e9d2d5f4d5aaa57868b95f7e55a2cbe6.ppt
- Количество слайдов: 26

Configuration Management: Getting Started Presented By: Tony Iannetta, Evergreen Systems 3/17/2018 1
Overview • What is Configuration Management • Why Configuration Management • The Scope of Configuration Management • What You Can Learn • Getting Started • Q&A
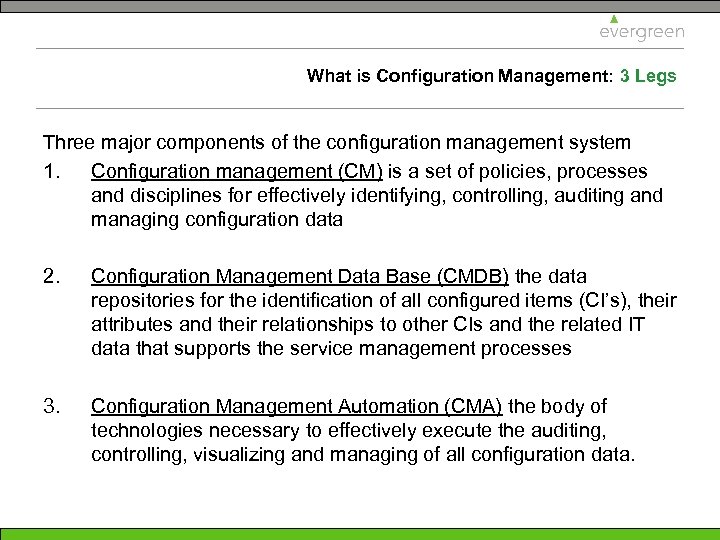
What is Configuration Management: 3 Legs Three major components of the configuration management system 1. Configuration management (CM) is a set of policies, processes and disciplines for effectively identifying, controlling, auditing and managing configuration data 2. Configuration Management Data Base (CMDB) the data repositories for the identification of all configured items (CI’s), their attributes and their relationships to other CIs and the related IT data that supports the service management processes 3. Configuration Management Automation (CMA) the body of technologies necessary to effectively execute the auditing, controlling, visualizing and managing of all configuration data.
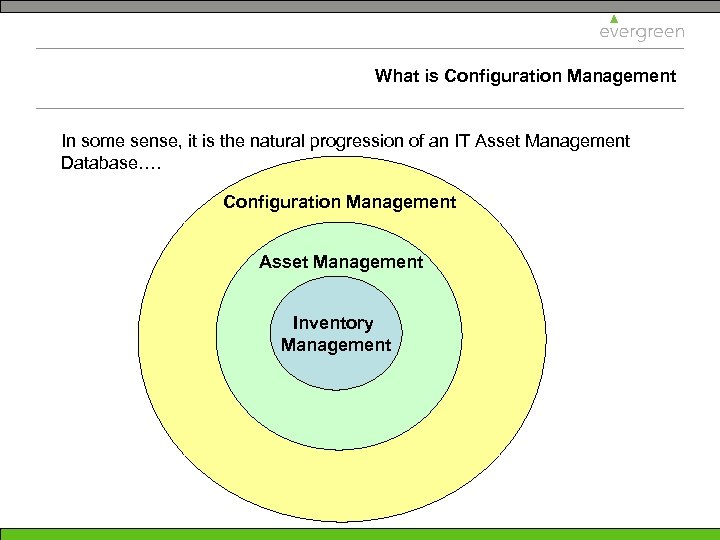
What is Configuration Management In some sense, it is the natural progression of an IT Asset Management Database…. Configuration Management Asset Management Inventory Management
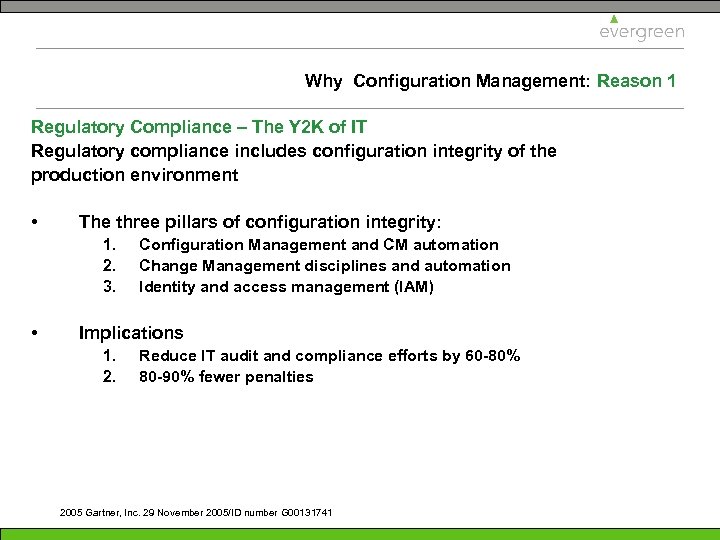
Why Configuration Management: Reason 1 Regulatory Compliance – The Y 2 K of IT Regulatory compliance includes configuration integrity of the production environment • The three pillars of configuration integrity: 1. 2. 3. • Configuration Management and CM automation Change Management disciplines and automation Identity and access management (IAM) Implications 1. 2. Reduce IT audit and compliance efforts by 60 -80% 80 -90% fewer penalties 2005 Gartner, Inc. 29 November 2005/ID number G 00131741
Why Configuration Management: Reason 2 Improving service quality Configuration management contributes to improving quality of service by – maintaining the information necessary to ensure IT changes do no harm – 87 % of all IT incidents are caused by poor change management. – Increase speed and responsiveness to changes in the business AND Lowering cost of service delivery Configuration management contributes to lowering the cost of service by: – Increasing utilization of existing IT resources – reducing the investment in IT infrastructure 2005 Gartner, Inc. 29 November 2005/ID number G 00131741
Why Configuration Management: Reason 3 Aligning IT with the business Configuration management contributes to improving alignment of IT with the business by – – – Enabling service level uptime agreements Enabling rapid development of new services or changes to existing services as the market dictates Demonstrating the same rigor in IT that the business puts toward it’s customer. 2005 Gartner, Inc. 28 September 2005/ID number G 00131333 Business Service Management (BSM) the real end game Stages of BSM of global $1 B+ companies – – – Chaotic – 35% - limited formal processes for managing IT Reactive – 44% - IT inventory management implemented project by project with some basic ITIL processes Stable – 14% - Integrated service delivery. IT asset management integrated with ITIL Proactive – 7% - Business service framework Predictive – 1 % - Resource allocation to business need Forester Research Inc. “IT Asset Management, ITIL and the CMDB Paving the Way for BSM”, October 2005
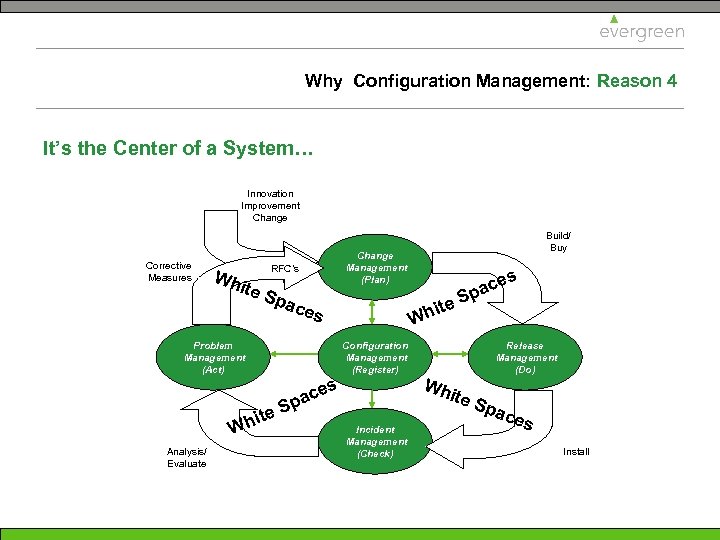
Why Configuration Management: Reason 4 It’s the Center of a System… Innovation Improvement Change Corrective Measures Wh ite RFC’s Spa Change Management (Plan) hite W ces Problem Management (Act) Configuration Management (Register) ces pa S ite h W Analysis/ Evaluate Build/ Buy S Wh Release Management (Do) ite Incident Management (Check) s ace p Spa ces Install
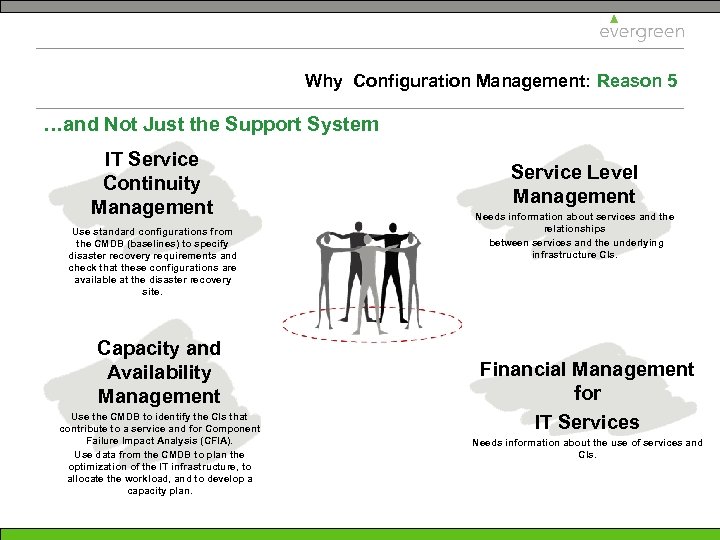
Why Configuration Management: Reason 5 …and Not Just the Support System IT Service Continuity Management Use standard configurations from the CMDB (baselines) to specify disaster recovery requirements and check that these configurations are available at the disaster recovery site. Capacity and Availability Management Use the CMDB to identify the CIs that contribute to a service and for Component Failure Impact Analysis (CFIA). Use data from the CMDB to plan the optimization of the IT infrastructure, to allocate the workload, and to develop a capacity plan. Service Level Management Needs information about services and the relationships between services and the underlying infrastructure CIs. Financial Management for IT Services Needs information about the use of services and CIs.
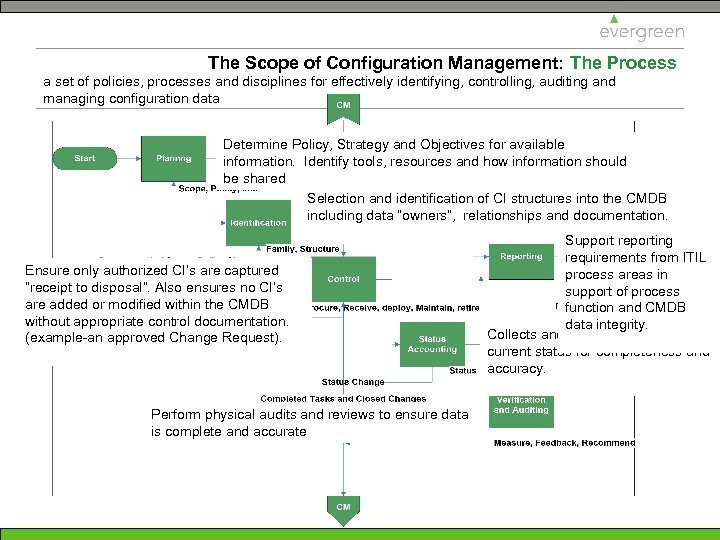
The Scope of Configuration Management: The Process a set of policies, processes and disciplines for effectively identifying, controlling, auditing and managing configuration data Determine Policy, Strategy and Objectives for available information. Identify tools, resources and how information should be shared Selection and identification of CI structures into the CMDB including data “owners”, relationships and documentation. Ensure only authorized CI’s are captured “receipt to disposal”. Also ensures no CI’s are added or modified within the CMDB without appropriate control documentation. (example-an approved Change Request). Perform physical audits and reviews to ensure data is complete and accurate Support reporting requirements from ITIL process areas in support of process function and CMDB data integrity. Collects and monitor CI history and current status for completeness and accuracy.
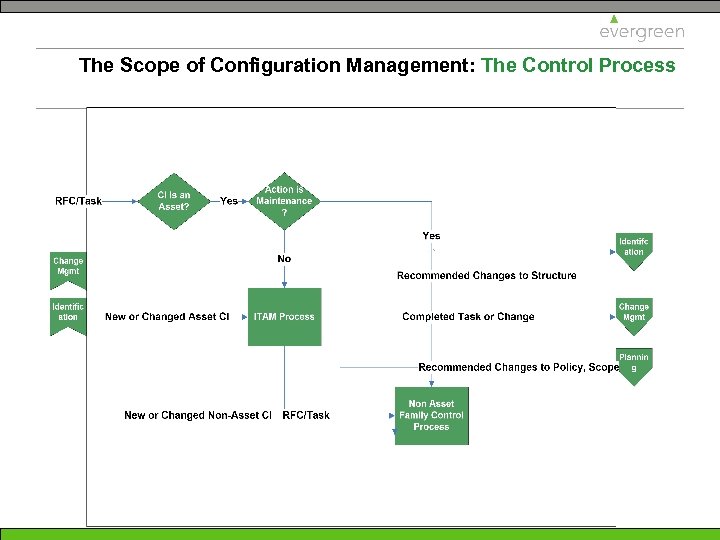
The Scope of Configuration Management: The Control Process
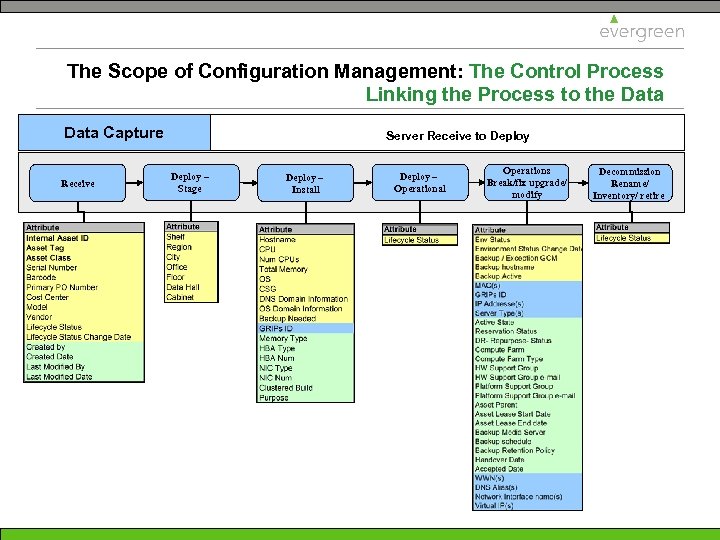
The Scope of Configuration Management: The Control Process Linking the Process to the Data Capture Receive Server Receive to Deploy – Stage Deploy – Install Deploy – Operational Operations Break/fix upgrade/ modify Decommission Rename/ Inventory/ retire
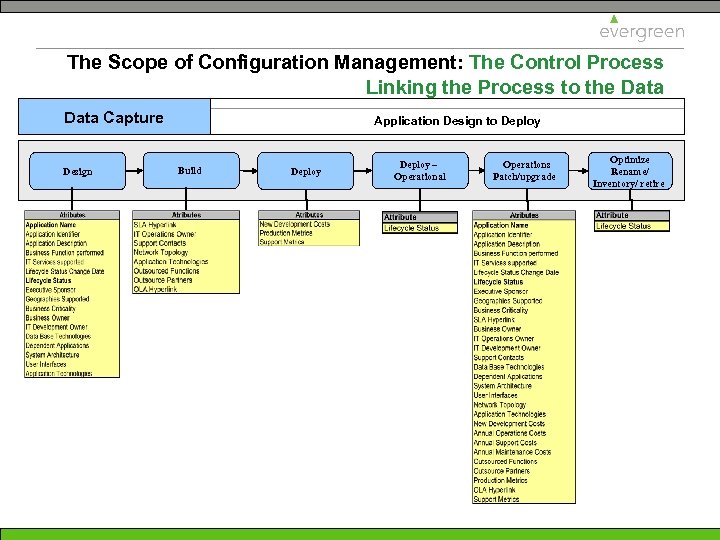
The Scope of Configuration Management: The Control Process Linking the Process to the Data Capture Design Application Design to Deploy Build Deploy – Operational Operations Patch/upgrade Optimize Rename/ Inventory/ retire
The Scope of the Configuration Management: The Data • CMDB – Configuration Management Data Base Ideally defines what we have, who uses it, how CIs interact with and impact other CIs, which services and business processes the CIs support • CI – Configuration Item (a category, type or family of IT components such as ‘servers’ or ‘applications’) – IT Asset management is a good source of CI’s but not all assets are CI’s and not all CI’s are assets. – Logical CI – The logical grouping of physical entities. The top tiers of a hierarchy – Physical CI – A physical, tangible IT component that performs a specific function. The lower tiers of a hierarchy – Virtual CI – Performs the same function as a physical CI but does not have a physical form • Attribute – a data field associated with the CI • System of Record – the official owner of an attribute (accountable for accuracy)
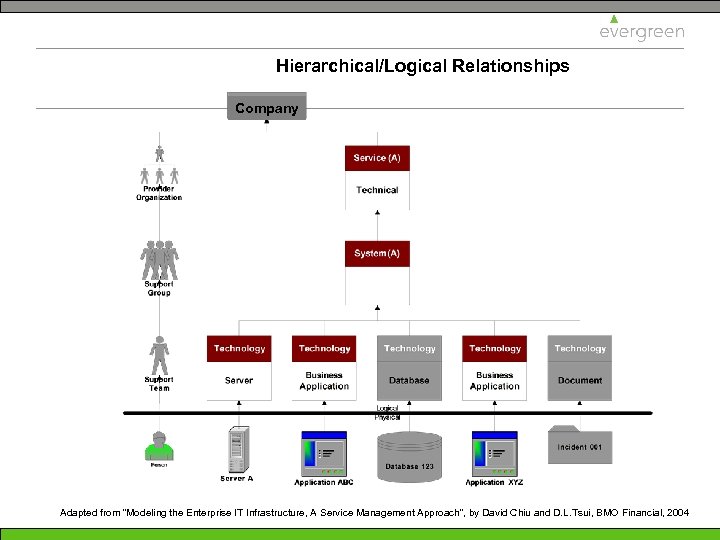
Hierarchical/Logical Relationships Company Adapted from “Modeling the Enterprise IT Infrastructure, A Service Management Approach”, by David Chiu and D. L. Tsui, BMO Financial, 2004
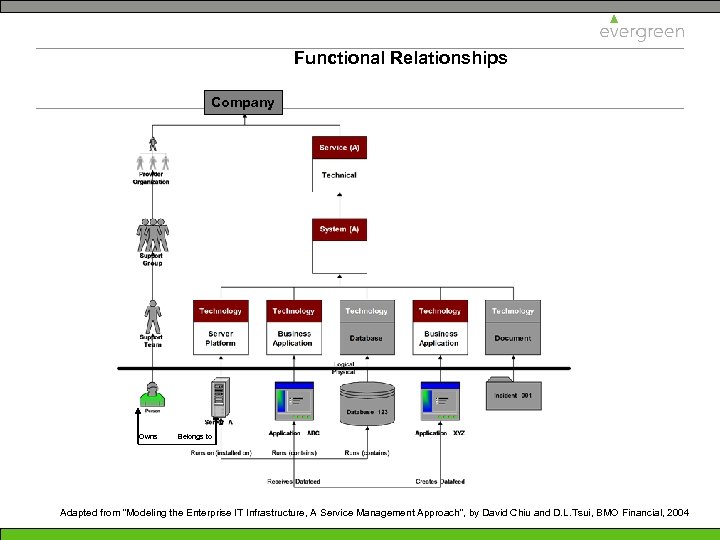
Functional Relationships Company Owns Belongs to Adapted from “Modeling the Enterprise IT Infrastructure, A Service Management Approach”, by David Chiu and D. L. Tsui, BMO Financial, 2004

The Scope of the Configuration Management: The Technology The Vendor Landscape is everchanging…… Charles Betz, ERP 4 IT
The Scope of the Configuration Management: The Technology A Successful Configuration Management Technology Platforms should…. • Act to federate (Integrate) key vendors and tools • Support reconciliation of CIs – real time discovery – Application and infrastructure discovery • Support/Enable automated mapping of CI relationships – Relationship visualization – Correlates relationships back to the business service or process • Support/Enable synchronization of the environment
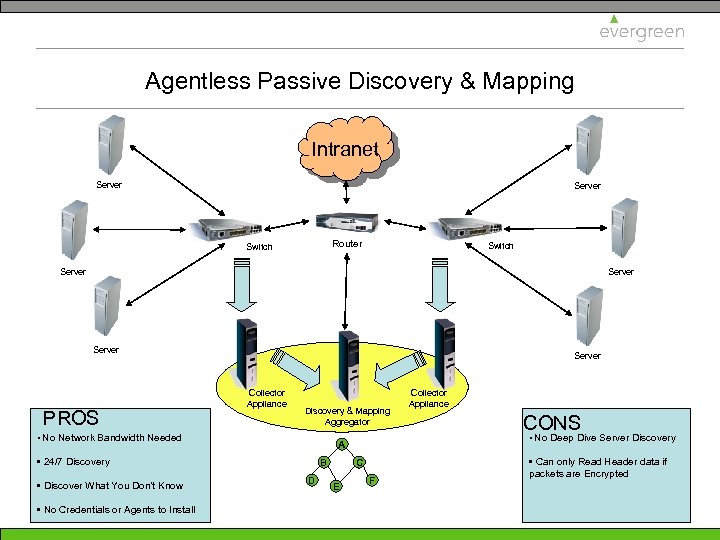
Agentless Passive Discovery & Mapping Intranet Server Router Switch Server PROS Server Collector Appliance Discovery & Mapping Aggregator • No Network Bandwidth Needed • Discover What You Don’t Know • No Credentials or Agents to Install B D C E CONS • No Deep Dive Server Discovery A • 24/7 Discovery Collector Appliance F • Can only Read Header data if packets are Encrypted
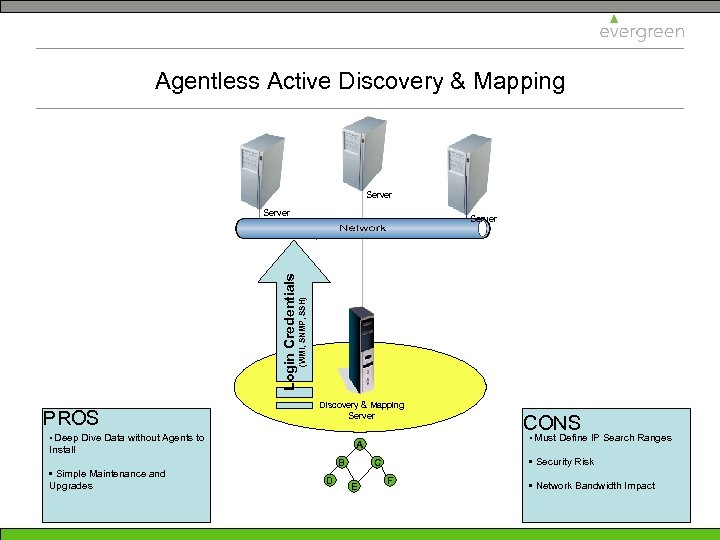
Agentless Active Discovery & Mapping Server PROS Server (WMI, SNMP, SSH) Login Credentials Server Discovery & Mapping Server • Deep Dive Data without Agents to • Simple Maintenance and Upgrades • Must Define IP Search Ranges A Install B D • Security Risk C E CONS F • Network Bandwidth Impact
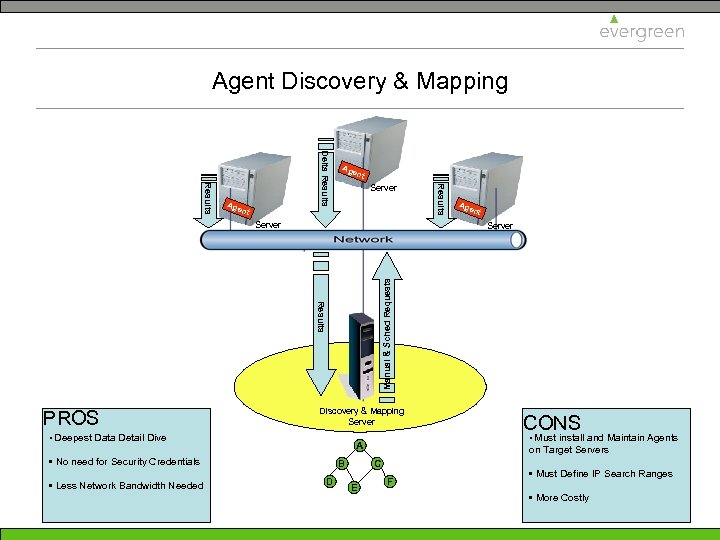
Agent Discovery & Mapping nt nt Server nt Manual & Sched Requests Discovery & Mapping Server • Deepest Data Detail Dive B D on Target Servers C E CONS • Must install and Maintain Agents A • No need for Security Credentials • Less Network Bandwidth Needed Age Server Results PROS Results Delta Results Age F • Must Define IP Search Ranges • More Costly
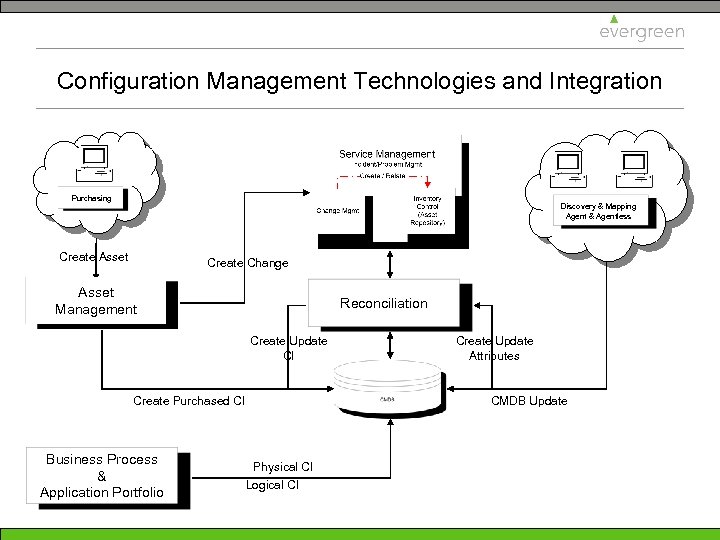
Configuration Management Technologies and Integration Purchasing Discovery & Mapping Agent & Agentless Create Asset Create Change Asset Management Reconciliation Create Update CI Create Purchased CI Business Process & Application Portfolio Create Update Attributes CMDB Update Physical CI Logical CI
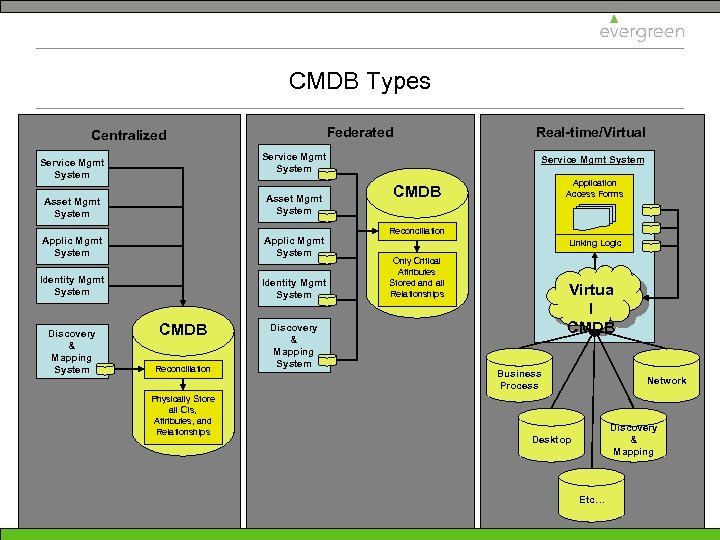
CMDB Types Federated Centralized Service Mgmt System Asset Mgmt System Applic Mgmt System Identity Mgmt System Discovery & Mapping System CMDB Reconciliation Physically Store all CIs, Attributes, and Relationships Discovery & Mapping System Real-time/Virtual Service Mgmt System Application Access Forms CMDB Reconciliation Linking Logic Only Critical Attributes Stored and all Relationships Virtua l CMDB Business Process Network Discovery & Mapping Desktop Etc…
Best Practices and Lessons Learned • • • Executive Commitment – Early, Continuous, Visible high-level sponsorship is critical Scope and Charter – Start with “easy wins” and high-value efforts. – Fully define set of definitions of terms and concepts – Get assets under control first with policy adherence – Consider IT Governance Strategy when developing Configuration Management strategy Marketing and Adoption – Include stakeholders in policy and process design for buy-in – Focus extra effort on cross-departmental processes and hand-off’s – Identify “your job will get harder” cases for extra training and support – Over-communicate with all stakeholders – Embrace conflict: it means people care and are paying attention Process – CHANGE MANAGEMENT – Build policies and processes for ongoing development – Start with Asset Management (Receipt to Disposal) Technology – Know what you have before you acquire more stuff – Develop configuration management disciplines before automating Data – Use the processes to drive the data requirements (just enough data) – Data accuracy and control to ensure ongoing accuracy is critical – Reduce the number of repositories – Start with a wide and shallow approach for CI relationships
Getting Started Begin by…. . • • • Establish a reasonable scope Document terms and concepts Documenting the current state of IT data and process Develop a product portfolio of current technologies Formulate the future state of IT data, process and technologies Formulate a roadmap and break it into doable phases Position for organizational change Establish a comprehensive foundation Establish data integrity Integrate with the enterprise Establish linkages Perform audits
Configuration Management Questions?
e9d2d5f4d5aaa57868b95f7e55a2cbe6.ppt