b1defdc8b0fbd43a7d62d7096b40dd57.ppt
- Количество слайдов: 84
 Computer Science IPSec CPSC 499 Information Security Management
Computer Science IPSec CPSC 499 Information Security Management
 Outline • Internet Protocol – – Datagram format IPv 4 addressing NAT IPv 6 • IPSec – – Security Association (SA) IPSec Base Protocol (AH, ESP) Encapsulation Mode (transport, tunnel) Key Management Computer Science
Outline • Internet Protocol – – Datagram format IPv 4 addressing NAT IPv 6 • IPSec – – Security Association (SA) IPSec Base Protocol (AH, ESP) Encapsulation Mode (transport, tunnel) Key Management Computer Science
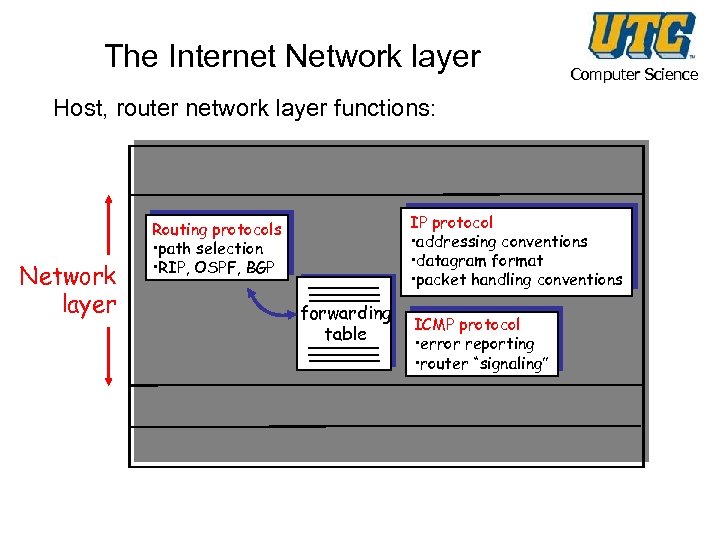 The Internet Network layer Computer Science Host, router network layer functions: Transport layer: TCP, UDP Network layer IP protocol • addressing conventions • datagram format • packet handling conventions Routing protocols • path selection • RIP, OSPF, BGP forwarding table ICMP protocol • error reporting • router “signaling” Link layer physical layer
The Internet Network layer Computer Science Host, router network layer functions: Transport layer: TCP, UDP Network layer IP protocol • addressing conventions • datagram format • packet handling conventions Routing protocols • path selection • RIP, OSPF, BGP forwarding table ICMP protocol • error reporting • router “signaling” Link layer physical layer
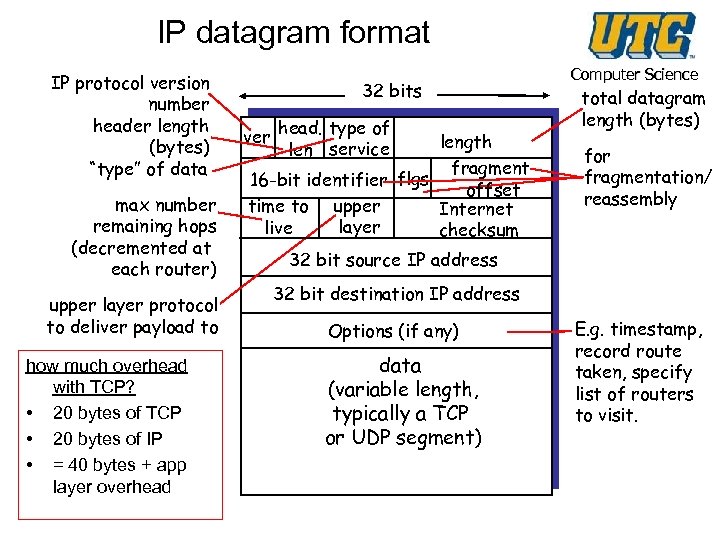 IP datagram format IP protocol version number header length (bytes) “type” of data max number remaining hops (decremented at each router) upper layer protocol to deliver payload to how much overhead with TCP? • 20 bytes of TCP • 20 bytes of IP • = 40 bytes + app layer overhead 32 bits ver head. type of len service length fragment 16 -bit identifier flgs offset upper time to Internet layer live checksum Computer Science total datagram length (bytes) for fragmentation/ reassembly 32 bit source IP address 32 bit destination IP address Options (if any) data (variable length, typically a TCP or UDP segment) E. g. timestamp, record route taken, specify list of routers to visit.
IP datagram format IP protocol version number header length (bytes) “type” of data max number remaining hops (decremented at each router) upper layer protocol to deliver payload to how much overhead with TCP? • 20 bytes of TCP • 20 bytes of IP • = 40 bytes + app layer overhead 32 bits ver head. type of len service length fragment 16 -bit identifier flgs offset upper time to Internet layer live checksum Computer Science total datagram length (bytes) for fragmentation/ reassembly 32 bit source IP address 32 bit destination IP address Options (if any) data (variable length, typically a TCP or UDP segment) E. g. timestamp, record route taken, specify list of routers to visit.
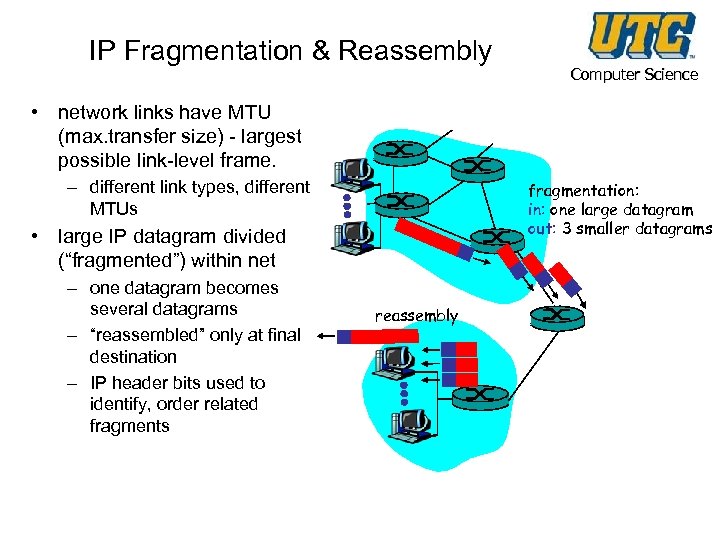 IP Fragmentation & Reassembly Computer Science • network links have MTU (max. transfer size) - largest possible link-level frame. – different link types, different MTUs fragmentation: in: one large datagram out: 3 smaller datagrams • large IP datagram divided (“fragmented”) within net – one datagram becomes several datagrams – “reassembled” only at final destination – IP header bits used to identify, order related fragments reassembly
IP Fragmentation & Reassembly Computer Science • network links have MTU (max. transfer size) - largest possible link-level frame. – different link types, different MTUs fragmentation: in: one large datagram out: 3 smaller datagrams • large IP datagram divided (“fragmented”) within net – one datagram becomes several datagrams – “reassembled” only at final destination – IP header bits used to identify, order related fragments reassembly
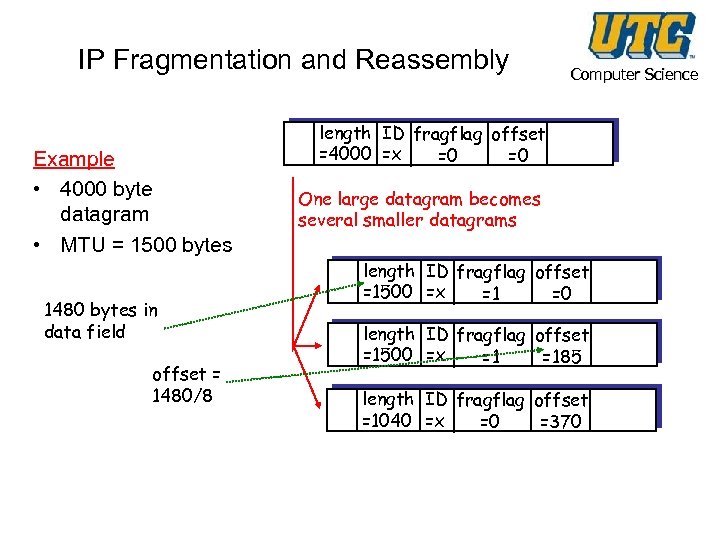 IP Fragmentation and Reassembly Example • 4000 byte datagram • MTU = 1500 bytes 1480 bytes in data field offset = 1480/8 Computer Science length ID fragflag offset =4000 =x =0 =0 One large datagram becomes several smaller datagrams length ID fragflag offset =1500 =x =1 =0 length ID fragflag offset =1500 =x =1 =185 length ID fragflag offset =1040 =x =0 =370
IP Fragmentation and Reassembly Example • 4000 byte datagram • MTU = 1500 bytes 1480 bytes in data field offset = 1480/8 Computer Science length ID fragflag offset =4000 =x =0 =0 One large datagram becomes several smaller datagrams length ID fragflag offset =1500 =x =1 =0 length ID fragflag offset =1500 =x =1 =185 length ID fragflag offset =1040 =x =0 =370
 Outline • Internet Protocol – – Datagram format IPv 4 addressing NAT IPv 6 • IPSec – – Security Association (SA) IPSec Base Protocol (AH, ESP) Encapsulation Mode (transport, tunnel) Key Management Computer Science
Outline • Internet Protocol – – Datagram format IPv 4 addressing NAT IPv 6 • IPSec – – Security Association (SA) IPSec Base Protocol (AH, ESP) Encapsulation Mode (transport, tunnel) Key Management Computer Science
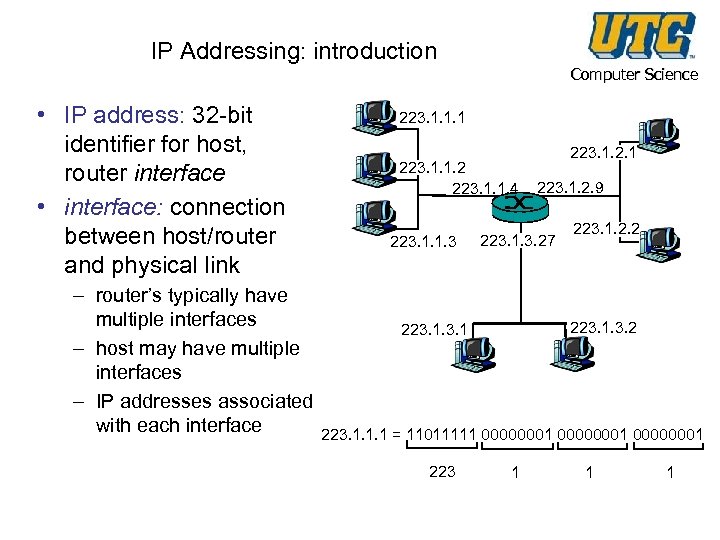 IP Addressing: introduction • IP address: 32 -bit identifier for host, router interface • interface: connection between host/router and physical link – router’s typically have multiple interfaces – host may have multiple interfaces – IP addresses associated with each interface Computer Science 223. 1. 1. 1 223. 1. 1. 2 223. 1. 1. 4 223. 1. 1. 3 223. 1. 2. 1 223. 1. 2. 9 223. 1. 3. 27 223. 1. 2. 2 223. 1. 1. 1 = 11011111 00000001 223 1 1 1
IP Addressing: introduction • IP address: 32 -bit identifier for host, router interface • interface: connection between host/router and physical link – router’s typically have multiple interfaces – host may have multiple interfaces – IP addresses associated with each interface Computer Science 223. 1. 1. 1 223. 1. 1. 2 223. 1. 1. 4 223. 1. 1. 3 223. 1. 2. 1 223. 1. 2. 9 223. 1. 3. 27 223. 1. 2. 2 223. 1. 1. 1 = 11011111 00000001 223 1 1 1
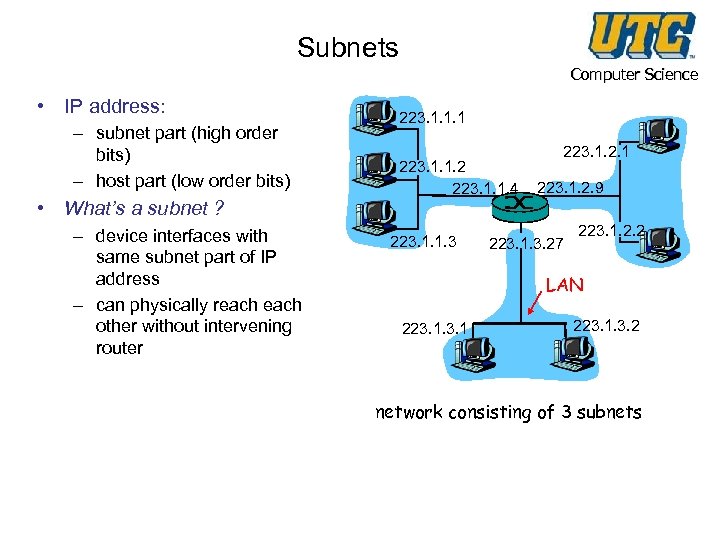 Subnets Computer Science • IP address: – subnet part (high order bits) – host part (low order bits) • What’s a subnet ? – device interfaces with same subnet part of IP address – can physically reach other without intervening router 223. 1. 1. 1 223. 1. 1. 2 223. 1. 1. 4 223. 1. 1. 3 223. 1. 2. 1 223. 1. 2. 9 223. 1. 3. 27 223. 1. 2. 2 LAN 223. 1. 3. 2 network consisting of 3 subnets
Subnets Computer Science • IP address: – subnet part (high order bits) – host part (low order bits) • What’s a subnet ? – device interfaces with same subnet part of IP address – can physically reach other without intervening router 223. 1. 1. 1 223. 1. 1. 2 223. 1. 1. 4 223. 1. 1. 3 223. 1. 2. 1 223. 1. 2. 9 223. 1. 3. 27 223. 1. 2. 2 LAN 223. 1. 3. 2 network consisting of 3 subnets
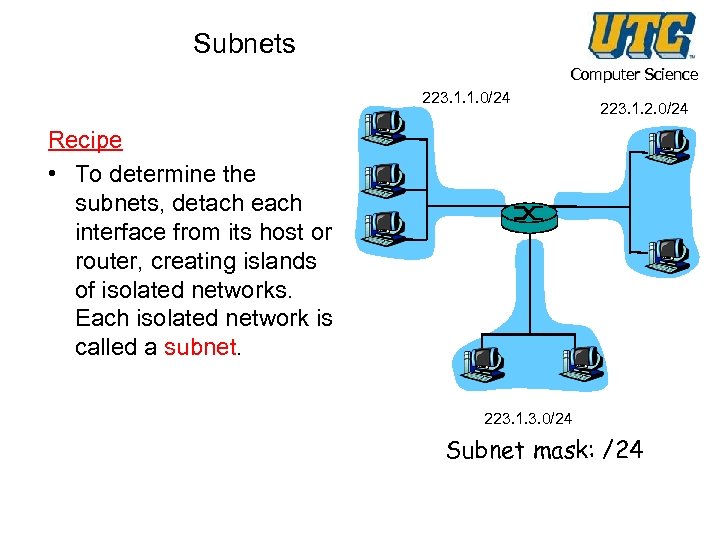 Subnets Computer Science 223. 1. 1. 0/24 223. 1. 2. 0/24 Recipe • To determine the subnets, detach each interface from its host or router, creating islands of isolated networks. Each isolated network is called a subnet. 223. 1. 3. 0/24 Subnet mask: /24
Subnets Computer Science 223. 1. 1. 0/24 223. 1. 2. 0/24 Recipe • To determine the subnets, detach each interface from its host or router, creating islands of isolated networks. Each isolated network is called a subnet. 223. 1. 3. 0/24 Subnet mask: /24
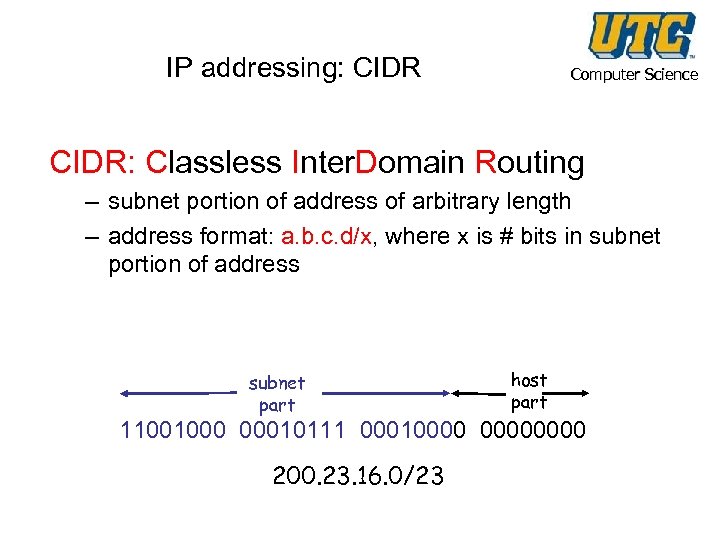 IP addressing: CIDR Computer Science CIDR: Classless Inter. Domain Routing – subnet portion of address of arbitrary length – address format: a. b. c. d/x, where x is # bits in subnet portion of address subnet part host part 11001000 00010111 00010000 200. 23. 16. 0/23
IP addressing: CIDR Computer Science CIDR: Classless Inter. Domain Routing – subnet portion of address of arbitrary length – address format: a. b. c. d/x, where x is # bits in subnet portion of address subnet part host part 11001000 00010111 00010000 200. 23. 16. 0/23
 IP addresses: how to get one? Computer Science Q: How does host get IP address? • hard-coded by system admin in a file – Wintel: control-panel->network->configuration>tcp/ip->properties – UNIX: /etc/rc. config • DHCP: Dynamic Host Configuration Protocol: dynamically get address from as server – “plug-and-play” (more in next chapter)
IP addresses: how to get one? Computer Science Q: How does host get IP address? • hard-coded by system admin in a file – Wintel: control-panel->network->configuration>tcp/ip->properties – UNIX: /etc/rc. config • DHCP: Dynamic Host Configuration Protocol: dynamically get address from as server – “plug-and-play” (more in next chapter)
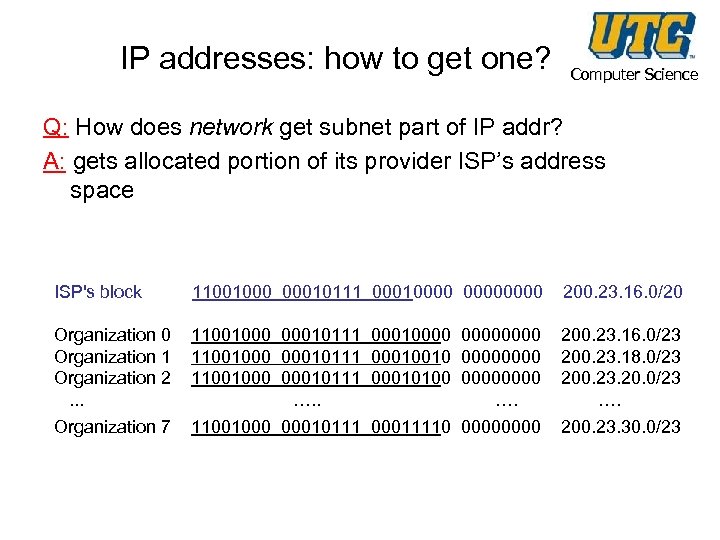 IP addresses: how to get one? Computer Science Q: How does network get subnet part of IP addr? A: gets allocated portion of its provider ISP’s address space ISP's block 11001000 00010111 00010000 200. 23. 16. 0/20 Organization 1 Organization 2. . . 11001000 00010111 00010000 11001000 00010111 00010010 0000 11001000 00010111 00010100 0000 …. 200. 23. 16. 0/23 200. 23. 18. 0/23 200. 23. 20. 0/23 …. Organization 7 11001000 00010111 00011110 0000 200. 23. 30. 0/23
IP addresses: how to get one? Computer Science Q: How does network get subnet part of IP addr? A: gets allocated portion of its provider ISP’s address space ISP's block 11001000 00010111 00010000 200. 23. 16. 0/20 Organization 1 Organization 2. . . 11001000 00010111 00010000 11001000 00010111 00010010 0000 11001000 00010111 00010100 0000 …. 200. 23. 16. 0/23 200. 23. 18. 0/23 200. 23. 20. 0/23 …. Organization 7 11001000 00010111 00011110 0000 200. 23. 30. 0/23
 Outline • Internet Protocol – – Datagram format IPv 4 addressing NAT IPv 6 • IPSec – – Security Association (SA) IPSec Base Protocol (AH, ESP) Encapsulation Mode (transport, tunnel) Key Management Computer Science
Outline • Internet Protocol – – Datagram format IPv 4 addressing NAT IPv 6 • IPSec – – Security Association (SA) IPSec Base Protocol (AH, ESP) Encapsulation Mode (transport, tunnel) Key Management Computer Science
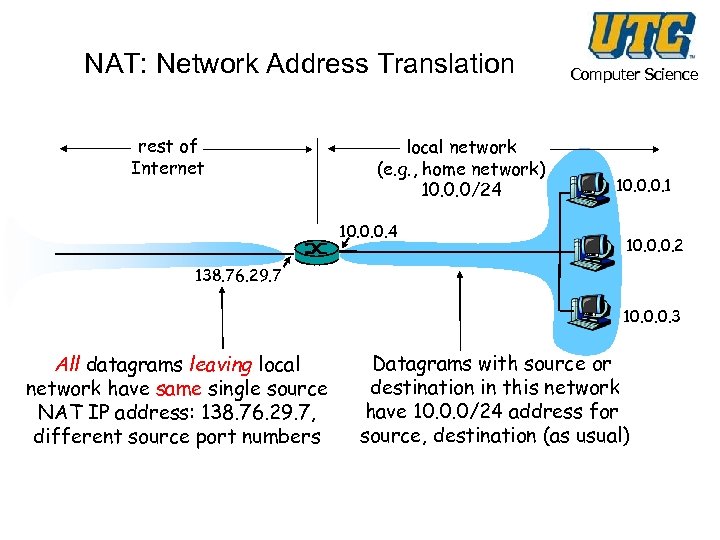 NAT: Network Address Translation rest of Internet local network (e. g. , home network) 10. 0. 0/24 10. 0. 0. 4 Computer Science 10. 0. 0. 1 10. 0. 0. 2 138. 76. 29. 7 10. 0. 0. 3 All datagrams leaving local network have same single source NAT IP address: 138. 76. 29. 7, different source port numbers Datagrams with source or destination in this network have 10. 0. 0/24 address for source, destination (as usual)
NAT: Network Address Translation rest of Internet local network (e. g. , home network) 10. 0. 0/24 10. 0. 0. 4 Computer Science 10. 0. 0. 1 10. 0. 0. 2 138. 76. 29. 7 10. 0. 0. 3 All datagrams leaving local network have same single source NAT IP address: 138. 76. 29. 7, different source port numbers Datagrams with source or destination in this network have 10. 0. 0/24 address for source, destination (as usual)
 NAT: Network Address Translation Computer Science • Motivation: local network uses just one IP address as far as outside word is concerned: – no need to be allocated range of addresses from ISP: just one IP address is used for all devices – can change addresses of devices in local network without notifying outside world – can change ISP without changing addresses of devices in local network – devices inside local net not explicitly addressable, visible by outside world (a security plus).
NAT: Network Address Translation Computer Science • Motivation: local network uses just one IP address as far as outside word is concerned: – no need to be allocated range of addresses from ISP: just one IP address is used for all devices – can change addresses of devices in local network without notifying outside world – can change ISP without changing addresses of devices in local network – devices inside local net not explicitly addressable, visible by outside world (a security plus).
 NAT: Network Address Translation Computer Science Implementation: NAT router must: – outgoing datagrams: replace (source IP address, port #) of every outgoing datagram to (NAT IP address, new port #). . . remote clients/servers will respond using (NAT IP address, new port #) as destination addr. – remember (in NAT translation table) every (source IP address, port #) to (NAT IP address, new port #) translation pair – incoming datagrams: replace (NAT IP address, new port #) in dest fields of every incoming datagram with corresponding (source IP address, port #) stored in NAT table
NAT: Network Address Translation Computer Science Implementation: NAT router must: – outgoing datagrams: replace (source IP address, port #) of every outgoing datagram to (NAT IP address, new port #). . . remote clients/servers will respond using (NAT IP address, new port #) as destination addr. – remember (in NAT translation table) every (source IP address, port #) to (NAT IP address, new port #) translation pair – incoming datagrams: replace (NAT IP address, new port #) in dest fields of every incoming datagram with corresponding (source IP address, port #) stored in NAT table
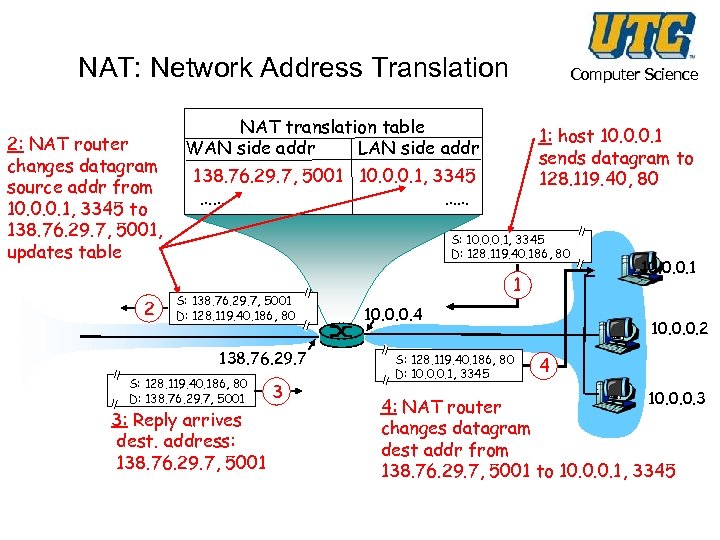 NAT: Network Address Translation 2: NAT router changes datagram source addr from 10. 0. 0. 1, 3345 to 138. 76. 29. 7, 5001, updates table 2 Computer Science NAT translation table WAN side addr LAN side addr 1: host 10. 0. 0. 1 sends datagram to 128. 119. 40, 80 138. 76. 29. 7, 5001 10. 0. 0. 1, 3345 …… …… S: 10. 0. 0. 1, 3345 D: 128. 119. 40. 186, 80 S: 138. 76. 29. 7, 5001 D: 128. 119. 40. 186, 80 138. 76. 29. 7 S: 128. 119. 40. 186, 80 D: 138. 76. 29. 7, 5001 3: Reply arrives dest. address: 138. 76. 29. 7, 5001 3 1 10. 0. 0. 4 S: 128. 119. 40. 186, 80 D: 10. 0. 0. 1, 3345 10. 0. 0. 1 10. 0. 0. 2 4 10. 0. 0. 3 4: NAT router changes datagram dest addr from 138. 76. 29. 7, 5001 to 10. 0. 0. 1, 3345
NAT: Network Address Translation 2: NAT router changes datagram source addr from 10. 0. 0. 1, 3345 to 138. 76. 29. 7, 5001, updates table 2 Computer Science NAT translation table WAN side addr LAN side addr 1: host 10. 0. 0. 1 sends datagram to 128. 119. 40, 80 138. 76. 29. 7, 5001 10. 0. 0. 1, 3345 …… …… S: 10. 0. 0. 1, 3345 D: 128. 119. 40. 186, 80 S: 138. 76. 29. 7, 5001 D: 128. 119. 40. 186, 80 138. 76. 29. 7 S: 128. 119. 40. 186, 80 D: 138. 76. 29. 7, 5001 3: Reply arrives dest. address: 138. 76. 29. 7, 5001 3 1 10. 0. 0. 4 S: 128. 119. 40. 186, 80 D: 10. 0. 0. 1, 3345 10. 0. 0. 1 10. 0. 0. 2 4 10. 0. 0. 3 4: NAT router changes datagram dest addr from 138. 76. 29. 7, 5001 to 10. 0. 0. 1, 3345
 NAT: Network Address Translation Computer Science • 16 -bit port-number field: – 60, 000 simultaneous connections with a single LANside address! • NAT is controversial: – routers should only process up to layer 3 – violates end-to-end argument • NAT possibility must be taken into account by app designers, eg, P 2 P applications – address shortage should instead be solved by IPv 6
NAT: Network Address Translation Computer Science • 16 -bit port-number field: – 60, 000 simultaneous connections with a single LANside address! • NAT is controversial: – routers should only process up to layer 3 – violates end-to-end argument • NAT possibility must be taken into account by app designers, eg, P 2 P applications – address shortage should instead be solved by IPv 6
 Outline • Internet Protocol – – Datagram format IPv 4 addressing NAT IPv 6 • IPSec – – Security Association (SA) IPSec Base Protocol (AH, ESP) Encapsulation Mode (transport, tunnel) Key Management Computer Science
Outline • Internet Protocol – – Datagram format IPv 4 addressing NAT IPv 6 • IPSec – – Security Association (SA) IPSec Base Protocol (AH, ESP) Encapsulation Mode (transport, tunnel) Key Management Computer Science
 IPv 6 Header • Initial motivation: Computer Science – 32 -bit address space soon to be completely allocated. – Expands addresses to 128 bits • 430, 000, 000 for every square inch of earth’s surface! • Solves IPv 4 problem of insufficient address space • Additional motivation: – header format helps speed processing/forwarding – header changes to facilitate Qo. S IPv 6 datagram format: – fixed-length 40 byte header – no fragmentation allowed
IPv 6 Header • Initial motivation: Computer Science – 32 -bit address space soon to be completely allocated. – Expands addresses to 128 bits • 430, 000, 000 for every square inch of earth’s surface! • Solves IPv 4 problem of insufficient address space • Additional motivation: – header format helps speed processing/forwarding – header changes to facilitate Qo. S IPv 6 datagram format: – fixed-length 40 byte header – no fragmentation allowed
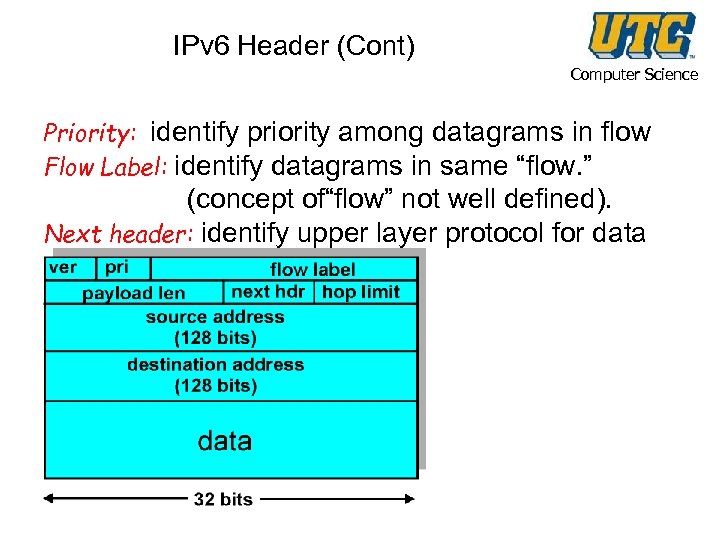 IPv 6 Header (Cont) Computer Science Priority: identify priority among datagrams in flow Flow Label: identify datagrams in same “flow. ” (concept of“flow” not well defined). Next header: identify upper layer protocol for data
IPv 6 Header (Cont) Computer Science Priority: identify priority among datagrams in flow Flow Label: identify datagrams in same “flow. ” (concept of“flow” not well defined). Next header: identify upper layer protocol for data
 Other Changes from IPv 4 Computer Science • Checksum: removed entirely to reduce processing time at each hop • Options: allowed, but outside of header, indicated by “Next Header” field • ICMPv 6: new version of ICMP – additional message types, e. g. “Packet Too Big” – multicast group management functions
Other Changes from IPv 4 Computer Science • Checksum: removed entirely to reduce processing time at each hop • Options: allowed, but outside of header, indicated by “Next Header” field • ICMPv 6: new version of ICMP – additional message types, e. g. “Packet Too Big” – multicast group management functions
 IPv 6 Security – IPsec mandated Computer Science • IPsec is mandated in IPv 6 – This means that all implementations (i. e. hosts, routers, etc) must have IPsec capability to be considered as IPv 6 -conformant • When (If? ) IPv 6 is in widespread use, this means that IPsec will be installed everywhere – At the moment, IPsec is more common in network devices (routers, etc) than user hosts, but this would change with IPsec • All hosts having IPsec => real end-to-end security possible
IPv 6 Security – IPsec mandated Computer Science • IPsec is mandated in IPv 6 – This means that all implementations (i. e. hosts, routers, etc) must have IPsec capability to be considered as IPv 6 -conformant • When (If? ) IPv 6 is in widespread use, this means that IPsec will be installed everywhere – At the moment, IPsec is more common in network devices (routers, etc) than user hosts, but this would change with IPsec • All hosts having IPsec => real end-to-end security possible
 IPv 6 Security Computer Science • Enough IP addrs for every imaginable device + Real end-to-end security = Ability to securely communicate from anything to anything
IPv 6 Security Computer Science • Enough IP addrs for every imaginable device + Real end-to-end security = Ability to securely communicate from anything to anything
 IPv 6 Security – harder to scan networks Computer Science • With IPv 4, it is easy to scan a network – With tools like nmap, can scan a typical subnet in a few minutes see: http: //www. insecure. org/nmap/ – Returning list of active hosts and open ports – Many worms also operate by scanning • e. g. Blaster, Slammer – Attackers (& worms) scan for proxies, weak services and back doors
IPv 6 Security – harder to scan networks Computer Science • With IPv 4, it is easy to scan a network – With tools like nmap, can scan a typical subnet in a few minutes see: http: //www. insecure. org/nmap/ – Returning list of active hosts and open ports – Many worms also operate by scanning • e. g. Blaster, Slammer – Attackers (& worms) scan for proxies, weak services and back doors
 IPv 6 Security – harder to scan networks Computer Science • With IPv 6, sparse address allocation makes such brute force scanning impractical – It is 4 billion times harder to scan 1 IPv 6 subnet than all of IPv 4 • No more Blaster, Slammer, … • Use of “dense” address allocations makes it easier though
IPv 6 Security – harder to scan networks Computer Science • With IPv 6, sparse address allocation makes such brute force scanning impractical – It is 4 billion times harder to scan 1 IPv 6 subnet than all of IPv 4 • No more Blaster, Slammer, … • Use of “dense” address allocations makes it easier though
 Transition From IPv 4 To IPv 6 Computer Science Transition from IPv 4 to IPv 6 will take time: • Due to need to support legacy systems and applications, not all system can be upgraded simultaneously • Instead, organisations deploy IPv 6 piecewise with pilot/experimental implementations first known as “ 6 to 4” • Thus need for IPv 4 -IPv 6 coexistence – Have dual-stack systems (supporting both v 4 and v 6) – Tunnelling used to deliver IPv 6 packets over IPv 4 networks • Tunneling: IPv 6 carried as payload in IPv 4 datagram among IPv 4 routers
Transition From IPv 4 To IPv 6 Computer Science Transition from IPv 4 to IPv 6 will take time: • Due to need to support legacy systems and applications, not all system can be upgraded simultaneously • Instead, organisations deploy IPv 6 piecewise with pilot/experimental implementations first known as “ 6 to 4” • Thus need for IPv 4 -IPv 6 coexistence – Have dual-stack systems (supporting both v 4 and v 6) – Tunnelling used to deliver IPv 6 packets over IPv 4 networks • Tunneling: IPv 6 carried as payload in IPv 4 datagram among IPv 4 routers
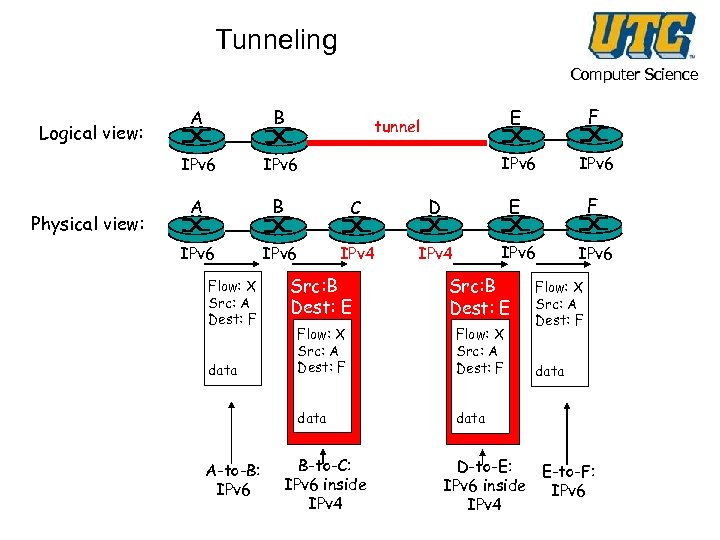 Tunneling Computer Science Physical view: B C IPv 6 IPv 4 F IPv 6 D E F IPv 4 IPv 6 A E IPv 6 B IPv 6 Logical view: A tunnel data A-to-B: IPv 6 Src: B Dest: E Flow: X Src: A Dest: F data B-to-C: IPv 6 inside IPv 4 Flow: X Src: A Dest: F data D-to-E: E-to-F: IPv 6 inside IPv 6 IPv 4
Tunneling Computer Science Physical view: B C IPv 6 IPv 4 F IPv 6 D E F IPv 4 IPv 6 A E IPv 6 B IPv 6 Logical view: A tunnel data A-to-B: IPv 6 Src: B Dest: E Flow: X Src: A Dest: F data B-to-C: IPv 6 inside IPv 4 Flow: X Src: A Dest: F data D-to-E: E-to-F: IPv 6 inside IPv 6 IPv 4
 Outline • Internet Protocol – – Datagram format IPv 4 addressing NAT IPv 6 • IPSec – – Security Association (SA) IPSec Base Protocol (AH, ESP) Encapsulation Mode (transport, tunnel) Key Management Computer Science
Outline • Internet Protocol – – Datagram format IPv 4 addressing NAT IPv 6 • IPSec – – Security Association (SA) IPSec Base Protocol (AH, ESP) Encapsulation Mode (transport, tunnel) Key Management Computer Science
 IP Security (IPsec) Computer Science • Suite of protocols from Internet Engineering Task Force (IETF) providing encryption and authentication at the IP layer – Arose from needs identified in RFC 1636 – Specifications in: • • RFC 2401: Security architecture RFC 2402: Authentication RFC 2406: Encryption RFC 2408: Key management • Objective is to encrypt and/or authenticate all traffic at the IP level.
IP Security (IPsec) Computer Science • Suite of protocols from Internet Engineering Task Force (IETF) providing encryption and authentication at the IP layer – Arose from needs identified in RFC 1636 – Specifications in: • • RFC 2401: Security architecture RFC 2402: Authentication RFC 2406: Encryption RFC 2408: Key management • Objective is to encrypt and/or authenticate all traffic at the IP level.
 IP Security Issues • • Computer Science Eavesdropping Modification of packets in transit Identity spoofing (forged source IP addresses) Denial of service • Many solutions are application-specific – TLS for Web, S/MIME for email, SSH for remote login • IPSec aims to provide a framework of open standards for secure communications over IP – Protect every protocol running on top of IPv 4 and IPv 6
IP Security Issues • • Computer Science Eavesdropping Modification of packets in transit Identity spoofing (forged source IP addresses) Denial of service • Many solutions are application-specific – TLS for Web, S/MIME for email, SSH for remote login • IPSec aims to provide a framework of open standards for secure communications over IP – Protect every protocol running on top of IPv 4 and IPv 6
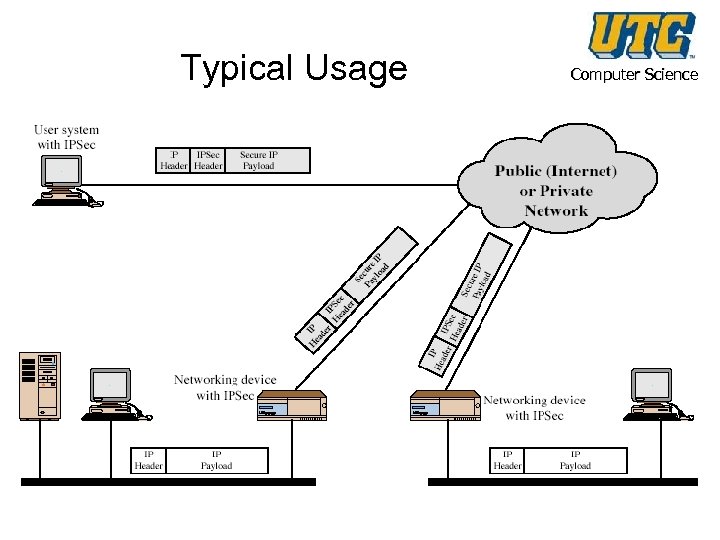 Typical Usage Computer Science
Typical Usage Computer Science
 IPSec Services Computer Science • Data origin authentication • Confidentiality • Connectionless and partial sequence integrity – Connectionless = integrity for a single IP packet – Partial sequence integrity = prevent packet replay • Limited traffic flow confidentiality – Eavesdropper cannot determine who is talking • These services are transparent to applications above transport (TCP/UDP) layer
IPSec Services Computer Science • Data origin authentication • Confidentiality • Connectionless and partial sequence integrity – Connectionless = integrity for a single IP packet – Partial sequence integrity = prevent packet replay • Limited traffic flow confidentiality – Eavesdropper cannot determine who is talking • These services are transparent to applications above transport (TCP/UDP) layer
 Major IPSec Components Computer Science • Security Association (SA) Database • Each SA refers to all the security parameters of one communication direction • For two-way communications, at least two SAs are needed. • Two Protocols • AH – Authentication Header • ESP – Encapsulating Security Payload 1. Encryption only 2. Encryption with authentication • Two Encapsulation modes 1. Transport mode 2. Tunnel mode
Major IPSec Components Computer Science • Security Association (SA) Database • Each SA refers to all the security parameters of one communication direction • For two-way communications, at least two SAs are needed. • Two Protocols • AH – Authentication Header • ESP – Encapsulating Security Payload 1. Encryption only 2. Encryption with authentication • Two Encapsulation modes 1. Transport mode 2. Tunnel mode
 Outline • Internet Protocol – – Datagram format IPv 4 addressing NAT IPv 6 • IPSec – – Security Association (SA) IPSec Base Protocol (AH, ESP) Encapsulation Mode (transport, tunnel) Key Management Computer Science
Outline • Internet Protocol – – Datagram format IPv 4 addressing NAT IPv 6 • IPSec – – Security Association (SA) IPSec Base Protocol (AH, ESP) Encapsulation Mode (transport, tunnel) Key Management Computer Science
 Security Association (SA) Computer Science • In order to communicate, each pair of hosts must set up SA with each other • Acts as virtual connection for which various parameters are set: – – Type of protection Algorithms Keys … • Simplex: a one way relationship between a sender and a receiver. • For either AH or ESP, but not both
Security Association (SA) Computer Science • In order to communicate, each pair of hosts must set up SA with each other • Acts as virtual connection for which various parameters are set: – – Type of protection Algorithms Keys … • Simplex: a one way relationship between a sender and a receiver. • For either AH or ESP, but not both
 Security Association (SA) • Computer Science Each SA uniquely identified by: – Security Parameters Index (SPI) • 32 -bit string assigned to this SA (local meaning only) – IP destination address of packets • May be end user system, or firewall or router – Security Protocol Identifier (e. g. AH, ESP) • For each IP packet, governing SA is identified by: – Destination IP address in packet header – SPI in extension header (AH or ESP)
Security Association (SA) • Computer Science Each SA uniquely identified by: – Security Parameters Index (SPI) • 32 -bit string assigned to this SA (local meaning only) – IP destination address of packets • May be end user system, or firewall or router – Security Protocol Identifier (e. g. AH, ESP) • For each IP packet, governing SA is identified by: – Destination IP address in packet header – SPI in extension header (AH or ESP)
 Security Association (SA) Computer Science • It contains all the security parameters needed for one way communication – – Sequence number counter Anti-replay window Protocol (e. g. AH / ESP) Transform mode (e. g. transport / tunnel mode / wildcard) – Protocol parameters (e. g. AES, 128 -bit, CBC mode, SHA-1) – Lifetime of the SA – etc.
Security Association (SA) Computer Science • It contains all the security parameters needed for one way communication – – Sequence number counter Anti-replay window Protocol (e. g. AH / ESP) Transform mode (e. g. transport / tunnel mode / wildcard) – Protocol parameters (e. g. AES, 128 -bit, CBC mode, SHA-1) – Lifetime of the SA – etc.
 Outline • Internet Protocol – – Datagram format IPv 4 addressing NAT IPv 6 • IPSec – – Security Association (SA) IPSec Base Protocol (AH, ESP) Encapsulation Mode (transport, tunnel) Key Management Computer Science
Outline • Internet Protocol – – Datagram format IPv 4 addressing NAT IPv 6 • IPSec – – Security Association (SA) IPSec Base Protocol (AH, ESP) Encapsulation Mode (transport, tunnel) Key Management Computer Science
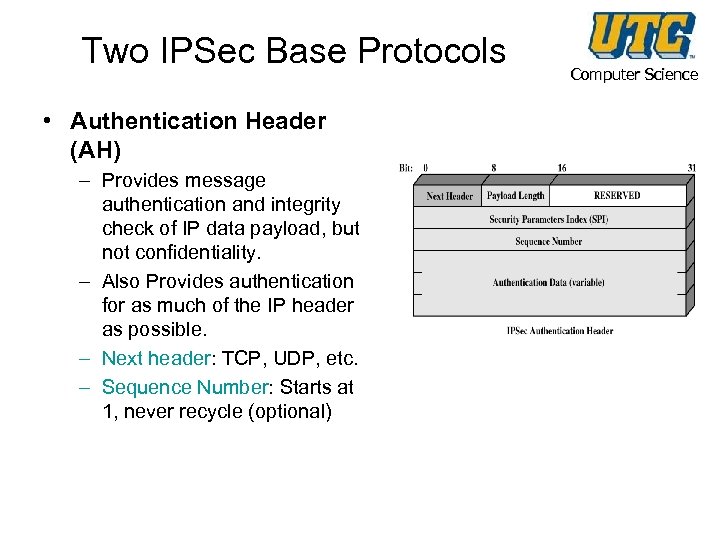 Two IPSec Base Protocols • Authentication Header (AH) – Provides message authentication and integrity check of IP data payload, but not confidentiality. – Also Provides authentication for as much of the IP header as possible. – Next header: TCP, UDP, etc. – Sequence Number: Starts at 1, never recycle (optional) Computer Science
Two IPSec Base Protocols • Authentication Header (AH) – Provides message authentication and integrity check of IP data payload, but not confidentiality. – Also Provides authentication for as much of the IP header as possible. – Next header: TCP, UDP, etc. – Sequence Number: Starts at 1, never recycle (optional) Computer Science
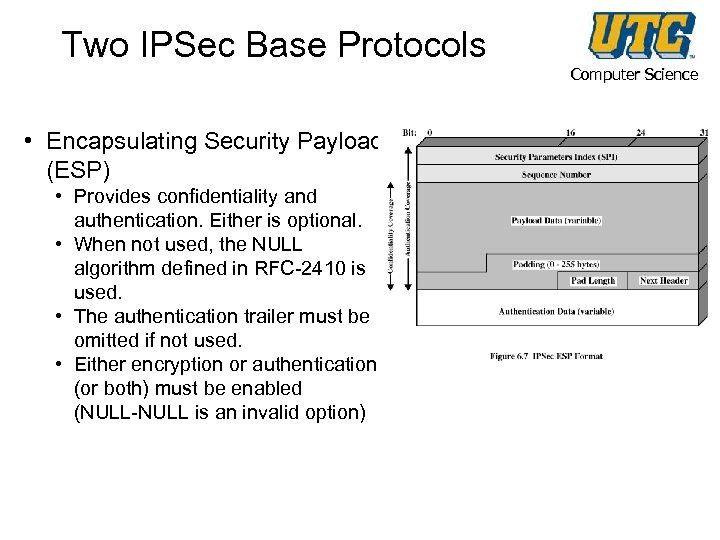 Two IPSec Base Protocols • Encapsulating Security Payload (ESP) • Provides confidentiality and authentication. Either is optional. • When not used, the NULL algorithm defined in RFC-2410 is used. • The authentication trailer must be omitted if not used. • Either encryption or authentication (or both) must be enabled (NULL-NULL is an invalid option) Computer Science
Two IPSec Base Protocols • Encapsulating Security Payload (ESP) • Provides confidentiality and authentication. Either is optional. • When not used, the NULL algorithm defined in RFC-2410 is used. • The authentication trailer must be omitted if not used. • Either encryption or authentication (or both) must be enabled (NULL-NULL is an invalid option) Computer Science
 Outline • Internet Protocol – – Datagram format IPv 4 addressing NAT IPv 6 • IPSec – – Security Association (SA) IPSec Base Protocol (AH, ESP) Encapsulation Mode (transport, tunnel) Key Management Computer Science
Outline • Internet Protocol – – Datagram format IPv 4 addressing NAT IPv 6 • IPSec – – Security Association (SA) IPSec Base Protocol (AH, ESP) Encapsulation Mode (transport, tunnel) Key Management Computer Science
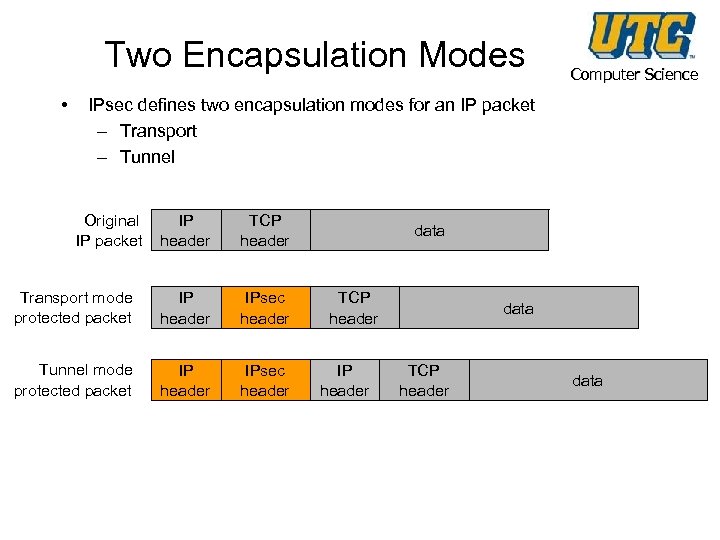 Two Encapsulation Modes • Computer Science IPsec defines two encapsulation modes for an IP packet – Transport – Tunnel Original IP packet IP header TCP header Transport mode protected packet IP header IPsec header Tunnel mode protected packet IP header IPsec header data TCP header IP header data TCP header data
Two Encapsulation Modes • Computer Science IPsec defines two encapsulation modes for an IP packet – Transport – Tunnel Original IP packet IP header TCP header Transport mode protected packet IP header IPsec header Tunnel mode protected packet IP header IPsec header data TCP header IP header data TCP header data
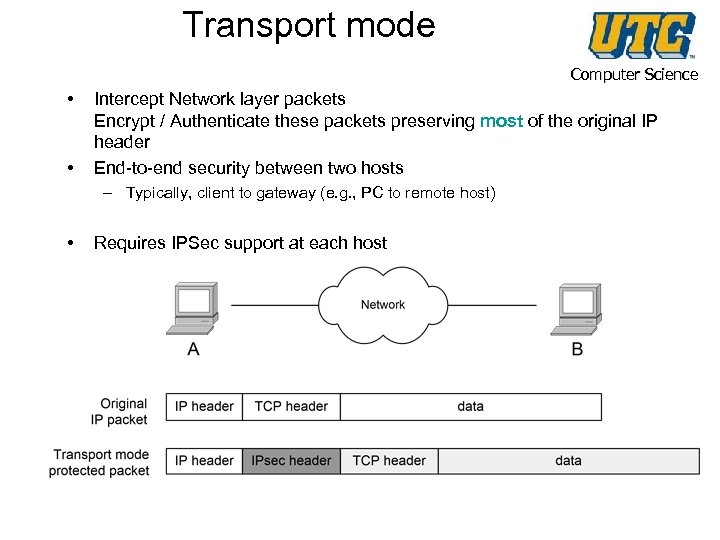 Transport mode Computer Science • • Intercept Network layer packets Encrypt / Authenticate these packets preserving most of the original IP header End-to-end security between two hosts – Typically, client to gateway (e. g. , PC to remote host) • Requires IPSec support at each host
Transport mode Computer Science • • Intercept Network layer packets Encrypt / Authenticate these packets preserving most of the original IP header End-to-end security between two hosts – Typically, client to gateway (e. g. , PC to remote host) • Requires IPSec support at each host
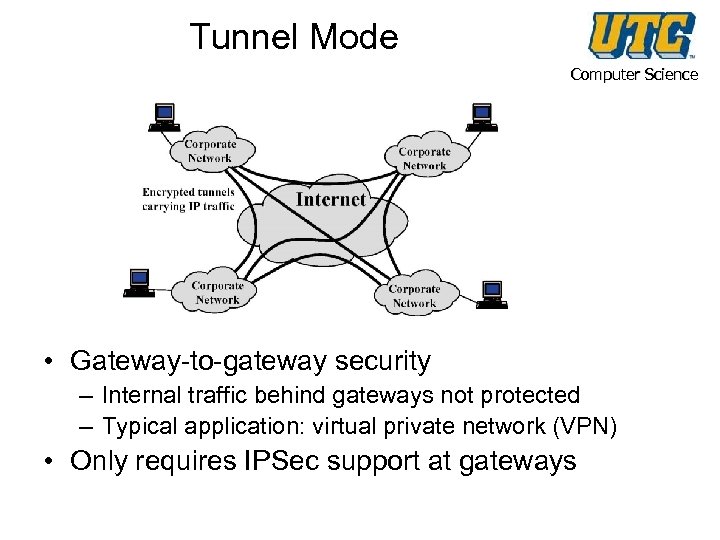 Tunnel Mode Computer Science • Gateway-to-gateway security – Internal traffic behind gateways not protected – Typical application: virtual private network (VPN) • Only requires IPSec support at gateways
Tunnel Mode Computer Science • Gateway-to-gateway security – Internal traffic behind gateways not protected – Typical application: virtual private network (VPN) • Only requires IPSec support at gateways
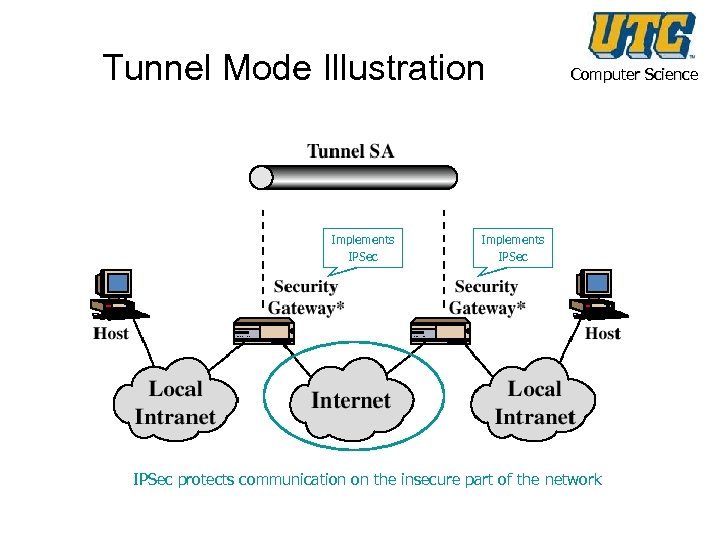 Tunnel Mode Illustration Implements IPSec Computer Science Implements IPSec protects communication on the insecure part of the network
Tunnel Mode Illustration Implements IPSec Computer Science Implements IPSec protects communication on the insecure part of the network
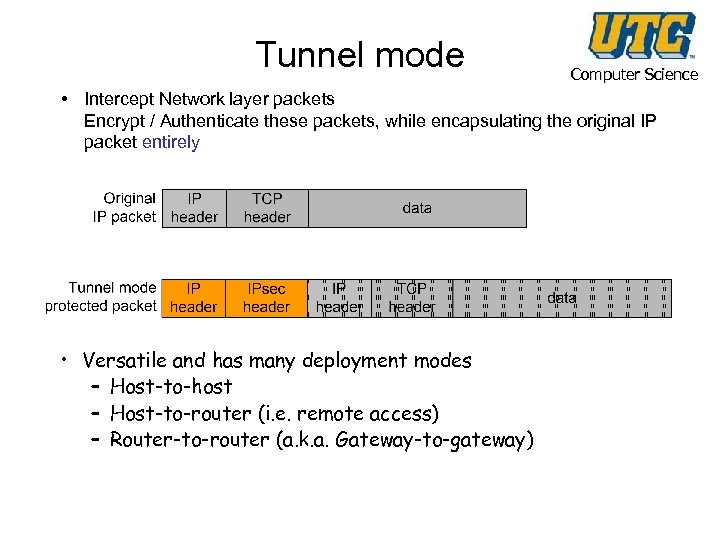 Tunnel mode Computer Science • Intercept Network layer packets Encrypt / Authenticate these packets, while encapsulating the original IP packet entirely • Versatile and has many deployment modes – Host-to-host – Host-to-router (i. e. remote access) – Router-to-router (a. k. a. Gateway-to-gateway)
Tunnel mode Computer Science • Intercept Network layer packets Encrypt / Authenticate these packets, while encapsulating the original IP packet entirely • Versatile and has many deployment modes – Host-to-host – Host-to-router (i. e. remote access) – Router-to-router (a. k. a. Gateway-to-gateway)
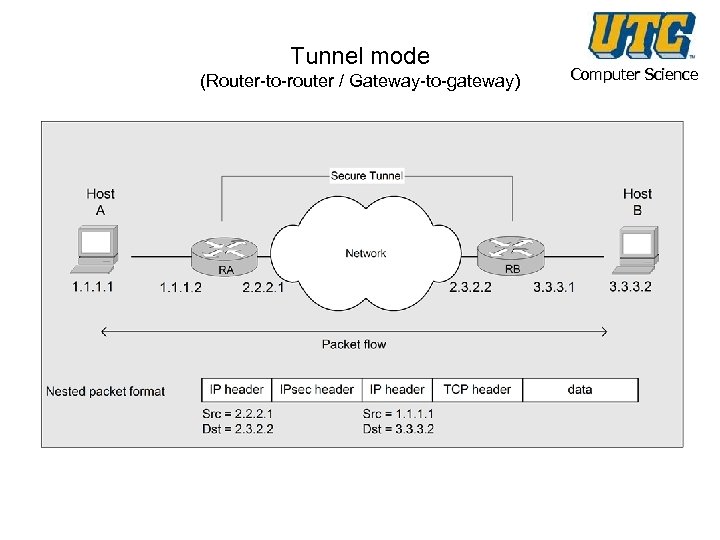 Tunnel mode (Router-to-router / Gateway-to-gateway) Computer Science
Tunnel mode (Router-to-router / Gateway-to-gateway) Computer Science
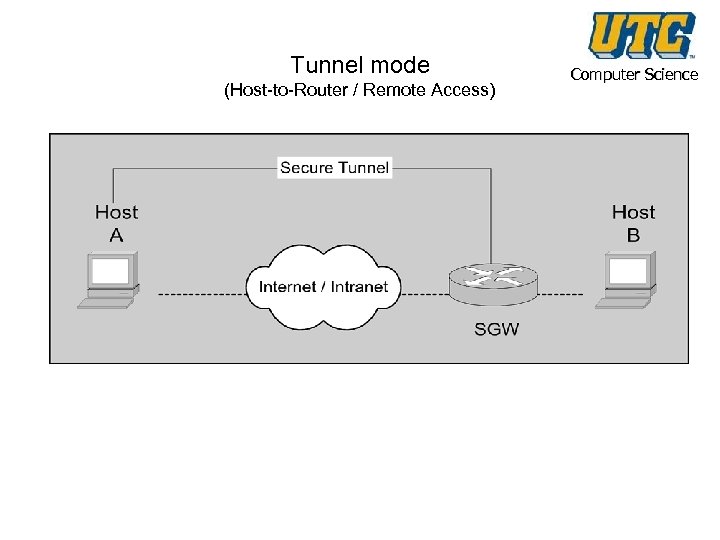 Tunnel mode (Host-to-Router / Remote Access) Computer Science
Tunnel mode (Host-to-Router / Remote Access) Computer Science
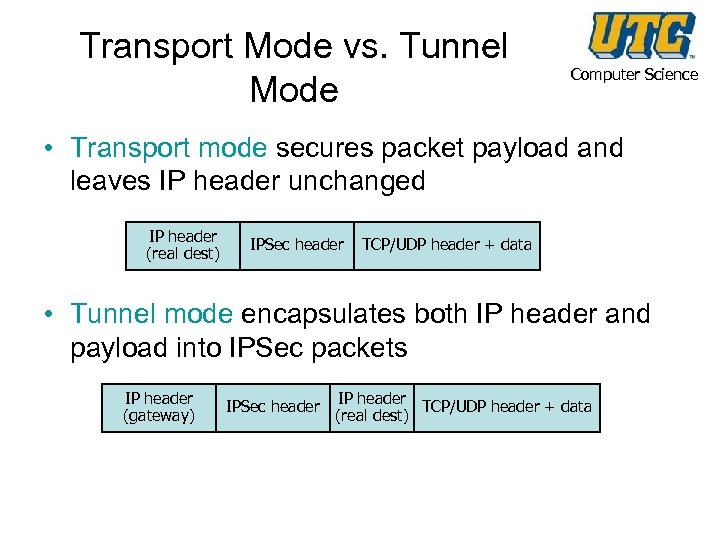 Transport Mode vs. Tunnel Mode Computer Science • Transport mode secures packet payload and leaves IP header unchanged IP header (real dest) IPSec header TCP/UDP header + data • Tunnel mode encapsulates both IP header and payload into IPSec packets IP header (gateway) IPSec header IP header TCP/UDP header + data (real dest)
Transport Mode vs. Tunnel Mode Computer Science • Transport mode secures packet payload and leaves IP header unchanged IP header (real dest) IPSec header TCP/UDP header + data • Tunnel mode encapsulates both IP header and payload into IPSec packets IP header (gateway) IPSec header IP header TCP/UDP header + data (real dest)
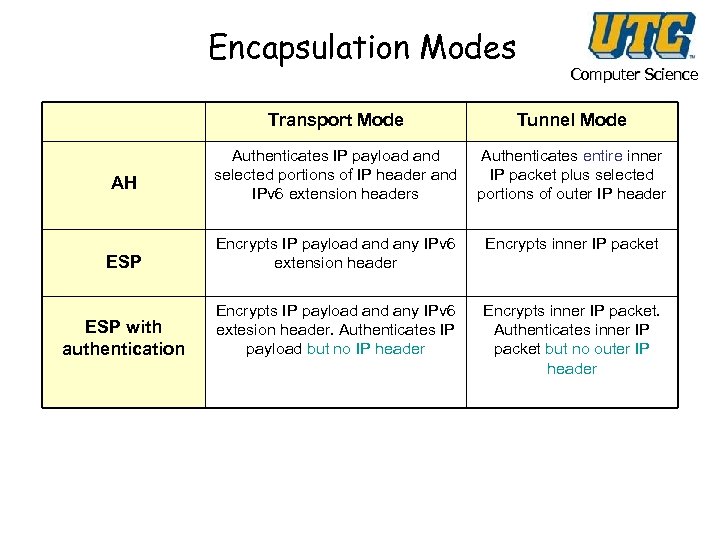 Encapsulation Modes Computer Science Transport Mode Tunnel Mode Authenticates IP payload and selected portions of IP header and IPv 6 extension headers Authenticates entire inner IP packet plus selected portions of outer IP header ESP Encrypts IP payload any IPv 6 extension header Encrypts inner IP packet ESP with authentication Encrypts IP payload any IPv 6 extesion header. Authenticates IP payload but no IP header Encrypts inner IP packet. Authenticates inner IP packet but no outer IP header AH
Encapsulation Modes Computer Science Transport Mode Tunnel Mode Authenticates IP payload and selected portions of IP header and IPv 6 extension headers Authenticates entire inner IP packet plus selected portions of outer IP header ESP Encrypts IP payload any IPv 6 extension header Encrypts inner IP packet ESP with authentication Encrypts IP payload any IPv 6 extesion header. Authenticates IP payload but no IP header Encrypts inner IP packet. Authenticates inner IP packet but no outer IP header AH
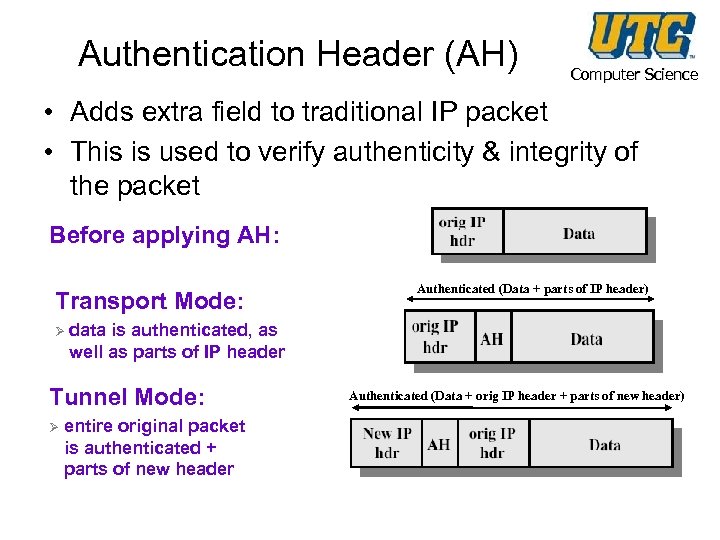 Authentication Header (AH) Computer Science • Adds extra field to traditional IP packet • This is used to verify authenticity & integrity of the packet Before applying AH: Transport Mode: Authenticated (Data + parts of IP header) Ø data is authenticated, as well as parts of IP header Tunnel Mode: Ø entire original packet is authenticated + parts of new header Authenticated (Data + orig IP header + parts of new header)
Authentication Header (AH) Computer Science • Adds extra field to traditional IP packet • This is used to verify authenticity & integrity of the packet Before applying AH: Transport Mode: Authenticated (Data + parts of IP header) Ø data is authenticated, as well as parts of IP header Tunnel Mode: Ø entire original packet is authenticated + parts of new header Authenticated (Data + orig IP header + parts of new header)
 Authentication Header (AH) Computer Science • Protection against replay attack with use of sequence number • Why have an Authentication-only protocol (AH)? – May be used where export/import/use of encryption is restricted – Faster implementation – Receiver can choose whether expend the effort to verify authenticity/integrity
Authentication Header (AH) Computer Science • Protection against replay attack with use of sequence number • Why have an Authentication-only protocol (AH)? – May be used where export/import/use of encryption is restricted – Faster implementation – Receiver can choose whether expend the effort to verify authenticity/integrity
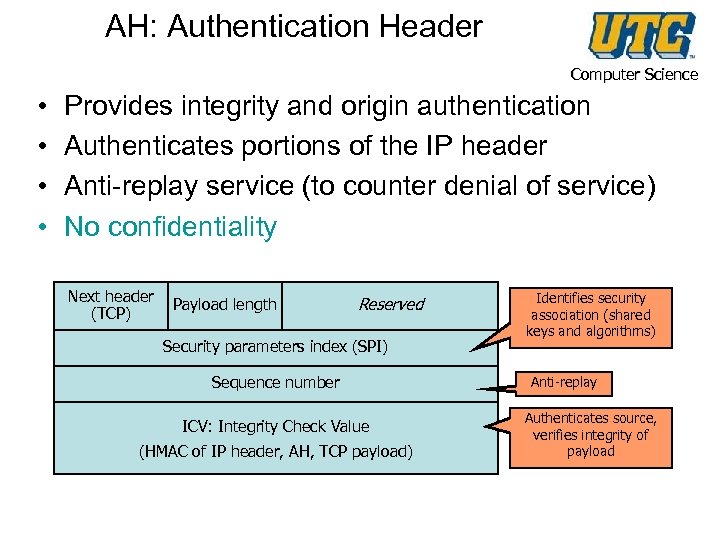 AH: Authentication Header Computer Science • • Provides integrity and origin authentication Authenticates portions of the IP header Anti-replay service (to counter denial of service) No confidentiality Next header (TCP) Payload length Reserved Security parameters index (SPI) Sequence number ICV: Integrity Check Value (HMAC of IP header, AH, TCP payload) Identifies security association (shared keys and algorithms) Anti-replay Authenticates source, verifies integrity of payload
AH: Authentication Header Computer Science • • Provides integrity and origin authentication Authenticates portions of the IP header Anti-replay service (to counter denial of service) No confidentiality Next header (TCP) Payload length Reserved Security parameters index (SPI) Sequence number ICV: Integrity Check Value (HMAC of IP header, AH, TCP payload) Identifies security association (shared keys and algorithms) Anti-replay Authenticates source, verifies integrity of payload
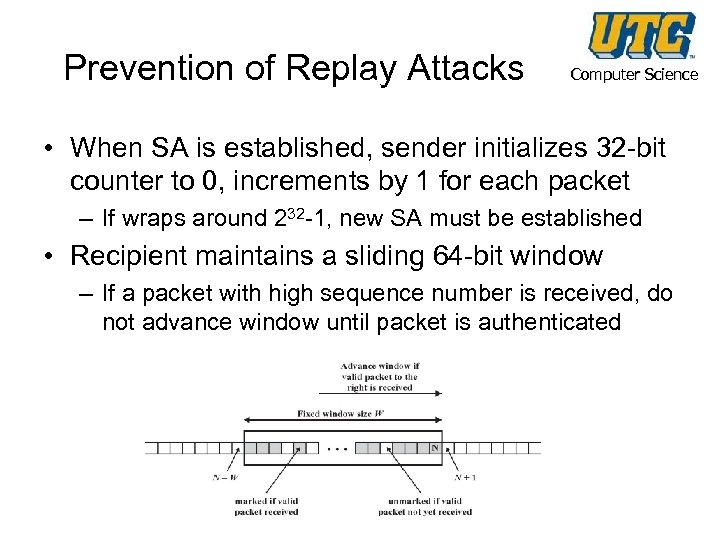 Prevention of Replay Attacks Computer Science • When SA is established, sender initializes 32 -bit counter to 0, increments by 1 for each packet – If wraps around 232 -1, new SA must be established • Recipient maintains a sliding 64 -bit window – If a packet with high sequence number is received, do not advance window until packet is authenticated
Prevention of Replay Attacks Computer Science • When SA is established, sender initializes 32 -bit counter to 0, increments by 1 for each packet – If wraps around 232 -1, new SA must be established • Recipient maintains a sliding 64 -bit window – If a packet with high sequence number is received, do not advance window until packet is authenticated
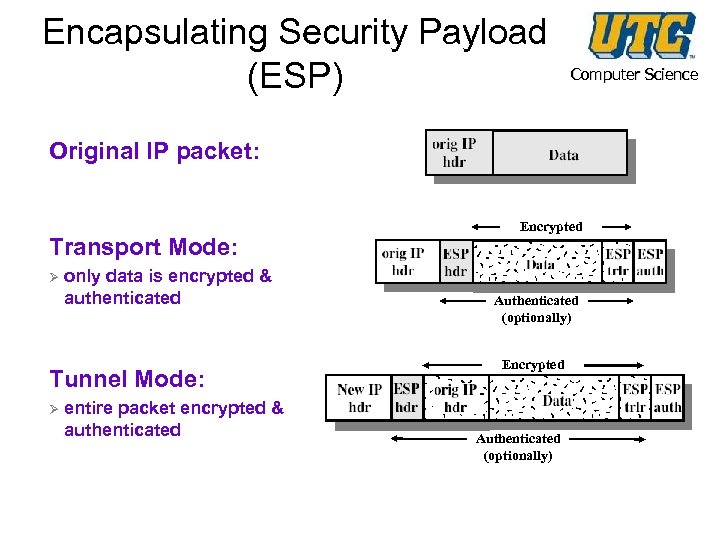 Encapsulating Security Payload (ESP) Computer Science Original IP packet: Transport Mode: Ø only data is encrypted & authenticated Tunnel Mode: Ø entire packet encrypted & authenticated Encrypted Authenticated (optionally)
Encapsulating Security Payload (ESP) Computer Science Original IP packet: Transport Mode: Ø only data is encrypted & authenticated Tunnel Mode: Ø entire packet encrypted & authenticated Encrypted Authenticated (optionally)
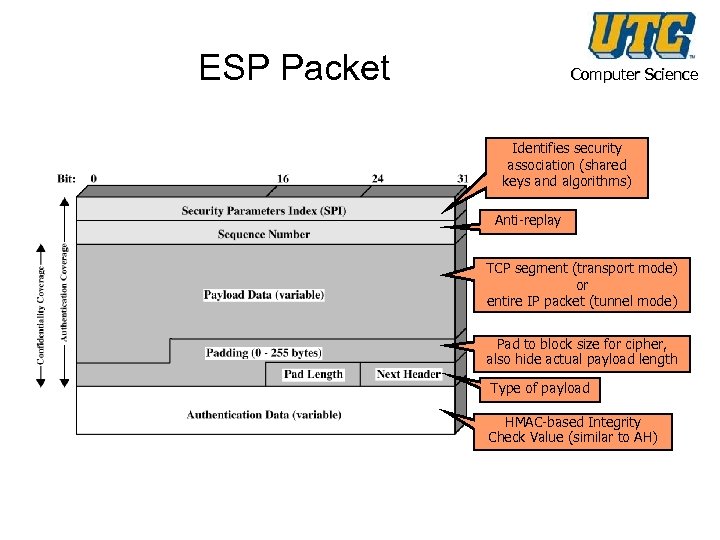 ESP Packet Computer Science Identifies security association (shared keys and algorithms) Anti-replay TCP segment (transport mode) or entire IP packet (tunnel mode) Pad to block size for cipher, also hide actual payload length Type of payload HMAC-based Integrity Check Value (similar to AH)
ESP Packet Computer Science Identifies security association (shared keys and algorithms) Anti-replay TCP segment (transport mode) or entire IP packet (tunnel mode) Pad to block size for cipher, also hide actual payload length Type of payload HMAC-based Integrity Check Value (similar to AH)
 Encapsulating Security Payload (ESP) Computer Science • Content of IP packet is encrypted and encapsulated between header and trailer fields. • Authentication data optionally added
Encapsulating Security Payload (ESP) Computer Science • Content of IP packet is encrypted and encapsulated between header and trailer fields. • Authentication data optionally added
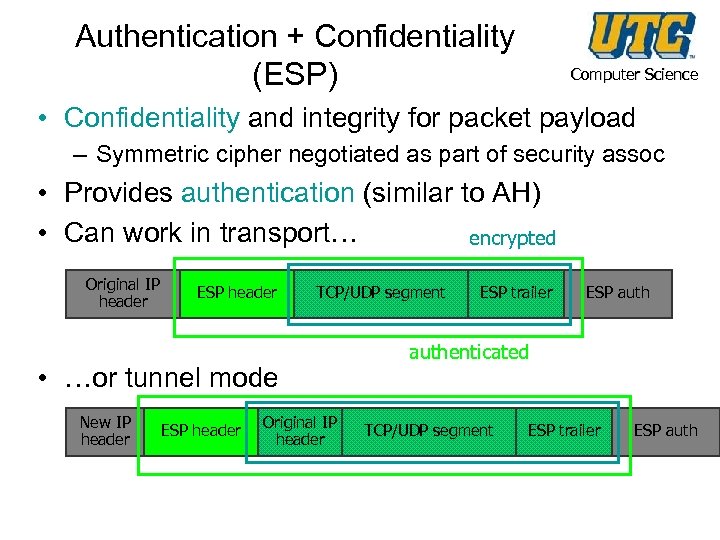 Authentication + Confidentiality (ESP) Computer Science • Confidentiality and integrity for packet payload – Symmetric cipher negotiated as part of security assoc • Provides authentication (similar to AH) • Can work in transport… encrypted Original IP header ESP header TCP/UDP segment • …or tunnel mode New IP header ESP header Original IP header ESP trailer ESP authenticated TCP/UDP segment ESP trailer ESP auth
Authentication + Confidentiality (ESP) Computer Science • Confidentiality and integrity for packet payload – Symmetric cipher negotiated as part of security assoc • Provides authentication (similar to AH) • Can work in transport… encrypted Original IP header ESP header TCP/UDP segment • …or tunnel mode New IP header ESP header Original IP header ESP trailer ESP authenticated TCP/UDP segment ESP trailer ESP auth
 Combining Security Associations • SAs can implement either AH or ESP • to implement both need to combine SAs – form a security bundle • have 4 cases (see next) Computer Science
Combining Security Associations • SAs can implement either AH or ESP • to implement both need to combine SAs – form a security bundle • have 4 cases (see next) Computer Science
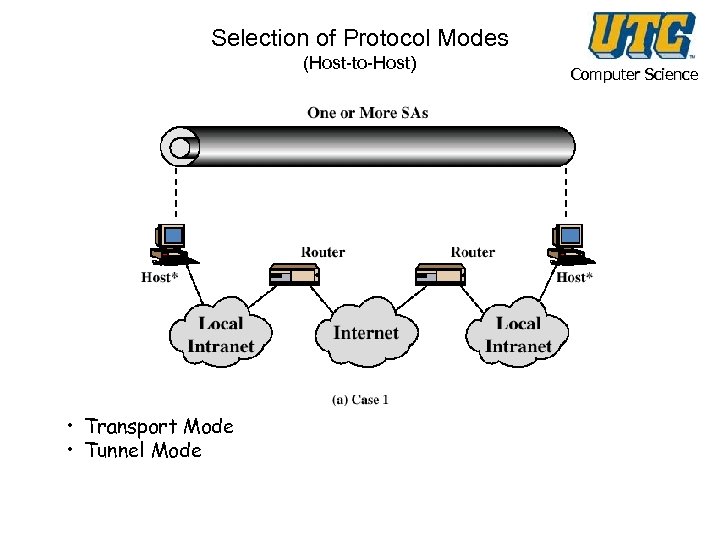 Selection of Protocol Modes (Host-to-Host) • Transport Mode • Tunnel Mode Computer Science
Selection of Protocol Modes (Host-to-Host) • Transport Mode • Tunnel Mode Computer Science
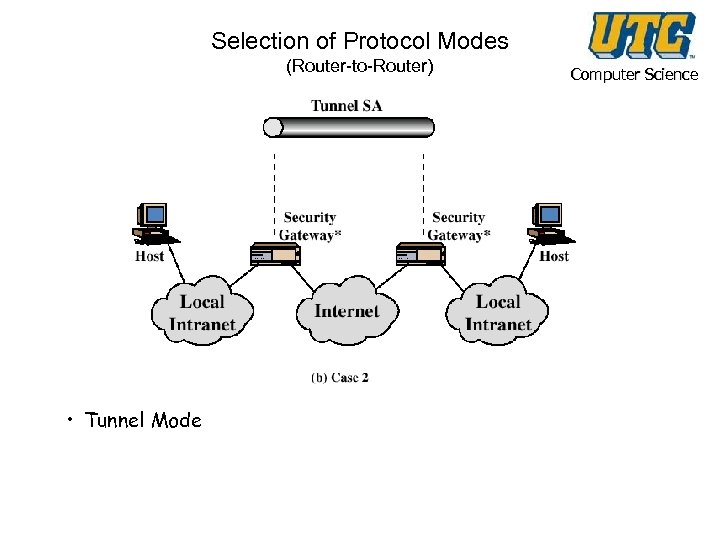 Selection of Protocol Modes (Router-to-Router) • Tunnel Mode Computer Science
Selection of Protocol Modes (Router-to-Router) • Tunnel Mode Computer Science
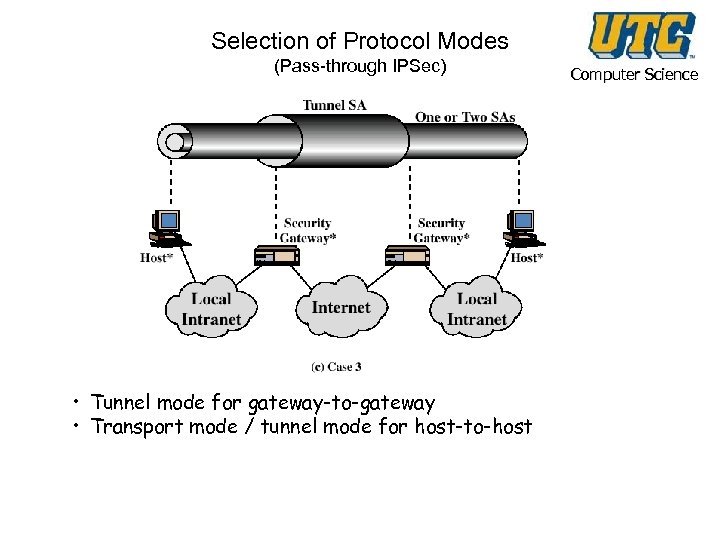 Selection of Protocol Modes (Pass-through IPSec) • Tunnel mode for gateway-to-gateway • Transport mode / tunnel mode for host-to-host Computer Science
Selection of Protocol Modes (Pass-through IPSec) • Tunnel mode for gateway-to-gateway • Transport mode / tunnel mode for host-to-host Computer Science
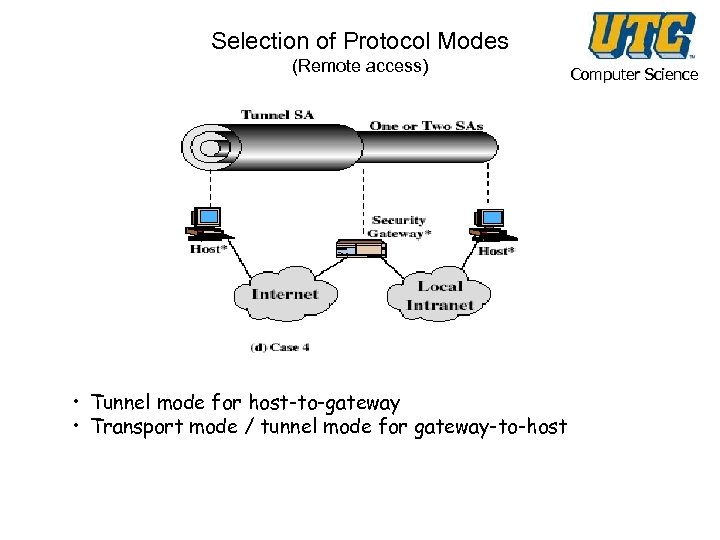 Selection of Protocol Modes (Remote access) • Tunnel mode for host-to-gateway • Transport mode / tunnel mode for gateway-to-host Computer Science
Selection of Protocol Modes (Remote access) • Tunnel mode for host-to-gateway • Transport mode / tunnel mode for gateway-to-host Computer Science
 Outline • Internet Protocol – – Datagram format IPv 4 addressing NAT IPv 6 • IPSec – – Security Association (SA) IPSec Base Protocol (AH, ESP) Encapsulation Mode (transport, tunnel) Key Management Computer Science
Outline • Internet Protocol – – Datagram format IPv 4 addressing NAT IPv 6 • IPSec – – Security Association (SA) IPSec Base Protocol (AH, ESP) Encapsulation Mode (transport, tunnel) Key Management Computer Science
 Key Management in IPsec Computer Science • Generation and distribution of secret keys • Manual – Sysadmin configures keys (doesn’t scale well) • automated key management – automated system for on demand creation of keys for SA’s in large systems – has Oakley & ISAKMP elements
Key Management in IPsec Computer Science • Generation and distribution of secret keys • Manual – Sysadmin configures keys (doesn’t scale well) • automated key management – automated system for on demand creation of keys for SA’s in large systems – has Oakley & ISAKMP elements
 Oakley Computer Science • a key exchange protocol • based on Diffie-Hellman key exchange • adds features to address weaknesses – cookies, groups (global params), nonces, DH key exchange with authentication
Oakley Computer Science • a key exchange protocol • based on Diffie-Hellman key exchange • adds features to address weaknesses – cookies, groups (global params), nonces, DH key exchange with authentication
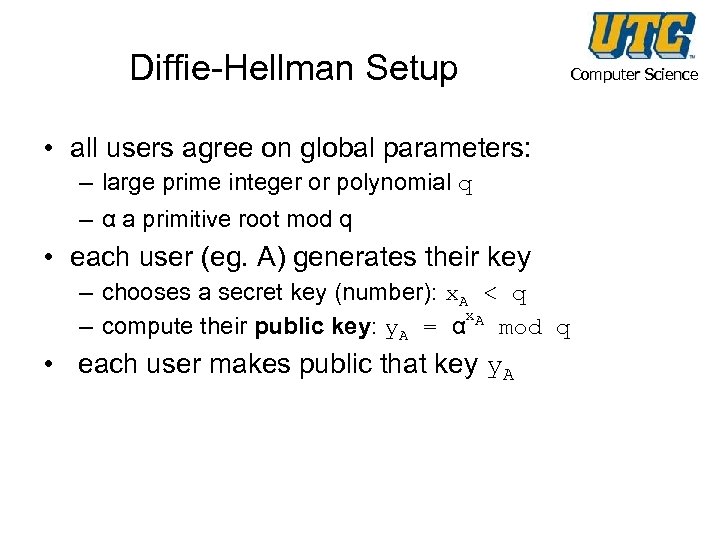 Diffie-Hellman Setup • all users agree on global parameters: – large prime integer or polynomial q – α a primitive root mod q • each user (eg. A) generates their key – chooses a secret key (number): x. A < q x. A – compute their public key: y. A = α mod q • each user makes public that key y. A Computer Science
Diffie-Hellman Setup • all users agree on global parameters: – large prime integer or polynomial q – α a primitive root mod q • each user (eg. A) generates their key – chooses a secret key (number): x. A < q x. A – compute their public key: y. A = α mod q • each user makes public that key y. A Computer Science
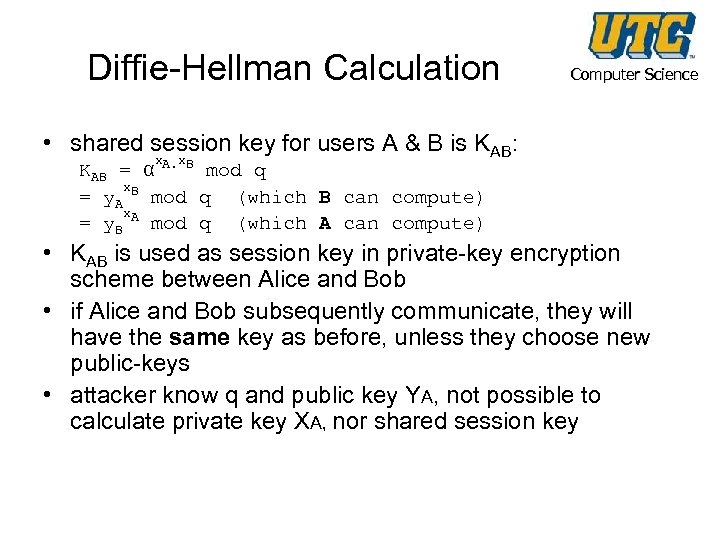 Diffie-Hellman Calculation Computer Science • shared session key for users A & B is KAB: x x KAB = α A. B mod q x = y. A B mod q (which B can compute) x = y. B A mod q (which A can compute) • KAB is used as session key in private-key encryption scheme between Alice and Bob • if Alice and Bob subsequently communicate, they will have the same key as before, unless they choose new public-keys • attacker know q and public key YA, not possible to calculate private key XA, nor shared session key
Diffie-Hellman Calculation Computer Science • shared session key for users A & B is KAB: x x KAB = α A. B mod q x = y. A B mod q (which B can compute) x = y. B A mod q (which A can compute) • KAB is used as session key in private-key encryption scheme between Alice and Bob • if Alice and Bob subsequently communicate, they will have the same key as before, unless they choose new public-keys • attacker know q and public key YA, not possible to calculate private key XA, nor shared session key
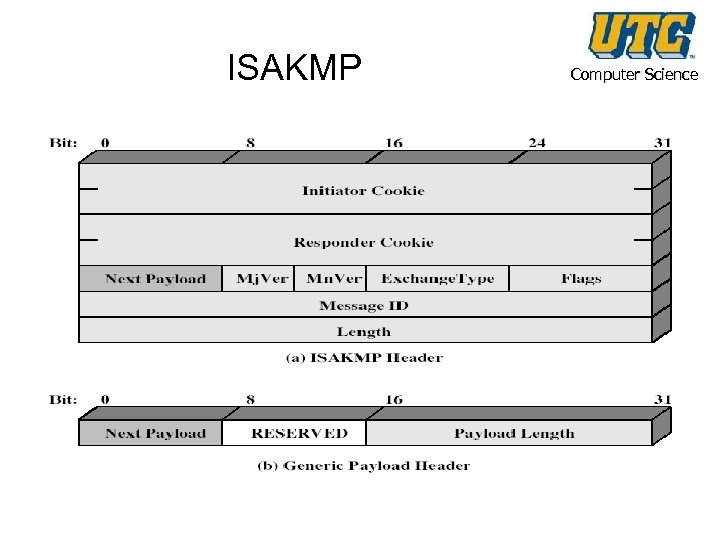
 ISAKMP Computer Science • Internet Security Association and Key Management Protocol (ISAKMP) • provides framework for key management • defines procedures and packet formats to establish, negotiate, modify, & delete SAs • independent of key exchange protocol, encryption alg, & authentication method
ISAKMP Computer Science • Internet Security Association and Key Management Protocol (ISAKMP) • provides framework for key management • defines procedures and packet formats to establish, negotiate, modify, & delete SAs • independent of key exchange protocol, encryption alg, & authentication method
 ISAKMP Computer Science
ISAKMP Computer Science
 IPsec Benefits Computer Science • Provides a level of security for all applications. – Allows deployment of new/emerging applications that may not have their own security. • Transparent to transport layer • Transparent to end-users – No need for training, key issue, key revocation, etc. • Can be provided to individual users where needed (e. g. off-site workers) • Extensible to new, stronger, cryptographic methods as these become available
IPsec Benefits Computer Science • Provides a level of security for all applications. – Allows deployment of new/emerging applications that may not have their own security. • Transparent to transport layer • Transparent to end-users – No need for training, key issue, key revocation, etc. • Can be provided to individual users where needed (e. g. off-site workers) • Extensible to new, stronger, cryptographic methods as these become available
 IPsec Drawbacks Computer Science • Processing performance overhead – Protection is applied to all traffic, though only a small portion may be security-sensitive • Blocks access to non-IPsec hosts • Hosts must have security association – Not great for short-lived connections • Not practical for broadcast
IPsec Drawbacks Computer Science • Processing performance overhead – Protection is applied to all traffic, though only a small portion may be security-sensitive • Blocks access to non-IPsec hosts • Hosts must have security association – Not great for short-lived connections • Not practical for broadcast
 Uses of IPsec Computer Science • Virtual Private Network (VPN) establishment – For connecting remote offices and users using public Internet • Low-cost remote access – e. g. teleworker gains secure access to company network via local call to ISP • Extranet connectivity – Secure communication with partners, suppliers, etc.
Uses of IPsec Computer Science • Virtual Private Network (VPN) establishment – For connecting remote offices and users using public Internet • Low-cost remote access – e. g. teleworker gains secure access to company network via local call to ISP • Extranet connectivity – Secure communication with partners, suppliers, etc.
 Note on VPN concept Computer Science • Private Network – A set of computers connected together and protected from the Internet (usually with a firewall) – Traditionally made up of LAN(s) within individual locations. If needed, wide area (e. g. inter-branch) connection is made by secure leased telecommunications lines.
Note on VPN concept Computer Science • Private Network – A set of computers connected together and protected from the Internet (usually with a firewall) – Traditionally made up of LAN(s) within individual locations. If needed, wide area (e. g. inter-branch) connection is made by secure leased telecommunications lines.
 Note on VPN concept Computer Science • Virtual Private Network (VPN) – Uses public (insecure) Internet for parts of network connectivity – Made possible by use of cryptography – Can be enabled by IPsec or SSH tunnelling, among other methods
Note on VPN concept Computer Science • Virtual Private Network (VPN) – Uses public (insecure) Internet for parts of network connectivity – Made possible by use of cryptography – Can be enabled by IPsec or SSH tunnelling, among other methods
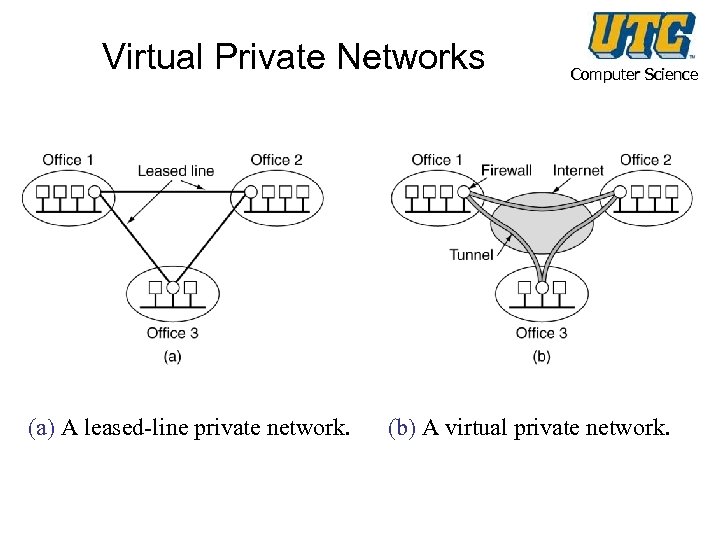 Virtual Private Networks (a) A leased-line private network. Computer Science (b) A virtual private network.
Virtual Private Networks (a) A leased-line private network. Computer Science (b) A virtual private network.
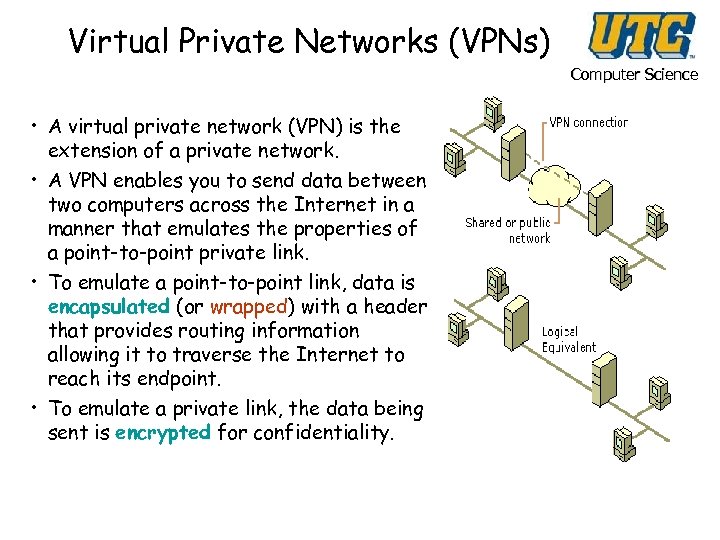 Virtual Private Networks (VPNs) Computer Science • A virtual private network (VPN) is the extension of a private network. • A VPN enables you to send data between two computers across the Internet in a manner that emulates the properties of a point-to-point private link. • To emulate a point-to-point link, data is encapsulated (or wrapped) with a header that provides routing information allowing it to traverse the Internet to reach its endpoint. • To emulate a private link, the data being sent is encrypted for confidentiality.
Virtual Private Networks (VPNs) Computer Science • A virtual private network (VPN) is the extension of a private network. • A VPN enables you to send data between two computers across the Internet in a manner that emulates the properties of a point-to-point private link. • To emulate a point-to-point link, data is encapsulated (or wrapped) with a header that provides routing information allowing it to traverse the Internet to reach its endpoint. • To emulate a private link, the data being sent is encrypted for confidentiality.
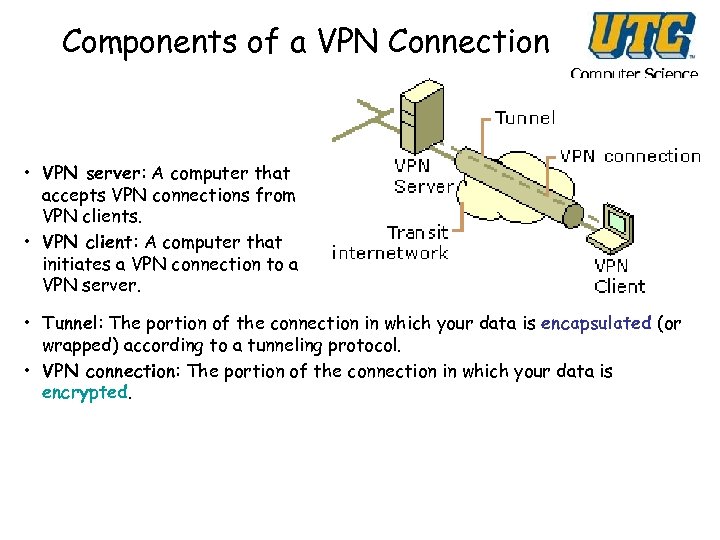 Components of a VPN Connection Computer Science • VPN server: A computer that accepts VPN connections from VPN clients. • VPN client: A computer that initiates a VPN connection to a VPN server. • Tunnel: The portion of the connection in which your data is encapsulated (or wrapped) according to a tunneling protocol. • VPN connection: The portion of the connection in which your data is encrypted.
Components of a VPN Connection Computer Science • VPN server: A computer that accepts VPN connections from VPN clients. • VPN client: A computer that initiates a VPN connection to a VPN server. • Tunnel: The portion of the connection in which your data is encapsulated (or wrapped) according to a tunneling protocol. • VPN connection: The portion of the connection in which your data is encrypted.
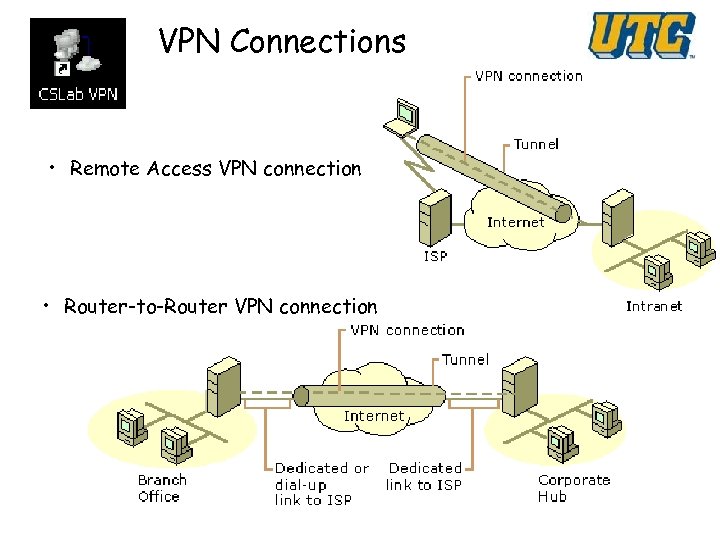 VPN Connections Computer Science • Remote Access VPN connection • Router-to-Router VPN connection
VPN Connections Computer Science • Remote Access VPN connection • Router-to-Router VPN connection
 Standards Computer Science • • • RFC 2401 IPSec RFC 2402 AH RFC 2403 HMAC MD 5 RFC 2404 HMAC SHA-1 RFC 2405 DES CBC with IV RFC 2406 IP ESP RFC 2407 DOI for ISAKMP RFC 2408 ISAKMP RFC 2409 IKE
Standards Computer Science • • • RFC 2401 IPSec RFC 2402 AH RFC 2403 HMAC MD 5 RFC 2404 HMAC SHA-1 RFC 2405 DES CBC with IV RFC 2406 IP ESP RFC 2407 DOI for ISAKMP RFC 2408 ISAKMP RFC 2409 IKE
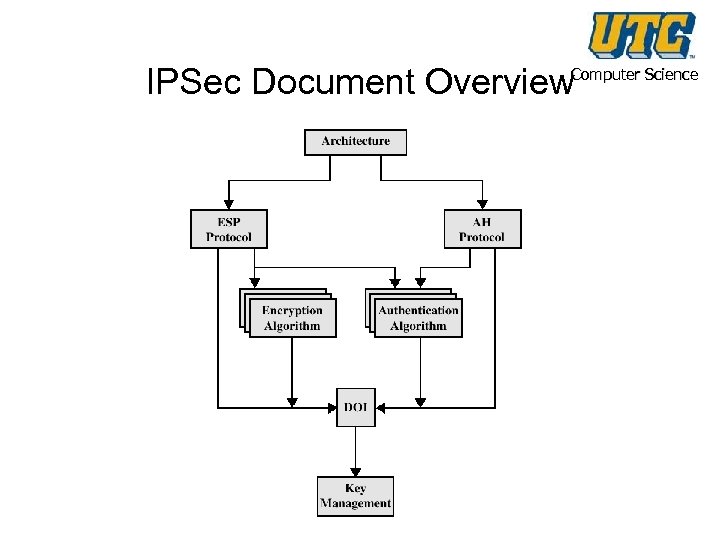 IPSec Document Overview Computer Science
IPSec Document Overview Computer Science
 Outline • Internet Protocol – – Datagram format IPv 4 addressing NAT IPv 6 • IPSec – – Security Association (SA) IPSec Base Protocol (AH, ESP) Encapsulation Mode (transport, tunnel) Key Management Computer Science
Outline • Internet Protocol – – Datagram format IPv 4 addressing NAT IPv 6 • IPSec – – Security Association (SA) IPSec Base Protocol (AH, ESP) Encapsulation Mode (transport, tunnel) Key Management Computer Science


