 Computer security: authentication of principals and cryptographic protocols Frans Kaashoek 6. 033 Spring 2007
Computer security: authentication of principals and cryptographic protocols Frans Kaashoek 6. 033 Spring 2007
 HKN Underground Guide https: //sixweb. mit. edu/student/evaluate/6. 033 s 2007 Link posted on 6. 033 home page Deadline: May 20
HKN Underground Guide https: //sixweb. mit. edu/student/evaluate/6. 033 s 2007 Link posted on 6. 033 home page Deadline: May 20
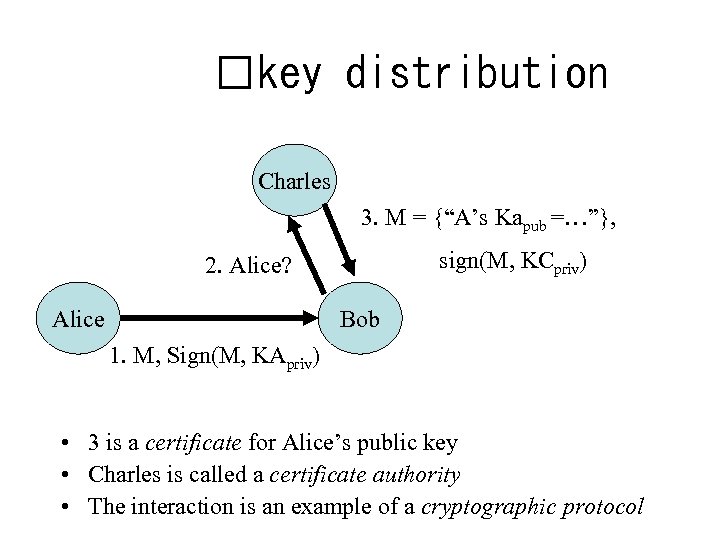 key distribution Charles 3. M = {“A’s Kapub =…”}, sign(M, KCpriv) 2. Alice? Alice Bob 1. M, Sign(M, KApriv) • 3 is a certificate for Alice’s public key • Charles is called a certificate authority • The interaction is an example of a cryptographic protocol
key distribution Charles 3. M = {“A’s Kapub =…”}, sign(M, KCpriv) 2. Alice? Alice Bob 1. M, Sign(M, KApriv) • 3 is a certificate for Alice’s public key • Charles is called a certificate authority • The interaction is an example of a cryptographic protocol
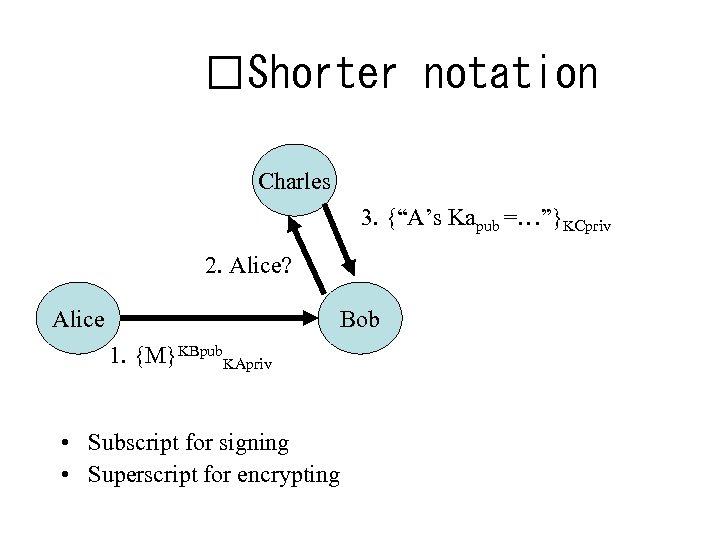 Shorter notation Charles 3. {“A’s Kapub =…”}KCpriv 2. Alice? Alice Bob 1. {M}KBpub. KApriv • Subscript for signing • Superscript for encrypting
Shorter notation Charles 3. {“A’s Kapub =…”}KCpriv 2. Alice? Alice Bob 1. {M}KBpub. KApriv • Subscript for signing • Superscript for encrypting
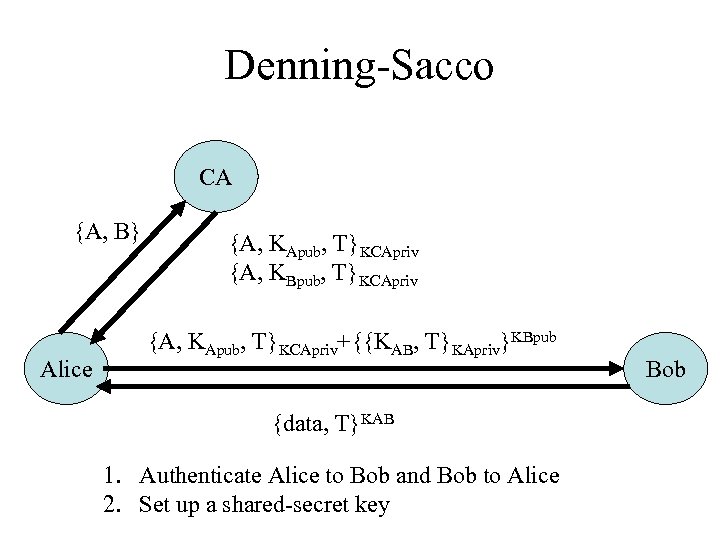 Denning-Sacco CA {A, B} Alice {A, KApub, T}KCApriv {A, KBpub, T}KCApriv {A, KApub, T}KCApriv+{{KAB, T}KApriv}KBpub {data, T}KAB 1. Authenticate Alice to Bob and Bob to Alice 2. Set up a shared-secret key Bob
Denning-Sacco CA {A, B} Alice {A, KApub, T}KCApriv {A, KBpub, T}KCApriv {A, KApub, T}KCApriv+{{KAB, T}KApriv}KBpub {data, T}KAB 1. Authenticate Alice to Bob and Bob to Alice 2. Set up a shared-secret key Bob
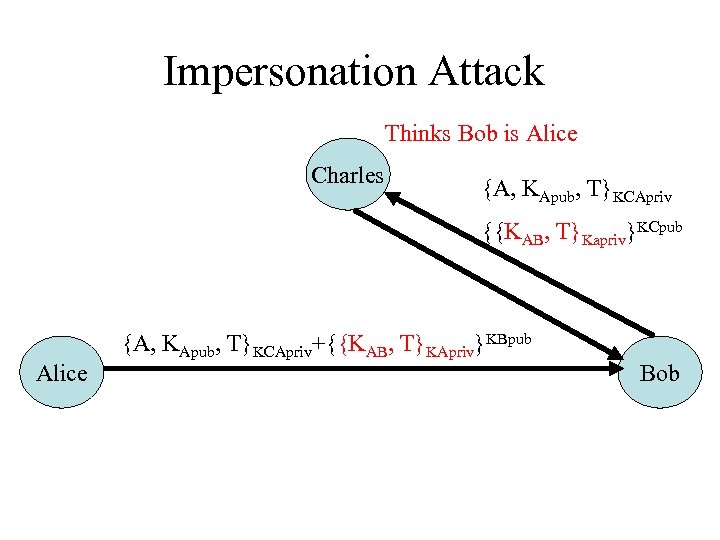 Impersonation Attack Thinks Bob is Alice Charles {A, KApub, T}KCApriv {{KAB, T}Kapriv}KCpub Alice {A, KApub, T}KCApriv+{{KAB, T}KApriv}KBpub Bob
Impersonation Attack Thinks Bob is Alice Charles {A, KApub, T}KCApriv {{KAB, T}Kapriv}KCpub Alice {A, KApub, T}KCApriv+{{KAB, T}KApriv}KBpub Bob
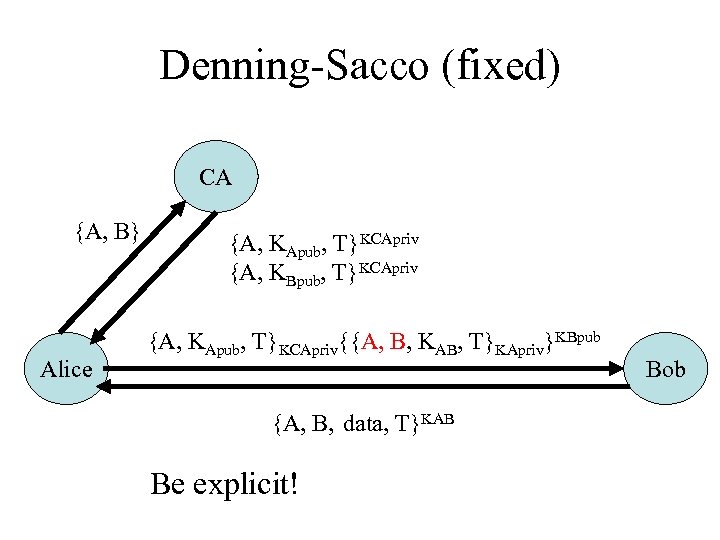 Denning-Sacco (fixed) CA {A, B} Alice {A, KApub, T}KCApriv {A, KBpub, T}KCApriv {A, KApub, T}KCApriv{{A, B, KAB, T}KApriv}KBpub {A, B, data, T}KAB Be explicit! Bob
Denning-Sacco (fixed) CA {A, B} Alice {A, KApub, T}KCApriv {A, KBpub, T}KCApriv {A, KApub, T}KCApriv{{A, B, KAB, T}KApriv}KBpub {A, B, data, T}KAB Be explicit! Bob
 Example: Web (SSL simplified) • U: https: //www. amazon. com • B →W: {randomc, session-id, ciphersuites} • B ← W: {randoms, session-id, {amazon. com, Kpub-amazon}Kversign} • B: verify({amazon. com, Kpub-amazon}Kversign, Kpub-verisign)? • B →W: {pre-master-secret}Kpub-amazon • . . .
Example: Web (SSL simplified) • U: https: //www. amazon. com • B →W: {randomc, session-id, ciphersuites} • B ← W: {randoms, session-id, {amazon. com, Kpub-amazon}Kversign} • B: verify({amazon. com, Kpub-amazon}Kversign, Kpub-verisign)? • B →W: {pre-master-secret}Kpub-amazon • . . .
 X 509 certificate • struct X 509_certificate { unsigned version; unsigned serial; signature_cipher_identifier; issuer_signature; issuer_name; subject_public_key_cipher_identifier; subject_public_key; validity_period; };
X 509 certificate • struct X 509_certificate { unsigned version; unsigned serial; signature_cipher_identifier; issuer_signature; issuer_name; subject_public_key_cipher_identifier; subject_public_key; validity_period; };