ba72fe924fa8b2ede4d0f7c5935483ab.ppt
- Количество слайдов: 21
 COMPUTER FORENSICS Tan (tan@atstake. com)
COMPUTER FORENSICS Tan (tan@atstake. com)
 FORENSICS IS A FOUR STEP PROCESS § § Acquisition Identification Evaluation Presentation RCMP Technical Security Branch - Computer Forensics: An Approach to Evidence in Cyberspace (RCMP GRC Publications) http: //www. rcmp-grc. gc. ca/tsb/pubs/bulletins/bull 41_3. htm , by Special Agent Mark M. Pollitt, Federal Bureau of Investigation, Baltimore, Maryland (4/96)
FORENSICS IS A FOUR STEP PROCESS § § Acquisition Identification Evaluation Presentation RCMP Technical Security Branch - Computer Forensics: An Approach to Evidence in Cyberspace (RCMP GRC Publications) http: //www. rcmp-grc. gc. ca/tsb/pubs/bulletins/bull 41_3. htm , by Special Agent Mark M. Pollitt, Federal Bureau of Investigation, Baltimore, Maryland (4/96)
 GROUND ZERO – WHAT YOU CAN DO § do not start looking through files § establish an evidence custodian - start a journal with the date and time, keep detailed notes § Designate equipment as “off-limits” to normal activity (if possible) – especially back-ups (with dump or other backup utilities), locally or remotely scheduled house-keeping, and configuration changes. § collate mail, DNS and other network service logs to support host data § capture exhaustive external TCP and UDP port scans of the host (unless tcp-wrapped) § contact security department or CERT, management, police or FBI, affected sites* § packaging/labeling and shipping § short-term storage
GROUND ZERO – WHAT YOU CAN DO § do not start looking through files § establish an evidence custodian - start a journal with the date and time, keep detailed notes § Designate equipment as “off-limits” to normal activity (if possible) – especially back-ups (with dump or other backup utilities), locally or remotely scheduled house-keeping, and configuration changes. § collate mail, DNS and other network service logs to support host data § capture exhaustive external TCP and UDP port scans of the host (unless tcp-wrapped) § contact security department or CERT, management, police or FBI, affected sites* § packaging/labeling and shipping § short-term storage
 Incident Response – What the Pros Do § Identify designate or become the evidence custodian § Review any journal of what has been done to the system already and how the intrusion was detected § Start or maintain existing journal § Install a sniffer § Backdoors § If possible without rebooting, make two byte by byte copies of the physical disk § Capture network info § Capture process listings and open files § Capture configuration information to disk and notes § Receipt and signing of data
Incident Response – What the Pros Do § Identify designate or become the evidence custodian § Review any journal of what has been done to the system already and how the intrusion was detected § Start or maintain existing journal § Install a sniffer § Backdoors § If possible without rebooting, make two byte by byte copies of the physical disk § Capture network info § Capture process listings and open files § Capture configuration information to disk and notes § Receipt and signing of data
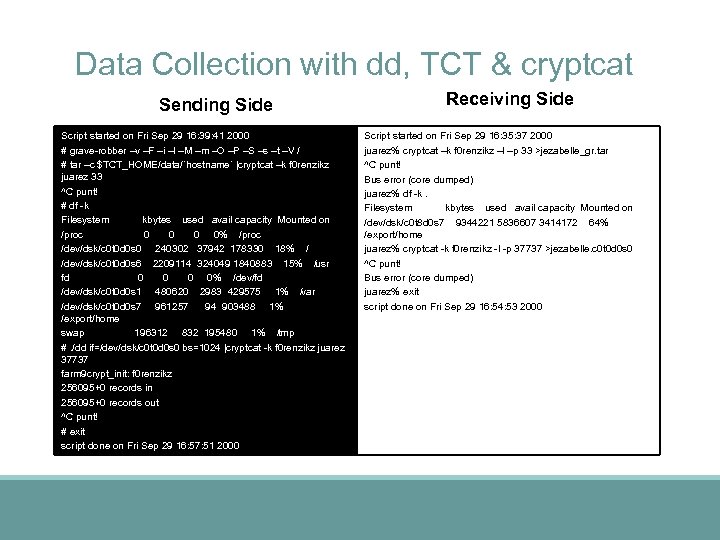 Data Collection with dd, TCT & cryptcat Sending Side Script started on Fri Sep 29 16: 39: 41 2000 # grave-robber –v –F –i –l –M –m –O –P –S –s –t –V / # tar –c $TCT_HOME/data/`hostname` |cryptcat –k f 0 renzikz juarez 33 ^C punt! # df -k Filesystem kbytes used avail capacity Mounted on /proc 0 0% /proc /dev/dsk/c 0 t 0 d 0 s 0 240302 37942 178330 18% / /dev/dsk/c 0 t 0 d 0 s 6 2209114 324049 1840883 15% /usr fd 0 0% /dev/fd /dev/dsk/c 0 t 0 d 0 s 1 480620 2983 429575 1% /var /dev/dsk/c 0 t 0 d 0 s 7 961257 94 903488 1% /export/home swap 196312 832 195480 1% /tmp #. /dd if=/dev/dsk/c 0 t 0 d 0 s 0 bs=1024 |cryptcat -k f 0 renzikz juarez 37737 farm 9 crypt_init: f 0 renzikz 256095+0 records in 256095+0 records out ^C punt! # exit script done on Fri Sep 29 16: 57: 51 2000 Receiving Side Script started on Fri Sep 29 16: 35: 37 2000 juarez% cryptcat –k f 0 renzikz –l –p 33 >jezabelle_gr. tar ^C punt! Bus error (core dumped) juarez% df -k. Filesystem kbytes used avail capacity Mounted on /dev/dsk/c 0 t 8 d 0 s 7 9344221 5836607 3414172 64% /export/home juarez% cryptcat -k f 0 renzikz -l -p 37737 >jezabelle. c 0 t 0 d 0 s 0 ^C punt! Bus error (core dumped) juarez% exit script done on Fri Sep 29 16: 54: 53 2000
Data Collection with dd, TCT & cryptcat Sending Side Script started on Fri Sep 29 16: 39: 41 2000 # grave-robber –v –F –i –l –M –m –O –P –S –s –t –V / # tar –c $TCT_HOME/data/`hostname` |cryptcat –k f 0 renzikz juarez 33 ^C punt! # df -k Filesystem kbytes used avail capacity Mounted on /proc 0 0% /proc /dev/dsk/c 0 t 0 d 0 s 0 240302 37942 178330 18% / /dev/dsk/c 0 t 0 d 0 s 6 2209114 324049 1840883 15% /usr fd 0 0% /dev/fd /dev/dsk/c 0 t 0 d 0 s 1 480620 2983 429575 1% /var /dev/dsk/c 0 t 0 d 0 s 7 961257 94 903488 1% /export/home swap 196312 832 195480 1% /tmp #. /dd if=/dev/dsk/c 0 t 0 d 0 s 0 bs=1024 |cryptcat -k f 0 renzikz juarez 37737 farm 9 crypt_init: f 0 renzikz 256095+0 records in 256095+0 records out ^C punt! # exit script done on Fri Sep 29 16: 57: 51 2000 Receiving Side Script started on Fri Sep 29 16: 35: 37 2000 juarez% cryptcat –k f 0 renzikz –l –p 33 >jezabelle_gr. tar ^C punt! Bus error (core dumped) juarez% df -k. Filesystem kbytes used avail capacity Mounted on /dev/dsk/c 0 t 8 d 0 s 7 9344221 5836607 3414172 64% /export/home juarez% cryptcat -k f 0 renzikz -l -p 37737 >jezabelle. c 0 t 0 d 0 s 0 ^C punt! Bus error (core dumped) juarez% exit script done on Fri Sep 29 16: 54: 53 2000
 Acquisition – Takin’ it Off-Line § § SLR – take pictures Considerations before pulling the plug Unplug the system from the network If possible freeze the system such that the current memory, swap files, and even CPU registers are saved or documented § Unplug the system (power) § Packaging/labeling § Shipping
Acquisition – Takin’ it Off-Line § § SLR – take pictures Considerations before pulling the plug Unplug the system from the network If possible freeze the system such that the current memory, swap files, and even CPU registers are saved or documented § Unplug the system (power) § Packaging/labeling § Shipping
 FBI List of Computer Forensic Laboratory Services § Content (what type of data) § Comparison (against known data) § Transaction (sequence) § Extraction (of data) § Deleted Data Files (recovery) § Format Conversion § Keyword Searching § Password (decryption) § Limited Source Code (analysis or compare) § Storage Media (many types)
FBI List of Computer Forensic Laboratory Services § Content (what type of data) § Comparison (against known data) § Transaction (sequence) § Extraction (of data) § Deleted Data Files (recovery) § Format Conversion § Keyword Searching § Password (decryption) § Limited Source Code (analysis or compare) § Storage Media (many types)
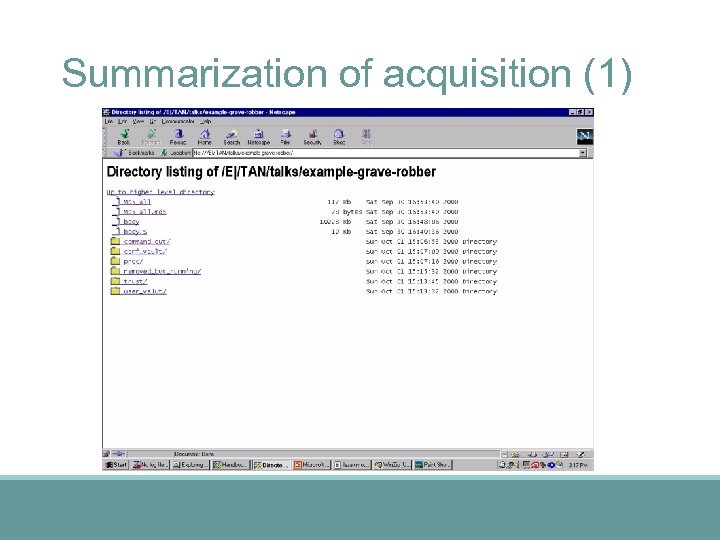 Summarization of acquisition (1)
Summarization of acquisition (1)
 Summarization of acquisition (2)
Summarization of acquisition (2)
 Summarization of acquisition (3)
Summarization of acquisition (3)
 Summarization of acquisition (4)
Summarization of acquisition (4)
 Extraction with Lazarus Script started on Sat Sep 30 16: 23: 03 2000 [root@plaything forensics]#. . /tct-1. 03/bin/lazarus -B -h -H. . /www -D. . /blocks -w. . /www -t. /valencia. hda 1 [root@plaything www]# cd. . /www [root@plaything www]# netscape. /valencia. hda 1. html
Extraction with Lazarus Script started on Sat Sep 30 16: 23: 03 2000 [root@plaything forensics]#. . /tct-1. 03/bin/lazarus -B -h -H. . /www -D. . /blocks -w. . /www -t. /valencia. hda 1 [root@plaything www]# cd. . /www [root@plaything www]# netscape. /valencia. hda 1. html
 Summarization of extraction (1)
Summarization of extraction (1)
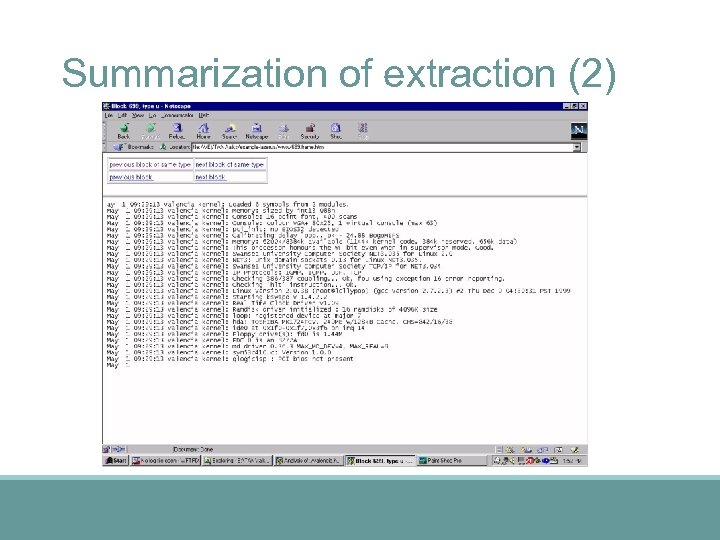 Summarization of extraction (2)
Summarization of extraction (2)
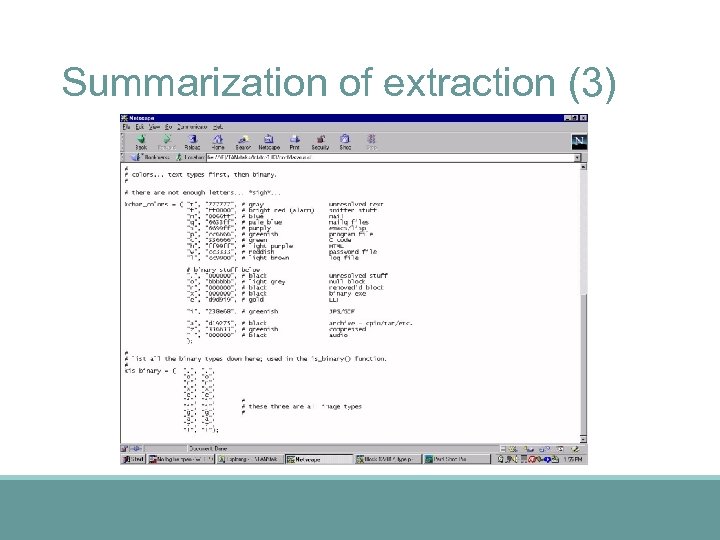 Summarization of extraction (3)
Summarization of extraction (3)
 Correlating Log Files § § Where to look What do log entries mean? How to narrow your search How reliable is the data?
Correlating Log Files § § Where to look What do log entries mean? How to narrow your search How reliable is the data?
 Shipping and Storage § § § UPS/FEDEX Requirements Laboratory Requirements Latent Materials Tamper Evident Packaging Restricted Access and Low Traffic, Camera Monitored Storage. § Sign In/Out for Chain of Custody
Shipping and Storage § § § UPS/FEDEX Requirements Laboratory Requirements Latent Materials Tamper Evident Packaging Restricted Access and Low Traffic, Camera Monitored Storage. § Sign In/Out for Chain of Custody
 Thinking Strategic § § § § Preparing with procedures and checklists Having an evidence locker OS Accounting turned on Log IP Numbers - DO NOT RESOLVE! Clocks synchronized to GPS on GMT Evidence Server Use of encrypted file systems Tools and materials
Thinking Strategic § § § § Preparing with procedures and checklists Having an evidence locker OS Accounting turned on Log IP Numbers - DO NOT RESOLVE! Clocks synchronized to GPS on GMT Evidence Server Use of encrypted file systems Tools and materials
 Pocket Security Toolkit
Pocket Security Toolkit
 ADDITIONAL RESOURCES § § § RCMP Article on the Forensic Process. http: //www. rcmpgrc. gc. ca/tsb/pubs/bulletins/bull 41_3. htm Lance Spitzner’s Page: Forensic Analysis, Building Honeypots http: //www. enteract. com/~lspitz/pubs. html Fish. com Security’s Forensic Page: The Coroner’s Toolkit (Unix), Computer Forensic Class Handouts. http: //www. fish. com/forensics/ The Forensic Toolkit (NT). http: //www. ntobjectives. com/forensic. htm Cryptcat. http: //www. farm 9. com/Free_Tools/Cryptcat Long Play Video Recorders. http: //www. pimall. com/nais/vrec. html FBI Handbook of Forensic Services. http: //www. fbi. gov/programs/lab/handbook/intro. htm Solaris Fingerprint Database for cryptographic comparison of system binaries. http: //sunsolve. sun. com/pub-cgi/file. Fingerprints. pl Inspecting Your Solaris System and Network Logs for Evidence of Intrusion. http: //www. cert. org/security-improvement/implementations/i 003. 01. html ONCTek List of possible Trojan/Backdoor Activity http: //www. onctek. com/trojanports. html Sixteen Tips for Testifying in Court from the “PI Mall” http: //www. pimall. com/nais/n. testify. html
ADDITIONAL RESOURCES § § § RCMP Article on the Forensic Process. http: //www. rcmpgrc. gc. ca/tsb/pubs/bulletins/bull 41_3. htm Lance Spitzner’s Page: Forensic Analysis, Building Honeypots http: //www. enteract. com/~lspitz/pubs. html Fish. com Security’s Forensic Page: The Coroner’s Toolkit (Unix), Computer Forensic Class Handouts. http: //www. fish. com/forensics/ The Forensic Toolkit (NT). http: //www. ntobjectives. com/forensic. htm Cryptcat. http: //www. farm 9. com/Free_Tools/Cryptcat Long Play Video Recorders. http: //www. pimall. com/nais/vrec. html FBI Handbook of Forensic Services. http: //www. fbi. gov/programs/lab/handbook/intro. htm Solaris Fingerprint Database for cryptographic comparison of system binaries. http: //sunsolve. sun. com/pub-cgi/file. Fingerprints. pl Inspecting Your Solaris System and Network Logs for Evidence of Intrusion. http: //www. cert. org/security-improvement/implementations/i 003. 01. html ONCTek List of possible Trojan/Backdoor Activity http: //www. onctek. com/trojanports. html Sixteen Tips for Testifying in Court from the “PI Mall” http: //www. pimall. com/nais/n. testify. html
 Thank you … … very much.
Thank you … … very much.


