45ad1c32d6bb2ddf0595a12fe3dbe90c.ppt
- Количество слайдов: 80
 Computer Networking Eliezer Dor (eliezer dor@gmail. com) Teaching Assistant: Allon Wagner Ch. 1: Introduction 1
Computer Networking Eliezer Dor (eliezer dor@gmail. com) Teaching Assistant: Allon Wagner Ch. 1: Introduction 1
 Course Information Lectures: Thursday 5 – 8 Recitation: Tuesday 16 – 17, 17 – 18 Dach 005 Dan David 001 Web site: http: //www. cs. tau. ac. il/~allonwag/comnet 2011 B/index. html Main Book: • Kurose-Ross: A Top-down Approach to Computer Networking Additional Books: 1. Keshav : An Engineering Approach to Computer Networking 2. Tanenbaum : Computer Networks 3. Bertsekas and Gallager : Data Networks Ch. 1: Introduction 2/71
Course Information Lectures: Thursday 5 – 8 Recitation: Tuesday 16 – 17, 17 – 18 Dach 005 Dan David 001 Web site: http: //www. cs. tau. ac. il/~allonwag/comnet 2011 B/index. html Main Book: • Kurose-Ross: A Top-down Approach to Computer Networking Additional Books: 1. Keshav : An Engineering Approach to Computer Networking 2. Tanenbaum : Computer Networks 3. Bertsekas and Gallager : Data Networks Ch. 1: Introduction 2/71
 Practical Information Homework assignment: Mandatory Both theoretical and programming Grades: Final Exam: theory exercises: Programming exercises: Ch. 1: Introduction 60% 20% 3/71
Practical Information Homework assignment: Mandatory Both theoretical and programming Grades: Final Exam: theory exercises: Programming exercises: Ch. 1: Introduction 60% 20% 3/71
 Chapter 1 Introduction Ch. 1: Introduction 4
Chapter 1 Introduction Ch. 1: Introduction 4
 Motivation n 1 st stage society: Agriculture, handicraft 2 nd stage society: Industrial, labor intensive Today’s society: n n automated industry with sophisticated logistics information intensive: n n business, knowledge, advertising, news, social interaction, recreation Future society is likely to be even more information-dominated Ch. 1: Introduction 5/71
Motivation n 1 st stage society: Agriculture, handicraft 2 nd stage society: Industrial, labor intensive Today’s society: n n automated industry with sophisticated logistics information intensive: n n business, knowledge, advertising, news, social interaction, recreation Future society is likely to be even more information-dominated Ch. 1: Introduction 5/71
 The Purpose of the Network serves network applications residing in hosts applications at distinct hosts need to co-ordinate actions / co-operate thus they need to communicate information to each other network must deliver that information to the right host to the right application process / thread network serves applications which serve users Ch. 1: Introduction 6/71
The Purpose of the Network serves network applications residing in hosts applications at distinct hosts need to co-ordinate actions / co-operate thus they need to communicate information to each other network must deliver that information to the right host to the right application process / thread network serves applications which serve users Ch. 1: Introduction 6/71
 Information n n A representation of knowledge Examples: n n n Can be represented in two ways n n n text, music, video, technical specifications software, instructions, reports, alarms analog (pictures / ideograms) digital (bits) the Digital Revolution n n convert information as pictures to information as bits networks move around bits instead of pictures Ch. 1: Introduction 7/71
Information n n A representation of knowledge Examples: n n n Can be represented in two ways n n n text, music, video, technical specifications software, instructions, reports, alarms analog (pictures / ideograms) digital (bits) the Digital Revolution n n convert information as pictures to information as bits networks move around bits instead of pictures Ch. 1: Introduction 7/71
 Challenges make order in the jungle of applications organize information into manageable units keep track of info units sent/ moving/ received take account of errors / misunderstandings etc. move the bits through the network u find the destination host in the network jungle u u using an efficient path learn automatically the current network topology make efficient use of link / router capacities resolve competition for use of same resource Cheaply, Securely, with Quality of Service, Ch. 1: Introduction 8/71
Challenges make order in the jungle of applications organize information into manageable units keep track of info units sent/ moving/ received take account of errors / misunderstandings etc. move the bits through the network u find the destination host in the network jungle u u using an efficient path learn automatically the current network topology make efficient use of link / router capacities resolve competition for use of same resource Cheaply, Securely, with Quality of Service, Ch. 1: Introduction 8/71
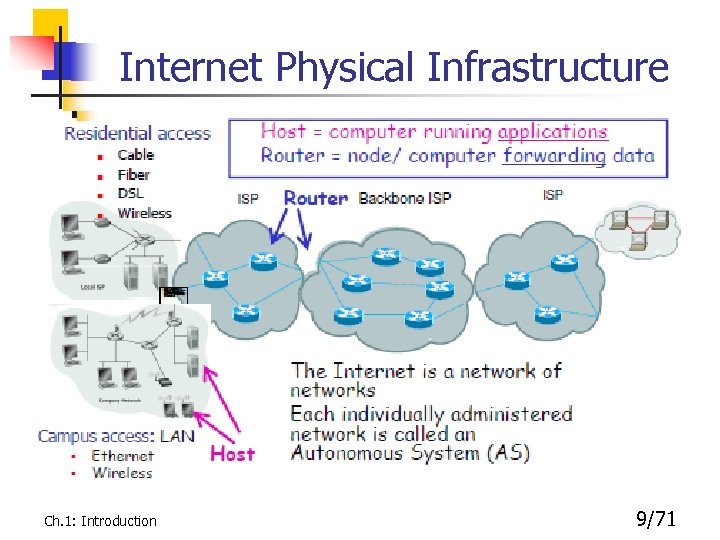 Internet Physical Infrastructure Ch. 1: Introduction 9/71
Internet Physical Infrastructure Ch. 1: Introduction 9/71
 This course’s Challenge n To discuss this complexity in an organized way, so that we n n n understand the issues / alternatives can follow/design/troubleshoot processes Need to divide the job into functional layers Understand the interrelation between them These problems are beyond a specific technology Ch. 1: Introduction 10/71
This course’s Challenge n To discuss this complexity in an organized way, so that we n n n understand the issues / alternatives can follow/design/troubleshoot processes Need to divide the job into functional layers Understand the interrelation between them These problems are beyond a specific technology Ch. 1: Introduction 10/71
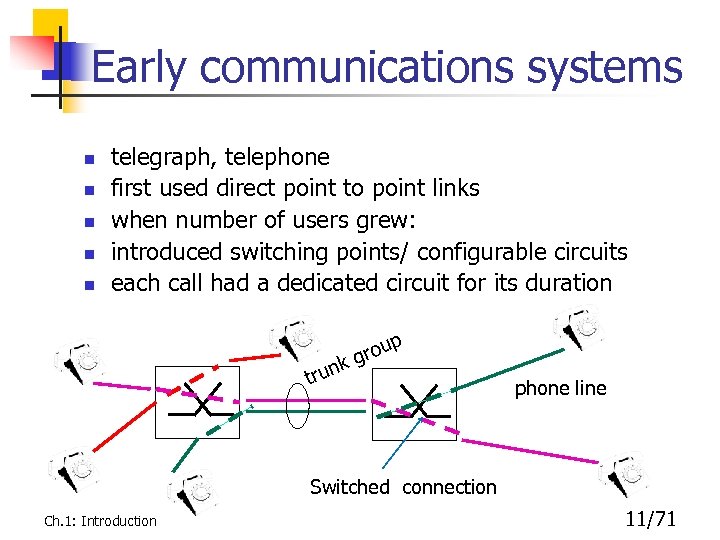 Early communications systems n n n telegraph, telephone first used direct point to point links when number of users grew: introduced switching points/ configurable circuits each call had a dedicated circuit for its duration k run t p rou g phone line Switched connection Ch. 1: Introduction 11/71
Early communications systems n n n telegraph, telephone first used direct point to point links when number of users grew: introduced switching points/ configurable circuits each call had a dedicated circuit for its duration k run t p rou g phone line Switched connection Ch. 1: Introduction 11/71
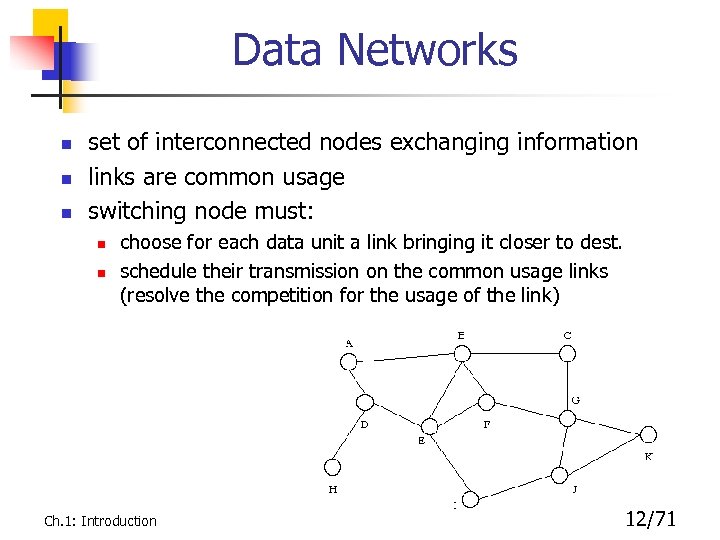 Data Networks n n n set of interconnected nodes exchanging information links are common usage switching node must: n n choose for each data unit a link bringing it closer to dest. schedule their transmission on the common usage links (resolve the competition for the usage of the link) Ch. 1: Introduction 12/71
Data Networks n n n set of interconnected nodes exchanging information links are common usage switching node must: n n choose for each data unit a link bringing it closer to dest. schedule their transmission on the common usage links (resolve the competition for the usage of the link) Ch. 1: Introduction 12/71
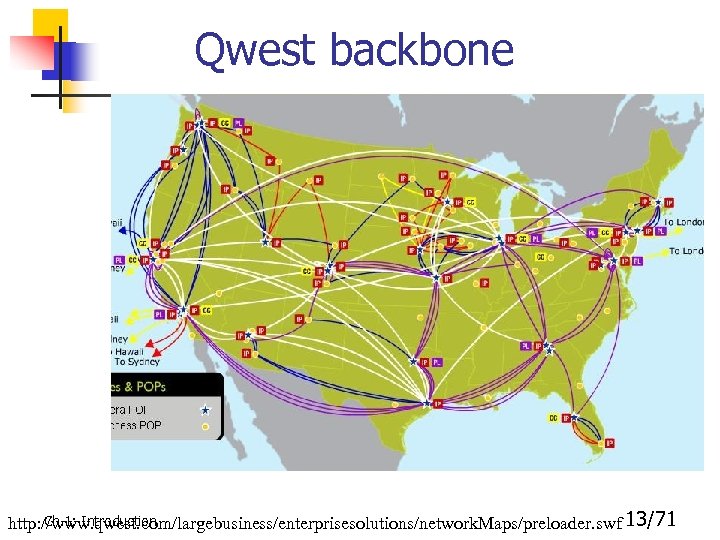 Qwest backbone Ch. 1: Introduction http: //www. qwest. com/largebusiness/enterprisesolutions/network. Maps/preloader. swf 13/71
Qwest backbone Ch. 1: Introduction http: //www. qwest. com/largebusiness/enterprisesolutions/network. Maps/preloader. swf 13/71
 Networking Tasks – phone net. sol’n Addressing - identify the end user phone number 1 -201 -222 -2673 = country code + region code + exchange + number Routing – Find route from source to destination. determined from phone number by static routing tables Forwarding – how information is moved circuit switching: : a fixed circuit along path to destination Information Units - How information is sent voice samples; no addressing attached samples sent continuously , 8000/sec network must prepare source-dest. circuit in advance Ch. 1: Introduction 14/71
Networking Tasks – phone net. sol’n Addressing - identify the end user phone number 1 -201 -222 -2673 = country code + region code + exchange + number Routing – Find route from source to destination. determined from phone number by static routing tables Forwarding – how information is moved circuit switching: : a fixed circuit along path to destination Information Units - How information is sent voice samples; no addressing attached samples sent continuously , 8000/sec network must prepare source-dest. circuit in advance Ch. 1: Introduction 14/71
 Networking Tasks – Internet Solution Addressing - identify the end user IP addresses 132. 66. 48. 37, = network number || host # Routing- How to get from source to destination routers learn automatically network topology build routing tables / updated frequently Forwarding – how information is moved packet switching: move packets 1 by 1 through routers. Information Units - How information is sent. self-descriptive packet = data + header contains destination address Ch. 1: Introduction 15/71
Networking Tasks – Internet Solution Addressing - identify the end user IP addresses 132. 66. 48. 37, = network number || host # Routing- How to get from source to destination routers learn automatically network topology build routing tables / updated frequently Forwarding – how information is moved packet switching: move packets 1 by 1 through routers. Information Units - How information is sent. self-descriptive packet = data + header contains destination address Ch. 1: Introduction 15/71
 Telephone networks support a high end-to-end quality of service, but is expensive Internet supports no quality of service but is flexible and cheap Future networks will have to support a wide range of service qualities at a reasonable cost Ch. 1: Introduction 16/71
Telephone networks support a high end-to-end quality of service, but is expensive Internet supports no quality of service but is flexible and cheap Future networks will have to support a wide range of service qualities at a reasonable cost Ch. 1: Introduction 16/71
 History 1961: 1964: 1967: 1972: Kleinrock shows effectiveness of packet-switching Baran - packet-switching concept in military networks ARPAnet – by Advanced Research Projects Agency ARPAnet demonstrated publicly (15 nodes total) first transport. email, protocols 1970: ALOHAnet satellite network in Hawaii LAN idea 1973: Metcalfe’s Ph. D thesis proposes Ethernet 1974: Cerf and Kahn - architecture for internetworking late 70’s: proprietary architectures: DECnet, SNA, XNA 1982 -5: TCP/IP, SMTP mail, DNS, FTP 1988: TCP congestion control 1991: ARPAnet commercialized: NSFnet , Internet 1989 -93: WWW, browser, http, html, URL Ch. 1: Introduction 17/71
History 1961: 1964: 1967: 1972: Kleinrock shows effectiveness of packet-switching Baran - packet-switching concept in military networks ARPAnet – by Advanced Research Projects Agency ARPAnet demonstrated publicly (15 nodes total) first transport. email, protocols 1970: ALOHAnet satellite network in Hawaii LAN idea 1973: Metcalfe’s Ph. D thesis proposes Ethernet 1974: Cerf and Kahn - architecture for internetworking late 70’s: proprietary architectures: DECnet, SNA, XNA 1982 -5: TCP/IP, SMTP mail, DNS, FTP 1988: TCP congestion control 1991: ARPAnet commercialized: NSFnet , Internet 1989 -93: WWW, browser, http, html, URL Ch. 1: Introduction 17/71
 Cerf and Kahn’s internetworking principles: n n autonomy - no internal changes required to interconnect networks best effort service model stateless routers decentralized control Defines today’s Internet architecture Ch. 1: Introduction 18/71
Cerf and Kahn’s internetworking principles: n n autonomy - no internal changes required to interconnect networks best effort service model stateless routers decentralized control Defines today’s Internet architecture Ch. 1: Introduction 18/71
 Why do we need Protocols n Communication is between applications or other S/W entities n Its objective: enable cooperation on a common task n Need protocols to understand each other n Semantics: what I report/ want of you to do n Syntax/ format: how write/ read this info Ch. 1: Introduction 19/71
Why do we need Protocols n Communication is between applications or other S/W entities n Its objective: enable cooperation on a common task n Need protocols to understand each other n Semantics: what I report/ want of you to do n Syntax/ format: how write/ read this info Ch. 1: Introduction 19/71
 Open/ Proprietary Protocols n Open protocol can be used by anyone n n n it is published by a standards organization or a public consortium e. g. draft standard Proprietary protocol is owned by a company n may be used subject to company’s agreement Ch. 1: Introduction 20/71
Open/ Proprietary Protocols n Open protocol can be used by anyone n n n it is published by a standards organization or a public consortium e. g. draft standard Proprietary protocol is owned by a company n may be used subject to company’s agreement Ch. 1: Introduction 20/71
 Why do we need Standards n Communication happens between entities n n n Hosts (personal computers, servers) Routers H/W entities produced by different vendors S/W applications/ OS entities also Need agreement to ensure correct, efficient and meaningful communication n this is called Interworking Ch. 1: Introduction 21/71
Why do we need Standards n Communication happens between entities n n n Hosts (personal computers, servers) Routers H/W entities produced by different vendors S/W applications/ OS entities also Need agreement to ensure correct, efficient and meaningful communication n this is called Interworking Ch. 1: Introduction 21/71
 Organizations that Issue Standards n IETF (Internet Engineering Task Force) n IEEE (Institute for Electrical and Electronic Engineers) n ITU (International Telecommunications Union) n ISO (International Organization for Standardization) n W 3 C (World Wide Web Consortium) Ch. 1: Introduction 22/71
Organizations that Issue Standards n IETF (Internet Engineering Task Force) n IEEE (Institute for Electrical and Electronic Engineers) n ITU (International Telecommunications Union) n ISO (International Organization for Standardization) n W 3 C (World Wide Web Consortium) Ch. 1: Introduction 22/71
 Why Layering n n n Communication is a very complex task What we need is: communication btw applications at distant hosts What is reasonably feasible in one piece is: the ability to transfer a series of bits over a link We need to bridge between very sophisticated applications and very primitive physical layer What is needed is to divide the task’s functionality into well chosen parts n n each part should be reasonably ‘easy’ to do they should work well together Ch. 1: Introduction 23/71
Why Layering n n n Communication is a very complex task What we need is: communication btw applications at distant hosts What is reasonably feasible in one piece is: the ability to transfer a series of bits over a link We need to bridge between very sophisticated applications and very primitive physical layer What is needed is to divide the task’s functionality into well chosen parts n n each part should be reasonably ‘easy’ to do they should work well together Ch. 1: Introduction 23/71
 How to do Layering n Define a conceptual Layering Model n n Set principles for proper usage of the model Build protocols for each layer n n n means: what is the function of each layer how they cooperate / use each other’s services protocol is between same layer entities @ distinct nodes there may be several protocols in each layer providing different type service for the layer’s function Define interfaces between layers n interface (here) is between distinct layer entities at same node (computing device) Ch. 1: Introduction 24/71
How to do Layering n Define a conceptual Layering Model n n Set principles for proper usage of the model Build protocols for each layer n n n means: what is the function of each layer how they cooperate / use each other’s services protocol is between same layer entities @ distinct nodes there may be several protocols in each layer providing different type service for the layer’s function Define interfaces between layers n interface (here) is between distinct layer entities at same node (computing device) Ch. 1: Introduction 24/71
 Layering Principles Modularity n each layer works independently of the others n n n this means: n n information exchange only according to Interfaces defined in the Model analogous to the Object Oriented principle in S/W eng. don’t change/peek into internal variables of other layers modularity is bypassed very seldom n only when there is no other solution to a problem Transparency n layering should be invisible to user Ch. 1: Introduction 25/71
Layering Principles Modularity n each layer works independently of the others n n n this means: n n information exchange only according to Interfaces defined in the Model analogous to the Object Oriented principle in S/W eng. don’t change/peek into internal variables of other layers modularity is bypassed very seldom n only when there is no other solution to a problem Transparency n layering should be invisible to user Ch. 1: Introduction 25/71
 Layering Benefits Layering enables: n discussion/understanding of the issues n n n efficient development of protocols n n n enables clear visualizing of relationships btw. functions it’s impossible to think about all layers @ once each layer has a different functional focus no need to think other layers when designing it easy replacement/maintenance of protocols n as long as modularity & interfaces are adhered to Layering is a good reference model for discussion Ch. 1: Introduction 26/71
Layering Benefits Layering enables: n discussion/understanding of the issues n n n efficient development of protocols n n n enables clear visualizing of relationships btw. functions it’s impossible to think about all layers @ once each layer has a different functional focus no need to think other layers when designing it easy replacement/maintenance of protocols n as long as modularity & interfaces are adhered to Layering is a good reference model for discussion Ch. 1: Introduction 26/71
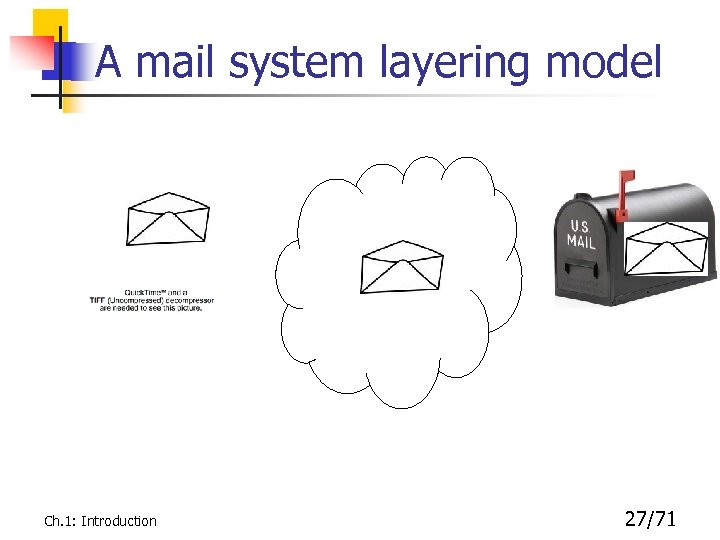 A mail system layering model Ch. 1: Introduction 27/71
A mail system layering model Ch. 1: Introduction 27/71
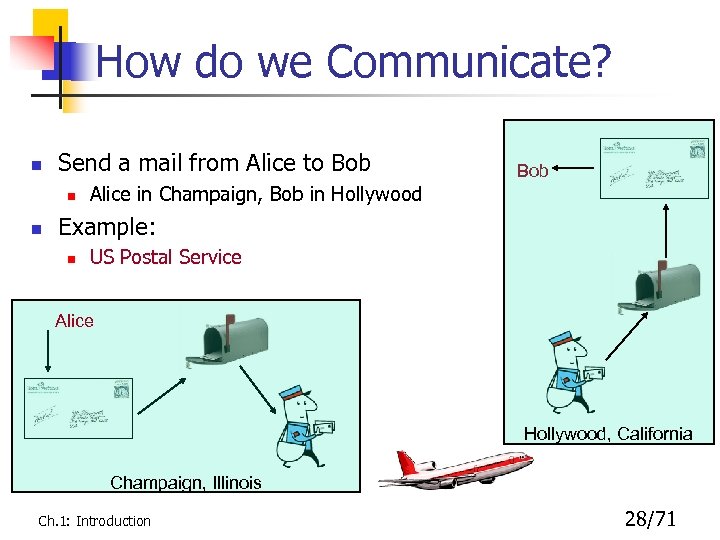 How do we Communicate? n Send a mail from Alice to Bob n n Bob Alice in Champaign, Bob in Hollywood Example: n US Postal Service Alice Hollywood, California Champaign, Illinois Ch. 1: Introduction 28/71
How do we Communicate? n Send a mail from Alice to Bob n n Bob Alice in Champaign, Bob in Hollywood Example: n US Postal Service Alice Hollywood, California Champaign, Illinois Ch. 1: Introduction 28/71
 What does Alice do? Alice 200 Cornfield Rd. Champaign, IL 61820 Bob 100 Santa Monica Blvd. Hollywood, CA 90028 n n Bob’s address (his mailbox) Bob’s name – in case people share mailbox Postage – have to pay! Alice’s own name and address n n in case Bob wants to return a message In case the mail has to be returned. Ch. 1: Introduction 29/71
What does Alice do? Alice 200 Cornfield Rd. Champaign, IL 61820 Bob 100 Santa Monica Blvd. Hollywood, CA 90028 n n Bob’s address (his mailbox) Bob’s name – in case people share mailbox Postage – have to pay! Alice’s own name and address n n in case Bob wants to return a message In case the mail has to be returned. Ch. 1: Introduction 29/71
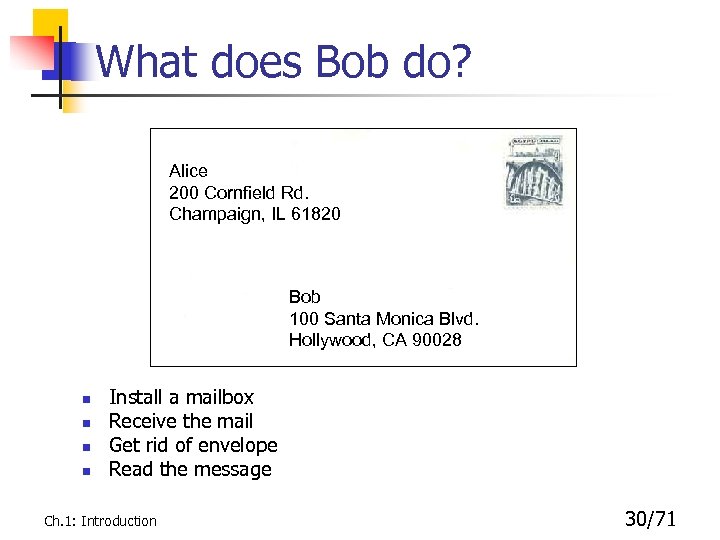 What does Bob do? Alice 200 Cornfield Rd. Champaign, IL 61820 Bob 100 Santa Monica Blvd. Hollywood, CA 90028 n n Install a mailbox Receive the mail Get rid of envelope Read the message Ch. 1: Introduction 30/71
What does Bob do? Alice 200 Cornfield Rd. Champaign, IL 61820 Bob 100 Santa Monica Blvd. Hollywood, CA 90028 n n Install a mailbox Receive the mail Get rid of envelope Read the message Ch. 1: Introduction 30/71
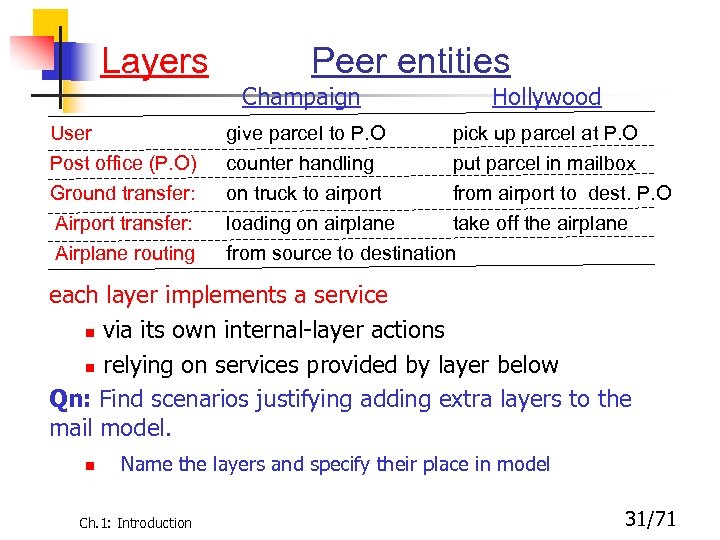 Layers Peer entities Champaign Hollywood User Post office (P. O) give parcel to P. O counter handling pick up parcel at P. O put parcel in mailbox Ground transfer: Airport transfer: Airplane routing on truck to airport from airport to dest. P. O loading on airplane take off the airplane from source to destination each layer implements a service n via its own internal-layer actions n relying on services provided by layer below Qn: Find scenarios justifying adding extra layers to the mail model. n Name the layers and specify their place in model Ch. 1: Introduction 31/71
Layers Peer entities Champaign Hollywood User Post office (P. O) give parcel to P. O counter handling pick up parcel at P. O put parcel in mailbox Ground transfer: Airport transfer: Airplane routing on truck to airport from airport to dest. P. O loading on airplane take off the airplane from source to destination each layer implements a service n via its own internal-layer actions n relying on services provided by layer below Qn: Find scenarios justifying adding extra layers to the mail model. n Name the layers and specify their place in model Ch. 1: Introduction 31/71
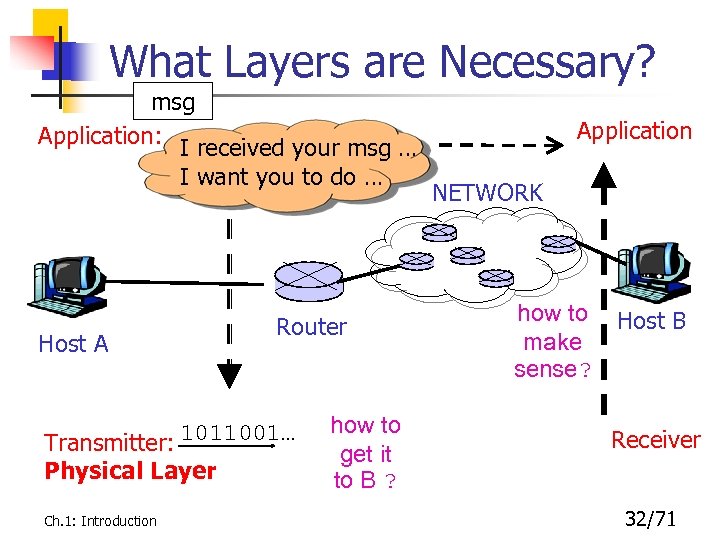 What Layers are Necessary? msg Application: I received your msg … I want you to do … Host A Router Transmitter: 1011001… Physical Layer Ch. 1: Introduction how to get it to B ? Application NETWORK how to make sense? Host B Receiver 32/71
What Layers are Necessary? msg Application: I received your msg … I want you to do … Host A Router Transmitter: 1011001… Physical Layer Ch. 1: Introduction how to get it to B ? Application NETWORK how to make sense? Host B Receiver 32/71
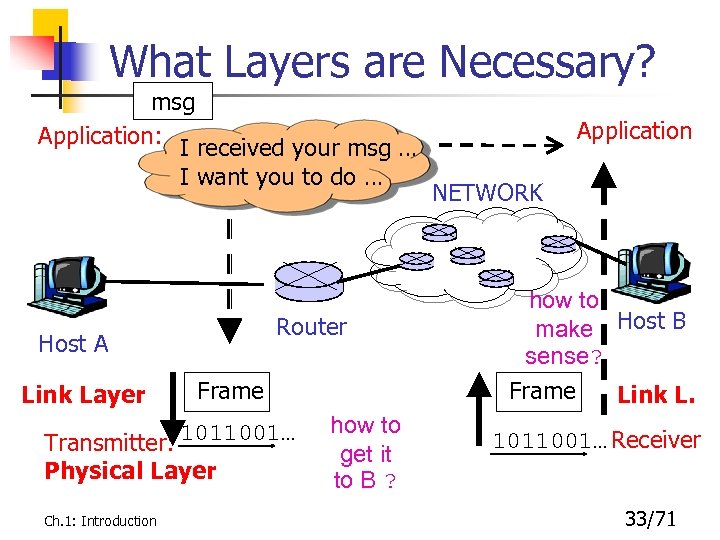 What Layers are Necessary? msg Application: I received your msg … I want you to do … Router Host A Link Layer Frame Transmitter: 1011001… Physical Layer Ch. 1: Introduction how to get it to B ? Application NETWORK how to make Host B sense? Frame Link L. 1011001… Receiver 33/71
What Layers are Necessary? msg Application: I received your msg … I want you to do … Router Host A Link Layer Frame Transmitter: 1011001… Physical Layer Ch. 1: Introduction how to get it to B ? Application NETWORK how to make Host B sense? Frame Link L. 1011001… Receiver 33/71
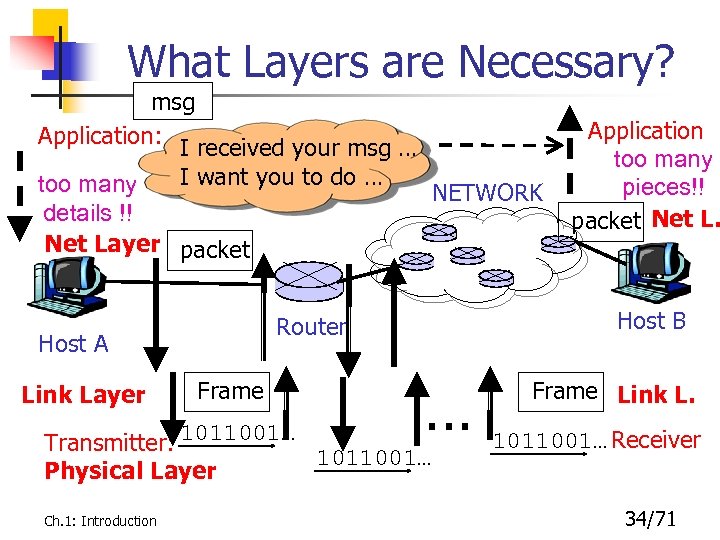 What Layers are Necessary? msg Application: I received your msg … I want you to do … too many NETWORK details !! Net Layer packet Link Layer Frame Transmitter: 1011001… Physical Layer Ch. 1: Introduction Host B Router Host A Application too many pieces!! packet Net L. … 1011001… Frame Link L. 1011001… Receiver 34/71
What Layers are Necessary? msg Application: I received your msg … I want you to do … too many NETWORK details !! Net Layer packet Link Layer Frame Transmitter: 1011001… Physical Layer Ch. 1: Introduction Host B Router Host A Application too many pieces!! packet Net L. … 1011001… Frame Link L. 1011001… Receiver 34/71
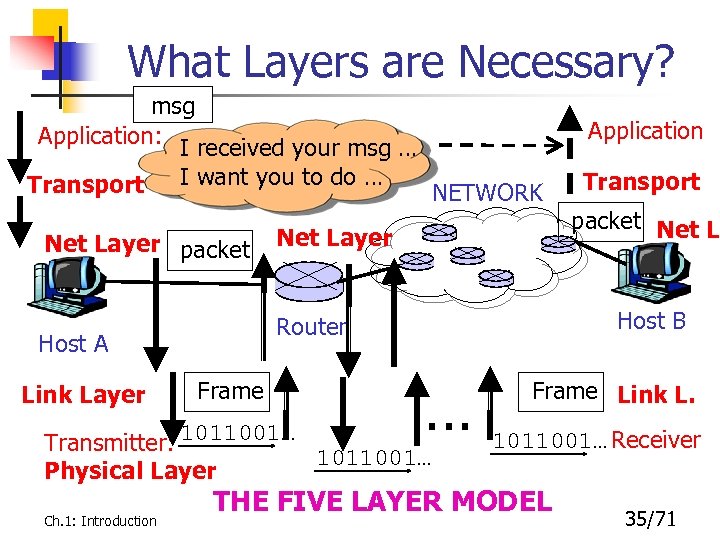 What Layers are Necessary? msg Application: I received your msg … Transport I want you to do … Net Layer packet Net Layer Frame Transmitter: 1011001… Physical Layer Ch. 1: Introduction NETWORK Transport packet Net L. Host B Router Host A Link Layer Application … 1011001… Frame Link L. 1011001… Receiver THE FIVE LAYER MODEL 35/71
What Layers are Necessary? msg Application: I received your msg … Transport I want you to do … Net Layer packet Net Layer Frame Transmitter: 1011001… Physical Layer Ch. 1: Introduction NETWORK Transport packet Net L. Host B Router Host A Link Layer Application … 1011001… Frame Link L. 1011001… Receiver THE FIVE LAYER MODEL 35/71
 Application Layer n Tasks: n write messages serving needs of application n n n n L 5 proper type of semantics (meaning, information) appropriate syntax/format, so that semantics is understood keep track of the interaction process / state machine Focus: on needs of a specific application type Data unit: Message Peer: the Application Layer at destination host Uses: the Transport Layer Used by: the application itself Run by: the application Ch. 1: Introduction 36/71
Application Layer n Tasks: n write messages serving needs of application n n n n L 5 proper type of semantics (meaning, information) appropriate syntax/format, so that semantics is understood keep track of the interaction process / state machine Focus: on needs of a specific application type Data unit: Message Peer: the Application Layer at destination host Uses: the Transport Layer Used by: the application itself Run by: the application Ch. 1: Introduction 36/71
 Transport Layer n Main Tasks: n prepare data for transfer n n n n n L 4 fragment data into proper size segments / reassemble at dest. add header which enables delivery to the correct appl. process optional: error- /flow- /congestion-control Data Unit: Segment Focus: on control of End-to-End data transfer Peer: the Transport Layer at destination host Uses: the Network Layer Used by: the Application Layer Run by: the OS of the host Ch. 1: Introduction 37/71
Transport Layer n Main Tasks: n prepare data for transfer n n n n n L 4 fragment data into proper size segments / reassemble at dest. add header which enables delivery to the correct appl. process optional: error- /flow- /congestion-control Data Unit: Segment Focus: on control of End-to-End data transfer Peer: the Transport Layer at destination host Uses: the Network Layer Used by: the Application Layer Run by: the OS of the host Ch. 1: Introduction 37/71
 Network Layer n Main Tasks: n n n n n L 3 learn network topology in real time prepare routing tables for fast usage in forwarding data network layer (WAN) addressing forward data from source to destination Data Unit: Datagram / “packet” Focus: on network and data fowarding Peers: the Network Layer along the whole path Uses: the Link Layer Used by: the Transport Layer Run by: the OS of the host, the router S/W Ch. 1: Introduction 38/71
Network Layer n Main Tasks: n n n n n L 3 learn network topology in real time prepare routing tables for fast usage in forwarding data network layer (WAN) addressing forward data from source to destination Data Unit: Datagram / “packet” Focus: on network and data fowarding Peers: the Network Layer along the whole path Uses: the Link Layer Used by: the Transport Layer Run by: the OS of the host, the router S/W Ch. 1: Introduction 38/71
 Link Layer n Main Tasks: n insert delimiters so start/end of frame can be known n n n n L 2 physical layer may transfer an endless stream of bits this is part of the task of the Link header and Link trailer in LAN, access control/ link layer addressing Data Unit: Frame Focus: data transfer over a link Peer: Link Layer at the other end of the link Uses: the Physical Layer Used by: the Network Layer Run by: the NIC (Network interface card, )כרטיס רשת Ch. 1: Introduction 39/71
Link Layer n Main Tasks: n insert delimiters so start/end of frame can be known n n n n L 2 physical layer may transfer an endless stream of bits this is part of the task of the Link header and Link trailer in LAN, access control/ link layer addressing Data Unit: Frame Focus: data transfer over a link Peer: Link Layer at the other end of the link Uses: the Physical Layer Used by: the Network Layer Run by: the NIC (Network interface card, )כרטיס רשת Ch. 1: Introduction 39/71
 Physical Layer n Main Tasks: n n n n n L 1 transmit signals that encode bits 1 and 0 receive such signals and decode bits from them synchronize the bit rate clocks of the peer nodes Data Unit: Bit Focus: bit transfer over a link Peer: the Physical Layer @ other end of the link Uses: the raw media: cable/ space Used by: the Link Layer Run by: transmitter/ receiver /wave propagation Ch. 1: Introduction 40/71
Physical Layer n Main Tasks: n n n n n L 1 transmit signals that encode bits 1 and 0 receive such signals and decode bits from them synchronize the bit rate clocks of the peer nodes Data Unit: Bit Focus: bit transfer over a link Peer: the Physical Layer @ other end of the link Uses: the raw media: cable/ space Used by: the Link Layer Run by: transmitter/ receiver /wave propagation Ch. 1: Introduction 40/71
 Protocols n A protocol is a set of rules and formats that govern the communication between communicating peers n n n set of valid message formats - syntax meaning of each message - semantics Necessary for any function that requires cooperation between peers Ch. 1: Introduction 41/71
Protocols n A protocol is a set of rules and formats that govern the communication between communicating peers n n n set of valid message formats - syntax meaning of each message - semantics Necessary for any function that requires cooperation between peers Ch. 1: Introduction 41/71
 Protocols n A protocol provides a service n n Peer entities use a protocol to provide a service to a higher-level peer entity n n For example: the post office “registered” protocol for reliable parcel transfer service for example, truck drivers use a protocol to present post offices with the abstraction of an unreliable parcel transfer service In the layering model: n each layer gives service to next higher layer Ch. 1: Introduction 42/71
Protocols n A protocol provides a service n n Peer entities use a protocol to provide a service to a higher-level peer entity n n For example: the post office “registered” protocol for reliable parcel transfer service for example, truck drivers use a protocol to present post offices with the abstraction of an unreliable parcel transfer service In the layering model: n each layer gives service to next higher layer Ch. 1: Introduction 42/71
 ISO OSI reference model n Reference model n n Service architecture n n formally defines what is meant by a layer, a service etc. describes the services provided by each layer and the service access point Protocol architecture n n set of protocols that implement the service architecture compliant service architectures may still use noncompliant protocol architectures Ch. 1: Introduction 43/71
ISO OSI reference model n Reference model n n Service architecture n n formally defines what is meant by a layer, a service etc. describes the services provided by each layer and the service access point Protocol architecture n n set of protocols that implement the service architecture compliant service architectures may still use noncompliant protocol architectures Ch. 1: Introduction 43/71
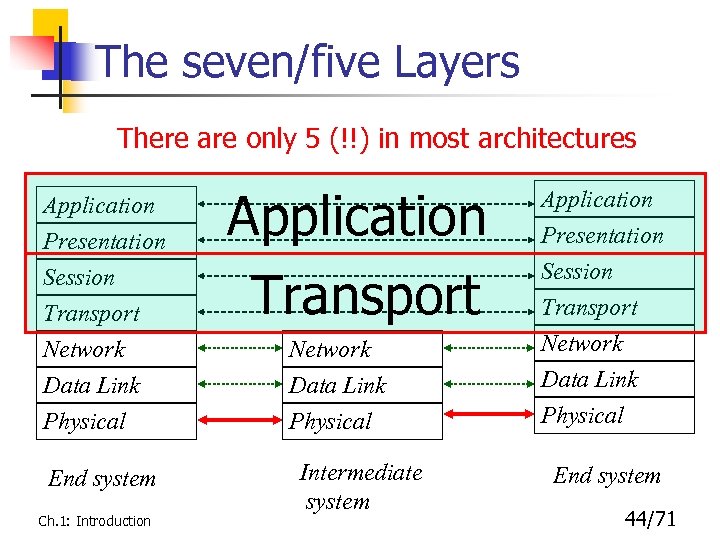 The seven/five Layers There are only 5 (!!) in most architectures Application Presentation Session Transport Network Data Link Physical Application Transport End system Intermediate system Ch. 1: Introduction Network Data Link Physical Application Presentation Session Transport Network Data Link Physical End system 44/71
The seven/five Layers There are only 5 (!!) in most architectures Application Presentation Session Transport Network Data Link Physical Application Transport End system Intermediate system Ch. 1: Introduction Network Data Link Physical Application Presentation Session Transport Network Data Link Physical End system 44/71
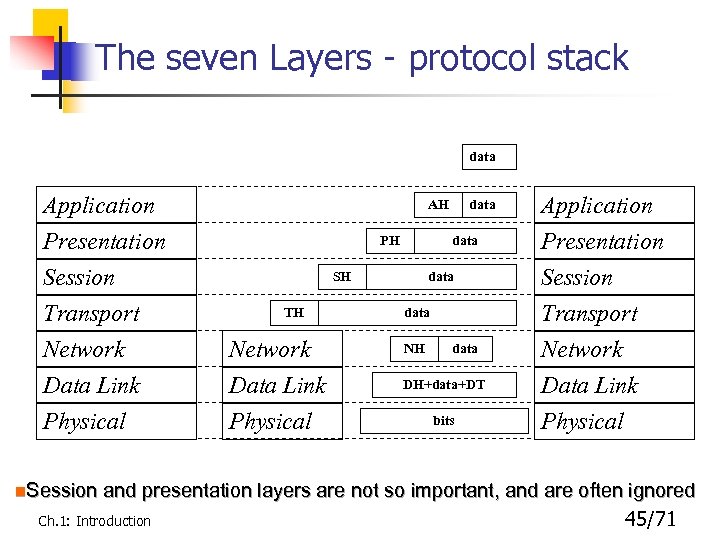 The seven Layers - protocol stack data Application Presentation Session Transport Network Data Link Physical n. Session AH PH data SH TH Network Data Link Physical data NH data DH+data+DT bits Application Presentation Session Transport Network Data Link Physical and presentation layers are not so important, and are often ignored Ch. 1: Introduction 45/71
The seven Layers - protocol stack data Application Presentation Session Transport Network Data Link Physical n. Session AH PH data SH TH Network Data Link Physical data NH data DH+data+DT bits Application Presentation Session Transport Network Data Link Physical and presentation layers are not so important, and are often ignored Ch. 1: Introduction 45/71
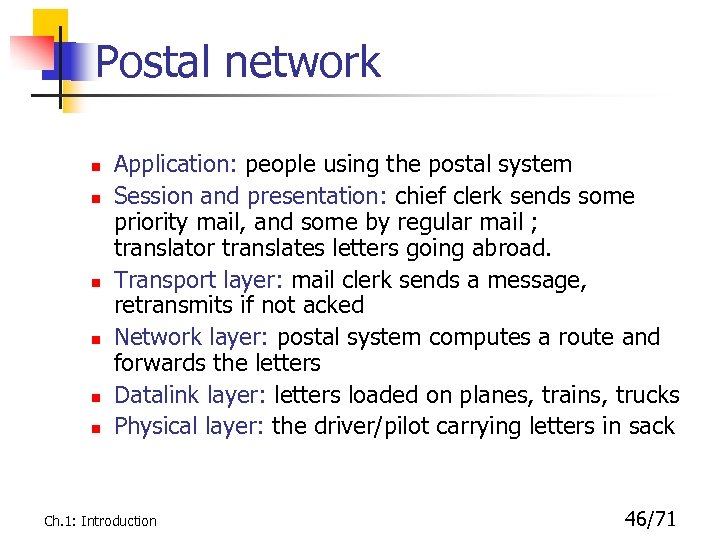 Postal network n n n Application: people using the postal system Session and presentation: chief clerk sends some priority mail, and some by regular mail ; translator translates letters going abroad. Transport layer: mail clerk sends a message, retransmits if not acked Network layer: postal system computes a route and forwards the letters Datalink layer: letters loaded on planes, trains, trucks Physical layer: the driver/pilot carrying letters in sack Ch. 1: Introduction 46/71
Postal network n n n Application: people using the postal system Session and presentation: chief clerk sends some priority mail, and some by regular mail ; translator translates letters going abroad. Transport layer: mail clerk sends a message, retransmits if not acked Network layer: postal system computes a route and forwards the letters Datalink layer: letters loaded on planes, trains, trucks Physical layer: the driver/pilot carrying letters in sack Ch. 1: Introduction 46/71
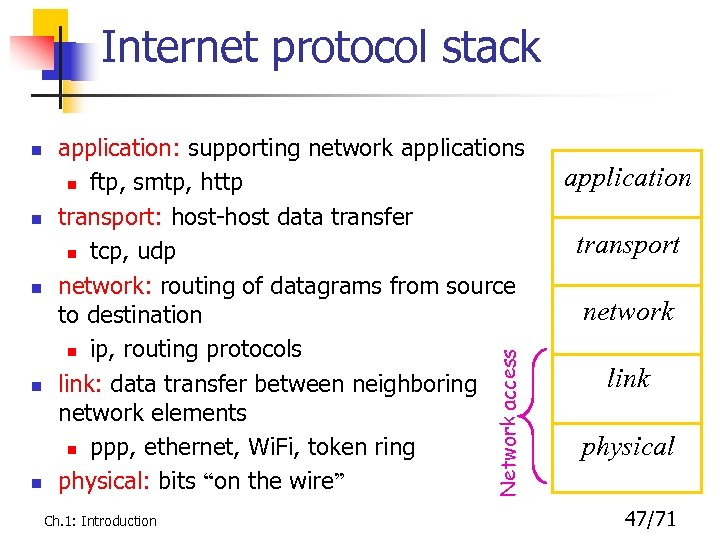 Internet protocol stack n n application: supporting network applications n ftp, smtp, http transport: host-host data transfer n tcp, udp network: routing of datagrams from source to destination n ip, routing protocols link: data transfer between neighboring network elements n ppp, ethernet, Wi. Fi, token ring physical: bits “on the wire” Network access n Ch. 1: Introduction application transport network link physical 47/71
Internet protocol stack n n application: supporting network applications n ftp, smtp, http transport: host-host data transfer n tcp, udp network: routing of datagrams from source to destination n ip, routing protocols link: data transfer between neighboring network elements n ppp, ethernet, Wi. Fi, token ring physical: bits “on the wire” Network access n Ch. 1: Introduction application transport network link physical 47/71
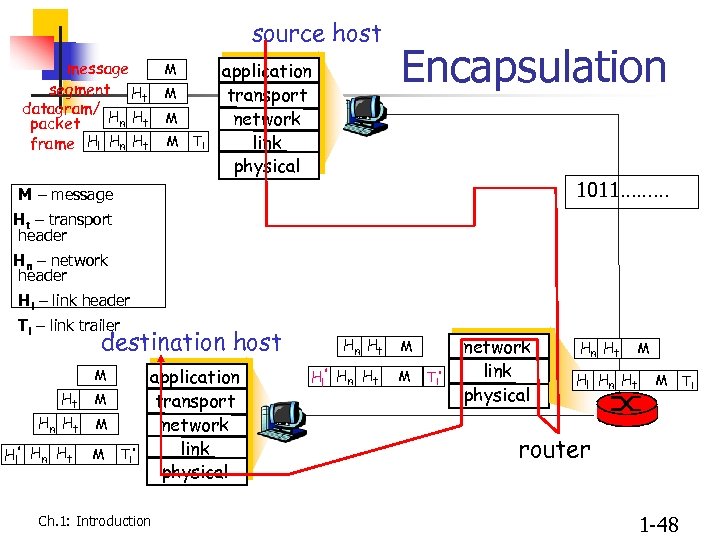 source host message M segment Ht M datagram/ H H n t M packet frame Hl Hn Ht M Tl application transport network link physical Encapsulation 1011……… M – message Ht – transport header Hn – network header Hl – link header Tl – link trailer destination host M Hn Ht M Hl ’ Hn Ht M Tl’ application transport network link physical Ch. 1: Introduction Hn Ht Hl ’ Hn Ht M M Tl’ network link physical Hn Ht M Hl Hn Ht M router 1 -48 Tl
source host message M segment Ht M datagram/ H H n t M packet frame Hl Hn Ht M Tl application transport network link physical Encapsulation 1011……… M – message Ht – transport header Hn – network header Hl – link header Tl – link trailer destination host M Hn Ht M Hl ’ Hn Ht M Tl’ application transport network link physical Ch. 1: Introduction Hn Ht Hl ’ Hn Ht M M Tl’ network link physical Hn Ht M Hl Hn Ht M router 1 -48 Tl
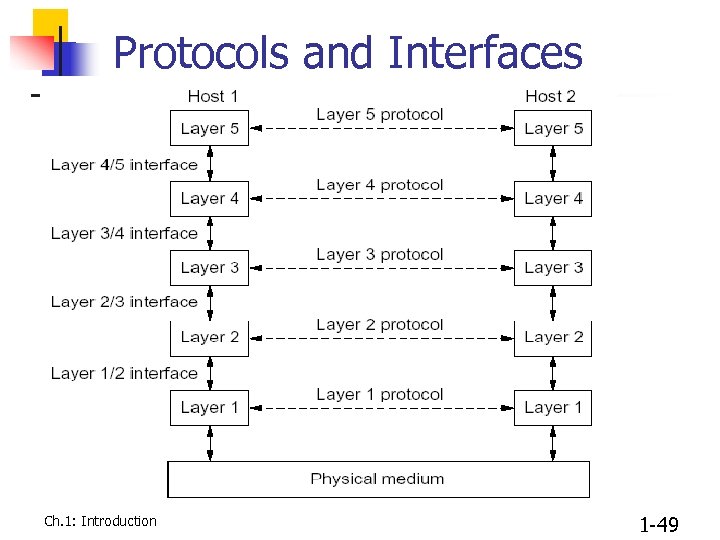 Protocols and Interfaces Ch. 1: Introduction 1 -49
Protocols and Interfaces Ch. 1: Introduction 1 -49
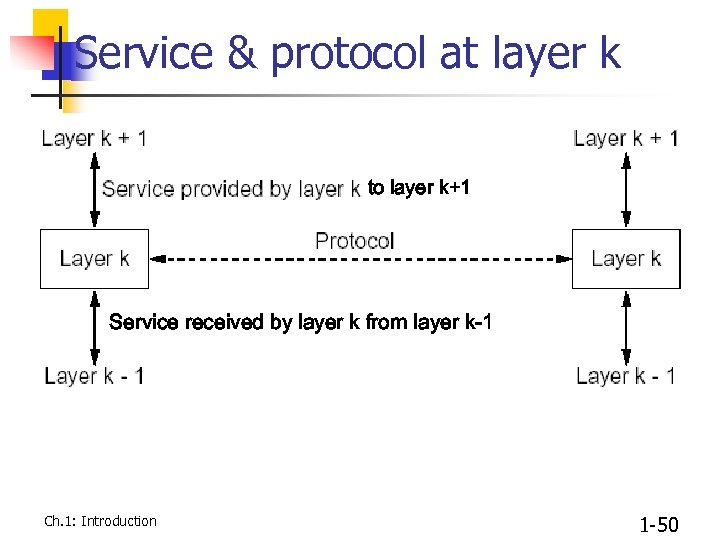 Service & protocol at layer k to layer k+1 Service received by layer k from layer k-1 Ch. 1: Introduction 1 -50
Service & protocol at layer k to layer k+1 Service received by layer k from layer k-1 Ch. 1: Introduction 1 -50
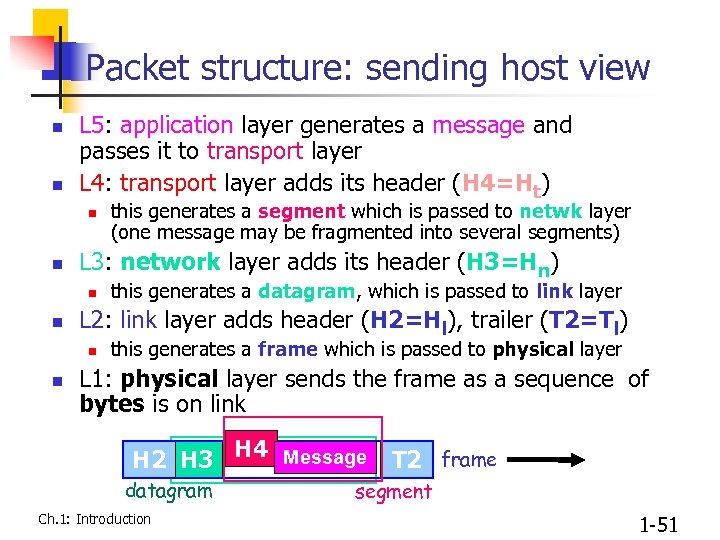 Packet structure: sending host view n n L 5: application layer generates a message and passes it to transport layer L 4: transport layer adds its header (H 4=Ht) n n L 3: network layer adds its header (H 3=Hn) n n this generates a datagram, which is passed to link layer L 2: link layer adds header (H 2=Hl), trailer (T 2=Tl) n n this generates a segment which is passed to netwk layer (one message may be fragmented into several segments) this generates a frame which is passed to physical layer L 1: physical layer sends the frame as a sequence of bytes is on link H 2 H 3 H 4 Message T 2 frame datagram Ch. 1: Introduction segment 1 -51
Packet structure: sending host view n n L 5: application layer generates a message and passes it to transport layer L 4: transport layer adds its header (H 4=Ht) n n L 3: network layer adds its header (H 3=Hn) n n this generates a datagram, which is passed to link layer L 2: link layer adds header (H 2=Hl), trailer (T 2=Tl) n n this generates a segment which is passed to netwk layer (one message may be fragmented into several segments) this generates a frame which is passed to physical layer L 1: physical layer sends the frame as a sequence of bytes is on link H 2 H 3 H 4 Message T 2 frame datagram Ch. 1: Introduction segment 1 -51
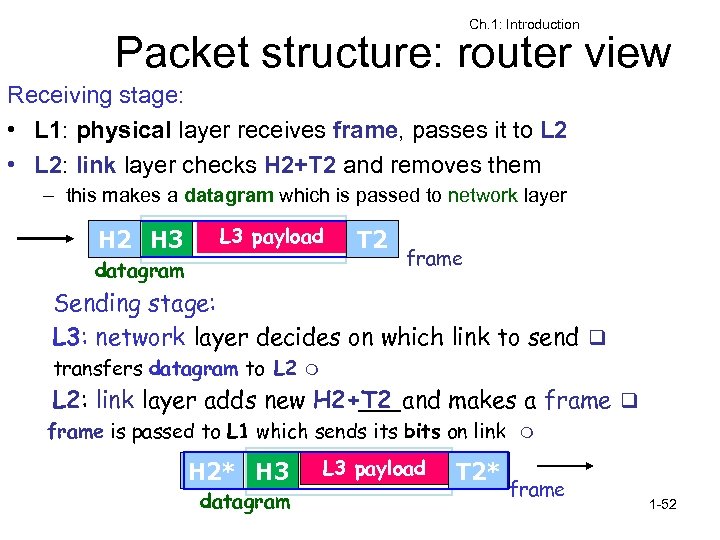 Ch. 1: Introduction Packet structure: router view Receiving stage: • L 1: physical layer receives frame, passes it to L 2 • L 2: link layer checks H 2+T 2 and removes them – this makes a datagram which is passed to network layer H 2 H 3 L 3 payload datagram T 2 frame Sending stage: L 3: network layer decides on which link to send q transfers datagram to L 2 m L 2: link layer adds new H 2+T 2 and makes a frame q frame is passed to L 1 which sends its bits on link H 2* H 3 datagram L 3 payload T 2* m frame 1 -52
Ch. 1: Introduction Packet structure: router view Receiving stage: • L 1: physical layer receives frame, passes it to L 2 • L 2: link layer checks H 2+T 2 and removes them – this makes a datagram which is passed to network layer H 2 H 3 L 3 payload datagram T 2 frame Sending stage: L 3: network layer decides on which link to send q transfers datagram to L 2 m L 2: link layer adds new H 2+T 2 and makes a frame q frame is passed to L 1 which sends its bits on link H 2* H 3 datagram L 3 payload T 2* m frame 1 -52
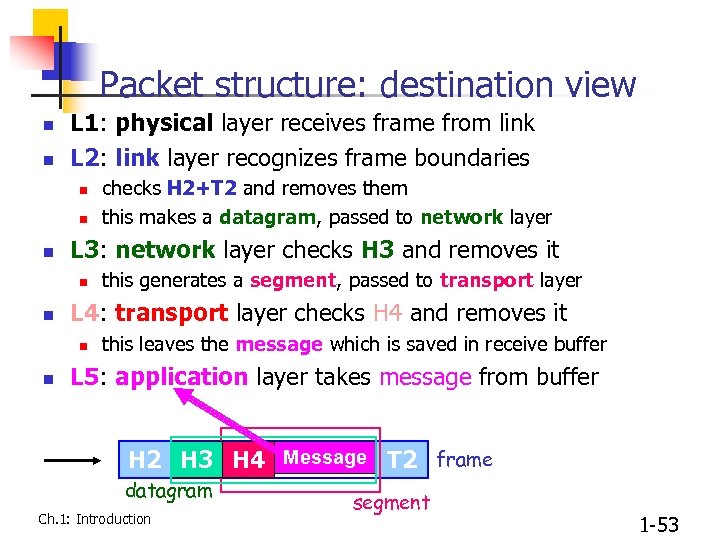 Packet structure: destination view n n L 1: physical layer receives frame from link L 2: link layer recognizes frame boundaries n n n L 3: network layer checks H 3 and removes it n n this generates a segment, passed to transport layer L 4: transport layer checks H 4 and removes it n n checks H 2+T 2 and removes them this makes a datagram, passed to network layer this leaves the message which is saved in receive buffer L 5: application layer takes message from buffer H 2 H 3 H 4 Message T 2 frame datagram Ch. 1: Introduction segment 1 -53
Packet structure: destination view n n L 1: physical layer receives frame from link L 2: link layer recognizes frame boundaries n n n L 3: network layer checks H 3 and removes it n n this generates a segment, passed to transport layer L 4: transport layer checks H 4 and removes it n n checks H 2+T 2 and removes them this makes a datagram, passed to network layer this leaves the message which is saved in receive buffer L 5: application layer takes message from buffer H 2 H 3 H 4 Message T 2 frame datagram Ch. 1: Introduction segment 1 -53
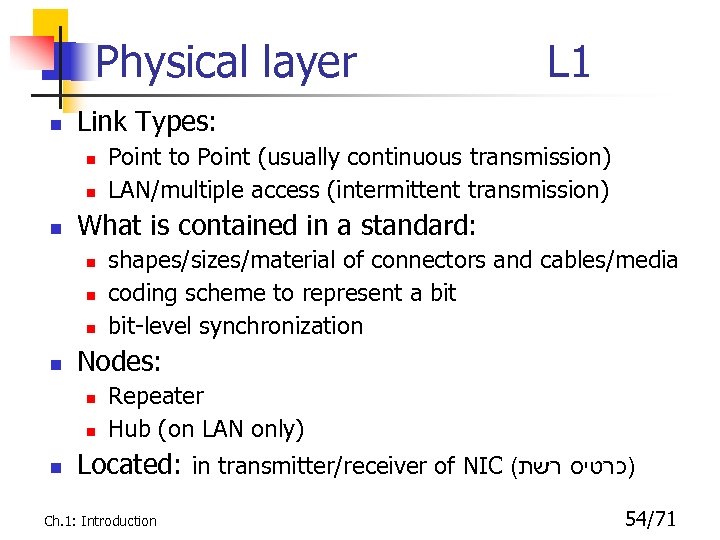 Physical layer n Link Types: n n n shapes/sizes/material of connectors and cables/media coding scheme to represent a bit-level synchronization Nodes: n n n Point to Point (usually continuous transmission) LAN/multiple access (intermittent transmission) What is contained in a standard: n n L 1 Repeater Hub (on LAN only) Located: in transmitter/receiver of NIC ( )כרטיס רשת Ch. 1: Introduction 54/71
Physical layer n Link Types: n n n shapes/sizes/material of connectors and cables/media coding scheme to represent a bit-level synchronization Nodes: n n n Point to Point (usually continuous transmission) LAN/multiple access (intermittent transmission) What is contained in a standard: n n L 1 Repeater Hub (on LAN only) Located: in transmitter/receiver of NIC ( )כרטיס רשת Ch. 1: Introduction 54/71
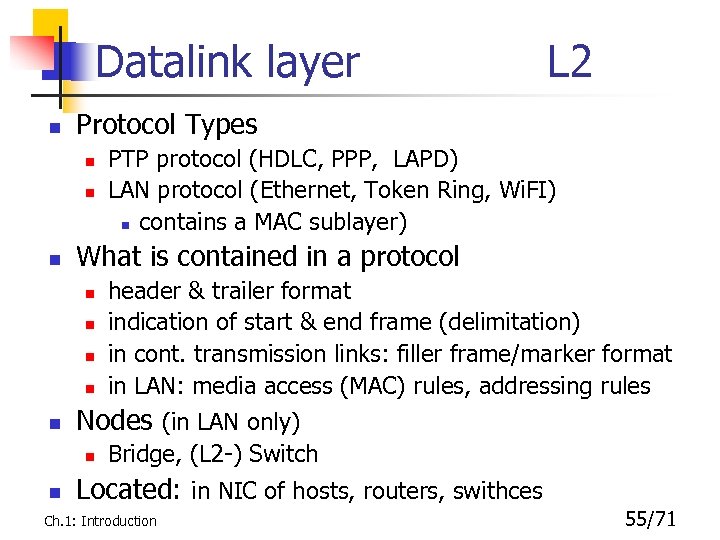 Datalink layer n Protocol Types n n n header & trailer format indication of start & end frame (delimitation) in cont. transmission links: filler frame/marker format in LAN: media access (MAC) rules, addressing rules Nodes (in LAN only) n n PTP protocol (HDLC, PPP, LAPD) LAN protocol (Ethernet, Token Ring, Wi. FI) n contains a MAC sublayer) What is contained in a protocol n n L 2 Bridge, (L 2 -) Switch Located: in NIC of hosts, routers, swithces Ch. 1: Introduction 55/71
Datalink layer n Protocol Types n n n header & trailer format indication of start & end frame (delimitation) in cont. transmission links: filler frame/marker format in LAN: media access (MAC) rules, addressing rules Nodes (in LAN only) n n PTP protocol (HDLC, PPP, LAPD) LAN protocol (Ethernet, Token Ring, Wi. FI) n contains a MAC sublayer) What is contained in a protocol n n L 2 Bridge, (L 2 -) Switch Located: in NIC of hosts, routers, swithces Ch. 1: Introduction 55/71
 Network layer n Network Types n n n n header format, address formats forwarding rules (how to use routing tables) What is contained in a routing protocol n n Circuit switching/Packet switching (datagram or VC) Protocol Types: Routing/ Forwarding What is contained in a forwarding protocol n n L 3 rules/ messages for learning topology info rules for building routing tables Nodes: Router Metaphor: Welds links into Host (ETE) “channel” Location: Host OS, Router S/W Ch. 1: Introduction 56/71
Network layer n Network Types n n n n header format, address formats forwarding rules (how to use routing tables) What is contained in a routing protocol n n Circuit switching/Packet switching (datagram or VC) Protocol Types: Routing/ Forwarding What is contained in a forwarding protocol n n L 3 rules/ messages for learning topology info rules for building routing tables Nodes: Router Metaphor: Welds links into Host (ETE) “channel” Location: Host OS, Router S/W Ch. 1: Introduction 56/71
 Network layer (more) L 3 n In datagram networks n n In connection-oriented network n n provides both routing and data forwarding separate data plane and control plane data plane only forwards and schedules data control plane prepares (virtual) circuits before data is sent Internet n n forwarding by IP protocol (a datagram protocol) n best effort service (no reliability tools) several routing protocols (RIP, OSFP, BGP) Ch. 1: Introduction 57/71
Network layer (more) L 3 n In datagram networks n n In connection-oriented network n n provides both routing and data forwarding separate data plane and control plane data plane only forwards and schedules data control plane prepares (virtual) circuits before data is sent Internet n n forwarding by IP protocol (a datagram protocol) n best effort service (no reliability tools) several routing protocols (RIP, OSFP, BGP) Ch. 1: Introduction 57/71
 Network layer (contd. ) n At end-systems n n segments and reassemble n n primarily hides details of datalink layer detects errors At intermediate systems n participates in routing protocol to create routing tables n responsible forwarding packets n schedules the transmission order of packets n chooses which packets to drop Ch. 1: Introduction 58/71
Network layer (contd. ) n At end-systems n n segments and reassemble n n primarily hides details of datalink layer detects errors At intermediate systems n participates in routing protocol to create routing tables n responsible forwarding packets n schedules the transmission order of packets n chooses which packets to drop Ch. 1: Introduction 58/71
 Transport layer n Protocol Types: n n n L 4 Reliable stream protocols (TCP, SCTP, SSL) Unreliable datagram protocols (UDP) What is contained a protocol header format n user-process multiplexing rules (using port) in Reliable protocols, also: n error control (ack, seq. #s, retransmission) n flow control (don’t overwhelm destination) n congestion control (don’t overload network) n n n Metaphor: Gives a Process to Process ETE channel Location: Hosts only, part of OS Ch. 1: Introduction 59/71
Transport layer n Protocol Types: n n n L 4 Reliable stream protocols (TCP, SCTP, SSL) Unreliable datagram protocols (UDP) What is contained a protocol header format n user-process multiplexing rules (using port) in Reliable protocols, also: n error control (ack, seq. #s, retransmission) n flow control (don’t overwhelm destination) n congestion control (don’t overload network) n n n Metaphor: Gives a Process to Process ETE channel Location: Hosts only, part of OS Ch. 1: Introduction 59/71
 Application layer n Application Types: n User-oriented applications (Web, Mail, File xfer. . ) n n n Infrastructure applications (DNS, NTP) Each application type has a separate protocol What is contained a protocol n n Protocols: HTTP, SMTP+POP, FTP Protocol Types: n n L 5 header format rules for mutual interaction of peer processes Metaphor: Talks to peer application about common job Location: Hosts only, run by the application S/W Ch. 1: Introduction 60/71
Application layer n Application Types: n User-oriented applications (Web, Mail, File xfer. . ) n n n Infrastructure applications (DNS, NTP) Each application type has a separate protocol What is contained a protocol n n Protocols: HTTP, SMTP+POP, FTP Protocol Types: n n L 5 header format rules for mutual interaction of peer processes Metaphor: Talks to peer application about common job Location: Hosts only, run by the application S/W Ch. 1: Introduction 60/71
 Layer Model Summary n n Studied (basically) the Internet 5 Layer Model OSI model (defined earlier, by ISO) n Contains 2 more layers: n n n Duplex ctrl, Data priority, Special session controls Presentation layer n n Application Layer is pushed to Layer 7 Not used in the Internet Session layer n n Layer 5 (Sessiion) Layer 6 (Presentation) Data structure standardization, encoding, encryption see Extra slides for more details Ch. 1: Introduction 61/71
Layer Model Summary n n Studied (basically) the Internet 5 Layer Model OSI model (defined earlier, by ISO) n Contains 2 more layers: n n n Duplex ctrl, Data priority, Special session controls Presentation layer n n Application Layer is pushed to Layer 7 Not used in the Internet Session layer n n Layer 5 (Sessiion) Layer 6 (Presentation) Data structure standardization, encoding, encryption see Extra slides for more details Ch. 1: Introduction 61/71
 History 1961 -1972: Early packet-switching principles 1961: Kleinrock - queuing theory shows effectiveness of packet-switching 1964: Baran - packet-switching in military networks 1967: ARPAnet – conceived by Advanced Research Projects Agency 1969: first ARPAnet node operational 1972: ARPAnet demonstrated publicly – NCP (Netwk Control Protocol) 1 st host-host protocol – first e-mail program – ARPAnet has 15 nodes Ch. 1: Introduction 62/71
History 1961 -1972: Early packet-switching principles 1961: Kleinrock - queuing theory shows effectiveness of packet-switching 1964: Baran - packet-switching in military networks 1967: ARPAnet – conceived by Advanced Research Projects Agency 1969: first ARPAnet node operational 1972: ARPAnet demonstrated publicly – NCP (Netwk Control Protocol) 1 st host-host protocol – first e-mail program – ARPAnet has 15 nodes Ch. 1: Introduction 62/71
 History 1972 -1980: Internetworking, new and proprietary nets 1970: ALOHAnet satellite network in Hawaii 1973: Metcalfe’s Ph. D thesis proposes Ethernet 1974: Cerf and Kahn - architecture for interconnecting networks late 70’s: proprietary architectures: DECnet, SNA, XNA late 70’s: switching fixed length packets (ATM precursor) 1979: ARPAnet has 200 nodes Ch. 1: Introduction 63/71
History 1972 -1980: Internetworking, new and proprietary nets 1970: ALOHAnet satellite network in Hawaii 1973: Metcalfe’s Ph. D thesis proposes Ethernet 1974: Cerf and Kahn - architecture for interconnecting networks late 70’s: proprietary architectures: DECnet, SNA, XNA late 70’s: switching fixed length packets (ATM precursor) 1979: ARPAnet has 200 nodes Ch. 1: Introduction 63/71
 Cerf and Kahn’s internetworking principles: – minimalism, autonomy - no internal changes required to interconnect networks – best effort service model – stateless routers – decentralized control Defines today’s Internet architecture Ch. 1: Introduction 64/71
Cerf and Kahn’s internetworking principles: – minimalism, autonomy - no internal changes required to interconnect networks – best effort service model – stateless routers – decentralized control Defines today’s Internet architecture Ch. 1: Introduction 64/71
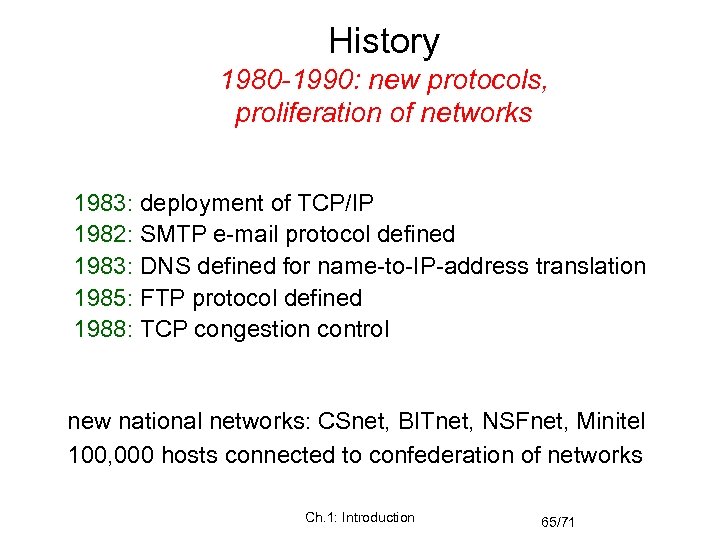 History 1980 -1990: new protocols, proliferation of networks 1983: deployment of TCP/IP 1982: SMTP e-mail protocol defined 1983: DNS defined for name-to-IP-address translation 1985: FTP protocol defined 1988: TCP congestion control new national networks: CSnet, BITnet, NSFnet, Minitel 100, 000 hosts connected to confederation of networks Ch. 1: Introduction 65/71
History 1980 -1990: new protocols, proliferation of networks 1983: deployment of TCP/IP 1982: SMTP e-mail protocol defined 1983: DNS defined for name-to-IP-address translation 1985: FTP protocol defined 1988: TCP congestion control new national networks: CSnet, BITnet, NSFnet, Minitel 100, 000 hosts connected to confederation of networks Ch. 1: Introduction 65/71
 History 1990 - : commercialization and WWW early 1990’s: ARPAnet decommissioned 1991: NSF lifts restrictions on commercial use of NSFnet (decommissioned, 1995) early 1990 s: WWW hypertext [Bush 1945, Nelson 1960’s] HTML, http: Berners-Lee 1994: Mosaic, later Netscape late 1990’s: commercialization of WWW Ch. 1: Introduction 66/71
History 1990 - : commercialization and WWW early 1990’s: ARPAnet decommissioned 1991: NSF lifts restrictions on commercial use of NSFnet (decommissioned, 1995) early 1990 s: WWW hypertext [Bush 1945, Nelson 1960’s] HTML, http: Berners-Lee 1994: Mosaic, later Netscape late 1990’s: commercialization of WWW Ch. 1: Introduction 66/71
 Demand Supply • Huge growth in users – The introduction of the web • Faster home access – Better user experience. • Infrastructure – Significant portion of telecommunication. • New evolving industries – Although, sometimes temporary setbacks Ch. 1: Introduction 67/71
Demand Supply • Huge growth in users – The introduction of the web • Faster home access – Better user experience. • Infrastructure – Significant portion of telecommunication. • New evolving industries – Although, sometimes temporary setbacks Ch. 1: Introduction 67/71
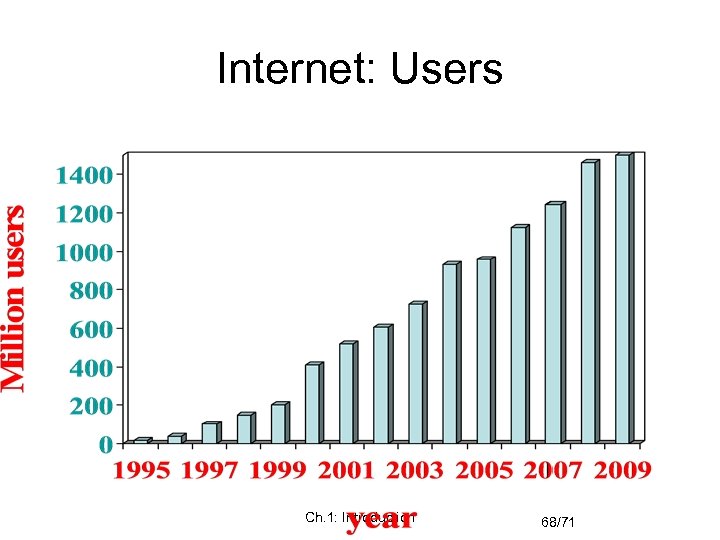 Internet: Users Ch. 1: Introduction 68/71
Internet: Users Ch. 1: Introduction 68/71
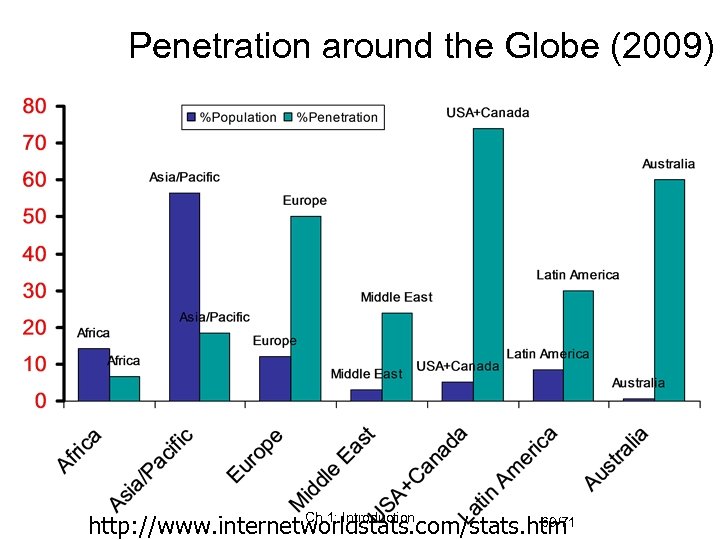 Penetration around the Globe (2009) Ch. 1: Introduction 69/71 http: //www. internetworldstats. com/stats. htm
Penetration around the Globe (2009) Ch. 1: Introduction 69/71 http: //www. internetworldstats. com/stats. htm
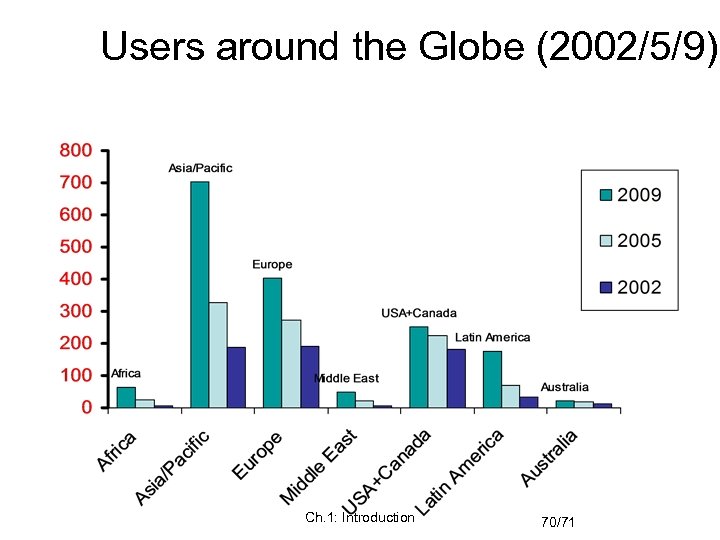 Users around the Globe (2002/5/9) Ch. 1: Introduction 70/71
Users around the Globe (2002/5/9) Ch. 1: Introduction 70/71
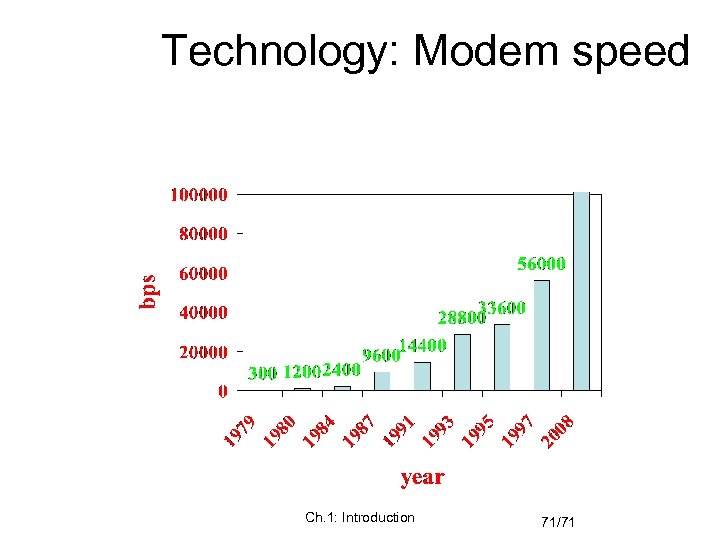 Technology: Modem speed Ch. 1: Introduction 71/71
Technology: Modem speed Ch. 1: Introduction 71/71
 Today’s options • • Modem: 56 K ISDN: 64 K – 128 K OBSOLETE Frame Relay: 56 K ++ Today High Speed Connections – Cable, ADSL, Satellite. – All are available at • 5 Mb (2005) • 30 Mb (2009) Ch. 1: Introduction 72/71
Today’s options • • Modem: 56 K ISDN: 64 K – 128 K OBSOLETE Frame Relay: 56 K ++ Today High Speed Connections – Cable, ADSL, Satellite. – All are available at • 5 Mb (2005) • 30 Mb (2009) Ch. 1: Introduction 72/71
 Coming soon (1999) Ch. 1: Introduction 73/71
Coming soon (1999) Ch. 1: Introduction 73/71
 Today (2005) Ch. 1: Introduction 74/71
Today (2005) Ch. 1: Introduction 74/71
 Session layer • Not common • Provides full-duplex service, expedited data delivery, and session synchronization • Internet – doesn’t have a standard session layer Ch. 1: Introduction 75/71
Session layer • Not common • Provides full-duplex service, expedited data delivery, and session synchronization • Internet – doesn’t have a standard session layer Ch. 1: Introduction 75/71
 Session layer (cont. ) • Duplex – if transport layer is simplex, concatenates two transport endpoints together • Expedited data delivery – allows some messages to skip ahead in end-system queues, by using a separate low-delay transport layer endpoint • Synchronization – allows users to place marks in data stream and to roll back to a prespecified mark Ch. 1: Introduction 76/71
Session layer (cont. ) • Duplex – if transport layer is simplex, concatenates two transport endpoints together • Expedited data delivery – allows some messages to skip ahead in end-system queues, by using a separate low-delay transport layer endpoint • Synchronization – allows users to place marks in data stream and to roll back to a prespecified mark Ch. 1: Introduction 76/71
 Presentation layer • Usually ad hoc • Touches the application data (Unlike other layers which deal with headers) • Hides data representation differences between applications – characters (ASCII, unicode, EBCDIC. ) • Can also encrypt data • Internet – no standard presentation layer – only defines network byte order for 2 - and 4 -byte integers Ch. 1: Introduction 77/71
Presentation layer • Usually ad hoc • Touches the application data (Unlike other layers which deal with headers) • Hides data representation differences between applications – characters (ASCII, unicode, EBCDIC. ) • Can also encrypt data • Internet – no standard presentation layer – only defines network byte order for 2 - and 4 -byte integers Ch. 1: Introduction 77/71
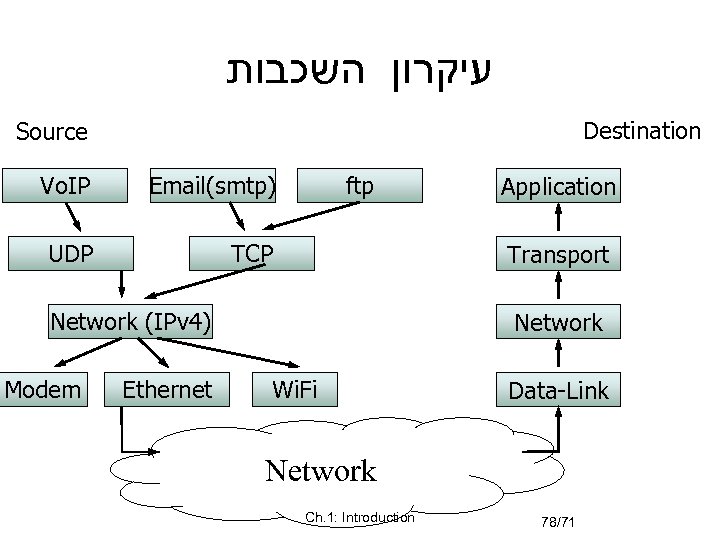 עיקרון השכבות Destination Source Vo. IP Email(smtp) UDP ftp TCP Transport Network (IPv 4) Modem Ethernet Application Network Wi. Fi Data-Link Network Ch. 1: Introduction 78/71
עיקרון השכבות Destination Source Vo. IP Email(smtp) UDP ftp TCP Transport Network (IPv 4) Modem Ethernet Application Network Wi. Fi Data-Link Network Ch. 1: Introduction 78/71
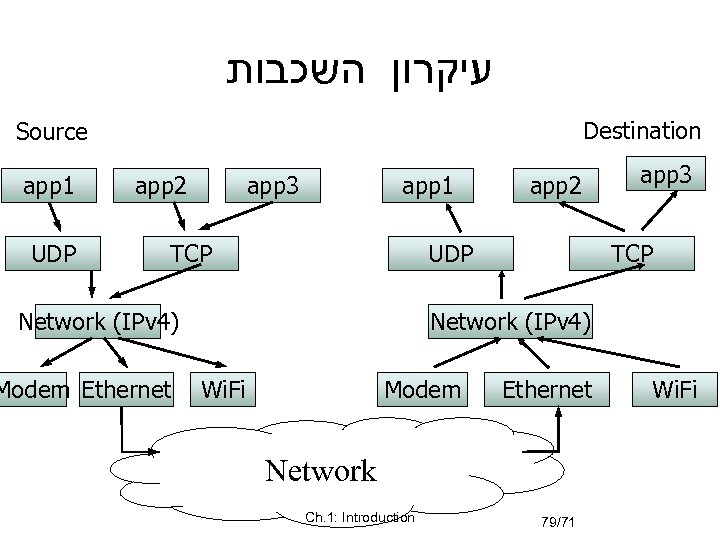 עיקרון השכבות Destination Source app 1 UDP app 2 app 3 app 1 TCP UDP Network (IPv 4) Modem Ethernet app 2 app 3 TCP Network (IPv 4) Wi. Fi Modem Ethernet Network Ch. 1: Introduction 79/71 Wi. Fi
עיקרון השכבות Destination Source app 1 UDP app 2 app 3 app 1 TCP UDP Network (IPv 4) Modem Ethernet app 2 app 3 TCP Network (IPv 4) Wi. Fi Modem Ethernet Network Ch. 1: Introduction 79/71 Wi. Fi
 Discussion • Layers break a complex problem into smaller, simpler pieces. • Why seven layers? – Need a top and a bottom 2 – Need to hide physical link; so need datalink 3 – Need both end-to-end and hop-by-hop actions; so need at least the network and transport layers 5 Ch. 1: Introduction 80/71
Discussion • Layers break a complex problem into smaller, simpler pieces. • Why seven layers? – Need a top and a bottom 2 – Need to hide physical link; so need datalink 3 – Need both end-to-end and hop-by-hop actions; so need at least the network and transport layers 5 Ch. 1: Introduction 80/71


