 Computer Security 3 e
Computer Security 3 e
 Chapter 1: Cryptography
Chapter 1: Cryptography
 Cryptography
Cryptography
 Origins of Cryptography
Origins of Cryptography
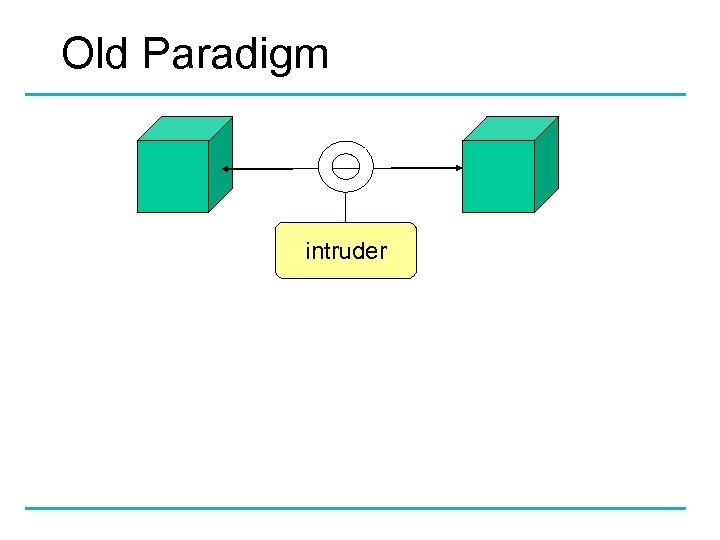 Old Paradigm intruder
Old Paradigm intruder
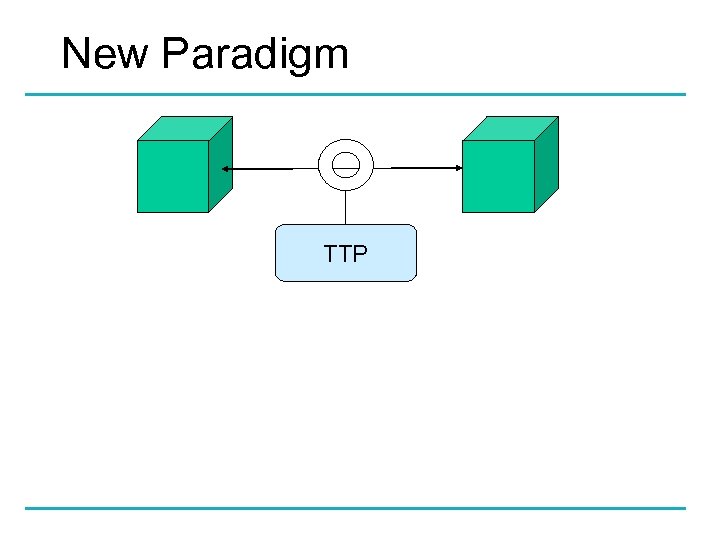 New Paradigm TTP
New Paradigm TTP
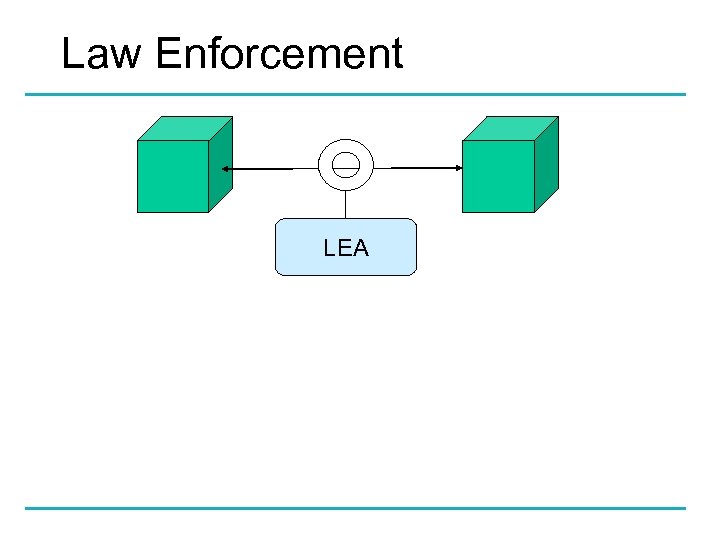 Law Enforcement LEA
Law Enforcement LEA
 Communications Security
Communications Security
 Cryptographic Keys
Cryptographic Keys
 Shifting the Goal Post
Shifting the Goal Post
 Crypto in Computer Security
Crypto in Computer Security
 Modular Arithmetic
Modular Arithmetic
 Fermat’s Little Theorem
Fermat’s Little Theorem
 Difficult Problems
Difficult Problems
 Integrity Check Functions
Integrity Check Functions
 One-way Functions
One-way Functions
 Collisions
Collisions
 Collision Resistance
Collision Resistance
 Birthday Paradox
Birthday Paradox
 Checksums
Checksums
 Discrete Exponentiation
Discrete Exponentiation
 Construction
Construction
 Construction
Construction
 HMAC (simplified)
HMAC (simplified)
 Digital signatures
Digital signatures
 Digital Signatures
Digital Signatures
 Digital Signatures
Digital Signatures
 One-time Signatures
One-time Signatures
 Digital Signature Algorithm
Digital Signature Algorithm
 Digital Signature Algorithm
Digital Signature Algorithm
 RSA Signatures
RSA Signatures
 RSA Signatures
RSA Signatures
 Performance Gains
Performance Gains
 Factorization & RSA
Factorization & RSA
 MACs & Digital Signatures
MACs & Digital Signatures
 Encryption
Encryption
 Terminology
Terminology
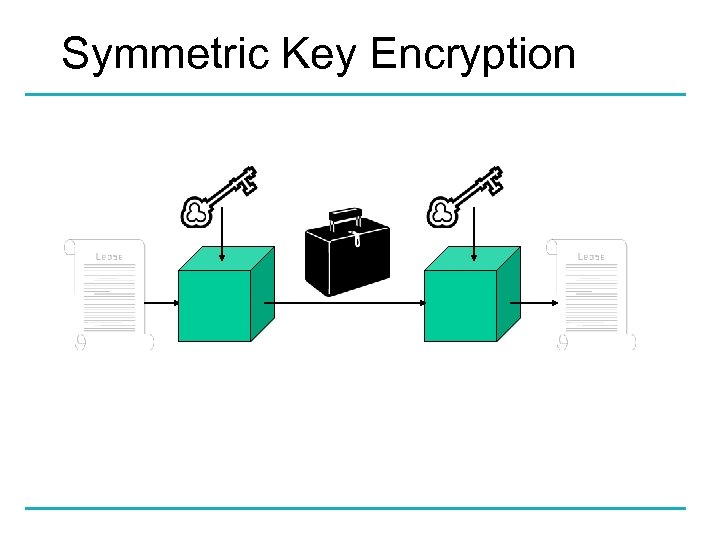 Symmetric Key Encryption
Symmetric Key Encryption
 Block Cipher Basics
Block Cipher Basics
 Round Structure
Round Structure
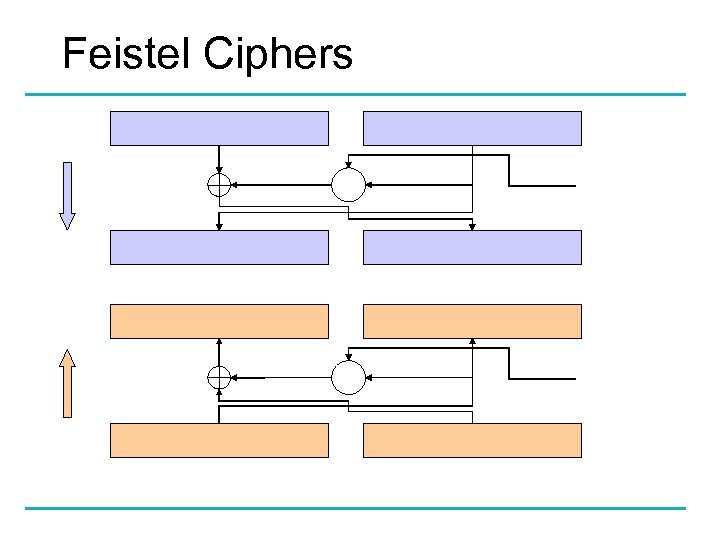 Feistel Ciphers
Feistel Ciphers
 Algorithms
Algorithms
 Data Encryption Standard
Data Encryption Standard
 Comments on Security
Comments on Security
 Using Encryption for Real
Using Encryption for Real
 Electronic Code Book Mode
Electronic Code Book Mode
 Error Propagation
Error Propagation
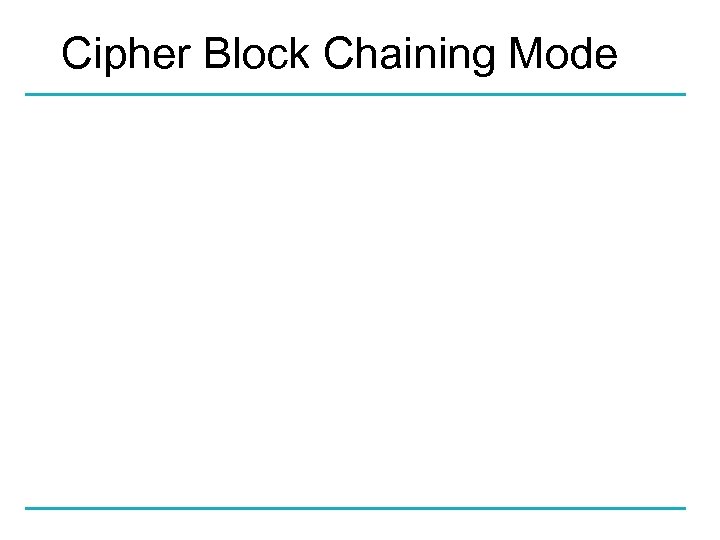 Cipher Block Chaining Mode
Cipher Block Chaining Mode
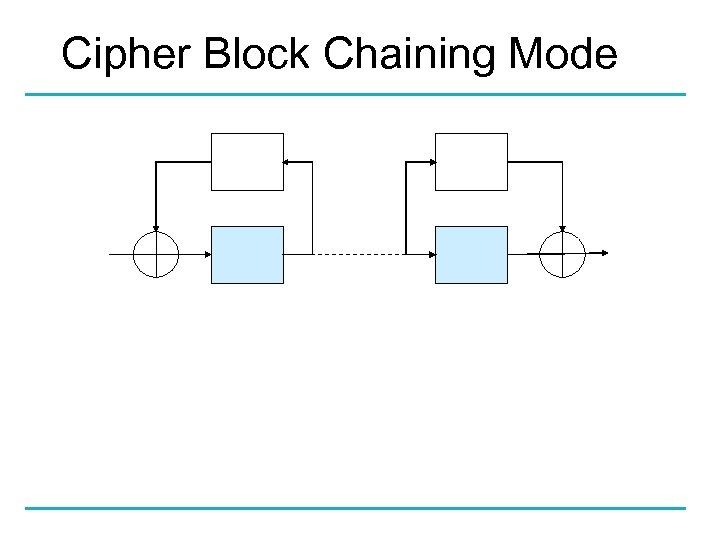 Cipher Block Chaining Mode
Cipher Block Chaining Mode
 Cipher Block Chaining Mode
Cipher Block Chaining Mode
 A Note on Plaintexts
A Note on Plaintexts
 Cipher Feedback Mode
Cipher Feedback Mode
 More Modes
More Modes
 Public key Encryption
Public key Encryption
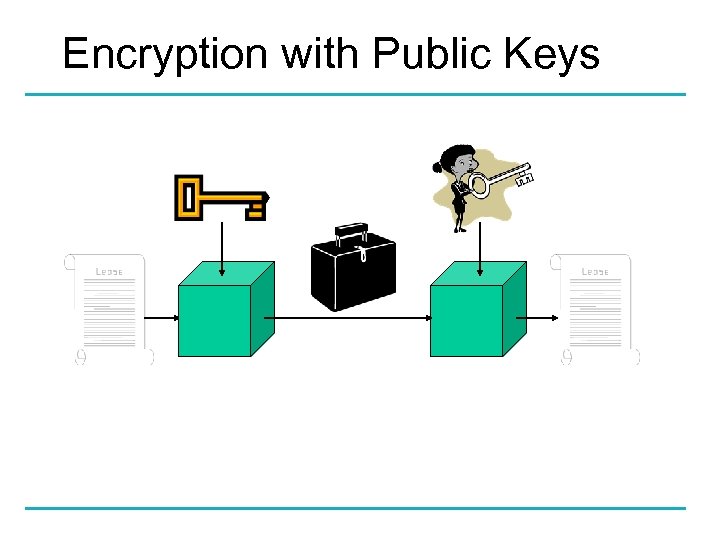 Encryption with Public Keys
Encryption with Public Keys
 Public key Encryption
Public key Encryption
 Public Key Infrastructures
Public Key Infrastructures
 RSA Encryption
RSA Encryption
 RSA Encryption
RSA Encryption
 Padding
Padding
 Bleichenbacher’s Attack
Bleichenbacher’s Attack
 Strength of Mechanisms
Strength of Mechanisms
 Performance
Performance
 Performance
Performance
 Comment on PKC
Comment on PKC