ef397662f1f67a1c74c2a0964774d73f.ppt
- Количество слайдов: 50

Computer Forensics Use of Malicious Input

Buffer and Heap Overflow Attacks n n Standard Tool to Break Into Systems. Used for Access Escalation. Very Common. Prototype of an Attack Mode.
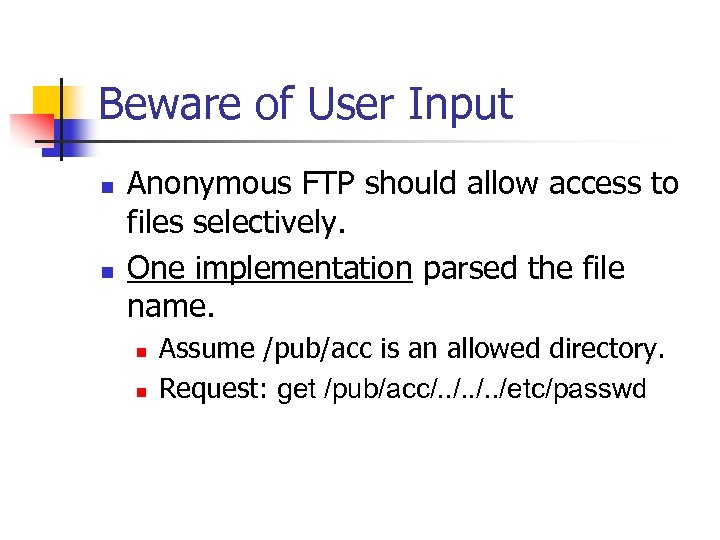
Beware of User Input n n Anonymous FTP should allow access to files selectively. One implementation parsed the file name. n n Assume /pub/acc is an allowed directory. Request: get /pub/acc/. . /etc/passwd
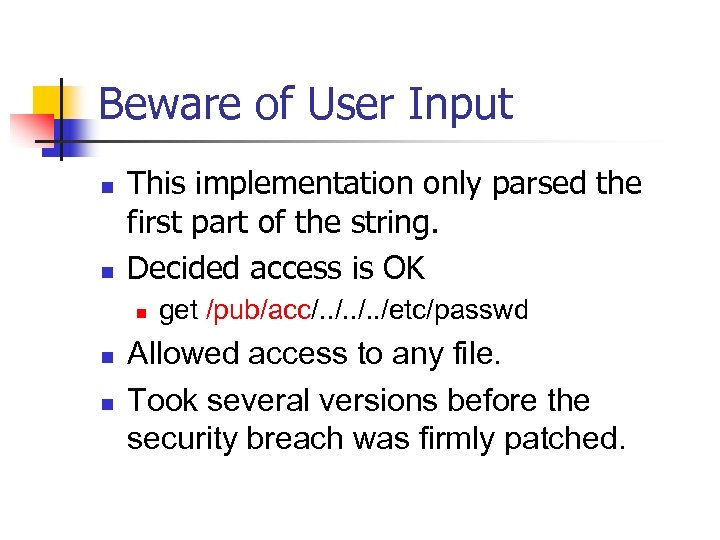
Beware of User Input n n This implementation only parsed the first part of the string. Decided access is OK n n n get /pub/acc/. . /etc/passwd Allowed access to any file. Took several versions before the security breach was firmly patched.

Morale: n Don’t reinvent the wheel. n n n Parsing input is difficult. n n Other implementations used a sandbox. Community had learned how to get it right. Users have an incentive to be inventive. ALL INPUT IS EVIL
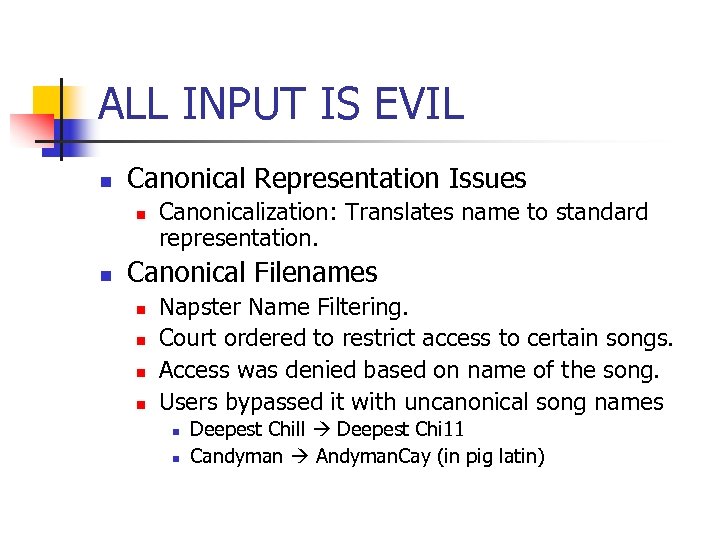
ALL INPUT IS EVIL n Canonical Representation Issues n n Canonicalization: Translates name to standard representation. Canonical Filenames n n Napster Name Filtering. Court ordered to restrict access to certain songs. Access was denied based on name of the song. Users bypassed it with uncanonical song names n n Deepest Chill Deepest Chi 11 Candyman Andyman. Cay (in pig latin)
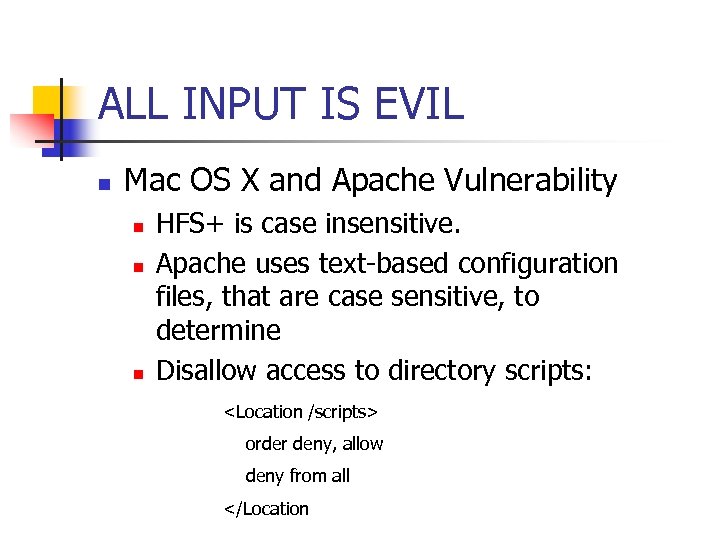
ALL INPUT IS EVIL n Mac OS X and Apache Vulnerability n n n HFS+ is case insensitive. Apache uses text-based configuration files, that are case sensitive, to determine Disallow access to directory scripts: <Location /scripts> order deny, allow deny from all </Location
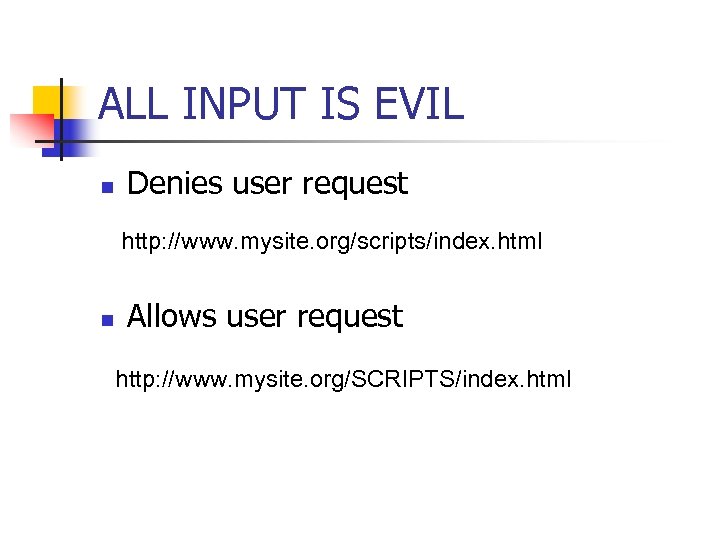
ALL INPUT IS EVIL n Denies user request http: //www. mysite. org/scripts/index. html n Allows user request http: //www. mysite. org/SCRIPTS/index. html

ALL INPUT IS EVIL n n n Sun Star. Office /tmp directory symbolic link vulnerability Symbolic link: file that points to another file. Symbolic links do not share access rights with the file they point to.

ALL INPUT IS EVIL n n Sun Star. Office creates file /tmp/soffice. tmp with 0777 access mask. Attacker links /tmp/soffice. tmp to /etc/passwd. Root runs Star. Office Permissions on /etc/passwd would get changed to 0777.

Canonicalization Issues n n Subsystems cooperate. First subsystem does not canonicalize input in the way the second one does.
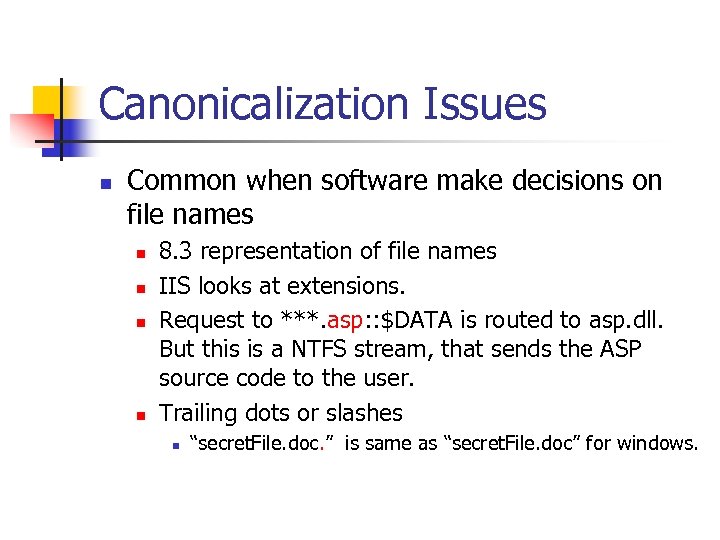
Canonicalization Issues n Common when software make decisions on file names n n 8. 3 representation of file names IIS looks at extensions. Request to ***. asp: : $DATA is routed to asp. dll. But this is a NTFS stream, that sends the ASP source code to the user. Trailing dots or slashes n “secret. File. doc. ” is same as “secret. File. doc” for windows.

Canonicalization Issues n n n AOL 5. 0 parental controls: n n \? tempmyfile is the same as tempmyfile Directory traversal. . / Bypass restriction on URL by adding period to file name. Secure IIS verifies incoming and outgoing data n n n Use hexcode: %64 elete instead of delete for key words. Use “%2 e%2 e/” for “. . /” Two canonalization issues in Security Software!
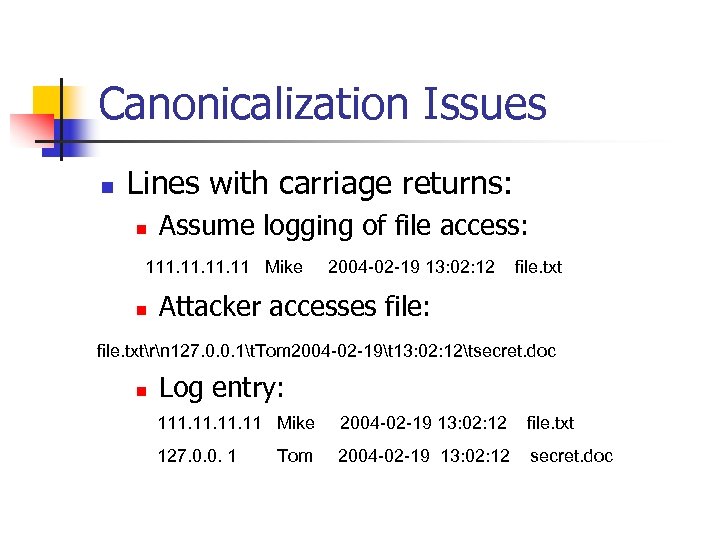
Canonicalization Issues n Lines with carriage returns: n Assume logging of file access: 111. 11. 11 Mike n 2004 -02 -19 13: 02: 12 file. txt Attacker accesses file: file. txtrn 127. 0. 0. 1t. Tom 2004 -02 -19t 13: 02: 12tsecret. doc n Log entry: 111. 11. 11 Mike 2004 -02 -19 13: 02: 12 file. txt 127. 0. 0. 1 2004 -02 -19 13: 02: 12 secret. doc Tom
Canonicalization Issues n Escaping: Many ways to represent a character n n n US-ASCII Hexadecimal escape codes UTF-8 variable width encoding UCS-2 Unicode encoding HTML escape codes Double Escaping

Canonicalization Issues n n Homograph Attacks Characters look the same, but are not Latin letter “o” Cyrillic character “o” (U+043 E)

Morale n n n Software should not make decisions based on names. If it has do, enforce name restrictions Don’t trust relative paths.
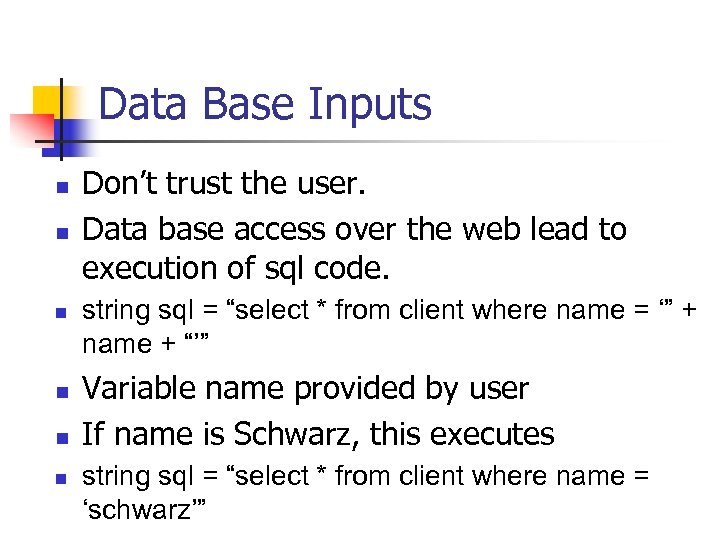
Data Base Inputs n n n Don’t trust the user. Data base access over the web lead to execution of sql code. string sql = “select * from client where name = ‘” + name + “’” Variable name provided by user If name is Schwarz, this executes string sql = “select * from client where name = ‘schwarz’”

Data Base Inputs n User enters: n n The sql statement becomes n n n Schwarz’ or 1=1 - string sql = “select * from client where name = ‘schwarz’ or 1=1 - -” Selects all clients - - SQL comment, comments out everything behind.
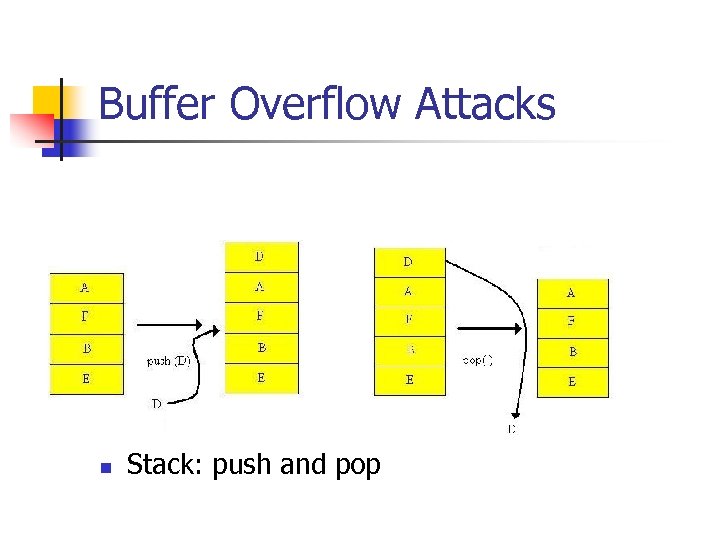
Buffer Overflow Attacks n Stack: push and pop

Buffer Overflow Attacks n Stack is area of program memory that contains static allocated variables, return addresses, etc.
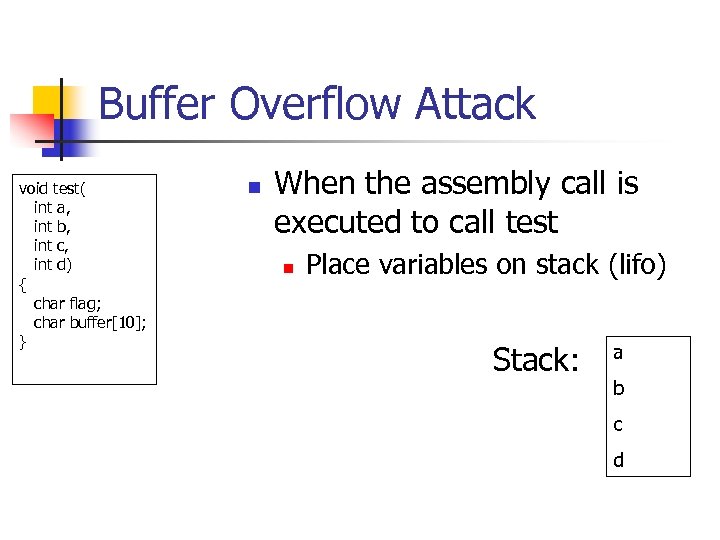
Buffer Overflow Attack void test( int a, int b, int c, int d) { char flag; char buffer[10]; } n When the assembly call is executed to call test n Place variables on stack (lifo) Stack: a b c d
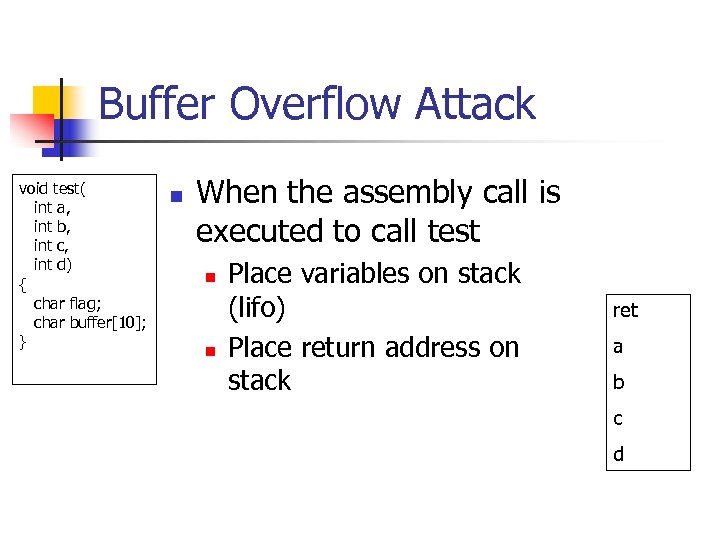
Buffer Overflow Attack void test( int a, int b, int c, int d) { char flag; char buffer[10]; } n When the assembly call is executed to call test n n Place variables on stack (lifo) Place return address on stack ret a b c d
![Buffer Overflow Attack buffer[0] buffer[1]. void test( int a, int b, int c, int Buffer Overflow Attack buffer[0] buffer[1]. void test( int a, int b, int c, int](https://present5.com/presentation/ef397662f1f67a1c74c2a0964774d73f/image-24.jpg)
Buffer Overflow Attack buffer[0] buffer[1]. void test( int a, int b, int c, int d) { char flag; char buffer[10]; } n When the assembly call is executed to call test n n … Place SFP (EBP) on stack n n n Saved frame pointer Used to address local variables Allocate local variables n flag, buffer . buffer[9] flag sfp ret a b c d
![Buffer Overflow Attack buffer[0] buffer[1]. void test( int a, int b, int c, int Buffer Overflow Attack buffer[0] buffer[1]. void test( int a, int b, int c, int](https://present5.com/presentation/ef397662f1f67a1c74c2a0964774d73f/image-25.jpg)
Buffer Overflow Attack buffer[0] buffer[1]. void test( int a, int b, int c, int d) { char flag; char buffer[10]; } n When function returns n Pop the local variables n n By resetting the stackpointer. Restore the frame pointer. Reload the value in ret into the program counter. Pop arguments. . buffer[9] flag sfp ret a b c d

Buffer Overflow Attack n Buffer overflow: n If user can input value into buffer without checking numbers, then we can overwrite important parts of the stack.
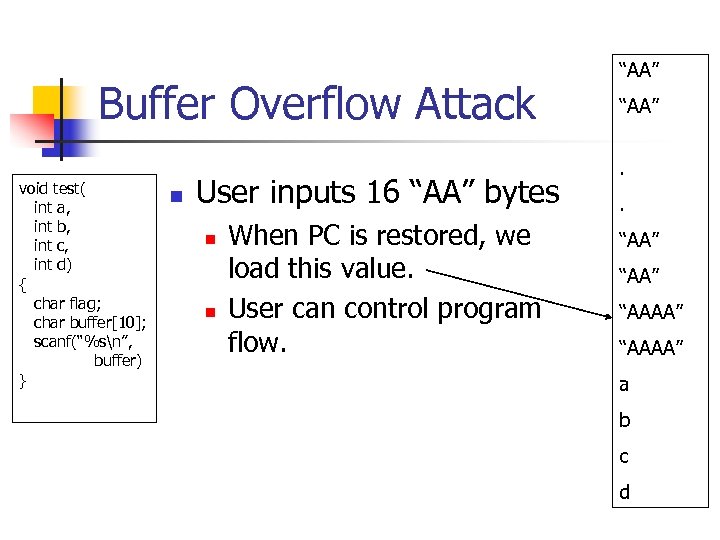
Buffer Overflow Attack void test( int a, int b, int c, int d) { char flag; char buffer[10]; scanf(“%sn”, buffer) } n User inputs 16 “AA” bytes n n When PC is restored, we load this value. User can control program flow. “AA”. . “AA” “AAAA” a b c d
![Buffer Overflow Attack int main(int argc, char* argv[]) { foo(argv[1]); return 0; } void Buffer Overflow Attack int main(int argc, char* argv[]) { foo(argv[1]); return 0; } void](https://present5.com/presentation/ef397662f1f67a1c74c2a0964774d73f/image-28.jpg)
Buffer Overflow Attack int main(int argc, char* argv[]) { foo(argv[1]); return 0; } void foo(const char* input) { char buf[10]; printf("Hello Worldn"); }
Buffer Overflow Attack Windows example: Compilers vary

Buffer Overflow Attack #pragma check_stack(off) #include <string. h> #include <stdio. h> void foo(const char* input) { char buf[10]; printf("My stack looks like: n%pn%pn%pnn"); strcpy(buf, input); printf("%sn", buf); printf("Now the stack looks like: n%pn%pn%pnn"); } void bar(void) { printf("Augh! I've been hacked!n"); }
![Buffer Overflow Attack int main(int argc, char* argv[]) { printf("Address of foo = %pn", Buffer Overflow Attack int main(int argc, char* argv[]) { printf("Address of foo = %pn",](https://present5.com/presentation/ef397662f1f67a1c74c2a0964774d73f/image-31.jpg)
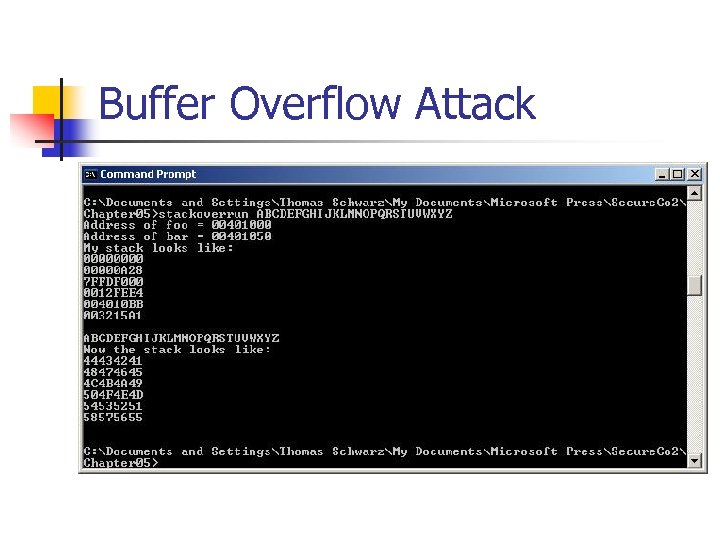
Buffer Overflow Attack int main(int argc, char* argv[]) { printf("Address of foo = %pn", foo); printf("Address of bar = %pn", bar); if (argc != 2) { printf("Please supply a string as an argument!n"); return -1; } foo(argv[1]); return 0; }

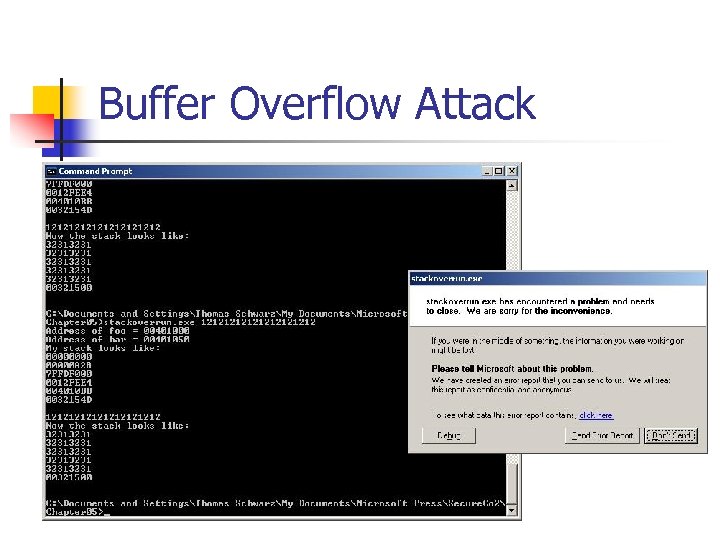
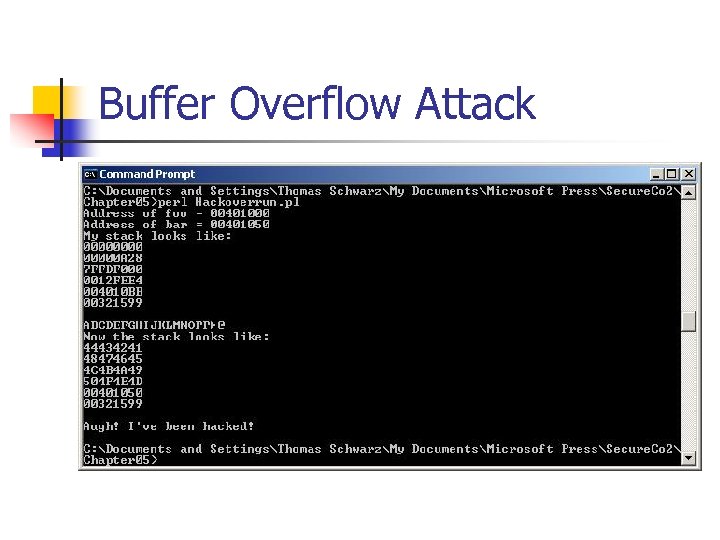
Buffer Overflow Attack Chapter 05>stackoverrun. exe Hello Address of foo = 00401000 Address of bar = 00401050 My stack looks like: 00000 A 28 7 FFDF 000 0012 FEE 4 004010 BB 0032154 D Hello Now the stack looks like: 6 C 6 C 6548 0000006 F 7 FFDF 000 0012 FEE 4 004010 BB 0032154 D
Buffer Overflow Attack
Buffer Overflow Attack
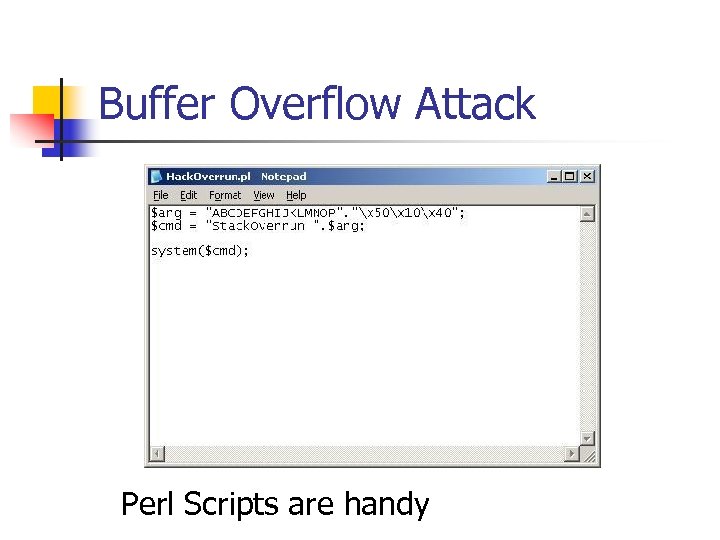
Buffer Overflow Attack Perl Scripts are handy
Buffer Overflow Attack
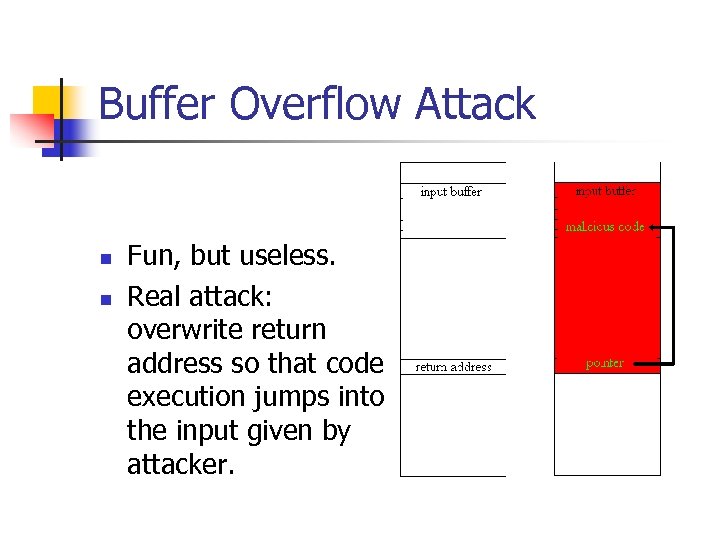
Buffer Overflow Attack n n Fun, but useless. Real attack: overwrite return address so that code execution jumps into the input given by attacker.

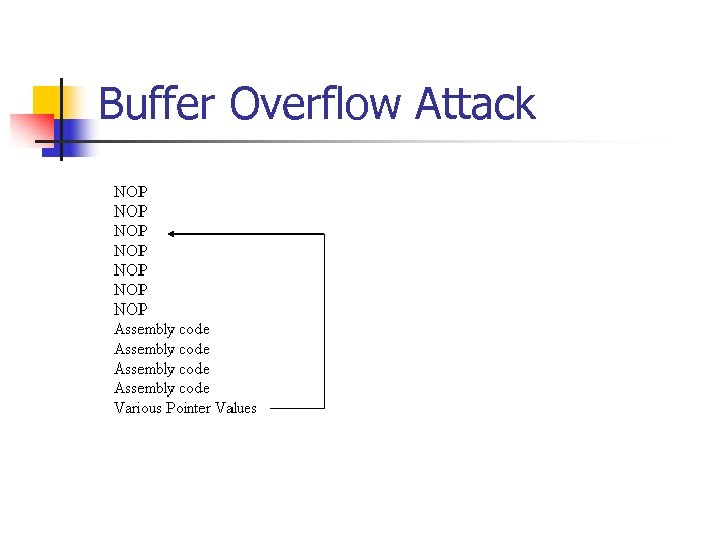
Buffer Overflow Attack n To protect against signatures, structure input n n n Varying stuff execve(/bin/sh) (gives new shell with program privileges in UNIX) Pointer to execve statement.

Buffer Overflow Attack n Finding vulnerabilities n n Script-kiddies scan target with automated tool. Tool creator has detailed analysis of vulnerabilities. n n Look for strcpy, gets, getws, memcpy memmove, scanf, … Alternatively, just cram the application until it crashes. n Crash used to give you locations of registers.

Buffer Overflow Attack n Finding vulnerabilities n Disassembly code for which a source is not available.

Buffer Overflow Attack n n Example: Cram in lots of input of As. Program crashes, EIP has value 4141. Sign of buffer overflow. Now try to feed more specific input.
Buffer Overflow Attack

Buffer Overflow Attack n n n Attack signature can be used by IDS. Vary the NOP commands. Many alternatives.
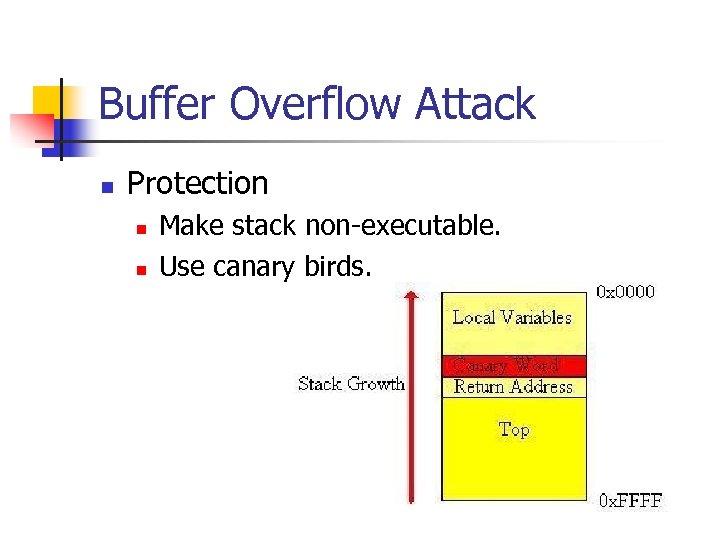
Buffer Overflow Attack n Protection n n Make stack non-executable. Use canary birds.

Buffer Overflow Attack n n Stack Guard MS Visual Studio use canaries.

Buffer Overflow Attack n MS Outlook Vcard: Virtual business card buffer overflow vulnerability. n n IIS 5 Internet Printing Protocol

Buffer Overflow Attacks n n n But the first MS implementation made it worse. When Canary was overwritten, program executed user written handler. Attacker could use buffer overflow to overwrite the address of the handler function. The overwriting value would point to the stack. The very same mechanism intended to prevent some buffer overflow attacks can be used to

Heap Overflow Attack n n n These protections do not apply to heaps, where dynamically allocated memory resides. Some of this memory contains the addresses of functions that are going to be called. Harder to find, harder to protect against.

Overflow Attacks n When the vulnerable program runs at administrator level, overflow attacks give escalation of privileges.

Remember: People attack computer systems because they can.
ef397662f1f67a1c74c2a0964774d73f.ppt