84260aadc27c7af526dac2dbc5d27c53.ppt
- Количество слайдов: 157
 Computer Science An Overview Allen C. -H. Wu Computer Science Department Tsing Hua University 1
Computer Science An Overview Allen C. -H. Wu Computer Science Department Tsing Hua University 1
 Preface 4 Beginning computer science students need exposure to the breadth of the subject in which they are planning to major. 4 A foundation from which they can understand the relevance and interrelationships of future courses. 2
Preface 4 Beginning computer science students need exposure to the breadth of the subject in which they are planning to major. 4 A foundation from which they can understand the relevance and interrelationships of future courses. 2
 Introduction 4 Computer science is the discipline that seeks to build a scientific foundation for a variety of topics. 4 Computer science provides the underpinnings for today’s computer applications as well as the foundations for tomorrow’s applications. 3
Introduction 4 Computer science is the discipline that seeks to build a scientific foundation for a variety of topics. 4 Computer science provides the underpinnings for today’s computer applications as well as the foundations for tomorrow’s applications. 3
 The Study of Algorithms 4 An algorithm is a set of steps that defines how a task is performed. 4 In the domain of computing machinery, algorithms are represented as programs within computers. 4 Algorithms + Data Structure -> Programs, Programs -> Software <=> Hardware. 4
The Study of Algorithms 4 An algorithm is a set of steps that defines how a task is performed. 4 In the domain of computing machinery, algorithms are represented as programs within computers. 4 Algorithms + Data Structure -> Programs, Programs -> Software <=> Hardware. 4
 The Study of Algorithms 4 The study of algorithms began as a subject in mathematics. 4 The major goal is to find a single set of directions that described how any problem of a particular type could be solved. 4 E. g. , the long division algorithm and the Euclidean algorithm. 5
The Study of Algorithms 4 The study of algorithms began as a subject in mathematics. 4 The major goal is to find a single set of directions that described how any problem of a particular type could be solved. 4 E. g. , the long division algorithm and the Euclidean algorithm. 5
 The Study of Algorithms 4 Machine Architecture - Data storage (Ch. 1) Data manipulation (Ch. 2) 4 Software. Operating systems and networks (Ch. 3). Algorithms (Ch. 4). Programming languages (Ch. 5) Software engineering (Ch. 6) 4 Data Organization. Data structures (Ch. 7). File structures (Ch. 8). Database structures (Ch. 9) 4 AI and Theory of Computation . . . 6
The Study of Algorithms 4 Machine Architecture - Data storage (Ch. 1) Data manipulation (Ch. 2) 4 Software. Operating systems and networks (Ch. 3). Algorithms (Ch. 4). Programming languages (Ch. 5) Software engineering (Ch. 6) 4 Data Organization. Data structures (Ch. 7). File structures (Ch. 8). Database structures (Ch. 9) 4 AI and Theory of Computation . . . 6
 The Development of Algorithmic Machines 4 Abacus. 4 Babbage’s difference engine. 4 Jacquard’s loom. 4 Herman Hollerith (holes in paper cards). 4 Mark I at Harvard University. 4 ENIAC at U. of Pennsylvania. 7
The Development of Algorithmic Machines 4 Abacus. 4 Babbage’s difference engine. 4 Jacquard’s loom. 4 Herman Hollerith (holes in paper cards). 4 Mark I at Harvard University. 4 ENIAC at U. of Pennsylvania. 7
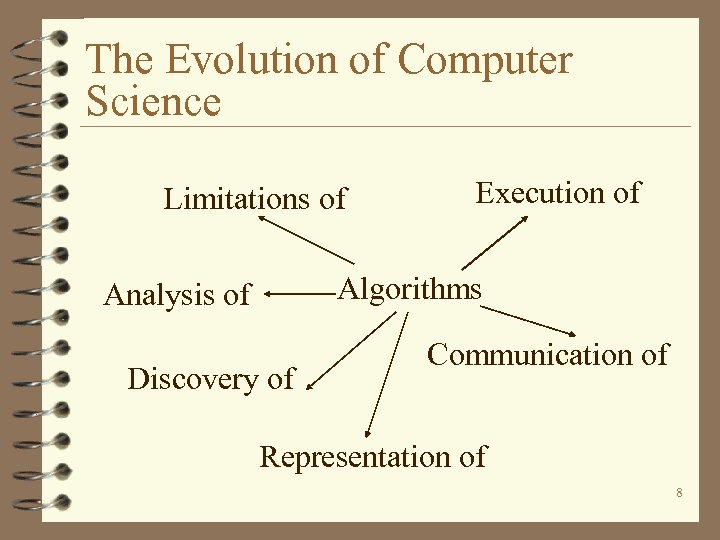 The Evolution of Computer Science Limitations of Execution of Algorithms Analysis of Discovery of Communication of Representation of 8
The Evolution of Computer Science Limitations of Execution of Algorithms Analysis of Discovery of Communication of Representation of 8
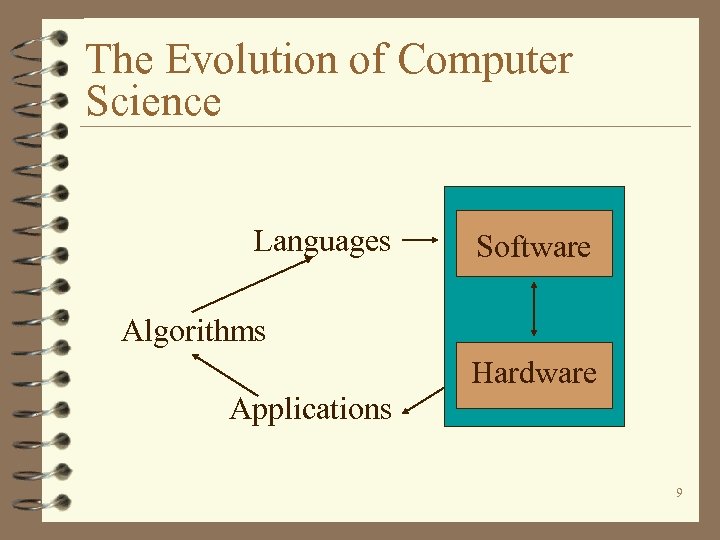 The Evolution of Computer Science Languages Software Algorithms Hardware Applications 9
The Evolution of Computer Science Languages Software Algorithms Hardware Applications 9
 Abstraction and Other Issues 4 Abstraction - the distinction between the external properties of a component and the internal details of the component’s construction. 4 Ethical issues. 4 Social issues. 4 Legal issues. 10
Abstraction and Other Issues 4 Abstraction - the distinction between the external properties of a component and the internal details of the component’s construction. 4 Ethical issues. 4 Social issues. 4 Legal issues. 10
 Part I: Machine Architecture 4 A major process in the development of a science is the construction of theories that are confirmed or rejected by experimentation. 4 In some cases these theories lie dormant for extended periods, waiting for technology to develop to the point that they can be tested. 11
Part I: Machine Architecture 4 A major process in the development of a science is the construction of theories that are confirmed or rejected by experimentation. 4 In some cases these theories lie dormant for extended periods, waiting for technology to develop to the point that they can be tested. 11
 Ch. 1 Data Storage 4 4 4 4 Storage of bits. Main memory. Mass storage. Coding information for storage. The binary system. Storing integers. Storing Fractions. Communication errors. 12
Ch. 1 Data Storage 4 4 4 4 Storage of bits. Main memory. Mass storage. Coding information for storage. The binary system. Storing integers. Storing Fractions. Communication errors. 12
 Storage of bits 4 Boolean operations, e. g. , AND, NOT, and OR. 4 Gates are devices that produce the output of a Boolean operation when given the operation’s input values. 4 A flip-flop is a circuit that has one of two output values (i. e. , 0 or 1), the output will flip or flop between two values under control of external stimuli. 13
Storage of bits 4 Boolean operations, e. g. , AND, NOT, and OR. 4 Gates are devices that produce the output of a Boolean operation when given the operation’s input values. 4 A flip-flop is a circuit that has one of two output values (i. e. , 0 or 1), the output will flip or flop between two values under control of external stimuli. 13
 Storage of Bits 4 A flip-flop is ideal for the storage of a bit within a computer (on a single wafer or chip). A flip-flop loses data when its power is turned off. 4 Cores, a donut-shaped rings of magnetic material, are obsolete today due to their size and power requirements. 4 A magnetic or laser storage device is commonly used when longevity is important. 14 4 Hexadecimal notation.
Storage of Bits 4 A flip-flop is ideal for the storage of a bit within a computer (on a single wafer or chip). A flip-flop loses data when its power is turned off. 4 Cores, a donut-shaped rings of magnetic material, are obsolete today due to their size and power requirements. 4 A magnetic or laser storage device is commonly used when longevity is important. 14 4 Hexadecimal notation.
 Main Memory 4 Cells - a typical cell size is 8 or called byte. 4 Address is used to identify individual cells in a main memory. 4 Random access memory (RAM). 4 Read only memory (ROM). 4 Most significant bit (MSB) and least significant bit (LSB). 15
Main Memory 4 Cells - a typical cell size is 8 or called byte. 4 Address is used to identify individual cells in a main memory. 4 Random access memory (RAM). 4 Read only memory (ROM). 4 Most significant bit (MSB) and least significant bit (LSB). 15
 Mass Storage 4 Secondary memory. 4 Storing large units of data (called files). 4 Mass storage systems are slow due to mechanical motion requirement. 4 On-line Vs. off-line operations. 16
Mass Storage 4 Secondary memory. 4 Storing large units of data (called files). 4 Mass storage systems are slow due to mechanical motion requirement. 4 On-line Vs. off-line operations. 16
 Mass Storage 4 4 Disk storage. Compact disks and CD-ROM. Tape storage. Physical Vs. logical records. 17
Mass Storage 4 4 Disk storage. Compact disks and CD-ROM. Tape storage. Physical Vs. logical records. 17
 Coding Information for Storage 4 American Standard Code for Information Interchange (ASCII) - 8 -bit codes. 4 International Standards Organization (ISO) - 16 -bit codes. 4 Binary-decimal number conversion. 4 Bit maps representation - Tag Image Format File (TIFF), Graphic Interchange Format (GIF), and Joint Photographs Experts Group (JPEG). 18
Coding Information for Storage 4 American Standard Code for Information Interchange (ASCII) - 8 -bit codes. 4 International Standards Organization (ISO) - 16 -bit codes. 4 Binary-decimal number conversion. 4 Bit maps representation - Tag Image Format File (TIFF), Graphic Interchange Format (GIF), and Joint Photographs Experts Group (JPEG). 18
 The Binary System 4 Binary addition. 4 Fractions in binary. 4 Radix point (same as decimal point in decimal notation). 19
The Binary System 4 Binary addition. 4 Fractions in binary. 4 Radix point (same as decimal point in decimal notation). 19
 Storing Integers 4 4 4 Excess notation. Two’s complement notation. Addition in two’s complement notation. Overflow problem. Double precision. Memory size Vs. accuracy of number representation. 20
Storing Integers 4 4 4 Excess notation. Two’s complement notation. Addition in two’s complement notation. Overflow problem. Double precision. Memory size Vs. accuracy of number representation. 20
 Storing Fractions 4 Floating-point notation. 4 Sign bit => Exponent => Mantissa. 4 Round-off errors. 21
Storing Fractions 4 Floating-point notation. 4 Sign bit => Exponent => Mantissa. 4 Round-off errors. 21
 Communication Errors 4 How can you make sure the information you receive is correct? ? ? 4 Coding techniques for error detection and correction. 4 Parity bits. 4 Error-correcting codes. 22
Communication Errors 4 How can you make sure the information you receive is correct? ? ? 4 Coding techniques for error detection and correction. 4 Parity bits. 4 Error-correcting codes. 22
 Ch. 2 Data Manipulation 4 The central processing unit. 4 The stored-program concept. 4 Program execution. 4 Other architectures. 4 Arithmetic/logic instructions. 4 Computer-peripheral communication. 23
Ch. 2 Data Manipulation 4 The central processing unit. 4 The stored-program concept. 4 Program execution. 4 Other architectures. 4 Arithmetic/logic instructions. 4 Computer-peripheral communication. 23
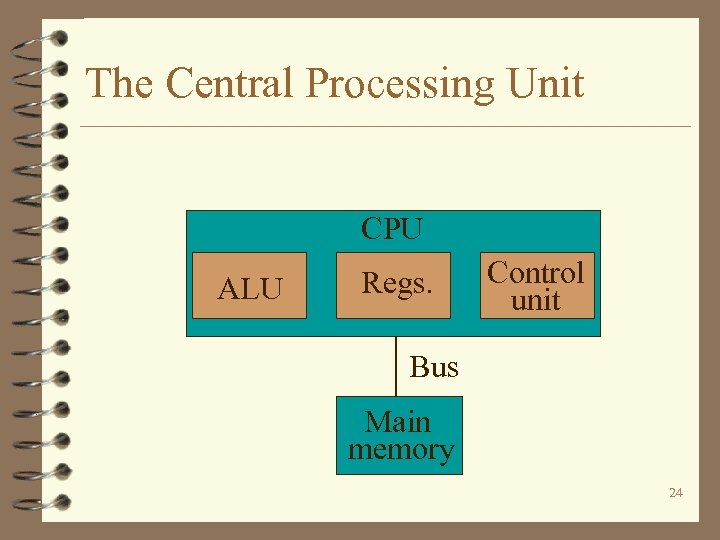 The Central Processing Unit CPU ALU Regs. Control unit Bus Main memory 24
The Central Processing Unit CPU ALU Regs. Control unit Bus Main memory 24
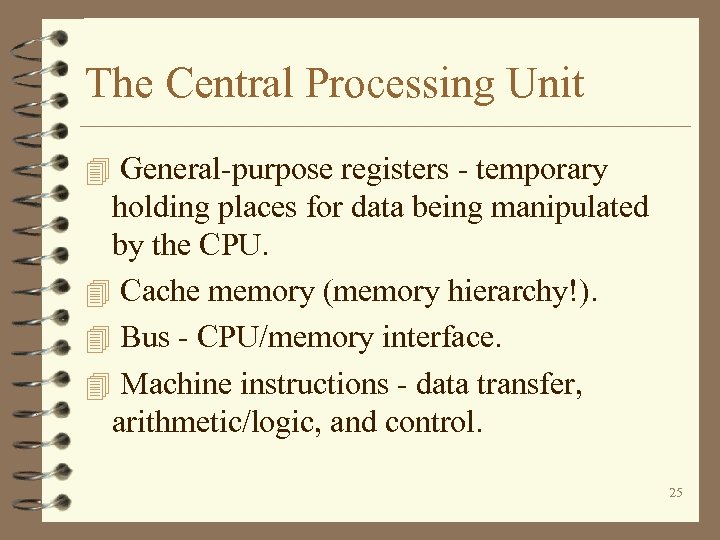 The Central Processing Unit 4 General-purpose registers - temporary holding places for data being manipulated by the CPU. 4 Cache memory (memory hierarchy!). 4 Bus - CPU/memory interface. 4 Machine instructions - data transfer, arithmetic/logic, and control. 25
The Central Processing Unit 4 General-purpose registers - temporary holding places for data being manipulated by the CPU. 4 Cache memory (memory hierarchy!). 4 Bus - CPU/memory interface. 4 Machine instructions - data transfer, arithmetic/logic, and control. 25
 The Stored-Program Concept 4 In early computing, the program is built into the control unit as a part of the machine. The user rewires the control unit to adapt different programs. 4 Instructions as bit patterns - a program and data can be coded and stored in main memory. A computer’s program can be changed merely by changing the contents of the computer’s memory instead of rewiring the control unit. 26
The Stored-Program Concept 4 In early computing, the program is built into the control unit as a part of the machine. The user rewires the control unit to adapt different programs. 4 Instructions as bit patterns - a program and data can be coded and stored in main memory. A computer’s program can be changed merely by changing the contents of the computer’s memory instead of rewiring the control unit. 26
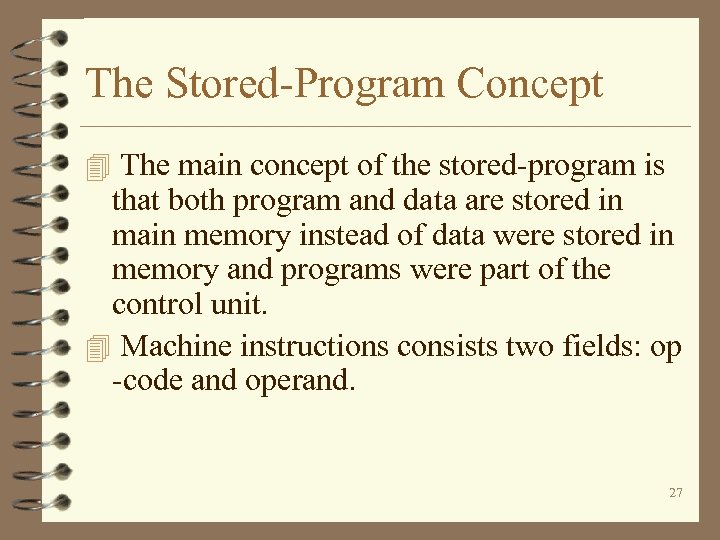 The Stored-Program Concept 4 The main concept of the stored-program is that both program and data are stored in main memory instead of data were stored in memory and programs were part of the control unit. 4 Machine instructions consists two fields: op -code and operand. 27
The Stored-Program Concept 4 The main concept of the stored-program is that both program and data are stored in main memory instead of data were stored in memory and programs were part of the control unit. 4 Machine instructions consists two fields: op -code and operand. 27
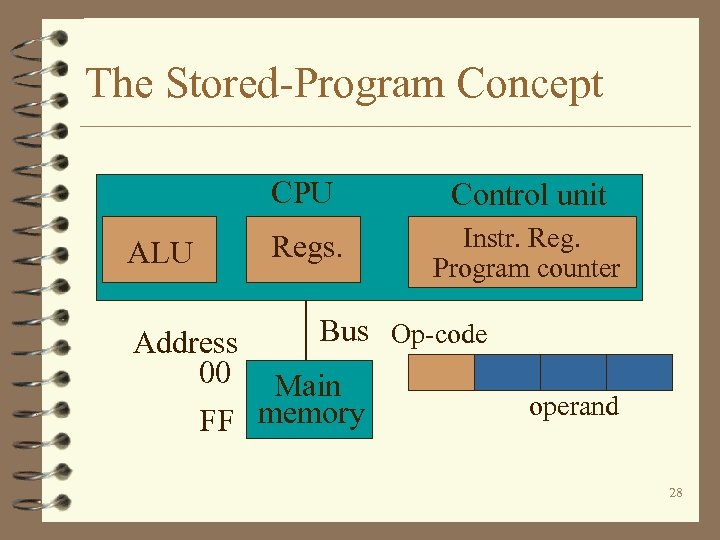 The Stored-Program Concept CPU ALU Control unit Regs. Instr. Reg. Program counter Bus Op-code Address 00 Main FF memory operand 28
The Stored-Program Concept CPU ALU Control unit Regs. Instr. Reg. Program counter Bus Op-code Address 00 Main FF memory operand 28
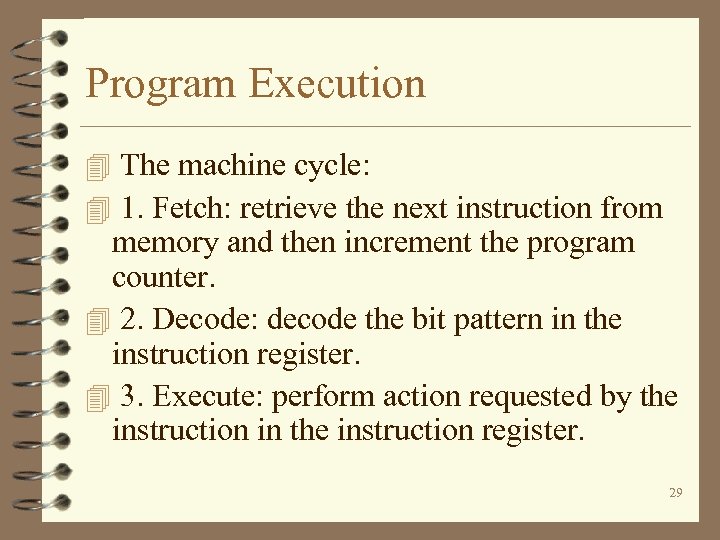 Program Execution 4 The machine cycle: 4 1. Fetch: retrieve the next instruction from memory and then increment the program counter. 4 2. Decode: decode the bit pattern in the instruction register. 4 3. Execute: perform action requested by the instruction in the instruction register. 29
Program Execution 4 The machine cycle: 4 1. Fetch: retrieve the next instruction from memory and then increment the program counter. 4 2. Decode: decode the bit pattern in the instruction register. 4 3. Execute: perform action requested by the instruction in the instruction register. 29
 Other Architectures 4 The design of a machine’s language - complex instruction set Vs. simple instruction set. 4 CISC Vs. RISC. 4 CISC - microprogram. 4 RISC - simple CPU design. 30
Other Architectures 4 The design of a machine’s language - complex instruction set Vs. simple instruction set. 4 CISC Vs. RISC. 4 CISC - microprogram. 4 RISC - simple CPU design. 30
 Other Architectures 4 Pipelining - the throughput concept. 4 Multiprocessor machines - parallel processing. 4 SISD, SIMD, MIMD. 4 Load balancing problem in multiprocessor machines. 4 Distributed systems. 31
Other Architectures 4 Pipelining - the throughput concept. 4 Multiprocessor machines - parallel processing. 4 SISD, SIMD, MIMD. 4 Load balancing problem in multiprocessor machines. 4 Distributed systems. 31
 Arithmetic/Logic Instructions 4 Logic operations - AND, OR, XOR, …. 4 Masking (AND operation) and bit map. 4 Rotation and shift operations - logic shift and arithmetic shift (leave the sign bit unchanged). 4 Arithmetic operations - add, subtract, …. . 32
Arithmetic/Logic Instructions 4 Logic operations - AND, OR, XOR, …. 4 Masking (AND operation) and bit map. 4 Rotation and shift operations - logic shift and arithmetic shift (leave the sign bit unchanged). 4 Arithmetic operations - add, subtract, …. . 32
 Computer-Peripheral Communication 4 Controllers handle communication between machine’s CPU and peripheral devices. 4 The controllers are often a stand-alone small computer, each with its own memory and CPU that performs a program to convert messages and data back and forth between machine and a peripheral device. 33
Computer-Peripheral Communication 4 Controllers handle communication between machine’s CPU and peripheral devices. 4 The controllers are often a stand-alone small computer, each with its own memory and CPU that performs a program to convert messages and data back and forth between machine and a peripheral device. 33
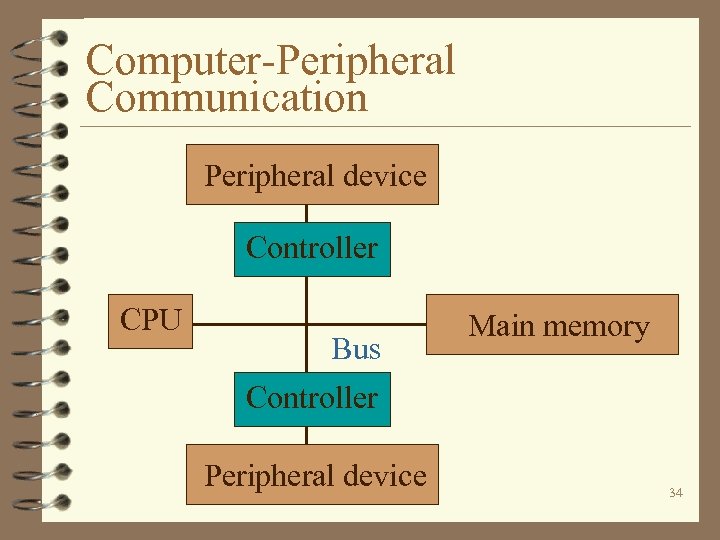 Computer-Peripheral Communication Peripheral device Controller CPU Bus Main memory Controller Peripheral device 34
Computer-Peripheral Communication Peripheral device Controller CPU Bus Main memory Controller Peripheral device 34
 Computer-Peripheral Communication 4 Direct memory access (DMA) - the ability of controller which can access memory directly. 4 Buffering - a buffer is any location where one system leaves data to be picked up later by another. 4 von Neumann bottleneck - central communication bus problem. 35
Computer-Peripheral Communication 4 Direct memory access (DMA) - the ability of controller which can access memory directly. 4 Buffering - a buffer is any location where one system leaves data to be picked up later by another. 4 von Neumann bottleneck - central communication bus problem. 35
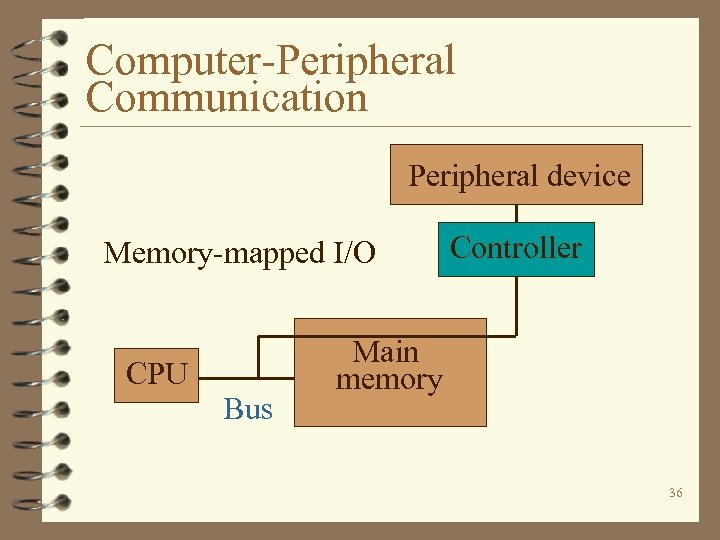 Computer-Peripheral Communication Peripheral device Memory-mapped I/O CPU Bus Controller Main memory 36
Computer-Peripheral Communication Peripheral device Memory-mapped I/O CPU Bus Controller Main memory 36
 Computer-Peripheral Communication 4 Port - the block of addresses associated with a controller. 4 Handshaking - the two-way communication that takes place between devices. 4 Parallel and serial communications. 4 Bits per second (bps) and baud rate. 4 Data compression. 4 Huffman code. 4 Lempel-Ziv encoding. 37
Computer-Peripheral Communication 4 Port - the block of addresses associated with a controller. 4 Handshaking - the two-way communication that takes place between devices. 4 Parallel and serial communications. 4 Bits per second (bps) and baud rate. 4 Data compression. 4 Huffman code. 4 Lempel-Ziv encoding. 37
 Part II: Software 4 In part II, we focus on topics associated with software. In particular, we will investigate the discovery, representation, and communication of algorithms. 4 Operating systems and networks. 4 Algorithms. 4 Programming languages. 4 Software engineering. 38
Part II: Software 4 In part II, we focus on topics associated with software. In particular, we will investigate the discovery, representation, and communication of algorithms. 4 Operating systems and networks. 4 Algorithms. 4 Programming languages. 4 Software engineering. 38
 Ch. 3 Operating Systems and Networks 4 The evolution of operating systems. 4 Operating system architecture. 4 Coordinating the machine’s activities. 4 Handling Competition among processes. 4 Network protocols. 39
Ch. 3 Operating Systems and Networks 4 The evolution of operating systems. 4 Operating system architecture. 4 Coordinating the machine’s activities. 4 Handling Competition among processes. 4 Network protocols. 39
 Operating Systems 4 Why needs an operating system? 4 Computer applications often require a single machine to perform activities that may compete with one another for the machine’s resources. It requires a high degree of coordination to ensure that unrelated activities do not interfere with one another and that communication between related activities is efficient and reliable. 4 What is an operating system? A software system which handles such a coordination task. 40
Operating Systems 4 Why needs an operating system? 4 Computer applications often require a single machine to perform activities that may compete with one another for the machine’s resources. It requires a high degree of coordination to ensure that unrelated activities do not interfere with one another and that communication between related activities is efficient and reliable. 4 What is an operating system? A software system which handles such a coordination task. 40
 The evolution of Operating Systems 4 Single-processor systems. 4 Batch processing - the execution of jobs (programs) by collecting them in a single batch, then executing them without further interaction with the user. 4 A job queue (FIFO) and a job control language (JCL). 4 The main drawback to batch processing is no interaction between user and job. 41
The evolution of Operating Systems 4 Single-processor systems. 4 Batch processing - the execution of jobs (programs) by collecting them in a single batch, then executing them without further interaction with the user. 4 A job queue (FIFO) and a job control language (JCL). 4 The main drawback to batch processing is no interaction between user and job. 41
 The Evolution of Operating Systems Interactive processing, Real-time processing. Time-sharing. Multitasking - time-sharing for a single user systems. 4 Multiprocessor systems - networks such as internet. 4 Load balancing and scaling problems. 4 4 42
The Evolution of Operating Systems Interactive processing, Real-time processing. Time-sharing. Multitasking - time-sharing for a single user systems. 4 Multiprocessor systems - networks such as internet. 4 Load balancing and scaling problems. 4 4 42
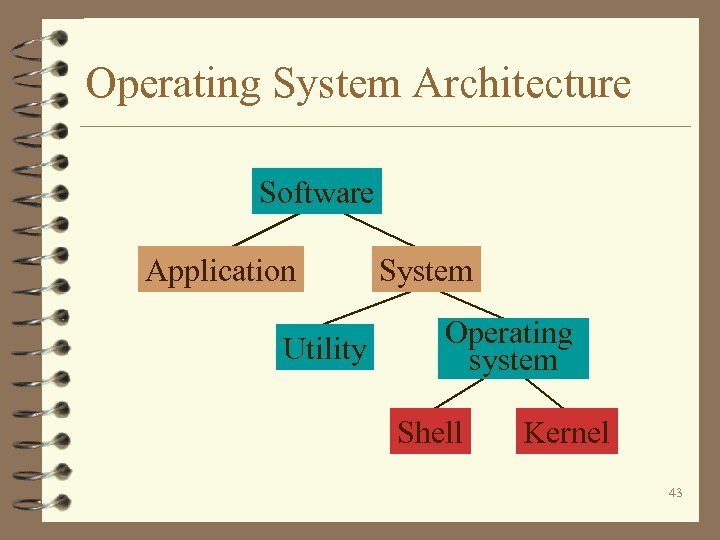 Operating System Architecture Software Application Utility System Operating system Shell Kernel 43
Operating System Architecture Software Application Utility System Operating system Shell Kernel 43
 Operating System Architecture 4 A machine’s software can be divided into two categories: application software and system software. 4 Application software - the programs for performing tasks particular to the machine’s utilization. 4 System software - performs tasks which are common to computer systems in general. 44
Operating System Architecture 4 A machine’s software can be divided into two categories: application software and system software. 4 Application software - the programs for performing tasks particular to the machine’s utilization. 4 System software - performs tasks which are common to computer systems in general. 44
 Operating System Architecture 4 System software can be divided into two categories: operating-system software and utility software. 4 Utility software consists of software units that extend the capabilities of the operating system. For example, the ability to format a disk or software for communicating through a modem over telephone lines. 45
Operating System Architecture 4 System software can be divided into two categories: operating-system software and utility software. 4 Utility software consists of software units that extend the capabilities of the operating system. For example, the ability to format a disk or software for communicating through a modem over telephone lines. 45
 Operating System Architecture 4 Shell - the portion of an operating system that defines the interface between the operating system and its users. 4 Graphical user interface (GUI). 4 Importance of uniformity in the humanmachine interface across a variety of machines. 4 UNIX Vs. MS-DOS and Windows. 46
Operating System Architecture 4 Shell - the portion of an operating system that defines the interface between the operating system and its users. 4 Graphical user interface (GUI). 4 Importance of uniformity in the humanmachine interface across a variety of machines. 4 UNIX Vs. MS-DOS and Windows. 46
 Operating System Architecture 4 Kernel - the internal part of an operating system, which contains those software components that perform the very basic functions required by the computer installation. 4 File manager - directory (folder) and path. 4 Device drivers. 4 Memory manager. 47
Operating System Architecture 4 Kernel - the internal part of an operating system, which contains those software components that perform the very basic functions required by the computer installation. 4 File manager - directory (folder) and path. 4 Device drivers. 4 Memory manager. 47
 Operating System Architecture 4 4 4 Main memory Vs. virtual memory. Pages. Scheduler and dispatcher. Booting (booting strapping). Bootstrap - a short program placed in ROM and this program is executed automatically when the machine is turned on. 48
Operating System Architecture 4 4 4 Main memory Vs. virtual memory. Pages. Scheduler and dispatcher. Booting (booting strapping). Bootstrap - a short program placed in ROM and this program is executed automatically when the machine is turned on. 48
 Coordinating the Machine Activities 4 Process - is a dynamic activity whose properties change as time progresses. 4 Process state - is a snapshot of the machine at that time. For example, the current position in the program being executed and the values in the CPU registers. 4 A program Vs. a process. 4 Interprocess communication. 49
Coordinating the Machine Activities 4 Process - is a dynamic activity whose properties change as time progresses. 4 Process state - is a snapshot of the machine at that time. For example, the current position in the program being executed and the values in the CPU registers. 4 A program Vs. a process. 4 Interprocess communication. 49
 Coordinating the Machine’s Activities 4 Process administration - the tasks associated with process coordination are handled by the scheduler and dispatcher within the operating system’s kernel. 4 Process table - keeps information of a process when it is created (assigned memory area, the priority, the status - ready or waiting). 50
Coordinating the Machine’s Activities 4 Process administration - the tasks associated with process coordination are handled by the scheduler and dispatcher within the operating system’s kernel. 4 Process table - keeps information of a process when it is created (assigned memory area, the priority, the status - ready or waiting). 50
 Coordinating the Machine’s Activities 4 The dispatcher is the component of the kernel that ensures that the scheduled processes are actually executed. 4 In a time-sharing system, the dispatcher divides time into time slices or quantum. 4 The dispatcher interrupts the process running out of a time slice and assign a time slice to another process (process switch). 51
Coordinating the Machine’s Activities 4 The dispatcher is the component of the kernel that ensures that the scheduled processes are actually executed. 4 In a time-sharing system, the dispatcher divides time into time slices or quantum. 4 The dispatcher interrupts the process running out of a time slice and assign a time slice to another process (process switch). 51
 Coordinating the Machine’s Activities 4 The client/server model. 4 A client - makes requests of other units. 4 A server - satisfies the requests made by clients. 4 The client/server model in the design software leads to uniformity among the types of communication taking place in the system. 52
Coordinating the Machine’s Activities 4 The client/server model. 4 A client - makes requests of other units. 4 A server - satisfies the requests made by clients. 4 The client/server model in the design software leads to uniformity among the types of communication taking place in the system. 52
 Handling Competition Among Processes 4 4 Competing resources among processes. Semaphores. Test-and-set. Critical region - is a sequence of instructions which can be executed by only one process. 53
Handling Competition Among Processes 4 4 Competing resources among processes. Semaphores. Test-and-set. Critical region - is a sequence of instructions which can be executed by only one process. 53
 Handling Competition Among Processes 4 Deadlock - when two or more processes are blocked from processing because each is waiting for access to resources allocated to another. 4 Three necessary conditions to avoid deadlock: 4 1. There is competition for non-shareable resources. 54
Handling Competition Among Processes 4 Deadlock - when two or more processes are blocked from processing because each is waiting for access to resources allocated to another. 4 Three necessary conditions to avoid deadlock: 4 1. There is competition for non-shareable resources. 54
 Handling Competition Among Processes 4 2. The resources are requested on a partial basis; that is, having received some resources, a process will return later to request more. 4 3. Once a resource has been allocated, it cannot be forcibly retrieved. 4 Spooling - holding data for output at a later but more convenient time. 55
Handling Competition Among Processes 4 2. The resources are requested on a partial basis; that is, having received some resources, a process will return later to request more. 4 3. Once a resource has been allocated, it cannot be forcibly retrieved. 4 Spooling - holding data for output at a later but more convenient time. 55
 Networks 4 Local area networks (LAN). 4 Wide area networks (WAN). 4 Proprietary networks. 4 Open networks. 4 Network topology - ring, bus, star, and irregular. 56
Networks 4 Local area networks (LAN). 4 Wide area networks (WAN). 4 Proprietary networks. 4 Open networks. 4 Network topology - ring, bus, star, and irregular. 56
 Networks 4 Internet - initiated in 1973 by the Defense Advanced Research Projects Agency (DARPA). Goal: develop the ability to connect a variety of computer networks o that they can function as a single network. 4 Internet addressing - domains (a collection of network clusters), network identifier, host address; ex. , chunghaw@cs. nthu. edu. tw. 57
Networks 4 Internet - initiated in 1973 by the Defense Advanced Research Projects Agency (DARPA). Goal: develop the ability to connect a variety of computer networks o that they can function as a single network. 4 Internet addressing - domains (a collection of network clusters), network identifier, host address; ex. , chunghaw@cs. nthu. edu. tw. 57
 Networks 4 Email and name server. 4 The world wide web - hypertext and hypermedia documents. 4 A browser - a client. 4 Uniform resource locator (URL) - a browser can contact the proper server and request the desired document. 4 Hypertext Markup Language (HTML). 58
Networks 4 Email and name server. 4 The world wide web - hypertext and hypermedia documents. 4 A browser - a client. 4 Uniform resource locator (URL) - a browser can contact the proper server and request the desired document. 4 Hypertext Markup Language (HTML). 58
 Networks 4 Unauthorized access to information and vandalism. 4 Passwords and data encryption. 4 Virus. 4 Worm. 59
Networks 4 Unauthorized access to information and vandalism. 4 Passwords and data encryption. 4 Virus. 4 Worm. 59
 Network Protocols 4 Protocols - the rules that govern the communication between different components within a computer system. 4 Token ring protocol for networks with the ring topology. 4 CSMA/CD (carrier sense, multiple access with collision detection) in an Ethernet. 60
Network Protocols 4 Protocols - the rules that govern the communication between different components within a computer system. 4 Token ring protocol for networks with the ring topology. 4 CSMA/CD (carrier sense, multiple access with collision detection) in an Ethernet. 60
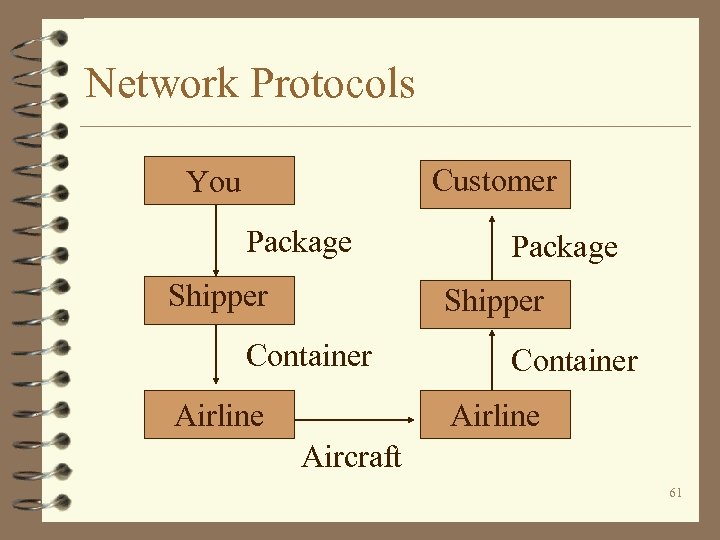 Network Protocols Customer You Package Shipper Container Airline Aircraft 61
Network Protocols Customer You Package Shipper Container Airline Aircraft 61
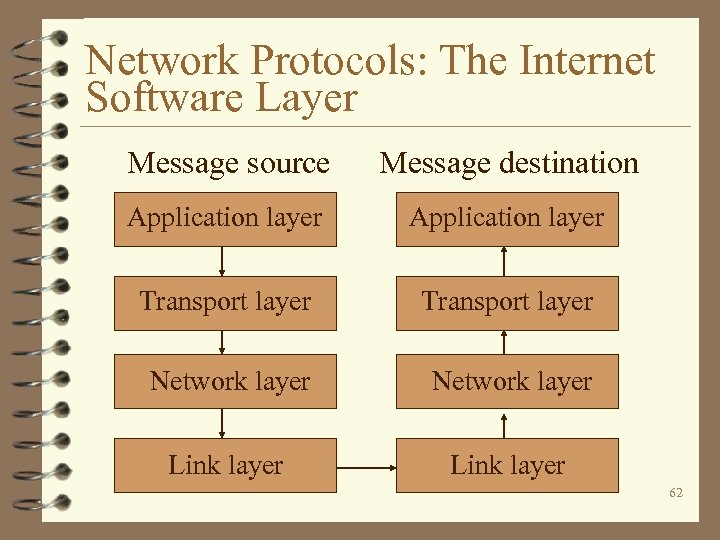 Network Protocols: The Internet Software Layer Message source Message destination Application layer Transport layer Network layer Link layer 62
Network Protocols: The Internet Software Layer Message source Message destination Application layer Transport layer Network layer Link layer 62
 Network Protocols 4 Open system interconnection (OSI). 4 International standards organization (ISO). 4 TCP/IP (transmission control protocol/internet protocol). 4 UDP (user datagram protocol). 63
Network Protocols 4 Open system interconnection (OSI). 4 International standards organization (ISO). 4 TCP/IP (transmission control protocol/internet protocol). 4 UDP (user datagram protocol). 63
 Ch. 4 Algorithms 4 4 4 The concept of an algorithm. Algorithm representation. Algorithm discovery. Iterative structures. Recursive structures. Efficiency and correctness. 64
Ch. 4 Algorithms 4 4 4 The concept of an algorithm. Algorithm representation. Algorithm discovery. Iterative structures. Recursive structures. Efficiency and correctness. 64
 The Concept of an Algorithm 4 An algorithm is an ordered set of unambiguous, executable steps, defining a terminating process. 4 Parallel algorithms. 4 Program Vs. algorithm Vs. process. 65
The Concept of an Algorithm 4 An algorithm is an ordered set of unambiguous, executable steps, defining a terminating process. 4 Parallel algorithms. 4 Program Vs. algorithm Vs. process. 65
 Algorithm Representation 4 Primitive is a set of well-defined building blocks which algorithm representations can be constructed. 4 Primitive - graphical and texture. 4 Primitive => programming language. 4 Primitive - syntax and semantics. 66
Algorithm Representation 4 Primitive is a set of well-defined building blocks which algorithm representations can be constructed. 4 Primitive - graphical and texture. 4 Primitive => programming language. 4 Primitive - syntax and semantics. 66
 Algorithm Representation 4 Pseudocode - is a notational system in which ideas can be expressed informally during the algorithm development process. 4 Ex. If you have more than $10 buy a cake; otherwise buy nothing => if (cond) then (act 1) else (act 2) 4 Ex. As long as you have money, you an spend => while(having money) do (spend) 67
Algorithm Representation 4 Pseudocode - is a notational system in which ideas can be expressed informally during the algorithm development process. 4 Ex. If you have more than $10 buy a cake; otherwise buy nothing => if (cond) then (act 1) else (act 2) 4 Ex. As long as you have money, you an spend => while(having money) do (spend) 67
 Algorithm Representation 4 Ex. Assign name the value price+tax. 4 Begin a pseudocode with procedure name. 4 Ex. The pseudocode for Greetings: procedure Greetings assign Count the value 3; while Count > 0 do (print the message “Hello” and assign Count the value Count - 1) 68
Algorithm Representation 4 Ex. Assign name the value price+tax. 4 Begin a pseudocode with procedure name. 4 Ex. The pseudocode for Greetings: procedure Greetings assign Count the value 3; while Count > 0 do (print the message “Hello” and assign Count the value Count - 1) 68
 Algorithm Discovery 4 The development of a program consists of two activities - discovering the underlying algorithm and representing that algorithm as a program. 4 The basic principles for problem-solving: 4 1. Understand the problem. 4 2. Get an idea as to how an algorithmic procedure might solve the problem. 69
Algorithm Discovery 4 The development of a program consists of two activities - discovering the underlying algorithm and representing that algorithm as a program. 4 The basic principles for problem-solving: 4 1. Understand the problem. 4 2. Get an idea as to how an algorithmic procedure might solve the problem. 69
 Algorithm Discovery 4 3. Formulate the algorithm and represent it as a program. 4 4. Evaluate the program for accuracy and for its potential as a tool for solving other problems. 4 Conscious work Vs. inspiration. 4 Stepwise refinement - a top-down methodology. 70
Algorithm Discovery 4 3. Formulate the algorithm and represent it as a program. 4 4. Evaluate the program for accuracy and for its potential as a tool for solving other problems. 4 Conscious work Vs. inspiration. 4 Stepwise refinement - a top-down methodology. 70
 Iterative Structures 4 Iterative structures - a collection of instructions is repeated in a looping manner. 4 The while loop structure. 4 The repeat loop structure. 4 The insertion sort algorithm. 71
Iterative Structures 4 Iterative structures - a collection of instructions is repeated in a looping manner. 4 The while loop structure. 4 The repeat loop structure. 4 The insertion sort algorithm. 71
 Recursive Structures 4 Recursive structures provide an alternative to the loop paradigm for repetitive structures (by invoking itself). 4 The binary search algorithm. 4 The quick sort algorithm. 72
Recursive Structures 4 Recursive structures provide an alternative to the loop paradigm for repetitive structures (by invoking itself). 4 The binary search algorithm. 4 The quick sort algorithm. 72
 Efficiency and Correctness 4 You can develop a variety of algorithms to solve the same problem. However, the choice between efficient and inefficient algorithms can make the difference between a practical solution to a problem and an impractical one. 4 Time and storage complexity of the algorithm. 73
Efficiency and Correctness 4 You can develop a variety of algorithms to solve the same problem. However, the choice between efficient and inefficient algorithms can make the difference between a practical solution to a problem and an impractical one. 4 Time and storage complexity of the algorithm. 73
 Efficiency and Correctness 4 How to make sure the algorithm and program developed is correct? 4 Difference between testing and verification. 4 Precondition, assertions, loop invariant. 74
Efficiency and Correctness 4 How to make sure the algorithm and program developed is correct? 4 Difference between testing and verification. 4 Precondition, assertions, loop invariant. 74
 Ch. 5 Programming Languages 4 4 4 Historical perspective. Traditional programming concepts. Program units. Language implementation. Parallel computing. Declarative programming. 75
Ch. 5 Programming Languages 4 4 4 Historical perspective. Traditional programming concepts. Program units. Language implementation. Parallel computing. Declarative programming. 75
 Historical Perspective 4 Machine language - binary form direct controls the hardware. 4 Assembly language - mnemonic form of the machine language. 4 High-level programming language English like language. 4 Evolution? 76
Historical Perspective 4 Machine language - binary form direct controls the hardware. 4 Assembly language - mnemonic form of the machine language. 4 High-level programming language English like language. 4 Evolution? 76
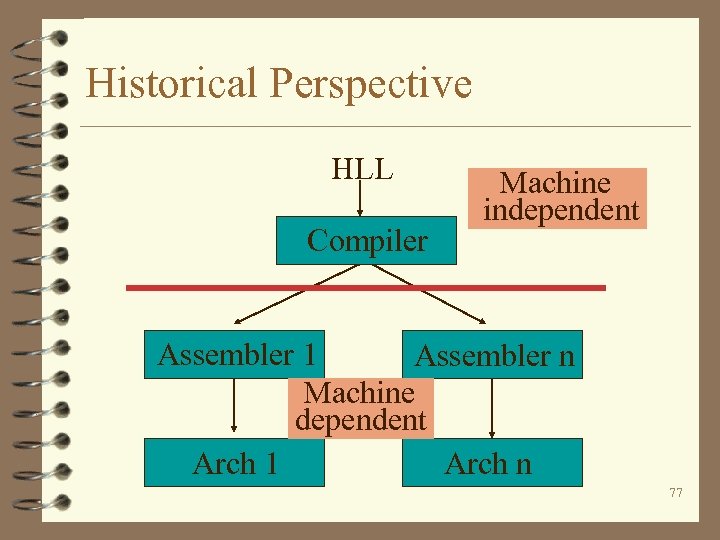 Historical Perspective HLL Compiler Machine independent Assembler 1 Assembler n Machine dependent Arch 1 Arch n 77
Historical Perspective HLL Compiler Machine independent Assembler 1 Assembler n Machine dependent Arch 1 Arch n 77
 Historical Perspective 1 st-generation - machine language. 2 nd-generation - assembly language. 3 rd-generation - machine independent. 4 th-generation - software packages that allow users to customize computer software to their applications without needing technical expertise. 4 5 th-generation - declarative (logic) programming. 78 4 4
Historical Perspective 1 st-generation - machine language. 2 nd-generation - assembly language. 3 rd-generation - machine independent. 4 th-generation - software packages that allow users to customize computer software to their applications without needing technical expertise. 4 5 th-generation - declarative (logic) programming. 78 4 4
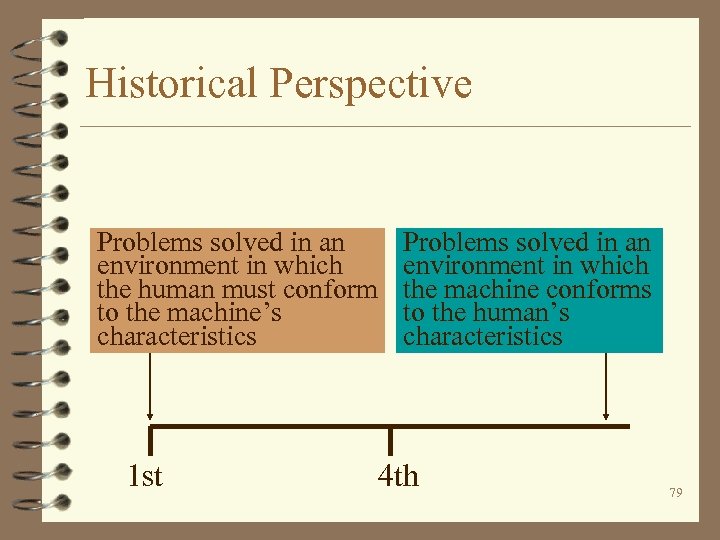 Historical Perspective Problems solved in an environment in which the human must conform to the machine’s characteristics 1 st Problems solved in an environment in which the machine conforms to the human’s characteristics 4 th 79
Historical Perspective Problems solved in an environment in which the human must conform to the machine’s characteristics 1 st Problems solved in an environment in which the machine conforms to the human’s characteristics 4 th 79
 Historical Perspective 4 Imperative paradigm - procedure paradigm, machine languages, FORTRAN, COBOL, ALGOL, BASIC, APL, C, PASCAL, ADA. 4 Functional paradigm - views the process of program development as the construction of “black boxes, ” each accepts inputs and produces outputs, LISP, ML, Scheme. 80
Historical Perspective 4 Imperative paradigm - procedure paradigm, machine languages, FORTRAN, COBOL, ALGOL, BASIC, APL, C, PASCAL, ADA. 4 Functional paradigm - views the process of program development as the construction of “black boxes, ” each accepts inputs and produces outputs, LISP, ML, Scheme. 80
 Historical Perspective 4 Object-oriented paradigm - units of data are viewed as active “objects” rather than the passive units envisioned by the imperative paradigm, SIMULA, Smalltalk, C++, Ada 95, Java. 4 Declarative paradigm - discover and implement a general problem-solving algorithm, GPSS, Prolog. 81
Historical Perspective 4 Object-oriented paradigm - units of data are viewed as active “objects” rather than the passive units envisioned by the imperative paradigm, SIMULA, Smalltalk, C++, Ada 95, Java. 4 Declarative paradigm - discover and implement a general problem-solving algorithm, GPSS, Prolog. 81
 Traditional Programming Concept 4 Statements in programming languages tend to fall into three categories: declarative statements, imperative statements, and comments. 4 Declarative statements - define customized terminology used in the program. 4 Imperative statements - describe steps in the underlying algorithm. 4 Comments. 82
Traditional Programming Concept 4 Statements in programming languages tend to fall into three categories: declarative statements, imperative statements, and comments. 4 Declarative statements - define customized terminology used in the program. 4 Imperative statements - describe steps in the underlying algorithm. 4 Comments. 82
 Traditional Programming Concept 4 4 4 Variables, constants, and literals. Data type - integer, read, Boolean, char…. . Data structure - array, queue, list, ……. . Assignment statements Control statements. Comments - internal documentation. 83
Traditional Programming Concept 4 4 4 Variables, constants, and literals. Data type - integer, read, Boolean, char…. . Data structure - array, queue, list, ……. . Assignment statements Control statements. Comments - internal documentation. 83
 Program Units 4 Breaking large programs into manageable units, units = modules, functions, objects. 4 Procedures and functions. 4 Parameter passing - formal parameters and actual parameter, call by address and call by value. 4 I/O statements. 84
Program Units 4 Breaking large programs into manageable units, units = modules, functions, objects. 4 Procedures and functions. 4 Parameter passing - formal parameters and actual parameter, call by address and call by value. 4 I/O statements. 84
 Language Implementation 4 Translation - converting a program from one language to another. 4 Translation involves three activities: 1. Lexical analysis, 2. Parsing, and 3. Code generation. 4 Lexical analysis - recognizing which strings of symbols from the source program represent a single entity. 85
Language Implementation 4 Translation - converting a program from one language to another. 4 Translation involves three activities: 1. Lexical analysis, 2. Parsing, and 3. Code generation. 4 Lexical analysis - recognizing which strings of symbols from the source program represent a single entity. 85
 Language Implementation 4 Parsing - identifying the grammatical structure of the program and recognizing the role of each component. 4 Fixed-format languages Vs. free-format languages. 4 Key words, reserved words, syntax diagram, parse tree. 4 Coercion and strongly typed. 86
Language Implementation 4 Parsing - identifying the grammatical structure of the program and recognizing the role of each component. 4 Fixed-format languages Vs. free-format languages. 4 Key words, reserved words, syntax diagram, parse tree. 4 Coercion and strongly typed. 86
 Language Implementation 4 Code generation - constructing the machine language instructions to simulate the statements recognized by the parser. 4 Code optimization. 4 Linker - links all necessary object programs to produce a complete, executable program. 4 Loader - place the program in memory for execution (what about multitasking? ) 87
Language Implementation 4 Code generation - constructing the machine language instructions to simulate the statements recognized by the parser. 4 Code optimization. 4 Linker - links all necessary object programs to produce a complete, executable program. 4 Loader - place the program in memory for execution (what about multitasking? ) 87
 Parallel Computing 4 Developing languages for describing processes that execute simultaneously. 4 Ada. 4 Linda - tuple space (a shared storage area), in which each process in the system can deposit and retrieve data bundles. 88
Parallel Computing 4 Developing languages for describing processes that execute simultaneously. 4 Ada. 4 Linda - tuple space (a shared storage area), in which each process in the system can deposit and retrieve data bundles. 88
 Declarative Programming 4 Logical deduction - resolution. 4 Resolution can be applied only to pairs of statements that appear in clause form. 4 Inconsistent - in a collection of statements, it it is impossible for all the statements to be true at the same time. 4 Prolog - a declarative programming language based on repeated resolution. 89
Declarative Programming 4 Logical deduction - resolution. 4 Resolution can be applied only to pairs of statements that appear in clause form. 4 Inconsistent - in a collection of statements, it it is impossible for all the statements to be true at the same time. 4 Prolog - a declarative programming language based on repeated resolution. 89
 Ch. 6 Software Engineering 4 4 4 The software engineering discipline. The software life cycle. Modularity. Development tools and techniques. Documentation. Software ownership and liability. 90
Ch. 6 Software Engineering 4 4 4 The software engineering discipline. The software life cycle. Modularity. Development tools and techniques. Documentation. Software ownership and liability. 90
 The Software Engineering Discipline 4 How to develop and manage a large program (>100 K lines of code) or a huge program (>1 M lines of code)? ? ? 4 What is software engineering discipline? 4 What is the quantitative system (metrics) to measure the quality and successfulness of the underlying software development? ? ? 4 Developing techniques for immediate applications and for future applications. 91
The Software Engineering Discipline 4 How to develop and manage a large program (>100 K lines of code) or a huge program (>1 M lines of code)? ? ? 4 What is software engineering discipline? 4 What is the quantitative system (metrics) to measure the quality and successfulness of the underlying software development? ? ? 4 Developing techniques for immediate applications and for future applications. 91
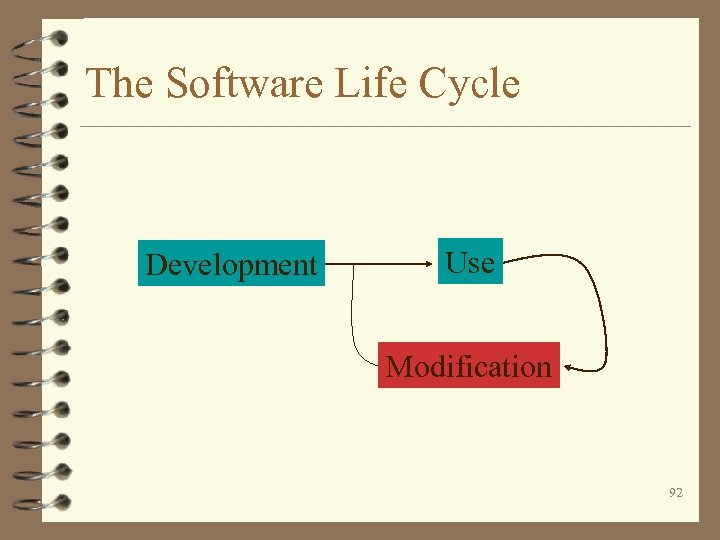 The Software Life Cycle Development Use Modification 92
The Software Life Cycle Development Use Modification 92
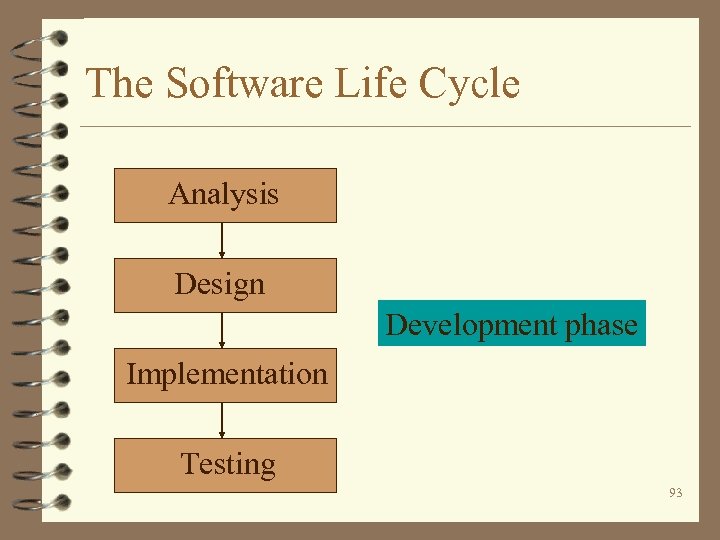 The Software Life Cycle Analysis Design Development phase Implementation Testing 93
The Software Life Cycle Analysis Design Development phase Implementation Testing 93
 The Software Life Cycle 4 Waterfall model. 4 Computer-aided software engineering (CASE). 4 Prototyping. 94
The Software Life Cycle 4 Waterfall model. 4 Computer-aided software engineering (CASE). 4 Prototyping. 94
 Modularity 4 Modular implementation - structure chart. 4 Coupling - control and data coupling. 4 Implicit coupling, global data - why is not good? Side effects! 4 Cohesion - the coupling between modules. 4 Logical cohesion and functional cohesion. 95
Modularity 4 Modular implementation - structure chart. 4 Coupling - control and data coupling. 4 Implicit coupling, global data - why is not good? Side effects! 4 Cohesion - the coupling between modules. 4 Logical cohesion and functional cohesion. 95
 Development Tools and Techniques 4 Top-down design. 4 Bottom-up design. 4 Dataflow diagrams - a pictorial representation of data paths. 4 Entity-relationship diagrams - a pictorial representation of the items of information (entities) within the system and the relationships between these pieces of information. 96
Development Tools and Techniques 4 Top-down design. 4 Bottom-up design. 4 Dataflow diagrams - a pictorial representation of data paths. 4 Entity-relationship diagrams - a pictorial representation of the items of information (entities) within the system and the relationships between these pieces of information. 96
 Development Tools and Techniques 4 Data dictionaries - a central depository of information about the data items appearing throughout the system. 4 Enhancing communication between the potential user of the system. 4 Establishing uniformity throughout the system. 97
Development Tools and Techniques 4 Data dictionaries - a central depository of information about the data items appearing throughout the system. 4 Enhancing communication between the potential user of the system. 4 Establishing uniformity throughout the system. 97
 Documentation, software Ownership and Liability 4 User documentation and system documentation. 4 Copyright and patent laws. 98
Documentation, software Ownership and Liability 4 User documentation and system documentation. 4 Copyright and patent laws. 98
 Part III: Data Organization 4 Data structures. 4 File structures. 4 Database structures. 99
Part III: Data Organization 4 Data structures. 4 File structures. 4 Database structures. 99
 Ch. 7 Data Structures 4 4 4 4 Arrays. Lists. Stacks. Queues. Trees. Customized data types. Object-oriented programming. 100
Ch. 7 Data Structures 4 4 4 4 Arrays. Lists. Stacks. Queues. Trees. Customized data types. Object-oriented programming. 100
 Arrays 4 One dimensional arrays. 4 Multidimensional arrays. 101
Arrays 4 One dimensional arrays. 4 Multidimensional arrays. 101
 Lists 4 Pointers. 4 Contiguous lists. 4 Linked lists. 102
Lists 4 Pointers. 4 Contiguous lists. 4 Linked lists. 102
 Stacks 4 Last-in first-out. 4 Push and pop. 4 Using stacks for maintaining procedure calls. 4 Other applications? ? ? 103
Stacks 4 Last-in first-out. 4 Push and pop. 4 Using stacks for maintaining procedure calls. 4 Other applications? ? ? 103
 Queues 4 4 First-in first-out. Head and tail. Circular queue. Applications? ? ? 104
Queues 4 4 First-in first-out. Head and tail. Circular queue. Applications? ? ? 104
 Trees 4 Trees - an organization chart; e. g. , family tree and company’s organization. 4 Root node, leaf nodes, arc, subtrees. 4 Parent, children, siblings. 4 Depth of a tree. 4 Tree implementation. 4 Binary tree. 4 Applications? ? ? 105
Trees 4 Trees - an organization chart; e. g. , family tree and company’s organization. 4 Root node, leaf nodes, arc, subtrees. 4 Parent, children, siblings. 4 Depth of a tree. 4 Tree implementation. 4 Binary tree. 4 Applications? ? ? 105
 Customized Data Types 4 User-defined types - allow programmers to define additional data types using the primitive types and structures as building blocks. 4 Abstract data types - encompasses both the storage system and the associated operations. 4 Encapsulation. 106
Customized Data Types 4 User-defined types - allow programmers to define additional data types using the primitive types and structures as building blocks. 4 Abstract data types - encompasses both the storage system and the associated operations. 4 Encapsulation. 106
 Object-Oriented Programming 4 Objects. 4 Methods (or member functions). 4 Class. 4 Inheritance. 107
Object-Oriented Programming 4 Objects. 4 Methods (or member functions). 4 Class. 4 Inheritance. 107
 Ch. 8 File Structures 4 Sequential files. 4 Text files. 4 Indexed files. 4 Hashed files. 4 The role of the operating system. 108
Ch. 8 File Structures 4 Sequential files. 4 Text files. 4 Indexed files. 4 Hashed files. 4 The role of the operating system. 108
 Sequential Files 4 When to use it? When all the records need to be proceeded, it makes no difference which records are proceeded first. 4 If the storage device is a tape system, we normally follow the sequential order because of the sequential nature of the tape itself. What’s about a disk system? ? ? 4 EOF and sentinel. 4 How to update a sequential file? 109
Sequential Files 4 When to use it? When all the records need to be proceeded, it makes no difference which records are proceeded first. 4 If the storage device is a tape system, we normally follow the sequential order because of the sequential nature of the tape itself. What’s about a disk system? ? ? 4 EOF and sentinel. 4 How to update a sequential file? 109
 Sequential Files 4 In PASCAL, statements read() and write() are used to retrieve and deposit information. Transaction file Old master file Merge Alg. See Figure 8. 3 New master file 110
Sequential Files 4 In PASCAL, statements read() and write() are used to retrieve and deposit information. Transaction file Old master file Merge Alg. See Figure 8. 3 New master file 110
 Text Files 4 Text file - the size of the logical records in a sequential file to a single byte (Char). 4 How to manipulate a text file? A word processor? 4 How to use text files to define an input and an output files to a program? 111
Text Files 4 Text file - the size of the logical records in a sequential file to a single byte (Char). 4 How to manipulate a text file? A word processor? 4 How to use text files to define an input and an output files to a program? 111
 Indexed Files 4 If you need to retrieve records in the file in an arbitrary order throughout the day, what is the main problem when you use a sequential file to store the records? 4 What’s the fast way to find the subject you are interesting in from a book? ? ? Ans. Using the index. 112
Indexed Files 4 If you need to retrieve records in the file in an arbitrary order throughout the day, what is the main problem when you use a sequential file to store the records? 4 What’s the fast way to find the subject you are interesting in from a book? ? ? Ans. Using the index. 112
 Indexed Files 4 An index for a file consists of a listing of the key field values occurring in the file along with the location in mass storage of the corresponding record. 4 Key field. 4 An inverted file - primary key and secondary key. 4 When records are inserted and deleted, all indexes must be updated. 113
Indexed Files 4 An index for a file consists of a listing of the key field values occurring in the file along with the location in mass storage of the corresponding record. 4 Key field. 4 An inverted file - primary key and secondary key. 4 When records are inserted and deleted, all indexes must be updated. 113
 Indexed Files 4 Index size - since the index must be moved to main memory to be searched, it must remain small enough to fit within a reasonable memory area. 4 What if the index size is too large? ? ? 4 The partial-index structure. 4 An index to the index. 114
Indexed Files 4 Index size - since the index must be moved to main memory to be searched, it must remain small enough to fit within a reasonable memory area. 4 What if the index size is too large? ? ? 4 The partial-index structure. 4 An index to the index. 114
 Hashed Files 4 Sequential files - process in a serial order. 4 Indexed files - direct access (random access). Overhead: maintaining an index table. 4 Hashed files - reduce the overhead by computing the location of a record in mass storage by applying an algorithm to the value of the key field in question. 115
Hashed Files 4 Sequential files - process in a serial order. 4 Indexed files - direct access (random access). Overhead: maintaining an index table. 4 Hashed files - reduce the overhead by computing the location of a record in mass storage by applying an algorithm to the value of the key field in question. 115
 Hashed Files 4 A particular hashing technique: 4 1. Divide the mass storage area allotted to the file into several sections called buckets. 4 2. Convert any key field value into a numeric value. 4 3. Divide any key field value stored in memory by the number of buckets. 4 4. Convert any key field value into an integer that identifies the bucket in memory. 116
Hashed Files 4 A particular hashing technique: 4 1. Divide the mass storage area allotted to the file into several sections called buckets. 4 2. Convert any key field value into a numeric value. 4 3. Divide any key field value stored in memory by the number of buckets. 4 4. Convert any key field value into an integer that identifies the bucket in memory. 116
 Hashed Files 4 What is the main concern when using hashed files? 4 Distribution problems - once we have chosen the hash algorithm, we have no control over the distribution of records in mass storage. 4 Clustering problem - majority of records are placed in the same bucket and the rest of buckets contain almost no records. 117
Hashed Files 4 What is the main concern when using hashed files? 4 Distribution problems - once we have chosen the hash algorithm, we have no control over the distribution of records in mass storage. 4 Clustering problem - majority of records are placed in the same bucket and the rest of buckets contain almost no records. 117
 Hashed Files 4 Overflow problem - unless the buckets are extremely large, overflow may occur. 4 Goal - how to select a hash algorithm that evenly distributes the records among the buckets. 4 Division method. 4 The midsquare method. 4 The extraction method. 118
Hashed Files 4 Overflow problem - unless the buckets are extremely large, overflow may occur. 4 Goal - how to select a hash algorithm that evenly distributes the records among the buckets. 4 Division method. 4 The midsquare method. 4 The extraction method. 118
 Hashed Files 4 Collision - more than one record will hash to the same bucket. 4 Assume insert records into 41 buckets: the probability of placing the 1 st record to an empty bucket is 41/41, the 2 nd is 40/41, the 3 rd is 39/41 and so on. The probability of placing 8 records into 8 empty buckets is (41/41)(40/41)(39/41)…. (34/41) =. 482 Less than 50%!!! 119
Hashed Files 4 Collision - more than one record will hash to the same bucket. 4 Assume insert records into 41 buckets: the probability of placing the 1 st record to an empty bucket is 41/41, the 2 nd is 40/41, the 3 rd is 39/41 and so on. The probability of placing 8 records into 8 empty buckets is (41/41)(40/41)(39/41)…. (34/41) =. 482 Less than 50%!!! 119
 Hashed Files 4 The high probability of collisions indicates that a hashed file should never be implemented under the assumption that clustering will never occur. 4 How to handle the overflow problem? 4 Reserve an additional area of mass storage to hold overflow records. 4 Double hashing method. 120
Hashed Files 4 The high probability of collisions indicates that a hashed file should never be implemented under the assumption that clustering will never occur. 4 How to handle the overflow problem? 4 Reserve an additional area of mass storage to hold overflow records. 4 Double hashing method. 120
 The Role of the Operating System 4 Operating systems need to manipulate files to perform designated tasks. 4 Operating systems maintains a table called a file descriptor or file control block for each file being processed. 4 In PASCAL, file descriptors can be created by assign() and reset(). 121
The Role of the Operating System 4 Operating systems need to manipulate files to perform designated tasks. 4 Operating systems maintains a table called a file descriptor or file control block for each file being processed. 4 In PASCAL, file descriptors can be created by assign() and reset(). 121
 Ch. 9 Database Structures 4 General issues. 4 The layered approach to database implementation. 4 The relational model. 4 Object-oriented databases. 4 Maintaining database integrity. 122
Ch. 9 Database Structures 4 General issues. 4 The layered approach to database implementation. 4 The relational model. 4 Object-oriented databases. 4 Maintaining database integrity. 122
 General Issues 4 A file Vs. a database organization. 4 Why needs a database system? 4 The consolidation approach - advantage: central control, disadvantage: security. 4 Database administrator (DBA). 4 Access privileges - schema and subschema. 4 Other issues - size and scope, privacy. 123
General Issues 4 A file Vs. a database organization. 4 Why needs a database system? 4 The consolidation approach - advantage: central control, disadvantage: security. 4 Database administrator (DBA). 4 Access privileges - schema and subschema. 4 Other issues - size and scope, privacy. 123
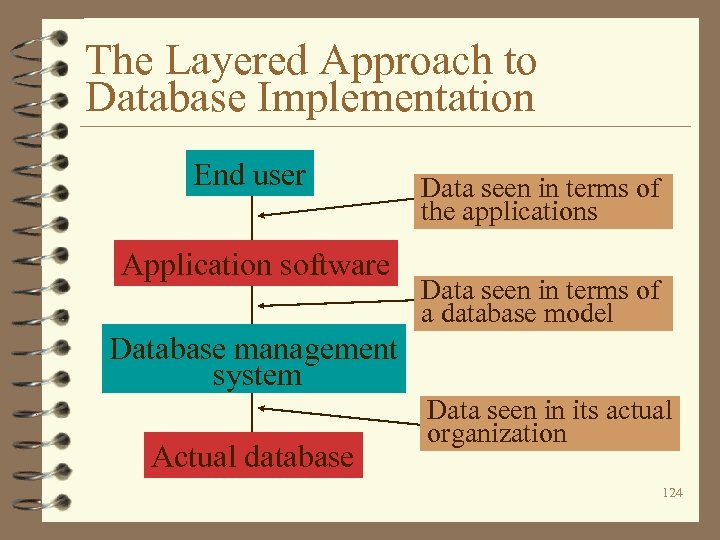 The Layered Approach to Database Implementation End user Application software Data seen in terms of the applications Data seen in terms of a database model Database management system Actual database Data seen in its actual organization 124
The Layered Approach to Database Implementation End user Application software Data seen in terms of the applications Data seen in terms of a database model Database management system Actual database Data seen in its actual organization 124
 The Layered Approach to Database Implementation 4 Database management system (DBMS). 4 The advantages of the separation of application software and the database management system: 4 1. Simplify the design process - for example the distributed database. 4 2. Providing a central controlling access to the database. 125
The Layered Approach to Database Implementation 4 Database management system (DBMS). 4 The advantages of the separation of application software and the database management system: 4 1. Simplify the design process - for example the distributed database. 4 2. Providing a central controlling access to the database. 125
 The Layered Approach to Database Implementation 4 3. Data independence - the ability to change the organization of the database itself without changing the application software. 4 4. Allows the application software to be written based on a simplified, conceptual view of the database (database model) instead of the actual complex database structure. 4 Host languages. 126
The Layered Approach to Database Implementation 4 3. Data independence - the ability to change the organization of the database itself without changing the application software. 4 4. Allows the application software to be written based on a simplified, conceptual view of the database (database model) instead of the actual complex database structure. 4 Host languages. 126
 The Relational Model 4 Relation - tuple (row) and attribute (column). 4 How to make up the database using the relations of data? 4 Extending the relation - pro and con? 4 Dividing information into various relations (nonloss decomposition) - pro and con? 127
The Relational Model 4 Relation - tuple (row) and attribute (column). 4 How to make up the database using the relations of data? 4 Extending the relation - pro and con? 4 Dividing information into various relations (nonloss decomposition) - pro and con? 127
 The Relational Model 4 Relational operations: 4 The SELECT operation. 4 The PROJECT operation. 4 The JOIN operation. 4 The SQL (Structured Query Language). 128
The Relational Model 4 Relational operations: 4 The SELECT operation. 4 The PROJECT operation. 4 The JOIN operation. 4 The SQL (Structured Query Language). 128
 Object-Oriented Databases 4 Why object-oriented databases: 4 1. Data independence can be achieved by encapsulation. 4 2. The concepts of classes and inheritance fit schemas and subschemas of databases. 4 3. Intelligent data objects that can answer questions themselves. 4 4. It may overcome some of the restrictions inherent in other database models. 129
Object-Oriented Databases 4 Why object-oriented databases: 4 1. Data independence can be achieved by encapsulation. 4 2. The concepts of classes and inheritance fit schemas and subschemas of databases. 4 3. Intelligent data objects that can answer questions themselves. 4 4. It may overcome some of the restrictions inherent in other database models. 129
 Maintaining Database Integrity Why database integrity is important? The commit/rollback protocol. Cascading roll back. Locking protocol - shared locks and exclusive locks. 4 Wound-wait protocol. 4 4 130
Maintaining Database Integrity Why database integrity is important? The commit/rollback protocol. Cascading roll back. Locking protocol - shared locks and exclusive locks. 4 Wound-wait protocol. 4 4 130
 PART IV: The Potential of Algorithmic Machines 4 Artificial Intelligence. 4 Theory of Computation. 131
PART IV: The Potential of Algorithmic Machines 4 Artificial Intelligence. 4 Theory of Computation. 131
 Ch. 10 Artificial Intelligence 4 4 4 4 Some philosophical issues. Image analysis. Reasoning. Control system activities. Using Heuristics. Artificial neural networks. Applications of AI. 132
Ch. 10 Artificial Intelligence 4 4 4 4 Some philosophical issues. Image analysis. Reasoning. Control system activities. Using Heuristics. Artificial neural networks. Applications of AI. 132
 Some Philosophical Issues 4 Machines Vs. humans. 4 Performance Vs. simulation. 4 Intelligence as an interior characteristic - Turing test and program DOCTOR (ELIZA). 4 How to create an intelligent machine? 133
Some Philosophical Issues 4 Machines Vs. humans. 4 Performance Vs. simulation. 4 Intelligence as an interior characteristic - Turing test and program DOCTOR (ELIZA). 4 How to create an intelligent machine? 133
 An Intelligent puzzle-solving machine 4 This machine takes the form of a metal box equipped with a gripper, a video camera, and a finger with a rubber end so that it does not slip when pushing something. 4 Actions: 1. Turn on the machine. 2. Place the puzzle. 3. The finger pushes the tiles back to the original order. 4. Turn off the machine. 134
An Intelligent puzzle-solving machine 4 This machine takes the form of a metal box equipped with a gripper, a video camera, and a finger with a rubber end so that it does not slip when pushing something. 4 Actions: 1. Turn on the machine. 2. Place the puzzle. 3. The finger pushes the tiles back to the original order. 4. Turn off the machine. 134
 Image Analysis 4 The first intelligent behavior required by the puzzle-solving machine is the extraction of information through a visual medium. 4 Perceive ability - determine the current status of the puzzle. 4 Optical character readers. 4 Character recognition based on matching the geometric characteristics. 135
Image Analysis 4 The first intelligent behavior required by the puzzle-solving machine is the extraction of information through a visual medium. 4 Perceive ability - determine the current status of the puzzle. 4 Optical character readers. 4 Character recognition based on matching the geometric characteristics. 135
 Reasoning 4 Is possible to develop proper programs targeted to all possible initial configurations (in total 181, 440 of them)? 4 Develop a program which can solve the problem itself - the ability to make decisions, draw conclusions, and in short, perform elementary reasoning activities. 136
Reasoning 4 Is possible to develop proper programs targeted to all possible initial configurations (in total 181, 440 of them)? 4 Develop a program which can solve the problem itself - the ability to make decisions, draw conclusions, and in short, perform elementary reasoning activities. 136
 Reasoning 4 A production system consists of three main components: 4 1. A collection of states - start/goal states. 4 2. A collection of productions (rules). 4 3. A control system - which consists of the logic that solves the problem of moving from the start state to the goal state. 4 State graph - conceptualizing all states, rules, and preconditions in a production 137 system.
Reasoning 4 A production system consists of three main components: 4 1. A collection of states - start/goal states. 4 2. A collection of productions (rules). 4 3. A control system - which consists of the logic that solves the problem of moving from the start state to the goal state. 4 State graph - conceptualizing all states, rules, and preconditions in a production 137 system.
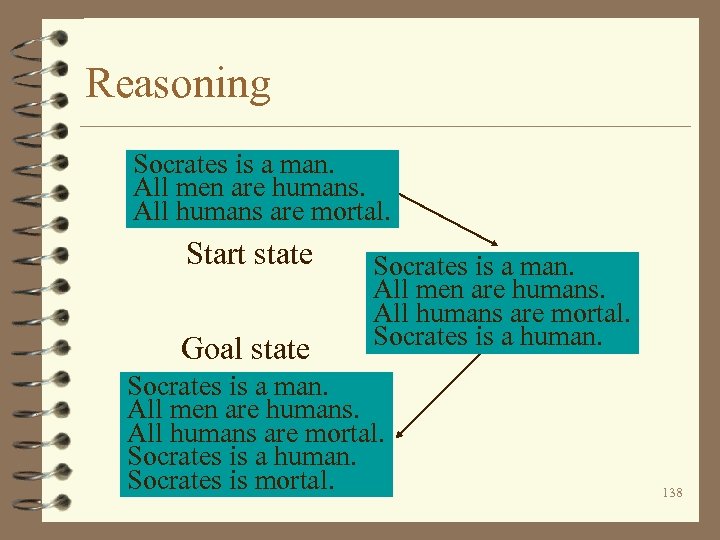 Reasoning Socrates is a man. All men are humans. All humans are mortal. Start state Goal state Socrates is a man. All men are humans. All humans are mortal. Socrates is a human. Socrates is mortal. 138
Reasoning Socrates is a man. All men are humans. All humans are mortal. Start state Goal state Socrates is a man. All men are humans. All humans are mortal. Socrates is a human. Socrates is mortal. 138
 Control System Activities A state-graph traversal problem. Search tree. How to build a search tree? It is impractical to develop a full search tree for a complex problem. 4 Using depth-first construction instead of breadth-first manner. 4 Avoiding redundancy. 4 4 139
Control System Activities A state-graph traversal problem. Search tree. How to build a search tree? It is impractical to develop a full search tree for a complex problem. 4 Using depth-first construction instead of breadth-first manner. 4 Avoiding redundancy. 4 4 139
 Using Heuristics 4 Heuristics - the use of intuition, a rule of thumb which may lead to a correct direction but offer no assurance on it. 4 How to develop a heuristic - first develop a quantitative measure by which a program can determine which of several states is considered closest to the goal (cost function). 140
Using Heuristics 4 Heuristics - the use of intuition, a rule of thumb which may lead to a correct direction but offer no assurance on it. 4 How to develop a heuristic - first develop a quantitative measure by which a program can determine which of several states is considered closest to the goal (cost function). 140
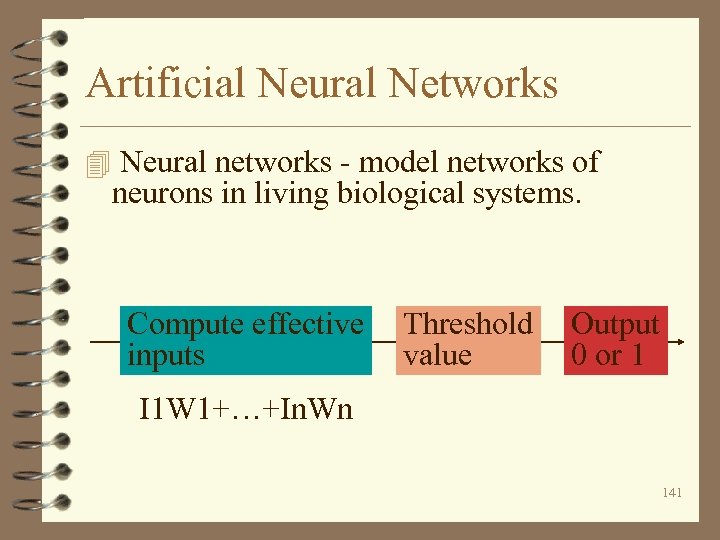 Artificial Neural Networks 4 Neural networks - model networks of neurons in living biological systems. Compute effective inputs Threshold value Output 0 or 1 I 1 W 1+…+In. Wn 141
Artificial Neural Networks 4 Neural networks - model networks of neurons in living biological systems. Compute effective inputs Threshold value Output 0 or 1 I 1 W 1+…+In. Wn 141
 Applications of Artificial Intelligence 4 Language processing. 4 Robotics. 4 Database systems. 4 Expert systems. 142
Applications of Artificial Intelligence 4 Language processing. 4 Robotics. 4 Database systems. 4 Expert systems. 142
 Ch. 11 Theory of Computation 4 A bare bones programming. 4 Turing machines. 4 Computable functions. 4 A noncomputable function. 4 Complexity and its measure. 4 Problem classification. 143
Ch. 11 Theory of Computation 4 A bare bones programming. 4 Turing machines. 4 Computable functions. 4 A noncomputable function. 4 Complexity and its measure. 4 Problem classification. 143
 A Bare Bones Programming Language 4 A universal programming language - a language encompasses the power of algorithmic processes themselves; i. e. , if a problem can be solved algorithmically, the an algorithm for solving the problem can be expressed in the language. On the other hand, if the problem can not be expressed in the language, there is no such an algorithm to solve the problem. 144
A Bare Bones Programming Language 4 A universal programming language - a language encompasses the power of algorithmic processes themselves; i. e. , if a problem can be solved algorithmically, the an algorithm for solving the problem can be expressed in the language. On the other hand, if the problem can not be expressed in the language, there is no such an algorithm to solve the problem. 144
 A Bare Bones Programming Language 4 Data description statements - all variables are considered to be of type “bit pattern of any length. ” => no need a declarative part. 4 Process description statements - three assignment statements: clear, incr, decr and one control structure: while-end. 145
A Bare Bones Programming Language 4 Data description statements - all variables are considered to be of type “bit pattern of any length. ” => no need a declarative part. 4 Process description statements - three assignment statements: clear, incr, decr and one control structure: while-end. 145
 A Bare Bones Programming Language “move tax to extra” Clear aux; clear extra; while tax not 0 do; incr aux; decr tax; end; while aux not 0 do; incr tax; incr extra; decr aux; end; 146
A Bare Bones Programming Language “move tax to extra” Clear aux; clear extra; while tax not 0 do; incr aux; decr tax; end; while aux not 0 do; incr tax; incr extra; decr aux; end; 146
 Turing Machines 4 Turing machines - are conceptual devices for studying the power of algorithmic processes. 4 A Turing machine consists of a control unit that can read and write symbols on a tape 4 The machine must be in one of a finite number of states, start/halt states. 147
Turing Machines 4 Turing machines - are conceptual devices for studying the power of algorithmic processes. 4 A Turing machine consists of a control unit that can read and write symbols on a tape 4 The machine must be in one of a finite number of states, start/halt states. 147
 Turing Machines 4 Today’s computers <=> Turing machines finite memories <=> infinite supply of tape CPU <=> the control unit bit patterns <=> states 4 The significance of Turing machines in theoretical computer science - the computation power of Turing machines is as great as any algorithmic system. 148
Turing Machines 4 Today’s computers <=> Turing machines finite memories <=> infinite supply of tape CPU <=> the control unit bit patterns <=> states 4 The significance of Turing machines in theoretical computer science - the computation power of Turing machines is as great as any algorithmic system. 148
 Computable Functions 4 How to measure computing power? 4 Goal: using Turing machines to investigate the power of the bare bones language. 4 Computing the functions is the process of determining an output of a function from its inputs. 4 If one machine is capable of computing more functions than another, the former is considered the more powerful. 149
Computable Functions 4 How to measure computing power? 4 Goal: using Turing machines to investigate the power of the bare bones language. 4 Computing the functions is the process of determining an output of a function from its inputs. 4 If one machine is capable of computing more functions than another, the former is considered the more powerful. 149
 Computable Functions 4 Ex. A system in which function outputs are predetermined and recorded in a table. 4 Ex. Finding function outputs would be to describe how to compute the output. 4 Computable - the functions whose output values can be determined algorithmically from their input values. 4 Noncomputable functions! 150
Computable Functions 4 Ex. A system in which function outputs are predetermined and recorded in a table. 4 Ex. Finding function outputs would be to describe how to compute the output. 4 Computable - the functions whose output values can be determined algorithmically from their input values. 4 Noncomputable functions! 150
 Computable Functions 4 Turing computable. 4 The Church-Turing thesis. 4 If a computational system is capable of computing all the Turing-computable functions, it is considered to be a universal system. 4 Apply the Church-Turing these to confirm that the bare bones language is a universal programming language. 151
Computable Functions 4 Turing computable. 4 The Church-Turing thesis. 4 If a computational system is capable of computing all the Turing-computable functions, it is considered to be a universal system. 4 Apply the Church-Turing these to confirm that the bare bones language is a universal programming language. 151
 A Noncomputable Function 4 Computing the Godel number. 4 The halting problem. 152
A Noncomputable Function 4 Computing the Godel number. 4 The halting problem. 152
 Complexity and Its Measure 4 Time and storage complexities (Big O). 4 Order of complexity. 4 Polynomial and nonpolynomial problems. 4 NP problems - nondeterministic polynomial problems. 4 NP-complete problems. 153
Complexity and Its Measure 4 Time and storage complexities (Big O). 4 Order of complexity. 4 Polynomial and nonpolynomial problems. 4 NP problems - nondeterministic polynomial problems. 4 NP-complete problems. 153
 Roadmap to Computer Science Study 4 Fundamental courses: Physics, Mathematics, and Introduction to Computer Science. 4 Software: 4 1. Fundamental: Problem Solving and Programming, Data Structure, Algorithm, and Software Engineering. 4 2. Language: Assembly Language, Programming Language, C, and JAVA. 154
Roadmap to Computer Science Study 4 Fundamental courses: Physics, Mathematics, and Introduction to Computer Science. 4 Software: 4 1. Fundamental: Problem Solving and Programming, Data Structure, Algorithm, and Software Engineering. 4 2. Language: Assembly Language, Programming Language, C, and JAVA. 154
 Roadmap to Computer Science Study 4 3. Theory: Formal Language and Theory of Computation. 4 4. System: Operating System, Compiler, Networking, Database, and Multimedia. 4 Hardware: 4 1. Fundamental: Electronics, Logic Design, Digital System Design, and Computer Architecture. 155
Roadmap to Computer Science Study 4 3. Theory: Formal Language and Theory of Computation. 4 4. System: Operating System, Compiler, Networking, Database, and Multimedia. 4 Hardware: 4 1. Fundamental: Electronics, Logic Design, Digital System Design, and Computer Architecture. 155
 Roadmap to Computer Science Study 4 2. System: Microprocessors and VLSI design. 4 Applications: 4 1. Consumer products. 4 2. Artificial Intelligence. 4 3. Networking. 4 4. Image Processing. 4 5. Computer Architecture and Compiler. 156
Roadmap to Computer Science Study 4 2. System: Microprocessors and VLSI design. 4 Applications: 4 1. Consumer products. 4 2. Artificial Intelligence. 4 3. Networking. 4 4. Image Processing. 4 5. Computer Architecture and Compiler. 156
 Roadmap to Computer Science Study 4 6. VLSI and Computer-Aided Design. 4 7. Biological (Medical) Computing. 4 8. Multimedia. 4 9. Databases. 4 10. Education. 4 11. Business and management. 4 12. And more!!! 157
Roadmap to Computer Science Study 4 6. VLSI and Computer-Aided Design. 4 7. Biological (Medical) Computing. 4 8. Multimedia. 4 9. Databases. 4 10. Education. 4 11. Business and management. 4 12. And more!!! 157


