 Computer Security 1
Computer Security 1
 Computer Security 2
Computer Security 2
 Notation Computer Security 3
Notation Computer Security 3
 Session, Interchange Keys Computer Security 4
Session, Interchange Keys Computer Security 4
 Benefits Computer Security 5
Benefits Computer Security 5
 Key Exchange Algorithms Computer Security 6
Key Exchange Algorithms Computer Security 6
 Classical Key Exchange Computer Security 7
Classical Key Exchange Computer Security 7
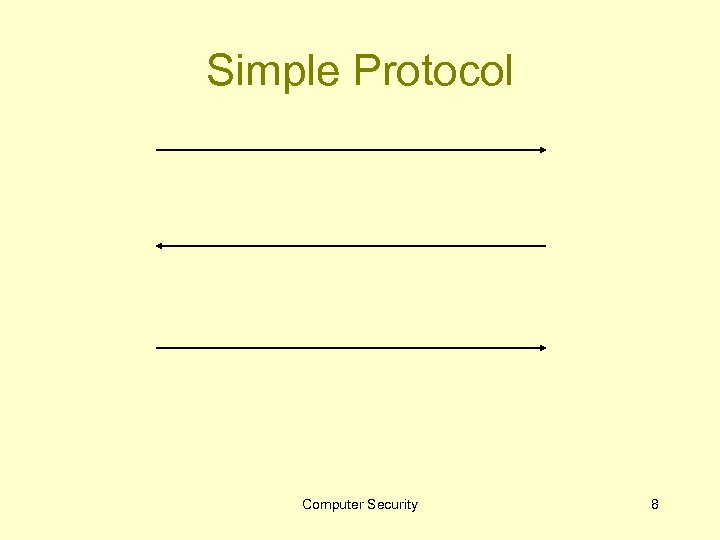 Simple Protocol Computer Security 8
Simple Protocol Computer Security 8
 Problems ? Computer Security 9
Problems ? Computer Security 9
 Needham-Schroeder Computer Security 10
Needham-Schroeder Computer Security 10
 Argument: Alice talking to Bob Computer Security 11
Argument: Alice talking to Bob Computer Security 11
 Argument: Bob talking to Alice Computer Security 12
Argument: Bob talking to Alice Computer Security 12
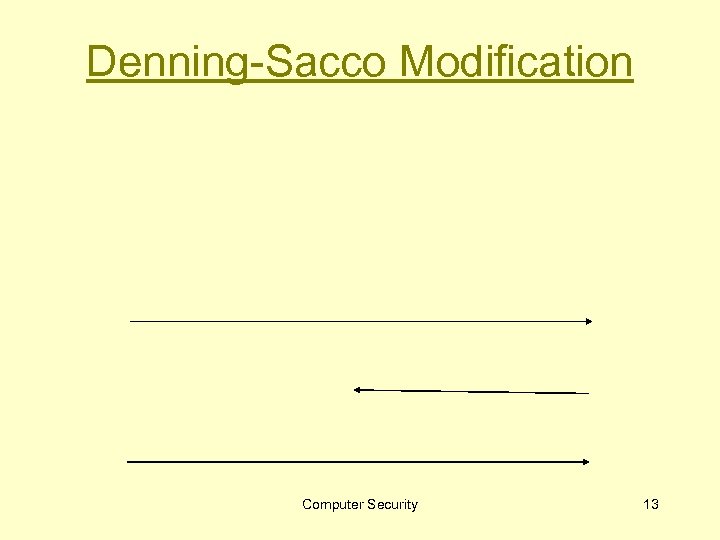 Denning-Sacco Modification Computer Security 13
Denning-Sacco Modification Computer Security 13
 Problem & Solution Computer Security 14
Problem & Solution Computer Security 14
 Needham-Schroeder with Denning-Sacco Modification Computer Security 15
Needham-Schroeder with Denning-Sacco Modification Computer Security 15
 Needham-Schroeder with Denning-Sacco Modification Computer Security 16
Needham-Schroeder with Denning-Sacco Modification Computer Security 16
 Otway-Rees Protocol Computer Security 17
Otway-Rees Protocol Computer Security 17
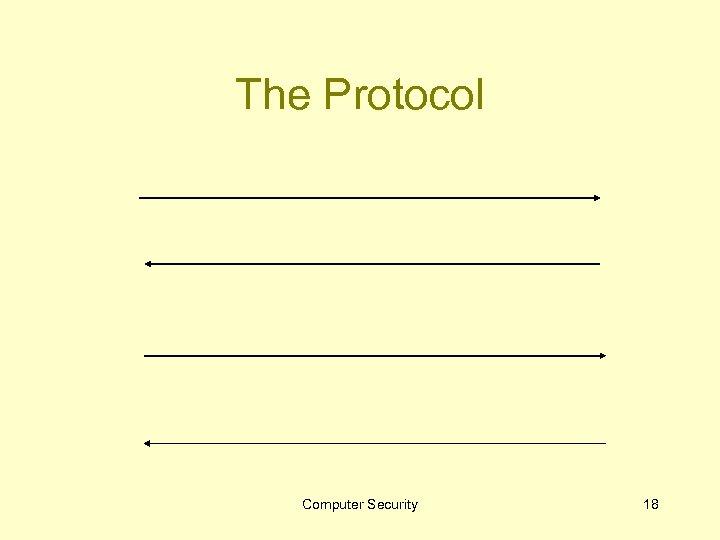 The Protocol Computer Security 18
The Protocol Computer Security 18
 Argument: Alice talking to Bob Computer Security 19
Argument: Alice talking to Bob Computer Security 19
 Argument: Bob talking to Alice Computer Security 20
Argument: Bob talking to Alice Computer Security 20
 Computer Security 21
Computer Security 21
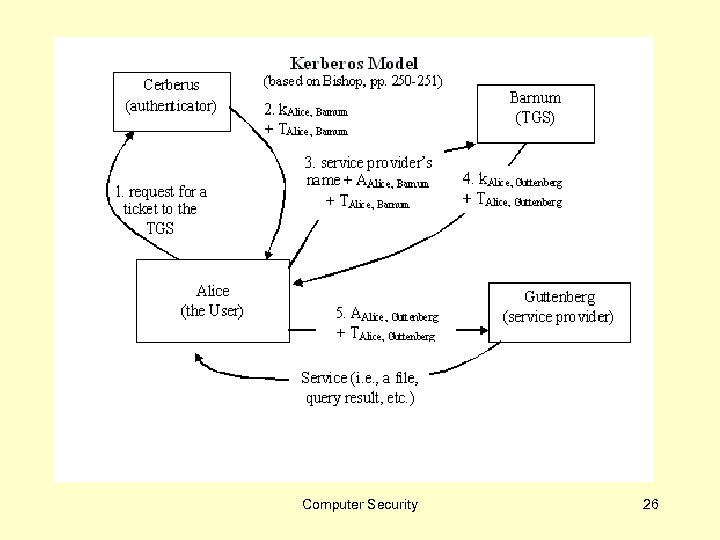
 Kerberos Computer Security 22
Kerberos Computer Security 22
 Idea Computer Security 23
Idea Computer Security 23
 Computer Security 24
Computer Security 24
 Authenticator Computer Security 25
Authenticator Computer Security 25
 Computer Security 26
Computer Security 26
 Computer Security 27
Computer Security 27
 Computer Security 28
Computer Security 28
 Analysis Computer Security 29
Analysis Computer Security 29
 Computer Security 30
Computer Security 30
 Key Exchange using Public Key Computer Security 31
Key Exchange using Public Key Computer Security 31
 Problem and Solution Computer Security 32
Problem and Solution Computer Security 32
 Notes Computer Security 33
Notes Computer Security 33
 Computer Security 34
Computer Security 34
 Key Generation Computer Security 35
Key Generation Computer Security 35
 What is “Random”? Computer Security 36
What is “Random”? Computer Security 36
 What is “Pseudorandom”? Computer Security 37
What is “Pseudorandom”? Computer Security 37
 Best Pseudorandom Numbers Computer Security 38
Best Pseudorandom Numbers Computer Security 38
 Computer Security 39
Computer Security 39
 Computer Security 40
Computer Security 40
 Computer Security 41
Computer Security 41