d73cb33dc3d67a992846543733b9a7b9.ppt
- Количество слайдов: 36
 Computer Security: Principles and Practice Chapter 21 – Internet Security Protocols and Standards First Edition by William Stallings and Lawrie Brown Lecture slides by Lawrie Brown
Computer Security: Principles and Practice Chapter 21 – Internet Security Protocols and Standards First Edition by William Stallings and Lawrie Brown Lecture slides by Lawrie Brown
 Objectives The student should be able to Ø Define VPN, intranet VPN, extranet VPN, tunnel. Ø Describe the advantages of link versus end-to-end encryption. Ø Define the protection provided by SSL, TLS, IPsec. Ø Show where the following protocols exist in the protocol stack, and describe which applications they can be used with: SSL, TLS, IPSec, S-MIME. Ø Show a diagram of what happens to a packet during Tunnel versus Transport mode concerning the packet format. Ø Describe the difference between IPSec’s Authentication Header and . Encapsulated Security Payload protocols
Objectives The student should be able to Ø Define VPN, intranet VPN, extranet VPN, tunnel. Ø Describe the advantages of link versus end-to-end encryption. Ø Define the protection provided by SSL, TLS, IPsec. Ø Show where the following protocols exist in the protocol stack, and describe which applications they can be used with: SSL, TLS, IPSec, S-MIME. Ø Show a diagram of what happens to a packet during Tunnel versus Transport mode concerning the packet format. Ø Describe the difference between IPSec’s Authentication Header and . Encapsulated Security Payload protocols
 Internet Security Protocols and Standards Ø Secure Sockets Layer (SSL) / Transport Layer Security (TLS) Ø IPv 4 and IPv 6 Security Ø S/MIME (Secure/Multipurpose Internet Mail Extension)
Internet Security Protocols and Standards Ø Secure Sockets Layer (SSL) / Transport Layer Security (TLS) Ø IPv 4 and IPv 6 Security Ø S/MIME (Secure/Multipurpose Internet Mail Extension)
 VPNs Virtual Private Network (VPN): A means of carrying private traffic over a public network Ø Uses link encryption to give users sense that they are operating on a private network when they are actually transmitting over a public network Ø Communications pass through an encrypted tunnel Intranet VPN: Connects two or more private networks within the same company Extranet VPN: Connects two or more private networks between different companies Ø E. g. , B 2 B or business-to-business communication. Remote Access VPN: A roaming user has access to a private network via wireless, hotel room, etc.
VPNs Virtual Private Network (VPN): A means of carrying private traffic over a public network Ø Uses link encryption to give users sense that they are operating on a private network when they are actually transmitting over a public network Ø Communications pass through an encrypted tunnel Intranet VPN: Connects two or more private networks within the same company Extranet VPN: Connects two or more private networks between different companies Ø E. g. , B 2 B or business-to-business communication. Remote Access VPN: A roaming user has access to a private network via wireless, hotel room, etc.
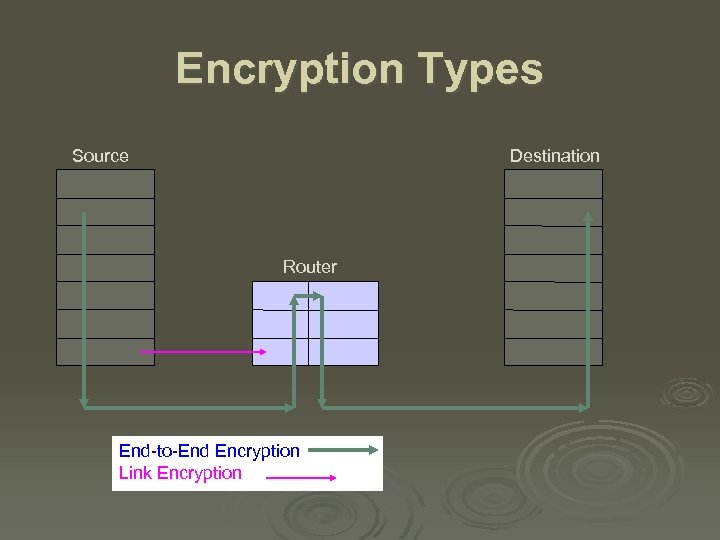 Encryption Types Source Destination Router End-to-End Encryption Link Encryption
Encryption Types Source Destination Router End-to-End Encryption Link Encryption
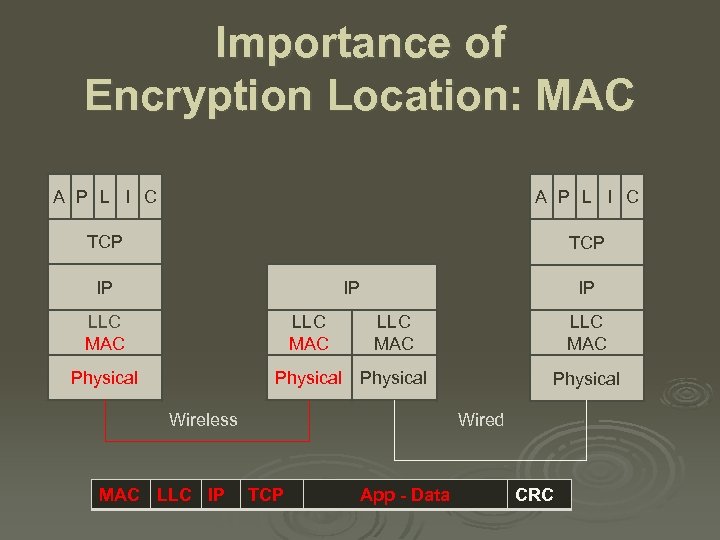 Importance of Encryption Location: MAC A P L I C TCP IP IP IP LLC MAC Physical Wireless MAC LLC IP Wired TCP App - Data CRC
Importance of Encryption Location: MAC A P L I C TCP IP IP IP LLC MAC Physical Wireless MAC LLC IP Wired TCP App - Data CRC
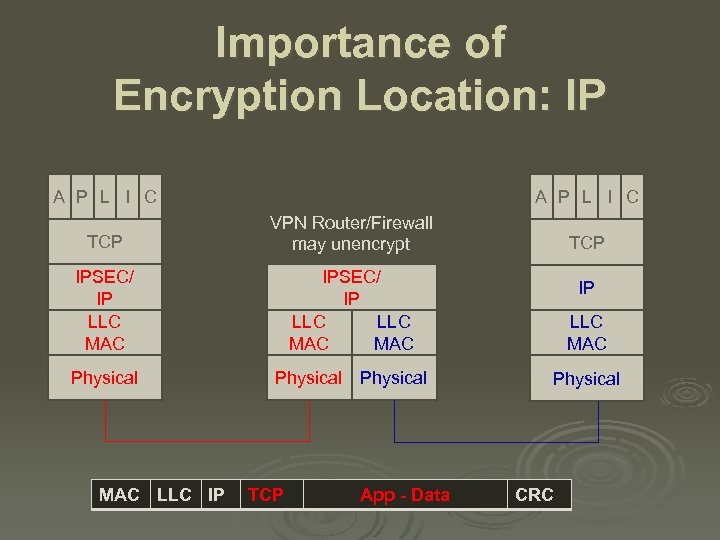 Importance of Encryption Location: IP A P L I C TCP VPN Router/Firewall may unencrypt IPSEC/ IP LLC MAC Physical MAC LLC IP Physical TCP Physical App - Data TCP IP LLC MAC Physical CRC
Importance of Encryption Location: IP A P L I C TCP VPN Router/Firewall may unencrypt IPSEC/ IP LLC MAC Physical MAC LLC IP Physical TCP Physical App - Data TCP IP LLC MAC Physical CRC
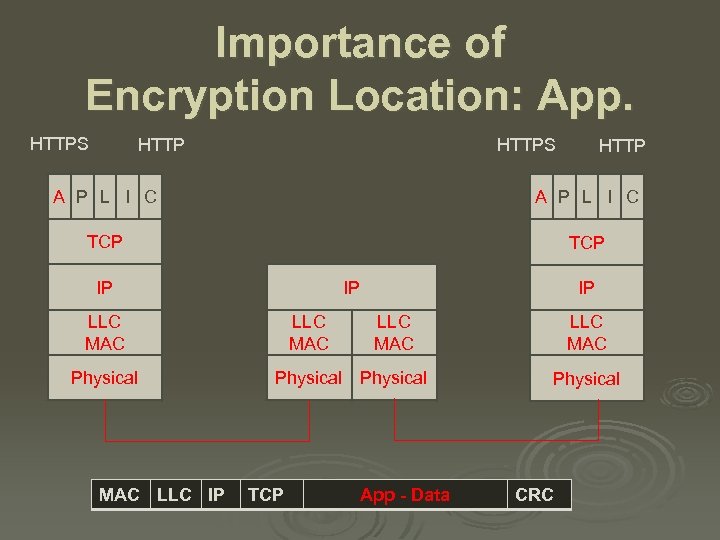 Importance of Encryption Location: App. HTTPS HTTP A P L I C TCP IP IP IP LLC MAC Physical MAC LLC IP TCP App - Data CRC
Importance of Encryption Location: App. HTTPS HTTP A P L I C TCP IP IP IP LLC MAC Physical MAC LLC IP TCP App - Data CRC
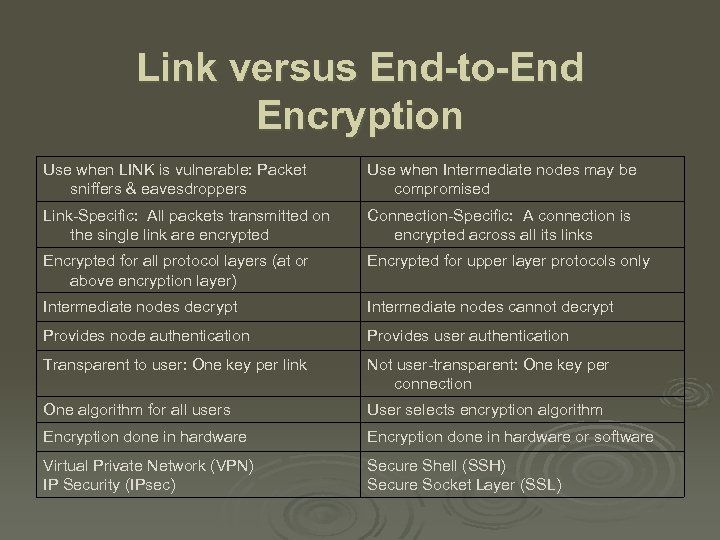 Link versus End-to-End Encryption Use when LINK is vulnerable: Packet sniffers & eavesdroppers Use when Intermediate nodes may be compromised Link-Specific: All packets transmitted on the single link are encrypted Connection-Specific: A connection is encrypted across all its links Encrypted for all protocol layers (at or above encryption layer) Encrypted for upper layer protocols only Intermediate nodes decrypt Intermediate nodes cannot decrypt Provides node authentication Provides user authentication Transparent to user: One key per link Not user-transparent: One key per connection One algorithm for all users User selects encryption algorithm Encryption done in hardware or software Virtual Private Network (VPN) IP Security (IPsec) Secure Shell (SSH) Secure Socket Layer (SSL)
Link versus End-to-End Encryption Use when LINK is vulnerable: Packet sniffers & eavesdroppers Use when Intermediate nodes may be compromised Link-Specific: All packets transmitted on the single link are encrypted Connection-Specific: A connection is encrypted across all its links Encrypted for all protocol layers (at or above encryption layer) Encrypted for upper layer protocols only Intermediate nodes decrypt Intermediate nodes cannot decrypt Provides node authentication Provides user authentication Transparent to user: One key per link Not user-transparent: One key per connection One algorithm for all users User selects encryption algorithm Encryption done in hardware or software Virtual Private Network (VPN) IP Security (IPsec) Secure Shell (SSH) Secure Socket Layer (SSL)
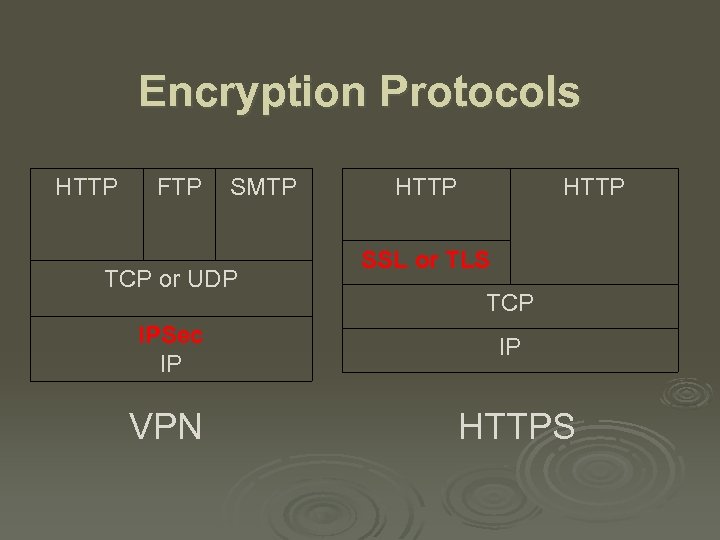 Encryption Protocols HTTP FTP SMTP TCP or UDP HTTP SSL or TLS TCP IPSec IP IP VPN HTTPS
Encryption Protocols HTTP FTP SMTP TCP or UDP HTTP SSL or TLS TCP IPSec IP IP VPN HTTPS
 Secure Sockets Layer (SSL) Ø transport layer security service l l Ø Ø originally developed by Netscape version 3 designed with public input subsequently became Internet standard RFC 2246: Transport Layer Security (TLS) use TCP to provide a reliable endto-end service may be provided in underlying protocol suite or embedded in specific packages l SSL + HTTP used together = HTTPS HTTP SSL or TLS TCP IP
Secure Sockets Layer (SSL) Ø transport layer security service l l Ø Ø originally developed by Netscape version 3 designed with public input subsequently became Internet standard RFC 2246: Transport Layer Security (TLS) use TCP to provide a reliable endto-end service may be provided in underlying protocol suite or embedded in specific packages l SSL + HTTP used together = HTTPS HTTP SSL or TLS TCP IP
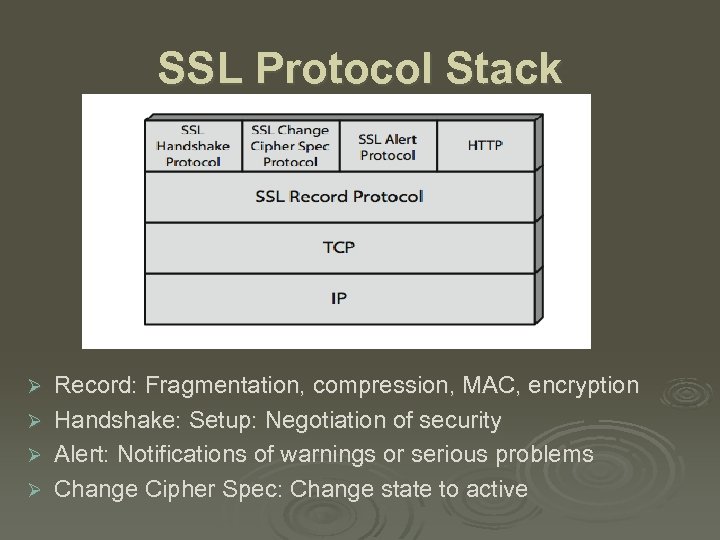 SSL Protocol Stack Ø Ø Record: Fragmentation, compression, MAC, encryption Handshake: Setup: Negotiation of security Alert: Notifications of warnings or serious problems Change Cipher Spec: Change state to active
SSL Protocol Stack Ø Ø Record: Fragmentation, compression, MAC, encryption Handshake: Setup: Negotiation of security Alert: Notifications of warnings or serious problems Change Cipher Spec: Change state to active
 SSL Record Protocol Services Ø message integrity l l using a MAC with shared secret key similar to HMAC but with different padding Ø confidentiality l l l using symmetric encryption with a shared secret key defined by Handshake Protocol AES, IDEA, RC 2 -40, DES, 3 DES, Fortezza, RC 4 -40, RC 4 -128 message is compressed before encryption
SSL Record Protocol Services Ø message integrity l l using a MAC with shared secret key similar to HMAC but with different padding Ø confidentiality l l l using symmetric encryption with a shared secret key defined by Handshake Protocol AES, IDEA, RC 2 -40, DES, 3 DES, Fortezza, RC 4 -40, RC 4 -128 message is compressed before encryption
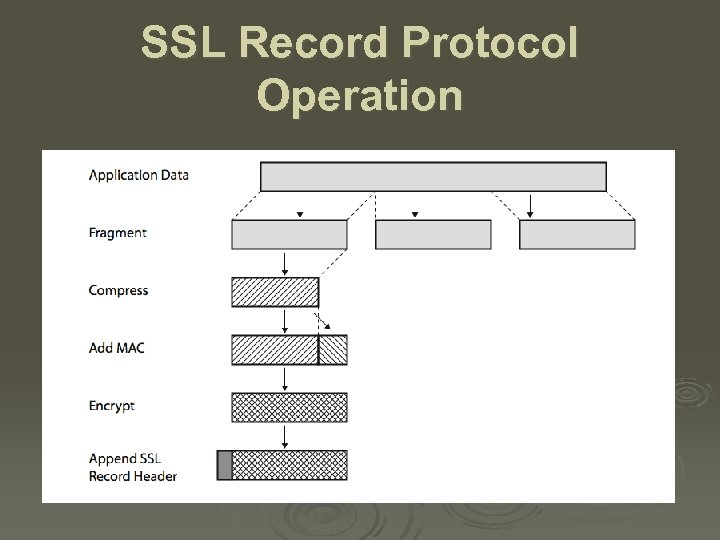 SSL Record Protocol Operation
SSL Record Protocol Operation
 SSL Change Cipher Spec Protocol Ø one of 3 SSL specific protocols which use the SSL Record protocol Ø a single message Ø causes pending state to become current Ø hence updating the cipher suite in use
SSL Change Cipher Spec Protocol Ø one of 3 SSL specific protocols which use the SSL Record protocol Ø a single message Ø causes pending state to become current Ø hence updating the cipher suite in use
 SSL Alert Protocol conveys SSL-related alerts to peer entity Ø severity Ø • warning or fatal Ø specific alert • fatal: unexpected message, bad record mac, decompression failure, handshake failure, illegal parameter • warning: close notify, no certificate, bad certificate, unsupported certificate, certificate revoked, certificate expired, certificate unknown Ø compressed & encrypted like all SSL data
SSL Alert Protocol conveys SSL-related alerts to peer entity Ø severity Ø • warning or fatal Ø specific alert • fatal: unexpected message, bad record mac, decompression failure, handshake failure, illegal parameter • warning: close notify, no certificate, bad certificate, unsupported certificate, certificate revoked, certificate expired, certificate unknown Ø compressed & encrypted like all SSL data
 SSL Handshake Protocol allows server & client to: Ø authenticate each other to negotiate encryption & MAC algorithms to negotiate cryptographic keys to be used l l l Ø comprises a series of messages in phases 1. 2. 3. 4. Establish Security Capabilities Server Authentication and Key Exchange Client Authentication and Key Exchange Finish
SSL Handshake Protocol allows server & client to: Ø authenticate each other to negotiate encryption & MAC algorithms to negotiate cryptographic keys to be used l l l Ø comprises a series of messages in phases 1. 2. 3. 4. Establish Security Capabilities Server Authentication and Key Exchange Client Authentication and Key Exchange Finish
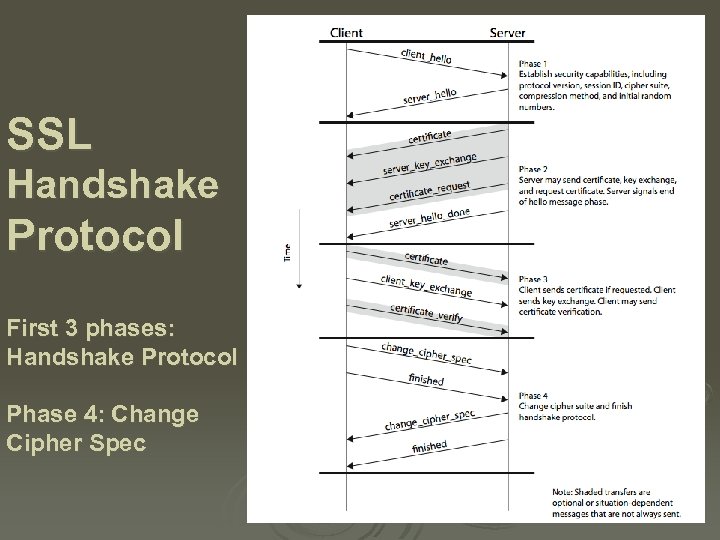 SSL Handshake Protocol First 3 phases: Handshake Protocol Phase 4: Change Cipher Spec
SSL Handshake Protocol First 3 phases: Handshake Protocol Phase 4: Change Cipher Spec
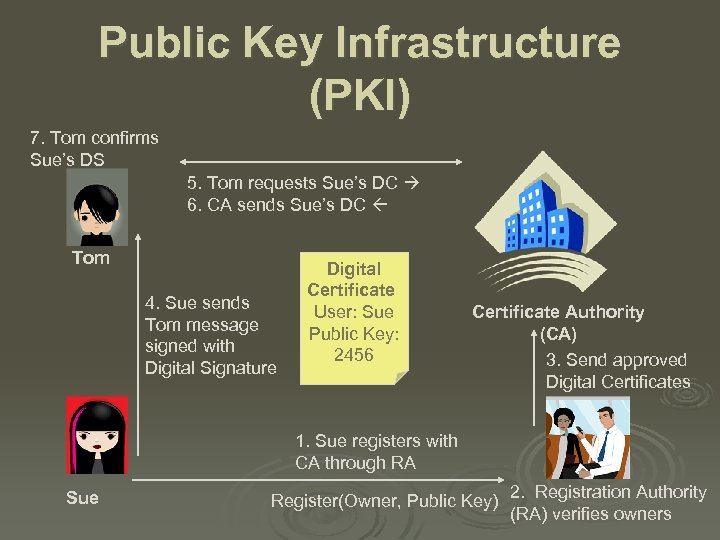 Public Key Infrastructure (PKI) 7. Tom confirms Sue’s DS 5. Tom requests Sue’s DC 6. CA sends Sue’s DC Tom 4. Sue sends Tom message signed with Digital Signature Digital Certificate User: Sue Public Key: 2456 Certificate Authority (CA) 3. Send approved Digital Certificates 1. Sue registers with CA through RA Sue Register(Owner, Public Key) 2. Registration Authority (RA) verifies owners
Public Key Infrastructure (PKI) 7. Tom confirms Sue’s DS 5. Tom requests Sue’s DC 6. CA sends Sue’s DC Tom 4. Sue sends Tom message signed with Digital Signature Digital Certificate User: Sue Public Key: 2456 Certificate Authority (CA) 3. Send approved Digital Certificates 1. Sue registers with CA through RA Sue Register(Owner, Public Key) 2. Registration Authority (RA) verifies owners
 IP Security Ø various application security mechanisms exist l eg. S/MIME, PGP, Kerberos, SSL/HTTPS Ø security concerns cross protocol layers Ø hence would like security implemented by the network for all applications Ø authentication & encryption security features included in next-generation IPv 6 Ø also usable in existing IPv 4
IP Security Ø various application security mechanisms exist l eg. S/MIME, PGP, Kerberos, SSL/HTTPS Ø security concerns cross protocol layers Ø hence would like security implemented by the network for all applications Ø authentication & encryption security features included in next-generation IPv 6 Ø also usable in existing IPv 4
 IPSec Ø general IP Security mechanisms Ø provides l l l authentication confidentiality key management Ø applicable to use over LANs, across public & private WANs, & for the Internet
IPSec Ø general IP Security mechanisms Ø provides l l l authentication confidentiality key management Ø applicable to use over LANs, across public & private WANs, & for the Internet
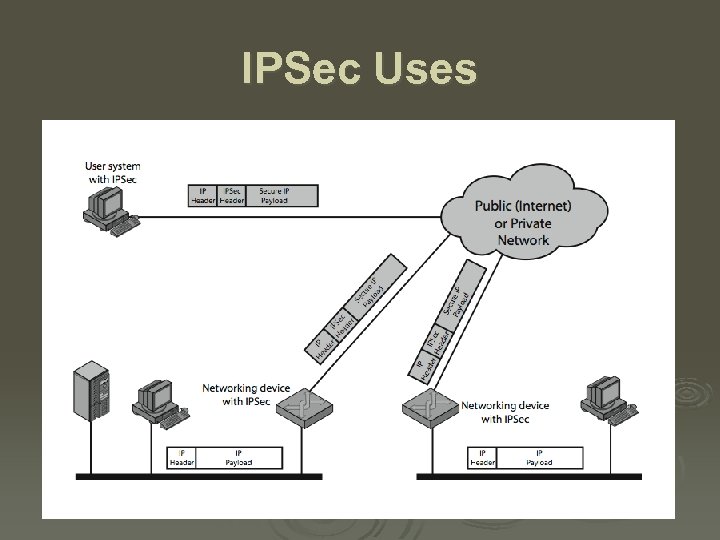 IPSec Uses
IPSec Uses
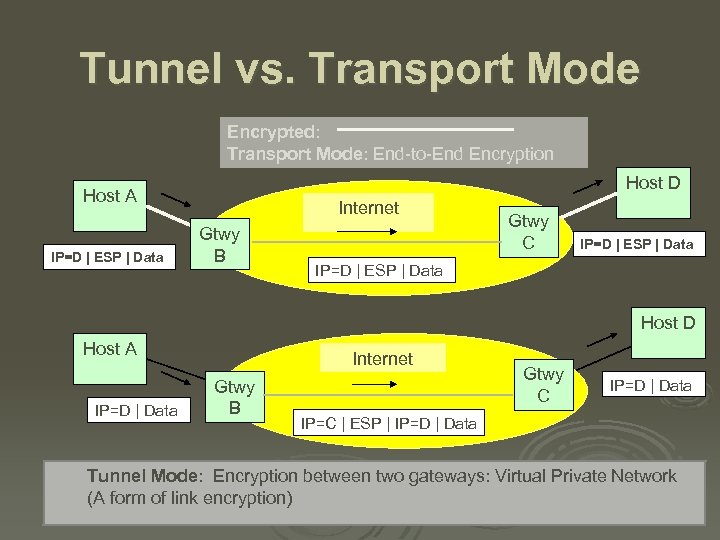 Tunnel vs. Transport Mode Encrypted: Transport Mode: End-to-End Encryption Host D Host A IP=D | ESP | Data Internet Gtwy B Gtwy C IP=D | ESP | Data Host D Host A IP=D | Data Internet Gtwy B Gtwy C IP=D | Data IP=C | ESP | IP=D | Data Tunnel Mode: Encryption between two gateways: Virtual Private Network (A form of link encryption)
Tunnel vs. Transport Mode Encrypted: Transport Mode: End-to-End Encryption Host D Host A IP=D | ESP | Data Internet Gtwy B Gtwy C IP=D | ESP | Data Host D Host A IP=D | Data Internet Gtwy B Gtwy C IP=D | Data IP=C | ESP | IP=D | Data Tunnel Mode: Encryption between two gateways: Virtual Private Network (A form of link encryption)
 Benefits of IPSec Ø in a firewall/router provides strong security to all traffic crossing the perimeter Ø in a firewall/router is resistant to bypass Ø is below transport layer, hence transparent to applications Ø can be transparent to end users Ø can provide security for individual users Ø secures routing architecture
Benefits of IPSec Ø in a firewall/router provides strong security to all traffic crossing the perimeter Ø in a firewall/router is resistant to bypass Ø is below transport layer, hence transparent to applications Ø can be transparent to end users Ø can provide security for individual users Ø secures routing architecture
 IP Security Architecture Ø mandatory in IPv 6, optional in IPv 4 Ø have two security header extensions: l l l Authentication Header (AH) Encapsulating Security Payload (ESP) Key Exchange function Ø VPNs want both authentication/encryption l hence usually use ESP Ø specification is quite complex l numerous RFC’s 2401/2402/2406/2408
IP Security Architecture Ø mandatory in IPv 6, optional in IPv 4 Ø have two security header extensions: l l l Authentication Header (AH) Encapsulating Security Payload (ESP) Key Exchange function Ø VPNs want both authentication/encryption l hence usually use ESP Ø specification is quite complex l numerous RFC’s 2401/2402/2406/2408
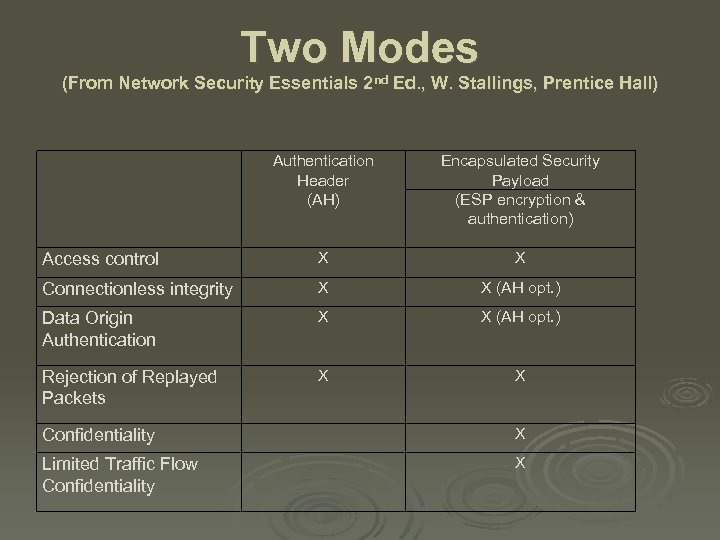 Two Modes (From Network Security Essentials 2 nd Ed. , W. Stallings, Prentice Hall) Authentication Header (AH) Encapsulated Security Payload (ESP encryption & authentication) Access control X X Connectionless integrity X X (AH opt. ) Data Origin Authentication X X (AH opt. ) Rejection of Replayed Packets X X Confidentiality X Limited Traffic Flow Confidentiality X
Two Modes (From Network Security Essentials 2 nd Ed. , W. Stallings, Prentice Hall) Authentication Header (AH) Encapsulated Security Payload (ESP encryption & authentication) Access control X X Connectionless integrity X X (AH opt. ) Data Origin Authentication X X (AH opt. ) Rejection of Replayed Packets X X Confidentiality X Limited Traffic Flow Confidentiality X
 Security Associations Ø a one-way relationship between sender & receiver that affords security for traffic flow Ø defined by 3 parameters: l l l Security Parameters Index (SPI): SA IP Destination Address: Unicast Security Protocol Identifier: AH or EH Ø has a number of other parameters l seq no, AH & EH info, lifetime etc Ø have a database of Security Associations l Holds data for each SA
Security Associations Ø a one-way relationship between sender & receiver that affords security for traffic flow Ø defined by 3 parameters: l l l Security Parameters Index (SPI): SA IP Destination Address: Unicast Security Protocol Identifier: AH or EH Ø has a number of other parameters l seq no, AH & EH info, lifetime etc Ø have a database of Security Associations l Holds data for each SA
 Authentication Header (AH) Ø provides support for data integrity & authentication of IP packets l l end system/router can authenticate user/app prevents address spoofing attacks by tracking sequence numbers Ø based on use of a MAC l HMAC-MD 5 -96 or HMAC-SHA-1 -96 Ø parties must share a secret key
Authentication Header (AH) Ø provides support for data integrity & authentication of IP packets l l end system/router can authenticate user/app prevents address spoofing attacks by tracking sequence numbers Ø based on use of a MAC l HMAC-MD 5 -96 or HMAC-SHA-1 -96 Ø parties must share a secret key
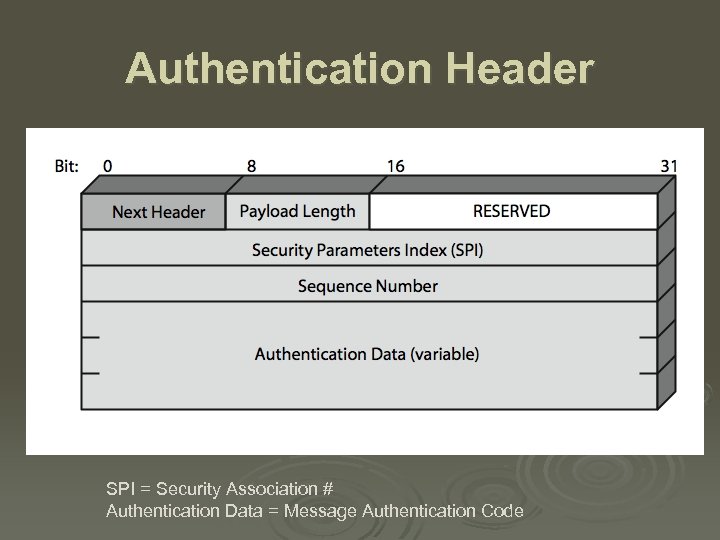 Authentication Header SPI = Security Association # Authentication Data = Message Authentication Code
Authentication Header SPI = Security Association # Authentication Data = Message Authentication Code
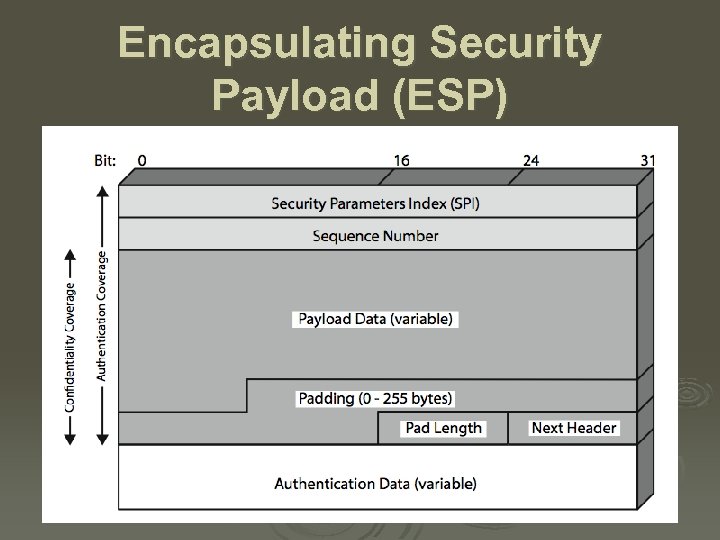 Encapsulating Security Payload (ESP)
Encapsulating Security Payload (ESP)
 Key Management Ø handles key generation & distribution Ø typically need 2 pairs of keys l 2 per direction for AH & ESP Ø manual key management l sysadmin manually configures every system Ø automated key management l l automated system for on demand creation of keys for SA’s in large systems has Oakley & ISAKMP elements
Key Management Ø handles key generation & distribution Ø typically need 2 pairs of keys l 2 per direction for AH & ESP Ø manual key management l sysadmin manually configures every system Ø automated key management l l automated system for on demand creation of keys for SA’s in large systems has Oakley & ISAKMP elements
 S/MIME (Secure/Multipurpose Internet Mail Extensions) Ø security enhancement to MIME email l l original Internet RFC 822 email was text only MIME provided support for varying content types and multi-part messages with encoding of binary data to textual form S/MIME added security enhancements Ø have S/MIME support in many mail agents l eg MS Outlook, Mozilla, Mac Mail etc
S/MIME (Secure/Multipurpose Internet Mail Extensions) Ø security enhancement to MIME email l l original Internet RFC 822 email was text only MIME provided support for varying content types and multi-part messages with encoding of binary data to textual form S/MIME added security enhancements Ø have S/MIME support in many mail agents l eg MS Outlook, Mozilla, Mac Mail etc
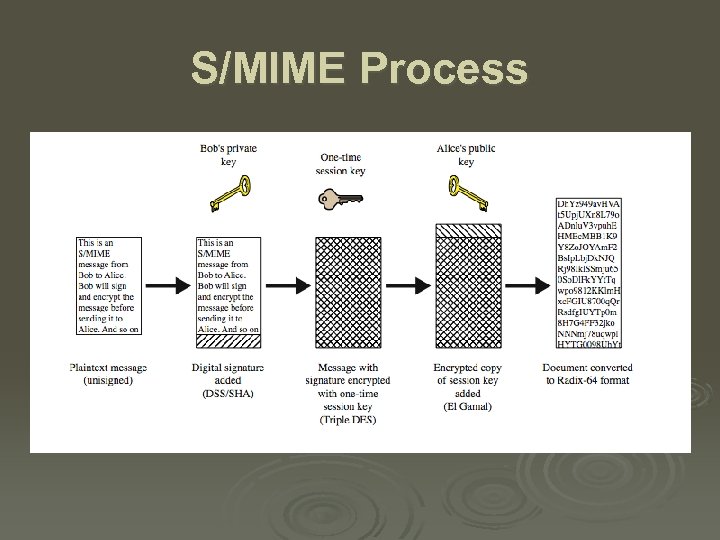 S/MIME Process
S/MIME Process
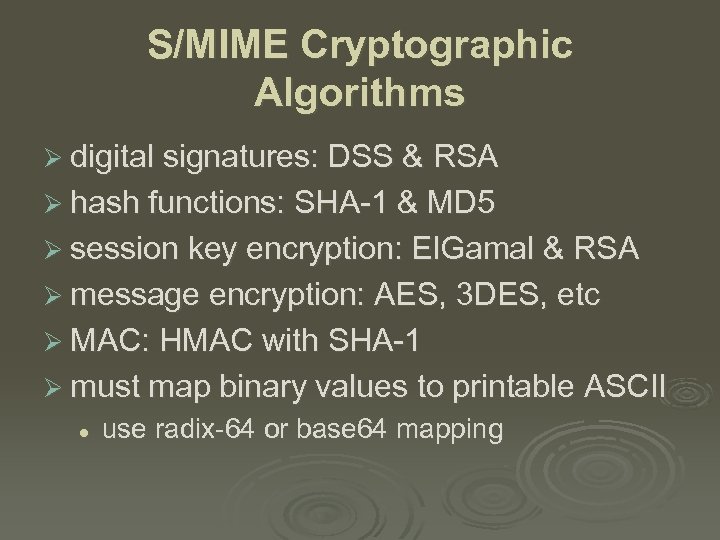 S/MIME Cryptographic Algorithms Ø digital signatures: DSS & RSA Ø hash functions: SHA-1 & MD 5 Ø session key encryption: El. Gamal & RSA Ø message encryption: AES, 3 DES, etc Ø MAC: HMAC with SHA-1 Ø must map binary values to printable ASCII l use radix-64 or base 64 mapping
S/MIME Cryptographic Algorithms Ø digital signatures: DSS & RSA Ø hash functions: SHA-1 & MD 5 Ø session key encryption: El. Gamal & RSA Ø message encryption: AES, 3 DES, etc Ø MAC: HMAC with SHA-1 Ø must map binary values to printable ASCII l use radix-64 or base 64 mapping
 S/MIME Public Key Certificates Ø S/MIME has effective encryption and signature services Ø but also need to manage public-keys Ø S/MIME uses X. 509 v 3 certificates Ø each client has a list of trusted CA’s certs Ø and own public/private key pairs & certs Ø certificates must be signed by trusted CA’s
S/MIME Public Key Certificates Ø S/MIME has effective encryption and signature services Ø but also need to manage public-keys Ø S/MIME uses X. 509 v 3 certificates Ø each client has a list of trusted CA’s certs Ø and own public/private key pairs & certs Ø certificates must be signed by trusted CA’s
 Summary Ø Secure Sockets Layer (SSL) / Transport Layer Security (TLS) Ø IPsec: IPv 4 and IPv 6 Security Ø S/MIME (Secure/Multipurpose Internet Mail Extension)
Summary Ø Secure Sockets Layer (SSL) / Transport Layer Security (TLS) Ø IPsec: IPv 4 and IPv 6 Security Ø S/MIME (Secure/Multipurpose Internet Mail Extension)


