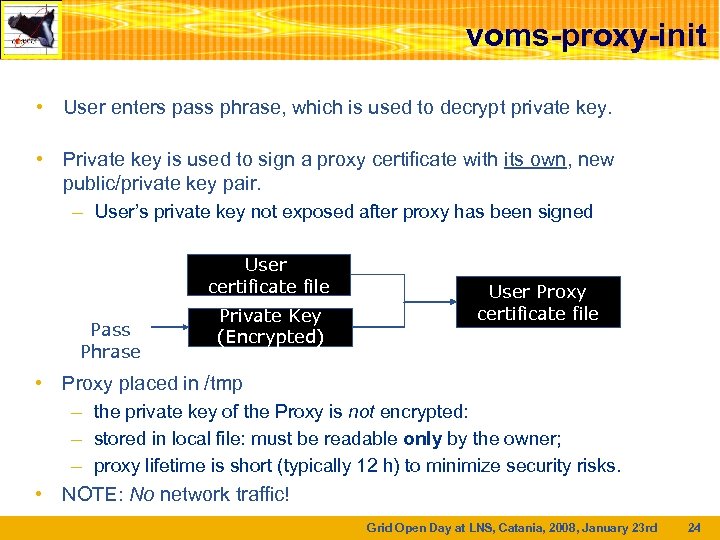 voms-proxy-init • User enters pass phrase, which is used to decrypt private key. • Private key is used to sign a proxy certificate with its own, new public/private key pair. – User’s private key not exposed after proxy has been signed User certificate file Pass Phrase Private Key (Encrypted) User Proxy certificate file • Proxy placed in /tmp – the private key of the Proxy is not encrypted: – stored in local file: must be readable only by the owner; – proxy lifetime is short (typically 12 h) to minimize security risks. • NOTE: No network traffic! Grid Open Day at LNS, Catania, 2008, January 23 rd 24
voms-proxy-init • User enters pass phrase, which is used to decrypt private key. • Private key is used to sign a proxy certificate with its own, new public/private key pair. – User’s private key not exposed after proxy has been signed User certificate file Pass Phrase Private Key (Encrypted) User Proxy certificate file • Proxy placed in /tmp – the private key of the Proxy is not encrypted: – stored in local file: must be readable only by the owner; – proxy lifetime is short (typically 12 h) to minimize security risks. • NOTE: No network traffic! Grid Open Day at LNS, Catania, 2008, January 23 rd 24
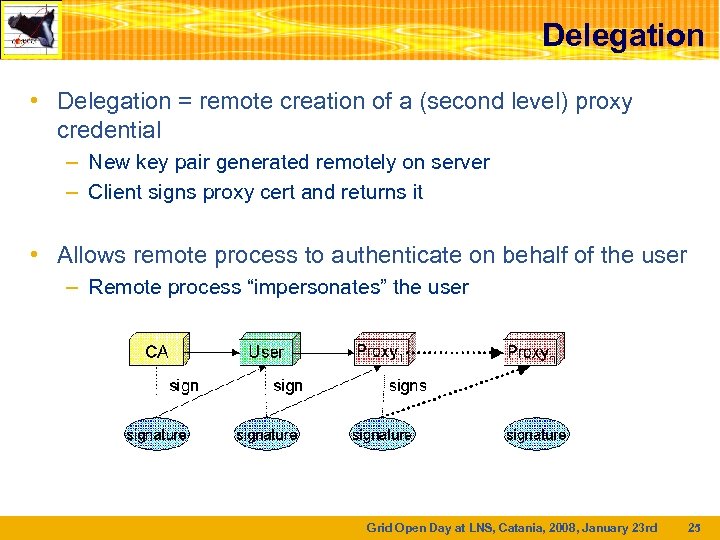 Delegation • Delegation = remote creation of a (second level) proxy credential – New key pair generated remotely on server – Client signs proxy cert and returns it • Allows remote process to authenticate on behalf of the user – Remote process “impersonates” the user Grid Open Day at LNS, Catania, 2008, January 23 rd 25
Delegation • Delegation = remote creation of a (second level) proxy credential – New key pair generated remotely on server – Client signs proxy cert and returns it • Allows remote process to authenticate on behalf of the user – Remote process “impersonates” the user Grid Open Day at LNS, Catania, 2008, January 23 rd 25
 Proxy destroy and Info • voms-proxy-init ≡ “login to the Grid” • To “logout” you have to destroy your proxy: – voms-proxy-destroy – This does NOT destroy any proxies that were delegated from this proxy. – You cannot revoke a remote proxy • To gather information about your proxy: – voms-proxy-info – Options for grid-proxy-info: -subject -type -strength -issuer -timeleft -help Grid Open Day at LNS, Catania, 2008, January 23 rd 26
Proxy destroy and Info • voms-proxy-init ≡ “login to the Grid” • To “logout” you have to destroy your proxy: – voms-proxy-destroy – This does NOT destroy any proxies that were delegated from this proxy. – You cannot revoke a remote proxy • To gather information about your proxy: – voms-proxy-info – Options for grid-proxy-info: -subject -type -strength -issuer -timeleft -help Grid Open Day at LNS, Catania, 2008, January 23 rd 26
 Long term proxy --> Myproxy • • • Proxy has limited lifetime (default is 12 h) – Bad idea to have longer proxy However, a grid task might need to use a proxy for much longer time – Grid jobs in HEP on LCG last up to 21 days myproxy server: – Allows to create and store a long term proxy certificate: – myproxy-init -s
Long term proxy --> Myproxy • • • Proxy has limited lifetime (default is 12 h) – Bad idea to have longer proxy However, a grid task might need to use a proxy for much longer time – Grid jobs in HEP on LCG last up to 21 days myproxy server: – Allows to create and store a long term proxy certificate: – myproxy-init -s
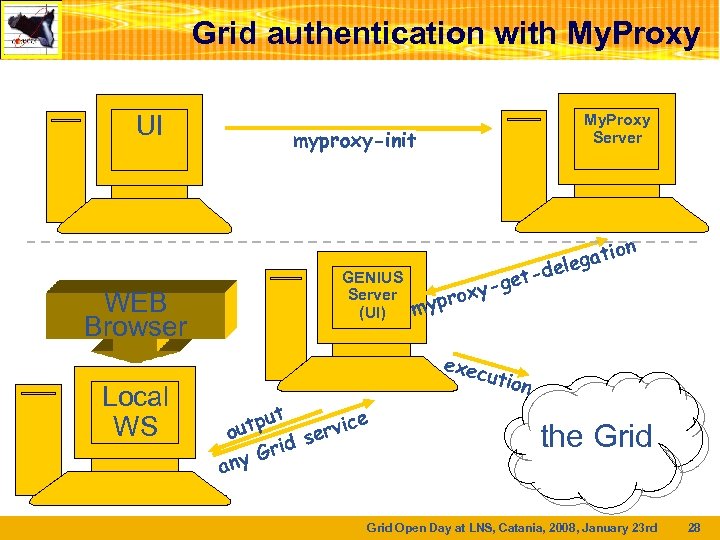 Grid authentication with My. Proxy UI WEB Browser Local WS My. Proxy Server myproxy-init GENIUS Server (UI) n et g oxypr my exec ut e utp rvic o e id s r ny G a tio lega -de ution the Grid Open Day at LNS, Catania, 2008, January 23 rd 28
Grid authentication with My. Proxy UI WEB Browser Local WS My. Proxy Server myproxy-init GENIUS Server (UI) n et g oxypr my exec ut e utp rvic o e id s r ny G a tio lega -de ution the Grid Open Day at LNS, Catania, 2008, January 23 rd 28
 Practice • Import your certificate in your browser – If you received a. pem certificate you need to convert it to PKCS 12 – Use openssl command line (available in each EGEE/LCG UI) § openssl pkcs 12 –export –in usercert. pem –inkey userkey. pem –out my_cert. p 12 –name ’My Name’ • COMETA (and other VOs): – You receive already a PKCS 12 certificate (can import it directly into the web browser) – For future use, you will need usercert. pem and userkey. pem in a directory $HOME/. globus on your UI – Export the PKCS 12 cert to a local dir on UI and use again openssl: § openssl pkcs 12 -nocerts -in my_cert. p 12 -out userkey. pem § openssl pkcs 12 -clcerts -nokeys -in my_cert. p 12 -out usercert. pem • Hands on: – https: //grid. ct. infn. it/twiki/bin/view/PI 2 S 2/User. Tutorials Grid Open Day at LNS, Catania, 2008, January 23 rd 35
Practice • Import your certificate in your browser – If you received a. pem certificate you need to convert it to PKCS 12 – Use openssl command line (available in each EGEE/LCG UI) § openssl pkcs 12 –export –in usercert. pem –inkey userkey. pem –out my_cert. p 12 –name ’My Name’ • COMETA (and other VOs): – You receive already a PKCS 12 certificate (can import it directly into the web browser) – For future use, you will need usercert. pem and userkey. pem in a directory $HOME/. globus on your UI – Export the PKCS 12 cert to a local dir on UI and use again openssl: § openssl pkcs 12 -nocerts -in my_cert. p 12 -out userkey. pem § openssl pkcs 12 -clcerts -nokeys -in my_cert. p 12 -out usercert. pem • Hands on: – https: //grid. ct. infn. it/twiki/bin/view/PI 2 S 2/User. Tutorials Grid Open Day at LNS, Catania, 2008, January 23 rd 35
 Questions Grid Open Day at LNS, Catania, 2008, January 23 rd 36
Questions Grid Open Day at LNS, Catania, 2008, January 23 rd 36


