b69091000eda06483667d5bc6932696e.ppt
- Количество слайдов: 14
 Computer Science CSC 405 Introduction to Computer Security Lab session CSC 405 Lab By Yuzheng Zhou 1
Computer Science CSC 405 Introduction to Computer Security Lab session CSC 405 Lab By Yuzheng Zhou 1
 Roadmap • Lab 2 Set-UID – – 1. 2. Why do we need set-uid program? (prob. 1) Set-uid program How is set-uid implemented in Minix (prob. 2) When we run set-uid in Minix and Linux, why do we get different results ? (prob. 3 & 5) 3. Set-uid vulnerability: PATH environment variable (prob. 4) 4. Use setuid() carefully (Prob. 6) 1. Lab 3 Set-Random. UID grading policy Computer Science CSC 405 Lab By Yuzheng Zhou 2
Roadmap • Lab 2 Set-UID – – 1. 2. Why do we need set-uid program? (prob. 1) Set-uid program How is set-uid implemented in Minix (prob. 2) When we run set-uid in Minix and Linux, why do we get different results ? (prob. 3 & 5) 3. Set-uid vulnerability: PATH environment variable (prob. 4) 4. Use setuid() carefully (Prob. 6) 1. Lab 3 Set-Random. UID grading policy Computer Science CSC 405 Lab By Yuzheng Zhou 2
 passwd, chsh, su • passwd – Allow users to change their passwords – Users’ passwords are stored in /etc/shadow, which is neither readable nor writable to normal • su – Allows user to become the super-user – User must pass super-user’s password as an argument. • chsh – Allow users to change their login shells – Users’ login shell are stored in /etc/passwd, which is neither readable nor writable to normal Computer Science CSC 405 Lab By Yuzheng Zhou 3
passwd, chsh, su • passwd – Allow users to change their passwords – Users’ passwords are stored in /etc/shadow, which is neither readable nor writable to normal • su – Allows user to become the super-user – User must pass super-user’s password as an argument. • chsh – Allow users to change their login shells – Users’ login shell are stored in /etc/passwd, which is neither readable nor writable to normal Computer Science CSC 405 Lab By Yuzheng Zhou 3
 passwd, chsh, su (Cont’d) • passwd, chsh, su – Runnable by anybody – Need to access files (etc/shadow, etc/passwd) which are neither readable nor writable to normal user – How to achieve the goal? Need to be set-root-UID programs Computer Science CSC 405 Lab By Yuzheng Zhou 4
passwd, chsh, su (Cont’d) • passwd, chsh, su – Runnable by anybody – Need to access files (etc/shadow, etc/passwd) which are neither readable nor writable to normal user – How to achieve the goal? Need to be set-root-UID programs Computer Science CSC 405 Lab By Yuzheng Zhou 4
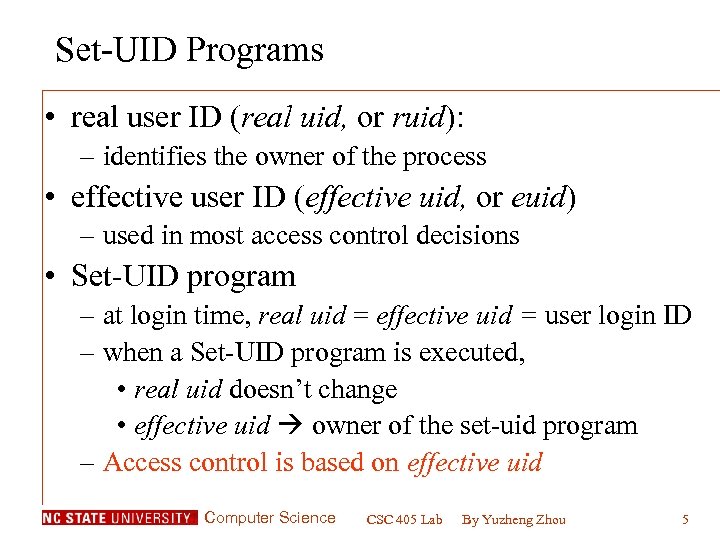 Set-UID Programs • real user ID (real uid, or ruid): – identifies the owner of the process • effective user ID (effective uid, or euid) – used in most access control decisions • Set-UID program – at login time, real uid = effective uid = user login ID – when a Set-UID program is executed, • real uid doesn’t change • effective uid owner of the set-uid program – Access control is based on effective uid Computer Science CSC 405 Lab By Yuzheng Zhou 5
Set-UID Programs • real user ID (real uid, or ruid): – identifies the owner of the process • effective user ID (effective uid, or euid) – used in most access control decisions • Set-UID program – at login time, real uid = effective uid = user login ID – when a Set-UID program is executed, • real uid doesn’t change • effective uid owner of the set-uid program – Access control is based on effective uid Computer Science CSC 405 Lab By Yuzheng Zhou 5
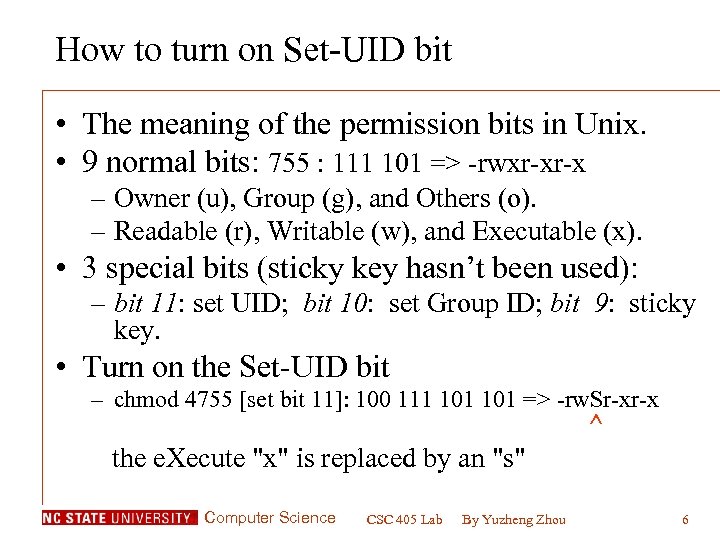 How to turn on Set-UID bit • The meaning of the permission bits in Unix. • 9 normal bits: 755 : 111 101 => -rwxr-xr-x – Owner (u), Group (g), and Others (o). – Readable (r), Writable (w), and Executable (x). • 3 special bits (sticky key hasn’t been used): – bit 11: set UID; bit 10: set Group ID; bit 9: sticky key. • Turn on the Set-UID bit – chmod 4755 [set bit 11]: 100 111 101 => -rw. Sr-xr-x ^ the e. Xecute "x" is replaced by an "s" Computer Science CSC 405 Lab By Yuzheng Zhou 6
How to turn on Set-UID bit • The meaning of the permission bits in Unix. • 9 normal bits: 755 : 111 101 => -rwxr-xr-x – Owner (u), Group (g), and Others (o). – Readable (r), Writable (w), and Executable (x). • 3 special bits (sticky key hasn’t been used): – bit 11: set UID; bit 10: set Group ID; bit 9: sticky key. • Turn on the Set-UID bit – chmod 4755 [set bit 11]: 100 111 101 => -rw. Sr-xr-x ^ the e. Xecute "x" is replaced by an "s" Computer Science CSC 405 Lab By Yuzheng Zhou 6
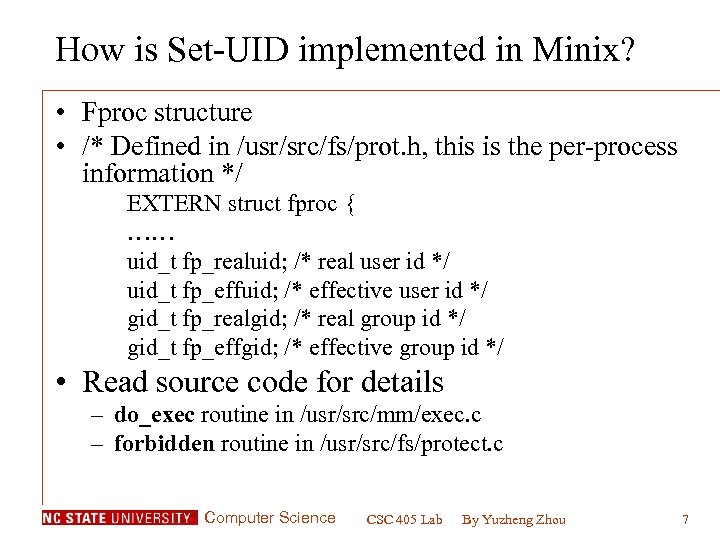 How is Set-UID implemented in Minix? • Fproc structure • /* Defined in /usr/src/fs/prot. h, this is the per-process information */ EXTERN struct fproc { …… uid_t fp_realuid; /* real user id */ uid_t fp_effuid; /* effective user id */ gid_t fp_realgid; /* real group id */ gid_t fp_effgid; /* effective group id */ • Read source code for details – do_exec routine in /usr/src/mm/exec. c – forbidden routine in /usr/src/fs/protect. c Computer Science CSC 405 Lab By Yuzheng Zhou 7
How is Set-UID implemented in Minix? • Fproc structure • /* Defined in /usr/src/fs/prot. h, this is the per-process information */ EXTERN struct fproc { …… uid_t fp_realuid; /* real user id */ uid_t fp_effuid; /* effective user id */ gid_t fp_realgid; /* real group id */ gid_t fp_effgid; /* effective group id */ • Read source code for details – do_exec routine in /usr/src/mm/exec. c – forbidden routine in /usr/src/fs/protect. c Computer Science CSC 405 Lab By Yuzheng Zhou 7
 Run Set-UID Programs • In Minix • Login as root. % cp /bin/sh /tmp/ % chmod 4755 /tmp/sh % exit • Login as yuzheng (normal user) $ /tmp/sh $ id $ uid=10 (yuzheng) gid=3(other) euid=0(root) suid=10(yuzheng) $ vi /etc/passwd (can open it !!!) Computer Science CSC 405 Lab By Yuzheng Zhou 8
Run Set-UID Programs • In Minix • Login as root. % cp /bin/sh /tmp/ % chmod 4755 /tmp/sh % exit • Login as yuzheng (normal user) $ /tmp/sh $ id $ uid=10 (yuzheng) gid=3(other) euid=0(root) suid=10(yuzheng) $ vi /etc/passwd (can open it !!!) Computer Science CSC 405 Lab By Yuzheng Zhou 8
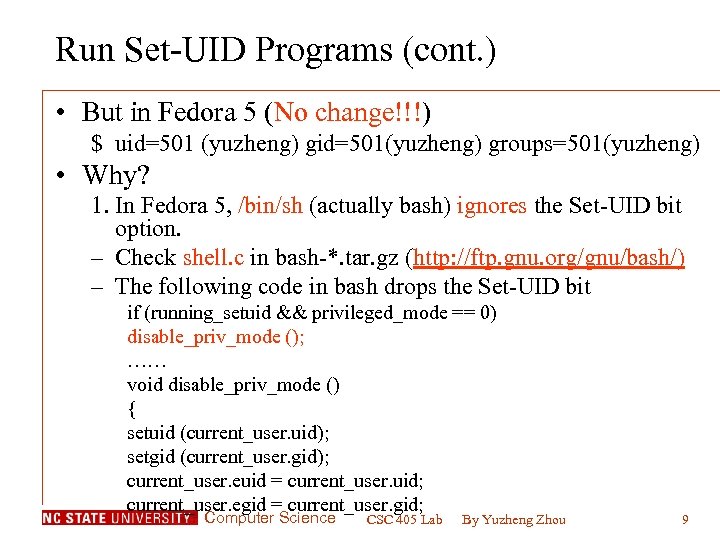 Run Set-UID Programs (cont. ) • But in Fedora 5 (No change!!!) $ uid=501 (yuzheng) gid=501(yuzheng) groups=501(yuzheng) • Why? 1. In Fedora 5, /bin/sh (actually bash) ignores the Set-UID bit option. – Check shell. c in bash-*. tar. gz (http: //ftp. gnu. org/gnu/bash/) – The following code in bash drops the Set-UID bit if (running_setuid && privileged_mode == 0) disable_priv_mode (); …… void disable_priv_mode () { setuid (current_user. uid); setgid (current_user. gid); current_user. euid = current_user. uid; current_user. egid = current_user. gid; Computer Science CSC 405 Lab By Yuzheng Zhou 9
Run Set-UID Programs (cont. ) • But in Fedora 5 (No change!!!) $ uid=501 (yuzheng) gid=501(yuzheng) groups=501(yuzheng) • Why? 1. In Fedora 5, /bin/sh (actually bash) ignores the Set-UID bit option. – Check shell. c in bash-*. tar. gz (http: //ftp. gnu. org/gnu/bash/) – The following code in bash drops the Set-UID bit if (running_setuid && privileged_mode == 0) disable_priv_mode (); …… void disable_priv_mode () { setuid (current_user. uid); setgid (current_user. gid); current_user. euid = current_user. uid; current_user. egid = current_user. gid; Computer Science CSC 405 Lab By Yuzheng Zhou 9
 PATH Environment Variable • system("ls") invoke the /bin/sh program, and then let the shell program to execute ls. • the shell searches for ls using the PATH environment variable. • The attacker can change PATH and cause ls in the current directory to be executed. $ export PATH =. : $PATH • Do you get root privilege? In Minix: yes; In Fedora: No Computer Science CSC 405 Lab By Yuzheng Zhou 10
PATH Environment Variable • system("ls") invoke the /bin/sh program, and then let the shell program to execute ls. • the shell searches for ls using the PATH environment variable. • The attacker can change PATH and cause ls in the current directory to be executed. $ export PATH =. : $PATH • Do you get root privilege? In Minix: yes; In Fedora: No Computer Science CSC 405 Lab By Yuzheng Zhou 10
 system() and execve() • System() invokes /bin/sh first. – In Fedora, it execv /bin/sh with arguments"sh", "-c" and the user provided string. • In Fedora 5, /bin/sh (actually bash) ignores the Set. UID bit option. – Why system() is more secure than execve in Linux – So, for problem 5 (a), we get “permission denied” message in Linux. • Want to read source code ? – download glibc-*. tar. gz from http: //ftp. gnu. org/gnu/glibc/ – search system and execve Computer Science CSC 405 Lab By Yuzheng Zhou 11
system() and execve() • System() invokes /bin/sh first. – In Fedora, it execv /bin/sh with arguments"sh", "-c" and the user provided string. • In Fedora 5, /bin/sh (actually bash) ignores the Set. UID bit option. – Why system() is more secure than execve in Linux – So, for problem 5 (a), we get “permission denied” message in Linux. • Want to read source code ? – download glibc-*. tar. gz from http: //ftp. gnu. org/gnu/glibc/ – search system and execve Computer Science CSC 405 Lab By Yuzheng Zhou 11
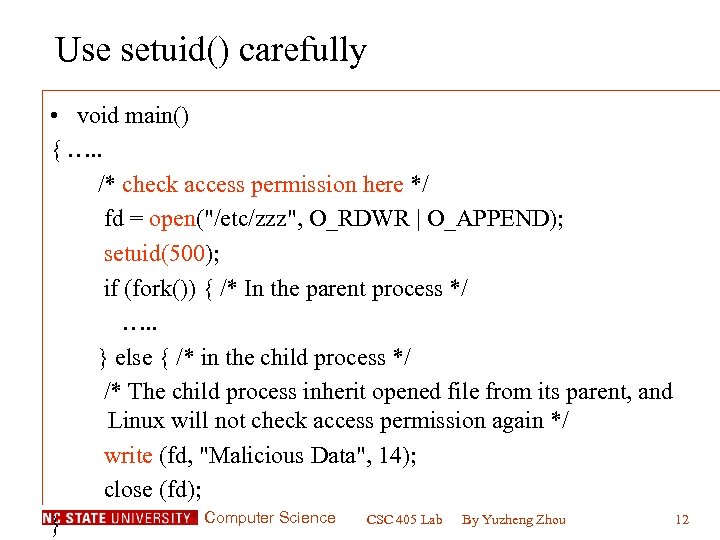 Use setuid() carefully • void main() { …. . /* check access permission here */ fd = open("/etc/zzz", O_RDWR | O_APPEND); setuid(500); if (fork()) { /* In the parent process */ …. . } else { /* in the child process */ /* The child process inherit opened file from its parent, and Linux will not check access permission again */ write (fd, "Malicious Data", 14); close (fd); Computer Science CSC 405 Lab By Yuzheng Zhou 12 }
Use setuid() carefully • void main() { …. . /* check access permission here */ fd = open("/etc/zzz", O_RDWR | O_APPEND); setuid(500); if (fork()) { /* In the parent process */ …. . } else { /* in the child process */ /* The child process inherit opened file from its parent, and Linux will not check access permission again */ write (fd, "Malicious Data", 14); close (fd); Computer Science CSC 405 Lab By Yuzheng Zhou 12 }
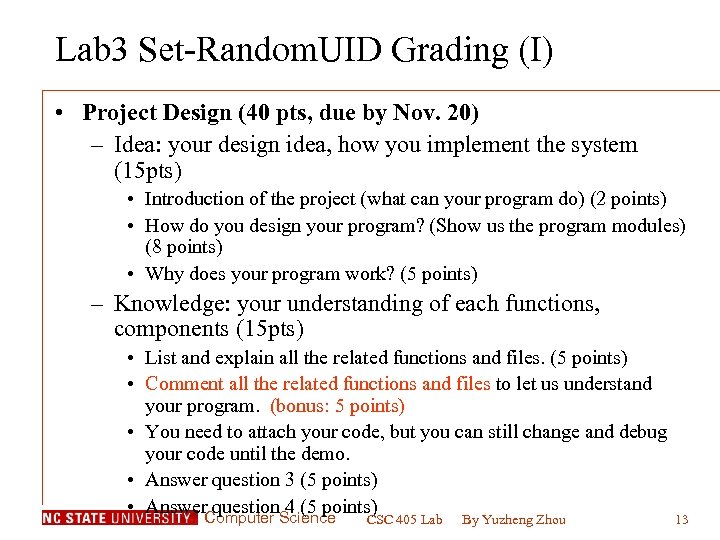 Lab 3 Set-Random. UID Grading (I) • Project Design (40 pts, due by Nov. 20) – Idea: your design idea, how you implement the system (15 pts) • Introduction of the project (what can your program do) (2 points) • How do you design your program? (Show us the program modules) (8 points) • Why does your program work? (5 points) – Knowledge: your understanding of each functions, components (15 pts) • List and explain all the related functions and files. (5 points) • Comment all the related functions and files to let us understand your program. (bonus: 5 points) • You need to attach your code, but you can still change and debug your code until the demo. • Answer question 3 (5 points) • Answer question 4 (5 points) Computer Science CSC 405 Lab By Yuzheng Zhou 13
Lab 3 Set-Random. UID Grading (I) • Project Design (40 pts, due by Nov. 20) – Idea: your design idea, how you implement the system (15 pts) • Introduction of the project (what can your program do) (2 points) • How do you design your program? (Show us the program modules) (8 points) • Why does your program work? (5 points) – Knowledge: your understanding of each functions, components (15 pts) • List and explain all the related functions and files. (5 points) • Comment all the related functions and files to let us understand your program. (bonus: 5 points) • You need to attach your code, but you can still change and debug your code until the demo. • Answer question 3 (5 points) • Answer question 4 (5 points) Computer Science CSC 405 Lab By Yuzheng Zhou 13
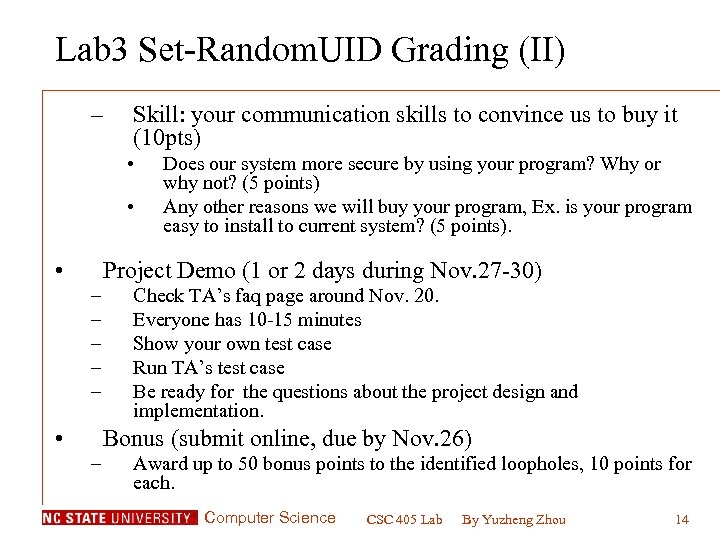 Lab 3 Set-Random. UID Grading (II) – Skill: your communication skills to convince us to buy it (10 pts) • • • Does our system more secure by using your program? Why or why not? (5 points) Any other reasons we will buy your program, Ex. is your program easy to install to current system? (5 points). Project Demo (1 or 2 days during Nov. 27 -30) – – – • Check TA’s faq page around Nov. 20. Everyone has 10 -15 minutes Show your own test case Run TA’s test case Be ready for the questions about the project design and implementation. Bonus (submit online, due by Nov. 26) – Award up to 50 bonus points to the identified loopholes, 10 points for each. Computer Science CSC 405 Lab By Yuzheng Zhou 14
Lab 3 Set-Random. UID Grading (II) – Skill: your communication skills to convince us to buy it (10 pts) • • • Does our system more secure by using your program? Why or why not? (5 points) Any other reasons we will buy your program, Ex. is your program easy to install to current system? (5 points). Project Demo (1 or 2 days during Nov. 27 -30) – – – • Check TA’s faq page around Nov. 20. Everyone has 10 -15 minutes Show your own test case Run TA’s test case Be ready for the questions about the project design and implementation. Bonus (submit online, due by Nov. 26) – Award up to 50 bonus points to the identified loopholes, 10 points for each. Computer Science CSC 405 Lab By Yuzheng Zhou 14


