6c58afdfdef1ae9cf85b6fe87700312a.ppt
- Количество слайдов: 165
 Computer Forensics Network Protocols Overview for Network Forensics
Computer Forensics Network Protocols Overview for Network Forensics
 Focus of this presentation Protocols With a few anecdotes, how-to-dos and previews thrown in.
Focus of this presentation Protocols With a few anecdotes, how-to-dos and previews thrown in.
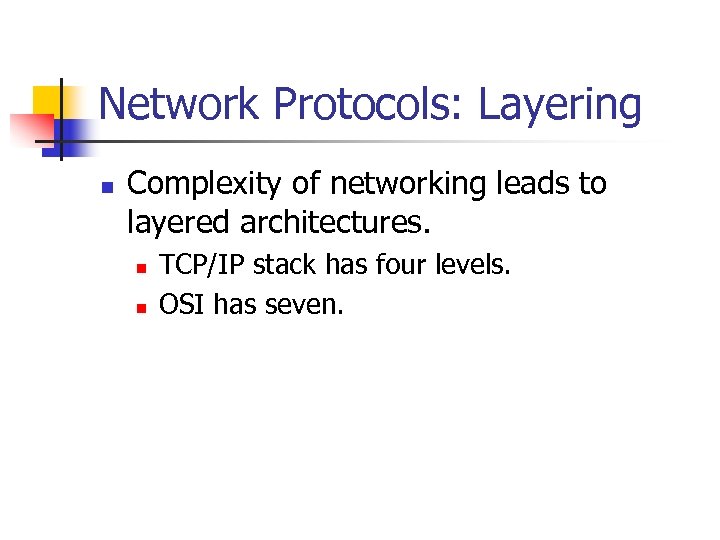 Network Protocols: Layering n Complexity of networking leads to layered architectures. n n TCP/IP stack has four levels. OSI has seven.
Network Protocols: Layering n Complexity of networking leads to layered architectures. n n TCP/IP stack has four levels. OSI has seven.
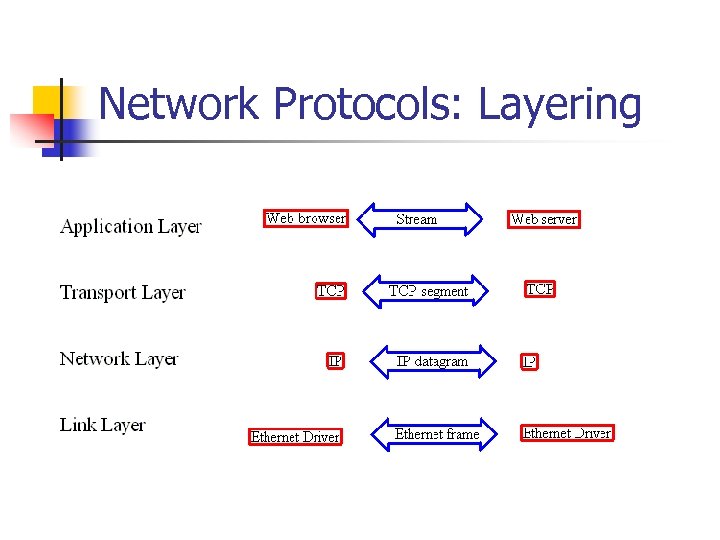 Network Protocols: Layering
Network Protocols: Layering
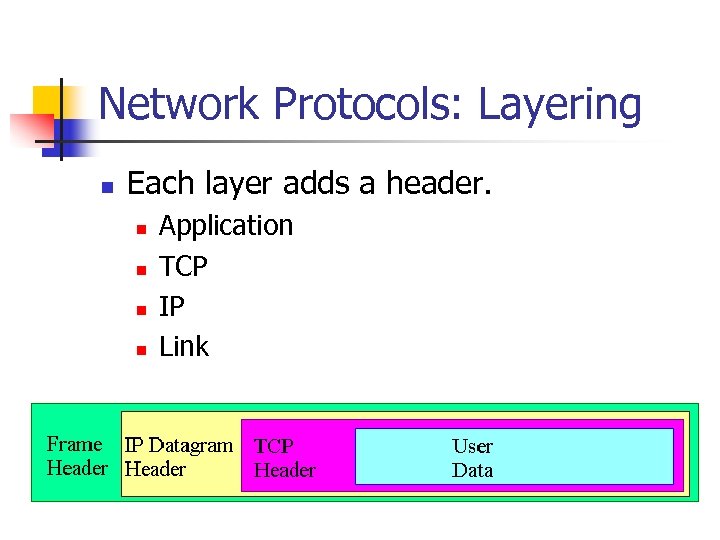 Network Protocols: Layering n Each layer adds a header. n n Application TCP IP Link
Network Protocols: Layering n Each layer adds a header. n n Application TCP IP Link
 Repetition: Capturing Data on a Network n Develop a threat model before deploying Network Security Monitoring n n n Internal / External Attacker Wireless / Wired / … Develop Monitoring zoning n n n Demilitarized zone Wireless zone Intranet zones
Repetition: Capturing Data on a Network n Develop a threat model before deploying Network Security Monitoring n n n Internal / External Attacker Wireless / Wired / … Develop Monitoring zoning n n n Demilitarized zone Wireless zone Intranet zones
 Repetition: Capturing Data on a Network n Wired monitoring n n Hubs SPAN ports Taps Inline devices
Repetition: Capturing Data on a Network n Wired monitoring n n Hubs SPAN ports Taps Inline devices
 Repetition: Capturing Data on a Network n Hubs n n Broadcasts incoming data on all interfaces. Be careful about NIC capacity (10/1000 Mb/sec) Be careful about hub quality Are inexpensive, but can introduce collisions on the links where the hub sits.
Repetition: Capturing Data on a Network n Hubs n n Broadcasts incoming data on all interfaces. Be careful about NIC capacity (10/1000 Mb/sec) Be careful about hub quality Are inexpensive, but can introduce collisions on the links where the hub sits.
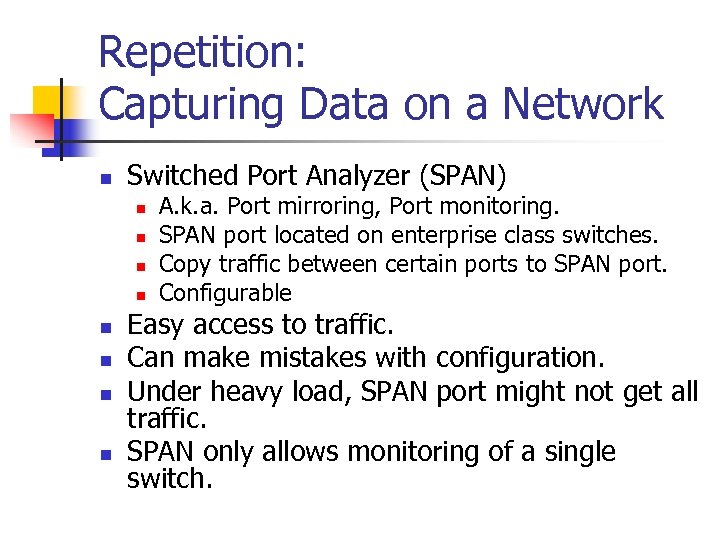 Repetition: Capturing Data on a Network n Switched Port Analyzer (SPAN) n n n n A. k. a. Port mirroring, Port monitoring. SPAN port located on enterprise class switches. Copy traffic between certain ports to SPAN port. Configurable Easy access to traffic. Can make mistakes with configuration. Under heavy load, SPAN port might not get all traffic. SPAN only allows monitoring of a single switch.
Repetition: Capturing Data on a Network n Switched Port Analyzer (SPAN) n n n n A. k. a. Port mirroring, Port monitoring. SPAN port located on enterprise class switches. Copy traffic between certain ports to SPAN port. Configurable Easy access to traffic. Can make mistakes with configuration. Under heavy load, SPAN port might not get all traffic. SPAN only allows monitoring of a single switch.
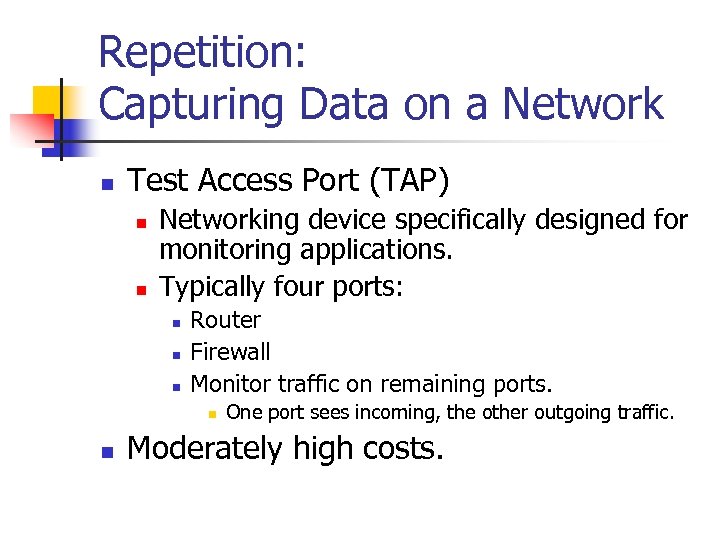 Repetition: Capturing Data on a Network n Test Access Port (TAP) n n Networking device specifically designed for monitoring applications. Typically four ports: n n n Router Firewall Monitor traffic on remaining ports. n n One port sees incoming, the other outgoing traffic. Moderately high costs.
Repetition: Capturing Data on a Network n Test Access Port (TAP) n n Networking device specifically designed for monitoring applications. Typically four ports: n n n Router Firewall Monitor traffic on remaining ports. n n One port sees incoming, the other outgoing traffic. Moderately high costs.
 Repetition: Capturing Data on a Network n Specialized inline devices: n Server or hardware device n Filtering bridges n Server with Open. BSD and two NICs
Repetition: Capturing Data on a Network n Specialized inline devices: n Server or hardware device n Filtering bridges n Server with Open. BSD and two NICs
 Link Layer n Network Interface Cards (NIC) n n Format 48 b written as twelve hex bytes. n n n Unique Medium Access Control (MAC) number First 6 identify vendor. Last 6 serial number. NICs either select based on MAC address or are in promiscuous mode (capture every packet).
Link Layer n Network Interface Cards (NIC) n n Format 48 b written as twelve hex bytes. n n n Unique Medium Access Control (MAC) number First 6 identify vendor. Last 6 serial number. NICs either select based on MAC address or are in promiscuous mode (capture every packet).
 Link Layer n n n Address Resolution Protocol (ARP) Resolves IP addresses to MAC addresses RFC 826
Link Layer n n n Address Resolution Protocol (ARP) Resolves IP addresses to MAC addresses RFC 826
 Link Layer: ARP Resolution Protocol n n Assume node A with IP address 10. 10. 100 and MAC 00: 01: 02: 03: 04: 05 wants to talk to IP address 10. 10. 101. Sends out a broadcast who-has request: 00: 01: 02: 03: 04: 05; ff: ff: ff: ff; arp 42 who-has 10. 10. 101 n n All devices on the link capture the packet and pass it to the IP layer. 10. 101 is the only one to answer: a 0: a 0; 00: 01: 02: 03: 04: 05; arp 64; arp reply 10. 10. 101 is-at a 0: a 0: a 0 n A caches the value in its arp cache.
Link Layer: ARP Resolution Protocol n n Assume node A with IP address 10. 10. 100 and MAC 00: 01: 02: 03: 04: 05 wants to talk to IP address 10. 10. 101. Sends out a broadcast who-has request: 00: 01: 02: 03: 04: 05; ff: ff: ff: ff; arp 42 who-has 10. 10. 101 n n All devices on the link capture the packet and pass it to the IP layer. 10. 101 is the only one to answer: a 0: a 0; 00: 01: 02: 03: 04: 05; arp 64; arp reply 10. 10. 101 is-at a 0: a 0: a 0 n A caches the value in its arp cache.
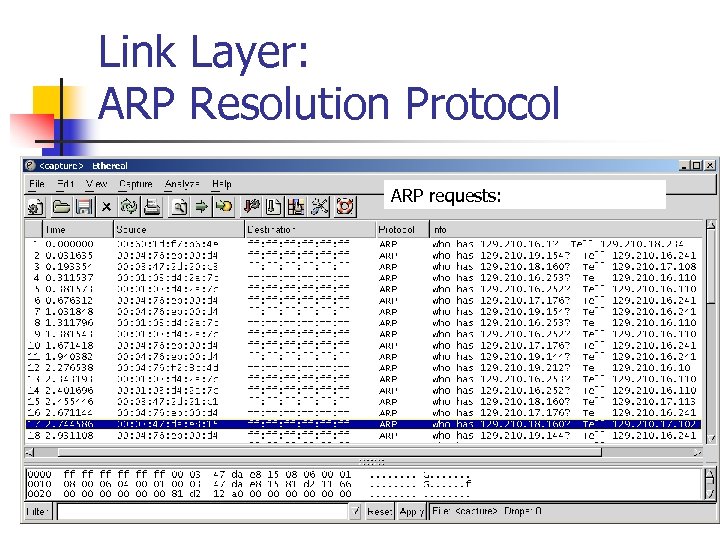 Link Layer: ARP Resolution Protocol ARP requests:
Link Layer: ARP Resolution Protocol ARP requests:
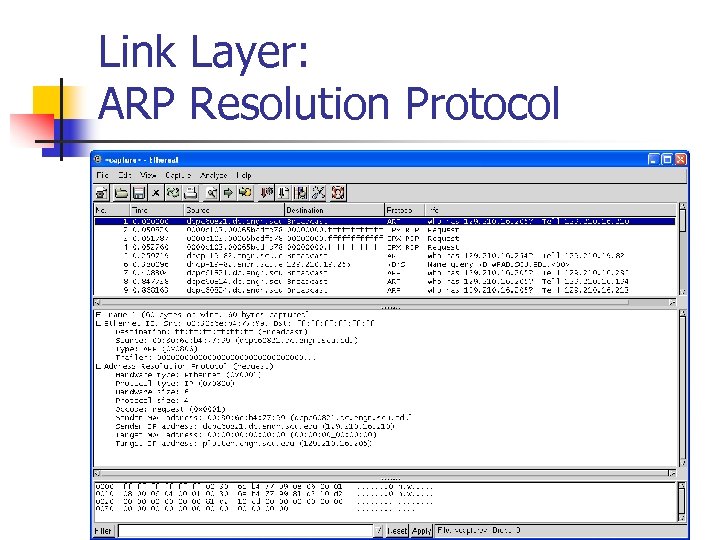 Link Layer: ARP Resolution Protocol
Link Layer: ARP Resolution Protocol
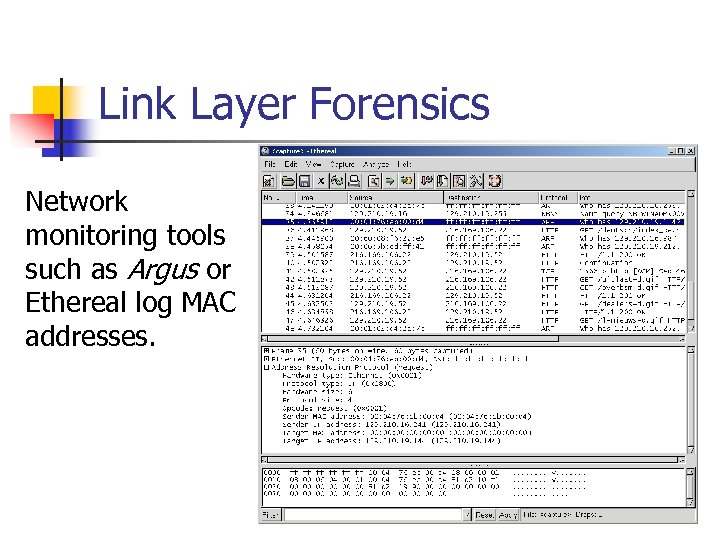 Link Layer Forensics Network monitoring tools such as Argus or Ethereal log MAC addresses.
Link Layer Forensics Network monitoring tools such as Argus or Ethereal log MAC addresses.
 Link Layer Forensics Example: Spike in network traffic comes from a computer with a certain IP address. However, Argus logs reveal that the traffic comes from a computer with a different MAC then the computer assigned that IP. (Spoofing) Finally, intrusion response finds the computer with that MAC, a Linux laptop that has been compromised and is used for a Denial of Service attack.
Link Layer Forensics Example: Spike in network traffic comes from a computer with a certain IP address. However, Argus logs reveal that the traffic comes from a computer with a different MAC then the computer assigned that IP. (Spoofing) Finally, intrusion response finds the computer with that MAC, a Linux laptop that has been compromised and is used for a Denial of Service attack.
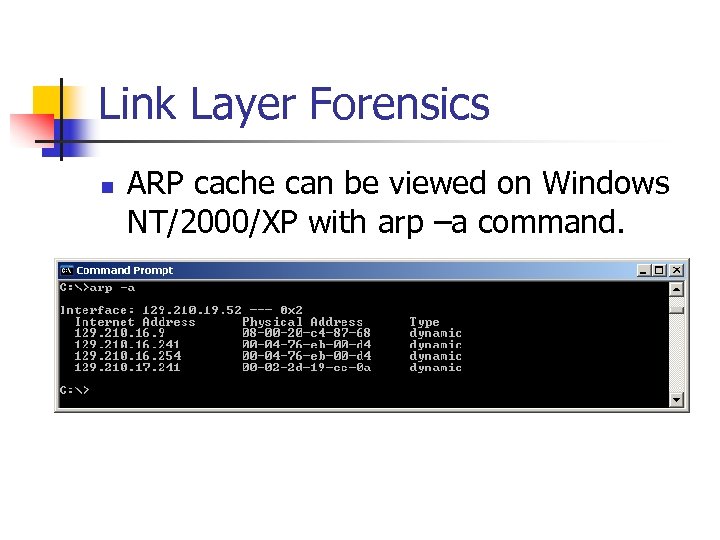 Link Layer Forensics n ARP cache can be viewed on Windows NT/2000/XP with arp –a command.
Link Layer Forensics n ARP cache can be viewed on Windows NT/2000/XP with arp –a command.
 ATM n n n n uses fiber optic cables and ATM switches. encapsulates data into ATM cells. number identifies the circuit that ATM has established between two computers. ATMARP allows machines to discover MAC addresses. n n ATMARP has a central server that responds to ARP requests. ATM forensics is similar.
ATM n n n n uses fiber optic cables and ATM switches. encapsulates data into ATM cells. number identifies the circuit that ATM has established between two computers. ATMARP allows machines to discover MAC addresses. n n ATMARP has a central server that responds to ARP requests. ATM forensics is similar.
 Link Layer Evidence n n Sniffers in promiscuous mode. Intruders also use sniffers. n n n Intruders sometimes encrypt their traffic. n n Typically monitor traffic to / from compromised system. Sometimes they monitor themselves coming back to look at the sniffer logs. But the sniffers still see the packets, they just cannot read them. Installing sniffers can violate the wire-tapping and other laws and is resource-intensive. n Free. BSD / Open. BSD seem to be the best platforms.
Link Layer Evidence n n Sniffers in promiscuous mode. Intruders also use sniffers. n n n Intruders sometimes encrypt their traffic. n n Typically monitor traffic to / from compromised system. Sometimes they monitor themselves coming back to look at the sniffer logs. But the sniffers still see the packets, they just cannot read them. Installing sniffers can violate the wire-tapping and other laws and is resource-intensive. n Free. BSD / Open. BSD seem to be the best platforms.
 Link Layer Evidence n Sniffer location: n On compromised machine. n n n Evidence not trustworthy. Nearby host. Switched Port Analyzer (SPAN) n n n Copies network traffic from one switch port to another Only copy valid ethernet packets. Do not duplicate all error information. Copying process has lower priority and some packets might not be mirrored. Misses out on traffic on the local link.
Link Layer Evidence n Sniffer location: n On compromised machine. n n n Evidence not trustworthy. Nearby host. Switched Port Analyzer (SPAN) n n n Copies network traffic from one switch port to another Only copy valid ethernet packets. Do not duplicate all error information. Copying process has lower priority and some packets might not be mirrored. Misses out on traffic on the local link.
 Link Layer Evidence n Sniffer configuration n n Can capture entire frames. Or only first part. n Tcpdump default setting.
Link Layer Evidence n Sniffer configuration n n Can capture entire frames. Or only first part. n Tcpdump default setting.
 Link Layer Evidence n n Some organizations log ARP information. Routers keep ARP tables. n n n show ip arp All hosts keep ARP tables. DHCP often assigns addresses only to computers with known MAC.
Link Layer Evidence n n Some organizations log ARP information. Routers keep ARP tables. n n n show ip arp All hosts keep ARP tables. DHCP often assigns addresses only to computers with known MAC.
 Link Layer Evidence An employee received harassing e-mail from a host on the employer’s network with IP address 192. 168. 1. 65. DHCP server database showed that this IP was assigned to a computer with MAC address 00: 48: 5 c: 3 a: 6 c. This MAC belonged to a network printer. The router’s ARP table showed that the IP address 192. 168. 1. 65. was used by a computer with MAC 00: 30: 65: 4 b: 2 a: 5 c. (IP-spoofing) Although this MAC was not on the organization’s list, there were only a few Apple computers on the network and the culprit was soon found.
Link Layer Evidence An employee received harassing e-mail from a host on the employer’s network with IP address 192. 168. 1. 65. DHCP server database showed that this IP was assigned to a computer with MAC address 00: 48: 5 c: 3 a: 6 c. This MAC belonged to a network printer. The router’s ARP table showed that the IP address 192. 168. 1. 65. was used by a computer with MAC 00: 30: 65: 4 b: 2 a: 5 c. (IP-spoofing) Although this MAC was not on the organization’s list, there were only a few Apple computers on the network and the culprit was soon found.
 Link Layer Evidence n Analyze and filter log files: n Keyword searches n n E. g. for USER, PASS, login Nicknames, channel names Filters Reconstruction n E. g. contents of web-mail inbox.
Link Layer Evidence n Analyze and filter log files: n Keyword searches n n E. g. for USER, PASS, login Nicknames, channel names Filters Reconstruction n E. g. contents of web-mail inbox.
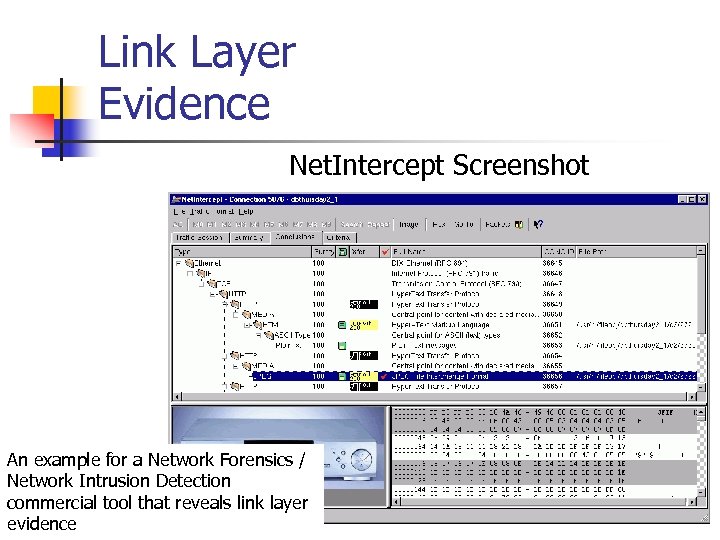 Link Layer Evidence Net. Intercept Screenshot An example for a Network Forensics / Network Intrusion Detection commercial tool that reveals link layer evidence
Link Layer Evidence Net. Intercept Screenshot An example for a Network Forensics / Network Intrusion Detection commercial tool that reveals link layer evidence
 ARP Package n n RFC 826 ARP package : n n n n n 0 -1: Hardware type (0 x 0001 – Ethernet) 2 -3: Protocol type (0 x 0800 – IP) 4: Number of bytes in hardware address (6 for MAC) 5: Number of bytes in protocol address (4 for IP) 6 -7: Opcode: 1 for ARP request, 2 for an ARP reply 8 -13: Source MAC 14 -17: Source IP 18 -23: Target MAC 24 -27: Target IP
ARP Package n n RFC 826 ARP package : n n n n n 0 -1: Hardware type (0 x 0001 – Ethernet) 2 -3: Protocol type (0 x 0800 – IP) 4: Number of bytes in hardware address (6 for MAC) 5: Number of bytes in protocol address (4 for IP) 6 -7: Opcode: 1 for ARP request, 2 for an ARP reply 8 -13: Source MAC 14 -17: Source IP 18 -23: Target MAC 24 -27: Target IP
 ARP Package Ethereal deassembly of ARP package
ARP Package Ethereal deassembly of ARP package
 Monitoring Tools n Arpwatch n monitors ethernet activity and keeps a database of ethernet/ip address pairings.
Monitoring Tools n Arpwatch n monitors ethernet activity and keeps a database of ethernet/ip address pairings.
 Attacks on ARP n Package Generators for various OS. n Allow an attacker to subvert a chosen protocol n n hping 2 for Windows. *NIX, XWindows: n n packit n http: //sourceforge. net/projects/packitgui/ IP Sorcery and many, many more. Use to create arbitrary packages
Attacks on ARP n Package Generators for various OS. n Allow an attacker to subvert a chosen protocol n n hping 2 for Windows. *NIX, XWindows: n n packit n http: //sourceforge. net/projects/packitgui/ IP Sorcery and many, many more. Use to create arbitrary packages
 Attacks on ARP n Switch Flooding n Switches contain a switch address table. n n n Switch address table associates ports with MAC addresses. Switch flooding creates many false entries. Switches fail in two different modes: n Fail open: n n Switch converts into a hub. n This allows to monitor traffic through the switch from any port. Fail closed: n Switch stops functioning. n Denial of Service (Do. S) attack
Attacks on ARP n Switch Flooding n Switches contain a switch address table. n n n Switch address table associates ports with MAC addresses. Switch flooding creates many false entries. Switches fail in two different modes: n Fail open: n n Switch converts into a hub. n This allows to monitor traffic through the switch from any port. Fail closed: n Switch stops functioning. n Denial of Service (Do. S) attack
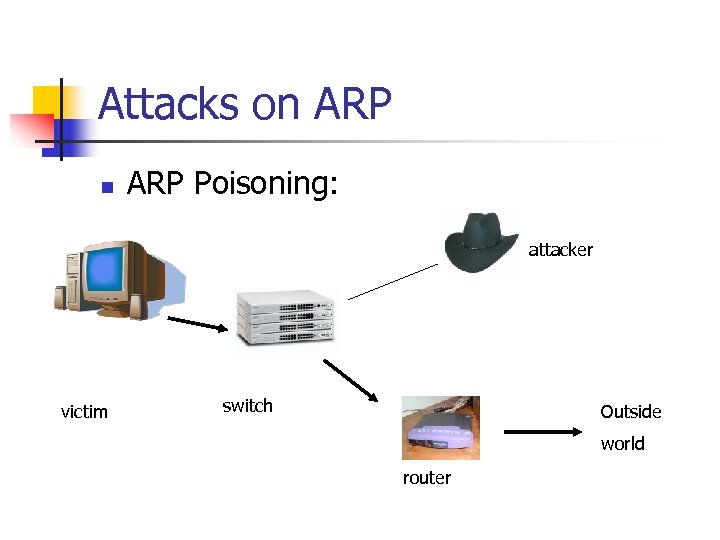 Attacks on ARP Poisoning: attacker victim switch Outside world router
Attacks on ARP Poisoning: attacker victim switch Outside world router
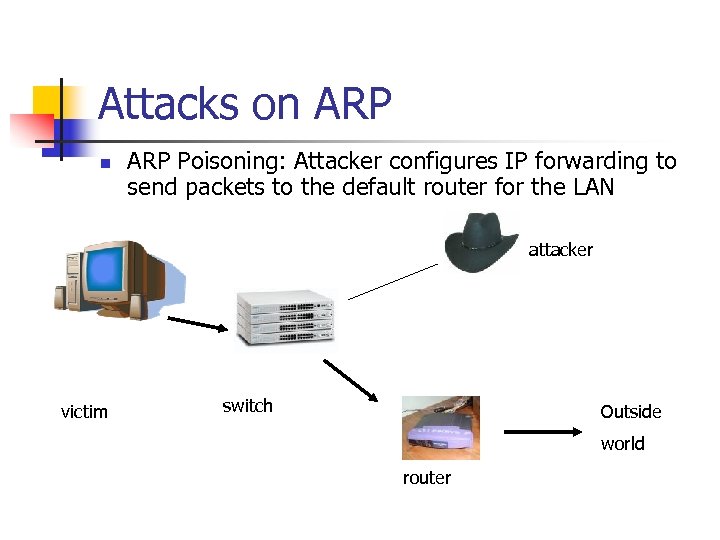 Attacks on ARP Poisoning: Attacker configures IP forwarding to send packets to the default router for the LAN attacker victim switch Outside world router
Attacks on ARP Poisoning: Attacker configures IP forwarding to send packets to the default router for the LAN attacker victim switch Outside world router
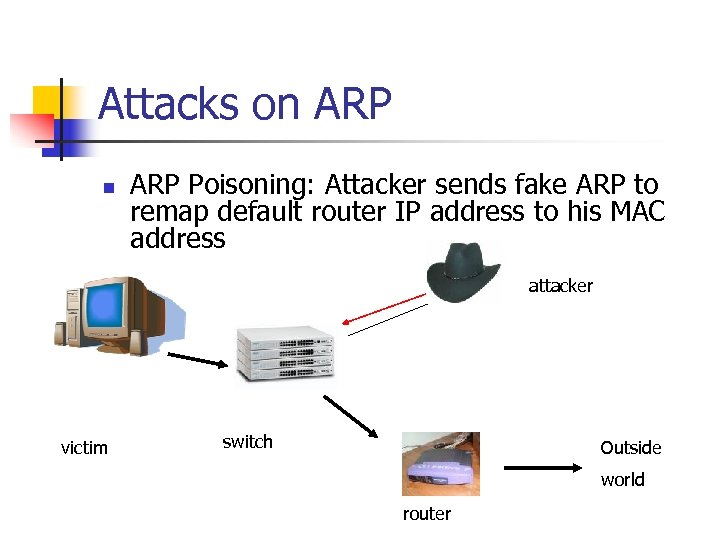 Attacks on ARP Poisoning: Attacker sends fake ARP to remap default router IP address to his MAC address attacker victim switch Outside world router
Attacks on ARP Poisoning: Attacker sends fake ARP to remap default router IP address to his MAC address attacker victim switch Outside world router
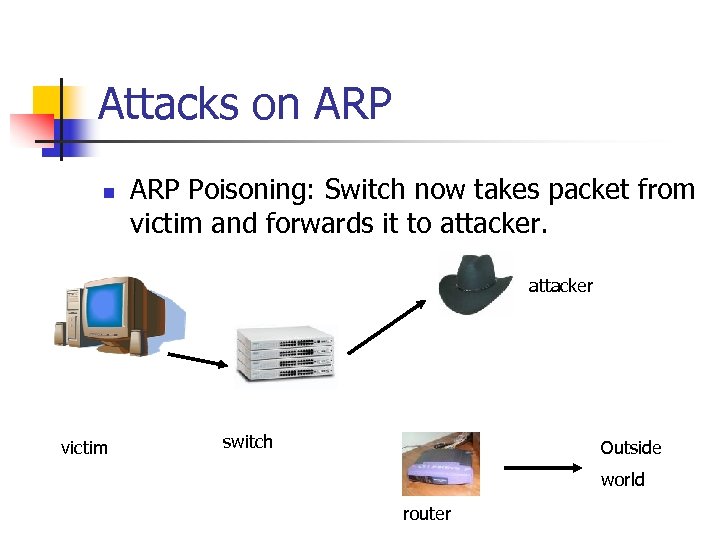 Attacks on ARP Poisoning: Switch now takes packet from victim and forwards it to attacker victim switch Outside world router
Attacks on ARP Poisoning: Switch now takes packet from victim and forwards it to attacker victim switch Outside world router
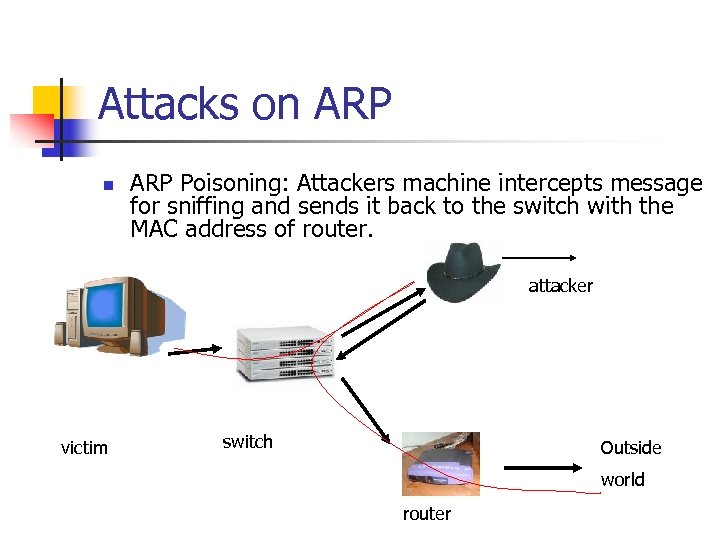 Attacks on ARP Poisoning: Attackers machine intercepts message for sniffing and sends it back to the switch with the MAC address of router. attacker victim switch Outside world router
Attacks on ARP Poisoning: Attackers machine intercepts message for sniffing and sends it back to the switch with the MAC address of router. attacker victim switch Outside world router
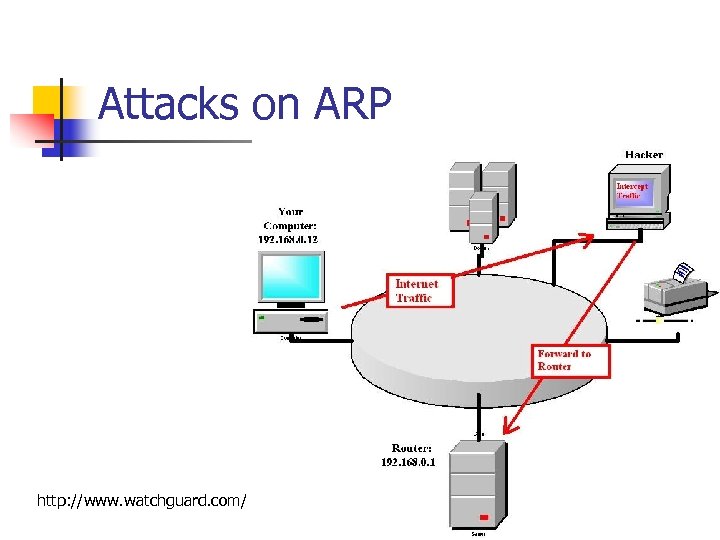 Attacks on ARP http: //www. watchguard. com/
Attacks on ARP http: //www. watchguard. com/
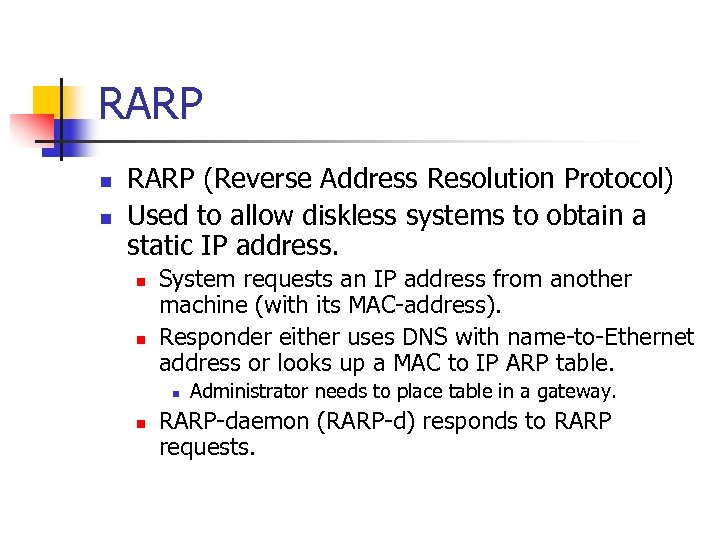 RARP n n RARP (Reverse Address Resolution Protocol) Used to allow diskless systems to obtain a static IP address. n n System requests an IP address from another machine (with its MAC-address). Responder either uses DNS with name-to-Ethernet address or looks up a MAC to IP ARP table. n n Administrator needs to place table in a gateway. RARP-daemon (RARP-d) responds to RARP requests.
RARP n n RARP (Reverse Address Resolution Protocol) Used to allow diskless systems to obtain a static IP address. n n System requests an IP address from another machine (with its MAC-address). Responder either uses DNS with name-to-Ethernet address or looks up a MAC to IP ARP table. n n Administrator needs to place table in a gateway. RARP-daemon (RARP-d) responds to RARP requests.
 RARP n RARP vulnerability n Use RARP together with ARP spoofing to request an IP address and take part in communications over the network.
RARP n RARP vulnerability n Use RARP together with ARP spoofing to request an IP address and take part in communications over the network.
 RARP Package n Package Format as in ARP: n n n n n 0 -1: Hardware type (0 x 0001 – Ethernet) 2 -3: Protocol type (0 x 0800 – IP) 4: Number of bytes in hardware address (6 for MAC) 5: Number of bytes in protocol address (4 for IP) 6 -7: Opcode: 1 for ARP request, 2 for an ARP reply 8 -13: Source MAC 14 -17: Source IP 18 -23: Target MAC 24 -27: Target IP
RARP Package n Package Format as in ARP: n n n n n 0 -1: Hardware type (0 x 0001 – Ethernet) 2 -3: Protocol type (0 x 0800 – IP) 4: Number of bytes in hardware address (6 for MAC) 5: Number of bytes in protocol address (4 for IP) 6 -7: Opcode: 1 for ARP request, 2 for an ARP reply 8 -13: Source MAC 14 -17: Source IP 18 -23: Target MAC 24 -27: Target IP
 IP n n Uses IP addresses of source and destination. IP datagrams are moved from hop to hop. “Best Effort” service. Corrupted datagrams are detected and dropped.
IP n n Uses IP addresses of source and destination. IP datagrams are moved from hop to hop. “Best Effort” service. Corrupted datagrams are detected and dropped.
 IP n n n Addresses contain IP address and port number. IPv 4 addresses are 32 bit longs IPv 6 addresses are 8*16 bits long.
IP n n n Addresses contain IP address and port number. IPv 4 addresses are 32 bit longs IPv 6 addresses are 8*16 bits long.
 IP: ICMP n n Internet Control Message Protocol Created to deal with non-transient problems. For example n n n Fragmentation is necessary, but the No Frag flag is set. UPD datagram sent to a non-listening port. Ping. n n Used to detect network connectivity before it became too useful for attack reconnaissance. Does not use ports. Allows broadcasting. More on ICMP later
IP: ICMP n n Internet Control Message Protocol Created to deal with non-transient problems. For example n n n Fragmentation is necessary, but the No Frag flag is set. UPD datagram sent to a non-listening port. Ping. n n Used to detect network connectivity before it became too useful for attack reconnaissance. Does not use ports. Allows broadcasting. More on ICMP later
 IP: ICMP n ICMP error messages should not be sent: n n For any but the first fragment. A source address of broadcast or loopback address. n n Are probably malicious, anyway. Otherwise: ICMP messages could proliferate and throttle a network
IP: ICMP n ICMP error messages should not be sent: n n For any but the first fragment. A source address of broadcast or loopback address. n n Are probably malicious, anyway. Otherwise: ICMP messages could proliferate and throttle a network
 IP: ICMP n ICMP errors are not sent: n In response to an ICMP error message. n n Otherwise, craft a message with invalid UDP source and destination port. Then watch ICMP ping-pong. A destination broadcast address. n Don’t answer with destination unreachable for a broadcast. Otherwise, this makes it trivial to scan a network.
IP: ICMP n ICMP errors are not sent: n In response to an ICMP error message. n n Otherwise, craft a message with invalid UDP source and destination port. Then watch ICMP ping-pong. A destination broadcast address. n Don’t answer with destination unreachable for a broadcast. Otherwise, this makes it trivial to scan a network.
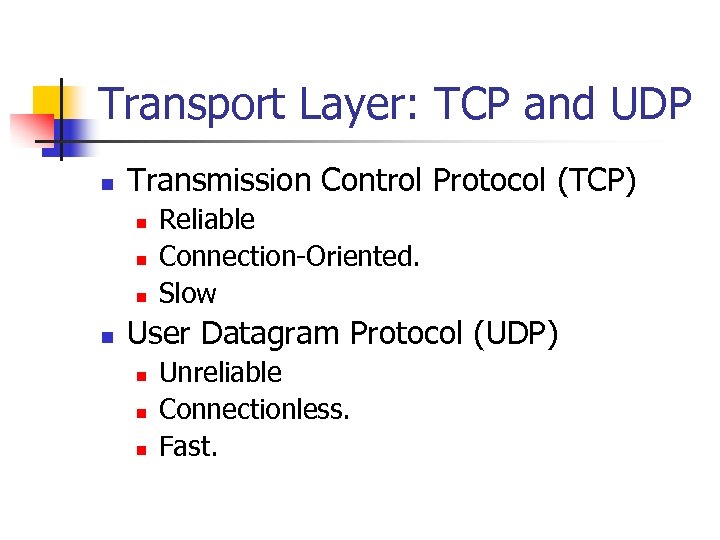 Transport Layer: TCP and UDP n Transmission Control Protocol (TCP) n n Reliable Connection-Oriented. Slow User Datagram Protocol (UDP) n n n Unreliable Connectionless. Fast.
Transport Layer: TCP and UDP n Transmission Control Protocol (TCP) n n Reliable Connection-Oriented. Slow User Datagram Protocol (UDP) n n n Unreliable Connectionless. Fast.
 TCP n n n Only supports unicasting. Full duplex connection. Message numbers to prevent loss of messages.
TCP n n n Only supports unicasting. Full duplex connection. Message numbers to prevent loss of messages.
 TCP: Three Way Handshake n n Initiator to responder: Syns Responder to initator: Acks, Synt Initiator to responder: Ackt Sets up two connections with initial message numbers s and t.
TCP: Three Way Handshake n n Initiator to responder: Syns Responder to initator: Acks, Synt Initiator to responder: Ackt Sets up two connections with initial message numbers s and t.
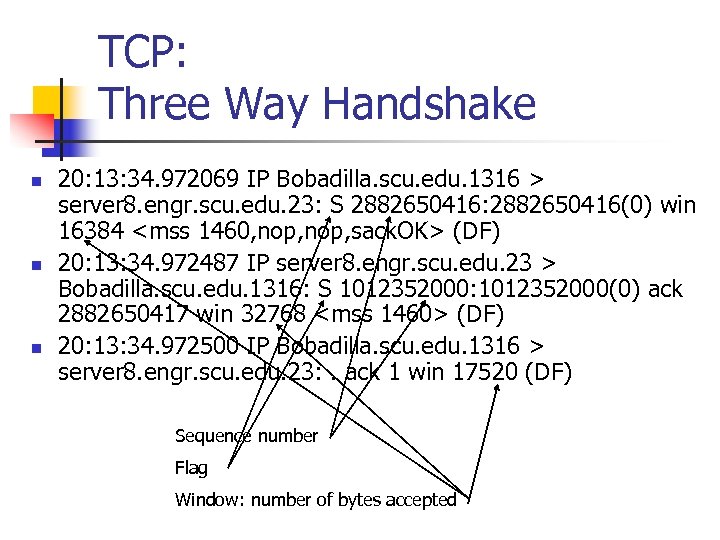 TCP: Three Way Handshake n n n 20: 13: 34. 972069 IP Bobadilla. scu. edu. 1316 > server 8. engr. scu. edu. 23: S 2882650416: 2882650416(0) win 16384
TCP: Three Way Handshake n n n 20: 13: 34. 972069 IP Bobadilla. scu. edu. 1316 > server 8. engr. scu. edu. 23: S 2882650416: 2882650416(0) win 16384
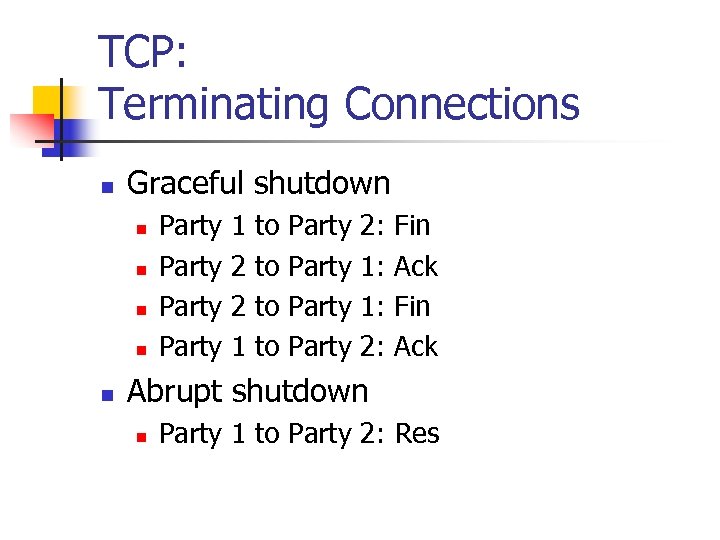 TCP: Terminating Connections n Graceful shutdown n n Party 1 2 2 1 to to Party 2: 1: 1: 2: Fin Ack Abrupt shutdown n Party 1 to Party 2: Res
TCP: Terminating Connections n Graceful shutdown n n Party 1 2 2 1 to to Party 2: 1: 1: 2: Fin Ack Abrupt shutdown n Party 1 to Party 2: Res
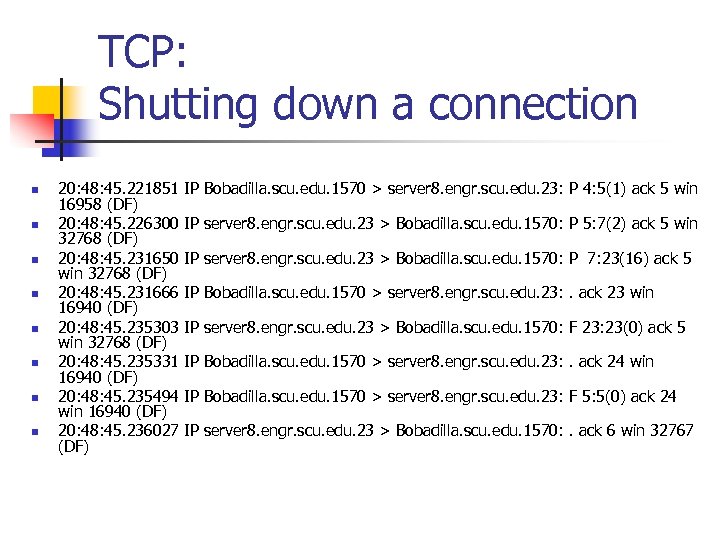 TCP: Shutting down a connection n n n n 20: 48: 45. 221851 16958 (DF) 20: 48: 45. 226300 32768 (DF) 20: 48: 45. 231650 win 32768 (DF) 20: 48: 45. 231666 16940 (DF) 20: 48: 45. 235303 win 32768 (DF) 20: 48: 45. 235331 16940 (DF) 20: 48: 45. 235494 win 16940 (DF) 20: 48: 45. 236027 (DF) IP Bobadilla. scu. edu. 1570 > server 8. engr. scu. edu. 23: P 4: 5(1) ack 5 win IP server 8. engr. scu. edu. 23 > Bobadilla. scu. edu. 1570: P 5: 7(2) ack 5 win IP server 8. engr. scu. edu. 23 > Bobadilla. scu. edu. 1570: P 7: 23(16) ack 5 IP Bobadilla. scu. edu. 1570 > server 8. engr. scu. edu. 23: . ack 23 win IP server 8. engr. scu. edu. 23 > Bobadilla. scu. edu. 1570: F 23: 23(0) ack 5 IP Bobadilla. scu. edu. 1570 > server 8. engr. scu. edu. 23: . ack 24 win IP Bobadilla. scu. edu. 1570 > server 8. engr. scu. edu. 23: F 5: 5(0) ack 24 IP server 8. engr. scu. edu. 23 > Bobadilla. scu. edu. 1570: . ack 6 win 32767
TCP: Shutting down a connection n n n n 20: 48: 45. 221851 16958 (DF) 20: 48: 45. 226300 32768 (DF) 20: 48: 45. 231650 win 32768 (DF) 20: 48: 45. 231666 16940 (DF) 20: 48: 45. 235303 win 32768 (DF) 20: 48: 45. 235331 16940 (DF) 20: 48: 45. 235494 win 16940 (DF) 20: 48: 45. 236027 (DF) IP Bobadilla. scu. edu. 1570 > server 8. engr. scu. edu. 23: P 4: 5(1) ack 5 win IP server 8. engr. scu. edu. 23 > Bobadilla. scu. edu. 1570: P 5: 7(2) ack 5 win IP server 8. engr. scu. edu. 23 > Bobadilla. scu. edu. 1570: P 7: 23(16) ack 5 IP Bobadilla. scu. edu. 1570 > server 8. engr. scu. edu. 23: . ack 23 win IP server 8. engr. scu. edu. 23 > Bobadilla. scu. edu. 1570: F 23: 23(0) ack 5 IP Bobadilla. scu. edu. 1570 > server 8. engr. scu. edu. 23: . ack 24 win IP Bobadilla. scu. edu. 1570 > server 8. engr. scu. edu. 23: F 5: 5(0) ack 24 IP server 8. engr. scu. edu. 23 > Bobadilla. scu. edu. 1570: . ack 6 win 32767
 TCP Exchanging Data n Each packet has a sequence number. n n (One for each direction. ) Initial sequence numbers are created during initial three way handshake. n n NMap uses the creation of these sequence numbers to determine the OS. OS are now much better with truly random sequence numbers.
TCP Exchanging Data n Each packet has a sequence number. n n (One for each direction. ) Initial sequence numbers are created during initial three way handshake. n n NMap uses the creation of these sequence numbers to determine the OS. OS are now much better with truly random sequence numbers.
 TCP Exchanging Data n n Party that receives packet sends an acknowledgement. Acknowledgement consists in n Ack flag. Sequence number of the next package to be expected. (TCPDump shows number of bytes acknowledged).
TCP Exchanging Data n n Party that receives packet sends an acknowledgement. Acknowledgement consists in n Ack flag. Sequence number of the next package to be expected. (TCPDump shows number of bytes acknowledged).
 TCP Exchanging Data n If a package is lost, then the ack sequence number will not change: n n n “Duplicate acknowledgement” Depending on settings, sender will resend, after at most three stationary ack numbers. Also, senders resend after timeout.
TCP Exchanging Data n If a package is lost, then the ack sequence number will not change: n n n “Duplicate acknowledgement” Depending on settings, sender will resend, after at most three stationary ack numbers. Also, senders resend after timeout.
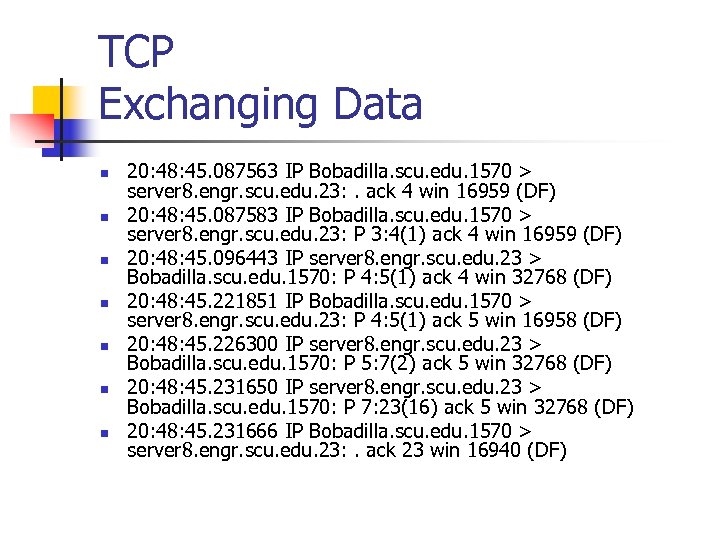 TCP Exchanging Data n n n n 20: 48: 45. 087563 IP Bobadilla. scu. edu. 1570 > server 8. engr. scu. edu. 23: . ack 4 win 16959 (DF) 20: 48: 45. 087583 IP Bobadilla. scu. edu. 1570 > server 8. engr. scu. edu. 23: P 3: 4(1) ack 4 win 16959 (DF) 20: 48: 45. 096443 IP server 8. engr. scu. edu. 23 > Bobadilla. scu. edu. 1570: P 4: 5(1) ack 4 win 32768 (DF) 20: 48: 45. 221851 IP Bobadilla. scu. edu. 1570 > server 8. engr. scu. edu. 23: P 4: 5(1) ack 5 win 16958 (DF) 20: 48: 45. 226300 IP server 8. engr. scu. edu. 23 > Bobadilla. scu. edu. 1570: P 5: 7(2) ack 5 win 32768 (DF) 20: 48: 45. 231650 IP server 8. engr. scu. edu. 23 > Bobadilla. scu. edu. 1570: P 7: 23(16) ack 5 win 32768 (DF) 20: 48: 45. 231666 IP Bobadilla. scu. edu. 1570 > server 8. engr. scu. edu. 23: . ack 23 win 16940 (DF)
TCP Exchanging Data n n n n 20: 48: 45. 087563 IP Bobadilla. scu. edu. 1570 > server 8. engr. scu. edu. 23: . ack 4 win 16959 (DF) 20: 48: 45. 087583 IP Bobadilla. scu. edu. 1570 > server 8. engr. scu. edu. 23: P 3: 4(1) ack 4 win 16959 (DF) 20: 48: 45. 096443 IP server 8. engr. scu. edu. 23 > Bobadilla. scu. edu. 1570: P 4: 5(1) ack 4 win 32768 (DF) 20: 48: 45. 221851 IP Bobadilla. scu. edu. 1570 > server 8. engr. scu. edu. 23: P 4: 5(1) ack 5 win 16958 (DF) 20: 48: 45. 226300 IP server 8. engr. scu. edu. 23 > Bobadilla. scu. edu. 1570: P 5: 7(2) ack 5 win 32768 (DF) 20: 48: 45. 231650 IP server 8. engr. scu. edu. 23 > Bobadilla. scu. edu. 1570: P 7: 23(16) ack 5 win 32768 (DF) 20: 48: 45. 231666 IP Bobadilla. scu. edu. 1570 > server 8. engr. scu. edu. 23: . ack 23 win 16940 (DF)
 TCP flags n Part of TCP header n n n n F : FIN - Finish; end of session S : SYN - Synchronize; indicates request to start session R : RST - Reset; drop a connection P : PUSH - Push; packet is sent immediately A : ACK - Acknowledgement U : URG - Urgent E : ECE - Explicit Congestion Notification Echo W : CWR - Congestion Window Reduced
TCP flags n Part of TCP header n n n n F : FIN - Finish; end of session S : SYN - Synchronize; indicates request to start session R : RST - Reset; drop a connection P : PUSH - Push; packet is sent immediately A : ACK - Acknowledgement U : URG - Urgent E : ECE - Explicit Congestion Notification Echo W : CWR - Congestion Window Reduced
 TCP Example with Ethereal
TCP Example with Ethereal
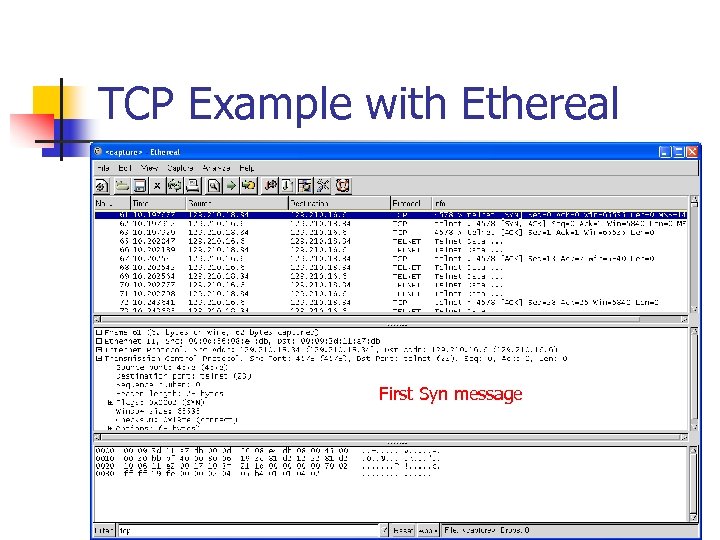 TCP Example with Ethereal First Syn message
TCP Example with Ethereal First Syn message
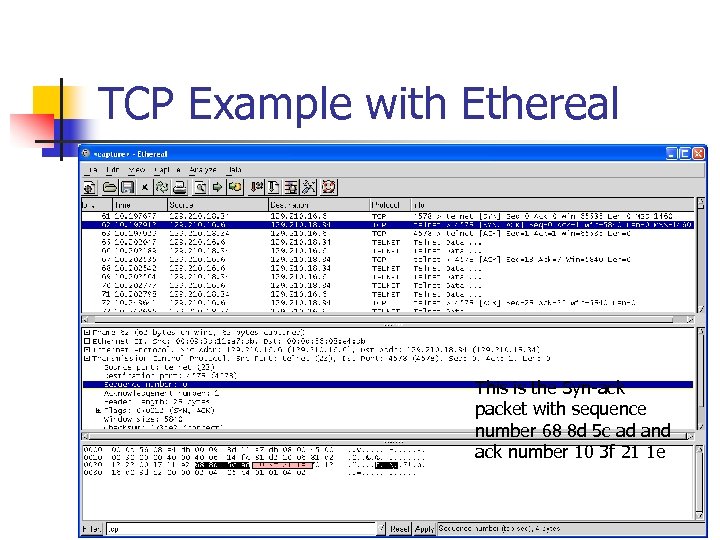 TCP Example with Ethereal This is the Syn-ack packet with sequence number 68 8 d 5 c ad and ack number 10 3 f 21 1 e
TCP Example with Ethereal This is the Syn-ack packet with sequence number 68 8 d 5 c ad and ack number 10 3 f 21 1 e
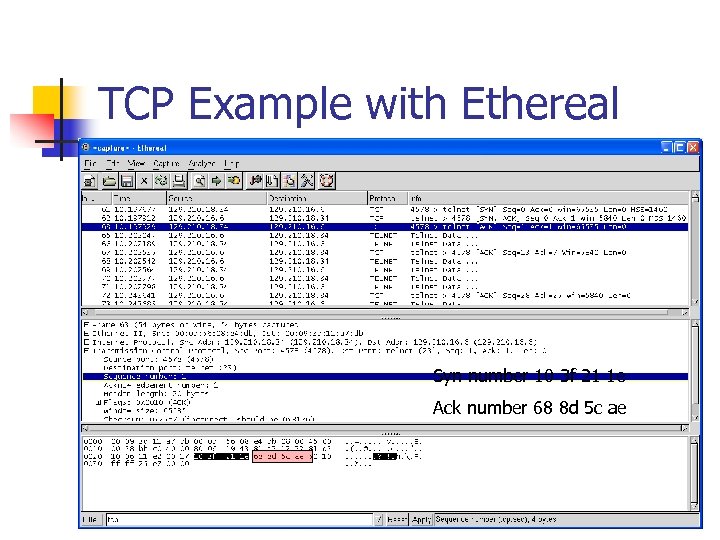 TCP Example with Ethereal Syn number 10 3 f 21 1 e Ack number 68 8 d 5 c ae
TCP Example with Ethereal Syn number 10 3 f 21 1 e Ack number 68 8 d 5 c ae
 TCP Example with Ethereal
TCP Example with Ethereal
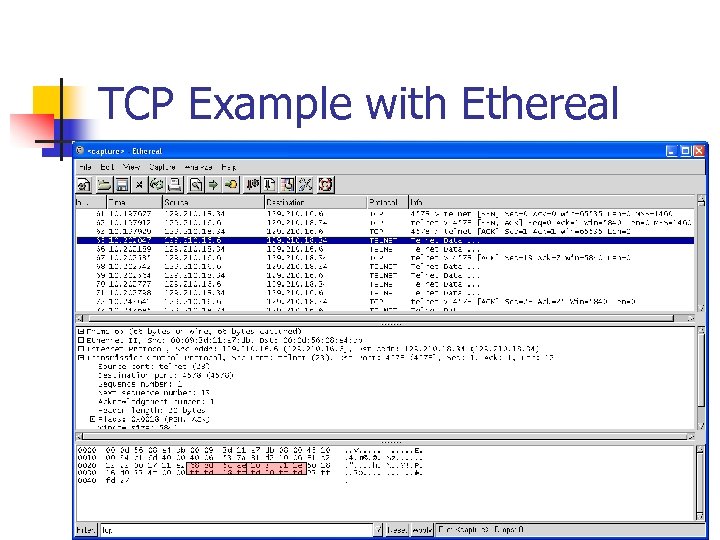 TCP Example with Ethereal
TCP Example with Ethereal
 UDP n n n “Send and pray” No connection. No special header like TCP. Protocol field in the IP header is 0 x 11 Another field in the IP header contains UDP specific header information
UDP n n n “Send and pray” No connection. No special header like TCP. Protocol field in the IP header is 0 x 11 Another field in the IP header contains UDP specific header information
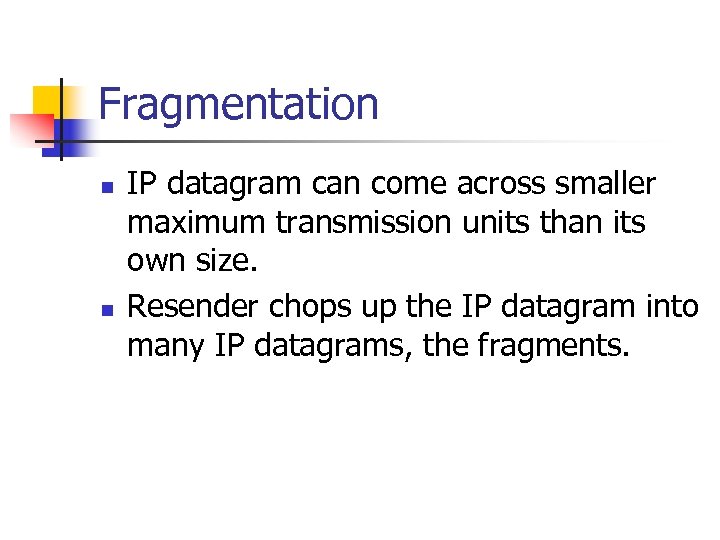 Fragmentation n n IP datagram can come across smaller maximum transmission units than its own size. Resender chops up the IP datagram into many IP datagrams, the fragments.
Fragmentation n n IP datagram can come across smaller maximum transmission units than its own size. Resender chops up the IP datagram into many IP datagrams, the fragments.
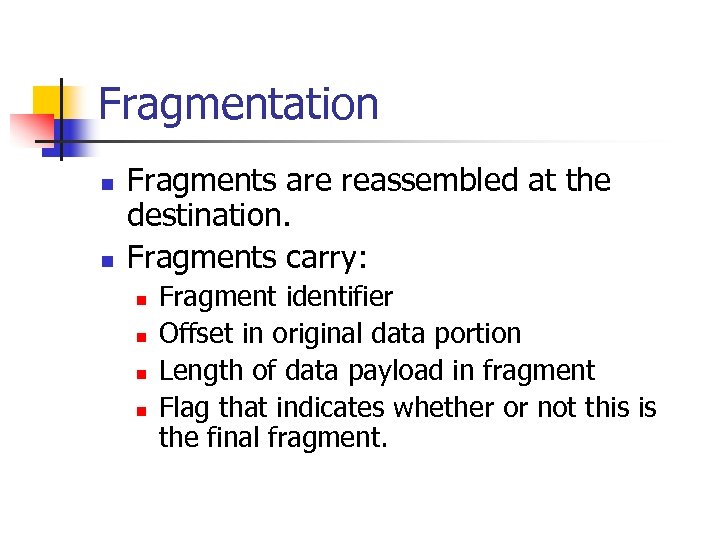 Fragmentation n n Fragments are reassembled at the destination. Fragments carry: n n Fragment identifier Offset in original data portion Length of data payload in fragment Flag that indicates whether or not this is the final fragment.
Fragmentation n n Fragments are reassembled at the destination. Fragments carry: n n Fragment identifier Offset in original data portion Length of data payload in fragment Flag that indicates whether or not this is the final fragment.
 Fragmentation Example n Large Echo Request n ping -l 1480 129. 218. 198 n Assume MTU is 1500
Fragmentation Example n Large Echo Request n ping -l 1480 129. 218. 198 n Assume MTU is 1500
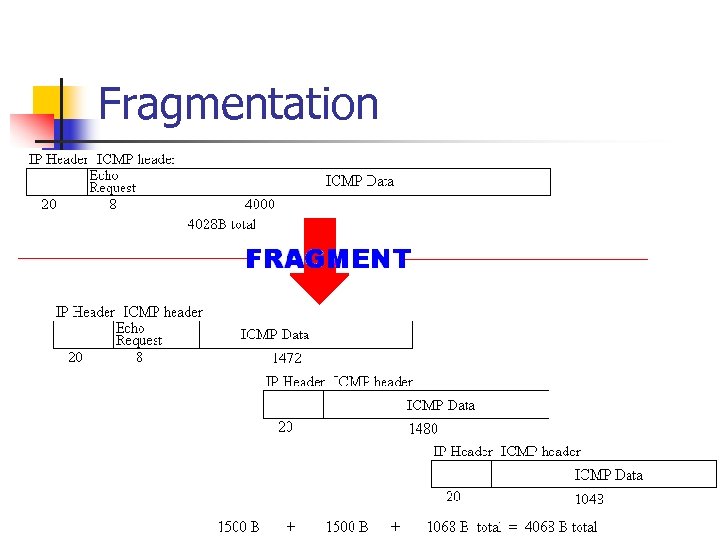 Fragmentation
Fragmentation
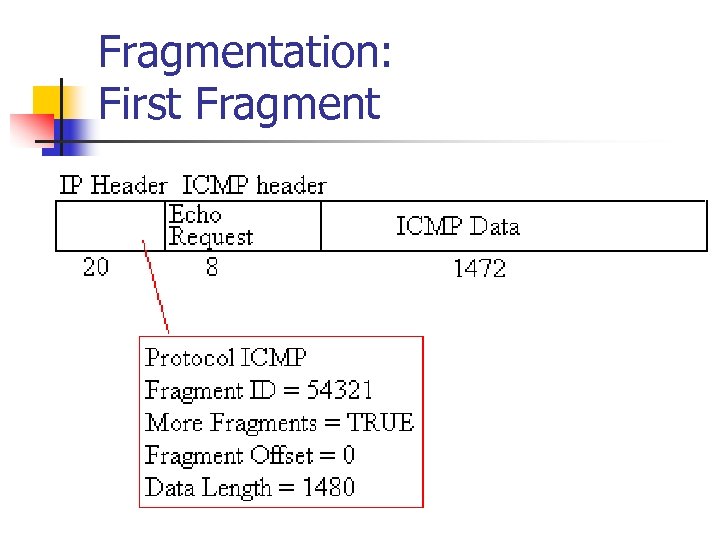 Fragmentation: First Fragment
Fragmentation: First Fragment
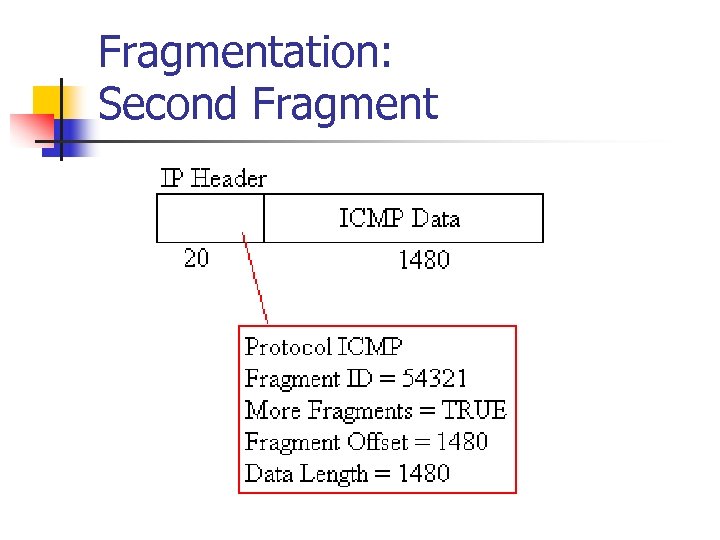 Fragmentation: Second Fragment
Fragmentation: Second Fragment
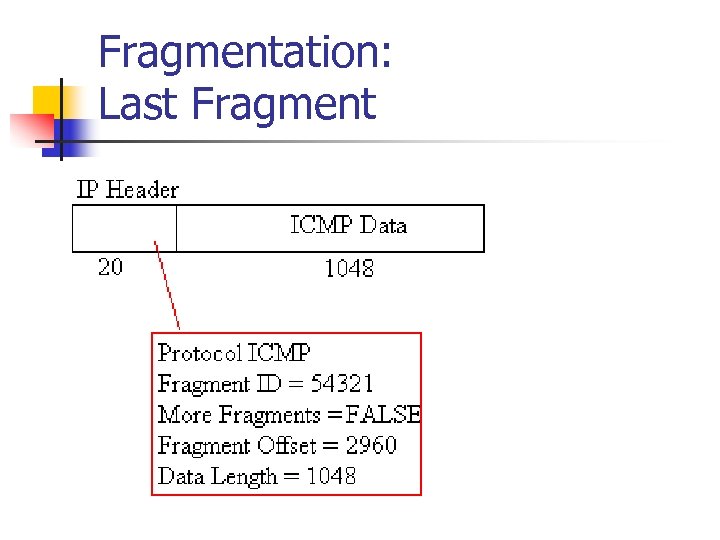 Fragmentation: Last Fragment
Fragmentation: Last Fragment
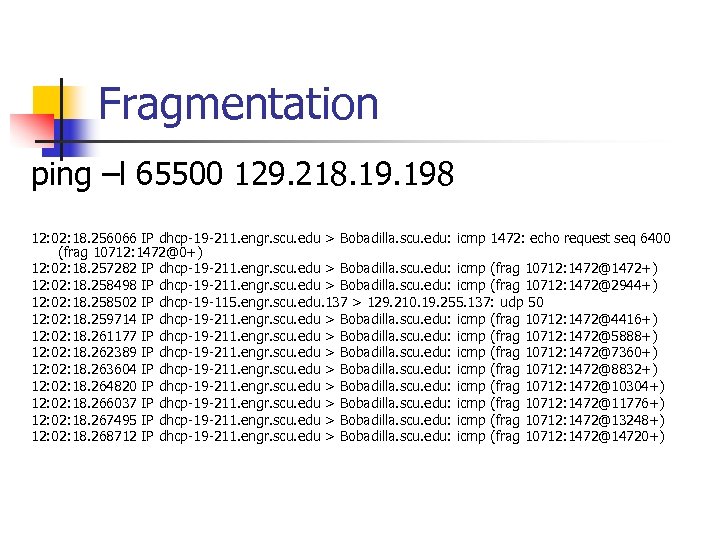 Fragmentation ping –l 65500 129. 218. 198 12: 02: 18. 256066 IP dhcp-19 -211. engr. scu. edu > Bobadilla. scu. edu: icmp 1472: echo request seq 6400 (frag 10712: 1472@0+) 12: 02: 18. 257282 IP dhcp-19 -211. engr. scu. edu > Bobadilla. scu. edu: icmp (frag 10712: 1472@1472+) 12: 02: 18. 258498 IP dhcp-19 -211. engr. scu. edu > Bobadilla. scu. edu: icmp (frag 10712: 1472@2944+) 12: 02: 18. 258502 IP dhcp-19 -115. engr. scu. edu. 137 > 129. 210. 19. 255. 137: udp 50 12: 02: 18. 259714 IP dhcp-19 -211. engr. scu. edu > Bobadilla. scu. edu: icmp (frag 10712: 1472@4416+) 12: 02: 18. 261177 IP dhcp-19 -211. engr. scu. edu > Bobadilla. scu. edu: icmp (frag 10712: 1472@5888+) 12: 02: 18. 262389 IP dhcp-19 -211. engr. scu. edu > Bobadilla. scu. edu: icmp (frag 10712: 1472@7360+) 12: 02: 18. 263604 IP dhcp-19 -211. engr. scu. edu > Bobadilla. scu. edu: icmp (frag 10712: 1472@8832+) 12: 02: 18. 264820 IP dhcp-19 -211. engr. scu. edu > Bobadilla. scu. edu: icmp (frag 10712: 1472@10304+) 12: 02: 18. 266037 IP dhcp-19 -211. engr. scu. edu > Bobadilla. scu. edu: icmp (frag 10712: 1472@11776+) 12: 02: 18. 267495 IP dhcp-19 -211. engr. scu. edu > Bobadilla. scu. edu: icmp (frag 10712: 1472@13248+) 12: 02: 18. 268712 IP dhcp-19 -211. engr. scu. edu > Bobadilla. scu. edu: icmp (frag 10712: 1472@14720+)
Fragmentation ping –l 65500 129. 218. 198 12: 02: 18. 256066 IP dhcp-19 -211. engr. scu. edu > Bobadilla. scu. edu: icmp 1472: echo request seq 6400 (frag 10712: 1472@0+) 12: 02: 18. 257282 IP dhcp-19 -211. engr. scu. edu > Bobadilla. scu. edu: icmp (frag 10712: 1472@1472+) 12: 02: 18. 258498 IP dhcp-19 -211. engr. scu. edu > Bobadilla. scu. edu: icmp (frag 10712: 1472@2944+) 12: 02: 18. 258502 IP dhcp-19 -115. engr. scu. edu. 137 > 129. 210. 19. 255. 137: udp 50 12: 02: 18. 259714 IP dhcp-19 -211. engr. scu. edu > Bobadilla. scu. edu: icmp (frag 10712: 1472@4416+) 12: 02: 18. 261177 IP dhcp-19 -211. engr. scu. edu > Bobadilla. scu. edu: icmp (frag 10712: 1472@5888+) 12: 02: 18. 262389 IP dhcp-19 -211. engr. scu. edu > Bobadilla. scu. edu: icmp (frag 10712: 1472@7360+) 12: 02: 18. 263604 IP dhcp-19 -211. engr. scu. edu > Bobadilla. scu. edu: icmp (frag 10712: 1472@8832+) 12: 02: 18. 264820 IP dhcp-19 -211. engr. scu. edu > Bobadilla. scu. edu: icmp (frag 10712: 1472@10304+) 12: 02: 18. 266037 IP dhcp-19 -211. engr. scu. edu > Bobadilla. scu. edu: icmp (frag 10712: 1472@11776+) 12: 02: 18. 267495 IP dhcp-19 -211. engr. scu. edu > Bobadilla. scu. edu: icmp (frag 10712: 1472@13248+) 12: 02: 18. 268712 IP dhcp-19 -211. engr. scu. edu > Bobadilla. scu. edu: icmp (frag 10712: 1472@14720+)
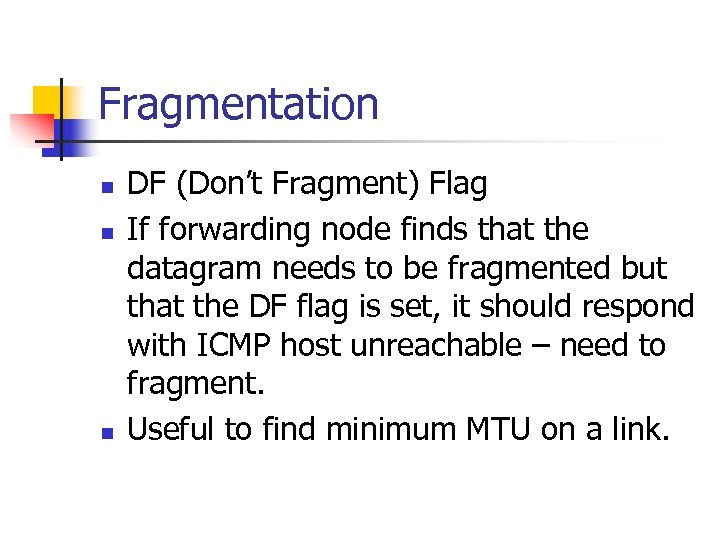 Fragmentation n DF (Don’t Fragment) Flag If forwarding node finds that the datagram needs to be fragmented but that the DF flag is set, it should respond with ICMP host unreachable – need to fragment. Useful to find minimum MTU on a link.
Fragmentation n DF (Don’t Fragment) Flag If forwarding node finds that the datagram needs to be fragmented but that the DF flag is set, it should respond with ICMP host unreachable – need to fragment. Useful to find minimum MTU on a link.
 Fragmentation n Fragmentation has security implications n n n Stateless firewalls look only at individual packages. Protocol header is only in the first fragment. “Stealth attacks / scans” have evil payload only in the second and following fragments.
Fragmentation n Fragmentation has security implications n n n Stateless firewalls look only at individual packages. Protocol header is only in the first fragment. “Stealth attacks / scans” have evil payload only in the second and following fragments.
 Fragments: Teardrop and Friends n Teardrop (1997) n n n Fragments with overlapping offset fields. Many contemporary OS crashed, hang, rebooted. Jolt 2 n n Single fragment with non-zero offset. Receiving system allocates resources to reconstruct a datagram that never arrives.
Fragments: Teardrop and Friends n Teardrop (1997) n n n Fragments with overlapping offset fields. Many contemporary OS crashed, hang, rebooted. Jolt 2 n n Single fragment with non-zero offset. Receiving system allocates resources to reconstruct a datagram that never arrives.
 Fragments: Teardrop and Friends n Create fragments that seem to come from a GB datagram. n n Ping of Death n n Trusting OS tries to allocate memory and dies. Win 95 allowed to send a ping that was just a tad too long. Receiving host would crash. Unnamed Attacks n Missing fragments lead to resource allocation.
Fragments: Teardrop and Friends n Create fragments that seem to come from a GB datagram. n n Ping of Death n n Trusting OS tries to allocate memory and dies. Win 95 allowed to send a ping that was just a tad too long. Receiving host would crash. Unnamed Attacks n Missing fragments lead to resource allocation.
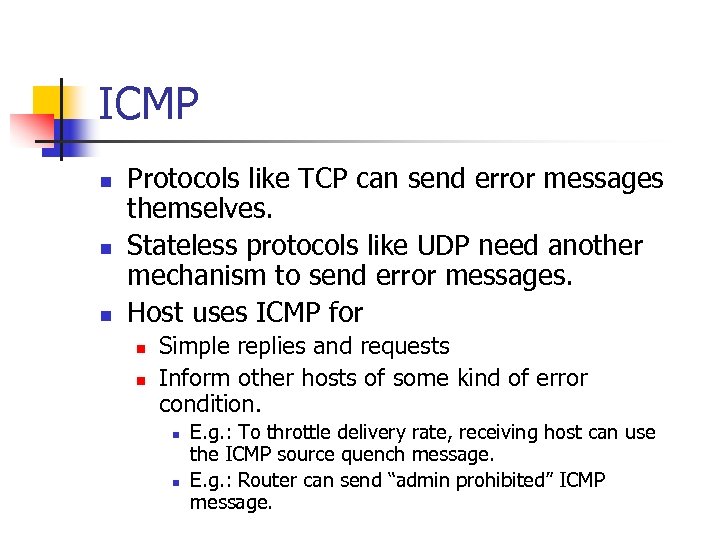 ICMP n n n Protocols like TCP can send error messages themselves. Stateless protocols like UDP need another mechanism to send error messages. Host uses ICMP for n n Simple replies and requests Inform other hosts of some kind of error condition. n n E. g. : To throttle delivery rate, receiving host can use the ICMP source quench message. E. g. : Router can send “admin prohibited” ICMP message.
ICMP n n n Protocols like TCP can send error messages themselves. Stateless protocols like UDP need another mechanism to send error messages. Host uses ICMP for n n Simple replies and requests Inform other hosts of some kind of error condition. n n E. g. : To throttle delivery rate, receiving host can use the ICMP source quench message. E. g. : Router can send “admin prohibited” ICMP message.
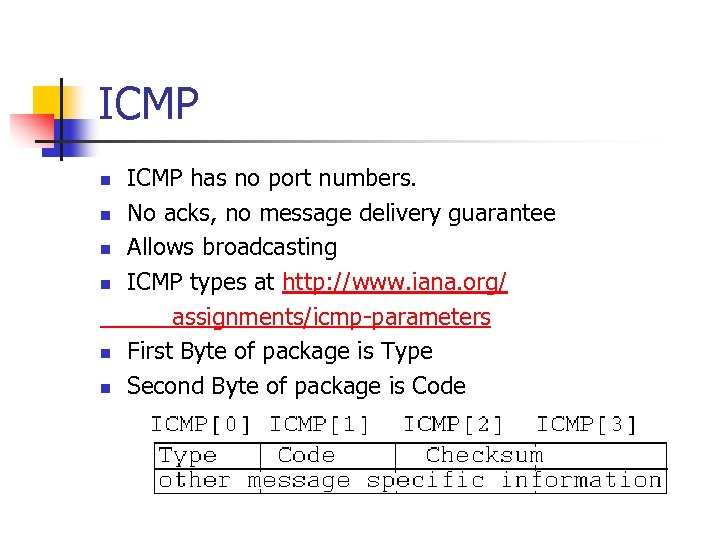 ICMP n n n ICMP has no port numbers. No acks, no message delivery guarantee Allows broadcasting ICMP types at http: //www. iana. org/ assignments/icmp-parameters First Byte of package is Type Second Byte of package is Code
ICMP n n n ICMP has no port numbers. No acks, no message delivery guarantee Allows broadcasting ICMP types at http: //www. iana. org/ assignments/icmp-parameters First Byte of package is Type Second Byte of package is Code
 ICMP n Attackers can use ICMP for scanning: n n n Mapping a network. Detect availability of target. Detect OS through the way that host responds.
ICMP n Attackers can use ICMP for scanning: n n n Mapping a network. Detect availability of target. Detect OS through the way that host responds.
 ICMP Tireless Mapper n n n Sends ICMP echo requests messages to all possible IP addresses Many IDS might not capture this scan if the number of packages per hour is small. Therefore: Firewalls should filter incoming ping requests.
ICMP Tireless Mapper n n n Sends ICMP echo requests messages to all possible IP addresses Many IDS might not capture this scan if the number of packages per hour is small. Therefore: Firewalls should filter incoming ping requests.
 ICMP Efficient Mapper n Use the ICMP echo request with a broadcast address. n Ping 129. 210. 19. 255
ICMP Efficient Mapper n Use the ICMP echo request with a broadcast address. n Ping 129. 210. 19. 255
 ICMP Clever Mapper n Use a different ICMP message such as ICMP address mask. n Determines the class of the network
ICMP Clever Mapper n Use a different ICMP message such as ICMP address mask. n Determines the class of the network
 ICMP: Normal activity Normal messages: n Host unreachable n Port unreachable n Admin prohibited n Need to fragment n Time exceeded in transit
ICMP: Normal activity Normal messages: n Host unreachable n Port unreachable n Admin prohibited n Need to fragment n Time exceeded in transit
 ICMP: Normal activity Host unreachable n Router at target host’s network sends such a message. n This gives out info to an attacker. n Some routers (Cisco) allow an access control list entry: n no ip unreachable
ICMP: Normal activity Host unreachable n Router at target host’s network sends such a message. n This gives out info to an attacker. n Some routers (Cisco) allow an access control list entry: n no ip unreachable
 ICMP: Normal activity Port unreachable n target. host > sending. host: icmp: target. host udp port ntp unreachable (DF) n Used for UDP n TCP has the RESET message to inform sender.
ICMP: Normal activity Port unreachable n target. host > sending. host: icmp: target. host udp port ntp unreachable (DF) n Used for UDP n TCP has the RESET message to inform sender.
 ICMP: Normal activity Unreachable - Admin Prohibited n Router informs sender that this type of message cannot be forwarded. n n Router decision based on access control list. Message leaks information to outside scanner.
ICMP: Normal activity Unreachable - Admin Prohibited n Router informs sender that this type of message cannot be forwarded. n n Router decision based on access control list. Message leaks information to outside scanner.
 ICMP: Normal activity Need to Frag n Router informs sender that DF is set, but that the package is larger than the MTU.
ICMP: Normal activity Need to Frag n Router informs sender that DF is set, but that the package is larger than the MTU.
 ICMP: Normal activity Time Exceeded In-Transit n Packages contain Time To Live (TTL) value. n Each router handling a package decrements the TTL value. n If TTL is zero, router discards package and sends the Time Exceeded In-Transit message to the sender.
ICMP: Normal activity Time Exceeded In-Transit n Packages contain Time To Live (TTL) value. n Each router handling a package decrements the TTL value. n If TTL is zero, router discards package and sends the Time Exceeded In-Transit message to the sender.
 ICMP: Normal activity n ICMP messages contain additional date in the package. n n In particular: IP header followed by eight bytes of protocol header and data of the original datagram. Not all OS implementations do this in exactly the same way. n n Nmap used this for OS fingerprinting. Lately, all TCP/IP stack implementations have been fixed to remove OS idiosyncracies.
ICMP: Normal activity n ICMP messages contain additional date in the package. n n In particular: IP header followed by eight bytes of protocol header and data of the original datagram. Not all OS implementations do this in exactly the same way. n n Nmap used this for OS fingerprinting. Lately, all TCP/IP stack implementations have been fixed to remove OS idiosyncracies.
 Malicious ICMP: Smurf Attack Smurf attack on victim 129. 219. 198 n Step 1: Send ICMP echo request to a broadcast address with spoofed IP of 129. 219. 198 n Step 2: Router allows in ICMP echo request to broadcast address n Step 3: All live hosts respond with ICMP echo reply to real machine with source IP 129. 219. 198
Malicious ICMP: Smurf Attack Smurf attack on victim 129. 219. 198 n Step 1: Send ICMP echo request to a broadcast address with spoofed IP of 129. 219. 198 n Step 2: Router allows in ICMP echo request to broadcast address n Step 3: All live hosts respond with ICMP echo reply to real machine with source IP 129. 219. 198
 Malicious ICMP: Smurf Attack n ISMP Smurf Attack n n Denial of Service Attack. Effort of Attacker << Effort of Victim. Uses ICMP replies from network as an amplifier. Works well if victim has a slow connection.
Malicious ICMP: Smurf Attack n ISMP Smurf Attack n n Denial of Service Attack. Effort of Attacker << Effort of Victim. Uses ICMP replies from network as an amplifier. Works well if victim has a slow connection.
 Malicious ICMP: Tribal Flood Network n n Based on Smurf Creates zombies out of compromised machines Compromised machines use a trigger to start bombarding a victim with requests Many variations on this theme
Malicious ICMP: Tribal Flood Network n n Based on Smurf Creates zombies out of compromised machines Compromised machines use a trigger to start bombarding a victim with requests Many variations on this theme
 Malicious ICMP: Winfreeze (obsolete) n n Uses the ICMP redirect message. Legal use is to update routing information. Flood of redirect message causes the victim (Win 95 / Win 98) to redirect traffic to itself via random hosts. Victim spends too much time updating routing table.
Malicious ICMP: Winfreeze (obsolete) n n Uses the ICMP redirect message. Legal use is to update routing information. Flood of redirect message causes the victim (Win 95 / Win 98) to redirect traffic to itself via random hosts. Victim spends too much time updating routing table.
 Malicious ICMP: Loki n n Uses ICMP packages for covert channel A compromised host with a Loki server responds to requests from a Loki client. Requests are sent via ping messages with data embedded in ICMP pings. Originally used bytes 6 and 7. n http: //sourceforge. net/projects/loki-lib/
Malicious ICMP: Loki n n Uses ICMP packages for covert channel A compromised host with a Loki server responds to requests from a Loki client. Requests are sent via ping messages with data embedded in ICMP pings. Originally used bytes 6 and 7. n http: //sourceforge. net/projects/loki-lib/
 Malicious ICMP: Simple Counter-Measures n n Limit ICMP messages at the firewall. Leads to inefficiencies, such as trying a TCP connection to a host that is down. Need to admit path MTU discovery. Log those that are let through.
Malicious ICMP: Simple Counter-Measures n n Limit ICMP messages at the firewall. Leads to inefficiencies, such as trying a TCP connection to a host that is down. Need to admit path MTU discovery. Log those that are let through.
 Harmless Behavior: TCP n Destination Host not Listening on Requested Port n n Receiver acknowledges and resets at the same time. Destination Host does not Exist n Router sends with the ICMP: Host xxx. yyy unreachable
Harmless Behavior: TCP n Destination Host not Listening on Requested Port n n Receiver acknowledges and resets at the same time. Destination Host does not Exist n Router sends with the ICMP: Host xxx. yyy unreachable
 Harmless Behavior: TCP n Destination Port Blocked n Router responds with an icmp message: n n icmp: xxx. yyy unreachable – admin prohibited filter Router does not respond. n Sender retries up to a protocol dependent maximum number of retries time
Harmless Behavior: TCP n Destination Port Blocked n Router responds with an icmp message: n n icmp: xxx. yyy unreachable – admin prohibited filter Router does not respond. n Sender retries up to a protocol dependent maximum number of retries time
 Harmless Behavior: UDP n Destination Host not Listening on Requested Port n Destination host sends icmp message: n n icmp: xxx. yyy port domain unreachable Or: destination host does not respond. n Sender will possibly retry several times
Harmless Behavior: UDP n Destination Host not Listening on Requested Port n Destination host sends icmp message: n n icmp: xxx. yyy port domain unreachable Or: destination host does not respond. n Sender will possibly retry several times
 Harmless Behavior: Windows Tracert n tracert (traceroute) uses ICMP pings n n n Tracing host sends ICMP echo request with TTL = 1. Then tracing host sends ICMP echo request with TTL = 2, etc. First router responds to first request. n n If not destination, then with icmp: time exceeded in transit message Second router responds to second request, etc.
Harmless Behavior: Windows Tracert n tracert (traceroute) uses ICMP pings n n n Tracing host sends ICMP echo request with TTL = 1. Then tracing host sends ICMP echo request with TTL = 2, etc. First router responds to first request. n n If not destination, then with icmp: time exceeded in transit message Second router responds to second request, etc.
 Harmless Behavior: Unix Tracert n traceroute uses UDP to random ephemeral port. n n n Tracing host sends UDP package with TTL = 1. Then tracing host sends UDP package with TTL = 2, etc. First router responds to first request. n If not destination, then with icmp: time exceeded in transit message n Second router responds to second request, etc. n Target responds with a port unreachable message.
Harmless Behavior: Unix Tracert n traceroute uses UDP to random ephemeral port. n n n Tracing host sends UDP package with TTL = 1. Then tracing host sends UDP package with TTL = 2, etc. First router responds to first request. n If not destination, then with icmp: time exceeded in transit message n Second router responds to second request, etc. n Target responds with a port unreachable message.
 FTP n n Uses TCP Active / Passive FTP Both use port 21 to issue FTP commands. Active FTP: n n Uses port 20 for data. FTP server establishes connection to client
FTP n n Uses TCP Active / Passive FTP Both use port 21 to issue FTP commands. Active FTP: n n Uses port 20 for data. FTP server establishes connection to client
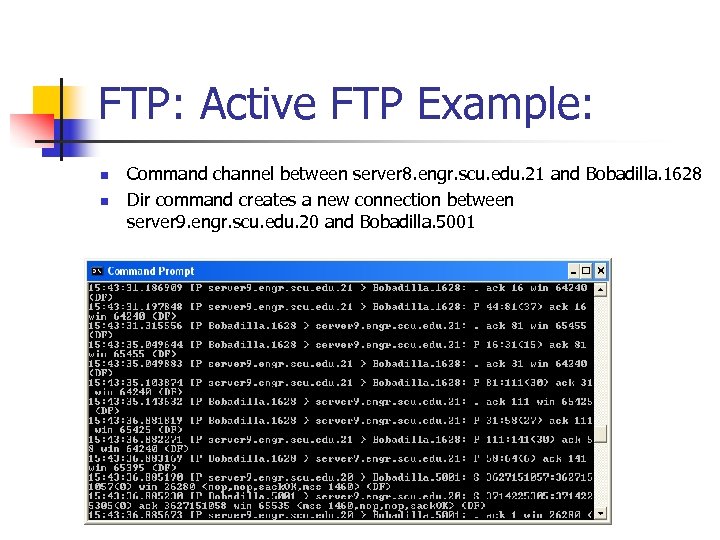 FTP: Active FTP Example: n n Command channel between server 8. engr. scu. edu. 21 and Bobadilla. 1628 Dir command creates a new connection between server 9. engr. scu. edu. 20 and Bobadilla. 5001
FTP: Active FTP Example: n n Command channel between server 8. engr. scu. edu. 21 and Bobadilla. 1628 Dir command creates a new connection between server 9. engr. scu. edu. 20 and Bobadilla. 5001
 FTP n n The opening of a connection from the outside to an ephemeral port is dangerous. Passive FTP: The client initiates the data connection to port 20.
FTP n n The opening of a connection from the outside to an ephemeral port is dangerous. Passive FTP: The client initiates the data connection to port 20.
 Malicious TCP Use: Mitnick Attack (obsolete) n SYN flood n n n Goal is to disconnect victim from the net. Throws hundreds / thousands of SYN packets Return address is spoofed. Recipient’s stack of connections waiting to be established is flooded. Still works with DDo. S attack.
Malicious TCP Use: Mitnick Attack (obsolete) n SYN flood n n n Goal is to disconnect victim from the net. Throws hundreds / thousands of SYN packets Return address is spoofed. Recipient’s stack of connections waiting to be established is flooded. Still works with DDo. S attack.
 Malicious TCP Use: Mitnick Attack (obsolete) n Identify Trust Relationships n n n Extensive network mapping. Nbtstat/finger, showmount, rpcinfo -r, … Rpcinfo provides information about the remote procedure call services and their ports
Malicious TCP Use: Mitnick Attack (obsolete) n Identify Trust Relationships n n n Extensive network mapping. Nbtstat/finger, showmount, rpcinfo -r, … Rpcinfo provides information about the remote procedure call services and their ports
 Malicious TCP Use: Mitnick Attack (obsolete) n Initiate a number of TCP connections to the host. n n n Send SYN packet. Receive SYN/ACK packet. Send RES so that victim is not flooded. Observe the sequence number values between different connections. Can they be predicted?
Malicious TCP Use: Mitnick Attack (obsolete) n Initiate a number of TCP connections to the host. n n n Send SYN packet. Receive SYN/ACK packet. Send RES so that victim is not flooded. Observe the sequence number values between different connections. Can they be predicted?
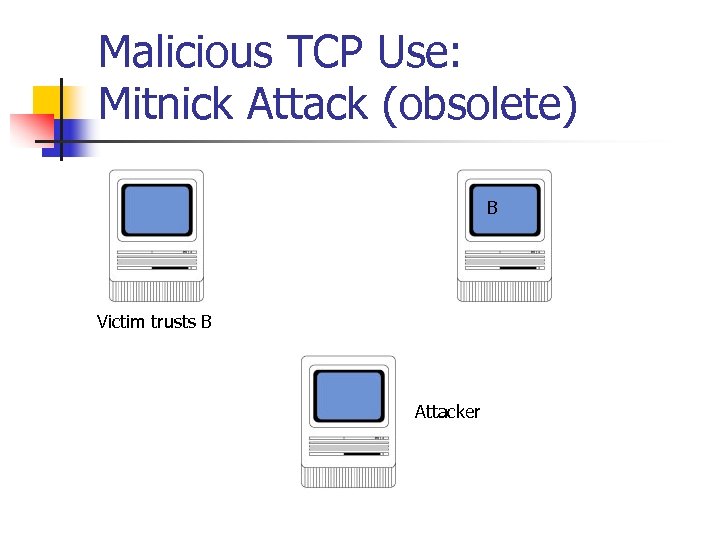 Malicious TCP Use: Mitnick Attack (obsolete) B Victim trusts B Attacker
Malicious TCP Use: Mitnick Attack (obsolete) B Victim trusts B Attacker
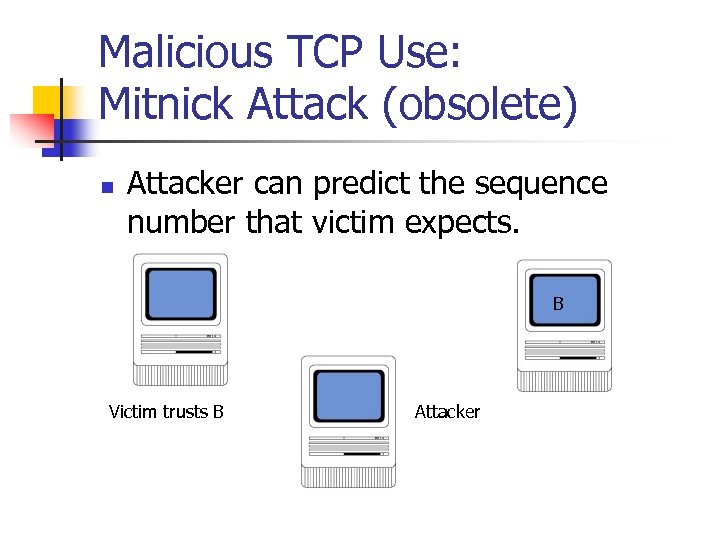 Malicious TCP Use: Mitnick Attack (obsolete) n Attacker can predict the sequence number that victim expects. B Victim trusts B Attacker
Malicious TCP Use: Mitnick Attack (obsolete) n Attacker can predict the sequence number that victim expects. B Victim trusts B Attacker
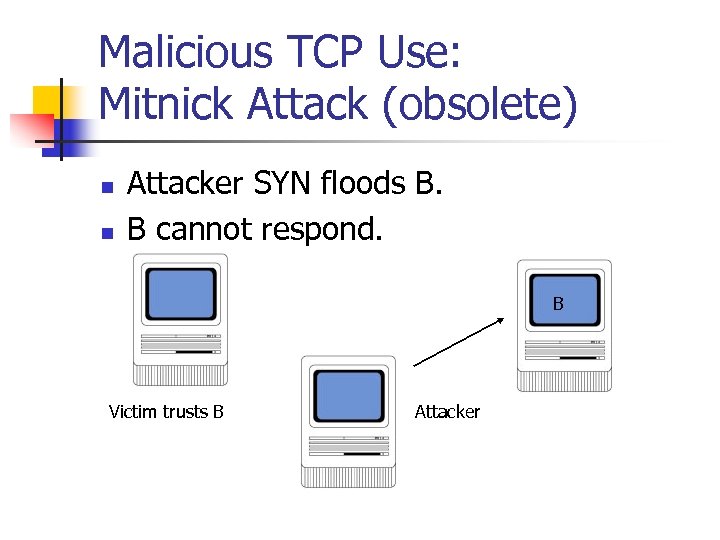 Malicious TCP Use: Mitnick Attack (obsolete) n n Attacker SYN floods B. B cannot respond. B Victim trusts B Attacker
Malicious TCP Use: Mitnick Attack (obsolete) n n Attacker SYN floods B. B cannot respond. B Victim trusts B Attacker
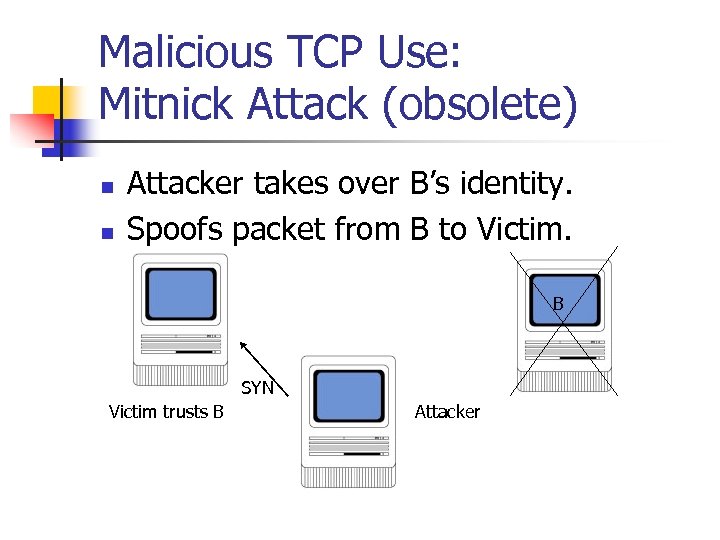 Malicious TCP Use: Mitnick Attack (obsolete) n n Attacker takes over B’s identity. Spoofs packet from B to Victim. B SYN Victim trusts B Attacker
Malicious TCP Use: Mitnick Attack (obsolete) n n Attacker takes over B’s identity. Spoofs packet from B to Victim. B SYN Victim trusts B Attacker
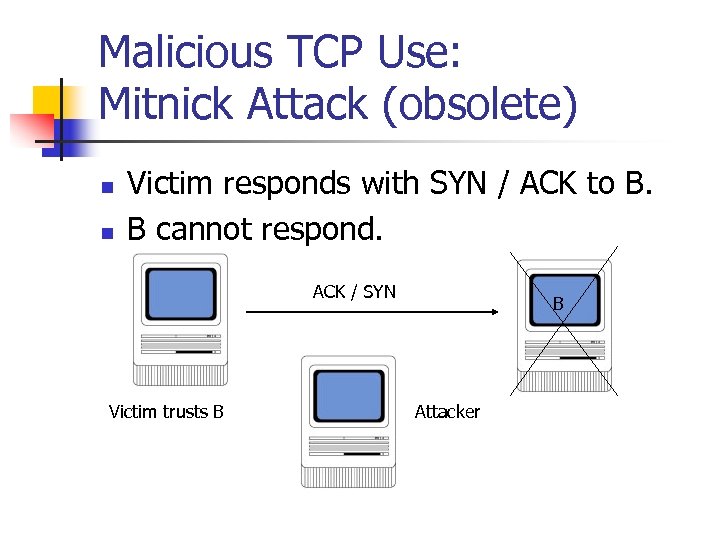 Malicious TCP Use: Mitnick Attack (obsolete) n n Victim responds with SYN / ACK to B. B cannot respond. ACK / SYN Victim trusts B B Attacker
Malicious TCP Use: Mitnick Attack (obsolete) n n Victim responds with SYN / ACK to B. B cannot respond. ACK / SYN Victim trusts B B Attacker
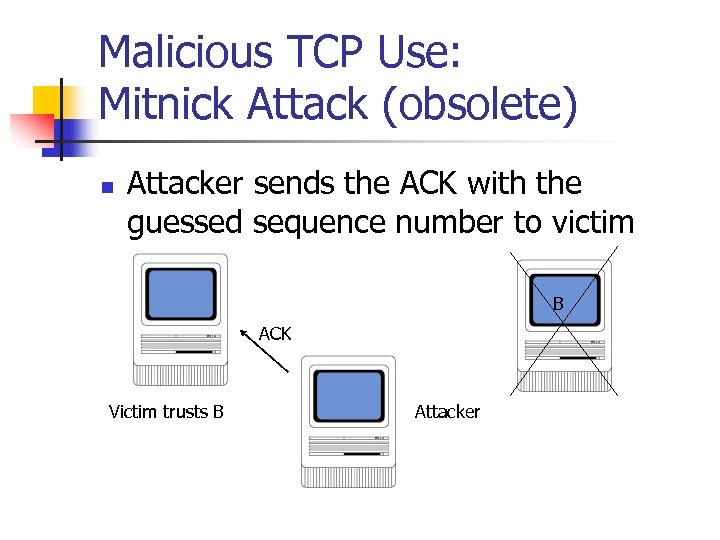 Malicious TCP Use: Mitnick Attack (obsolete) n Attacker sends the ACK with the guessed sequence number to victim B ACK Victim trusts B Attacker
Malicious TCP Use: Mitnick Attack (obsolete) n Attacker sends the ACK with the guessed sequence number to victim B ACK Victim trusts B Attacker
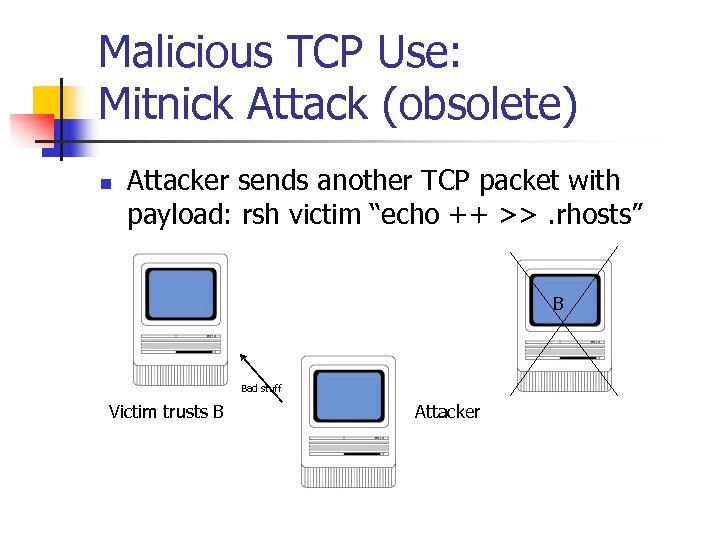 Malicious TCP Use: Mitnick Attack (obsolete) n Attacker sends another TCP packet with payload: rsh victim “echo ++ >>. rhosts” B Bad stuff Victim trusts B Attacker
Malicious TCP Use: Mitnick Attack (obsolete) n Attacker sends another TCP packet with payload: rsh victim “echo ++ >>. rhosts” B Bad stuff Victim trusts B Attacker
 Malicious TCP Use: Mitnick Attack (obsolete) n Now victim trusts everyone. B Victim trusts everyone. Attacker
Malicious TCP Use: Mitnick Attack (obsolete) n Now victim trusts everyone. B Victim trusts everyone. Attacker
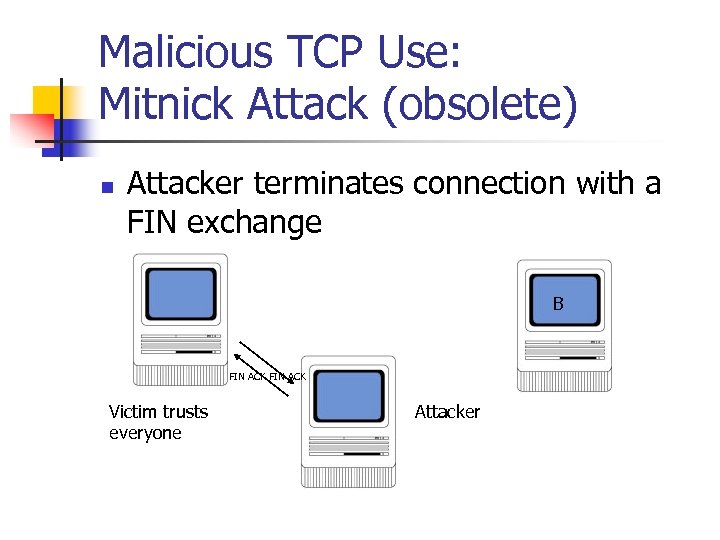 Malicious TCP Use: Mitnick Attack (obsolete) n Attacker terminates connection with a FIN exchange B FIN ACK Victim trusts everyone Attacker
Malicious TCP Use: Mitnick Attack (obsolete) n Attacker terminates connection with a FIN exchange B FIN ACK Victim trusts everyone Attacker
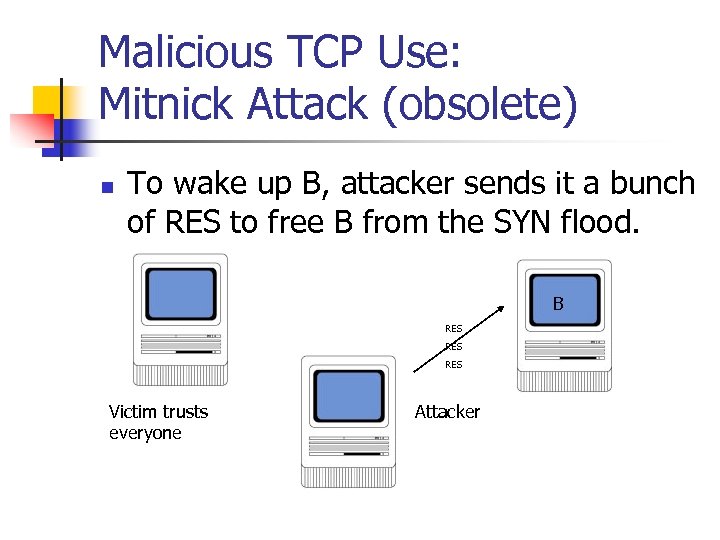 Malicious TCP Use: Mitnick Attack (obsolete) n To wake up B, attacker sends it a bunch of RES to free B from the SYN flood. B RES RES Victim trusts everyone Attacker
Malicious TCP Use: Mitnick Attack (obsolete) n To wake up B, attacker sends it a bunch of RES to free B from the SYN flood. B RES RES Victim trusts everyone Attacker
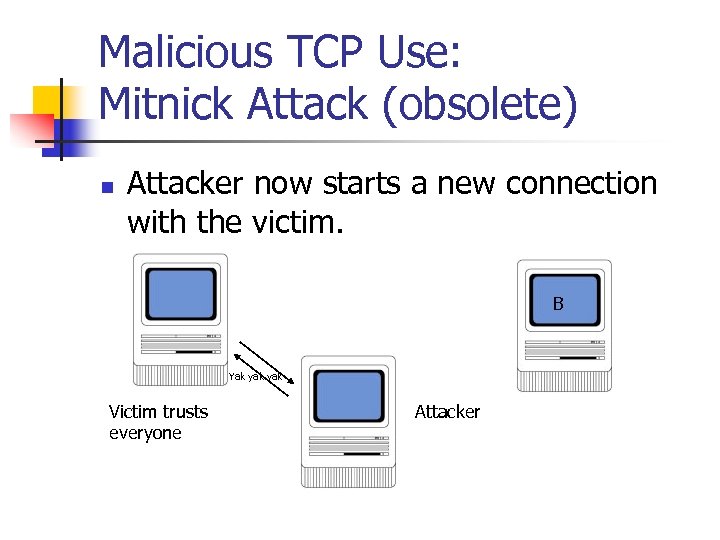 Malicious TCP Use: Mitnick Attack (obsolete) n Attacker now starts a new connection with the victim. B Yak yak Victim trusts everyone Attacker
Malicious TCP Use: Mitnick Attack (obsolete) n Attacker now starts a new connection with the victim. B Yak yak Victim trusts everyone Attacker
 Malicious TCP Use: Mitnick Attack Detection n n Network based intrusion detection (NID) can find the original site mapping. NID can find the reconnaissance by finding “finger” “showmount” etc. commands. n n n Directed to the same port (111). This is a dangerous port. Frequent.
Malicious TCP Use: Mitnick Attack Detection n n Network based intrusion detection (NID) can find the original site mapping. NID can find the reconnaissance by finding “finger” “showmount” etc. commands. n n n Directed to the same port (111). This is a dangerous port. Frequent.
 Malicious TCP Use: Mitnick Attack Detection n Host scans log instances where a single system accesses multiple hosts at the same time. Host-based Intrusion Detection (HID) can find access to a single port. HID / Tripwire could find changes to. rhosts.
Malicious TCP Use: Mitnick Attack Detection n Host scans log instances where a single system accesses multiple hosts at the same time. Host-based Intrusion Detection (HID) can find access to a single port. HID / Tripwire could find changes to. rhosts.
 Malicious TCP Use: Mitnick Attack Detection Computer Forensics can detect the attack by n Logging network traffic. n Examining MAC of important files (. rhosts)
Malicious TCP Use: Mitnick Attack Detection Computer Forensics can detect the attack by n Logging network traffic. n Examining MAC of important files (. rhosts)
 Malicious TCP Use: Mitnick Attack Prevention n Router-based Firewall blocks certain type of traffic. n n Host-based firewall blocks n n Network mapping. SYN flooding. Access to dangerous ports. Security policy n n Disallows reconnaissance tools. Enforces better authentication.
Malicious TCP Use: Mitnick Attack Prevention n Router-based Firewall blocks certain type of traffic. n n Host-based firewall blocks n n Network mapping. SYN flooding. Access to dangerous ports. Security policy n n Disallows reconnaissance tools. Enforces better authentication.
 Domain Name Servers n n Provide mapping from host names to IP addresses. DNS resolution process n n n Client sends a gethostbyname message to the local domain name server. Local domain name server sends back ip address. Uses UDP (almost exclusively)
Domain Name Servers n n Provide mapping from host names to IP addresses. DNS resolution process n n n Client sends a gethostbyname message to the local domain name server. Local domain name server sends back ip address. Uses UDP (almost exclusively)
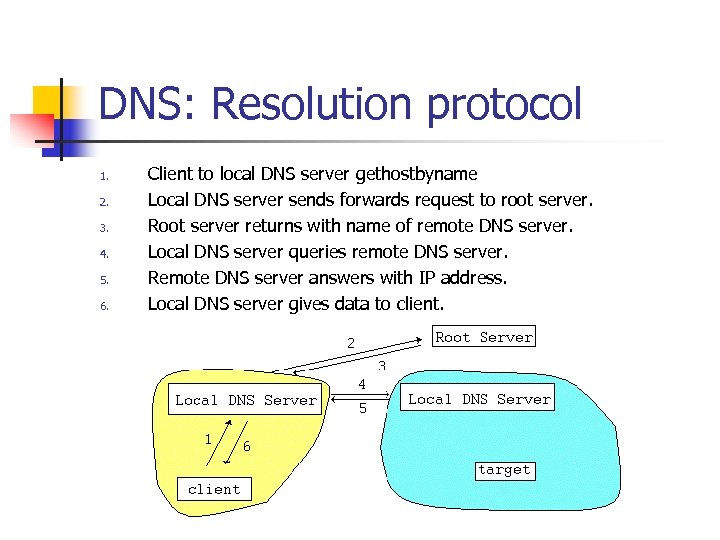 DNS: Resolution protocol 1. 2. 3. 4. 5. 6. Client to local DNS server gethostbyname Local DNS server sends forwards request to root server. Root server returns with name of remote DNS server. Local DNS server queries remote DNS server. Remote DNS server answers with IP address. Local DNS server gives data to client.
DNS: Resolution protocol 1. 2. 3. 4. 5. 6. Client to local DNS server gethostbyname Local DNS server sends forwards request to root server. Root server returns with name of remote DNS server. Local DNS server queries remote DNS server. Remote DNS server answers with IP address. Local DNS server gives data to client.
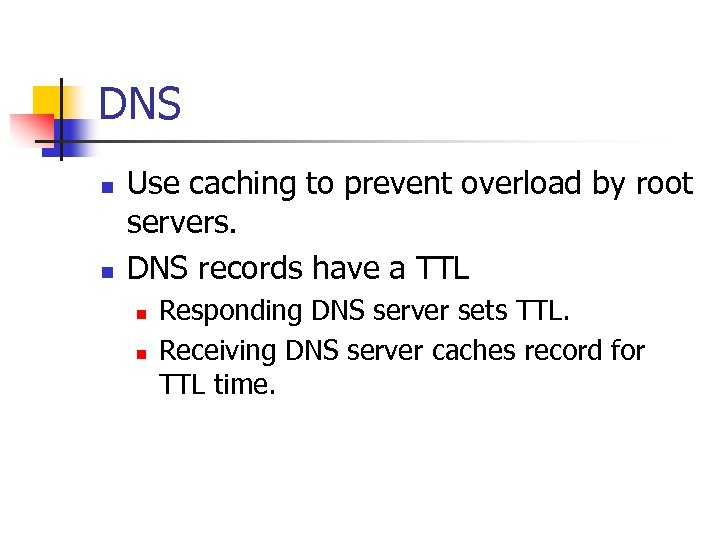 DNS n n Use caching to prevent overload by root servers. DNS records have a TTL n n Responding DNS server sets TTL. Receiving DNS server caches record for TTL time.
DNS n n Use caching to prevent overload by root servers. DNS records have a TTL n n Responding DNS server sets TTL. Receiving DNS server caches record for TTL time.
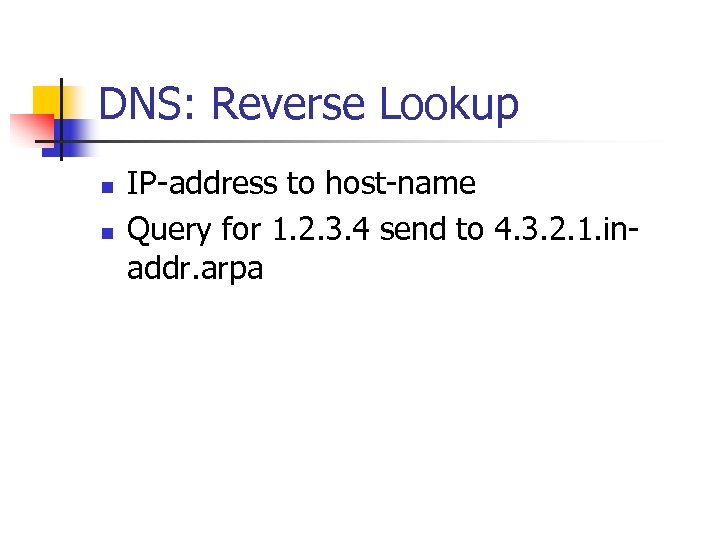 DNS: Reverse Lookup n n IP-address to host-name Query for 1. 2. 3. 4 send to 4. 3. 2. 1. inaddr. arpa
DNS: Reverse Lookup n n IP-address to host-name Query for 1. 2. 3. 4 send to 4. 3. 2. 1. inaddr. arpa
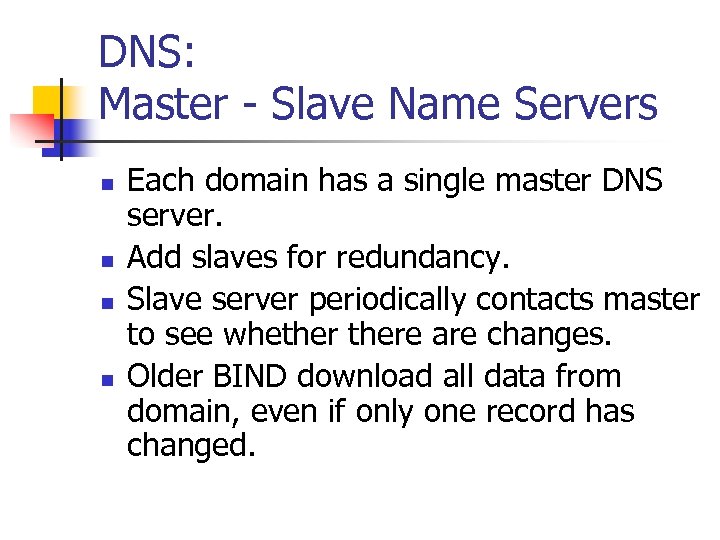 DNS: Master - Slave Name Servers n n Each domain has a single master DNS server. Add slaves for redundancy. Slave server periodically contacts master to see whethere are changes. Older BIND download all data from domain, even if only one record has changed.
DNS: Master - Slave Name Servers n n Each domain has a single master DNS server. Add slaves for redundancy. Slave server periodically contacts master to see whethere are changes. Older BIND download all data from domain, even if only one record has changed.
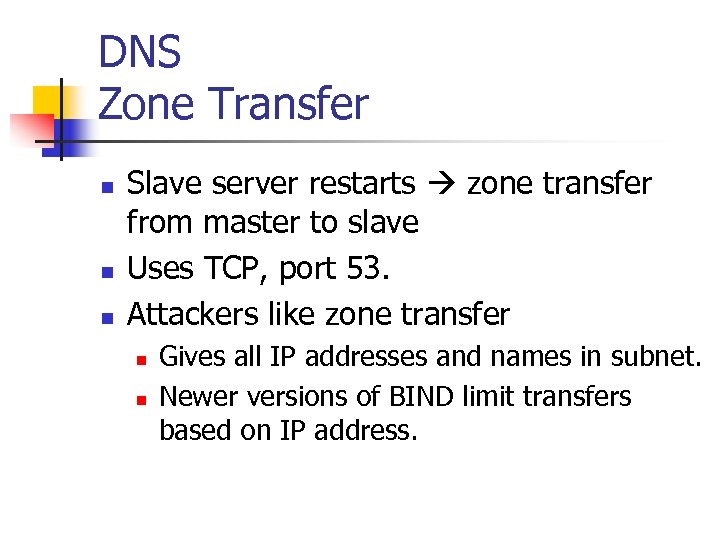 DNS Zone Transfer n n n Slave server restarts zone transfer from master to slave Uses TCP, port 53. Attackers like zone transfer n n Gives all IP addresses and names in subnet. Newer versions of BIND limit transfers based on IP address.
DNS Zone Transfer n n n Slave server restarts zone transfer from master to slave Uses TCP, port 53. Attackers like zone transfer n n Gives all IP addresses and names in subnet. Newer versions of BIND limit transfers based on IP address.
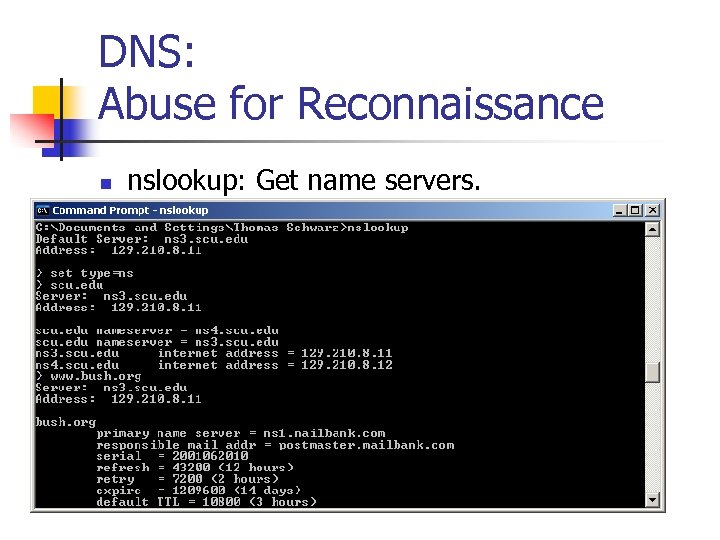 DNS: Abuse for Reconnaissance n nslookup: Get name servers.
DNS: Abuse for Reconnaissance n nslookup: Get name servers.
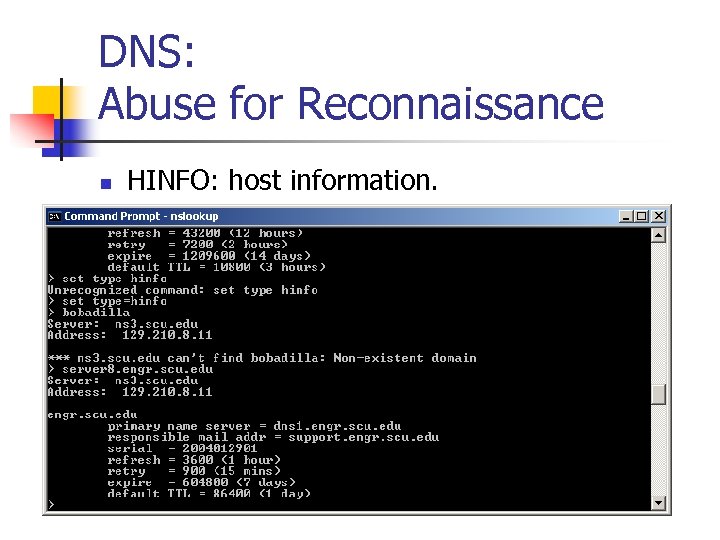 DNS: Abuse for Reconnaissance n HINFO: host information.
DNS: Abuse for Reconnaissance n HINFO: host information.
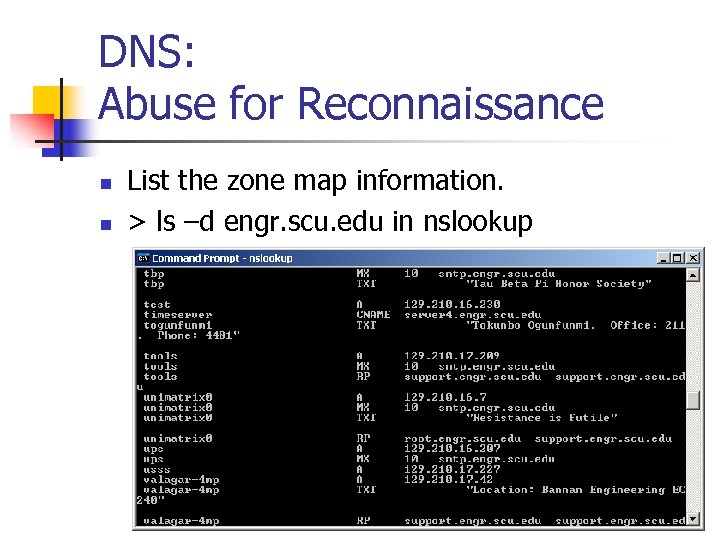 DNS: Abuse for Reconnaissance n n List the zone map information. > ls –d engr. scu. edu in nslookup
DNS: Abuse for Reconnaissance n n List the zone map information. > ls –d engr. scu. edu in nslookup
 DNS: Abuses and Problems n n DNS cache poisoning Affects BIND versions before 8. 1. 1. Based on lack of authentication Some BIND versions cache every DNS data they see.
DNS: Abuses and Problems n n DNS cache poisoning Affects BIND versions before 8. 1. 1. Based on lack of authentication Some BIND versions cache every DNS data they see.
 DNS Cache Poisoning n n Attack on Hillary Clinton’s Run for Senate Website Traffic to www. hillary 2000. org (IP address 206. 245. 150. 74) redirected to www. hillaryno. com (IP address 206. 245. 150. 74. )
DNS Cache Poisoning n n Attack on Hillary Clinton’s Run for Senate Website Traffic to www. hillary 2000. org (IP address 206. 245. 150. 74) redirected to www. hillaryno. com (IP address 206. 245. 150. 74. )
 DNS Cache Poisoning n Step 1: Evil sends a bogus query to the victim’s name server that contains data www. hillary 2000. org at 206. 245. 150. 74
DNS Cache Poisoning n Step 1: Evil sends a bogus query to the victim’s name server that contains data www. hillary 2000. org at 206. 245. 150. 74
 DNS Cache Poisoning n n n Step 2: Name server accepts the bogus information (even though it is contained in a query). Step 3: Victim requests IP address of hillary 2000. org and is directed to hillaryno. com. Vulnerability arises from lack of authentication and of using queries to update entries at the queried server.
DNS Cache Poisoning n n n Step 2: Name server accepts the bogus information (even though it is contained in a query). Step 3: Victim requests IP address of hillary 2000. org and is directed to hillaryno. com. Vulnerability arises from lack of authentication and of using queries to update entries at the queried server.
 DNS Cache Poisoning n Birthday Attack n n Attacker sends large number of queries to a vulnerable name server asking for hillary 2000. Attacker sends an equal number of phony replies (with the poisoned data). Name server will generate requests to resolve hillary 2000. With high probability, one of the phony answers will have the same transaction number as the name server’s query.
DNS Cache Poisoning n Birthday Attack n n Attacker sends large number of queries to a vulnerable name server asking for hillary 2000. Attacker sends an equal number of phony replies (with the poisoned data). Name server will generate requests to resolve hillary 2000. With high probability, one of the phony answers will have the same transaction number as the name server’s query.
 DNS: The Bind Birthday Attack
DNS: The Bind Birthday Attack
 DNS Cache Poisoning n n n Redirect traffic to a fake Pay-Pal or other ecommerce site. Set-up Man in the Middle Attacks Defenses: n n Domain Owner has to rely on the DNS system. ISP name server admin needs to protect by n n n Updating BIND or replacing it with djbdns Two name servers, one for the public domain information to the outside, another for internal use. End user has to rely on the DNS system.
DNS Cache Poisoning n n n Redirect traffic to a fake Pay-Pal or other ecommerce site. Set-up Man in the Middle Attacks Defenses: n n Domain Owner has to rely on the DNS system. ISP name server admin needs to protect by n n n Updating BIND or replacing it with djbdns Two name servers, one for the public domain information to the outside, another for internal use. End user has to rely on the DNS system.
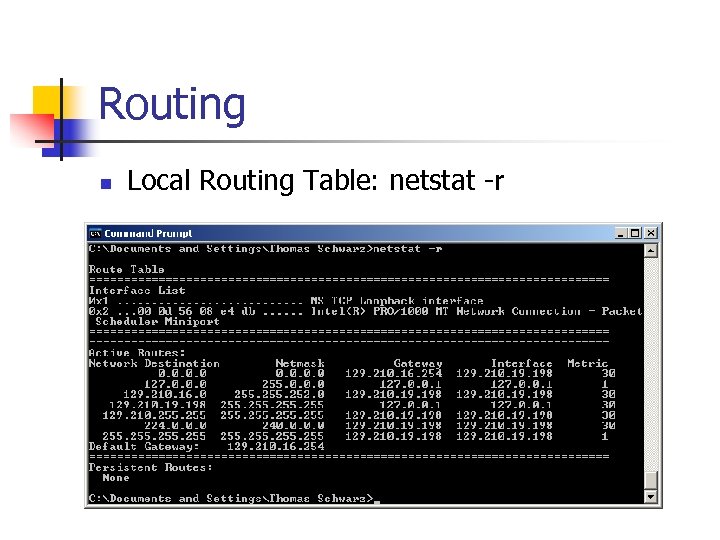 Routing n Local Routing Table: netstat -r
Routing n Local Routing Table: netstat -r
 Static Routing n IP Layer searches the routing table in the following order n n n Search for a matching destination host address Search for a matching destination network address Search for a default entry
Static Routing n IP Layer searches the routing table in the following order n n n Search for a matching destination host address Search for a matching destination network address Search for a default entry
 Routing n n n Static routes are typically added during the boot process. Administrative changes with a “routing” command. ICMP routing discovery messages
Routing n n n Static routes are typically added during the boot process. Administrative changes with a “routing” command. ICMP routing discovery messages
 Routing Changes n n A host might have inefficient entries in the routing table. ICMP Router Discovery Protocol (IRDP) n n n ICMP redirect messages ICMP routing discovery messages IRDP needs to be enabled.
Routing Changes n n A host might have inefficient entries in the routing table. ICMP Router Discovery Protocol (IRDP) n n n ICMP redirect messages ICMP routing discovery messages IRDP needs to be enabled.
 Routing Changes n ICMP Redirect Message n n A sends message to D. Routing table says to send to B first.
Routing Changes n ICMP Redirect Message n n A sends message to D. Routing table says to send to B first.
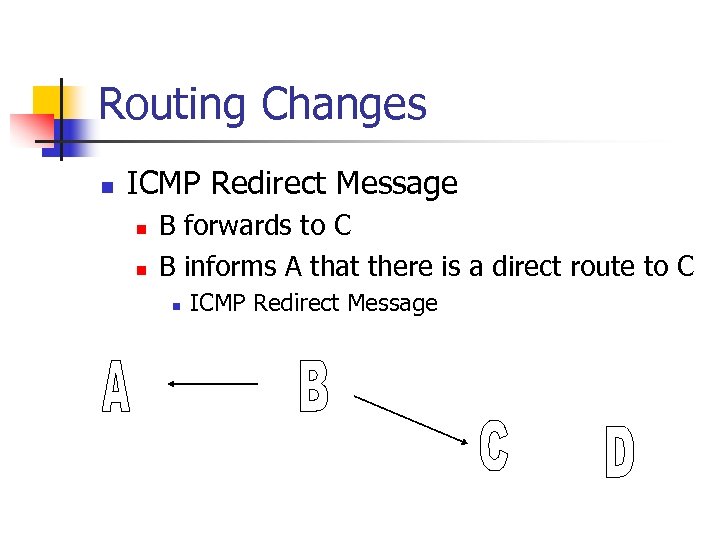 Routing Changes n ICMP Redirect Message n n B forwards to C B informs A that there is a direct route to C n ICMP Redirect Message
Routing Changes n ICMP Redirect Message n n B forwards to C B informs A that there is a direct route to C n ICMP Redirect Message
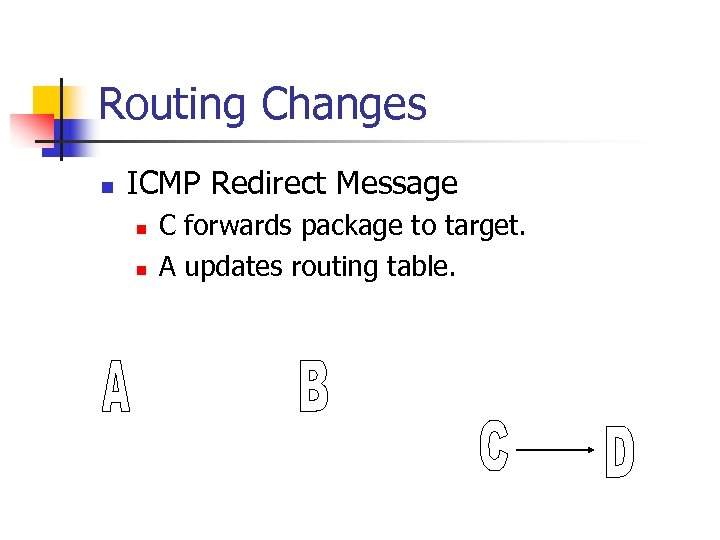 Routing Changes n ICMP Redirect Message n n C forwards package to target. A updates routing table.
Routing Changes n ICMP Redirect Message n n C forwards package to target. A updates routing table.
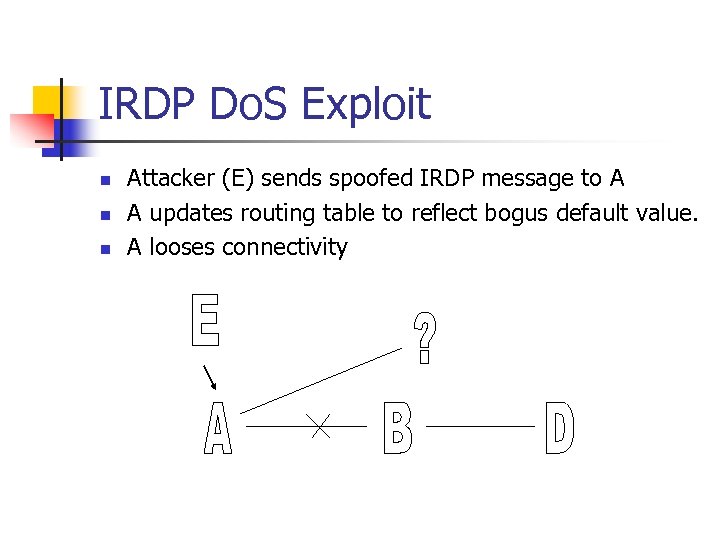 IRDP Do. S Exploit n n n Attacker (E) sends spoofed IRDP message to A A updates routing table to reflect bogus default value. A looses connectivity
IRDP Do. S Exploit n n n Attacker (E) sends spoofed IRDP message to A A updates routing table to reflect bogus default value. A looses connectivity
 IRDP Windows Exploit n n n Windows (95, 98, 2000) and some Solaris systems are vulnerable. If a Windows hosts runs a Dynamic Host Configuration Protocol (DHCP) client, it obtains its default route from the DHCP server. ICMP router advertisement can be spoofed. First router advertisement is checked for correct IP address. Second router advertisement is erroneously not.
IRDP Windows Exploit n n n Windows (95, 98, 2000) and some Solaris systems are vulnerable. If a Windows hosts runs a Dynamic Host Configuration Protocol (DHCP) client, it obtains its default route from the DHCP server. ICMP router advertisement can be spoofed. First router advertisement is checked for correct IP address. Second router advertisement is erroneously not.
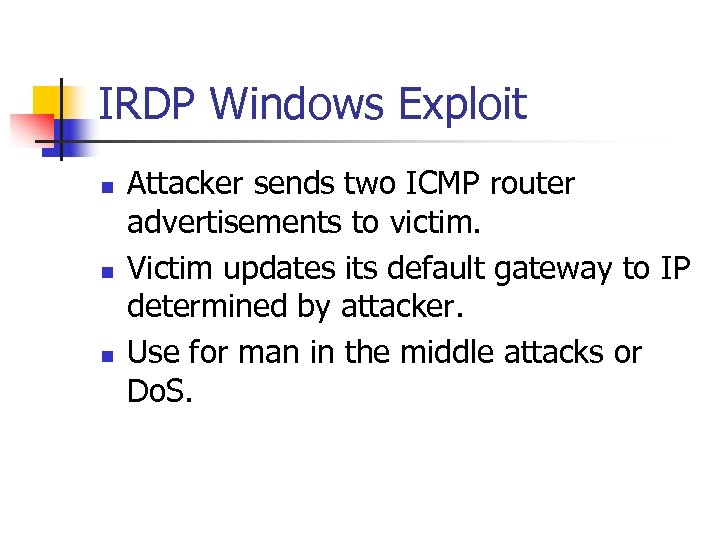 IRDP Windows Exploit n n n Attacker sends two ICMP router advertisements to victim. Victim updates its default gateway to IP determined by attacker. Use for man in the middle attacks or Do. S.
IRDP Windows Exploit n n n Attacker sends two ICMP router advertisements to victim. Victim updates its default gateway to IP determined by attacker. Use for man in the middle attacks or Do. S.
 ARP Poisoning n n Address resolution protocol associates MAC addresses with IP addresses. Four Messages n n ARP Request: “Who has this IP? ” ARP Reply: “I have this IP. My MAC is …” Reverse ARP Request: “Who has that MAC? ” Reverse ARP Request Reply: “I have that MAC, my IP is …”
ARP Poisoning n n Address resolution protocol associates MAC addresses with IP addresses. Four Messages n n ARP Request: “Who has this IP? ” ARP Reply: “I have this IP. My MAC is …” Reverse ARP Request: “Who has that MAC? ” Reverse ARP Request Reply: “I have that MAC, my IP is …”
 ARP Poisoning n n n ARP is very efficient, but does not do any authentication. Many OS still accept ARP replies even without making an ARP request. ARP poisoning: Spoofing an ARP package with false ARP data.
ARP Poisoning n n n ARP is very efficient, but does not do any authentication. Many OS still accept ARP replies even without making an ARP request. ARP poisoning: Spoofing an ARP package with false ARP data.
 ARP Poisoning n Denial of Service: n n Spoofed ARP message can associate the default gateway address with a nonexisting MAC. Traffic to the outside is no longer picked up.
ARP Poisoning n Denial of Service: n n Spoofed ARP message can associate the default gateway address with a nonexisting MAC. Traffic to the outside is no longer picked up.
 ARP Poisoning n Man in the Middle n Intercept traffic between devices A and B. n n n n n A has IP IA and MAC MA. B has IP IB and MAC MB. Attacker has machine C with MAC MC. Attacker sends an ARP reply to B: IA is at MC. B updates its ARP cache entry: IA is at MC. Attacker sends an ARP reply to A: IB is at MC. A updates its ARP cache entry: IB is at MC. A sends traffic to IB on a level 1 frame to MC. C intercepts the package and forwards it to MB. Traffic from A to B (and vice versa) now flows through C.
ARP Poisoning n Man in the Middle n Intercept traffic between devices A and B. n n n n n A has IP IA and MAC MA. B has IP IB and MAC MB. Attacker has machine C with MAC MC. Attacker sends an ARP reply to B: IA is at MC. B updates its ARP cache entry: IA is at MC. Attacker sends an ARP reply to A: IB is at MC. A updates its ARP cache entry: IB is at MC. A sends traffic to IB on a level 1 frame to MC. C intercepts the package and forwards it to MB. Traffic from A to B (and vice versa) now flows through C.
 ARP Poisoning n MAC flooding n n n n Switches maintain a MAC to port table. Traffic only flows to destination. Attacker sends lots of bogus ARP data to switch. Switch’s ARP table is flooded. Switches either stop functioning (Do. S attack) or drop to hub mode. Switch in hub mode forwards a package to all ports. Allows traffic to be sniffed.
ARP Poisoning n MAC flooding n n n n Switches maintain a MAC to port table. Traffic only flows to destination. Attacker sends lots of bogus ARP data to switch. Switch’s ARP table is flooded. Switches either stop functioning (Do. S attack) or drop to hub mode. Switch in hub mode forwards a package to all ports. Allows traffic to be sniffed.
 ARP Poisoning n Small networks: n n n Could use a static ARP table. Disables ARP messaging. All ARP entries need to be put in by hand maintained. Will not work with DHCP. Maintenance becomes quickly impossible with larger size of network. Some Win OS will still accept and use dynamic ARP updates, even if all routes are statically encoded.
ARP Poisoning n Small networks: n n n Could use a static ARP table. Disables ARP messaging. All ARP entries need to be put in by hand maintained. Will not work with DHCP. Maintenance becomes quickly impossible with larger size of network. Some Win OS will still accept and use dynamic ARP updates, even if all routes are statically encoded.
 ARP Poisoning n Large Networks n n Use Port Security features on higher-end switches. Allow only one MAC address. Prevents hackers from embedding their MAC address more than once. All networks n Monitor ARP traffic (ARP monitoring tool)
ARP Poisoning n Large Networks n n Use Port Security features on higher-end switches. Allow only one MAC address. Prevents hackers from embedding their MAC address more than once. All networks n Monitor ARP traffic (ARP monitoring tool)
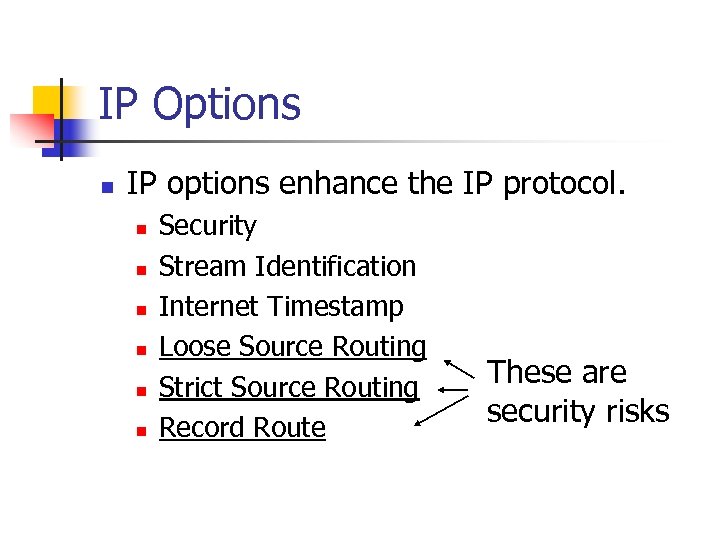 IP Options n IP options enhance the IP protocol. n n n Security Stream Identification Internet Timestamp Loose Source Routing Strict Source Routing Record Route These are security risks
IP Options n IP options enhance the IP protocol. n n n Security Stream Identification Internet Timestamp Loose Source Routing Strict Source Routing Record Route These are security risks
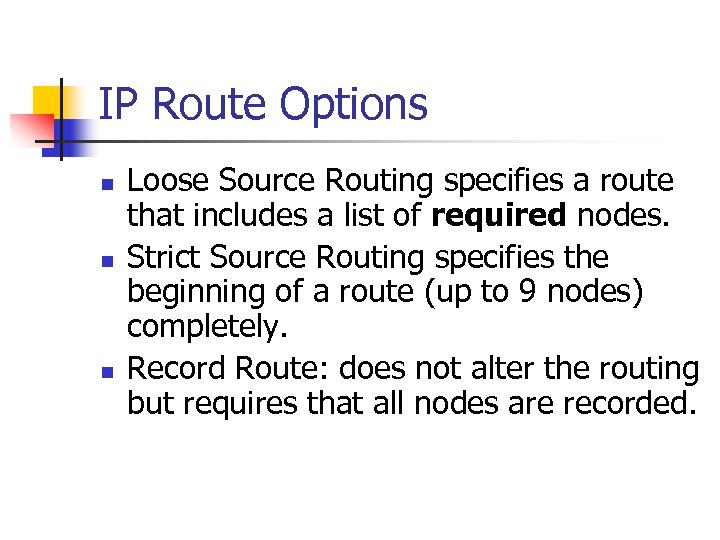 IP Route Options n n n Loose Source Routing specifies a route that includes a list of required nodes. Strict Source Routing specifies the beginning of a route (up to 9 nodes) completely. Record Route: does not alter the routing but requires that all nodes are recorded.
IP Route Options n n n Loose Source Routing specifies a route that includes a list of required nodes. Strict Source Routing specifies the beginning of a route (up to 9 nodes) completely. Record Route: does not alter the routing but requires that all nodes are recorded.
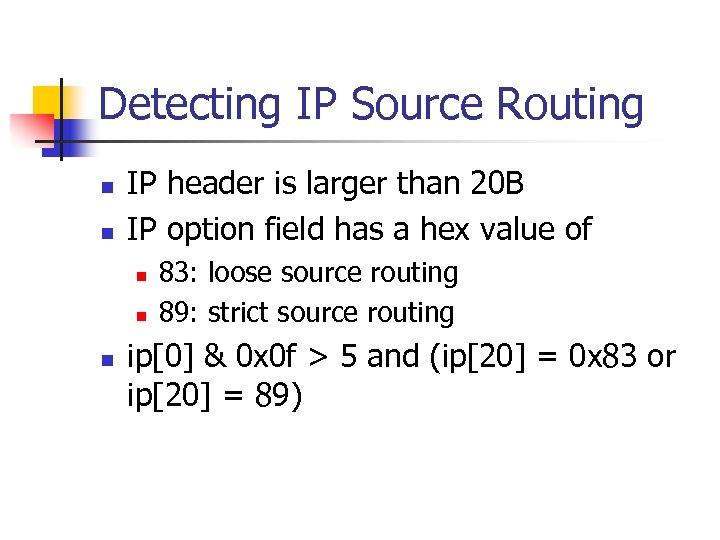 Detecting IP Source Routing n n IP header is larger than 20 B IP option field has a hex value of n n n 83: loose source routing 89: strict source routing ip[0] & 0 x 0 f > 5 and (ip[20] = 0 x 83 or ip[20] = 89)
Detecting IP Source Routing n n IP header is larger than 20 B IP option field has a hex value of n n n 83: loose source routing 89: strict source routing ip[0] & 0 x 0 f > 5 and (ip[20] = 0 x 83 or ip[20] = 89)
 Source Route Exploit n n n Spoofing host requires source routing through a host trusted by the victim. Victim decides that the traffic comes from a trusted host. Therefore: firewalls need to disable source-routing or network admin needs to disable trust relationships.
Source Route Exploit n n n Spoofing host requires source routing through a host trusted by the victim. Victim decides that the traffic comes from a trusted host. Therefore: firewalls need to disable source-routing or network admin needs to disable trust relationships.
 Internet Group Management Protocol (IGMP) n n n Defined by RFC 1112. IGMP messages use IP Protocol 2 IGMP are used to join and leave multicast groups.
Internet Group Management Protocol (IGMP) n n n Defined by RFC 1112. IGMP messages use IP Protocol 2 IGMP are used to join and leave multicast groups.
 TCP/IP Related Evidence n Sniffer Logs A computer intrusion left a program called router behind. Investigation of the binary code revealed that it was a Portuguese language sniffer storing data in a given file. The sniffer file contained log entries of log-ins from Brazil to a non-authenticated account as well as further activities.
TCP/IP Related Evidence n Sniffer Logs A computer intrusion left a program called router behind. Investigation of the binary code revealed that it was a Portuguese language sniffer storing data in a given file. The sniffer file contained log entries of log-ins from Brazil to a non-authenticated account as well as further activities.
 TCP/IP Related Evidence n Authentication, Server Logs Maury Travis Case: During a series of homicides in St. Louis, a reporter received a letter with the location of an additional victim. The FBI determined that the map was from Expedia. com. The web server logs showed that only one IP address requested that particular map around the time that the letter was sent.
TCP/IP Related Evidence n Authentication, Server Logs Maury Travis Case: During a series of homicides in St. Louis, a reporter received a letter with the location of an additional victim. The FBI determined that the map was from Expedia. com. The web server logs showed that only one IP address requested that particular map around the time that the letter was sent.
 TCP/IP Related Evidence The IP address belonged to an ISP. The ISP logs showed that this IP address was registered to Maury Travis. The telephone number from the connection was made also belonged to Maury Travis. A (warranted) search of Maury Travis’ home found a torture chamber and videotapes of Maury torturing and killing victims. Maury killed himself while in custody. The total number of victims is unknown.
TCP/IP Related Evidence The IP address belonged to an ISP. The ISP logs showed that this IP address was registered to Maury Travis. The telephone number from the connection was made also belonged to Maury Travis. A (warranted) search of Maury Travis’ home found a torture chamber and videotapes of Maury torturing and killing victims. Maury killed himself while in custody. The total number of victims is unknown.
 TCP/IP Related Evidence n n Internet dial-up logs are created by RADIUS and TACACS authentication servers. These servers are also used for VPN concentrators. Kerberos logs authentication requests. …
TCP/IP Related Evidence n n Internet dial-up logs are created by RADIUS and TACACS authentication servers. These servers are also used for VPN concentrators. Kerberos logs authentication requests. …
 TCP/IP Related Evidence n Application Logs n n When someone defaces web servers, they usually view them shortly before and after defacement. The web logs might contain evidence of someone checking for vulnerabilities before defacement. n With the IP address that they used.
TCP/IP Related Evidence n Application Logs n n When someone defaces web servers, they usually view them shortly before and after defacement. The web logs might contain evidence of someone checking for vulnerabilities before defacement. n With the IP address that they used.
 TCP/IP Related Evidence n Application Logs n Mail servers log details of message. n Example: An email spoofer makes a typo. n n n Logs contains entries with backspaces, … OS log connections. Network devices log.
TCP/IP Related Evidence n Application Logs n Mail servers log details of message. n Example: An email spoofer makes a typo. n n n Logs contains entries with backspaces, … OS log connections. Network devices log.


